Access Protocol remote cRIO
Currently I have a set-up that allows me to communicate my cRIO remotely using series and TCP/IP protocols with serial modems and wireless routers/bridges. I would like to be able to extend this network using a cellular modem. Is it possible to use my code TCP/IP functionality for communication via a cellular modem or do I need to use features of Service Web of LabVIEW?
If this is possible using a Web Service, it is possible to have a real time application and a Web Service at the same time works as a starter on a cRIO app? I want the ability to actively pass the communication problems of network protocols.
Thank you
Matt
Hello Matt,
In General, the answer to your main question is Yes, you can use a cellular modem to the network at a cRIO. Devices like the BlueTree BT-6600 and Sierra Airlink Raven X have been used in the past with cRIOs. Using only the TCP/IP protocol with these modems, you must configure the modem to the port of the information forward for the cRIO based on IPv6 on the modem and the designation of the port. TCP/IP in LabVIEW functions just these two pieces of information, that I could find some information on the use of cRIO and cell phones, but nothing specific about the installer or difficulties you might face. This kind of network configuration is beyond the scope of what we support here at NOR, so unfortunately there is not much in our database on this subject.
It should not be necessary to use a Web Service to connect via the modem that you configure ports TCP/IP and IPs correctly. Web services use the HTTP protocol to transfer data via Ethernet or some physical network layer is in place. Therefore, the web service is simply a wrapper of information that transmitting on the same lines of communication. If you can not configure TCP/IP correctly, then web services can still run, but configuration ports and addresses IP is easier with TCP than web services. In addition, you can run a real-time application and a web service with startup applications. You could set up an application that includes the web interface screws or configure a web service which includes the action of applying background, but you can not have two startup applications. If you have configured a real-time application that uses TCP/IP, you can configure a set of background code that uses HTTP instead. This allows you to switch between protocols using a kind of input control, as a value Boolean network has published a shared variable, select in which case runs. This implementation is highly dependent on what you're trying to accomplish.
I hope you find some useful information. Good luck with your application.
Tags: NI Software
Similar Questions
-
Original title: the local policy of this system does ot allows you to open an interactive session
I get this error message when you try to access a remote desktop connection. The local policy of this system does ot allows you to open an interactive session
Hi CamilleHolt,
1. were you able to use the before remote desktop connection?
You can try the following steps and check if it helps.
a. Click Start, point to settings and then click Control Panel.
b. double-click System and select the remote settings and then click the Remote tab.
c. click Select users, and then add the name of the user account
d. click Add and then click OK.
Note: Adding users to the remote desktop group requires that you are connected via an administrator account.
Hope this information is useful.
Jeremy K
Microsoft Answers Support Engineer. -
Access to remote files blackBerry Z10
I don't have a problem with the XP pc, can access it remotely. my Vista pc is problematic, most of the time it shows "offline" and even when 'online' I can't always access shared folders.
Connected with link PCs, the two pc is matched, both have active WiFi.
Today, pilots would not charge when I plugged the USB Vista, the Z10 restarted with no luck.
Link uninstalled and re-installed, loading drivers and has worked perfectly, disconnected Z10, Lo an behold, remained connected to WiFi.
Wonder for how long.
-
Cannot access a remote LAN with Cisco Client
Hello
IAM using an ASA 5505 and connect with the Cisco Client 5.0.02.0090. The Client connects to the Remote LAN and get an IP of the SAA.
But I can't access the Remote LAN or ping the Interface of the ASA trainee.
Can someone help me with this problem?
If the client computer is in the same subnet as the other PC, then its dislikes a question ASA.
Just make sure that the client computer is in the subnet, default gateway of 192.168.20.100 192.168.20./24 and connected to a switchport on vlan 1.
Finally, check whether the DNS resolution works, or if you can browse the internet with the ip address.
-
My source data in the remote database schema (say C3.case). And I am trying to insert data of this CASE table in my database table (for example SIMS.case) I use the stored procedure to load the data.
I was going through the documentation and I thought that the creation of MV is not possible in this case is the source table in the remote database schema. Is this correct?
or create a link DB is the only option available to access the remote database schema table.
Thank you.
Hello
2929538 wrote:
My apologies for the bad conventions help. I meant remote schema.
the required data and the destination table, the two are in oracle, but in totally different schemas.
Yes, you said a table is in a scheme called C3, and the other is in a schema called SIMS. Are these schemas in the same database or in different databases?
If they are in the same database, then you do not have a database link. Or the other schema can reference tables in the other qualifying names correctly, for example
SELECT *.
OF C3. case_studies
...
assuming that the right privileges have been granted.
If the schemas are in different databases, a database link is the best way to access data in a database in a different database.
Without a database link, you will probably use some kind of use outside the database to write the data to a database, the file if necessary, transport and read in other databases. DataPump files of images or CSV files, as Paulzip said in answer to #1, could be used for this.
-
When I try to run the converter that we receive the following error message, FAILED: cannot access the remote Converter Standalone Agent service. It does not exist or is not responding.
