Centralized authentication (IAS/Radius) in IDS/IPS 4260
All,
I was in charge of configuring authentication centralized via IAS for all IPS/IDS devices in the enterprise. After much invest I'm pretty sure that my goal is not available due to the limitations of the device. However, I'm still not sure at 100%. My questions are:
1 is anyone can provide a link or any documentation showing permanently the IPS 4260 supports Radius IAS authentication?
a. If no, what would be a suitable alternative? CSM, etc.. ?
Cisco IPS sensors do not currently support authenticated access to the outside. They can't stand
assignment of authentication and the role of user/password local name.
Scott
Tags: Cisco Security
Similar Questions
-
Filtering of IP addresses on an IDS/IPS signature
Forgive me, I'm pretty green when it comes to signatures manipulting IDS/IPS.
Is there a way to filter an IP or a subnet of a signature of IDS/IPS?
Senario:
We have 2 ASAs with IPS and IDS 2 4260 modules, we use IPS Manager Express 6.1 to manage. I get a mail server is triggering signature 5748-x because its sending a helo instead of a noop verb. It is very good for this paticular mail server. So I would remove its IP address or its signature of the filter IP address therefore in this case does not the signature. However, I don't want to disable the signature in the case where he is somewhere else.
any help is greatly appreciated.
e-
You will need to use a filter event action. See (for version 6):
http://www.Cisco.com/en/us/docs/security/IPS/6.0/Configuration/Guide/IDM/dmEvtRul.html
-
Shell exec user permission on ASA using IAS radius
With the help of ASA 5540 - 8.0 (4) & trying to get approval for Shell EXEC (15) for the authenticated user fron IAS radius server. Used on the SAA aaa authorization command & specified attributes on the IAS radius as shown in the configuration guide, but still the user will be deposited into default exec level. I need to use the enable command to get the user to the privilege level of exec.
Hi all
Although the 'Exec authorization command' was introduced into the code ASA 7.1 the ASA does not support the feature AAA Exec permission yet, so it cannot be configured with RADIUS or GANYMEDE.
The enhancement request has already been filed on it.
-
Changes in prices for the contracts of Support for Cisco IDS/IPS
Nice day
My boss asked me if there is no value added regarding Cisco's recent move to charge separately for hardware and software support for IDS/IPS product line.
Other than what is obvious (need software support for updates of signature, need of material support in case something breaks), I'm having a hard time to provide a response.
Can anyone suggest what is the increased value, other than annual recurrent costs more we get as a result of this change of license?
Also, was there any release press or other notice to the client about this change?
I am at a loss...
Alex Arndt
Alex,
Cut through the spin and the hype... the software support allows us to finance a development team dedicated to signature, which has improved our signature rejection rates and response times. In addition, it is allowing us to expand our coverage to keep IDS 4.1 to get the support of the signature. It is contrary to our previous policy which would have seen 4.1 updates to signature cut shortly after 5.0 released.
A side effect of this is that our development team is now free to focus on the development of the feature, and you will see more updates, more often.
Can't comment on press releases and others, they make your head spin my ;)
Scott
-
Get a Smartnet contract also gives you updated signature IDS/IPS?
One of my clients is looking into getting an ASA5510 with module AIP - SSM. I realize that with IDS/IPS systems, it is * essential * to keep files up-to-date signatures. Buying me the Smartnet contract for the bundle gives updates signature files, or is there another package that I need to buy?
I see references to the "Cisco Services for IPS", but this seems to be mainly for routers/IOS firewall/IDS packages.
There is not a Smartnet contract for the ASA/AIP-SSM bundle.
The only contract SmartNET SSM packages with the CSC - SSM and not the AIP - SSM.
When buying a bundle ASA/AIP-SSM, you'll need to buy a package maintenance contract. Package maintenance contracts are Cisco Service for the IPS markets and include the support of signature for the AIP - SSM and the software and hardware in support of ASA and AIP - SSM (software and hardware support, is what it is normally part of SmartNET).
