ASA NAT to 8.4
I'm doing the VPN tunnel between router IOS and ASA 5505. The ASA has a dynamic IP address
Everything would be ok, but I don't understand NAT in ASA's new orders. Can you tell me how to convert it to version 8.3 - 4?
access-list no. - NAT allowed extended ip 10.1.1.0 255.255.255.0 10.2.1.0 255.255.255.0
Global 1 interface (outside)
NAT (inside) - No. - NAT 0 access list
NAT (inside) 1 0.0.0.0 0.0.0.0
I use this link
http://www.Cisco.com/c/en/us/support/docs/security/PIX-500-series-Securi...
Thanks for any help.
Take a look at the document, depending on where you can find almost everything on the new model of NAT:
Especially "NAT0 / NAT Exemption / identity NAT ' in part"TWICE-NAT-MANUAL-NAT"is relevant for this task.
Tags: Cisco Security
Similar Questions
-
CSCue51351 - ASA NAT huge config causes traceback because of the unbalanced tree p3
Hi experts ASA
CSCue51351 - ASA NAT huge config causes traceback because of the unbalanced tree p3
I want to know that how huge?
Below, this Condition of DDT is SSP60.
----------------------
Symptom:
Version 9 8.4 (4) current ASA code can generate a traceback with thread name: DATAPATH-7-2315 and reload.
Conditions:
Seen on ASA5585-SSP-60 running in the failover environment.
Workaround solution:
None
----------------------
SSP60 can perform up to 10 000 000 simultaneous sessions.
It's more than 10 000 000 simultaneous sessions?
Kind regards.
Word
Hello Word,
This flaw does not affect the number of concurrent sessions.
Instead, this fault comes to play if you have a large number of statements NAT or ACL (say 25 k +) which you change and at the same time the unit treats a large number of new connections per second (say 20 k +), what then is there the possibility of hitting this issue.
Sincerely,
David.
-
ASA NAT 9.1 as object under standalone vs NAT command command
Hey guys,.
I'm setting up a few new 5515 X ASAs.
Are there major differences between the two methods of syntax NAT? They both seem to work in a lab environment. I find that the first method mentioned in the Cisco documentation for one-to-one NAT static execution, however.
Method 1:
network of the object Test-DMZ-Server_EXT
Home 172.25.1.2
network of the LOCAL-RANGE_EXT object
Home 172.17.1.2network of LOCAL-RANGE object
host 192.168.10.2
NAT (inside, outside) static LOCAL-RANGE_EXT
network of the DMZ-Test Server object
Home 192.168.199.2
NAT (DMZ, all) public static Test-DMZ-Server_EXT
network of the ANY object
subnet 0.0.0.0 0.0.0.0
dynamic NAT (all, outside) interfaceMethod 2:
network of LOCAL-RANGE object
host 192.168.10.2
network of the DMZ-Test Server object
Home 192.168.199.2
network of the object Test-DMZ-Server_EXT
Home 172.25.1.2
network of the LOCAL-RANGE_EXT object
Home 172.17.1.2NAT (DMZ, all) source static-DMZ-Server Test Test-DMZ-Server_EXT
NAT (insdie, outside) Shared source LOCAL-RANGE-LOCAL-RANGE_EXTNAT (all, outside) source Dynamics one interface
Thank you
Hello
Both formats of configuration can achieve the same thing.
The first is Auto NAT / NAT network of the object where the user configures the configuration complete "nat" under the created 'object'. Generally, this format of configuration is used to configure static dynamic static NAT PAT and PAT at least.
The second configuration is twice the NAT / manual NAT who uses different configurations 'object' and ' object-group ' to list the addresses/actual in the NAT configurations. This "nat" configuration is not located under objects, but rather to use them. Generally, this format of configuration is used to configure the NAT type NAT0 configurations or policy.
While the two configuration to achieve the same there is a big difference between them. In the new NAT configuration format introduced in paragraph 8.3, NAT configurations are divided into 3 Sections which sets their priority in the "nat" configurations
They are as follows
- Article 1 = manual NAT / twice by NAT
- Section 2 = Auto NAT / NAT network object
- Section 3 = manual NAT / twice by NAT
- a parameter added "after the automatic termination" is required to move this Section 3 configuration
So depending on what format you use you might find yourself of the substitution of some other configuration by inserting article 1 configuration (what you are doing by using the manual NAT / double configuration NAT format). Well I would say that it becomes a problem that in some situations in simple firewall configurations. I would say that the problem the most common here on the forums is usually when a user has configured a dynamic PAT in the Section 1 and static PAT (Port Forward) in Section 2, and uses the same public IP as PAT address both. This creates a situation where all traffic from external networks is the dynamic configuration PAT in Section 1, rather than any static configuration PAT in Section 2.
Another big difference between NAT Auto and manual NAT is the fact that NAT Auto does that source address translation (which may seem odd depending on which side you are looking for the situation) while Manuel NAT can do the conversion for the source and destination IP address. But that you configure static NAT, it didn't really matter. The two formats NAT can achieve the same thing.
Ultimately nothing for example prevents you all just about everything using Section 1 Manual NAT if you wanted to. You can set up no matter what type of NAT you wanted on this stretch alone and would not use NAT Auto at all if it was your wish. But I would say that's not suggestable and even less so if you have a large NAT configuration.
My personal suggestion in brief is as follows
- Article 1 = use of the configurations type NAT0 and static/dynamic policy NAT as these configurations are usually intended to replace typical NAT configurations.
- Section 2 = use static and static NAT PAT that this provides the format of simpler configuration for the listed configurations and they are still quite high in priority being in Section 2. NAT configuration manual would require several configurations of 'object' to achieve the same.
- Section 3 = Place all your Dynamic NAT/PAT or NAT + PAT configurations here because this should be the last connection NAT must match in all cases when it has nothing specifically designed for guests.
I find that with the above way you keep your severed much NAT configuration and know what where. The configuration is also a little less cluttered when configurations are not in the same Section.
If you want to read more about the new format of configuration NAT you can check out a document, I wrote here in 2013. Although it includes the things I mentioned above also.
https://supportforums.Cisco.com/document/132066/ASA-NAT-83-NAT-operation...
You can of course ask here in this discussion if you want :)
Remember to mark a reply as the answer if it answered your question.
Hope this helps :)
-Jouni
-
Hello
I have a question about NAT and routing on the SAA. I'm relatively new to ASA and don't know if it works or not. I have a pool of public IP (209.x.x.x/28) that routes my ISP to the external interface of my ASA. IP was assigned address for the outside of the ASA is an address of 206.x.x.2/24 with a default GW of 206.x.x.1. I intend using NAT to allow my web/mail servers on the DMZ (192.168.x.x) use 209.x.x.x addresses. However, I do know how to make it work since I'm not arping on any interface for 209.x.x.x addresses as they will be sent to the 206.x.x.2 address by the ISP. Can I just set up a translation NAT (on the external interface?) of the 209.x.x.x on 192.168.x.x address and the ASA will figure it out?
Thanks for the help.
Todd
The ASa will figure it out, he will answer ARP queries for all that he has set up in a "static" command As long as th PSIA routes 209.x.x.x directly to the ASA addresses then it should all work fine.
You just need to add lines like the following:
static (dmz, external) 209.x.x.x netmask 255.255.255.255 192.168.x.x
for each of your internal servers in the DMZ. Then an access-list to allow only HTTP/SMTP/etc through these addresses 209.x.x.x.
list of allowed inbound tcp access any host 209.x.x.x eq smtp
list of allowed inbound tcp access any host 209.y.y.y eq http
Access-group interface incoming outside
-
Hi all
Please I need to be clear on one point:
is
static (Inside, Outside) 10.10.10.1 11.11.11.1 netmask 255.255.255.0
the same thing that
static (Outside, Inside) 11.11.11.1 10.10.10.1 netmask 255.255.255.0?
No, they are not same. The order of a static NAT device is:
static (real_interface,mapped_interface) mapped_ip real_ip netmask mask
What you do is: static (network more secure, less secure network). If you can do one of these:
static (DMZ, Outside) etc.
static (Inside, DMZ) etc.
static (Inside, Outside) etc.
If your case you should do: static (inside address, external) 100.100.100.100 192.168.10.1 netmask 255.255.255.255
This external address 100.100.100.100 inside NAT will address 192.168.10.1.
HTH
-
ASA 8.4 (3) - applying NAT breaks my tunnel from site to site - "Routing failed.