RaymondT
Given that the conversion works, you can have a software or configuration of Windows Server. Check the Windows event logs. Anything in current policies that could prevent?
-
Able to interact with a Panel before the remote cRIO to a computer, but not another
I have a cRIO application that publishes a remote façade for the monitoring and control of the application. A PC (Win7 & firefox), I can see, interact and control the cRIO through published remote façade. A second PC, also Win7, I can see and monitor the status of the cRIO, but no interaction does not control remote that opens and it's true that I use IE, FF or Chrome as a browser. When a PC is connected to the cRIO, via a dedicated Ethernet connection and only the cRIO and PC are on this network. For this private network of two devices, the PC is always the address 192.168.1.1 while the cRIO always use 192.168.84.199 (port 8000).
The rules of firewall on both computers are configured to allow all inbound and outbound programs/ports/protocols to be used between these two IP addresses.
Two PC's have development systems LabVIEW to update installed on it (which more or less guarantees that they have the minimum requirement LV of execution necessary to see and use a remote façade).
What may be different on the PC who discovers, but cannot interact with the remote control?
Right-click on the second, and then select "take control of this VI.
As far I know - that a viewer of the remote façade can control the frame at any time - the rest cannot display.
-
RA-tunnel upward, but can not access to remote resources
The VPN client connects successfully to the PIX, but it does not appear that all traffic through the tunnel. There is a tunnel from site to site, which works very well, it's just the stuff of RA that doesn't. He had worked at some point and then stopped. This is a sanitized config:
:
6.3 (3) version PIX
interface ethernet0 car
interface ethernet1 100full
ethernet0 nameif outside security0
nameif ethernet1 inside the security100
activate the password *.
passwd *.
name of host depot-pix
domain.local domain name
fixup protocol dns-length maximum 512
fixup protocol ftp 21
fixup protocol h323 h225 1720
fixup protocol h323 ras 1718-1719
fixup protocol http 80
fixup protocol rsh 514
fixup protocol rtsp 554
fixup protocol sip 5060
fixup protocol sip udp 5060
fixup protocol 2000 skinny
No fixup not protocol smtp 25
fixup protocol sqlnet 1521
fixup protocol tftp 69
names of
name 2.2.2.2 cottage-pix
Server1 name 192.168.0.3
name 192.168.0.4 Server2
vpn ip 192.168.0.0 access list permit 255.255.255.0 192.168.10.0 255.255.255.0
vpn access list allow icmp a whole
vpn ip 192.168.0.0 access list permit 192.168.30.0 255.255.255.0 255.255.255.0 sign
access list permit ip 192.168.0.0 split tunnel 255.255.255.0 192.168.30.0 255.255.255.0
access-list acl_out permit icmp any one
acl_out tcp allowed access list any interface outside eq https
acl_out tcp allowed access list any interface outside eq 9333
pager lines 24
opening of session
monitor debug logging
debug logging in buffered memory
ICMP allow any inaccessible outside
Outside 1500 MTU
Within 1500 MTU
IP 1.2.3.4 address outside 255.255.255.248
IP address inside 192.168.0.1 255.255.255.0
alarm action IP verification of information
alarm action attack IP audit
IP local pool vpnPool 192.168.30.10 - 192.168.30.20
PDM logging 100 information
history of PDM activate
ARP timeout 14400
Global 1 interface (outside)
NAT (inside) 0-list of access vpn
NAT (inside) 1 0.0.0.0 0.0.0.0 0 0
public static tcp (indoor, outdoor) interface smtp server1 smtp netmask 255.255.255.255 0 0
public static tcp (indoor, outdoor) interface 5989 192.168.0.2 5989 netmask 255.255.255.255 0 0
public static tcp (indoor, outdoor) interface https server1 https netmask 255.255.255.255 0 0
public static tcp (indoor, outdoor) interface 9333 server2 9333 netmask 255.255.255.255 0 0
Access-group acl_out in interface outside
Route outside 0.0.0.0 0.0.0.0 1.2.3.5 1
Timeout xlate 0:05:00
Timeout conn 01:00 half-closed 0:10:00 udp 0: CPP 02:00 0:10:00 01:00 h225
H323 timeout 0:05:00 mgcp 0: sip from 05:00 0:30:00 sip_media 0:02:00
Timeout, uauth 0:05:00 absolute
GANYMEDE + Protocol Ganymede + AAA-server
RADIUS Protocol RADIUS AAA server
AAA-server local LOCAL Protocol
RADIUS protocol AAA-server raAuth
raAuth AAA-server (host server1 secretkey timeout 5 inside)
RADIUS protocol local AAA server
Enable http server
http 192.168.0.0 255.255.255.0 inside
No snmp server location
No snmp Server contact
SNMP-Server Community public
No trap to activate snmp Server
enable floodguard
Permitted connection ipsec sysopt
Crypto ipsec transform-set strong esp-3des esp-sha-hmac
Crypto-map Dynamics 20 set transformation-strong dynMap
map OutsideMap 10 ipsec-isakmp crypto
card crypto OutsideMap 10 is the vpn address
card crypto OutsideMap 10 set counterpart cottage-pix
map OutsideMap 10 game of transformation-strong crypto
map OutsideMap 20-isakmp ipsec crypto dynamic dynMap
card crypto client OutsideMap of authentication raAuth
OutsideMap interface card crypto outside
ISAKMP allows outside
ISAKMP key * address cottage-pix netmask 255.255.255.255
ISAKMP nat-traversal 20
part of pre authentication ISAKMP policy 9
ISAKMP policy 9 3des encryption
ISAKMP policy 9 sha hash
9 1 ISAKMP policy group
ISAKMP policy 9 life 86400
part of pre authentication ISAKMP policy 20
ISAKMP policy 20 3des encryption
ISAKMP policy 20 chopping sha
20 2 ISAKMP policy group
ISAKMP duration strategy of life 20 86400
vpngroup address vpnPool pool remoteAccess
vpngroup dns-server server1 remoteAccess
vpngroup remoteAccess wins-server server1
vpngroup remoteAccess by default-field domain.local
vpngroup split-tunnel remoteAccess split tunnel
vpngroup idle time 1800 remoteAccess
remoteAccess vpngroup password *.