Packages you will need to purchase a maintenance contract Service Cisco IPS using one of the formats following part numbers:
CON-SUw-ASxAyKz
The 'w' will be 1,2,3 or 4 depending on the level of service.
The 'x' will be either 1 for the 5510, 2 for the 5520 or 4 for the 5540.
'Y' will be 10 for the AIP-SSM-10 or 20 for the AIP-SSM-20.
The z will be 8 or 9 depending on the level of encryption.
Thus, for example:
CON-SU2-AS2A20K9 - would be 8 X 5 X 4 support for the ASA 5520 bundled with the AIP-SSM-20 with the top encryption.
NOTE: There is also SP contracts for purchase by service providers who follow a slightly different format.
There are a few users who have purchased the ASA and the AIP - SSM separately.
When purcahsed separately you would need to purchase a contract SmartNET for the ASA and a separate Department of Cisco for IPS for the AIP - SSM maintenance contract.
Maintenane AIP - SSM contract will be in the following format:
CON-SUw-ASIPyK9
The 'w' will be 1,2,3 or 4 depending on the level of service.
'Y' will be 10 for the AIP-SSM-10 or 20 for the AIP-SSM-20.
Thus, for example:
CON-SU2-ASIP20K9 would be 8 X 5 X 4 support for the AIP-SSM-20.
What you find is that buying a separate SmartNET for the ASA and Service Cisco IPS for the AIP - SSM will be more expensive than buying a single Cisco IPS's Service to the ASA/AIP-SSM bundle. This is because there is a discount when buying by the beam.
-
IPS 4260 sensor - NETWORK ports
The IPS 4260 only comes with 1 port NIC, is what it means he cannot run in promisicious mode and must purchase additional NETWORK card interfaces to run inline?
It comes with a single command and control NICS and NIC monitoring.
Followed NIC can be used for monitoring promiscuity or InLine Vlan pair of surveillance.
With InLine Vlan pair followed you plug changing the port on a switch and do a 2 trunk port VLAN.
The configuration of the sensor inside match you 2 VLANS.
Packets entering Vlan A will be analyzed and passed on Vlan B.
Packets entering Vlan B will be analysed and transmitted on A Vlan.
Then InLine Vlan pairs is like an InLine sensor interface is connected to A Vlan, and the other interface connected to Vlan B; but he is able to do using a single interface.
For the monitoring of traditional InLine Interface pair, yes you will need to purchase an additional NIC
The 4260 supports 3 additional types of network cards: 10/100/1000 TX 1000 SX and 10 Gbps SX.
-
Hello
simple question about the implementation of inline IPS 4260 mode between PIX and core router. IS it possible just to plug pix inside interface with an SPI interface and another nucleus iterface with SPI interface and create line-interface-pair. Or I have to create another VLAN on Core router just to span traffic through IP, using additional ports on the router? Thanks in advance
Yes for inline IPS-4260 of monitoring can be placed between the router and the Pix.
On the 4260 create a pair of InLine interface using the interfaces of the probe 2 and assign it to sensor virtual vs0.
Optionally configure the speed and duplex settings of 2 interfaces of the 4260 so they correspond to any speed hard and duplex parameters that may already be on the Pix and the router.
Disconnect the connection between the router and the Pix. Plug this Pix interface in one of the interfaces of the probe in the pair and this interface of router in the interface of the other probe of the pair.
The sensor should be now able to do inline followed between the router and the Pix.
No configuration change is required on the Pix or router, when you use the method above to add the pair of inline interface 4260.
Of course, you want to do during a downtime planned for your network.
-
Detection of injections SQL with IDS/IPS on cisco ASA?
Hello
Is it possible to detect or prevent attacks by injecting SQL using Cisco IDS / IPS on ASA or with regular expressions?
Is any signature available in IDS/IPS for this? And what is effective, is in terms of the generation of correct alarms?
Thanks in advance
Deepak,
We have several signatures to detect generic SQL injection attacks in the family x-5930 of signatures.
