Backup Tunnel VPN Firewall even
I have 2 VPN tunnels on the same worm 6.3 pix firewall (5) tunnels goes to the remote site. On the remote site, there are 2 internet circuits has a primary and a secondary. The primary circuit goes to one tunnel on my firewall and secondary goes to another tunnel on my firewall that only appears when the primary circuit breaks down.
We notice that when the primary circuit falls backup on the pix firewall tunnel is up but the traffic stops flowing after a few minutes and I need to erase the crypto isakmp before traffic starts to flow again.
Am I missing something with my setups when VPN is similar to this type of installation?
You must configure the tunnel dpd so that once the main tunnel breaks down the PIX must erase the SA for this tunnel.
now based on the code that you have 6.3 (5), keepalive feature is not available
http://www.Cisco.com/en/us/docs/security/PIX/pix63/command/reference/c.html#wp1034654
Thank you
-Syed
Tags: Cisco Security
Similar Questions
-
AnyConnect vpn and a tunnel vpn Firewall even outside of the interface.
I have a (no connection) remote access vpn and ipsec tunnel connection to return to our supplier is on the same firewall outside interface.
The problem is when users remote vpn in they are not able to ping or join the provider above the tunnel network.
now, I understand that this is a Bobby pin hair or u turn due to traffic but I'm still not able to understand how the remote vpn users can reach the network of the provider on the tunnel that ends on the same interface where remote access vpn is also configured.
The firewall is asa 5510 worm 9.1
Any suggestions please.
Hello
You are on the right track. Turning U will be required to allow vpn clients access to resources in the L2L VPN tunnel.
The essence is that the split tunneling to access list must include subnets of the remote VPN to peer once the user connects they have directions pertaining to remote resources on anyconnect VPN
Please go through this post and it will guide you how to set up the u turn on the SAA.
https://supportforums.Cisco.com/document/52701/u-turninghairpinning-ASAKind regards
Dinesh MoudgilPS Please rate helpful messages.
-
Tunnel VPN Firewall (both sides of the Site B, same IP series)
Hi Experts,
I'm in a weird situation, hope I can get an answer from you guys.
I had created VPN tunnel to our customer on our firewall 3 years.
Now we create the VPN tunnel for new customer, but the IP settings to the new customer is the same as the former client. How can we get through this that we can not change the IP settings on both clients.
Here are the technical details
Older Client settings:
(1) our authorized Local LAN IP: 192.168.3.0/24
(2) customer Local LAN IP authorized: 10.0.0.0/8 (as several range of network to the client end)
New customer to make settings:
(1) our authorized Local LAN IP: 192.168.3.0/24
(2) authorized customer Local LAN IP: 10.10.16.0/24
10.10.32.0/24
Please help as well how we can make the settings without making any changes on the client side.
I am using firewall Watchguard XTM 515
Thank you best regards &,.
Mandeep
This issue is beyond the scope of this site (for consumers) and to be sure, you get the best (and fastest) reply, we have to ask either on Technet (for IT Pro) or MSDN (for developers)* -
Tunnel VPN RV-042 for Dual WAN Failover backup function
We have customers with dual WAN failover scenarios with site-to-site VPN tunnels.
In the past, the VPN tunnel backup feature has been available in the RV-082.
One of the new RV-042 firmware versions have the function of backup Tunnel VPN available?
The feature is supported on the RV042 V3 hardware.
-
Tunnel GRE / IP Sec VPN firewall between the router Cisco and Fortigate
Hello
Can I do GRE Tunnel / VPN IP Sec between Cisco router and Fortigate Firewall?
Thank you
Hi zine,.
As long as the Fortigate device support GRE over IPSEC, you will be able to create the tunnel between these 2 devices.
Here is the config for the Cisco Site:
https://supportforums.Cisco.com/document/16066/how-configure-GRE-over-IPSec-tunnel-routers
Happy holidays!
-Randy-
-
problems with vpn firewall/proxy configuration
Hello
I want to access vpn through firewall/proxy (Client VPN) client-side.
I installed the vpn gateway as firewall pix 515 using Microsoft CA IKE SA.
I want to establish the vpn tunnel to my vpn through a proxy/firewall client.
I tried in some places of vpn client where the firewall acts as a linux machine in which he allowed with the ipsec and NAT esp feature. Its works perfectly. But only one concurrent vpn client. Also the first tunnel vpn disconnects when the second user tries without knowing the first established tunnel.
