Cisco ISE - authentication policy
Hello guys,.
Hold the opinions of a scalable strategy for authentication of users and / or the workstations in Cisco's ISE for the following scenario:
Customer with some 130 branch offices. Each branch has an another AD domain without trust with the HQ and with the other branches.
Knowing that the ISE supports integration with up to 50 domains, what suggestion for this case?
Kind regards
Daniel Stefani
Stefani,
Of course it will work, you can even use a centralized architecture CA, make sure just that you can distribute these certificates at endpoints...
Another option is to check if the AD user account is limited (disabled, locked, has expired, password has expired and so on) via LDAP, but you need the username is equal to some field in the certificate (CN or SAN).
Kind regards
Fabio
Tags: Cisco Security
Similar Questions
-
If an end point is several strategies for profiling and each political profile creates a new identity group and unique identity group will be endpoint we present you in. I understand that an endpoint can only be profiled as a single group of identity. Another way of framing the question is, are matched top-down profiling policies or another way? Thanks in advance.
No problem of Graham. To answer your second question: the attributes that are collected first what triggers a rule profiling would be used first. For example, let's say you have a rule of profiling CF 100 which is looking for DHCP of XYZ class identifier, and then a second rule profiling CF 100 which is looking for the MAC YES of ABC. In this case, the second rule would be affected first as the MAC information is collected before the DHCP info is. As a result, the device will be profiled and placed in the endpoint group associated with the second profiling rule until / unless additional attributes are collected which would correspond to a different rule of profiling CF > 100.
I hope this makes sense
Thank you for evaluating useful messages!
-
ISE - authentication radius AAA for n access
Hello
I have configured the switches to use the ISE as a Radius Server to authenticate with, on the ISE, I configured an authentication strategy
for the 'DNA' using the devices 'Wired' group that points to the source of identity AD to authenticate.
All testing switches access connection we found 2 results:
1.A domain user can connect to the switch as expected.
2. each domain user that exists in the source of advertising identity can connect, this is an undesirable result.
So I will try to find a way to restrict access to the ENAD to only a specific group belonging to the announcement, for example the group/OU
of the IT_department only.
I did not, would appreciate any ideas on how to achieve this.
Switching configurations:
=================
AAA new-model
!
AAA authentication login default local radius group
!
ISE authentication policy
==================
!
Policy name: DNA authentication
Condition: ": a device Type equal to: all Types of devices #Wired.
Authorized Protocol: default network access
Use the identity source: AD1
!
No problem is how to set up policies, don't forget to evaluate any useful comments when you are finished testing.
Thank you
Tarik admani
-
Authentication (Windows Server 2013) AD Cisco ISE problem
Background:
Has deployed two Cisco ISE 1.1.3. ISE will be used to authenticate users wireless access admin WLC and switches. Database backend is Microsoft running on Windows Server 2012 AD. Existing Cisco ACS 4.2 still running and authenticate users. There are two Cisco WLCs version 7.2.111.3.
Wireless users authenticates to AD, through works of GBA 4.2. Access admin WLC and switches to the announcement through ISE works. Authentication with PEAP-MSCHAPv2 access and admin PAP/ASCII wireless.
Problem:
Wireless users cannot authenticate to the announcement through ISE. This is the error message '11051 RADIUS packet contains invalid state attribute' & '24444 Active Directory failed because of an error that is not specified in the ISE'.
Conducted a detailed test of the AD of the ISE. The test was a success and the result seems fine except for the below:
xxdc01.XX.com (10.21.3.1)
Ping: 0 Mins Ago
Status: down
xxdc02.XX.com (10.21.3.2)
Ping: 0 Mins Ago
Status: down
xxdc01.XX.com
Last success: Thu Jan 1 10:00 1970
March 11 failure: read 11:18:04 2013
Success: 0
Chess: 11006
xxdc02.XX.com
Last success: Fri Mar 11 09:43:31 2013
March 11 failure: read 11:18:04 2013
Success: 25
Chess: 11006
Domain controller: xxdc02.xx.com:389
Domain controller type: unknown functional level DC: 5
Domain name: xx.COM
IsGlobalCatalogReady: TRUE
DomainFunctionality: 2 = (DS_BEHAVIOR_WIN2003)
ForestFunctionality: 2 = (DS_BEHAVIOR_WIN2003)
Action taken:
Log Cisco ISE and WLC by using the credentials of the AD. This excludes the connection AD, clock and AAA shared secret as the problem.