So I'm a few 5510 preconfiguration is before shipment to the site. I have my tunnel VPN from Site to Site and can ping of internal subnets between the sites. However, as soon as I configure NAT on my interface my pings die outside. I checked a guide very full config posted by TAC and I think the answer is to set up two times-NAT, which I believe I did. I don't always get no package in the tunnel.
A hint, I found, is that I get the journaled message when NAT is applied & affecting routing "ASA-6-110003: routing could not locate the next hop for ICMP from Outside:10.56.8.4/512 to Internal:172.16.60.253/0.
Output sh run object / run object-group sh / sh run nat / show the two ASA nat: -.
SITE 1
= sh run object
network obj_any object
subnet 0.0.0.0 0.0.0.0
network of the BH-Asterisk object
host x.x.x.x
BG Hill Asterisk description
network of the BH-Exchange object
host x.x.x.x
BG Hill Exchange Server description
the DH - AV object network
10.56.20.0 subnet 255.255.255.0
Description AV DH
the DH-Asterisk object network
host x.x.x.x
DH Asterisk description
the object-Diffie-Hellman exchange network
Home 10.56.1.253
Description Exchange Diffie-Hellman
the DH-guests object network
10.56.8.0 subnet 255.255.255.0
DH customers description
the object DH ME network
10.56.24.0 subnet 255.255.255.0
DH ME description
the DH-phones object network
10.56.16.0 subnet 255.255.255.0
Description phones DH
network of the DH-security object
10.56.32.0 subnet 255.255.255.0
Description safety DH
DH-internal object network
10.56.1.0 subnet 255.255.255.0
Description internal DH
network object internally-BH
10.60.1.0 subnet 255.255.255.0
Description internal BH
network of the BH-phones object
10.60.16.0 subnet 255.255.255.0
Description BH phones
network of the BH-security object
10.60.32.0 subnet 255.255.255.0
BH Security description
network of the BH - AV object
10.60.20.0 subnet 255.255.255.0
Description AV BH
network of the BH-guests object
10.60.8.0 subnet 255.255.255.0
BH invited description
network of the BH - ASA object
host 1.1.1.1
the DH - ASA object network
host 1.1.1.2
network of the BH-RAS object
10.60.99.0 subnet 255.255.255.0
the DH-RAS object network
10.56.99.0 subnet 255.255.255.0
network of the NETWORK_OBJ_10.56.99.0_26 object
255.255.255.192 subnet 10.56.99.0
network of the BH-UC560 object
Home 172.16.60.253
network of the DH-UC560 object
Home 172.16.56.253= RJ5510-DOHA # sh run object-group
the BGHill object-group network
Description of subnets in BGHill
BH-internal network-object
network-object BH-phones
network-object BH - AV
network-object BH-security
network-object BH-guests
network-object BH-RAS
BH-UC560 network-object
object-group network DH
Description of subnets in DH
network-object DH - AV
network-object DH-guests
network-object DH ME
network-object DH-phones
network-object DH-security
DH-internal network-object
network-object DH-RAS
network object-DH-UC560= RJ5510-DH # sh run nat
NAT (AV, outdoors) static source DH DH static destination BGHill BGHill
NAT (comments, outdoors) static source DH DH static destination BGHill BGHill
NAT (inside, outside) static source DH DH static destination BGHill BGHill
NAT (phones, outdoors) static source DH DH static destination BGHill BGHill
NAT (safety, outdoors) static source DH DH static destination BGHill BGHill
NAT (ME out) static source DH DH static destination BGHill BGHill
!
the DH - AV object network
dynamic NAT interface (AV, outdoors)
the object-Diffie-Hellman exchange network
x.x.x.x static NAT (indoor, outdoor)
the DH-guests object network
dynamic NAT interface (comments, outdoors)
the object DH ME network
dynamic NAT interface (ME, outdoor)
the DH-phones object network
dynamic NAT interface (phones, outdoors)
network of the DH-security object
dynamic NAT interface (safety, outdoors)
DH-internal object network
dynamic NAT interface (indoor, outdoor)= HD-RJ5510 # see nat
Manual NAT policies (Section 1)
1 (f) (outdoor) static source DH DH destination static BGHill BGHill
translate_hits = 0, untranslate_hits = 386
2 (guest) (outdoor) static source DH DH destination static BGHill BGHill
translate_hits = 180, untranslate_hits = 0
3 (inside) (outside) static source DH DH destination static BGHill BGHill
translate_hits = 0, untranslate_hits = 0
4 (phones) (outdoor) static source DH DH destination static BGHill BGHill
translate_hits = 0, untranslate_hits = 0
5 (security) (outdoor) static source DH DH destination static BGHill BGHill
translate_hits = 0, untranslate_hits = 0
6 (ME) (outdoor) static source DH DH destination static BGHill BGHill
translate_hits = 0, untranslate_hits = 0Auto NAT policies (Section 2)
1 (outdoor) source static-Exchange Diffie-Hellman x.x.x.x (internal)
translate_hits = 0, untranslate_hits = 0
2 (internal) interface of DH-internal dynamics of the source (outdoor)
translate_hits = 0, untranslate_hits = 0
3 (comments) interface (outside) dynamic source DH-guests
translate_hits = 2, untranslate_hits = 0
4 (phones) to the dynamic interface of DH-phones of the source (outside)
translate_hits = 0, untranslate_hits = 0
5 (AV) to dynamic source DH - AV interface (outside)
translate_hits = 0, untranslate_hits = 0
6 (I) dynamic source DH-ME interface (outside)
translate_hits = 0, untranslate_hits = 0
7 (security) to DH-security dynamic interface of the source (outside)
translate_hits = 0, untranslate_hits = 0SITE 2: -.
= object # executed sh
network obj_any object
subnet 0.0.0.0 0.0.0.0
network of the BH-Asterisk object
host x.x.x.x
BH Hill Asterisk description
network of the BH-Exchange object
Home 10.60.1.253
BH Hill Exchange Server description
the DH - AV object network
10.56.20.0 subnet 255.255.255.0
Description AV DH
the DH-Asterisk object network
host x.x.x.x
DH Asterisk description
the object-Diffie-Hellman exchange network
host x.x.x.x
Description Exchange Diffie-Hellman
the DH-guests object network
10.56.8.0 subnet 255.255.255.0
DH customers description
the object DH ME network
10.56.24.0 subnet 255.255.255.0
DH ME description
the DH-phones object network
10.56.16.0 subnet 255.255.255.0
Description phones DH
network of the DH-security object
10.56.32.0 subnet 255.255.255.0
Description safety DH
DH-internal object network
10.56.1.0 subnet 255.255.255.0
Description internal DH
network object internally-BH
10.60.1.0 subnet 255.255.255.0
Description internal BH
network of the BH-phones object
10.60.16.0 subnet 255.255.255.0
Description BH phones
network of the BH-security object
10.60.32.0 subnet 255.255.255.0
BH Security description
network of the BH - AV object
10.60.20.0 subnet 255.255.255.0
Description AV BH
network of the BH-guests object
10.60.8.0 subnet 255.255.255.0
BH invited description
network of the BH - ASA object
host 1.1.1.1
the DH - ASA object network
host 1.1.1.2
network of the NETWORK_OBJ_10.60.99.0_26 object
255.255.255.192 subnet 10.60.99.0
network of the BH-RAS object
10.60.99.0 subnet 255.255.255.0
the DH-RAS object network
10.56.99.0 subnet 255.255.255.0
network of the BH-UC560 object
Home 172.16.60.253
network of the DH-UC560 object
Home 172.16.56.253= # sh run object-group
the BHHill object-group network
Description of subnets in BH Hill
BH-internal network-object
network-object BH-phones
network-object BH - AV
network-object BH-security
network-object BH-guests
network-object BH-RAS
BH-UC560 network-object
object-group network DH
Description of subnets in DH
network-object DH - AV
network-object DH-guests
network-object DH ME
network-object DH-phones
network-object DH-security
DH-internal network-object
network-object DH-RAS
network object-DH-UC560= # sh run nat
NAT (inside, outside) static source BHHill BHHill static destination DH DH
NAT (AV, outdoors) static source BHHill BHHill static destination DH DH
NAT (comments, outdoors) static source BHHill BHHill static destination DH DH
NAT (phones, outdoors) static source BHHill BHHill static destination DH DH
NAT (safety, outdoors) static source BHHill BHHill static destination DH DH
!