I heard that we can drive this problem using "NAT Taversal" mode which is available in version ios 6.3 as concentrator 3000 Cisco pix.
I want to know how NAT Traversal can solve my problem in which multiple concurrent users without support nat esp in a configuration only one simultaneous user without support nat esp in a configuration of firewall/proxy or firewall/proxy.
Thank you
Karthikeyan V
The VPN client is able to detect that he's been through a NAT/PAT device on the way to the hub/PIX, and then if both ends support it, they will automatically start NAT - T and encapsulate the IPSec packets in UDP port 4500 packets. These can then be NAT would properly and you will not get disconnections or problems you currently see.
You don't see that a client can connect and customers being disconnected when the other connects it is your PAT instrument cannot process the ISAKMP and IPSec packets correctly. It is a fairly common symptom.
PIX v6.3 code will support NAT - T, should be available in March sometime.
-
Recently I tried to build a tunnel VPN of LAN LAN 2 connecting an Asa to a current zone based firewall 2911. It's a standard IPSec psk tunnel nothing complicated. I got the tunnel to establish, but I could only get traffic to encap on the side of the SAA and decap on the side of 2911. I couldn't return circulation. I followed this doc classic here for IPSec in the last example.
http://www.Cisco.com/en/us/prod/collateral/vpndevc/ps5708/ps5710/ps1018/...
And I don't know that the SAA is right I have built a ton of those but I am new to zfw. I don't see anything about a NAT rule exempt. But as all used real IPs instead of NAT I wasn't sure and I have found no info. I do free NAT? If If you are using a roadmap on the end you NAT overload line config as in the past?
I also have a pair of area to "self" and I didn't know if I need something there to be able to do a ping from inside the 2911 interface when the tunnel is at the top of the remote end. Thank you
Is the pair area yourself, outside of itself?
And you say that you do not use only NAT, have real addresses (public routable addresses?), so why you have to make an exception for NAT you have not?
-
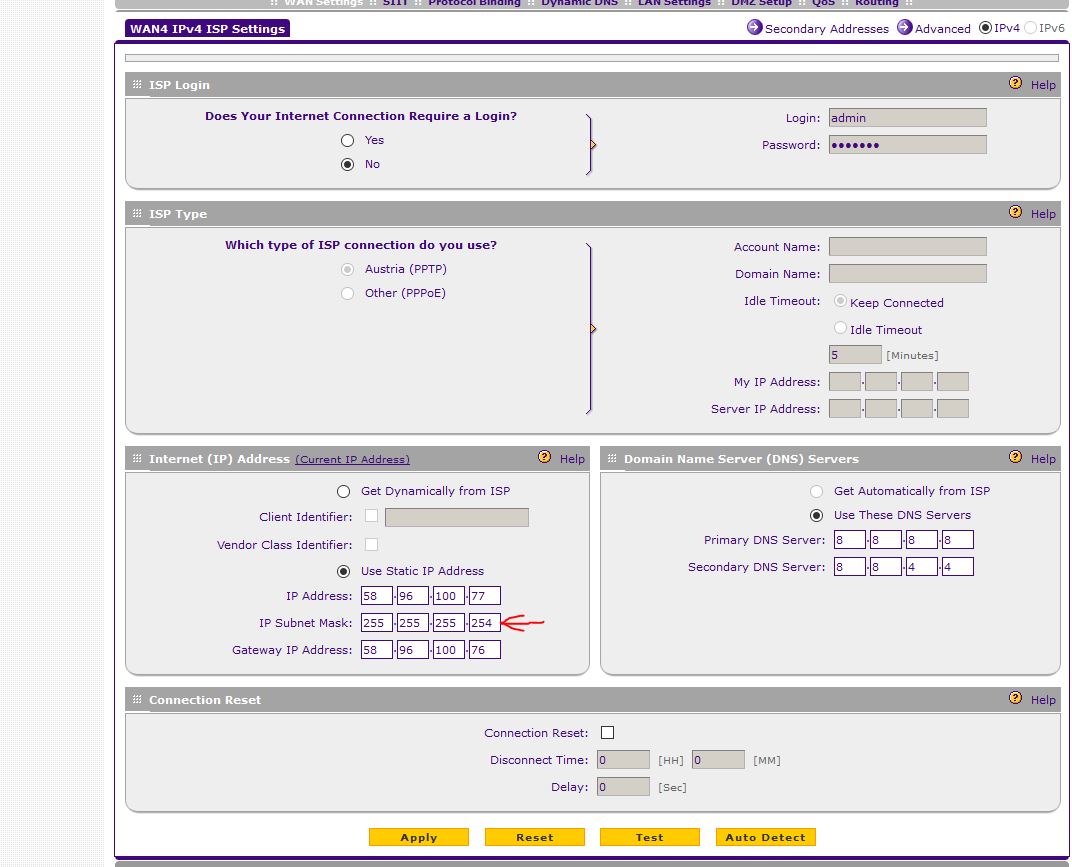
I can't add/subnet mask 31 255.255.255.254 ISP WAN > static IP setting in VPN Firewall SRX5308
Hello
I can't add/subnet mask 31 255.255.255.254 ISP WAN > static IP setting in VPN Firewall SRX5308. When I try to apply it, I get the popup error message like "invalid IP subnet mask. Please enter 0/128/192/224/240/248/252 for octet 4 ". I try to add provider NTU fiber optic internet service in one of the 4 WAN settings. The vendor gave me a 31 block IP and the subnet as 255.255.255.254 mask. It is a limitation in this firewall? I have to ask the provider to give me a 30 block the IP instead? With 30 block IP subnet mask will be 255.255.255.252 who is authorized by this firewall setting. I tried this on another (SnapGear SG560) firewall and it works without any problem. See the screenshots below. Can someone please?
