AnyConnect-Parent encryption NO
Hi community support.
When you view the VPN sessions in ASDM, encryption AnyConnect-Parent shows that 'none' should not say RC4 or AES, something like that? is a part of the traffic unencrypted? It is comfort to check that the SSL Tunnel shows like RC4 just trying to have a better understanding of this, if you guys could point me to a few articles explaining these behaviors that would be great. Thank you for your comments.

Delmiro
Hi Delmiro,
Here is the basic understanding of the tunnels that are created when we connect to the ssl.
Depends on the mecahnism which is no longer used, you can use the weblaunch or the stand-alone client
Depending on the connection, you will create three different tunnels (sessions) on the SAA, each with a specific purpose:
Without client or Parent Tunnel: It is the main session that is created during the negotiation to install the session cookie that is needed in case a reconnection is necessary due to hibernation or network connectivity issues, etc. According to the mechanism of connection, the ASA will list the session as a Clientless (Weblaunch Portal) or Parent (Standalone AnyConnect).
Note: the AnyConnect-Parent represents the session when the client is not actively connected. It does not represent an encrypted tunnel. It's actually a database on the SAA entry. So if the customer closes to the bottom/beds, tunnels (IPsec, IKE, TLS, DTLS) are torn down, but the Parent remains until the idle timer or time of max connection comes into play. It allows the user to reconnect without repeating the authentication.
-Tunnel SSL: The SSL connection is first established, and data are transmitted through this connection when trying to establish a connection DTLS. Once the DTLS connection has been established, the client start to send packets through the DTLS connection instead of the SSL connection. Control packets, on the other hand, always go to the SSL connection.
DTLS-Tunnel: When the DTLS Tunnel is fully established, all data is now moving towards the DTLS-tunnel and the SSL tunnel is used only for the occasional control channel traffic. If something happened to UDP, DTLS-Tunnel will be demolished and all data will again cross the SSL Tunnel.
I hope this helps.
Concerning
Regnier
Tags: Cisco Security
Similar Questions
-
CERT ID on ASA change with impact session AnyConnect?
Hello all - I should probably know this answer, however, I'm not 100%.
If I change the cert ID (trust point) of the external interface to use a "most recent" certificate, although there are client AnyConnect connected, the session will end?
I believe that the answer is Yes, since the keys will change.
Any help is appreciated!
Thank you!
Hello
He not disconnect users, because the main purpose of the use of cert in the first place other than identity is to distribute safe symmetric session key. Once this is done, the work of cert is done.
I did a quick test on my end.
I have connected a customer to the ASA using certificates. Here are the results:
ASA-32-25 # sh run all the ssl
SSL server-version everything
client SSL version all
SSL encryption, 3des-sha1-aes128-sha1 aes256-sha1 md5 - rc4-rc4-sha1
Trust SSL SSL outdoors<-- this="" is="" the="" certificate="" applied="" on="" outside="">
SSL certificate authentication CAF-timeout 2Now, I have connected my client and he got connected successfully:
ASA-32-25 (config) # poster not vpn - its
Session type: AnyConnect
Username: anyconnect Index: 50
Public IP address 192.168.10.2 assigned IP:: x.x.x.x
Protocol: AnyConnect-Parent-Tunnel SSL
License: AnyConnect Premium
Encryption: AnyConnect-Parent: (1) no SSL Tunnel: 3DES (1)
Hash: AnyConnect-Parent: (1) no SSL Tunnel: SHA1 (1)
TX Bytes: 11488 bytes Rx: 1351
Group Policy: Group GroupPolicy_Test Tunnel: Test
Connect time: 12:24:15 EDT Thursday, April 17, 2014
Time: 0 h: 00 m: 04 s
Inactivity: 0 h: 00 m: 00s
Result of the NAC: unknown
Map VLANS: VLAN n/a: noI removed then, the certificate for the external interface.
ASA-32-25 (config) # points trust without ssl SSL outdoors
And when I checked the status of the connected client, I saw that he was still logged:
ASA-32-25 (config) # poster not vpn - its
Session type: AnyConnect
Username: anyconnect Index: 50
Public IP address 192.168.10.2 assigned IP:: x.x.x.x
Protocol: AnyConnect-Parent-Tunnel SSL
License: AnyConnect Premium
Encryption: AnyConnect-Parent: (1) no SSL Tunnel: 3DES (1)
Hash: AnyConnect-Parent: (1) no SSL Tunnel: SHA1 (1)
TX Bytes: 11488 bytes Rx: 1351
Group Policy: Group GroupPolicy_Test Tunnel: Test
Connect time: 12:24:15 EDT Thursday, April 17, 2014
Time: 0 h: 00 m: 12s
Inactivity: 0 h: 00 m: 00s
Result of the NAC: unknown
Map VLANS: VLAN n/a: noThe conclusion therefore, is that users will not be cut if you change the certificate on the external interface.
Hope that answers your question.
Vishnu
-
Impossible to ping anyconnect Client IP de ASA
Hello world
I can't connect to cisco anyconenct fine no problem.
When connected I ping the SAA in interface and other subnets that are behind the ASA inside the interface from the PC connected through the VPN.
My only problem is that of ASA, I cannot ping IP of 10.0.0.5.
ASA1 # sh anyconnect vpn-sessiondb
Session type: AnyConnect
User name: anyconnect_user index: 54
Assigned IP: 10.0.0.5 Public IP address: 192.168.98.2
Protocol: AnyConnect-Parent-Tunnel SSL DTLS-Tunnel
License: AnyConnect Essentials
Encryption: AnyConnect-Parent: (1) no SSL Tunnel: (1) AES128 DTLS-Tunnel: (1) AES128
Hash: AnyConnect-Parent: (1) no SSL Tunnel: (1) SHA1 DTLS-Tunnel: SHA1 (1)
TX Bytes: 12318 bytes Rx: 73502
Group Policy: anyconnect_group
Tunnel of Group: anyconnect_connection_profile
Connect time: 23:21:28 MST Friday, March 7, 2014
Duration: 0 h: 34 m: 33 s
Inactivity: 0 h: 00 m: 00s
Result of the NAC: unknown
Map VLANS: VLAN n/a: noI ping the switch connected to ASA inside interface
ASA1 # ping 10.0.0.2
Type to abort escape sequence.
Send 5, echoes ICMP 100 bytes to 10.0.0.2, time-out is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = ms 04/01/10
I can ping from the ASA inside interface
ASA1 # ping 10.0.0.1 - ASA inside interface
Type to abort escape sequence.
Send 5, echoes ICMP 100 bytes to 10.0.0.1, time-out is 2 seconds:
!!!!!
Success rate is 100 per cent (5/5), round-trip min/avg/max = 1/1/1 ms
ASA1 # ping 10.0.0.5
Type to abort escape sequence.
Send 5, echoes ICMP 100 bytes to 10.0.0.5, time-out is 2 seconds:
?????
Success rate is 0% (0/5)
ASA1 #.
Journal of the shows
March 7, 2014 23:00:52: % ASA-6-302020: built outgoing ICMP connection for 10.0.0.5/0(LOCAL\anyconnect_user faddr) gaddr laddr 192.168.1.171/1168 192.168.1.171/1168
March 7, 2014 23:01:02: % ASA-6-302021: connection of disassembly ICMP for faddr 10.0.0.5/0(LOCAL\anyconnect_user) gaddr laddr 192.168.1.171/1168 192.168.1.171/1168
Where IP 192.168.1.171 is ASA outside interface
Concerning
MAhesh
Hello Manu,
Have you tried to ping the network interior? Or the package from inside the source interface of the ASA? Remember, you should have some rules exemption nat for packets going through the VPN connection. That's how specify us which networks are allowed to join the VPN clients. If you ping without specify any interface the packet is going to come from the external interface, and probably this interface/subnet is not allowed through the VPN connection. Using split tunnel or tunnelall?
You can try to activate the management of access to the inside interface and the ping from the inside. These packages should hit the exemption nat rule and will be sent through the tunnel instead of the Internet.
These are the necessary commands:
To specify an interface as an interface of management only, enter the following command:
hostname(config)# management access inside
Then, you could do an inside 10.0.0.5 ping to ping the ASA AnyConnect client.
Notes on the access management command:
If your VPN tunnel ends on an interface, but you want to manage the ASA by accessing a different interface, you can identify this interface as an interface for management access. For example, if you enter the ASA of the external interface, this feature allows you to connect inside the interface by using ASDM, SSH, Telnet or SNMP. or you can test inside the interface at the entrance to the external interface. Management is accessible by the following VPN tunnels types: client IPsec, the client AnyConnect SSL VPN and IPsec LAN-to-LAN.