(2) wireless authentication tested using EAP-FAST, but same problem occurs.
(3) detailed error message shows below. This excludes any authentication and authorization policies. Even before hitting the authentication policy, the AD search fails.
12304 extract EAP-response containing PEAP stimulus / response
11808 extracted EAP-response containing EAP - MSCHAP VERSION challenge response to the internal method and accepting of EAP - MSCHAP VERSION such as negotiated
Evaluate the politics of identity
15006 set default mapping rule
15013 selected identity Store - AD1
24430 Authenticating user in Active Directory
24444 active Directory operation failed because of an error that is not specified in the ISE
(4) enabled the registration of debugging AD and had a look at the logging. Nothing significant, and no clue about the problem.
(5) wireless tested on different mobile phones with the same error and laptos
(6) delete and add new customer/features of AAA Cisco ISE and WLC
(7) ISE services restarted
(8) join domain on Cisco ISE
(9) notes of verified version of ISE 1.1.3 and WLC 7.2.111.3 for any open caveats. Find anything related to this problem.
10) there are two ISE and two deployed WLC. Tested a different combination of ISE1 to WLC1, ISE1 to WLC2, etc. This excludes a hardware problem of WLC.
Other possibilities/action:
1) test it on another version WLC. Will have to wait for approval of the failure to upgrade the WLC software.
(2) incompatibility between Cisco ISE and AD running on Microsoft Windows Server 2012
Did he experienced something similar to have ideas on why what is happening?
Thank you.
Update:
(1) built an another Cisco ISE 1.1.3 sever in another data center that uses the same domain but other domain controller. Thai domain controller running Windows Server 2008. This work and successful authentication.
(2) my colleague tested in a lab environment Cisco ISE 1.1.2 with Windows Server 2012. He has had the same problem as described.
This leads me to think that there is a compatibility issue of Cisco ISE with Windows Server 2012.
Yes, it seems that 1.1.3 doesn't support Server 2012 as of yet.
External identity Source OS/Version
Microsoft Windows Active Directory 2003 R2 32-bit and 64-bit
Active Directory Microsoft Windows 2008 32-bit and 64-bit
Microsoft Windows Active Directory 2008 R2 64-bit only
Microsoft Windows Active Directory 2003 32-bit only
http://www.Cisco.com/en/us/docs/security/ISE/1.1/compatibility/ise_sdt.PDF
-
Cisco ISE 1.1.2.145 Admin authentication via the LDAP protocol
I have configured the LDAP protocol and able to retrieve our LDAP directory structure. Now, I'm trying to point authentication "Admin Access" Source 'External identity', which is the new LDAP IS I created. But I couldn't find an option to authenticate locally if for some reason the LDAP configuration does not work. I learned that the ISE can automatically return to local auth as external sources Idenitity are inaccessible. How can I test the LDAP authentication with breaking them our Admin Access? I thought to open two parallel sessions, one with Super Admin account Local and one with the domain account. But I noticed that ISE communication is smart enough for the closing session/connection no matter what other sessions in different browsers so, basically, I can't open two parallel sessions the same machine to test. Suggestions? or am I missing something here?
Thanks in advance.