concerning
Ridwan
/ 31 would be used in specific scenarios where you * really * need to keep the address space and on links only point to point. To be honest I've never met anyone, or any ISP that uses it. It works on point to point, because, well, there no need to broadcast address because there are only two devices on the link (one on each side of the cable)... IP address ranges would be;. 0-. 1,.2-. 3, etc.
Most (if not all) Netgear devices will prevent you from setting 31, but you will probably be able to use without problem in all 30 cases, according to the setup of the ISP I do not think that it would cause you problems really. But if you can, I would certainly ask a 30 instead.
-
RV120W Wireless - N VPN Firewall - DHCP reservation
Hello
I have two or three sites with VPN Firewall-Router Wireless-N RV120W, I need the ip address of the client printers in reserve, but I do not see the option. could someone show how to book clients ip?... or this function isn't avialiable longer?
Thank you
Hi Eduardo, this function must be placed-
Networking
>
LAN (local area network)
>
Public static DHCP (LAN)
-Tom
Please mark replied messages useful -
Hello. I'm creating a tunnel VPN IPSec LAN - to - LAN of my ASA5510 to another network but met an obstacle bit. My counterpart on the other side has informed me that he already has a VPN tunnel to another company that has the same IP range as my network(10.100.16.0 /24) and can not create the tunnel.
I was wondering is it possible to use NAT on the VPN tunnel so that traffic that goes from my network over the VPN tunnel gets translated and my counterpart on the other side sees this reflects the range of IP addresses?
Thanks in advance for any help.
Hello
Yes, you can use the same address you already use for internet access.
Just update your list of access crypto to reflect the new address and to ensure that the third party did the same.
Jon
-
Tunnel VPN site to Site with 2 routers Cisco 1921
Hi all
So OK, I'm stumped. I create much s2s vpn tunnels before, but this one I just can't go there. It's just a tunnel VPN Site to Site simple using pre-shared keys. I would appreciate it if someone could take a look at our configs for both routers running and provide a comment. This is the configuration for both routers running. Thank you!
Router 1
=======
Current configuration: 4009 bytes
!
! Last configuration change at 19:01:31 UTC Wednesday, February 22, 2012 by asiuser
!
version 15.0
horodateurs service debug datetime msec
Log service timestamps datetime msec
no password encryption service
!
SJWHS-RTRSJ host name
!
boot-start-marker
boot-end-marker
!
!
No aaa new-model
!
!
!
!
No ipv6 cef
IP source-route
IP cef
!
!
DHCP excluded-address 192.168.200.1 IP 192.168.200.110
DHCP excluded-address IP 192.168.200.200 192.168.200.255
!
IP dhcp POOL SJWHS pool
network 192.168.200.0 255.255.255.0
default router 192.168.200.1
10.10.2.1 DNS server 10.10.2.2
!
!
no ip domain search
IP-name 10.10.2.1 Server
IP-name 10.10.2.2 Server
!
Authenticated MultiLink bundle-name Panel
!
!