Hope this helps,
Luis
-
ASA AnyConnect client is unable to obtain the IP address of the remote DHCP server
I and ASA with 10 client AnyConnect profiles set up to get their IP address of my Windows DHCP server.
It was working fine yesterday.
I saved the config and rebooted the device.
Now it won't deliver to my vpn clients intellectual property.
I don't understand what is happening.
If I change the profiles to use a local pool he assigns an IP address and works very well.
But I can't use the local pools. I have to use the DHCP server on the local network.
The ONLY thing that was made was that a license allowing the AnyConnect Essentials has been installed recently.
I get this in debugging:
6 August 30, 2011 10:44:39 DAP: test49, Addr 107.44.142.20 user, connection AnyConnect: following DAP records were selected for this connection: DfltAccessPolicy
6 August 30, 2011 10:44:39 group user IP <107.44.142.20>AnyConnect parent session began.
7 August 30, 2011 10:44:39 IPAA: received message 'UTL_IP_ [IKE_] ADDR_REQ.
6 August 30, 2011 10:44:39 IPAA: attempt to query DHCP 1 successful
6 August 30, 2011 10:44:39 IPAA: DHCP configured, the request succeeded for tunnel-group "MCSO-mobile."
6 August 30, 2011 10:44:39 172.18.4.7 67 172.18.1.46 67 Built UDP outgoing connection 30957 for Internal:172.18.1.46/67 (172.18.1.46/67) at identity:172.18.4.7/67 (172.18.4.7/67)
7 August 30, 2011 10:44:39 192.168.6.1 built ISP1:192.168.6.1 local-home
6 August 30, 2011 10:44:39 172.18.1.46 1 192.168.6.1 0 built outgoing ICMP connection for faddr gaddr laddr 172.18.1.46/1 172.18.1.46/1 192.168.6.1/0
6 August 30, 2011 10:44:41 172.18.1.46 67 192.168.6.0 67 Built UDP outgoing connection 30960 for ISP1:192.168.6.0/67 (192.168.6.0/67) at Internal:172.18.1.46/67 (172.18.1.46/67)
6 August 30, 2011 10:44:42 192.168.6.1 0 172.18.1.46 1 connection disassembly ICMP for faddr gaddr laddr 172.18.1.46/1 172.18.1.46/1 192.168.6.1/0
7 August 30, 2011 10:44:52 IPAA: message received 'UTL_IP_DHCP_INVALID_ADDR '.
4 August 30, 2011 10:44:52 IPAA: could not get the address of the local strategy group or tunnel-group pools
Well, your config looks good. You also upgrade the operating system? Maybe you hit a new bug.
I heard no problems after the installation of a license, but it might be interesting to open a TAC case and learn if you hit a bug.
-
Cisco ASA VPN session reflect a public IP of different source
Hi all
I tested and managed to successfully establish the vpn on my cisco asa 5520.
On my syslog, I can see "parent anyconnect session has begun" during my setting up vpn and "webvpn session is over" at the end of my vpn session
where public ip used to establish the vpn address is reflected. However after the line "webvpn session is over", I can see other lines in my syslog example "group = vpngroup, username = test, ip = x.x.x.x, disconnected session, session type: anyconnect parent, duration 0 h: 00m23s, xmt bytes: 0, rcv:0 bytes, reason: requested user" where x.x.x.x is not the ip address used to establish my vpn for remote access, it is not related to my vpn ip address below. I am very sure that the x.x.x.x ip failed any vpn for my cisco asa5520. So why it is reflected in my logs to asa cisco? Pls advise, TIA!
Hello
Think I remember some display on a similar question in the past. Did some research on google and the next BugID was mentioned in the discussion.
113019 syslog reports an invalid address when the VPN client disconnects. -
Tunnel of splitting, essentials, and vpn-sessiondb
Hello
I'm looking to clarify a few things related to anyconnect vpn. Here is my setup, I have a portal page custom that users log in which authenticates with RADIUS. Anyconnect then automatically downloads to the client. Apart from that I use all the features of the portal (clientless SSL was previously used, but not more). I am preparing a device that will serve as a cold spare and because I no longer need without client I prefer to put everything just licensed Essentials on this, I'll try to find confirmation on a number of things and have not found anything definitive. Here are the questions:
1. I can tunnel of splitting with essentials license? The documentation all said "complete tunnel" is the same as the tunnel of all?
2. in the execution of a "show vpn-sessiondb svc" the session is shown as a SSL without client, it is ASA 8.2, I lab tested to confirm the default group policy is configured to only allows svc webvpn not as Protocol "vpn-tunnel-Protocol svc", which is the policy applied to the session. Is this some sort of error 8.2 display?
3. because I only use the portal for authentication and then page by downloading the client anyconnect this should always work with most of what I read, correct?
Thanks for taking a peek.
1. you can probably split tunnel. "full-tunnel" here means "not without customer", everything works exactly as with ordinary vpn cisco client.
2 al ' 8.4 it shows this:
Protocol: AnyConnect-Parent-Tunnel SSL
3. it will work for authentication and the client download, but nothing more.
-
Where a session anyconnection on an ASA does not have its encryption method of? Looks like the default is 3DES, but I can't find where in the config, the encryption method is applied. The game of transformation that I use for IPSec is not be applied to the anyconnect customer.
Thank you
Bill
Hello
Setup > remote access VPN > advanced > settings SSL
"The ASA uses Protocol Secure Sockets Layer (SSL) and its successor, TLS (Transport Layer) security to support transmission messages secure ASDM, Clientless VPN and browser-based sessions. The SSL settings window allows you to configure the version SSL and algorithms of encryption for clients and servers. It also allows you to apply previously configured trustpoints specific interfaces and configure a backup trustpoint for interfaces which do not have an associated trustpoint. »
Source: Online help ASDM.
Best regards
Paul
-
AnyConnect 2.5 on XP installation fails
Anyone who has trouble with Anyconnect 2.5 install on Windows XP? Once it breaks down, can I have the user click on the link of manual installation and works perfectly. However, the automatic installation fails. Users have administrator rights. 2.5 also installs on Vista and Windows 7 without any problem. I get the following error on attempted installations of XP...
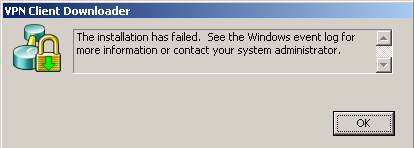
In the case log, I get a large number of events similar to this...
/ * Style definitions * / table. MsoNormalTable {mso-style-name : « Table Normal » ; mso-tstyle-rowband-taille : 0 ; mso-tstyle-colband-taille : 0 ; mso-style-noshow:yes ; mso-style-priorité : 99 ; mso-style-qformat:yes ; mso-style-parent : » « ;" mso-rembourrage-alt : 0 à 5.4pt 0 à 5.4pt ; mso-para-margin : 0 ; mso-para-marge-bottom : .0001pt ; mso-pagination : widow-orphelin ; police-taille : 11.0pt ; famille de police : « Calibri », « sans-serif » ; mso-ascii-font-family : Calibri ; mso-ascii-theme-font : minor-latin ; mso-fareast-font-family : « Times New Roman » ; mso-fareast-theme-font : minor-fareast ; mso-hansi-font-family : Calibri ; mso-hansi-theme-font : minor-latin ; mso-bidi-font-family : « Times New Roman » ; mso-bidi-theme-font : minor-bidi ;}
Event type: error
Event source: vpndownloader
Event category: (1).
Event ID: 2
Date: 29/07/2010
Time: 09:07:11
User: n/a
Computer: LVAK349
Description:
The description for the event (2) in Source (vpndownloader) ID is not found. The local computer may not have the information necessary registry or message DLL files to display messages from a remote computer. You may be able to use the option/auxsource = flag to retrieve this description; For more information, see Help and Support. The following information is part of the event: function: CManifestMgr::ProcessManifests
File:.\ManifestMgr.cpp
Online: 658
Called the function: GetManifest
Return code: 0 (0x00000000)
Description: Could not get the main manifest
.Can you please verify what are you allowing ssl encryption as below.
SSL cipher aes128-sha1-3des-sha1
Concerning
BR
-
How can I encrypt a drive where cs diskutil convert reports 'a problem', let the unreadable disk?
I try to encrypt my Time Machine backup volume, but diskutil refuses and leaves the disc unreadable (but fixable using Linux). How can I proceed?