network of the BH-Exchange object
x.x.x.x static NAT (indoor, outdoor)
network object internally-BH
dynamic NAT interface (indoor, outdoor)
network of the BH-phones object
dynamic NAT interface (phones, outdoors)
network of the BH-security object
dynamic NAT interface (safety, outdoors)
network of the BH - AV object
dynamic NAT interface (AV, outdoors)
network of the BH-guests object
dynamic NAT interface (comments, outdoors)= # sh nat
Manual NAT policies (Section 1)
1 (inside) (outside) static source BHHill BHHill static destination DH DH
translate_hits = 421, untranslate_hits = 178
2 (AV) to (outside) static source BHHill BHHill static destination DH DH
translate_hits = 0, untranslate_hits = 0
3 (guest) (outdoor) static source BHHill BHHill static destination DH DH
translate_hits = 0, untranslate_hits = 0
4 (phones) (outdoor) static source BHHill BHHill static destination DH DH
translate_hits = 0, untranslate_hits = 0
5 (security) (outdoor) static source BHHill BHHill static destination DH DH
translate_hits = 0, untranslate_hits = 0Auto NAT policies (Section 2)
1 (outdoor) static source BH-Exchange x.x.x.x (internal)
translate_hits = 0, untranslate_hits = 0
2 (internal) interface of BH-internal dynamics of the source (outdoor)
translate_hits = 0, untranslate_hits = 0
3 (comments) interface (outside) dynamic source BH-guests
translate_hits = 0, untranslate_hits = 0
4 (phones) to the dynamic interface of BH-phones of the source (outside)
translate_hits = 0, untranslate_hits = 0
5 (AV) to dynamic source BH - AV interface (outside)
translate_hits = 0, untranslate_hits = 0
6 (security) at the interface of BH-security dynamic of the source (outdoor)
translate_hits = 0, untranslate_hits = 0
RJ5510-BH #.I admit that I am scoobied with this one, but I hope that someone will find the capture?
Thank you
In fact, the problem is with the NAT because because you use the same object on different States of NAT attached to different interfaces.
The SAA can go crazy with it...
I must leave now.
As soon as I get back I'll explain this a little further.
Kind regards
Julio
Note all useful posts
-
The ASA to use a different Port SSH
Please let me know if you have heard of this
Thank you
Dave
Dave,
According to my knowledge the ASA does not support this. Anthony we have a device before the ASA natting redirect some ther port at 22 of the SAA.
I hope this helps.
Kind regards
SOM
PS: Please check the issue as resolved if it is answered. Note the useful messages. Thank you.
-
Hello
I'm new to configurations of ASA and who need help with Setup on an execution code 8.6 X 5555. I need allow network several ip address ranges from my inside several subnets outside the network so that external systems only see traffic entering an ip address and may not be the ip address of the external interface. I was able to do this with a box and statements IOS nat-based firewall but difficult to do the same in the bones of the ASA.
Hello
Sound is fairly simple and fast, for your condition, you should use.
Information on PAT Dynamics
Dynamic PAT translates multiple real addresses to a single IP address mapped by translating the port real, address and source, the mapped address and a unique port. If necessary, the actual source port number is used for the mapped port. However, if the actual port is not available, by default mapped ports are selected in the same range of ports than the real port number: 0 to 511, 512 to 1023 and 1024 to 65535. Therefore, ports below 1024 have only a small PAT pool that can be used. (8.4 (3) and later, not including 8.5 (1) or 8.6 (1)) If you have a lot of traffic that uses the lower ranges of port, you can now specify a flat range of ports to use instead of the three levels of unequal size.
Each connection requires a separate translation session because the source port is different for each connection. For example, 10.1.1.1:1025 requires a separate 10.1.1.1:1026 translation.
Figure 27-10 illustrates a typical scenario of PAT dynamic. Only real hosts can create a session of NAT, who answered the questionnaire of traffic is allowed to return. The mapped address is the same for each translation, but the port is assigned dynamically.
Figure 27-10 dynamic PAT
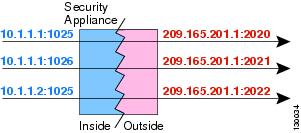
After the expiry of the connection port forwarding expires after 30 seconds of inactivity. The timeout is not configurable. The destination network users may not reliably initiate a connection to a host that uses PAT (even if the connection is allowed by an access rule).
Understanding of NAT
Let me know if you need help on this, you can do PAT with additional IP addresses that are available on outside interface. You must have appropriate for the additional ip address routing
HTH
Sandy. -
ASA: VPN IPSEC Tunnel from 5505(ver=8.47) to 5512 (ver = 9.23)
Hi-
We have connected tunnel / VPN configuration between an ASA 5505 - worm = 8.4 (7) and 5512 - worm = 9.2 (3).
We can only ping in a sense - 5505 to the 5512, but not of vice-versa(5512 to 5505).Networks:
Local: 192.168.1.0 (answering machine)
Distance: 192.168.54.0 (initiator)See details below on our config:
SH run card cry
card crypto outside_map 2 match address outside_cryptomap_ibfw
card crypto outside_map 2 pfs set group5
outside_map 2 peer XX crypto card game. XX.XXX.XXX
card crypto outside_map 2 set transform-set ESP-AES-256-SHA ikev1
crypto map outside_map 2 set ikev2 AES256 ipsec-proposaloutside_map interface card crypto outside
Note:
Getting to hit numbers below on rules/ACL...SH-access list. I have 54.0
permit for access list 6 outside_access_out line scope ip 192.168.1.0 255.255.255.0 192.168.54.0 255.255.255.0 (hitcnt = 15931) 0x01aecbcc
permit for access list 1 outside_cryptomap_ibfw line extended ip object NETWORK_OBJ_192.168.1.0_24 object NETWORK_OBJ_192.168.54.0_24 (hitcnt = 3) 0xa75f0671
access-list 1 permit line outside_cryptomap_ibfw extended ip 192.168.1.0 255.255.255.0 192.168.54.0 255.255.255.0 (hitcnt = 3) 0xa75f0671SH run | I have access-group
Access-group outside_access_out outside interfaceNOTE:
WE have another working on the 5512 - VPN tunnel we use IKE peer #2 below (in BOLD)...HS cry his ikev1
IKEv1 SAs:
HIS active: 2
Generate a new key SA: 0 (a tunnel report Active 1 and 1 to generate a new key during the generate a new key)
Total SA IKE: 21 peer IKE: XX. XX.XXX.XXX
Type: L2L role: answering machine
Generate a new key: no State: MM_ACTIVE
2 IKE peers: XXX.XXX.XXX.XXX
Type: L2L role: answering machine
Generate a new key: no State: MM_ACTIVESH run tunnel-group XX. XX.XXX.XXX
tunnel-group XX. XX.XXX.XXX type ipsec-l2l
tunnel-group XX. XX.XXX.XXX General-attributes
Group - default policy - GroupPolicy_XX.XXX.XXX.XXX
tunnel-group XX. XX.XXX.XXX ipsec-attributes
IKEv1 pre-shared-key *.
remote control-IKEv2 pre-shared-key authentication *.SH run | I have political ikev1
ikev1 160 crypto policy
preshared authentication
aes-256 encryption
Group 5
life 86400SH run | I Dynamics
NAT interface dynamic obj - 0.0.0.0 source (indoor, outdoor)
NAT source auto after (indoor, outdoor) dynamic one interfaceNOTE:
To from 5512 at 5505-, we can ping a host on the remote network of ASA local# ping inside the 192.168.54.20
Type to abort escape sequence.
Send 5, echoes ICMP 100 bytes to 192.168.54.20, wait time is 2 seconds:
!!!!!
Success rate is 100 per cent (5/5), round-trip min/avg/max = 30/32/40 msDetermination of 192.168.1.79 - local host route to 192.168.54.20 - remote host - derivation tunnel?
The IPSEC tunnel check - seems OK?
