Cisco CallManager and DHCP beyond vswitch
I have a test lab setup for our managers to call cicso 8.6 running in vmware. Everythings upward and the work. However, I can not all phones to pick up my 172.16.1.1 editor/dhcp server IP addresses. DHCP works very well in the vswitch in vmware, but nothing beyond. Maybe it's a problem with the configuration on my cisco switch, but I would check here thought incase there is something else I need to do on the vswitch.
I can ping everything in all directions without problem. I've got the physical hosts on the cisco switch that can ping the managers of the call and vice versa. I guess it's a vlan tagging problem, but don't know how to solve this problem. I do not have a router in the laboratory, only the switch that is configured as the gateway for the managers of the call.
Call managers - 172.16.1.1 (editor) default gateway is 172.16.1.254
... DHCP subnet is 172.16.1.0/24
.
VMware vSwitch - no vlan tagging, the vswtich is set to zero (0)
.
Cisco 3524 - IP Vlan1 172.16.1.254
... The port that connects the switch to host vmware...
switchport trunk encapsulation dot1q
switchport access vlan 172
switchport mode trunk
switchport voice vlan 172
spanning tree portfast
... The I have a phone plugged into the port...
switchport trunk encapsulation dot1q
switchport mode trunk
switchport voice vlan 172
.
.
Again, I can ping everything in and out of the switch just fine. I can't get anything on the physical switch to pick up an address 172.16.1.1 dhcp.
Promisc mode & forging of mac address enabled on your vswitch and portgroup - with out that DHCP does not.
Tags: VMware
Similar Questions
-
Hello
I just created a vSwitch1 in my ESXi 4.1 host to have an isolated network space, as shown in the image below:
And when any virtual computer starts, it doesn't have any dynamic IP address. This means that there is not "attached" to this network DHCP server. Of course, I could manually assign IP addresses for them. And of course I could also throw a third virtual machine in its own right in the network to play only the DHCP server role. But is there any DHCP server 'hidden' I could activate by typing a magical command in ESXi?
TIA
Not with ESXi - you will need two IP addresses of code hard or as you point abd build a virtual DHCP server and attach to vSwitch 1
-
Requirement of DNS and DHCP Server Essentials 2012 home
I have a Server Windows Essentials 2012 acting as DNS and DHCP server with a domain name for backups etc on my home network. It's that everything works fine, no errors, no problem. Works well actually, telling me when the children did not install updates or restarted.
I have two groups of users. My sons step, 10 and 12, which I want to use OpenDNS as a provider external DNS with a policy very, very limited and my wife and me who want to use indications of root or Google DNS or any other DNS provider. Others, specific devices no user (box of the xBox, WII, Satellite, TV, CCTV etc.) can use.
Before the 2012 server, I had a 2 k 3 server running in a virtual machine for DHCP, alone and put my wife and my devices on static reservations with the just and external DNS provider used OpenDNS as the default scope, DNS. Unfortunately different bits of domain services 2012 don't seem to work unless the server of 2012 is the first DNS server listed on client machines (backups failed. Impossible to find other local computers). Currently, this means that we are all using OpenDNS.
What I would like is a way to say 2012 to send adult group DNS queries to another DNS provider and leave the rest at default to OpenDNS, while still having them register in the original DNS domain. Any suggestions?
This issue is beyond the scope of this site and must be placed on Technet or MSDN -
function of guard of source IP and dhcp DHCP scope of exhaustion (customer parodies other customers)
Hello world.
A dhcp server assigns ip address based on the mac address by equipment of the customer field in the dhcp packets.
A potential attack is when a crowd of thugs mimics different mac addresses and causes the dhcp server to assign ip addresses until no ip address is left for legitimate host.
For example, a host with mac1 h1 is designated by the ip address of the dhcp server as:
199.199.199.1 mac1
DHCP server has this entry in its database.
Using hacking tools such as Yersinia or Gobbler can create a DHCP discover messages every time that create another mac for material scope of the client to the dhcp server, thereby causing a dhcp server to assign ip addresses because they are of legitimate dhcp to dhcp server discover messages with matching each another Mac in hardware of client addresses.
You could use dhcp snooping and it will avoid that (exhaustion of dhcp scope) and configure the switch to check if the CBC mac fits the hardware address of the client in the dhcp message. But when even we can creat spoofed discover messages where mac src in the ethernet header will match the client hardware address in dhcp discovery message. It did not always overcome the problem.