management-access inside
Console timeout 0
dhcpd outside auto_config
Terminal width 80
Cryptochecksum:9f8a7e0796962279858931db84e4e14a
: endHello
Want to send traffic destined to remote clients, through the tunnel from Site to Site.
The recommendation is to use a different ACL for nat0 and crypto ACL.
Federico.
-
Unable to access the remote host
Here is the configuration of pix of my client, the problem, here is... whenever it uses a Cisco VPN dialier, it can connect to the VPN, but cannot access any host on the distance, but with the same vpn Dialer & VPN pcf file, when it is used with a connection high speed which is not route with this PIX (or not behind the PIX) It works very well. Yet one thing I noticed, it's only when I give a static NAT, it is able to access on the remote & not through a NAT GLOBAL PC when the PC is behind the PIX.
6.3 (3) version PIX
interface ethernet0 car
Auto interface ethernet1
Auto interface ethernet2
ethernet0 nameif outside security0
nameif ethernet1 inside the security100
nameif dmz security50 ethernet2
enable encrypted password xxx
enable encrypted password xxx
TA.qizy4R//ChqQH encrypted passwd
fixup protocol dns-maximum length 1024
fixup protocol ftp 21
fixup protocol h323 h225 1720
fixup protocol h323 ras 1718-1719
fixup protocol http 80
fixup protocol pptp 1723
fixup protocol rsh 514
fixup protocol rtsp 554
fixup protocol sip 5060
No fixup protocol sip udp 5060
fixup protocol 2000 skinny
No fixup not protocol smtp 25
fixup protocol sqlnet 1521
fixup protocol tftp 69
access ip-list 110 permit a whole
access-list 120 allow icmp a whole
access-list 120 allow esp a whole
logging console warnings
Monitor logging warnings
logging buffered stored notifications
recording of debug trap
the logging queue 0
Outside 1500 MTU
Within 1500 MTU
MTU 1500 dmz
IP address outside x.x.x.x 255.255.255.240
IP address inside 192.168.0.1 255.255.0.0
no ip address address dmz
alarm action IP verification of information
alarm action attack IP audit
IP local pool homeuser_vpn 192.168.1.1 - 192.168.1.254
location of PDM 192.168.0.80 255.255.255.255 inside
location of PDM 192.168.0.207 255.255.255.255 inside
location of PDM 0.0.0.0 0.0.0.0 outdoors
forest warnings of PDM 100
history of PDM activate
ARP timeout 14400
Global 1 x.x.x.66 (outside)
NAT (inside) 0-list of access 123nonat
NAT (inside) 1 192.168.0.0 255.255.0.0 0 0
public static x.x.x.70 (Interior, exterior) 192.168.3.1 netmask 255.255.255.255 0 0
public static x.x.x.76 (Interior, exterior) 192.168.3.2 netmask 255.255.255.255 0 0
static (inside, outside) x.x.x.77 192.168.3.3 netmask 255.255.255.255 0 0
Access-group 120 in external interface
Access-group 110 in the interface inside
Route outside 0.0.0.0 0.0.0.0 x.x.x.x 1
Timeout xlate 03:00
Timeout conn 01:00 half-closed 0:10:00 udp 0: CPP 02:00 0:10:00 01:00 h225
H323 timeout 0:05:00 mgcp 0: sip from 05:00 0:30:00 sip_media 0:02:00
Timeout, uauth 0:05:00 absolute
GANYMEDE + Protocol Ganymede + AAA-server
RADIUS Protocol RADIUS AAA server
AAA-server local LOCAL Protocol
the ssh LOCAL console AAA authentication
source of x.x.x.x server NTP outside prefer
Enable http server
http 0.0.0.0 0.0.0.0 outdoors
http 192.168.0.207 255.255.255.255 inside
No snmp server location
No snmp Server contact
SNMP-Server Community public
No trap to activate snmp Server
enable floodguard
Telnet 192.168.0.197 255.255.255.255 inside
Telnet 192.168.0.80 255.255.255.255 inside
Telnet timeout 5
SSH 0.0.0.0 0.0.0.0 outdoors
SSH 192.168.0.0 255.255.0.0 inside
SSH timeout 60
Console timeout 0
dhcpd lease 3600
dhcpd ping_timeout 750
username admin password encrypted xxxx privilege 15
username password encrypted xxx privilege 2 admin1
Terminal width 80
Cryptochecksum:xxx
: end
# 123
Anand,
I would check to make sure that the N - NAT has something like: -.