-
Need for an IDS/IPS system for LAN users
Hello
I need to have an IDS/IPS for my users the in my network. We have 3xcisco 6509 to access with 4 level switch VLAN and am looking for a system to detect activities such as ports, IP scan analysis and... local network by desktop.
Please advise me.
Thank you
Mike
Hello
VLAN span is good, no problems at all but I wouldn't recommend 100% to go to IPS mode instead of ID. Safer and more restrictive, way
Concerning
-
Authentication with WPA IAS RADIUS
I have a 1131 I am running standalone (independent). I'm looking for an example of config on how to authenticate to my RADIUS server (running on my domain controller) and use WPA encryption. So far, all I can find are configs for the AP using WLCs. Can anyone help? Thank you!
Take a look at the link below. Is the one you want, MS PEAP w/IAS, there a ride fairly detailed on the configuration of the IAS and an AP.
HTH,
Steve
-
VPN split tunnel with 1811W and IAS RADIUS problems
I am very new to the implementation of a VPN IPSEC with a Cisco router. I know very well on the way to do it with a PIX / ASA, but the controls are a bit different in IOS, where my questions. Here is what is happening, I can connect to the VPN with the Cisco VPN Client. I would assign it an address of my ip pool that I created, but when I try to access the remote network somehow, I can't. I ran a tracert and what is really weird, is that I get the external IP address of the 1811W as my first jump when I list an internal IP address of the remote network (it also fixes the device FULL domain name, so I know that my DNS configuration is correct). I will list my config to the 1811W as well as the screenshot of the tracert. I've removed all the passwords that are encrypted, but they are there in the router config and I am able to connect to the network and click the IAS server behind it. Please excuse the config as we took it during another TI provider so that it can have a few additional entries that may not be necessary that I have not yet cleaned.
Tracert:
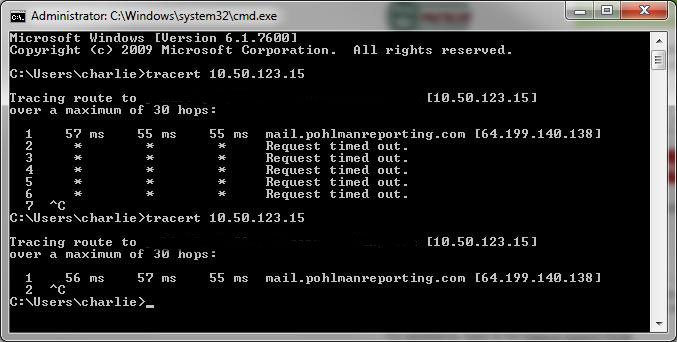
And here's the full config:
Building configuration...
Current configuration: 9320 bytes
!
version 12.4
no service button
horodateurs service debug datetime msec
Log service timestamps datetime localtime show-time zone
encryption password service
!
hostname RTR01
!
boot-start-marker
boot-end-marker
!
logging buffered 8192
enable password 7
!
AAA new-model
!
!
AAA authentication login userauthen local radius group
AAA authorization groupauthor LAN
!
!
AAA - the id of the joint session
clock TimeZone Central - 6
!
SSID dot11 internal
VLAN 5
open authentication
authentication wpa key management
Comments-mode
WPA - psk ascii 7
!
dot11 ssid public access
VLAN 10
open authentication
!
!
!
IP cef
No dhcp use connected vrf ip
DHCP excluded-address 192.168.1.1 IP 192.168.1.10
DHCP excluded-address IP 192.168.1.20 192.168.1.254
!
public IP dhcp pool
import all
network 192.168.1.0 255.255.255.0
default router 192.168.1.1
DNS-server 10.50.123.15 207.69.188.186
!
!
no ip domain search
IP domain name pohlmanreporting.com
!
Authenticated MultiLink bundle-name Panel
!
Crypto pki trustpoint TP-self-signed-3986412950
enrollment selfsigned
name of the object cn = IOS - Self - signed - certificate - 3986412950
revocation checking no
rsakeypair TP-self-signed-3986412950
!