You might say use IP source guard characteristic but it really will prevent this problem from happening?
Let me illustrate:
H1 - f1/1SW - DHCP server
Let's say that we have configured dhcp snooping on sw1 and f1/1 is untrusted port. Switch a suite dhcp binding
199.199.199.1 mac1 vlan1 f1/1
Then, we configure source ip guard in order to validate the mac src and src ip against the dhcp bindings. When you configure keep source ip first, it will allow dhcp only if a host can request ip address and dhcp binding can be built. After that IP keep source will validate ip or mac src src or both against the binding.depending dhcp on how configure us source ip guard.
In our case, we have configured source ip guard in order to validate the mac src and src ip against the dhcp binding.
A dhcp connection is already created as:
199.199.199.1 mac1 vlan 1 f1/1
Now, using hacking tools Yersinia or Gobbler on h1, we create our first spoofed dhcp discovery message where mac src = mac2 ethernet header and client harware address = mac2 in dhcp discovery message. As the switch is configured with the function of guard of source ip and therefore allows dhcp discover message to pass through. DHCP server after you receive the message dhcp assigns another IP from the pool. The dhcp server has now after the entries:
199.199.199.1 mac1
199.199.199.2 mac2.
We continue to spoofed dhcp to craft discover messages as described above and are dhcp server keep ip address assignment until exhausts the entire pool.
So my question is how ip source guard in conjunction with dhcp snooping doesn't stop this attack does not happen? (IE DHCP scope exhaustion)
I really appreciate your comments.
Thank you and have a week.
Hi Sara,.
Ask was quite interesting. As far as I know that whatever it is port snooping untrusted won't let your fake dhcp server.
You can take this query in the Sub forum of experts mentioned that is specific for dhcp snooping and source of guard.
https://supportforums.Cisco.com/message/3689811#3689811
Please assess whether the information provided is useful.
By
Knockaert
-
Series of unmanaged switches 100 and DHCP
Hi all, we have a router RV082 switch 8 ethernet ports, it is actually 8 lan with a DHCP address assignment devices (router is used as switch/router and DHCP server).
Now we need to increase the number of attached LAN devices (other pc, printers, etc.), and we think buy Cisco 100 ethernet switch Series 16 or 24 ports to connect to RV082.
In this case RV082 will be able to assign DHCP addresses for devices connected to the eth switch ports?
Thanks in advance.
Hi Loris, yes it is not a problem. You should be able to switch on a lan port, connect computers to the switch and things should be OK.
-Tom
Please mark replied messages useful -
Several VLANS and DHCP relay on two stacked switch SGE2000-G5
We were put to the task of securing a small desktop system managed that is currently set up with a standard switch for each of the offices (with different companies) to see each other and in some cases, access to each of the other documents on the network.
Obviously, this is far from adequate set up and our goal is to isolate each office using VIRTUAL networks, but share a common internet connection provided by managed offices. We have two switches for layer 3 Cisco SGE2000-G5, but we are new on Cisco equipment and VLAN, so we are not quite sure on how to implement this. DHCP must be provided by a router, there is no server. We are open to suggestions on the router as we still buy a.
I hope that someone may be useful.
Thank you very much
Jim
Hi Jim,.
SGE2000 switches you are using must be able to handle this without issue. What type of router you are using? As long as you have a router that will take in charge VLAN / several subnets, it should be a simple configuration.
Here's a quick run down of the measures to be implemented. (using vlan1 and vlan2)
On the router, create a vlan / subnet 2 and set the port to connect to your shared resources with the two VLAN 1 and 2 switch. (it will be untagged, two will be marked)
On the switch, create vlan2 and do the same for the port connected to the router. (vlan1 marked and tagged vlan2)
Now for each switch port that you want to assign the port access and vlan1 and vlan2. (this vlan will be without a label)
If your router allows, disable routing inter - vlan. If this isn't the case, you must create rules to block traffic from one network to the other.
All this happens under the assumption that your router can support VLAN and can also make DHCP for this VLAN.
Hope this information helps
-
Cisco VCS and integration Lync2013
Hello!
Could you tell me please, when CISCO officially support Lync2013 - free new software for VCS - C and documentation on integration?
The main interest is the possibility of transferring video between CISCO/MCU and Lync endpoints on the H.264 Protocol, who hails from Lync2013.
Right now, I've got VCS - C and RTM Lync2013 X7.2. During the video call without AMGW appeal established as audio only.