Crypto pki trustpoint TP-self-signed-236038042
enrollment selfsigned
name of the object cn = IOS - Self - signed - certificate - 236038042
revocation checking no
rsakeypair TP-self-signed-236038042
!
!
TP-self-signed-236038042 crypto pki certificate chain
certificate self-signed 01
30820241 308201AA A0030201 02020101 300 D 0609 2A 864886 F70D0101 04050030
8B1E638A EC
quit smoking
license udi pid xxxxxxxxxx sn CISCO1921/K9
!
!
!
redundancy
!
!
!
!
crypto ISAKMP policy 10
md5 hash
preshared authentication
ISAKMP crypto key presharedkey address 112.221.44.18
!
!
Crypto ipsec transform-set esp-3des esp-md5-hmac IPSecTransformSet1
!
map CryptoMap1 10 ipsec-isakmp crypto
defined by peer 112.221.44.18
game of transformation-IPSecTransformSet1
match address 100
!
!
!
!
!
interface GigabitEthernet0/0
192.168.200.1 IP address 255.255.255.0
automatic duplex
automatic speed
!
!
interface GigabitEthernet0/1
Description wireless bridge
IP 172.17.1.2 255.255.255.0
automatic duplex
automatic speed
!
!
interface FastEthernet0/0/0
Verizon DSL description for failover of VPN
IP 171.108.63.159 255.255.255.0
automatic duplex
automatic speed
card crypto CryptoMap1
!
!
!
Router eigrp 88
network 172.17.1.0 0.0.0.255
network 192.168.200.0
redistribute static
passive-interface GigabitEthernet0/0
passive-interface FastEthernet0/0/0
!
IP forward-Protocol ND
!
no ip address of the http server
local IP http authentication
IP http secure server
!
IP route 0.0.0.0 0.0.0.0 172.17.1.1
IP route 112.221.44.18 255.255.255.255 171.108.63.1
!
access-list 100 permit ip 192.168.200.0 0.0.0.255 10.10.0.0 0.0.255.255
!
!
!
!
!
!
control plan
!
!
!
Line con 0
Synchronous recording
local connection
line to 0
line vty 0 4
exec-timeout 30 0
Synchronous recording
local connection
transport input telnet ssh
!
Scheduler allocate 20000 1000
end
=======
Router 2
=======
Current configuration: 3719 bytes
!
! Last configuration change at 18:52:54 UTC Wednesday, February 22, 2012 by asiuser
!
version 15.0
horodateurs service debug datetime msec
Log service timestamps datetime msec
no password encryption service
!
SJWHS-RTRHQ host name
!
boot-start-marker
boot-end-marker
!
logging buffered 1000000
!
No aaa new-model
!
!
!
!
No ipv6 cef
IP source-route
IP cef
!
!
!
!
no ip domain search
!
Authenticated MultiLink bundle-name Panel
!
!
Crypto pki trustpoint TP-self-signed-3490164941
enrollment selfsigned
name of the object cn = IOS - Self - signed - certificate - 3490164941
revocation checking no
rsakeypair TP-self-signed-3490164941
!
!
TP-self-signed-3490164941 crypto pki certificate chain
certificate self-signed 01
30820243 308201AC A0030201 02020101 300 D 0609 2A 864886 F70D0101 04050030
2 060355 04031326 494F532D 53656 C 66 2 AND 536967 6E65642D 43657274 31312F30
EA1455E2 F061AA
quit smoking
license udi pid xxxxxxxxxx sn CISCO1921/K9
!
!
!
redundancy
!
!
!
!
crypto ISAKMP policy 10
md5 hash
preshared authentication
ISAKMP crypto key presharedkey address 171.108.63.159
!
86400 seconds, duration of life crypto ipsec security association
!
Crypto ipsec transform-set esp-3des esp-md5-hmac IPSecTransformSet1
!
map CryptoMap1 10 ipsec-isakmp crypto
defined by peer 171.108.63.159
game of transformation-IPSecTransformSet1
match address 100
!
!
!
!
!
interface GigabitEthernet0/0
no ip address
automatic duplex
automatic speed
!
!
interface GigabitEthernet0/0.1
encapsulation dot1Q 1 native
IP 10.10.1.6 255.255.0.0
!
interface GigabitEthernet0/1
IP 172.17.1.1 255.255.255.0
automatic duplex
automatic speed
!
!
interface FastEthernet0/0/0
IP 112.221.44.18 255.255.255.248
automatic duplex
automatic speed
card crypto CryptoMap1
!