!
TP-self-signed-3986412950 crypto pki certificate chain
certificate self-signed 01
quit smoking
!
!
password username admin privilege 15 7
username cisco password 7
username secret privilege 15 ssetech 5
Archives
The config log
!
!
!
!
crypto ISAKMP policy 1
BA 3des
md5 hash
preshared authentication
Group 2
!
crypto ISAKMP policy 10
BA 3des
preshared authentication
Group 2
!
Configuration group VPNGROUP crypto isakmp client
me?
DNS 10.50.123.15
domain domain.com
pool VPNPOOL
ACL 110
include-local-lan!
!
Crypto ipsec transform-set esp-3des-md5 esp-3des esp-md5-hmac
Crypto ipsec transform-set esp-des-md5 esp - esp-md5-hmac
Crypto ipsec transform-set esp-3des esp-sha-hmac TRANS_3DES_SHA
Crypto ipsec transform-set esp-3des esp-sha-hmac RIGHT
!
crypto dynamic-map EXA_DYNAMIC_MAP 10
Set transform-set RIGHT
market arriere-route
!
!
card crypto client EXT_MAP of authentication list userauthen
card crypto isakmp authorization list groupauthor EXT_MAP
crypto card for the EXT_MAP client configuration address respond
card crypto EXT_MAP 10-isakmp dynamic ipsec EXA_DYNAMIC_MAP
!
!
!
Bridge IRB
!
!
!
interface FastEthernet0
IP 64.199.140.138 255.255.255.248
IP access-group denied-hack-attack in
no ip redirection
no ip unreachable
no ip proxy-arp
NAT outside IP
IP virtual-reassembly
route IP cache flow
automatic duplex
automatic speed
No cdp enable
card crypto EXT_MAP
!
interface FastEthernet1
REDUNDANT INET CONNECTION description
no ip address
automatic duplex
automatic speed
!
interface FastEthernet2
!
interface FastEthernet3
!
interface FastEthernet4
!
interface FastEthernet5
!
FastEthernet6 interface
!
interface FastEthernet7
!
interface FastEthernet8
!
interface FastEthernet9
!
interface Dot11Radio0
Description 802. 11B / G interface
no ip address
!
encryption vlan 5 tkip encryption mode
!
SSID internal
!
public access SSID
!
Base speed - 1.0 2.0 basic basic-5, 5 6.0 9.0 basic-11, 0 12.0 18.0 24.0 36.0 48.0
channel 2462
root of station-role
!
interface Dot11Radio0.5
encapsulation dot1Q 5
No cdp enable
Bridge-Group 1
Bridge-group subscriber-loop-control 1
Bridge-Group 1 covering-disabled people
Bridge-Group 1 block-unknown-source
No source of bridge-Group 1-learning
unicast bridge-Group 1-floods
!
interface Dot11Radio0.10
encapsulation dot1Q 10
IP 192.168.1.1 255.255.255.0
IP access-group 130 to
IP nat inside
IP virtual-reassembly
No cdp enable
!
interface Dot11Radio1
description of the 802 interface. 11A
no ip address
Shutdown
Speed - Basic6.0 9.0 basic - 12.0 18.0 basic-24, 0-36.0 48.0 54.0
root of station-role
!
interface Vlan1
no ip address
Bridge-Group 1
!
interface Async1
no ip address
encapsulation sheet
!
interface BVI1
IP 10.50.123.1 255.255.255.0
IP access-group 105 to
IP nat inside
IP virtual-reassembly
IP tcp adjust-mss 1452
!
local IP VPNPOOL 192.168.130.1 pool 192.168.130.50
IP route 0.0.0.0 0.0.0.0 64.199.140.137
IP route 10.60.52.0 255.255.255.0 10.50.123.2
!
!