"permit access ip 192.168.0.0 list 123nonat 255.255.255.0 192.168.1.0 255.255.255.0.
And enable NAT - T - she might be his house do not understand/IPSEC passthrough device support:--
"isakmp nat-traversal 20.
And add: -.
"access-list 120 permit udp any any eq 4500.
HTH.
-
Difficulty accessing 1 remote desktop when connected with VPN
Hello world
I have an ASA 5505 and have a problem where when I connect via VPN, I can RDP into a server using its internal address but I can't RDP to another server using its internal address.
One that I can connect to a an IP of 192.168.2.10 and I can't connect to a a 192.168.2.11 on 3390 port IP address.
The two rules are configured exactly the same except for the IP addresses and I can't see why I can't connect to this server.
I am also able to connect to my camera system with an IP on port 37777 192.168.2.25 and able to ping any other device on the network internal.
I also tried ping he and Telnet to port 3390 without success.
Here is the config.
ASA 4,0000 Version 1
!
!
interface Ethernet0/0
switchport access vlan 3
!
interface Ethernet0/1
!
interface Ethernet0/2
switchport access vlan 2
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
!
interface Ethernet0/7
!
interface Vlan2
nameif inside
security-level 100
IP 192.168.2.2 255.255.255.0
!
interface Vlan3
nameif outside
security-level 0
10.1.1.1 IP address 255.255.255.0
!
passive FTP mode
clock timezone IS - 5
clock to summer time EDT recurring
network obj_any object
subnet 0.0.0.0 0.0.0.0
network of the OWTS-LAN-OUT object
10.1.1.10 range 10.1.1.49
network of the OWTS-LAN-IN object
Subnet 192.168.2.0 255.255.255.0
service of the RDP3389 object
service destination tcp 3389 eq
Description of DC
the object SERVER-IN network
host 192.168.2.10
network of the SERVER-OUT object
Home 10.1.1.50
network of the CAMERA-IN-TCP object
Home 192.168.2.25
network of the CAMERA-OUT object
Home 10.1.1.51
service object CAMERA-TCP
Service tcp destination eq 37777
the object SERVER-Virt-IN network
Home 192.168.2.11
network of the SERVER-Virt-OUT object
Home 10.1.1.52
service of the RDP3390 object
Service tcp destination eq 3390
Description of VS for Master
network of the CAMERA-IN-UDP object
Home 192.168.2.25
service object CAMERA-UDP
Service udp destination eq 37778
the object OWTS LAN OUT VPN network
subnet 10.1.1.128 255.255.255.128
the object SERVER-Virt-IN-VPN network
Home 192.168.2.11
the object SERVER-IN-VPN network
host 192.168.2.10
the object CAMERA-IN-VPN network
Home 192.168.2.25
object-group Protocol TCPUDP
object-protocol udp
object-tcp protocol
AnyConnect_Client_Local_Print deny ip extended access list a whole
AnyConnect_Client_Local_Print list extended access permit tcp any any eq lpd
Note AnyConnect_Client_Local_Print of access list IPP: Internet Printing Protocol
AnyConnect_Client_Local_Print list extended access permit tcp any any eq 631
print the access-list AnyConnect_Client_Local_Print Note Windows port
AnyConnect_Client_Local_Print list extended access permit tcp any any eq 9100
access-list AnyConnect_Client_Local_Print mDNS Note: multicast DNS protocol
AnyConnect_Client_Local_Print list extended access permit udp any host 224.0.0.251 eq 5353
AnyConnect_Client_Local_Print of access list LLMNR Note: link Local Multicast Name Resolution protocol
AnyConnect_Client_Local_Print list extended access permit udp any host 224.0.0.252 eq 5355
Note access list TCP/NetBIOS protocol AnyConnect_Client_Local_Print
AnyConnect_Client_Local_Print list extended access permit tcp any any eq 137
AnyConnect_Client_Local_Print list extended access udp allowed any any eq netbios-ns
implicit rule of access-list inside1_access_in Note: allow all traffic to less secure networks
inside1_access_in of access allowed any ip an extended list
outside_access_in list extended access allowed object RDP3389 any host 192.168.2.10
outside_access_in list extended access allowed object RDP3390 any host 192.168.2.11
outside_access_in list extended access allowed object CAMERA TCP any host 192.168.2.25
outside_access_in list extended access allowed object CAMERA UDP any host 192.168.2.25
pager lines 24
Enable logging
exploitation forest-size of the buffer 10240
asdm of logging of information
Within 1500 MTU
Outside 1500 MTU
local pool RAVPN 10.1.1.129 - 10.1.1.254 255.255.255.128 IP mask
no failover
ICMP unreachable rate-limit 1 burst-size 1
don't allow no asdm history
ARP timeout 14400
NAT static destination SERVER-IN-VPN SERVER-IN-VPN (indoor, outdoor) static source OWTS LAN OUT VPN OWTS-LAN-OUT-VPN
NAT static destination of CAMERA-IN-VPN VPN-IN-CAMERA (indoor, outdoor) static source OWTS LAN OUT VPN OWTS-LAN-OUT-VPN
NAT static destination of SERVER Virt-IN-VPN-SERVER-Virt-IN-VPN (indoor, outdoor) static source OWTS LAN OUT VPN OWTS-LAN-OUT-VPN
!