It is a disc of TB USB3 Western Digital Elements 107 3.
It has one HFS partition + and works very well.
diskutil verifyDisk and diskutil verifyVolume don't report any problems. I also used Alsoft DiskWarrior to repair inconsistencies, without problems.
If I try to convert the volume, diskutil report 'a problem', like this:
rb@Silverbird$ /usr/sbin/diskutil cs convert /Volumes/RB3TB1/ Started CoreStorage operation on disk4s2 RB3TB1 Resizing disk to fit Core Storage headers Creating Core Storage Logical Volume Group Attempting to unmount disk4s2 Switching disk4s2 to Core Storage Waiting for Logical Volume to appear Mounting Logical Volume A problem occurred; undoing all changes Switching partition from Core Storage type to original type Undoing creation of Logical Volume Group Reclaiming space formerly used by Core Storage metadata Error: -69842: Couldn't mount disk
This leaves the unreadable disk. diskutil cs list shows the drive as a basic storage volume that is "online" and "reversible" but it may not be mounted or acted on, nor can the physical volume of the parent. Disk utility crashes at startup when the drive is connected. diskutil repairDisk on volume of parent reports:
Repairing the partition map might erase disk4s1, proceed? (y/N) y Started partition map repair on disk4 Checking prerequisites Problems were encountered during repair of the partition map Error: -69808: Some information was unavailable during an internal lookup
In fact, all access to the disc seems to be broken at this point.
rb@Silverbird$ sudo /usr/sbin/gpt show /dev/disk4 gpt show: unable to open device '/dev/disk4': Input/output error
You cannot read the device using hexdump. The kernel seems mightily confused.
I was able to recover the disc mounting Linux using the utility 'gdisk' to change the partition type to AF02 (storage of carrots) to AF00 (HFS +). After that, diskutil checks the disk so the volume as OK.
I think that Apple has a bug where diskutil fails to return the partition type.
But this me no bugs more closely to encrypt my backup volume.
Anyone have any idea what might be the 'problem' and how do I proceed?
rb@Silverbird$ /usr/sbin/diskutil info /Volumes/RB3TB1 Device Identifier: disk5s2 Device Node: /dev/disk5s2 Whole: No Part of Whole: disk5 Device / Media Name: RB3TB1 Volume Name: RB3TB1 Mounted: Yes Mount Point: /Volumes/RB3TB1 File System Personality: Journaled HFS+ Type (Bundle): hfs Name (User Visible): Mac OS Extended (Journaled) Journal: Journal size 229376 KB at offset 0x8f07408000 Owners: Enabled Partition Type: Apple_HFS OS Can Be Installed: Yes Media Type: Generic Protocol: USB SMART Status: Not Supported Volume UUID: F096E831-F27D-3433-9BBE-6B65F4F69FA5 Disk / Partition UUID: FE09034E-6AA0-4490-82A1-1F7E894ACD91 Total Size: 3.0 TB (3000110108672 Bytes) (exactly 5859590056 512-Byte-Units) Volume Free Space: 78.1 GB (78142939136 Bytes) (exactly 152622928 512-Byte-Units) Device Block Size: 4096 Bytes Allocation Block Size: 4096 Bytes Read-Only Media: No Read-Only Volume: No Device Location: External Removable Media: No
The disk contains files of about 732000000, according to the disk utility (in reality the directory entries).
This is OS X 10.11.2, day, based on a new install of OS X 10.11 last month.
Hello RPTB1,.
Thank you for using communities of Apple Support.
I see that you are wanting to encrypt your Time Machine backup disk. I see you are trying to do through Terminal or Unix command line, have you tried to use it through the Time Machine configuration and preferences? Take a look at this article and see how it works for you.
OS X El Capitan: choose a backup drive, then set the encryption options
Best regards.
-
Algorithms of different SSL encryption between 5525 x and x 5555?
Good afternoon
I have an ASA 5525 x and an ASA 5555 x. Both of them run 9.4 (2.6).
5525 x supports all the new encryptions that are discussed in the notes.
lab-asa5525x# sh ssl ciphersCurrent cipher configuration:default (fips): ECDHE-ECDSA-AES256-GCM-SHA384 ECDHE-RSA-AES256-GCM-SHA384 DHE-RSA-AES256-GCM-SHA384 AES256-GCM-SHA384 ECDHE-ECDSA-AES256-SHA384 ECDHE-RSA-AES256-SHA384 DHE-RSA-AES256-SHA256 AES256-SHA256 ECDHE-ECDSA-AES128-GCM-SHA256 ECDHE-RSA-AES128-GCM-SHA256 DHE-RSA-AES128-GCM-SHA256 AES128-GCM-SHA256 ECDHE-ECDSA-AES128-SHA256 ECDHE-RSA-AES128-SHA256 DHE-RSA-AES128-SHA256 AES128-SHA256 DHE-RSA-AES256-SHA AES256-SHA DHE-RSA-AES128-SHA AES128-SHAtlsv1 (fips): DHE-RSA-AES256-SHA AES256-SHA DHE-RSA-AES128-SHA AES128-SHAtlsv1.1 (fips): DHE-RSA-AES256-SHA AES256-SHA DHE-RSA-AES128-SHA AES128-SHAtlsv1.2 (custom): ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-SHA256 ECDHE-ECDSA-AES256-GCM-SHA384 ECDHE-ECDSA-AES256-SHA384 ECDHE-ECDSA-AES128-GCM-SHA256 ECDHE-ECDSA-AES128-SHA256dtlsv1 (fips): DHE-RSA-AES256-SHA AES256-SHA DHE-RSA-AES128-SHA AES128-SHAlab-asa5525x# lab-asa5525x# sh runn all sslssl server-version tlsv1.2ssl client-version tlsv1.2ssl cipher default fipsssl cipher tlsv1 fipsssl cipher tlsv1.1 fipsssl cipher tlsv1.2 custom "ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-SHA256"ssl cipher dtlsv1 fipsssl dh-group group24ssl ecdh-group group20ssl trust-point 2016-03.lab-asa Outsidessl certificate-authentication fca-timeout 2lab-asa5525x#
5555 x does not support encryption of elliptical curve which are discussed in the notes.ASA5555x-01# sh ssl ciphersCurrent cipher configuration:default (medium): DHE-RSA-AES256-SHA256 AES256-SHA256 DHE-RSA-AES128-SHA256 AES128-SHA256 DHE-RSA-AES256-SHA AES256-SHA DHE-RSA-AES128-SHA AES128-SHA DES-CBC3-SHAtlsv1 (medium): DHE-RSA-AES256-SHA AES256-SHA DHE-RSA-AES128-SHA AES128-SHA DES-CBC3-SHAtlsv1.1 (medium): DHE-RSA-AES256-SHA AES256-SHA DHE-RSA-AES128-SHA AES128-SHA DES-CBC3-SHAtlsv1.2 (medium): DHE-RSA-AES256-SHA256 AES256-SHA256 DHE-RSA-AES128-SHA256 AES128-SHA256 DHE-RSA-AES256-SHA AES256-SHA DHE-RSA-AES128-SHA AES128-SHA DES-CBC3-SHAdtlsv1 (medium): DHE-RSA-AES256-SHA AES256-SHA DHE-RSA-AES128-SHA AES128-SHA DES-CBC3-SHAASA5555x-01# ASA5555x-01# sh runn all sslssl server-version tlsv1.2ssl client-version tlsv1.2ssl cipher default mediumssl cipher tlsv1 mediumssl cipher tlsv1.1 mediumssl cipher tlsv1.2 mediumssl cipher dtlsv1 mediumssl dh-group group2ssl ecdh-group group19ssl trust-point 2016-03.ssl-vpn Outside_85ssl certificate-authentication fca-timeout 2ASA5555x-01#
I opened a case of TAC and 5585 9.4 (2.6) also running of the TAC engineer does not support encryption EC? Can someone help me understand what Miss me? X - platforms ASA should support the same features, right? Thank you TimHello
Disable the Anyconnect essentials from the setting global webvpn, toured here.
CLI:
WebVPN
No anyconnect essentials
Thank you
-
ASA 5515 - Anyconnect - inside the subnet connection problem
Hi all
I have a problem with the connection to the Interior/subnet using Anyconnect SSL VPN.