IP http server
local IP http authentication
IP http secure server
IP http timeout policy inactive 600 life 86400 request 10000
IP nat POOL 64.199.140.138 pool 64.199.140.142 netmask 255.255.255.248
overload of IP nat inside source list 120 interface FastEthernet0
IP nat inside source map of route-nat interface FastEthernet0 overload
IP nat inside source static tcp 10.50.123.14 21 64.199.140.138 21 expandable
IP nat inside source static tcp 10.50.123.11 25 64.199.140.138 25 expandable
IP nat inside source static tcp 10.50.123.11 80 64.199.140.138 80 extensible
IP nat inside source static tcp 10.50.123.11 143 64.199.140.138 143 extensible
IP nat inside source static tcp 10.50.123.11 443 64.199.140.138 443 extensible
IP nat inside source static tcp 10.50.123.10 64.199.140.138 1723 1723 extensible
IP nat inside source static tcp 10.50.123.14 21 64.199.140.139 21 expandable
IP nat inside source static tcp 10.50.123.18 80 64.199.140.139 80 extensible
IP nat inside source static tcp 10.50.123.18 443 64.199.140.139 443 extensible
IP nat inside source static tcp 10.50.123.18 64.199.140.139 3389 3389 extensible
IP nat inside source static tcp 10.50.123.14 80 64.199.140.141 80 extensible
IP nat inside source static tcp 10.50.123.14 443 64.199.140.141 443 extensible
IP nat inside source static 10.50.123.40 expandable 64.199.140.142
!
deny-hack-attack extended IP access list
permit udp 10.0.0.0 0.255.255.255 any eq snmp
deny udp any any eq snmp
deny udp any any eq tftp
deny udp any any eq bootpc
deny udp any any eq bootps
deny ip 172.16.0.0 0.15.255.255 all
deny ip 192.168.0.0 0.0.255.255 everything
allow an ip
!
recording of debug trap
record 10.50.123.15
access-list 99 allow 10.0.0.0 0.255.255.255
access-list 99 allow 69.63.100.0 0.0.1.255
access-list 102 permit ip 10.50.123.0 0.0.0.255 10.60.52.0 0.0.0.255
access-list 105 deny ip any host 69.63.101.225
105 ip access list allow a whole
access-list 110 permit ip 10.50.123.0 0.0.0.255 192.168.130.0 0.0.0.255
access-list 111 deny ip 10.50.123.0 0.0.0.255 10.10.0.0 0.0.255.255
access-list 111 deny ip 10.50.123.0 0.0.0.255 10.60.52.0 0.0.0.255
access-list 111 allow ip 10.50.123.0 0.0.0.255 any
access-list 112 deny ip 10.50.123.0 0.0.0.255 172.0.0.0 0.0.0.255
access ip-list 112 allow a whole
access-list 120 allow ip 192.168.1.0 0.0.0.255 any
access-list 130 allow udp 192.168.1.0 0.0.0.255 host 10.50.123.10 eq field
access list 130 permit tcp 192.168.1.0 0.0.0.255 host 10.50.123.10 eq field
access list 130 permit tcp 192.168.1.0 0.0.0.255 host 10.50.123.16 eq www
access list 130 permit tcp 192.168.1.0 0.0.0.255 host 10.50.123.16 eq 443
access-list 130 deny ip any 10.0.0.0 0.255.255.255
access-list 130 ip allow a whole
SNMP-server community no RO
!
!
!
map of route-nat allowed 10
corresponds to the IP 111
!
!
!
RADIUS-server host 10.50.123.13 auth-port 1645 acct-port 1646 hits 7
!
control plan
!
Bridge Protocol ieee 1
1 channel ip bridge
!
Line con 0
exec-timeout 120 0
line 1
Modem InOut
StopBits 1
Speed 115200
FlowControl hardware
line to 0
line vty 0 4
location * Access Virtual Terminal allowed only from internal network *.
access-class 99 in
exec-timeout 0 0
connection of authentication userauthen
transport input telnet ssh
!
max-task-time 5000 Planner!
WebVPN cef
!
WebVPN context Default_context
SSL authentication check all
!
no go
!
!
endYou must also create NAT exemption for traffic between your internal network to the VPN Client pool.