network of the OWTS-LAN-IN object
NAT dynamic interface (indoor, outdoor)
the object SERVER-IN network
NAT (inside, outside) Shared SERVER-OUT service tcp 3389 3389
network of the CAMERA-IN-TCP object
NAT (inside, outside) static CAMERA-OFF 37777 37777 tcp service
the object SERVER-Virt-IN network
NAT (inside, outside) Shared SERVER-Virt-OUT 3390 3390 tcp service
inside1_access_in access to the interface inside group
Access-group outside_access_in in interface outside
Route outside 0.0.0.0 0.0.0.0 10.1.1.2 1
Timeout xlate 03:00
Pat-xlate timeout 0:00:30
Timeout conn 01:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
Sunrpc timeout 0:10:00 h323 0:05:00 h225 mgcp from 01:00 0:05:00 mgcp-pat 0:05:00
Sip timeout 0:30:00 sip_media 0:02:00 prompt Protocol sip-0: 03:00 sip - disconnect 0:02:00
Timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
Floating conn timeout 0:00:00
dynamic-access-policy-registration DfltAccessPolicy
identity of the user by default-domain LOCAL
Enable http server
http 192.168.2.0 255.255.255.0 inside
No snmp server location
No snmp Server contact
Server enable SNMP traps snmp authentication linkup, linkdown warmstart of cold start
Crypto ipsec transform-set ikev1 ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
Crypto ipsec transform-set ikev1 ESP-DES-SHA esp - esp-sha-hmac
Crypto ipsec transform-set ikev1 SHA-ESP-3DES esp-3des esp-sha-hmac
Crypto ipsec transform-set ikev1 esp ESP-DES-MD5-esp-md5-hmac
Crypto ipsec transform-set ikev1 ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
Crypto ipsec transform-set ikev1 ESP-3DES-MD5-esp-3des esp-md5-hmac
Crypto ipsec transform-set ikev1 ESP-AES-256-SHA esp-aes-256 esp-sha-hmac
Crypto ipsec transform-set ikev1 ESP-AES-128-SHA aes - esp esp-sha-hmac
Crypto ipsec transform-set ikev1 ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
Crypto ipsec transform-set ikev1 ESP-AES-128-MD5-esp - aes esp-md5-hmac
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 pfs Group1 set
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 define ikev1 transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA MD5-ESP-3DES ESP
DES-SHA ESP-DES-MD5
outside_map card crypto 65535-isakmp dynamic ipsec SYSTEM_DEFAULT_CRYPTO_MAP
outside_map interface card crypto outside
Crypto ca trustpoint ASDM_TrustPoint0
Terminal registration
name of the object CN = SACTSGRO
Configure CRL
Crypto ikev1 allow outside
IKEv1 crypto policy 10
authentication crack
aes-256 encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 20
authentication rsa - sig
aes-256 encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 30
preshared authentication
aes-256 encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 40
authentication crack
aes-192 encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 50
authentication rsa - sig
aes-192 encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 60
preshared authentication
aes-192 encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 70
authentication crack
aes encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 80
authentication rsa - sig
aes encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 90
preshared authentication
aes encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 100
authentication crack
3des encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 110
authentication rsa - sig
3des encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 120
preshared authentication
3des encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 130
authentication crack
the Encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 140
authentication rsa - sig
the Encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 150
preshared authentication
the Encryption
sha hash
Group 2
life 86400
Telnet 192.168.2.0 255.255.255.0 inside
Telnet timeout 15
SSH 192.168.2.0 255.255.255.0 inside
SSH timeout 5
SSH version 2
SSH group dh-Group1-sha1 key exchange
Console timeout 15
dhcpd auto_config inside
!
a basic threat threat detection
statistical threat detection port
Statistical threat detection Protocol
Statistics-list of access threat detection
no statistical threat detection tcp-interception
WebVPN
username admin privilege 15 xxxxx encrypted password
attributes of user admin name
VPN-group-policy DfltGrpPolicy
type tunnel-group CTSGRA remote access
attributes global-tunnel-group CTSGRA
address RAVPN pool
IPSec-attributes tunnel-group CTSGRA
IKEv1 pre-shared-key *.