Hi Srinivas,
Even if you configure LDAP as a source of external identity of admin access, you can always internal relief without having locked. According to the ISE user guide:
During the operation, Cisco ISE is designed to "fall back" and try to perform the internal identity database authentication, if the communication with the external identity store has not been established, or if it fails. In addition, whenever an administrator for which you have configured external authentication launches a browser and initiates a logon session, the administrator must still the option authentication of demand through the local Cisco ISE database by choosing 'Internal' to the Selector drop-down storage of identity in the Connect dialog box.
http://www.Cisco.com/en/us/docs/security/ISE/1.1/user_guide/ise_man_identities.html#wp1351543
Please see the attached screenshot by my lab ISE:
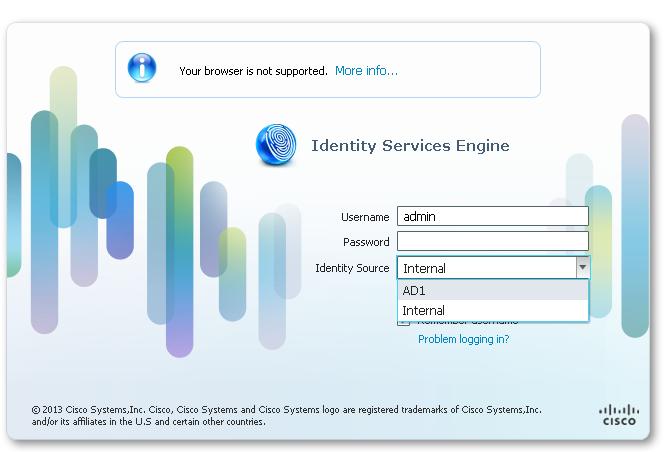
I configured the admin authentication against AD, but I still see both 'Internal' and 'AD' at the time of the connection.
I hope this helps.
Thank you
Aastha
-
Authentication for 802.1 x and Cisco ISE printer
Hello
What is the best practice to authenticate a 802 printer. 1 x in Cisco ISE?
The printer can store a certificate for authentication and support EAP - TLS.
Thanks for the reply.
Marco
Please refer to the rules of authentication
www.Cisco.com/c/en/US/TD/docs/Security/ISE/1-2/user_guide/ise_user_guide...
-
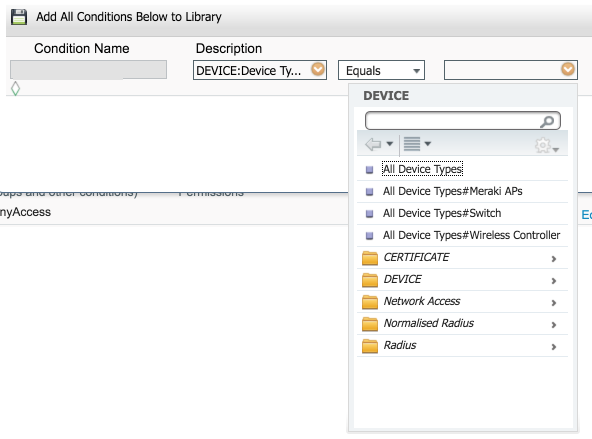
I am very new to Cisco ISE and Meraki. I try to get the Radius configuration for wireless authentication. When I do a test of the Meraki to ISE, it passes.
When I try to connect from my laptop, I look at the logs of the Radius and it passes; However, it does not connect me to good policy. I keep hitting the default policy. I have my Meraki police above the default policy in the strategy defined in article. I have attached what looks like my strategy game.
Devices does not really matter. Here is what I see when I create a device group (where you add the access point to this group), and then create the condition:
And here is where I create the condition of strategy game and you should be able to select the Meraki access points:
This will give you the condition similar to what I posted above. This is perhaps why you aren't hit that is not matching the condition for this game.
-
Group of endpoint Cisco ISE 1.4 hotspot
Patch 1.4 Cisco ISE 6
Cisco WLC 8.0.121
Setup
the WLC has a named Hotspot SSID. It uses mac auth with radius of the NAC to redirect to the Hotspot portal of reviews on the ISE.
drops flexconnect users in vlan 401 (with preAuthAcl), after the PSU, it is initially a COA to move users to VLANs 413 with permitInternetAcl
Description of the problem:
users connect to the SSID of the access point and get an IP address valid in vlan 401
redirected to the page of the hotspot on the ISE with a PSU and the PIN code request.
are they disconnect from the network and reconnect, the ISE sends a certificate of authenticity to move to 413 without the Hotspot portal.
what I've noticed, is that as soon as users get the redirect of the original Web page, they are moved to the endpoint group defined in the hotspot portal.