SH crypto ipsec his
Interface: outside
Tag crypto map: outside_map, seq num: 2, local addr: XX.XXX.XXX.XXXoutside_cryptomap_ibfw to access ip 192.168.1.0 scope list allow 255.255.255.0 192.168.54.0 255.255.255.0
local ident (addr, mask, prot, port): (192.168.1.0/255.255.255.0/0/0)
Remote ident (addr, mask, prot, port): (192.168.54.0/255.255.255.0/0/0)
current_peer: XX. XX.XXX.XXX#pkts program: 4609, #pkts encrypt: 4609, #pkts digest: 4609
#pkts decaps: 3851, #pkts decrypt: 3851, #pkts check: 3851
compressed #pkts: 0, unzipped #pkts: 0
#pkts uncompressed: 4609, model of #pkts failed: 0, #pkts Dang failed: 0
success #frag before: 0, failures before #frag: 0, #fragments created: 0
Sent #PMTUs: 0, #PMTUs rcvd: 0, reassembly: 20th century / of frgs #decapsulated: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid errors ICMP rcvd: 0, #Invalid ICMP errors received: 0
#send errors: 0, #recv errors: 0local crypto endpt. : XX.XXX.XXX.XXX/0, remote Start crypto. : XX. XX.XXX.XXX/0
Path mtu 1500, ipsec 74 (44) generals, media, mtu 1500
PMTU time remaining: 0, political of DF: copy / df
Validation of ICMP error: disabled, TFC packets: disabled
current outbound SPI: CDC99C9F
current inbound SPI: 06821CBBSAS of the esp on arrival:
SPI: 0x06821CBB (109190331)
transform: aes-256-esp esp-sha-hmac no compression
running parameters = {L2L, Tunnel, group 5 PFS, IKEv1}
slot: 0, id_conn: 339968, crypto-card: outside_map
calendar of his: service life remaining (KB/s) key: (3914789/25743)
Size IV: 16 bytes
support for replay detection: Y
Anti-replay bitmap:
0xFFFFFFFF to 0xFFFFFFFF
outgoing esp sas:
SPI: 0xCDC99C9F (3452542111)
transform: aes-256-esp esp-sha-hmac no compression
running parameters = {L2L, Tunnel, group 5 PFS, IKEv1}
slot: 0, id_conn: 339968, crypto-card: outside_map
calendar of his: service life remaining (KB/s) key: (3913553/25743)
Size IV: 16 bytes
support for replay detection: Y
Anti-replay bitmap:
0x00000000 0x00000001--> The local ASA 5512 - where we have questions - tried Packet Tracer... seems we receive requests/responses...
SH cap CAP
34 packets captured
1: 16:41:08.120477 192.168.1.79 > 192.168.54.20: icmp: echo request
2: 16:41:08.278138 192.168.54.20 > 192.168.1.79: icmp: echo request
3: 16:41:08.278427 192.168.1.79 > 192.168.54.20: icmp: echo reply
4: 16:41:09.291992 192.168.54.20 > 192.168.1.79: icmp: echo request
5: 16:41:09.292282 192.168.1.79 > 192.168.54.20: icmp: echo reply--> On the ASA 5505 distance - we can ping through the 5512 to the local host (192.168.1.79)
SH cap A2
42 packets captured
1: 16:56:16.136559 802. 1 q vlan P0 192.168.54.20 #1 > 192.168.1.79: icmp: echo request
2: 16:56:16.168860 802. 1 q vlan P0 192.168.1.79 #1 > 192.168.54.20: icmp: echo reply
3: 16:56:17.140434 802. 1 q vlan P0 192.168.54.20 #1 > 192.168.1.79: icmp: echo request
4: 16:56:17.171652 802. 1 q vlan P0 192.168.1.79 #1 > 192.168.54.20: icmp: echo reply
5: 16:56:18.154426 802. 1 q vlan P0 192.168.54.20 #1 > 192.168.1.79: icmp: echo request
6: 16:56:18.186178 802. 1 q vlan P0 192.168.1.79 #1 > 192.168.54.20: icmp: echo reply
7: 16:56:19.168417 802. 1 q vlan P0 192.168.54.20 #1 > 192.168.1.79: icmp: echo request--> Package trace on 5512 does no problem... but we cannot ping from host to host?
entry Packet-trace within the icmp 192.168.1.79 8 0 detailed 192.168.54.20
Phase: 4
Type: CONN-SETTINGS
Subtype:
Result: ALLOW
Config:
class-map default class
match any
Policy-map global_policy
class class by default
Decrement-ttl connection set
global service-policy global_policy
Additional information:
Direct flow from returns search rule:
ID = 0x7fffa2d0ba90, priority = 7, area = conn-set, deny = false
hits = 4417526, user_data = 0x7fffa2d09040, cs_id = 0 x 0, use_real_addr, flags = 0 x 0 = 0 protocol
IP/ID=0.0.0.0 SRC, mask = 0.0.0.0, port = 0, = 0 tag
IP/ID=0.0.0.0 DST, mask is 0.0.0.0, port = 0, tag = 0, dscp = 0 x 0
input_ifc = output_ifc = any to inside,Phase: 5
Type: NAT
Subtype:
Result: ALLOW
Config:
NAT interface dynamic obj - 0.0.0.0 source (indoor, outdoor)
Additional information:
Definition of dynamic 192.168.1.79/0 to XX.XXX.XXX.XXX/43904
Direct flow from returns search rule:
ID = 0x7fffa222d130, priority = 6, area = nat, deny = false
hits = 4341877, user_data = 0x7fffa222b970, cs_id = 0 x 0, flags = 0 x 0 = 0 protocol
IP/ID=0.0.0.0 SRC, mask = 0.0.0.0, port = 0, = 0 tag
IP/ID=0.0.0.0 DST, mask is 0.0.0.0, port = 0, tag = 0, dscp = 0 x 0
input_ifc = inside, outside = output_ifc...
Phase: 14
Type: CREATING STREAMS
Subtype:
Result: ALLOW
Config:
Additional information:
New workflow created with the 7422689 id, package sent to the next module
Information module for forward flow...
snp_fp_tracer_drop
snp_fp_inspect_ip_options
snp_fp_inspect_icmp
snp_fp_translate
snp_fp_adjacency
snp_fp_fragment
snp_ifc_statInformation for reverse flow...
snp_fp_tracer_drop
snp_fp_inspect_ip_options
snp_fp_translate
snp_fp_inspect_icmp
snp_fp_adjacency
snp_fp_fragment
snp_ifc_statResult:
input interface: inside
entry status: to the top
entry-line-status: to the top
output interface: outside
the status of the output: to the top
output-line-status: to the top
Action: allow--> On remote ASA 5505 - Packet track is good and we can ping remote host very well... dunno why he "of Nations United-NAT?
Destination - initiator:
entry Packet-trace within the icmp 192.168.54.20 8 0 detailed 192.168.1.79
...
Phase: 4
Type: UN - NAT
Subtype: static
Result: ALLOW
Config:
NAT (inside, outside) static source NETWORK_OBJ_192.168.54.0_24 NETWORK_OBJ_192.168.54.0_24 NETWORK_OBJ_192.168.1.0_24 NETWORK_OBJ_192.168.1.0_24 non-proxy-arp-search of route static destination
Additional information:
NAT divert on exit to the outside interface
Untranslate 192.168.1.79/0 to 192.168.1.79/0
...Summary:
We "don't" ping from a host (192,168.1.79) on 5512 - within the network of the 5505 - inside the network host (192.168.54.20).
But we can ping the 5505 - inside the network host (192.168.54.20) 5512 - inside the network host (192.168.1.79).Please let us know what other details we can provide to help solve, thanks for any help in advance.
-SP
Well, I think it is a NAT ordering the issue.
Basically as static and this NAT rule-
NAT interface dynamic obj - 0.0.0.0 source (indoor, outdoor)
are both in article 1 and in this article, it is done on the order of the rules so it does match the dynamic NAT rule rather than static because that seems to be higher in the order.
To check just run a 'sh nat"and this will show you what order everthing is in.
The ASA is working its way through the sections.
You also have this-
NAT source auto after (indoor, outdoor) dynamic one interface
which does the same thing as first statement but is in section 3, it is never used.
If you do one of two things-
(1) configure the static NAT statement is above the dynamic NAT in section 1 that is to say. You can specify the command line
or
(2) remove the dynamic NAT of section 1 and then your ASA will use the entry in section 3.
There is a very good document on this site for NAT and it is recommended to use section 3 for your general purpose NAT dynamic due precisely these questions.
It is interesting on your ASA 5505 you duplicated your instructions of dynamic NAT again but this time with article 2 and the instructions in section 3 that is why your static NAT works because he's put in correspondence before all your dynamic rules.
The only thing I'm not sure of is you remove the dynamic NAT statement in article 1 and rely on the statement in section 3, if she tears the current connections (sorry can't remember).
Then you can simply try to rearrange so your static NAT is above it just to see if it works.
Just in case you want to see the document here is the link-
Jon
-
Problem with Tunnel VPN L2L between 2 ASA´s
Hi guys,.
I have some problems with my VPN Site to site tunnel between 2 ASA (5520/5505).
I watched a lot of videos on youtube, but I can't find out why the tunnel does not...
Both devices can ping eachothers WAN IP address (outside interfaces), but I don't see any traffic between the 2 sites. It seems that the tunnel is not open to everyone. When i PING from the local to the Remote LAN (which should be an interesting traffic for the tunnel...), the its IKEv1 remains empty...
Am I missing something? I can't understand it more why same phase 1 is not engaged.