!
class-map inspection_default
match default-inspection-traffic
!
!
Policy-map global_policy
class inspection_default
inspect the icmp
!
global service-policy global_policy
context of prompt hostname
no remote anonymous reporting call
Cryptochecksum:0140431e7642742a856e91246356e6a2
: end
Thanks for your help
Ok
So, basically, you set up the router so that you can directly connect to the ASA using the Cisco VPN Client. And also, the goal was ultimately only allow traffic to the LAN through the VPN Client ONLY connection.
It seems to me to realize that you have only the following configurations of NAT
VPN Client NAT0 / free of NAT / identity NAT
the object of the LAN network
Subnet 192.168.2.0 255.255.255.0
network of the VPN-POOL object
subnet 10.1.1.128 255.255.255.128
NAT static destination LAN LAN (indoor, outdoor) static source VPN-VPN-POOL
The NAT configuration above is simply to tell the ASA who don't do any type of NAT when there is traffic between the network 192.168.2.0/24 LAN and VPN 10.1.1.128/25 pool. That way if you have additional hosts on the local network that needs to be connected to, you won't have to do any form of changes to the NAT configurations for customer VPN users. You simply to allow connections in the ACL list (explained further below)
Failure to PAT
object-group network by DEFAULT-PAT-SOURCE
object-network 192.168.2.0 255.255.255.0
NAT automatic interface after (indoor, outdoor) dynamic source by DEFAULT-PAT-SOURCE
This configuration is intended just to replace the previous rule of PAT dynamic on the SAA. I guess that your router will do the translation of the ASA "outside" IP address of the interface to the public IP address of routers and this configuration should allow normal use of the Internet from the local network.
I suggest you remove all other NAT configurations, before adding these.
Control of the VPN clients access to internal resources
Also, I assume that your current VPN client is configured as full Tunnel. In other words, it will tunnel all traffic to the VPN connection, so that its assets?
To control traffic from the VPN Client users, I would suggest that you do the following
- Set up "no sysopt permit vpn connection"
- This will change the ASA operation so that connections through a VPN connection NOT allowed by default in order to bypass the ACL 'outside' interface. So, after this change, you can allow connections you need in the 'outer' interface ACL.
- Configure rules you need for connections from VPN clients to the "external" ACL interface. Although I guess they already exist as you connect there without the VPN also
I can't say this with 100% certainty, but it seems to me that the things above, you should get to the point where you can access internal resources ONLY after when you have connected to the ASA via the connection of the VPN client. Naturally take precautions like backups of configuration if you want to major configuration changes. If you manage remotely the ASA then you also also have the ability to configure a timer on the SAA, whereupon it recharges automatically. This could help in situations where a missconfiguration breaks you management connection and you don't have another way to connect remotely. Then the ASA would simply restart after that timer missed and also restart with the original configuration (as long as you did not record anything between the two)
Why you use a different port for the other devices RDP connection? I can understand it if its use through the Internet, but if the RDP connection would be used by the VPN Client only so I don't think that it is not necessary to manipulate the default port 3389 on the server or on the SAA.
Also of course if there is something on the side of real server preventing these connections then these configuration changes may not help at all.
Let me know if I understood something wrong
-Jouni
- Set up "no sysopt permit vpn connection"
-
Unable to access the remote VPN LAN
My VPN ends very well, but cannot access the local network. The warning is the LAN is a public good 24 subnet. I'm not sure how to NAT the LAN to access the VPN subnet and not to disturb any other functionality. I have attached the configuration.
Thank you in advance.
ciscoasa # sh run
: Saved
:
ASA Version 8.2 (2)
!
ciscoasa hostname
activate the encrypted Anuj/1RTcTy/SmZO password
2KFQnbNIdI.2KYOU encrypted passwd
names of
!
interface Vlan1
nameif inside
security-level 100
IP address .149.200 255.255.255.0
!
interface Vlan2
nameif outside
security-level 0
IP address *.165.37.131 255.255.255.248
!
interface Vlan5
No nameif
security-level 50
IP 10.10.10.1 255.255.255.0
!
interface Ethernet0/0
switchport access vlan 2
!
interface Ethernet0/1
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
switchport access vlan 5
!
interface Ethernet0/6
!
interface Ethernet0/7
!