What I've read about this behavior makes me understand that it is a default behavior, but if that's the case then I'm not sure on how I can make my font to check if the PSU has been accepted.
Thank you
Maarten
Cisco WLC 8.2.100
Patch 1.4 ISE 6
Similar Hotspot ISE installation, of similar rules except change VLAN. I have observed the same behavior.
This configuration was working on patch 5.
Update:
I found a solution based on the following bug. Use the following attribute in the authorization rule. The success page remains but no Instant Internet access is available using this workaround solution.
https://Tools.Cisco.com/bugsearch/bug/CSCux22558/?referring_site=bugquic...
' Workaround:
"Use the LEAST 24 endpoints: LastAUPAcceptanceHours for example (means PUA agreed less than 24 hours ago). -
Access VPN ASA and cisco ISE Admin
Hello
Currently I'm deployment anyconnect VPN Solution for my client on ASA 9.2 (3). We use the ISE 1.3 to authenticate remote users.
In the policy stipulates the conditions, I put the condition as below.
Policy name: Anyconnect
Condition: DEVICE: Device Type Device Type #All Device Types #Dial - in access EQUALS AND
RADIUS: NAS-Port-Type is equal to virtualI'm authenticating users against the AD.
I am also restrict users based on group membership in authorization policies by using the OU attributes.
This works as expected for remote users.
We also use the ISE to authenticate administrators to connect to the firewall. Now what happens is, Cisco ASA valid also against policy, administrators and their default name Anyconnect.
Now the question is, how to set up different political requirement for access network admin and users the same Firewall VPN.
Any suggestions on this would be a great help.
See you soon,.
Sri
You can get some ideas from this article of mine:
http://ltlnetworker.WordPress.com/2014/08/31/using-Cisco-ISE-as-a-generic-RADIUS-server/
-
Cisco ISE 1.2 and the ad group
Hello
I have Cisco ISE installed on my EXSi server for my test pilot. I added several ad groups at ISE as well.
I created a condition of authorization policy, that is WIRELESS_DOT1X_USERS (see screenshot)
Basically, I just replicate the default Wireless_802.1X and added Network Access: EapAuthentication, Equals, EAP - TLS.My problem is, I have been unable to join the wireless network, if I added my ad group to the authorization strategy (see screenshot). The user I is a member of WLAN USERS. If I removed the authorization policy group, the use is able to join the wireless network.
I have attached the screenshot of ISE newspapers as well. I checked the ISE, AD/NPS, WLC, laptop computer time and date, and they are all in sync.
I also have the WLC added as NPS client on my network.
I checked the newspaper AD and I found it, it was the local management user WLCs trying to authenticate. It is supposed to be my wireless user Credential is not the WLC.
It's the paper I received from the AD/NPS
Access denied to user network policy server.
Contact the server administrator to strategy network for more information.
User:
Security ID: NULL SID
Account name: admin
Domain account: AAENG
Account name: AAENG\admin
Client computer:
Security ID: NULL SID
Account name: -.
Full account name: -.
OS version: -.
Called Station identifier: -.
Calling the Station identifier: -.
NAS:
NAS IPv4 address: 172.28.255.42
NAS IPv6 address: -.
NAS identifier: RK3W5508-01
NAS Port Type: -.
NAS Port: -
RADIUS client:
Friendly name of client: RK3W5508-01
The client IP address: 172.28.255.42
Information about authentication:
Connection request policy name: Windows authentication for all users use
The network policy name: -.
Authentication provider: Windows
Authentication server: WIN - RSTMIMB7F45.aaeng.local
Authentication type: PAP
EAP Type: -
Identifier for account: -.
Results of logging: Accounting Information was written in the local log file.
Reason code: 16
Reason: Authentication failed due to incompatibility of user credentials. The provided username is not mapped to an existing user account or the password is incorrect.
Hello
The problem is with what ISE name, it's choosing to search of the AD. If you look in the ISE newspapers down, you'll see the username that use ISE (firstname, lastname) to search for the AD.
In your certificate template see what attribute containst name AD (possibly the dns name or email or the name of principle of RFC 822 NT), go to your profile to authenticate cerificate and use this attribute for the user name.