You NAT won't. In your config file traffic is NATted initially and then does not match any more crypto ACL. You must move the rule dynamic NAT/PAT until the end of the table on two ASAs NAT:
no nat (INSIDE,OUTSIDE) source dynamic any interface nat (INSIDE,OUTSIDE) after-auto source dynamic any interface
-
Site to Site between ASA VPN connection and router 2800
I'm trying to get a L2L VPN working between a ASA code 8.4 and a 2800 on 12.4.
I first saw the following errors in the debug logs on the side of the ASA:
Error message % PIX | ASA-6-713219: KEY-GAIN message queues to deal with when
ITS P1 is complete.I see the following on the end of 2800:
ISAKMP: (0): treatment charge useful vendor id
ISAKMP: (0): provider ID seems the unit/DPD but major incompatibility of 157
ISAKMP: (0): provider ID is NAT - T v3
ISAKMP: (0): treatment charge useful vendor id
ISAKMP: (0): provider ID seems the unit/DPD but major incompatibility of 69
ISAKMP (0): provider ID is NAT - T RFC 3947
ISAKMP: (0): treatment charge useful vendor id
ISAKMP: (0): treatment of frag vendor id IKE payload
ISAKMP: (0): IKE Fragmentation support not enabled
ISAKMP: (0): entry = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
ISAKMP: (0): former State = new State IKE_R_MM1 = IKE_R_MM1ISAKMP: (0): built NAT - T of the seller-rfc3947 ID
ISAKMP: (0): send package to x.x.x.x my_port 500 peer_po0 (R) MM_SA_SETUP
ISAKMP: (0): sending a packet IPv4 IKE.
ISAKMP: (0): entry = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
ISAKMP: (0): former State = new State IKE_R_MM1 = IKE_R_MM2ISAKMP (0): packet received from x.x.x.x dport 500 sports global (R)
MM_SA_SETUP
ISAKMP: (0): entry = IKE_MESG_FROM_PEER, IKE_MM_EXCH
ISAKMP: (0): former State = new State IKE_R_MM2 = IKE_R_MM3ISAKMP: (0): processing KE payload. Message ID = 0
ISAKMP: (0): processing NONCE payload. Message ID = 0
ISAKMP: (0): found peer pre-shared key x.x.x.x corresponding
ISAKMP: (2345): treatment charge useful vendor id
ISAKMP: (2345): provider ID is the unit
ISAKMP: (2345): treatment charge useful vendor id
ISAKMP: (2345): provider ID seems the unit/DPD but major incompatibility of 54
ISAKMP: (2345): provider ID is XAUTH
ISAKMP: (2345): treatment charge useful vendor id
ISAKMP: (2345): addressing another box of IOS!
ISAKMP: (2345): treatment charge useful vendor id
ISAKMP: (2345): vendor ID seems the unit/DPD but hash mismatch
ISAKMP: receives the payload type 20
ISAKMP (2345): sound not hash no match - this node outside NAT
ISAKMP: receives the payload type 20
ISAKMP (2345): no NAT found for oneself or peer
ISAKMP: (2345): entry = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
ISAKMP: (2345): former State = new State IKE_R_MM3 = IKE_R_MM3ISAKMP: (2345): sending package x.x.x.x my_port Exchange 500 500 (R)
MM_KEY_EXCH
----------
This is part of the configuration of the ASA:
network of the ABCD object
10.20.30.0 subnet 255.255.255.0
network of the ABCD-Net object
172.16.10.0 subnet 255.255.255.0
cry-map-77-ip object-group XXXX object abc-site_Network allowed extended access list
access list abc-site extended permitted ip object-group XXXX object abc-site_Network
ip access list of abc-site allowed extended object abc-site_Network object-group XXXX-60
NAT (any, any) static source 20 XXXX XXXX-20 destination static abc-site_Network abc-site_Network
NAT (any, any) static source 20 XXXX XXXX-20 destination static abc-site_Network abc-site_Network
XXXX-20
object-group network XXXX-20
ABCD-Net network object
object-abcd-Int-Net Group
XXXX_127
object-group network XXXX-20
ABCD-Net network object
object-abcd-Int-Net Group
ip access list of abc-site allowed extended object abc-site_Network object-group XXXX-60
Crypto card off-map-44 11 match address cry-map-77
card crypto out-map-44 11 counterpart set 62.73.52.xxx
card crypto out-map-44 11 set ikev1 transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA MD5-ESP-3DES ESP-DES-SHA ESP-DES-MD5cry-map-77-ip object-group XXXX object abc-site_Network allowed extended access list
Crypto card off-map-44 11 match address cry-map-77
card crypto out-map-44 11 counterpart set 62.73.52.xxx
card crypto out-map-44 11 set ikev1 transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA MD5-ESP-3DES ESP-DES-SHA ESP-DES-MD5card crypto out-map-44 11 set transform-set ESP-3DES-SHA ikev1
object-group network XXXX
ABCD-Net network object
object-abcd-Int-Net Group------------------------
Here is a part of the 2800:
!
crypto ISAKMP policy 1
BA 3des
preshared authentication
Group 2
ISAKMP crypto key r2374923 address 72.15.21.xxx
!
!
Crypto ipsec transform-set esp-SHA-ESP-3DES-3des esp-sha-hmac
!
card crypto cry-map-1 1 ipsec-isakmp
the value of 72.15.21.xxx peer
game of transformation-ESP-3DES-SHA
match address VPN
!
type of class-card inspect match class-map-vpn
game group-access 100
type of class-card inspect cm-inspect-1 correspondence
group-access name inside-out game
type of class-card inspect correspondence cm-inspect-2
match the name of group-access outside
!
!
type of policy-card inspect policy-map-inspect
class type inspect cm-inspect-1
inspect
class class by default
drop
type of policy-card inspect policy-map-inspect-2
class type inspect class-map-vpn
inspect
class type inspect cm-inspect-2
class class by default
drop
!!
interface FastEthernet0
IP address 74.25.89.xxx 255.255.255.252
NAT outside IP
IP virtual-reassembly
security of the outside Member area
automatic duplex
automatic speed
crypto cry-card-1 card
!
interface FastEthernet1
no ip address
Shutdown
automatic duplex
automatic speed
!
IP nat inside source overload map route route-map-1 interface FastEthernet0
!
IP access-list extended inside-out
IP 172.16.10.0 allow 0.0.0.255 any
IP nat - acl extended access list
deny ip 192.168.0.0 0.0.255.255 172.16.10.0 0.0.0.255
deny ip 10.200.0.0 0.0.255.255 172.16.10.0 0.0.0.255
deny ip 192.168.0.0 0.0.255.255 172.16.10.0 0.0.0.255
deny ip 0.0.255.255 28.20.14.xxx.0.0 172.16.10.0 0.0.0.255
refuse the 10.10.10.0 ip 0.0.0.255 172.16.10.0 0.0.0.255
refuse the 172.16.10.0 ip 0.0.0.255 192.168.0.0 0.0.255.255
refuse the 172.16.10.0 ip 0.0.0.255 10.200.0.0 0.0.255.255
refuse the 172.16.10.0 ip 0.0.0.255 192.168.0.0 0.0.255.255
refuse the 172.16.10.0 ip 0.0.0.255 28.20.14.xxx.0.0 0.0.255.255
refuse the 172.16.10.0 ip 0.0.0.255 10.10.10.0 0.0.0.255
allow an ip
outside extended IP access list
allow an ip
list of IP - VPN access scope
IP 172.16.10.0 allow 0.0.0.255 192.168.0.0 0.0.255.255
IP 172.16.10.0 allow 0.0.0.255 10.200.0.0 0.0.255.255
IP 172.16.10.0 allow 0.0.0.255 192.168.0.0 0.0.255.255
IP 172.16.10.0 allow 0.0.0.255 28.20.14.xxx.0.0 0.0.255.255
IP 172.16.10.0 allow 0.0.0.255 10.10.10.0 0.0.0.255
IP 192.168.0.0 allow 0.0.255.255 172.16.10.0 0.0.0.255
IP 10.200.0.0 allow 0.0.255.255 172.16.10.0 0.0.0.255
IP 192.168.0.0 allow 0.0.255.255 172.16.10.0 0.0.0.255
28.20.14.xxx.0.0 0.0.255.255 ip permit 172.16.10.0 0.0.0.255
ip licensing 10.10.10.0 0.0.0.255 172.16.10.0 0.0.0.255access-list 23 allow 192.168.0.0 0.0.255.255
access-list 23 allow 10.200.0.0 0.0.255.255
access-list 23 allow 172.16.10.0 0.0.0.255
access-list 123 note category class-map-LCA-4 = 0
access-list 123 allow ip 192.168.0.0 0.0.255.255 172.16.10.0 0.0.0.255
access-list 123 allow ip 10.200.0.0 0.0.255.255 172.16.10.0 0.0.0.255
access-list 123 allow ip 192.168.0.0 0.0.255.255 172.16.10.0 0.0.0.255
access-list 123 allow ip 0.0.255.255 28.20.14.xxx.0.0 172.16.10.0 0.0.0.255
access-list 123 allow ip 10.10.10.0 0.0.0.255 172.16.10.0 0.0.0.255
access-list 123 allow ip 172.16.10.0 0.0.0.255 192.168.0.0 0.0.255.255
access-list 123 allow ip 172.16.10.0 0.0.0.255 10.200.0.0 0.0.255.255
access-list 123 allow ip 172.16.10.0 0.0.0.255 192.168.0.0 0.0.255.255
access-list 123 allow ip 172.16.10.0 0.0.0.255 28.20.14.xxx.0.0 0.0.255.255
access-list 123 allow ip 172.16.10.0 0.0.0.255 10.10.10.0 0.0.0.255
!