When using with Lync2010, it worked on Protocol H.263 and CIF resolution.
Evgeniy salvation,
We are currently investigating the possibilities to achieve interoperability between Lync 2013, VCS and video devices on the side of the VCS standards-based, it is a work in progress and at this stage, it is to early to provide any factual information on when interop will be available.
In contrast to Lync 2010, Lync 2013 does not support H.263 for video and it so that will remove the OCS/Lync integration. I do however think that you should be able to make a two-way video between Lync 2013 and VCS-joined endpoints if you use an AMGW tried that yet?
Thank you
Andreas
-
Backdoor in Cisco routers and firewalls.
The more I read on the NSA scandal (and Yes, I apparently a scandal) less I trust corporations hardware and software. There is no reason for anyone to doubt that all Cisco equipment comes with a backdoor. Because these probable backdoors exist it's a matter of time before hackers discover and exploit them. It's happened to Microsoft a number of times and there is no reason that it could not happen to Cisco. It is no longer our trust Cisco equipment and have already started researching alternatives network.
It is more a crazy conspiracy theory, that is the reality.
In all liklihood, we use a series of firewall to further isolate our network against intrusions. To reduce costs, we can keep our existing in this topology Cisco equipment, but we will replace hardware Cisco when it breaks down or needs to be upgraded. I do the same thing with my home network.
In the last months, we already moved all of our e-mail to secure servers overseas and changed all our McAfee, AVG and Avast antivirus software. We are also researching Linux distributions to replace Microsoft.
If Cisco wants to protect their brand, they need to take a stand or see their market share continue to erode. There must be a CEO to a U.S. company that will take this position and be a hero rather that continue to be a lap dog.
Hello
use open-source based linux firewalls and routers.
and check the source cod
-
Hi all
I'm having a bit of difficulty up a SG300 - 28 p to L3 and DHCP. I will attach a basic network diagram and a very short list of my needs.
I'm building a temporary network for a company event 1 day that I can't make it work in our office "Lab".
L3 - SG300 - 28 p connects to our provider using a connection of the SFP.
I have to be able to address IP DHCP 300 + using the SG300 - 28 p
My problem is that I can ping my 2 machines test (manually configured IP) about 172.16.0.3 and 172.16.0.4, but cannot ping after the (internet) referral. Also DHCP distributes no intellectual property for the range 172.16.0.10 - 172.16.1.200
VLAN 1 is set to 10.2.2.20 access port (to the provider through a connection on port 28 FPS)
VLAN 100 is 172.16.0.2 access port (ports 1-26)
I have the WLC and WAP tri...
Is the set of even possible? I know that the EQ network is a bit budget for users, but for a one day business event I just do not have a budget for the purchase of switches better.
Please excuse the gross chart.
Thank you in advance.
-RJ
Thanks for the reply.
With the information that you have provided, it seems the only part missing is the way return the unit for service providers. Unfortunately there is no way around that, and no, you will not be able to put anything between the two, because the device doing the NATting is unity of suppliers.
I think that what is happening is that traffic is actually the side provider, but there is no way to do so as soon as the provider is not a route for the subnet in 172.16.x.x.
Out of curiosity, why do you use a VLAN for the devices connected to the SG300? Could you use the 10 subnet Ip addresses? If you do this, you will not need to have a route back from the supplier, as all devices will be on the same subnet.
-
Cisco show and share to publish on the internet
Dear Experts
We have new deployment for Cisco SNS, and we publish SNS on the internet. I need help to do it and any recommendations, please.
Thank you
Richard
Hi Richard
Solve you your problem? I have to make sure of the following.
1. you can access external SNS internally.
2-natting is ok between IP Public & private.
3. for the DNS record, make sure that the name must be the same on the inside & outside. For example internlly vod.bnp.med.ca and create a record public vod.bnp.med.ca should be the same FQDN, otherwise your SNS will never work. For authentication, you must publish the DMM.
Note: your question this internal FQDN differs from the external FQDN of the SNS.