Thank you
Tarik Admani
* Please note the useful messages *. -
Cisco ISE 1.1.1 with Windows posturing
Hello
We tired for configured windows posturing here's the scenario
We saw five ise boxes 3315 with version 1.1.1 off them 2 is admin, 2 is PS and 1 MNT
and we have local Symantec and WSUS Server.
We make posturing for Windows where I have a few questions
(1) is there an integration here of the local WSUS server with Cisco ISE where Cisco ISE can automatically take all the mandatory WSUS update according to the crititcality of the WSUS server.
(2) what is advised to set up the strategy of the Posture of the posture of windows in Cisco ISE and if manually configure windows political posture using specific KB and if there is an update available on Microsoft will we be able to configure the policy for the new update.
(3) we have configured authentication dot1x in cisco ise and asked as well as on switch port where once the user must be connected to dot1x port of the switch it invites username and password dot1x and therefore, authorization policy, it gives vlan appropriate dynamics.
But what are the ways where we can restrict the machine which is rather than the assets of the company and even if the user's user name and password in short any employee aware how we can restrict the user making the machine rather than the assets of the company?
(4) can configure US policy posture for antivirus which will keep us in normal mode and at the same time, we can put posturing for windows which monioring mode which only monitor policy posture and reflected in the monitoring, log in which does not restrict the network for windows posturing
That will be great if any one can please help me to get the issues
Thank you
Pranav
What follows is under the POLICY-OF ELEMENTS of STRATEGY-POSTURE-> REQUIREMENTS > >

What follows is located under
POLICY OF-> ELEMENTS OF STRATEGY-> POSTURE->
REPAIR-> WINDOWS SERVER UPDATE SERVICES REMEDIATION ACTIONS

What follows is part POLICY-> POSTURE

These settings work ALMOST flawlessly for me by forcing her we approved on our WSUS server for our group of workstations updated (all of our laptops are members of the) which meet the criteria of severity EXPRESS (critical and Important). Now, what I've discovered in the last few days is that... MS seems a bit random in their identification of what severity level they assign to their updates. For example... I think that a service pack of the operating system would be considered IMPORTANT if not CRITICAL... however... Look at this from the identification of the server WSUS from Windows 7 Service Pack 1:

Thus, those who updates you deleted, I'd go throgh your WSUS server to identify how they are identified by gravity, then according to your needs set the parameters of the ISE accordingly to ensure that you get updates you plan.
Hope this helps everyone out there who has similar problems.
Thank you
Dirk
-
Cisco ISE with GANYMEDE + and RADIUS both?
Hello
I'm wired opening of authentication on a network using Cisco ISE. I studied the conditions for this. I know that I need to enable the RADIUS on the Cisco switches on the network. The switches in the network are already programmed to GANYMEDE +. Anyone know if they can both operate on the same network at the same time?
Bob
I suppose that Ganymede is configured (with ACS 4.x or 5.x) for the peripheral administration via telnet/ssh, and now you need the RADIUS (radius) to authenticate 802. 1 x. Yes they can both work on the same network at the same time.
~ BR
Jatin kone* Does the rate of useful messages *.
-
Cisco ISE comments Sponsor Isssue Portal
Hi all
We have insatalled 5 boxes of ise 3315 IOS 1.0.4 in our network where in two of them are admin node, two services strategy and has a node mnt. We using sponsor portal for guest user wirless comments where we integrated WLC 5508 with ise and using weblogin for guest users.
We have created open ssid wlc and external aid redirected url to ise for the login page of comments.
But when we create a guest in the sponsor for guest user connection, user that we faced after publication
(1) when guest user gets connected to WiFi and connect to the portal of comments with credentials after putting the credentials then his new redirect to the same login page
wihout invites successful connection.
Can us guest login successful after comments connect to the portal of reviews or redirect any other link as google.com for guest user will be done the knowledge he is able to access the internet now
(2) we have appointed time profile 8hours first user login guest. When the guest user gets connected while putting in credentials on the portal of comments.