ASA worm. 5515
Please find below of configuration:
User access audit
ASA1 # show running-config
: Saved
:
ASA 9.1 Version 2
!
hostname ASA1
activate 8Ry2YjIyt7RRXU24 encrypted password
volatile xlate deny tcp any4 any4
volatile xlate deny tcp any4 any6
volatile xlate deny tcp any6 any4
volatile xlate deny tcp any6 any6
volatile xlate deny udp any4 any4 eq field
volatile xlate deny udp any4 any6 eq field
volatile xlate deny udp any6 any4 eq field
volatile xlate deny udp any6 any6 eq field
2KFQnbNIdI.2KYOU encrypted passwd
names of
mask of local pool swimming POOLS-for-AnyConnect 10.0.70.1 - 10.0.70.50 IP 255.255.255.0
!
interface GigabitEthernet0/0
nameif outside
security-level 0
address IP A.A.A.A 255.255.255.240
!
interface GigabitEthernet0/1
nameif inside
security-level 100
192.168.64.1 IP address 255.255.255.0
!
interface GigabitEthernet0/2
nameif dmz
security-level 20
address IP B.B.B.B 255.255.255.0
!
interface GigabitEthernet0/3
Shutdown
No nameif
no level of security
no ip address
!
interface GigabitEthernet0/4
Shutdown
No nameif
no level of security
no ip address
!
interface GigabitEthernet0/5
Shutdown
No nameif
no level of security
no ip address
!
interface Management0/0
management only
Shutdown
No nameif
no level of security
no ip address
!
passive FTP mode
network of the OBJ_GENERIC_ALL object
subnet 0.0.0.0 0.0.0.0
network outside_to_inside_FR-Appsrv01 object
Home 192.168.64.232
network outside_to_dmz_fr-websvr-uat object
Home 10.20.20.14
network inside_to_dmz object
192.168.64.0 subnet 255.255.255.0
gtc-tomcat network object
Home 192.168.64.228
network of the USA-Appsrv01-UAT object
Home 192.168.64.223
network of the USA-Websvr-UAT object
Home 10.20.20.13
network vpn_to_inside object
10.0.70.0 subnet 255.255.255.0
extended access list acl_out permit everything all unreachable icmp
acl_out list extended access permit icmp any any echo response
acl_out list extended access permit icmp any one time exceed
acl_out list extended access permit tcp any object outside_to_inside_FR-Appsrv01 eq 3389
acl_out list extended access permit tcp any object outside_to_inside_FR-Appsrv01 eq 28080
acl_out list extended access permit tcp any object outside_to_inside_FR-Appsrv01 eq 9876
acl_out list extended access permit udp any object outside_to_inside_FR-Appsrv01 eq 1720
acl_out list extended access permit tcp any object outside_to_dmz_fr-websvr-uat eq www
acl_out list extended access permit tcp any object outside_to_dmz_fr-websvr-uat eq https
acl_out list extended access permit tcp any object outside_to_dmz_fr-websvr-uat eq 3389
acl_out list extended access permit tcp any object USA-Appsrv01-UAT eq 9876
acl_out list extended access permit udp any eq USA-Appsrv01-UAT object 1720
acl_out list extended access permit tcp any object USA-Websvr-UAT eq www
acl_out list extended access permit tcp any USA-Websvr-UAT eq https object
acl_out list extended access permit tcp any object USA-Websvr-UAT eq 3389
acl_out list extended access permit tcp any object USA-Appsrv01-UAT eq 3389
acl_dmz list extended access permit icmp any any echo response
acl_dmz of access allowed any ip an extended list
acl_dmz list extended access permitted tcp object object to outside_to_dmz_fr-websvr-uat gtc-tomcat eq 8080
acl_dmz list extended access permitted tcp object object to outside_to_dmz_fr-websvr-uat gtc-tomcat eq 8081
acl_dmz list extended access permitted tcp object object to outside_to_dmz_fr-websvr-uat gtc-tomcat eq 3389
acl_dmz list extended access permitted tcp object USA-Websvr-UAT object USA-Appsrv01-UAT eq 8080
acl_dmz list extended access permitted tcp object USA-Websvr-UAT object USA-Appsrv01-UAT eq 8081
access extensive list ip 192.168.64.0 gtcvpn2 allow 255.255.255.0 10.0.70.0 255.255.255.0
pager lines 24
Outside 1500 MTU
Within 1500 MTU
MTU 1500 dmz
no failover
ICMP unreachable rate-limit 1 burst-size 1
don't allow no asdm history
ARP timeout 14400
no permit-nonconnected arp
NAT dynamic interface of OBJ_GENERIC_ALL source (indoor, outdoor)
NAT (inside, outside) static source all all static destination vpn_to_inside vpn_to_inside
!
network outside_to_inside_FR-Appsrv01 object
NAT static x.x.x.x (indoor, outdoor)
network outside_to_dmz_fr-websvr-uat object
NAT (dmz, outside) static x.x.x.x
network of the USA-Appsrv01-UAT object
NAT static x.x.x.x (indoor, outdoor)
network of the USA-Websvr-UAT object
NAT (dmz, outside) static x.x.x.x
Access-group acl_out in interface outside
Access-group acl_dmz in dmz interface
Route outside 0.0.0.0 0.0.0.0 B.B.B.B 1
Timeout xlate 03:00
Pat-xlate timeout 0:00:30
Timeout conn 01:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
Sunrpc timeout 0:10:00 h323 0:05:00 h225 mgcp from 01:00 0:05:00 mgcp-pat 0:05:00
Sip timeout 0:30:00 sip_media 0:02:00 prompt Protocol sip-0: 03:00 sip - disconnect 0:02:00
Timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
Floating conn timeout 0:00:00
dynamic-access-policy-registration DfltAccessPolicy
identity of the user by default-domain LOCAL
Enable http server
http 192.168.64.204 255.255.255.255 inside
No snmp server location
No snmp Server contact
Server enable SNMP traps snmp authentication linkup, linkdown warmstart of cold start
Crypto ipsec pmtu aging infinite - the security association
Crypto ca trustpoint ASDM_TrustPoint0
registration auto
name of the object CN = ASA1
GTCVPN2 key pair
Configure CRL
trustpool crypto ca policy
string encryption ca ASDM_TrustPoint0 certificates
certificate of 19897d 54
308201cf 30820138 a0030201 02020419 897d 864886f7 0d 010105 5430 0d06092a
0500302c 3111300f 06035504 03130851 57455354 32343031 17301506 092a 8648
09021608 51574553 54323430 31343132 30333034 30333237 301e170d 86f70d01
5a170d32 34313133 30303430 3332375a 302 c 3111 55040313 08515745 300f0603
53543234 30311730 1506092a 864886f7 010902 16085157 45535432 34303081 0d
9f300d06 092 has 8648 86f70d01 01010500 03818d 00 30818902 818100a 2 5e873d21
dfa7cc00 ee438d1d bc400dc5 220f2dc4 aa896be4 39843044 d0521010 88 has 24454
b4b1f345 84ec0ad3 cac13d47 a71f367a 2e71f5fc 0a9bd55f 05d 75648 72bfb9e9
c5379753 26ec523d f2cbc438 d234616f a71e4f4f 42f39dde e4b99020 cfcd00ad
73162ab8 1af6b6f5 fa1b47c6 d261db8b 4a75b249 60556102 03010001 fa3fbe7c
300 d 0609 2a 864886 f70d0101 8181007a 05050003 be791b64 a9f0df8f 982d162d
b7c884c1 eb183711 05d676d7 2585486e 5cdd23b9 af774a8f 9623e91a b3d85f10
af85c009 9590c0b3 401cec03 4dccf99a f1ee8c01 1e6f0f3a 6516579c 12d9cbab
59fcead4 63baf64b 7adece49 7799f94c 1865ce1d 2c0f3ced e65fefdc a784dc50
350e8ba2 998f3820 e6370ae5 7e6c543b 6c1ced
quit smoking
Telnet 192.168.64.200 255.255.255.255 inside
Telnet 192.168.64.169 255.255.255.255 inside
Telnet 192.168.64.190 255.255.255.255 inside
Telnet 192.168.64.199 255.255.255.255 inside
Telnet timeout 5
SSH timeout 5
SSH group dh-Group1-sha1 key exchange
Console timeout 0
a basic threat threat detection
Statistics-list of access threat detection
no statistical threat detection tcp-interception
SSL-trust ASDM_TrustPoint0 inside point
SSL-trust outside ASDM_TrustPoint0 point
WebVPN
allow outside
AnyConnect image disk0:/anyconnect-win-2.5.2014-k9.pkg 1
AnyConnect enable
tunnel-group-list activate
internal GroupPolicy_GTCVPN2 group strategy
attributes of Group Policy GroupPolicy_GTCVPN2
WINS server no
value of 192.168.64.202 DNS server 192.168.64.201
client ssl-VPN-tunnel-Protocol
Split-tunnel-policy tunnelspecified
value of Split-tunnel-network-list gtcvpn2
field default value mondomaine.fr
username cHoYQ5ZzE4HJyyq password of duncan / encrypted
username Aosl50Zig4zLZm4 admin password / encrypted
password encrypted sebol U7rG3kt653p8ctAz user name
type tunnel-group GTCVPN2 remote access
attributes global-tunnel-group GTCVPN2
Swimming POOLS-for-AnyConnect address pool
Group Policy - by default-GroupPolicy_GTCVPN2
tunnel-group GTCVPN2 webvpn-attributes
enable GTCVPN2 group-alias
!
class-map inspection_default
match default-inspection-traffic
!