!
!!
route-map-1 allowed route map 1
match the IP nat - acl
!Hello
I quickly browsed your config and I could notice is
your game of transformation (iskamp) on SAA and router are not the same, try to configure the same on both sides.
in the statement of the ASA NAT you gave (any, any) try to give the name of the interface instead of a whole.
-
Several outside networks ASA - 1 outside the Interface
Example scenario:
A 20.0.0.0 (primary) site
Site B 30.0.0.0 (primary)
Greetings,
I don't see being a problem from a point of view routing with 2 routers on each site and advertisements via BGP. We will announce the two networks at each site. However, mainly single site will get 20.0.0.0 traffic and site B will get 30.0.0.0 traffic. No problem with the NAT and so on.
What I do not know how to deal with right now is if site B fails and the site began to receive the 30.0.0.0 traffic. There is just a single link between the router and firewall, site with the 20.x.x.x network. Any recommendations how A site can receive 30.0.0.0 transparent if site B goes bankrupt? (from a Point of view of ASA/NAT)
Thank you
Chris
It is reasonable to assume that your ASA has a road the 30.0.0.0 network she is inside the interface?
If so
static (inside, outside) 30.0.0.0 30.0.0.0 netmask 255.0.0.0
as long as the traffic to 30.0.0.0 is forwarded to the external interface of the firewall site has it can then accept this traffic and will forward it on internally.
If I understand you, let me know.
Jon
-
On the Question of VPN S2S source NAT
Currently we have a number of implementation of VPN with various clients. We are NAT'ing range them at a 24 in our network to keep simple routing, but we seek to NAT Source our resources due to security problems. It is an example of a current virtual private network that we have configured:
outside_map crypto card 5 corresponds to the address SAMPLE_cryptomap
outside_map 5 peer set 99.99.99.99 crypto card
card crypto outside_map 5 set ikev1 transform-set ESP-3DES-MD5 SHA-ESP-3DES
card crypto outside_map 5 the value reverse-road
SAMPLE_cryptomap list extended access permitted ip object-group APP_CLIENT_Hosts-group of objects CLIENT_Hosts
NAT (inside, outside) static source APP_CLIENT_Hosts APP_CLIENT_Hosts CLIENT_Host_1_NAT CLIENT_Host_1 non-proxy-arp-search of route static destination
NAT (inside, outside) static source APP_CLIENT_Hosts APP_CLIENT_Hosts CLIENT_Host_2_NAT CLIENT_Host_2 non-proxy-arp-search of route static destination
NAT (inside, outside) static source APP_CLIENT_Hosts APP_CLIENT_Hosts CLIENT_Host_3_NAT CLIENT_Host_3 non-proxy-arp-search of route static destination
the APP_CLIENT_Hosts object-group network
network-object, object SITE1_APP_JCAPS_Dev_VIP
network-object, object SITE1_APP_JCAPS_Prod_VIP
network-object, object SITE2_APP_JCAPS_Dev_Host
network-object, object SITE2_APP_JCAPS_Prod_VIP
network-object, object SITE1_APP_PACS_Primary
network of the SITE1_APP_JCAPS_Dev_VIP object
Home 10.200.125.32
network of the SITE1_APP_JCAPS_Prod_VIP object
Home 10.200.120.32
network of the SITE2_APP_JCAPS_Dev_Host object
Home 10.30.15.30
network of the SITE2_APP_JCAPS_Prod_VIP object
Home 10.30.10.32
network of the SITE1_APP_PACS_Primary object
Home 10.200.10.75
network of the CLIENT_Host_1 object
host of the object-Network 192.168.15.100
network of the CLIENT_Host_2 object
host of the object-Network 192.168.15.130
network of the CLIENT_Host_3 object
host of the object-Network 192.168.15.15
network of the CLIENT_Host_1_NAT object
host of the object-Network 10.200.192.31
network of the CLIENT_Host_2_NAT object
host of the object-Network 10.200.192.32
network of the CLIENT_Host_3_NAT object
host of the object-Network 10.200.192.33
My question revolves around the Source NAT configuration. If I understand correctly, I have to configure 3 statements of NAT per NAT Source since there are three different destinations that are NAT' ed. I think I would need to add this:
network of the SITE1_APP_JCAPS_Dev_VIP_NAT object
Home 88.88.88.81
network of the SITE1_APP_JCAPS_Prod_VIP_NAT object
Home 88.88.88.82
network of the SITE2_APP_JCAPS_Dev_Host_NAT object
Home 88.88.88.83
network of the SITE2_APP_JCAPS_Prod_VIP_NAT object
Home 88.88.88.84
network of the SITE1_APP_PACS_Primary_NAT object
Home 88.88.88.85
NAT (inside, outside) static source SITE1_APP_JCAPS_Dev_VIP SITE1_APP_JCAPS_Dev_VIP_NAT CLIENT_Host_1_NAT CLIENT_Host_1 non-proxy-arp-search of route static destination
NAT (inside, outside) static source SITE1_APP_JCAPS_Dev_VIP SITE1_APP_JCAPS_Dev_VIP_NAT CLIENT_Host_2_NAT CLIENT_Host_2 non-proxy-arp-search of route static destination
NAT (inside, outside) static source SITE1_APP_JCAPS_Dev_VIP SITE1_APP_JCAPS_Dev_VIP_NAT CLIENT_Host_3_NAT CLIENT_Host_3 non-proxy-arp-search of route static destination
NAT (inside, outside) static source SITE1_APP_JCAPS_Prod_VIP SITE1_APP_JCAPS_Prod_VIP_NAT CLIENT_Host_1_NAT CLIENT_Host_1 non-proxy-arp-search of route static destination
NAT (inside, outside) static source SITE1_APP_JCAPS_Prod_VIP SITE1_APP_JCAPS_Prod_VIP_NAT CLIENT_Host_2_NAT CLIENT_Host_2 non-proxy-arp-search of route static destination
NAT (inside, outside) static source SITE1_APP_JCAPS_Prod_VIP SITE1_APP_JCAPS_Prod_VIP_NAT CLIENT_Host_3_NAT CLIENT_Host_3 non-proxy-arp-search of route static destination
NAT (inside, outside) static source SITE2_APP_JCAPS_Dev_Host SITE2_APP_JCAPS_Dev_Host_NAT CLIENT_Host_1_NAT CLIENT_Host_1 non-proxy-arp-search of route static destination
NAT (inside, outside) static source SITE2_APP_JCAPS_Dev_Host SITE2_APP_JCAPS_Dev_Host_NAT CLIENT_Host_2_NAT CLIENT_Host_2 non-proxy-arp-search of route static destination
NAT (inside, outside) static source SITE2_APP_JCAPS_Dev_Host SITE2_APP_JCAPS_Dev_Host_NAT CLIENT_Host_3_NAT CLIENT_Host_3 non-proxy-arp-search of route static destination
NAT (inside, outside) static source SITE2_APP_JCAPS_Prod_VIP SITE2_APP_JCAPS_Prod_VIP_NAT CLIENT_Host_1_NAT CLIENT_Host_1 non-proxy-arp-search of route static destination
NAT (inside, outside) static source SITE2_APP_JCAPS_Prod_VIP SITE2_APP_JCAPS_Prod_VIP_NAT CLIENT_Host_2_NAT CLIENT_Host_2 non-proxy-arp-search of route static destination
NAT (inside, outside) static source SITE2_APP_JCAPS_Prod_VIP SITE2_APP_JCAPS_Prod_VIP_NAT CLIENT_Host_3_NAT CLIENT_Host_3 non-proxy-arp-search of route static destination
NAT (inside, outside) static source SITE1_APP_PACS_Primary SITE1_APP_PACS_Primary_NAT CLIENT_Host_1_NAT CLIENT_Host_1 non-proxy-arp-search of route static destination
NAT (inside, outside) static source SITE1_APP_PACS_Primary SITE1_APP_PACS_Primary_NAT CLIENT_Host_2_NAT CLIENT_Host_2 non-proxy-arp-search of route static destination
NAT (inside, outside) static source SITE1_APP_PACS_Primary SITE1_APP_PACS_Primary_NAT CLIENT_Host_3_NAT CLIENT_Host_3 non-proxy-arp-search of route static destination
Is that correct, or is at - it an easier way to do this without having to add all statements of NAT? Moreover, any change would be to do on the access list?