!
!
Router eigrp 88
Network 10.10.0.0 0.0.255.255
network 172.17.1.0 0.0.0.255
redistribute static
passive-interface GigabitEthernet0/0
passive-interface GigabitEthernet0/0.1
!
IP forward-Protocol ND
!
no ip address of the http server
local IP http authentication
IP http secure server
!
IP route 0.0.0.0 0.0.0.0 112.221.44.17
!
access-list 100 permit ip 10.10.0.0 0.0.255.255 192.168.200.0 0.0.0.255
!
!
!
!
!
!
control plan
!
!
!
Line con 0
Synchronous recording
local connection
line to 0
line vty 0 4
exec-timeout 30 0
Synchronous recording
local connection
transport input telnet ssh
!
Scheduler allocate 20000 1000
end
When the GRE tunnel carries your traffic to private ip range, your ACL must contain address of the host of point to point the IPSec tunnel.
Since then, both routers are running EIGRP in the corporate network, let the EIGRP Exchange routes via GRE tunnel, which is a good practice, rather than push the ip ranges private individual through the IPSec tunnel.
Let me know, if that's what you want.
Thank you
-
Tunnel VPN from Site to Site dynamic
I spent the last 2 days, try to set up a dynamic tunnel VPN site to site of a Cisco 5510 to a Cisco SA540. The 540 is a dynamic supplier that can not be changed. There a dyndns account.
I was lucky that the other 10 sites are all static and the ADSM Assistant creates these tunnels without problems.
What I try to do is:
Is it possible to do it VIA ADSM?
If this isn't the case, someone please in detail can help with orders.
Kind regards
PP
Hello Paul,
This is possible thanks to the ASDM, but you do have to use some advanced settings:
Configuration > VPN Site to Site > advanced > Tunnel groups
It change the group called "DefaultL2LGroup" and add the brightness button before the SA540 (Note: all of your sites with dynamic IP addresses will have the same key communicated in advance, if you have IPSec VPN clients, it will be a good idea to use a different key).

Click ok and then apply.
Then go to Configuration > VPN Site to Site > advanced > Crypto Maps and add a new entry dynamic

Make sure that you match the phase 2 are on your SA540 (pictured ESP-AES-128-SHA), select a dynamic strategy and make the last sequence number (65535) then ok, apply.
Then go to Configuration > VPN Site to Site > advanced > IKE policies and make sure you have corresponding policies of the phase 1.

If no corresponding policy is found, add them.
Through CLI:
IKEv1 crypto policy 1
preshared authentication
aes encryption
sha hash
Group 2
Crypto-map dynamic outside_dyn_map 65535 set transform-set ESP-AES-128-SHA ikev1
CARD crypto ipsec-isakmp 65535 dynamic outside_dyn_map
IPSec-attributes tunnel-group DefaultL2LGroup
IKEv1 pre-shared-key *.
I hope this helps.
-
What VPN work as a PPTP vpn firewall CISCO-ASA-5520.
Hi all
Can you please tell me which replace the VPN I can configure PPTP on ASA 5520 firewall. What VPN work as a PPTP vpn firewall CISCO-ASA-5520.
You can use the wizard VPN of RA with ASDM and confiugre L2TP IPSEC VPN that does not need a VPN Client must be installed.
Michael
Please note all useful posts
-
Bring up the tunnel vpn crypto without interesting traffic map
Is it possible on ASA to bring up the tunnel vpn site to site static crypto map without generating interesting traffic? I want to reverse route injection generate road dynamic until traffic begins to flow.
Roman,
Unless something chnaged recently RRI inserts routes without present SAs, meaning that they are static (in contrast to current default behavior on IOS 12.4 (9) T-I_think leave).
But to answer the question, in more recent versions, you can bring up the tunnel using packet - trace CLI.
M.
Edit: request for improvement that will present the same features of IPP on ASA as on IOS:
http://Tools.Cisco.com/support/BugToolKit/search/getBugDetails.do?method=fetchBugDetails&bugId= CSCsx67450
-
Tunnel VPN site to Site - aggressive Mode
I searched the community for answers to this and that you have not found quite what I was looking for (or what seems logical). I have an ASA 5510 to A site with one website VPN tunnel to a SonicWall to site B. Which works very well. I need to create a tunnel for site C to site a using a tunnel of aggressive mode. I'm not quite sure how to do this. Any suggestion would be great!