!
type of policy-card inspect dns preset_dns_map
parameters
maximum message length automatic of customer
message-length maximum 512
Policy-map global_policy
class inspection_default
inspect the preset_dns_map dns
inspect the ftp
inspect h323 h225
inspect the h323 ras
Review the ip options
inspect the netbios
inspect the rsh
inspect the rtsp
inspect the skinny
inspect esmtp
inspect sqlnet
inspect sunrpc
inspect the tftp
inspect the sip
inspect xdmcp
!
global service-policy global_policy
context of prompt hostname
no remote anonymous reporting call
call-home
Profile of CiscoTAC-1
no active account
http https://tools.cisco.com/its/service/oddce/services/DDCEService destination address
email address of destination [email protected] / * /
destination-mode http transport
Subscribe to alert-group diagnosis
Subscribe to alert-group environment
Subscribe to alert-group monthly periodic inventory 19
Subscribe to alert-group configuration periodic monthly 19
daily periodic subscribe to alert-group telemetry
Cryptochecksum:0b972b3b751b59085bc2bbbb6b0c2281
: end
ASA1 #.I can connect to the ASA from outside with the Anyconnect client, split tunneling works well unfortunately I can't ping anything inside the network, VPN subnet: 255.255.255.0, inside the 192.168.64.x 255.255.255.0 subnet 10.0.70.x
When connecting from the outside, cisco anyconnect is showing 192.168.64.0/24 in the tab "details of the trip.
Do you know if I'm missing something? (internal subnet to subnet route vpn?)
Thank you
Use your internal subnet ASA as its default gateway? If this isn't the case, it will take a route pointing to the ASA inside the interface.
You can perform a packet - trace as:
Packet-trace entry inside tcp 192.168.64.2 80 10.0.70.1 1025
(simulation of traffic back from a web server inside a VPN client)
-
Cisco Anyconnect to mobile license?
Dear all:
Currently, we will activate cisco anyconnect for mobile (IPAD), our license is currently:
Material: ASA5510, 1024 MB RAM, Pentium 4 Celeron 1599 MHz processor
Internal ATA Compact Flash, 256 MBHardware encryption device: edge Cisco ASA - 55 x 0 Accelerator (revision 0 x 0)
The devices allowed for this platform:
The maximum physical Interfaces: unlimited
VLAN maximum: 100
Internal hosts: unlimited
Failover: Active/active
VPN - A: enabled
VPN-3DES-AES: enabled
Security contexts: 2
GTP/GPRS: disabled
VPN SSL counterparts: 10
The VPN peers total: 250
Sharing license: disabled
AnyConnect for Mobile: disabled
AnyConnect Cisco VPN phone: disabled
AnyConnect Essentials: disabled
Assessment of Advanced endpoint: disabled
Proxy sessions for the UC phone: 2
Total number of Sessions of Proxy UC: 2
Botnet traffic filter: disabledThis platform includes an ASA 5510 Security Plus license.
as I read, so cisco anyconnect for mobile (IPAD), I need two licenses:
AnyConnect Essentials and AnyConnect for Mobile, is that correct?
If I want to activate this just for 10 users, I can do this? What are the available license I have to select by the user issues a year (or over a year?)
can my final question get these licenses from Amazon, since google shows as these offers.
Please help thanks
I would go for the license more. It is much cheaper then the VPN-only-license and you can continue to use it when you change the ASA in a newer model.
-
AnyConnect client cannot ping gateway
I'm currently implementing anyconnect for some users in our Organization. Once the clients connect to the VPN via. AnyConnect, they cannot access anything whatsoever, including their default gateway (via ping). I'm not sure what I did wrong, but it's a quick fix, a person can report to me. It's a little frustrating because I had this lab work, but can not see the obvious errors.
Pool VPN: 192.168.200.0/24
inside the ASA interface 192.168.2.1
Grateful for any help received.
Greg
:
ASA Version 8.2 (1)
!
hostname asaoutsidedmz
activate the encrypted 123 password
123 encrypted passwd
names of
!
interface Ethernet0/0
link to the description to the ISP router / WAN
nameif outside
security-level 0
IP address x.x.x.235 255.255.255.224
!
interface Ethernet0/1
internal LAN interface Description
Shutdown
nameif inside
security-level 100
IP 192.168.1.1 255.255.255.0
!
interface Ethernet0/2
description of the DMZ interface
nameif dmz
security-level 50
IP 192.168.2.1 255.255.255.0
!
interface Ethernet0/3
Shutdown
No nameif
no level of security
no ip address
!
interface Management0/0
Shutdown
!
boot system Disk0: / asa821 - k8.bin
passive FTP mode
clock timezone IS - 5
clock to summer time EDT recurring
DNS domain-lookup outside
DNS domain-lookup dmz
DNS server-group DefaultDNS
cisco.com-domain name
outside_access_in list extended access permit tcp any host x.x.x.232 eq www
outside_access_in list extended access permit tcp any host x.x.x.234 eq ssh
pager lines 24
Outside 1500 MTU
Within 1500 MTU
MTU 1500 dmz
management of MTU 1500
local pool SSLVPNDHCP 192.168.200.20 - 192.168.200.25 255.255.255.0 IP mask
ICMP unreachable rate-limit 1 burst-size 1
ASDM image disk0: / asdm - 621.bin
don't allow no asdm history
ARP timeout 14400
Global interface 10 (external)
Global interface (dmz) 10
NAT (inside) 10 0.0.0.0 0.0.0.0
NAT (dmz) 10 0.0.0.0 0.0.0.0
static (dmz, external) x.x.x.232 192.168.2.18 netmask 255.255.255.255
static (dmz, external) x.x.x.234 192.168.2.36 netmask 255.255.255.255
Access-group outside_access_in in interface outside
Route outside 0.0.0.0 0.0.0.0 x.x.x.225 1
dynamic-access-policy-registration DfltAccessPolicy
RADIUS Protocol RADIUS AAA server
GANYMEDE + Protocol Ganymede + AAA-server
the ssh LOCAL console AAA authentication
No snmp server location
No snmp Server contact
Server enable SNMP traps snmp authentication linkup, linkdown cold start
life crypto ipsec security association seconds 28800
Crypto ipsec kilobytes of life - safety 4608000 association
No encryption isakmp nat-traversal
Telnet timeout 5
Console timeout 5
management-access inside
!
no statistical threat detection tcp-interception
WebVPN
allow outside
SVC disk0:/anyconnect-win-2.3.2016-k9.pkg 1 image
enable SVC
tunnel-group-list activate
internal group SSLVPN strategy
SSLVPN group policy attributes
value of SSL VPN profile banner
VPN - connections 1
VPN-idle-timeout 30
Protocol-tunnel-VPN l2tp ipsec svc
WebVPN
SVC request no svc default
attributes of Group Policy DfltGrpPolicy
Protocol-tunnel-VPN IPSec l2tp ipsec
username password privilege 123 encrypted test11 0
attributes of test11 username
type of remote access service
type tunnel-group SSLVPNTunnel remote access
attributes global-tunnel-group SSLVPNTunnel
address SSLVPNDHCP pool
Group Policy - by default-SSLVPN
tunnel-group SSLVPNTunnel webvpn-attributes
enable AgricorpVPN group-alias
!
class-map inspection_default
match default-inspection-traffic
!
!
type of policy-card inspect dns preset_dns_map
parameters
message-length maximum 512
Policy-map global_policy
class inspection_default
inspect the preset_dns_map dns
inspect the ftp
inspect h323 h225
inspect the h323 ras
inspect the rsh
inspect the rtsp
inspect esmtp
inspect sqlnet
inspect the skinny
inspect sunrpc
inspect xdmcp
inspect the sip
inspect the netbios
inspect the tftp
inspect the pptp
!
global service-policy global_policy
context of prompt hostname
: end
A few things to look at. Firstly, interface e0/1 is the stop of the config above for connecting clients will not be able to achieve the devices on the "inside" of the SAA. Second, you don't have NAT 0 rules configured to exempt the return of LAN or DMZ traffic to the client IP pool.