Hello
To my knowledge you should not create several new instructions from NAT. You should be well just create a new Group 'object' for new addresses your source address NAT.
To better explain, take a look at your current ' object-group ' that defines your source addresses
the APP_CLIENT_Hosts object-group network
network-object, object SITE1_APP_JCAPS_Dev_VIP
network-object, object SITE1_APP_JCAPS_Prod_VIP
network-object, object SITE2_APP_JCAPS_Dev_Host
network-object, object SITE2_APP_JCAPS_Prod_VIP
network-object, object SITE1_APP_PACS_Primary
Now you can do this sets up a "object-group" that contains a NAT IP address for each of the IP addresses inside the ' object-group ' and 'object' used above. The IMPORTANT thing is that the ' object-group ' that contains the NAT IP addresses is in the SAME ORDER as the actual source addresses.
I mean, this is the first IP address is in most object - group ' will correspond to the first IP address in the newly created "object-group" for the IP NAT addresses.
As above, you can simply have the same "nat" configurations 3 as before but you change/add in the newly created "object-group"
For example, you might do the following
network of the SITE1_APP_JCAPS_Dev_VIP_NAT object
Home 88.88.88.81
network of the SITE1_APP_JCAPS_Prod_VIP_NAT object
Home 88.88.88.82
network of the SITE2_APP_JCAPS_Dev_Host_NAT object
Home 88.88.88.83
network of the SITE2_APP_JCAPS_Prod_VIP_NAT object
Home 88.88.88.84
network of the SITE1_APP_PACS_Primary_NAT object
Home 88.88.88.85
the APP_CLIENT_Hosts_NAT object-group network
network-object, object SITE1_APP_JCAPS_Dev_VIP_NAT
network-object, object SITE1_APP_JCAPS_Prod_VIP_NAT
network-object, object SITE2_APP_JCAPS_Dev_Host_NAT
network-object, object SITE2_APP_JCAPS_Prod_VIP_NAT
network-object, object SITE1_APP_PACS_Primary_NAT
Then you add the following configurations of "nat"
NAT (inside, outside) 1 static source APP_CLIENT_Hosts APP_CLIENT_Hosts_NAT CLIENT_Host_1_NAT CLIENT_Host_1 non-proxy-arp-search of route static destination
Static NAT APP_CLIENT_Hosts APP_CLIENT_Hosts_NAT static destination CLIENT_Host_2_NAT CLIENT_Host_2 non-proxy-arp-search of source route 2 (inside, outside)
NAT 3 (indoor, outdoor) static source APP_CLIENT_Hosts APP_CLIENT_Hosts_NAT CLIENT_Host_3_NAT CLIENT_Host_3 non-proxy-arp-search of route static destination
Note line numbers, we added the above commands. This allows them to enter the upper part of the ASAs NAT rules, and therefore, they will become active immediately. Without line numbers that they will only be used after when you remove the old lines.
Then you can remove the "old"
no nat source (indoor, outdoor) public static APP_CLIENT_Hosts APP_CLIENT_Hosts CLIENT_Host_1_NAT CLIENT_Host_1 non-proxy-arp-search of route static destination
no nat source (indoor, outdoor) public static APP_CLIENT_Hosts APP_CLIENT_Hosts CLIENT_Host_2_NAT CLIENT_Host_2 non-proxy-arp-search of route static destination
no nat source (indoor, outdoor) public static APP_CLIENT_Hosts APP_CLIENT_Hosts CLIENT_Host_3_NAT CLIENT_Host_3 non-proxy-arp-search of route static destination
This should leave you with 3 configurations "nat" who made the NAT source addresses and destination.
Naturally while you perform this change you will also have to change the ACL Crypto to match the new source NAT. This is because as all NAT is done before any VPN on the ASA. So the destination addresses are Nations United for before VPN and source addresses are translated before VPN.
If you do not want to make the changes without affecting the connections too so I suggest
- Add rules to the ACL Crypto for new addresses (NAT) source. Of course, this must be done on both sides of the VPN L2L. You would still be leaving the original configurations to the Crypto ACL does not not the functioning of the L2L VPN.
- Add new configurations of "nat" above without the line numbers I mentioned who mean you that they wont be used until you remove the "old".
- When you are ready to be migrated to use the new IP addresses, simply remove the original "nat" configurations and the ASA will start the corresponding traffic for new "nat" configurations. Provided of course that there is no other "nat" configuration before the nine that could mess things up. This should be verified by the person making the changes.
Of course if you can afford a small cut when then changing the order in which you do things should not matter that much. In my work, that connections are usually not that critical that you can't make these changes almost at any point as it is a matter of minutes what it takes to make changes.
Hope this made sense and helped
Remember to mark a reply as the answer if it answered your question.
Feel free to ask more if necessary.
-Jouni
-
Hello world
I don't know that this subject has been beaten to death already on these forums. Nevertheless, I have yet to find the exact solution, I need. I have three machines, two routers and an ASA. One of the routers sits behind the ASA and I have a GRE VTI configuration between two routers with ASA NATting, one of the routers to a public IP address. I can guarantee the tunnel mode IPsec transport, but as soon as I pass in tunnel mode, the communication fails even if the SA is established.
Please see the configuration below and tell me what I am missing please. I changed the IP addresses for security.
The following configuration works when transform-set is set to the mode of transport
Note: The Router 2 is sitting behind the ASA and is coordinated to the public IP 200.1.1.2
Router 1:
Crypto ipsec transform-set SEC esp - aes 256 esp-md5-hmac
tunnel mode
!
Crypto ipsec IPSEC profile
transformation-SEC game
!
!
interface tunnels2
IP 172.16.1.1 255.255.255.252
tunnel source 200.1.1.1
tunnel destination 200.1.1.2
Ipsec IPSEC protection tunnel profile
!
SECURITYKEY address 200.1.1.2 isakmp encryption key
!
crypto ISAKMP policy 1
BA aes 256
md5 hash
preshared authentication
Group 2
ASA:
public static 200.1.1.2 (indoor, outdoor) 10.1.1.1 netmask 255.255.255.255
Router 2:
interface Tunnel121
address 172.16.1.2 IP 255.255.255.252
IP nat inside
IP virtual-reassembly
tunnel source 10.1.1.1
tunnel destination 200.1.1.1
Ipsec IPSEC protection tunnel profile
!
Crypto ipsec transform-set SEC esp - aes 256 esp-md5-hmac
tunnel mode
!
Crypto ipsec IPSEC profile
transformation-SEC game
!
SECURITYKEY address 200.1.1.1 isakmp encryption key
!
crypto ISAKMP policy 2
BA aes 256
md5 hash
preshared authentication
Group 2
There is no access-lists on the SAA except to allow a whole ICMP
I am very grateful for any guidance you can provide in advance guys.
Hello
MTU, and the overhead was in this case.
You changed encapsulating ipv4 instead of LIKING - which have less overhead (no GRE inside). This is why it started working.
If you want to continue using GRE you decrease the MTU as described.
---
Michal
-
Here is my config complete.
Here are a few notes
IP, obtained from the VPN 10.250.128.X
LAN IP 192.168.0.0/24
My atm VPN works #1 for those who don't
What I want to do is Nat my VPN for this
Example I want to access the computer 192.168.0.2 on the LAN of the company
I want to hit the PC (which is connected to the VPN) 192.168.200.2 and Cisco will convert 192.168.200.2 to 192.168.0.2 to be able to access my PC at work
Of course, I think about being able to do the other side also. (192.168.0.2 to 192.168.200.2 to be able to send the package back (not sure on this)
Can guys, help me, it's the ATM out of my knowledge and I
ASA Version 8.2 (1)
!