passive FTP mode
clock timezone GMT 0
standard permit access list MASTERPWRTRANS_splitTunnelAcl *. . 149.0 255.255.255.0
allow inside_nat0_outbound to access extensive ip list *. . 149.0 255.255.255.0 172.30.110.0 255.255.255.224
pager lines 24
Enable logging
asdm of logging of information
Within 1500 MTU
Outside 1500 MTU
local pool POOL1 172.30.110.1 - 172.30.110.30 IP 255.255.255.224 mask
ICMP unreachable rate-limit 1 burst-size 1
don't allow no asdm history
ARP timeout 14400
Global 1 interface (outside)
Global (outside) 2 *.165.37.132
NAT (inside) 0-list of access inside_nat0_outbound
NAT (inside) 2 *. .149.199 255.255.255.255
NAT (inside) 1 0.0.0.0 0.0.0.0
static (exterior, Interior) *. .149.199 *.165.37.132 netmask 255.255.255.255
Route outside 0.0.0.0 0.0.0.0 * 1.165.37.134
Timeout xlate 03:00
Timeout conn 01:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
Sunrpc timeout 0:10:00 h323 0:05:00 h225 mgcp from 01:00 0:05:00 mgcp-pat 0:05:00
Sip timeout 0:30:00 sip_media 0:02:00 prompt Protocol sip-0: 03:00 sip - disconnect 0:02:00
Timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
dynamic-access-policy-registration DfltAccessPolicy
RADIUS protocol Server AAA MPT
AAA server MPT (inside) host .149.210
Timeout 5
key *.
AAA authentication enable LOCAL console
the ssh LOCAL console AAA authentication
Enable http server
http 0.0.0.0 0.0.0.0 inside
http 0.0.0.0 0.0.0.0 outdoors
No snmp server location
No snmp Server contact
Server enable SNMP traps snmp authentication linkup, linkdown cold start
Crypto ipsec transform-set esp-SHA-ESP-3DES-3des esp-sha-hmac
Crypto ipsec transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
Crypto ipsec transform-set ESP-DES-SHA esp - esp-sha-hmac
Crypto ipsec transform-set ESP-DES-MD5 esp - esp-md5-hmac
Crypto ipsec transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
Crypto ipsec transform-set ESP-3DES-MD5-esp-3des esp-md5-hmac
Crypto ipsec transform-set ESP-AES-256-SHA 256 - aes - esp esp-sha-hmac
Crypto ipsec transform-set ESP-AES-128-SHA aes - esp esp-sha-hmac
Crypto ipsec transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
Crypto ipsec transform-set ESP-AES-128-MD5-esp - aes esp-md5-hmac
life crypto ipsec security association seconds 28800
Crypto ipsec kilobytes of life - safety 4608000 association
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 pfs Group1 set
Crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 value transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA MD5-ESP-3DES ESP-DES-SHA ESP-DES-MD5
outside_map card crypto 65535-isakmp dynamic ipsec SYSTEM_DEFAULT_CRYPTO_MAP
outside_map interface card crypto outside
crypto ISAKMP allow outside
crypto ISAKMP policy 10
preshared authentication
3des encryption
md5 hash
Group 2
life 86400
Telnet *. . 149.0 255.255.255.0 inside
Telnet timeout 5
SSH 0.0.0.0 0.0.0.0 outdoors
SSH timeout 5
Console timeout 0
management-access insidea basic threat threat detection
Statistics-list of access threat detection
no statistical threat detection tcp-interception
WebVPN
internal MASTERPWRTRANS group policy
MASTERPWRTRANS group policy attributes
value of DNS server *. . 149.10 *. . 149.11
Protocol-tunnel-VPN IPSec
Split-tunnel-policy tunnelspecified
value of Split-tunnel-network-list MASTERPWRTRANS_splitTunnelAcl
MCI.local value by default-field
ptiadmin encrypted BtOLil2gR0VaUjfX privilege 15 password username
mptadmin U2T.1fmOIe772zE username password / encrypted
type tunnel-group MASTERPWRTRANS remote access
attributes global-tunnel-group MASTERPWRTRANS
POOL1 address pool
TPM authentication server group
Group Policy - by default-MASTERPWRTRANS
IPSec-attributes tunnel-group MASTERPWRTRANS
pre-shared key *.
!
class-map inspection_default
match default-inspection-traffic
!
!
type of policy-card inspect dns preset_dns_map
parameters
maximum message length automatic of customer
message-length maximum 512
Policy-map global_policy
class inspection_default
inspect the preset_dns_map dns
inspect the ftp
inspect h323 h225
inspect the h323 ras
inspect the rsh
inspect the rtsp
inspect esmtp
inspect sqlnet
inspect the skinny
inspect sunrpc
inspect xdmcp
inspect the sip
inspect the netbios
inspect the tftp
Review the ip options
!
global service-policy global_policy
context of prompt hostname
Cryptochecksum:820529ed70de923a8375694004b2544c
: end
ciscoasa #.The 2821 should have a route pointing to the ASA for the VPN address pool (because the ASA is not the default gateway for the LAN).
That should do it.
Federico.
-
How to access the remote wifi router
Hello
I have a camera app on my phone where I can log in and check my home monitoring cameras. However, sometimes my homenetwork resets the ip address and if I'm not at home to check my new ip address, I don't know what is the new ip address to use and connect to check my cameras in the phone application.
Sometimes, I travel and I try to check the cameras and connection failed because the IP at home has changed.
I found this article, but I'm still waiting for e-mail by netgera! :
In addition, in the article, step 3:
- Click the router settings , and then select remote access to connect as.
HE IS No. TEL THING AS ACCESS to connect remotely.
Is there another way?