NOTE: I have included the parts of the running configuration that seem relevant to me. If I missed something please let me know.
ASA Version 8.2 (1)
interface Ethernet0/0
nameif outside
security-level 0
IP 1.2.3.4 255.255.255.248
!
10.5.2.0 IP Access-list extended site_B 255.255.255.0 allow 10.205.2.0 255.255.255.128
access extensive list ip 10.5.2.0 site_C allow 255.255.255.0 10.205.2.128 255.255.255.128
dynamic-access-policy-registration DfltAccessPolicy
Crypto ipsec transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
Crypto ipsec transform-set ESP-DES-SHA esp - esp-sha-hmac
Crypto ipsec transform-set ESP-DES-MD5 esp - esp-md5-hmac
Crypto ipsec transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
Crypto ipsec transform-set ESP-3DES-MD5-esp-3des esp-md5-hmac
Crypto ipsec transform-set ESP-AES-256-SHA 256 - aes - esp esp-sha-hmac
Crypto ipsec transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
Crypto ipsec transform-set ESP-AES-128-MD5-esp - aes esp-md5-hmac
Crypto ipsec transform-set esp-SHA-ESP-3DES-3des esp-sha-hmac
Crypto ipsec transform-set ESP-AES-128-SHA aes - esp esp-sha-hmac
Crypto ipsec transform-set esp-3des esp-sha-hmac 3des-sha1
life crypto ipsec security association seconds 28800
Crypto ipsec kilobytes of life - safety 4608000 association
crypto VPN 30 card matches the address site_B
card crypto VPN 30 peer set 4.3.2.1
crypto VPN 30 the transform-set 3des-sha1 value card
card crypto VPN 40 corresponds to the address site_C
card crypto VPN. 40 set peer 8.7.6.5
crypto VPN. 40 the transform-set 3des-sha1 value card
crypto ISAKMP allow outside
crypto ISAKMP policy 10
preshared authentication
3des encryption
sha hash
Group 2
life 86400
Crypto isakmp nat-traversal 30
crypto ISAKMP ipsec-over-tcp port 10000
attributes of Group Policy DfltGrpPolicy
Protocol-tunnel-VPN IPSec l2tp ipsec svc webvpn
tunnel-group 4.3.2.1 type ipsec-l2l
4.3.2.1 tunnel-group ipsec-attributes
pre-shared-key *.
tunnel-group 8.7.6.5 type ipsec-l2l
IPSec-attributes tunnel-group 8.7.6.5
pre-shared-key *.
David,
Please try this:
clear crypto ipsec its peer site_c_IP
clear configure VPN 40 crypto card
card crypto VPN 10 corresponds to the address site_C
card crypto VPN 10 set peer 8.7.6.5
crypto VPN 10 the transform-set 3des-sha1 value card
debug logging in buffered memory
capture drop all circular asp type
capture capin interface inside the match ip 10.5.2.0 255.255.255.0 10.205.2.128 255.255.255.128
After generating the traffic and INTERNAL of the machine behind the ASA:
view Journal | 10.205.2 Inc.
See the fall of cap. 10.205.2 Inc.
view Cape capin
In case it does not work:
(a) show the crypto classic table ASP.
(b) details of vpn-framework for table ASP.
(c) show cry its site_c peer ipsec
(d) entry packet - trace within the icmp 10.5.2.15 8 0 10.205.2.130 detail
(e) see the crypto ipsec his
At the same time, please.
Let me know how it goes.
Thank you
Portu.
Please note all useful posts
Maybe you are looking for
-
How do you prevent this message appear on my desk, on my macbook pro?
-
Issues of model libretto W100 - 106 (UK) - 3G, Windows 7, etc.
Hello forum,. Just bought a brand-new W100-106 (old stock but sealed package, the latest version of the BIOS, etc.) and I have a few questions, I would like to ask if it's okay. Absolutely LOVE with this machine, but would like to know: 1. is it poss
-
The last update disabled the right click.
Last updated FF7 disabled right click in FF only. How can I restore it? TIA
-
If I continue to turn off my router at night, it will be harmful to the router or it will reduce the useful life?
-
Two fingers scrolling does not not in Chrome to the touch screen?
This seems fine in Internet Explorer, someone may it confirm so I know that's not just my setup? The trackpad scrolling is fine in both, just the screen touch doesn't scroll not workingin Chrome for me.