-
Cannot access within LAN of Cisco Anyconnect
I'm new to the firewall and try to get my Anyconnect test configuration to connect to addresses within my Local network. The Anyconnect client connects easily, I can get to addresses Internet and tracer package told me it falls to phase 6, svc-webvpn. Can someone post my config? I don't know I'm missing something pretty obvious. Config is pasted below:
!
interface Ethernet0/0
Description< uplink="" to="" isp="">
switchport access vlan 20
!
interface Ethernet0/1
Description< inside="">
switchport access vlan 10
Speed 100
full duplex
!
interface Ethernet0/2
Description< home="" switch="">
switchport access vlan 10
!
interface Ethernet0/3
switchport access vlan 10
!
interface Ethernet0/4
!
interface Ethernet0/5
Shutdown
!
interface Ethernet0/6
Shutdown
!
interface Ethernet0/7
Shutdown
!
interface Vlan10
nameif inside
security-level 100
IP 192.168.1.99 address 255.255.255.0
!
interface Vlan20
nameif OUTSIDE
security-level 0
DHCP client dns update
IP address dhcp setroute
!
Vlan30 interface
No nameif
no level of security
no ip address
!
Banner motd
Banner motd +... +
Banner motd |
Banner motd | Any unauthorized use or access prohibited * |
Banner motd |
Banner motd | The Officer allowed the exclusive use.
Banner motd | You must have explicit permission to access or |
Banner motd | configure this device. All activities performed.
Banner motd | on this unit can be saved and violations of.
Banner motd | This strategy may result in disciplinary action, and |
Banner motd | may be reported to the police authorities. |
Banner motd |
Banner motd | There is no right to privacy on this device. |
Banner motd |
Banner motd +... +
Banner motd
boot system Disk0: / asa824-k8
passive FTP mode
clock timezone cst - 6
clock to summer time recurring cdt
permit same-security-traffic intra-interface
ICMP-type of object-group DEFAULT_ICMP
Description< default="" icmp="" types="" permit="">
response to echo ICMP-object
ICMP-unreachable object
ICMP-object has exceeded the time
object-group network obj and AnyConnect
host of the object-Network 192.168.7.20
host of the object-Network 192.168.7.21
host of the object-Network 192.168.7.22
host of the object-Network 192.168.7.23
host of the object-Network 192.168.7.24
host of the object-Network 192.168.7.25
access-list 101 extended allow icmp a whole
!
Note access-list ACL_OUTSIDE < anyconnect="" permit=""> >
ACL_OUTSIDE list extended access permitted tcp everything any https eq
ACL_OUTSIDE list extended access permit icmp any any DEFAULT_ICMP object-group
!
VPN_NAT list extended access permit ip host 192.168.7.20 all
VPN_NAT list extended access permit ip host 192.168.7.21 all
VPN_NAT list extended access permit ip host 192.168.7.22 all
VPN_NAT list extended access permit ip host 192.168.7.23 all
VPN_NAT list extended access permit ip host 192.168.7.24 all
VPN_NAT list extended access permit ip host 192.168.7.25 all
access-list extended sheep allowed ip group object obj-AnyConnect 192.168.1.0 255.255.255.0
pager lines 24
Enable logging
timestamp of the record
logging buffered information
logging trap information
exploitation forest asdm errors
MTU 1500 inside
Outside 1500 MTU
mask 192.168.7.20 - 192.168.7.25 255.255.255.0 IP local pool AnyconnectPool
ICMP unreachable rate-limit 1 burst-size 1
ASDM image disk0: / asdm - 645.bin
don't allow no asdm history
ARP timeout 14400
Global (1 interface OUTSIDE)
NAT (INSIDE) 1 192.168.1.0 255.255.255.0
NAT (OUTSIDE) 1 access-list VPN_NAT
Access-group ACL_OUTSIDE in interface OUTSIDE
!
router RIP
network 192.168.1.0
passive-interface OUTSIDE
version 2
!
Timeout xlate 03:00
Timeout conn 01:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
Sunrpc timeout 0:10:00 h323 0:05:00 h225 mgcp from 01:00 0:05:00 mgcp-pat 0:05:00
Sip timeout 0:30:00 sip_media 0:02:00 prompt Protocol sip-0: 03:00 sip - disconnect 0:02:00
Timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
dynamic-access-policy-registration DfltAccessPolicy
AAA authentication http LOCAL console
Enable http server
http 192.168.1.0 255.255.255.0 inside
http 192.168.2.0 255.255.255.0 inside
No snmp server location
No snmp Server contact
Server enable SNMP traps snmp authentication linkup, linkdown cold start
Sysopt connection tcpmss 1200
Crypto ipsec transform-set esp-SHA-ESP-3DES-3des esp-sha-hmac
life crypto ipsec security association seconds 28800
Crypto ipsec kilobytes of life - safety 4688000 association
Crypto-map dynamic dynmap 20 the value transform-set ESP-3DES-SHA
map outside_map 64553-isakmp ipsec crypto dynamic dynmap
outside_map interface card crypto OUTSIDE
!
ISAKMP crypto identity hostname
crypto ISAKMP allow outside
crypto ISAKMP policy 10
preshared authentication
3des encryption
sha hash
Group 2
life 86400
VPN-addr-assign local reuse-delay 120
SSH 192.168.1.0 255.255.255.0 inside
SSH 192.168.2.0 255.255.255.0 inside
SSH timeout 60
Console timeout 0
management-access INTERIOR
DHCP-client broadcast-flag
dhcpd x.x.x.x dns
dhcpd rental 43200
dhcpd ping_timeout 2000
dhcpd auto_config OUTSIDE
!
dhcpd address 192.168.1.150 - 192.168.1.180 inside
dhcpd allow inside
!
a basic threat threat detection
Statistics-list of access threat detection
no statistical threat detection tcp-interception
NTP 216.229.0.179 Server
SSL encryption, 3des-sha1-aes128-sha1 aes256-sha1 sha1 rc4
localtrust point of trust SSL outdoors
WebVPN
allow outside
AnyConnect essentials
SVC disk0:/anyconnect-win-4.2.01035-k9.pkg 1 image
SVC disk0:/anyconnect-linux-64-4.2.01035-k9.pkg 2 image
Picture disk0:/anyconnect-macosx-i386-4.2.01035-k9.pkg 3 SVC
enable SVC
tunnel-group-list activate
attributes of Group Policy DfltGrpPolicy
Protocol-tunnel-VPN IPSec l2tp ipsec svc webvpn
internal Anyconnect group strategy
attributes Anyconnect-group policy
value x.x.x.x DNS server
VPN-tunnel-Protocol svc
the address value AnyconnectPool pools
type tunnel-group remotevpn remote access
tunnel-group Anyconnect type remote access
tunnel-group Anyconnect General attributes
strategy-group-by default Anyconnect
tunnel-group Anyconnect webvpn-attributes
enable MY_RA group-alias
!
class-map inspection_default
match default-inspection-traffic
!
!
type of policy-card inspect dns preset_dns_map
parameters
message-length maximum 512
Policy-map global_policy
class inspection_default
inspect the preset_dns_map dns
inspect the ftp
inspect h323 h225
inspect the h323 ras
inspect the rsh
inspect the rtsp
inspect esmtp
inspect sqlnet
inspect the skinny
inspect sunrpc
inspect xdmcp
inspect the sip
inspect the netbios
inspect the tftp
Review the ip options
!
global service-policy global_policy
context of prompt hostname
Auto-update 30 3 1 survey period
Update automatic timeout 1
call-home
Profile of CiscoTAC-1
no active account
http https://tools.cisco.com/its/service/oddce/services/DDCEService destination address
email address of destination [email protected] / * /
destination-mode http transport
Subscribe to alert-group diagnosis
Subscribe to alert-group environment
Subscribe to alert-group monthly periodic inventory
monthly periodicals to subscribe to alert-group configuration
daily periodic subscribe to alert-group telemetry
Cryptochecksum:d41d8cd98f00b204e9800998ecf8427e
: end
Hello
You are missing a NAT FREE for Anyconnect traffic would allow you to access inside the network.
access-list allowed sheep ip 192.168.1.0 255.255.255.0 192.168.7.0 255.255.255.0
NAT (inside) 0 access-list sheep
Add these two lines in the config file and you should be able to access the network interior.