Help, please
P.S. I have a router WNDR4300-N750.
In the meantime what happens if Netgear is more professionally and send me the * beep * e mail for verification?
-
How to access messages remotely or via web?
How can I access e-mail remotely or via web. All I know is that you can't do through iCloud. (With the help of Macbook 10.11). Thank you.
You can if you use email to iCloud. If you do not, then you will need to access it from the web site of your email provider, for example, Google, Comcast.
-
front panel remote - cRIO-9012
Hello
I have trouble getting the remote façade work. When I try to view the page in my browser, I get the message "Required VI is not loaded in memory on the server computer." I tried following the steps in the following two links, but I still receive the message.
http://digital.NI.com/public.nsf/allkb/7FEE6BCFD264175C8625723E000D928E http://forums.NI.com/NI/board/message?board.ID=170&message.ID=275186&requireLogin=false
I wonder if something is set up correctly in my project tree. I posted a picture (counter_test_v7.vi, is what I'm trying to see the control panel). Any other ideas?
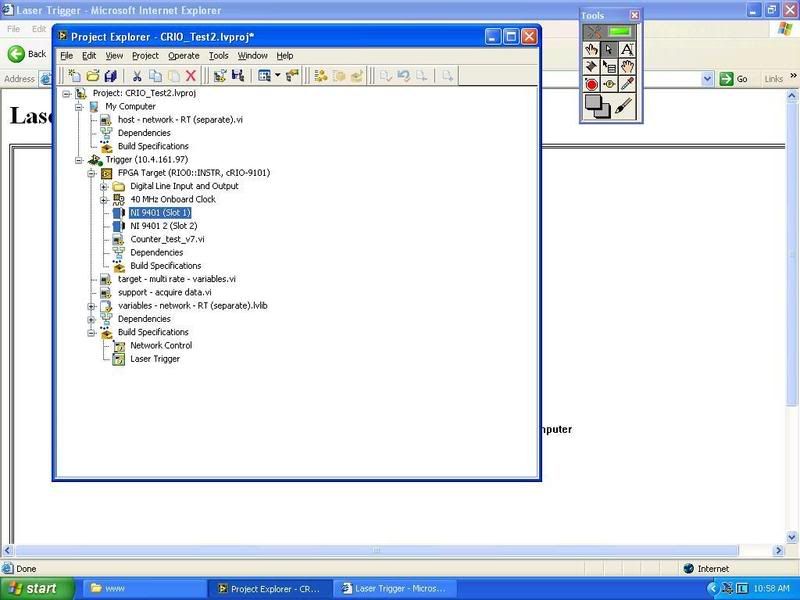
Thank you!
-Brian
Brian,
What you see is a correct behavior. What you need to do is to get your e/s of your FPGA to your RT of one of the two methods (as I see you are using LabVIEW 8.5.1 or more). The first method is to use a control node of read/write on your VI RT to access controls and indicators on your FPGA VI. The second method is to use a FIFO of DMA for your FPGA VI write its data to the FIFO and have your RT VI read from the FIFO. These are the methods you need to use to accomplish the task you're wanting.
I would recommend a training Module FPGA base available here: http://zone.ni.com/devzone/cda/tut/p/id/3555#toc5 specific lesson 6.
-
Create odbc connection between local access and remote access or sql remote
I need to connect to a remote access or sql database using my local in access 2007 version. I can't understand what I put in each of the available boxes. I see only a SQL driver to the system section of the odbc Wizard. If I decide that he wants to know where the sql server is... well, it's not local, I have a web address for this and may not know how to get the systΦme can recognize the information remotely. Help, please!
Means of access:
http://answers.Microsoft.com/en-us/Office/default.aspx
Office at the above link forums
http://social.answers.Microsoft.com/forums/en-us/addbuz
Access support at the link above.
They will help you with your questions of access when repost you in the Office Forums above.
See you soon.
Mick Murphy - Microsoft partner
Maybe you are looking for
-
How can I get mail from folder xy.default wrong data?
I've used TB for several years with a pop3 account. Now I have installed WIN 10 completely new and therefore also the TB. As I made a mistake in the use of TB over the years, I recognized all the time, I can not restore my secure e-mail and contacts.
-
El Capitan Iphone and Macbook Messages sync
After the last update of Mac OS X my iphone no longer synchronize messages with my macbook? I can send messages at once, but the stories are completely different, as used to synchronize messages for both devices. I left the game at a time and icloud
-
I came here today with a simple job in mind - to update my HP products in my profile. I found my profile but could not see a link change. I searched, and because I was not clear enough I had zillions of results mainly on the modification of a Windows
-
Want the software to change the serial number of the hard drive.
Original title: I need hdd seriyal number cheng. I have a hard drive and I penny chenge seriyal number del or you don?
-
Windows Vista Service Pack 2: Compatible blue screens
Hello. I tried to debug my friends computer. He had regular blue screens of death. I analyzed the dump files and it turned out that he had bad memory in the first 2 crashes (it linked several times windows memory diagnostic tool and even swap ram slo