You have the following NAT 2 instructions:
overload of IP nat inside source list 120 interface FastEthernet0
IP nat inside source map of route-nat interface FastEthernet0 overloadFor the 120 access list, please add the following:
120 extended IP access list
1 refuse the ip 10.50.123.0 0.0.0.255 192.168.130.0 0.0.0.255
Uses of "-nat ' ACL 111 route map, please also add the following:
111 extended IP access list
1 refuse the ip 10.50.123.0 0.0.0.255 192.168.130.0 0.0.0.255
Then ' delete ip nat trans * "after the above changes and try to connect again.
Hope that helps.
-
Configuration of Windows 2000 IAS RADIUS
I have a problem that I think some people have probably met. I am on Windows 2000 server and setup all my routers as customer to authenticate on my Radius server. Some trial and error, I discovered that the client IP address must be the source address of the packet. It is usually the most of our routers WAN interface.
However, we have a lot of routers with multiple links to the site that hosts the Radius server. This means that packages can come out through three interfaces of the router to get to the Radius server. Because the server is looking for the address of one of the interfaces, my authentication fails.
It is a problem because we lack OSPF and we cost equal to our Radius server location paths. Some lines are lines of failover as well. I guess my question is how can I circumvent add all IP addresses for each router that has multiple connections to the server at my client list in IAS? Or is there a way around it at all?
In global configuration Mode, try
radius IP source-interface command.
Cordially------Naman
-
Sharing the burden of the IDS/IPS
Hi experts,
Since it is possible to implement some IDS features on routers and PIX, along with the ID is, in a network where all 3 of these devices exist, is it interesting to implement some features on routers and PIX IDS?
And, if so, what factors are to be considered in deciding what signatures are enabled on what device?
In this type of scenario, which are considered best practices?
Thank you very much
It is possible to do what you ask. Note that the signature on the IPS appliance is a bigger, more complete than other devices together. The exact mix depends on your network configuration. I would say a finer granularity of inspection closer you to your network. For example, the PIX can perform basic firewall functions and filter most of the low-level, floods and general port scans probe. Some routers are good for the limitation of the flow, the traffic shaping, etc. Then the IPS can inspect flows coming into this challenge, focusing on all traffic that could hurt you (beyond knocking on your front door of firewall). Of course, this is just a scenario. Some people can't stand not knowing what to try to knock on the front door. Others do not want the hassle of trying to reconstitute the papers from three different pieces of equipment so they put things in different orders, such as IOS IPS, PIX. Another focus of exploration is what device you can use as a blocking device, the PIX or IOS router (or IP addresses in the case of mode inline operation).
Cisco means the blueprint of network SECURITY as a job, starting point architecture. The entire library of SECURITY white papers can be found here:
http://www.Cisco.com/en/us/partner/NetSol/ns340/ns394/ns171/ns128/networking_solutions_package.html
-
INTERNET AUTHENTICATION SERVICE RADIUS AUTHENTICATION USING
Hi, I have problems with the same configuration. I authenticate remote users in AD using the Internet Authentication Service on windows 2003 as radius server configure the same VPN via ASA5520 profile. Please a knowledge or have the same information on this type of server configuration? Thank you very much.
Greetings from the King.
Elias Vucinovich.
Have a look here.
Rgds
Jorge
-
802. 1 x authentication with Radius and win7 Mab
Good afternoon!