Thank you
Please note all relevant information
-
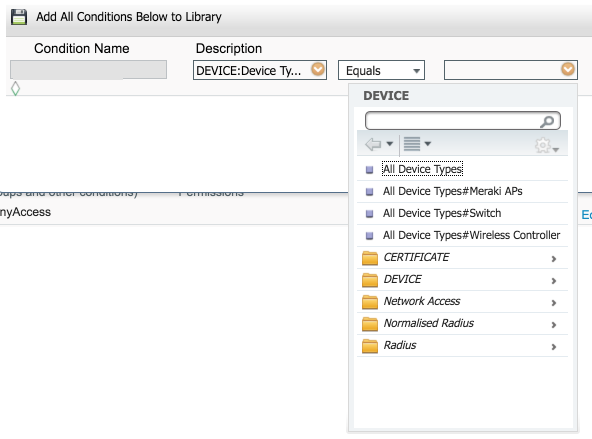
I am very new to Cisco ISE and Meraki. I try to get the Radius configuration for wireless authentication. When I do a test of the Meraki to ISE, it passes.
When I try to connect from my laptop, I look at the logs of the Radius and it passes; However, it does not connect me to good policy. I keep hitting the default policy. I have my Meraki police above the default policy in the strategy defined in article. I have attached what looks like my strategy game.
Devices does not really matter. Here is what I see when I create a device group (where you add the access point to this group), and then create the condition:
And here is where I create the condition of strategy game and you should be able to select the Meraki access points:
This will give you the condition similar to what I posted above. This is perhaps why you aren't hit that is not matching the condition for this game.
-
Cisco ACS GANYMEDE + AAA can be activated for telnet to Cisco 600 and 700 routers?
Unfortunately you can not configure radius AAA or Ganymede in routers series 600 or 700.
-
The traffic load between the power of Cisco ASA and FireSight Management Center fire
Hi all
I have a stupid question to ask.
Can I know what is the traffic load and the e/s flow between firepower Cisco ASA and FireSight Management Center?
Currently working on a project, client require such information to adapt to their network. Tried to find in the document from Cisco, but no luck.
Maybe you all have no idea to provide.
It varies depending on the number of events reported from the module to the CSP. No event = only health controls and policy changes are exchanged. 10,000 events per second = much more traffic.
Generally it is not a heavy load, however.
-
SNMP and DHCP requests on collector
Hello world
I want to see the SNMP and DHCP requests on the interface of collector.
How can I see these queries?
Y at - it logs through which we can see or some CLI to run on systems CASE.
Please help me on this and suggest.
Thank you
Abuzar
Hello
a newspaper would be quickly filled if she provided details on all packages.
The easiest way is to run a tcpdump on the collector.
tcpdump for example eth0-i
You can use tcpdump - help for more info.
Hope this helps,
Nicolas
===
Please note the answers that will help you
-
Configure to integrate Cisco ASA and JOINT
Hello
We have Cisco ASA and JOINT, need assistance on the integration of the same thing; Please email me so that I'll share the details of the architecture.
Thank you best regards &,.
REDA
Hi reda,.
If I correctly your diagram, you do not want to send any traffic from the external switch to the JOINT with a SPAN port and all traffic from your DMZ interfaces with another.
Is this correct?
If so, can you tell me why you want to inspect the traffic before it goes through the firewall? As I said in my original answer, we generally advise putting IP addresses after the firewall.
Not to mention that in your case, I guess that some traffic will be inspected twice so you will need to assign a different virtual sensors to each JOINT internal interfaces to ensure that the same instance does not see the traffic of several times.
Kind regards
Nicolas
Maybe you are looking for
-
Why I can't install the latest version of Adobe Flash Player on Firefox 18.0.0.232?
I tried and tried to get the latest version of Adobe Flash Player on Firefox, but it won't take. Tried through update on the plugin page, tried through the Adobe Web site and still no luck. I listed 18.0.0.232 version on my desktop, but it does not a
-
Favourite Add - ons disappear between sessions
When I start my computer lately, about three of my favorite FF (ver. 33.1.1) modules are installed is no longer. It's Lazarus, X-notify and theme and size Changer.I fonts can reinstall them manually, but it becomes a pain to do. I find that when I re
-
I can't set the mode of Windows 8 on Aurora.
I've been running Aurora for awhile now, but for about a month, Windows 8 mode button has disappeared from my menu. He disappeared just after an update. Is there any help what can I get on it?
-
CD player does not start automatically
HP Presario CQ71-140EA; Windows 7 Professional. When you insert a CD into the CD player, that player does not start automatically. I have to launch Windows Media Player or iTunes before CD games. Any ideas please?
-
Since the update today to 3.6.17 when I click to open a new tab it does not open
the plus sign to the right of the tab open {s] no longer works since the update.} Is - this intentional or just a bug? It's the same on both my PC running firefox.