Kind regards
Aditya
Please evaluate the useful messages and mark the correct answers.
-
AnyConnect client can not access local network
Hello
I have a problem with the Cisco anyconnect. Once clients are connected they cannot access anything whatsoever, including their default gateway.
Pool of the VPN client is on the same subnet as the LAN (139.16.1.x/24). Local network clients can access DMZ, VPN clients can ping computers on the local network, but they cannot access the DMZ.
I guess that any rule providing that traffic is absent but I m new with Cisco ASA and I m totally lost. I read as much as I could on this topic, but I do not understand which rule is necessary.
Thank you very much in advance for your support.
ASA release 9.4 (1)
!
ciscoasa hostname
activate the encrypted password of WmlxhdtfAnw9XbcA
TA.qizy4R//ChqQH encrypted passwd
names of
mask 139.16.1.50 - 139.16.1.80 255.255.255.0 IP local pool Pool_139
!
interface GigabitEthernet1/1
nameif outside
security-level 0
192.168.1.100 IP address 255.255.255.0
!
interface GigabitEthernet1/2
nameif inside
security-level 100
IP 139.16.1.1 255.255.255.0
!
interface GigabitEthernet1/3
nameif DMZ
security-level 50
IP 172.16.1.1 255.255.255.0
!
interface GigabitEthernet1/4
Shutdown
No nameif
no level of security
no ip address
!
interface GigabitEthernet1/5
Shutdown
No nameif
no level of security
no ip address
!
interface GigabitEthernet1/6
Shutdown
No nameif
no level of security
no ip address
!
interface GigabitEthernet1/7
Shutdown
No nameif
no level of security
no ip address
!
interface GigabitEthernet1/8
Shutdown
No nameif
no level of security
no ip address
!
Management1/1 interface
management only
nameif management
security-level 100
11.11.11.11 IP address 255.255.255.0
!
passive FTP mode
network obj_any object
subnet 0.0.0.0 0.0.0.0
internal subnet object-
139.16.1.0 subnet 255.255.255.0
network dmz subnet object
subnet 172.16.1.0 255.255.255.0
wialon Server external ip network object
Home 192.168.1.132
wialon-Server network objects
Home 172.16.1.69
Wialon-service-TCP object service
destination tcp source between 1 65535 21999 20100 service range
Wialon-service-UDP object service
destination service udp source between 0 65535 21999 20100 range
network of the NETWORK_OBJ_139.16.1.0_25 object
subnet 139.16.1.0 255.255.255.128
outside_acl list extended access permit tcp any object wialon-Server eq www
outside_acl list extended access allowed object Wialon-service-TCP any wialon-server object
outside_acl list extended access allowed object Wialon-service-UDP any wialon-server object
pager lines 24
asdm of logging of information
Outside 1500 MTU
Within 1500 MTU
MTU 1500 DMZ
management of MTU 1500
ICMP unreachable rate-limit 1 burst-size 1
don't allow no asdm history
ARP timeout 14400
no permit-nonconnected arp
NAT (inside, outside) static source any any static destination NETWORK_OBJ_139.16.1.0_25 NETWORK_OBJ_139.16.1.0_25 non-proxy-arp-search to itinerary
!
network obj_any object
dynamic NAT (all, outside) interface
internal subnet object-
NAT dynamic interface (indoor, outdoor)
wialon-Server network objects
NAT (DMZ, external) service wialon Server external ip static tcp www www
Access-group outside_acl in interface outside
Route outside 0.0.0.0 0.0.0.0 192.168.1.1 1
Timeout xlate 03:00
Pat-xlate timeout 0:00:30
Timeout conn 01:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
Sunrpc timeout 0:10:00 h323 0:05:00 h225 mgcp from 01:00 0:05:00 mgcp-pat 0:05:00
Sip timeout 0:30:00 sip_media 0:02:00 prompt Protocol sip-0: 03:00 sip - disconnect 0:02:00
Timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
Floating conn timeout 0:00:00
identity of the user by default-domain LOCAL
Enable http server
http 11.11.11.0 255.255.255.0 management
http 139.16.1.0 255.255.255.0 inside
No snmp server location
No snmp Server contact
service sw-reset button
Crypto ipsec ikev2 AES256 ipsec-proposal
Protocol esp encryption aes-256
Esp integrity sha - 1, md5 Protocol
Crypto ipsec ikev2 ipsec-proposal AES192
Protocol esp encryption aes-192
Esp integrity sha - 1, md5 Protocol
Crypto ipsec ikev2 ipsec-proposal AES
Esp aes encryption protocol
Esp integrity sha - 1, md5 Protocol
Crypto ipsec ikev2 proposal ipsec 3DES
Esp 3des encryption protocol
Esp integrity sha - 1, md5 Protocol
Crypto ipsec ikev2 ipsec-proposal OF
encryption protocol esp
Esp integrity sha - 1, md5 Protocol
Crypto ipsec pmtu aging infinite - the security association
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 define ikev2 AES256 AES192 AES 3DES ipsec-proposal OF
outside_map card crypto 65535-isakmp dynamic ipsec SYSTEM_DEFAULT_CRYPTO_MAP
outside_map interface card crypto outside
Crypto ca trustpoint ASDM_TrustPoint0
registration auto
domain name full ciscoasa.srdongato.null
E-mail [email protected] / * /
name of the object CN = srdongato
Serial number
Proxy-loc-transmitter
Configure CRL
Crypto ca trustpoint ASDM_Launcher_Access_TrustPoint_0
registration auto
full domain name no
name of the object CN = 139.16.1.1, CN = ciscoasa
ASDM_LAUNCHER key pair
Configure CRL
trustpool crypto ca policy
string encryption ca ASDM_TrustPoint0 certificates
certificate 09836256
30820381 30820269 a0030201 02020409 83625630 0d06092a 864886f7 0d 010105
05003050 31123010 06035504 03130973 72646f6e 6761746f 313 has 3012 06035504
05130b4a a 41443139 32323033 34343024 06092, 86 01090216 17636973 4886f70d
636f6173 612e7372 646f6e67 61746f2e 6e756c6c 31353132 30353036 301e170d
5a170d32 33333535 35313230 32303633 3335355a 30503112 30100603 55040313
09737264 6f6e6761 30120603 55040513 31393232 30333434 0b4a4144 746f313a
2a 864886 30240609 f70d0109 6973636f 02161763 6173612e 7372646f 6e676174
6f2e6e75 6c6c3082 0122300d 06092 has 86 01010105 00038201 0f003082 4886f70d
010a 0282 010100d 2 295e679c 153e8b6a d3f6131d 8ea646e3 aa0a5fa9 20e49259
ca895563 7e818047 033a4e8f 57f619e9 fa93bfd5 6c44141f b0abf2c0 8b86334e
bac63f41 99e6d676 c689dcf7 080f2715 038a8e1b 694a00de 7124565e a1948f09
8dbeffab c7c8a028 741c5b10 d0ede5e9 599f38fe 5b88f678 4decdc4b b 353, 6708
cfa2fbce f58be06e 18feba56 4b2b04a1 77773ec6 5c58d2ed d7ca4f17 980f0353
138bfe65 1b1165e6 7b6f94bb ab4d4286 e900178c 147a6dba 2427f38e e225030f
0a66d1eb 5075c57e 6d77e5bb 247f5bc3 8d3530f0 49dedf2d 21a24b5f daa08d98
690183cf e82a6b8d 5e489956 c5eecdbc 7fc2365c b629a52b 126b51e2 18590ed5
c9da8503 a639f102 03010001 a3633061 300f0603 551d 1301 01ff0405 30030101
ff300e06 03551d0f 0101ff04 86301f06 04030201 23 04183016 80143468 03551d
dec79103 0a91b530 1ada7e47 7e27b16d 4186301d 0603551d 0e041604 143468de
c791030a 91b5301a da7e477e 27b16d41 86300d 86f70d01 01050500 06 092 a 8648
003cdb04 03820101 8ef5ed31 c05c684b ad2b0062 96bfd39a ecb0a3fe 547aebe5
14b753e7 89f55827 3d4e0aa8 b8674e45 80d4c023 8e99a7b4 0907d 347 060a2fe4
fa6e0c2f 3b9cd708 a539c09f 7022d2ee fb6e2cf6 82b0e861 a2839a71 1512b3ec
e28664e9 732270c 9 d1c679d9 1eaf2ad5 31c3ff97 09aae869 88677a3d b 007, 5699