I have a question about 802.1 x I've set up a laboratory in which I have configured authentication mab with 802. 1 x, but I have a weird behavior of my network controller. On the switch (4948e), I see that the user is authenticated and authorized, and I can see my switch these outputs:
21 April 15:13:30.263: % AUTHMGR-5-START: start "mab" for the customer (a01d.48ac.b7f
(5) on the Interface item in gi1/11 AuditSessionID C0A8DF9C0000002E002F3DAC
* Apr 21 15:13:30.267: % MAB-5-SUCCESS: authentication successful for the client (a01d
. 48AC.B7F5) on the Interface item in gi1/11 AuditSessionID C0A8DF9C0000002E002F3DAC
* April 21 15:13:30.267: % AUTHMGR-7-RESULT: authentication result 'success' of me
ab' for the client (a01d.48ac.b7f5) on the Interface item in gi1/11 AuditSessionID C0A8DF9C00000
02E002F3DAC
* Apr 21 15:13:31.299: % AUTHMGR-5-SUCCESS: authorization succeeds in for the customer (a0
1d.48AC.B7F5) on the Interface item in gi1/11 AuditSessionID C0A8DF9C0000002E002F3DACIf I type "see the authentication session", the corresponding output.
Switch #show authentication sessions
Interface MAC address method ID of Session of field status
Item in gi1/11 a01d.48ac.b7f5 mab DATA Authz success C0A8DF9C0000002E002F3DACThe thing is that when I check my network controller, it said "authentication failure". That's what I've done so far:
1. I restarted my pc, the same behavior.
2. I disabled and enabled my network controller, the same behavior.
3. I rebooted the switch and re-configured. Same behavior.
4. I tried with another PC configuration. Same behavior.
5. I changed the configuration of "user authentication" using dot1x EAP authenticator and it worked.
This is the configuration I have on my switch:
AAA new-model
Group AAA dot1x default authentication RADIUS
Group AAA authorization network default RADIUS
start-stop radius group AAA accounting dot1x default
AAA - the id of the joint session!
control-dot1x system-auth
!
Switch #show run gigabitEthernet int 1/11
Building configuration...Current configuration: 128 bytes
!
interface GigabitEthernet1/11Cx-to-Host description
switchport access vlan 223
switchport mode access
Auto control of the port of authentication
MAB
endThis is the first time I'll put up a configuration 802. 1 x. I'm doing something wrong?
I really hope that I am not the only one with this kind of behavior!
Thank you for any assistance you can give me!
Status: Authz success
This means that the port is open. Is this permanent? Keep looking at the output of the show a few minutes see if it tries to dot1x too. Can you ping from the PC?
As authentication of 802. 1 X is enabled in the properties of the map NETWORK PC that you can expect dot1x method runs on the switch and eventually respond to the computer with auth fail. Authentication in the PC box is not necessary for MAB.
What type of RADIUS server you use and there 802.1 policy X in addition to MAB policy?
IP address: unknown
This means that the switch did not recognize the IP address of the host, probably due to the lack of
analysis of IP device
command. But it is not necessary for the plain MAB or dot1x.
Maybe you are looking for
-
Skype won't start do not. Antedated IE and Skype does not
Hello A couple of weeks ago, I started having a problem from Skype on my computer. Version 6.16, whenever I try to run Skype, the login screen flashes for a split second, but leaving the State of Skype light in the system tray (win7 he calls the "not
-
Qosmio G20 156 - card SD & DVD fail at the same time
Op sys: Windows MCE SP3 Card SD & dvd stopped working after I tried to update the sd driver. I downloaded the module sd-secure-en - 20080916100011.zip in the list of drivers for my SD card and on the execution of the installation requires a missing f
-
Satellite Pro A100 - how to get the Wlan connection works
Help! I'm a total beginner, and my problem is I can get a connection without wire only when I'm really close to my BT hub.My son has a laptop and gets a good connection anywhere in the House and even outside. He thinks I have a dodgy wireless adapter
-
hpdv6000 won't start - error updates configuration? !!
My HP Pavilion dv6000 won't start. When I turn on my laptop it goes through the normal stages of start-up, however it comes up with "configuration updates: stage 3 of 3-0% complete.". Do not turn off your computer. It remains on this page for a few m
-
[EC] Problema con Libreria Dell Powervault TL2000 - Media Attention
Salve, Ho no problema con una libreria Dell Powervault TL2000. Riporta di warning of United Nations Attention in the media, ed ogni operation che cerco di fare he va oppure if offline drive closed in attesa di non so cosa. Ho eseguito del Firmware ag