Terminal width 250
hostname hostname
turn on d0/xPtlKePBzdYTe of encrypted password
2KFQnbNIdI.2KYOU encrypted passwd
names of
!
interface Vlan1
nameif inside
security-level 100
IP 192.168.0.254 255.255.255.0
!
interface Vlan2
nameif outside
security-level 0
IP 10.0.128.1 255.255.255.0
!
interface Ethernet0/0
switchport access vlan 2
10 speed
full duplex
!
interface Ethernet0/1
10 speed
full duplex
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
!
interface Ethernet0/7
!
boot system Disk0: / asa821 - k8.bin
passive FTP mode
grp_outside_in tcp service object-group
Description Ports require for internal transfer
EQ smtp port object
EQ port ssh object
access list inside-out extended ip allowed any one
access list inside-out extended permit icmp any one
permit no_nat to access extended list ip 192.168.0.0 255.255.0.0 10.250.128.0 255.255.255.0
list access tunnel extended split ip 192.168.0.0 allow 255.255.20.0 10.250.128.0 255.255.255.0
access-list extended 100 permit ip 10.250.128.0 255.255.255.0 192.168.0.0 255.255.255.0
access-list extended 100 permit icmp 10.250.128.0 255.255.255.0 192.168.0.0 255.255.255.0
access list 101 scope ip allow a whole
access-list 101 extended allow icmp a whole
pager lines 34
Enable logging
timestamp of the record
debug logging in buffered memory
recording of debug trap
asdm of logging of information
Within 1500 MTU
Outside 1500 MTU
IP local pool mobilepool 10.250.128.100 - 10.250.128.130 mask 255.255.255.0
ICMP unreachable rate-limit 1 burst-size 1
ASDM image disk0: / asdm - 621.bin
don't allow no asdm history
ARP timeout 14400
Global 1 interface (outside)
NAT (inside) 0-list of access no_nat
NAT (inside) 1 0.0.0.0 0.0.0.0
NAT (outside) 1 0.0.0.0 0.0.0.0
Route outside 0.0.0.0 0.0.0.0 10.0.128.2 1
Timeout xlate 03:00
Timeout conn 01:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
Sunrpc timeout 0:10:00 h323 0:05:00 h225 mgcp from 01:00 0:05:00 mgcp-pat 0:05:00
Sip timeout 0:30:00 sip_media 0:02:00 prompt Protocol sip-0: 03:00 sip - disconnect 0:02:00
Timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
dynamic-access-policy-registration DfltAccessPolicy
the ssh LOCAL console AAA authentication
Enable http server
http 192.168.1.0 255.255.255.0 inside
http 192.168.0.0 255.255.255.0 inside
No snmp server location
No snmp Server contact
Server enable SNMP traps snmp authentication linkup, linkdown cold start
Crypto ipsec transform-set esp-3des esp-md5-hmac floating
life crypto ipsec security association seconds 28800
Crypto ipsec kilobytes of life - safety 4608000 association
Crypto-map dynamic dyn1 1 set transform-set floating
Crypto-map dynamic dyn1 1jeu reverse-road
mobilemap 1 card crypto ipsec-isakmp dynamic dyn1
mobilemap interface card crypto outside
crypto ISAKMP allow outside
crypto ISAKMP policy 1
preshared authentication
3des encryption
sha hash
Group 2
life 86400
Telnet timeout 5
SSH 192.168.0.0 255.255.255.0 inside
SSH 10.0.128.0 255.255.255.0 inside
SSH timeout 5
SSH version 2
Console timeout 0
dhcpd outside auto_config
!
a basic threat threat detection
Statistics-list of access threat detection
no statistical threat detection tcp-interception
WebVPN
internal vpn group policy
attributes of vpn group policy
VPN - 50 simultaneous connections
VPN-idle-timeout 2000
VPN-session-timeout 2000
internal mobile_policy group policy
attributes of the strategy of group mobile_policy
Split-tunnel-policy tunnelspecified
Split-tunnel-network-list value
admin N2TJh8TeuGc7EOVu encrypted privilege 15 password username
user1 gLGaPhl70GqS8DhN encrypted password username
password encrypted user user2 Y7.fXmPk3FvKUGOO name
type tunnel-group mobilegroup remote access
tunnel-group mobilegroup General-attributes
address mobilepool pool
Group Policy - by default-mobile_policy
mobilegroup group of tunnel ipsec-attributes
pre-shared-key *.
!
Global class-card class
match default-inspection-traffic
inspection of the class-map
class-map inspection_default
match default-inspection-traffic
!
!
type of policy-card inspect dns preset_dns_map
parameters
message-length maximum 512
Policy-map global_policy
class inspection_default
inspect the preset_dns_map dns
inspect the ftp
inspect h323 h225
inspect the h323 ras
inspect the rsh
inspect the rtsp
inspect esmtp
inspect sqlnet
inspect the skinny
inspect sunrpc
inspect xdmcp
inspect the sip
inspect the netbios
inspect the tftp
!
global service-policy global_policy
context of prompt hostname
Cryptochecksum:012d58f20bdf997d1e7b6927431e0015
: end
Hi Mr. Gyslain,
So, if I understand, you want the following things
- Local NAT LAN 192.168.0.0/24 to 192.168.200.0/24 for VPN Client users to their local network does not overlap with your local network while they are connected
To my knowledge, you should be able to handle this with the following changes to your configurations
- Configure policy NAT
- Changes to the rules of Tunnel from Split
- Remove the existing NAT0 rule
Here are some example configurations I think that need to manage the situation. Of course make sure you have the old configuration at hand if you need to return to the old
Remove the NAT0 rule
- no nat (inside) 0-list of access no_nat
- No no_nat access ip 192.168.0.0 scope list allow 255.255.0.0 10.250.128.0 255.255.255.0
By removing the above configuration, we want to avoid LAN projection with its originating IP address to the user from the VPN Client.
Creating policy NAT
- access list permit VPN-CLIENT-POLICY-NAT ip 192.168.0.0 255.255.255.0 10.250.128.0 255.255.255.0
- public static 192.168.200.0 (inside, outside) - list of access VPN-CLIENT-POLICY-NAT netmask 255.255.255.0
With the above configuration, we mean the ASA NAT your local 192.168.200.0/24 LAN 192.168.0.0/24 WHEN connections are established at network 10.250.128.0/24 destination which is the pool of the VPN Client. This natutally works in two ways. Also note that if your host LAN IP address is, for example, 192.168.0.100, there a 192.168.200.100 NAT address.
Change the VPN Client Split tunnel
- standard of TUNNEL VPN-SPLIT-access list permits 192.168.200.0 255.255.255.0
- attributes of the strategy of group mobile_policy
Split-tunnel-network-list value TUNNEL VPN-SPLIT
The above configuration is intended to change your configurations of client VPN Split Tunnel ACL to a Standard ACL that indicates which networks to send to the VPN to your customer. In this case, it would be the new teeth of politics of 192.168.200.0/24 network. After configuring the ACL you naturally set it up under the VPN settings.
I don't know if you have split tunnel configured at all because the configuration does not appear the ACL name at least. I know that you can at least have the "tunnelspecified" configuration line without specifying the actual ACL but do not know if what follows is a copy/paste problem or typo that should work with complete tunnel also.
With the above configuration, to my knowledge, everything should work.
-Jouni
EDIT: Some typos
Edit2: Name group policy was wrong
Maybe you are looking for
-
Search for Thunderbird fails to find existing messages.
When I touch information in the search box, some cases are found and others are not. I can grasp the entire e-mail address of a person who recently sent me a message and that the message is not retrieved. Messages has not found seem to be random, but
-
HP Pavilion HPE h8 - 1110t: new graphics card
OK, to buy a new HP Envy 32. I want to my care of graphics. I already upgraded my power to 650. Updated the BIOS tried a GTX 960 geforec, but it seems to be incomaptable wit of the BIOS. Any recommendations on a graphics card that will allow me
-
OfficeJet Pro8620: Error printer Officejet Pro8620
I'm on my third Officejet Pro8620 since January 20, 2016. The first printer kept to give a message to ' Please stop printer, then press "with lights flashing. After what happens every few minutes, I picked up the printer to the store and exchanged
-
Unable to start error: 0xc00000e9
There was no change to the laptop, this error message, it is impossible for me to recover and treat my work in class, not to mention the laptop does not start. help help! original title: windows does not start, the error message saying hardware or so
-
Impossible to download the program of educational marketing
* - Original - via cpu to agp that make title? Hi Im having trouble and I can come up with is the driver must be replaced, repaired updatedor? Im getting a 31 code and that the driver version is 6.0.6001.18000 pc turns on and when I try to download a