ecb3032e 2dd0f74f 81f9a8fb 79f30809 723bbdbf dfef4154 5ad6b012 a8f37093
481fa678 b44b0290 23390036 042828f3 5eefdc43 ebe52d26 78934455 9b4234a9
4146 166e5adc b431f12f 8d0fbf16 46306228 731c bfeebc43 34 76984 d2e6ebbc
88ca120a 96838694 d4f32884 963e7385 987ec6b0 dfa28d49 05ba5fa8 641bcfc7
ff92ac3c 52
quit smoking
string encryption ca ASDM_Launcher_Access_TrustPoint_0 certificates
Certificate 0 is 836256
308202cc a0030201 0202040a 0d06092a 83625630 864886f7 0d 010105 308201b 4
05003028 06035504 03130863 61736131 13301106 03550403 6973636f 3111300f
130a 3133 392e3136 2e312e31 31353132 30353036 35363236 5a170d32 301e170d
35313230 32303635 3632365a 30283111 55040313 08636973 636f6173 300f0603
61311330 11060355 0403130 3133392e 31362e31 2e313082 0122300d 06092 has 86
4886f70d 01010105 00038201 0f003082 010 has 0282 010100e7 a5c16e86 16c15a10
e018b868 bac7271a 30f1a3f8 ecb9c6b8 3ed4b1ad c9468f5e 287f2a7a 644f1496
c43a061e da927d09 a755b53e ed7c6a66 f2f1fb1e f944345c 86e08ce0 891c99b3
13101ab3 04963fad f91f987f 99f22a89 cd1e8c5a 5e4c026d 2cadd7b7 6620bbd1
b4a5135b 24ec886f fa061a06 dd536e96 1e483730 756c 4101 23f83a8d 944a7fbe
93c51d56 32ac0d17 ceb75f63 0ae24f07 f2c54e83 5b84ff00 16b0b899 c925c737
1765b 066 23 b 54645 bc419684 d09dd130 c1479949 68b0a779 df39b078 6fb0deb9
758b14c3 f0801faf f0ad60e1 a018ffba d769f867 3fe8e5fc 88ccc5b2 2319f5d4
617a78c4 74e7a64b 5c68276c 06ea57c1 d0ffce4b 358c4d02 03010001 300 d 0609
2a 864886 05050003 82010100 dff97c9f 4256fd47 8eb661fd d22ecea4 f70d0101
589eff09 958e01f1 a435a20e 5ed1cf19 af42e54d d61fc0ab cb2ee7ac 7fcb4513
1a44cc86 1e020d72 3a3f78d2 4 d 225177 857093d 9 f5fcf3c7 6e656d2b 54a0c522
f636b8cf 33c5ae34 ea340f32 85dff4c1 50165e7a e94de10b ced15752 0b3a76c1
2a50777b 20291106 a1a8a214 a 8 003716 680c15d4 ac3f7cc7 378f8f5f 38e3403f
f958c095 e549c8ed 4baf8cc5 bdcd230e 260754ea 953c3a4c eb01fef5 62b97e01
9f82ce6b f479dbdd 000c45af 8758b35f b4a958ee 32c4db3f 2ddc7385 dc05b0e3
78b609ba a9280841 2433ae87 5dd7a7c2 d5691068 1dc0eddc c23f99c5 3df8b1a5
aadbd82a 423f4ba8 563142bf 742771c 3
quit smoking
IKEv2 crypto policy 1
aes-256 encryption
integrity sha
Group 2 of 5
FRP sha
second life 86400
IKEv2 crypto policy 10
aes-192 encryption
integrity sha
Group 2 of 5
FRP sha
second life 86400
IKEv2 crypto policy 20
aes encryption
integrity sha
Group 2 of 5
FRP sha
second life 86400
IKEv2 crypto policy 30
3des encryption
integrity sha
Group 2 of 5
FRP sha
second life 86400
IKEv2 crypto policy 40
the Encryption
integrity sha
Group 2 of 5
FRP sha
second life 86400
Crypto ikev2 activate out of service the customer port 443
Crypto ikev2 access remote trustpoint ASDM_TrustPoint0
Telnet 139.16.1.0 255.255.255.0 inside
Telnet 11.11.11.0 255.255.255.0 management
Telnet timeout 5
without ssh stricthostkeycheck
SSH timeout 5
SSH group dh-Group1-sha1 key exchange
Console timeout 0
dhcpd outside auto_config
!
dhcpd address 172.16.1.69 - DMZ 172.16.1.69
dhcpd dns 87.216.1.65 87.216.1.66 DMZ interface
dhcpd option 3 ip 172.16.1.1 DMZ interface
dhcpd enable DMZ
!
a basic threat threat detection
Statistics-list of access threat detection
no statistical threat detection tcp-interception
SSL-trust outside ASDM_TrustPoint0 point
SSL-trust ASDM_Launcher_Access_TrustPoint_0 inside point
Trust ASDM_Launcher_Access_TrustPoint_0 inside the vpnlb-ip SSL-point
WebVPN
allow outside
AnyConnect image disk0:/anyconnect-win-3.1.12020-k9.pkg 1
AnyConnect profiles Wialon_client_profile disk0: / Wialon_client_profile.xml
AnyConnect enable
tunnel-group-list activate
Disable error recovery
internal GroupPolicy_Wialon group strategy
attributes of Group Policy GroupPolicy_Wialon
WINS server no
value of 192.168.1.1 DNS server
client ssl-VPN-tunnel-Protocol ikev2
by default no
WebVPN
AnyConnect value Wialon_client_profile type user profiles
dynamic-access-policy-registration DfltAccessPolicy
wialon_1 Wy2aFpAQTXQavfJD username encrypted password
wialon_2 4STJ9bvyWxOTxIyH encrypted password username
remote access to Wialon tunnel-group type
attributes global-tunnel-group Wialon
address pool Pool_139
Group Policy - by default-GroupPolicy_Wialon
tunnel-group Wialon webvpn-attributes
enable Wialon group-alias
!
class-map inspection_default
match default-inspection-traffic
!
!
type of policy-card inspect dns preset_dns_map
parameters
maximum message length automatic of customer
message-length maximum 512
Policy-map global_policy
class inspection_default
inspect the preset_dns_map dns
inspect the ftp
inspect h323 h225
inspect the h323 ras
inspect the rsh
inspect the rtsp
inspect esmtp
inspect sqlnet
inspect the skinny
inspect sunrpc
inspect xdmcp
inspect the sip
inspect the netbios
inspect the tftp
Review the ip options
!
global service-policy global_policy
context of prompt hostname
no remote anonymous reporting call
Cryptochecksum:447ec315ae30818a98f705fb1bf3fd75Hello
You don't have NAT exemption the DMZ network to the pool of VPN traffic.
Please try to add the following statement to run:
nat (DMZ,outside) 1 source static any any destination static NETWORK_OBJ_139.16.1.0_25 NETWORK_OBJ_139.16.1.0_25 route-lookup
Also please delete the existing instruction manual nat "non-proxy-arp" statement, because it can cause problems like you the ip subnet address pool is identical to that of the Interior of the network.no nat (inside,outside) source static any any destination static NETWORK_OBJ_139.16.1.0_25 NETWORK_OBJ_139.16.1.0_25 no-proxy-arp route-lookup nat (inside,outside) 1 source static any any destination static NETWORK_OBJ_139.16.1.0_25 NETWORK_OBJ_139.16.1.0_25 route-lookup
Cordially Véronique
Maybe you are looking for
-
I've just updated to v26 to your last. Can't find a topic tab?
I was looking for a subject tab to find the new version number. No luck. Running Windows 7 Pro 64 bit.
-
Cannot retrieve downloaded VeohWebPlayerSetup file with Unarchiver... How can I fix this problem?
Hi all. To download my videos on Veoh, I had downloaded their web player for Mac. But Unarchiver declares that it cannot extract this program. Opening of the finger on the button control too gives no results. What should I do? Thanks in advance. Dr.
-
Hellooo all,. I you'd be grateful if someone helped me with the readings of the parser I have attached to this announcement. I do not know if the ckt is correct and would like to know your answer please. Thanks for posting,
-
Replacing the hard drive not detected in windows 8 clean install
I have a Dell latitude E6330 and my HDD recently crashed. With the replacement hard dive, I could not clean install windows 8. The BIOS indicates the presence of the hard drive without problems diagnosed but windows 8 installation a driver is needed
-
How to send an illustrator file to ipad pro adobe draw?
Hi, I want to continue in the application Adobe Illustrator drawing to draw, but I don't know how to send it to the iPad, can someone help me please?