But we are facing problem after about 20 mins enhanced disconnects Internet and comments again Gets the login page of the portal of the guest and if we put the same credentials, then his work but after about 20 min interval disconnected Internet user.
Can someone help me resolved on observation about covers them cisco ise comments sponsor Portal
Thank you & best regards
Pranav Gade
Pranav your answers are online,
(1) when guest user gets connected to WiFi and connect to the portal of comments with credentials after putting the credentials then his new redirect to the same login page
wihout invites successful connection. When you use CWA (Central web authentication) there is no way we can redirect users by using the redirect url because it will always redirect users for each time they start a web request. There is no other cost functionality that will remove this condition because they have already been authenticated. Here is a guide that explains the user experience when using web Central auth -
http://www.Cisco.com/en/us/docs/security/ISE/1.1.1/user_guide/ise_guest_pol.html#wp1296954
Can us guest login successful after login guest Portal comments or redirect any other link as google.com for guest user will be acquainted with it is able to access the internet now This is not possible, you can change the verbage and force the AUP to be displayed to users informing them that they can start their web request after hitting the button I accept.
Here's to justify it experience, once users go through the process of reviews-
(2) we have appointed time profile 8hours first user login guest. When the guest user gets connected while putting in credentials on the portal of comments.
But we are facing problem after about 20 mins enhanced disconnects Internet and comments again Gets the login page of the portal of the guest and if we put the same credentials, then his work but after about 20 min interval disconnected Internet user. Check advance timer on your SSID you can be hitting the session on the WLC timeout. Please disable this option and let the functionality of COA ISE at expiration of the user on the controller sessions of.
Thank you
Tarik Admani
* Please note the useful messages *. -
Cisco ISE 1.3 disable "Identity Resolve" step?
Currently, I am working for a client with a Cisco ISE 1.3 deployment.
The Cisco access point are currently authenticated by MAB, the customer wants to improve that I proposed to implement EAP-FAST speed of the MAB for the AP for a quick and easy solution.
I work in the test and production environment, but I was cycling through the authentication process and found something strange.
I created a rule that if the Tunnel network protocol is EAP-FAST are authenticated by internal users.
It works very well, the ISE recognizes the flow and internal users through authenticatie.
15041 assessment political identity
15048 questioned PIP - Network Access.EapAuthentication
15048 questioned PIP - Network Access.EapTunnel
15004 Matched rule - EAP-FAST
15013 selected identity Source - internal users
24210 Looking user in IDStore of internal users ->
24212 found user in internal users IDStore
Authentication 22037 spentOn the way he also decided to search for the user in Active Directory.
Given that the user has not been created in Active Directory, that it does not.
Looking 24432 user in Active Directory -
>
Identity resolution 24325 ->
Search 24313 of corresponding accounts at the junction ->
24318 no corresponding account found in the forest ->
24322 identity resolution detected no corresponding case
Failure of the 24352 - ERROR_NO_SUCH_USER identity resolution
24412 not found user in Active Directory ->
15048 questioned PIP ->. ExternalGroups
15048 questioned PIP - Network Access.EapTunnel
15004 Matched rule - AP_EAPFAST
15016 selected the authorization - AP_Lan profile
11002 returned access RADIUS acceptanceSo the authentication and authorization is successful but he try's to resolve the user in active directory.
I checked the authentication for MAB process, and here I see the same error.
The MAC address of the device used to MAB also is added to the ISE, then authentication through internal users, authentication and authorization is successful, but ISE wants to solve the (MAC address of the device) user in Active Directory.
We also see this step for the flow of EAP - TLS, and in this case the identity stage via resolution is successful.
Is it possible that I can disable the resolution of identity through AD when the internal user group? (or in the world?)
I did some research and found this (search for LDAP users)
http://www.Cisco.com/en/us/docs/security/ISE/1.0/user_guide/ise10_man_id...
When I look at our deployment, it is nothing configured under LDAP.
If you have rules in your authorization rules that use ad groups that are in front of your MAB or the EAP-FAST rules, ISE will do a search to see if it needs to match this rule. Put your MAB and EAP-FAST rules about AD membership rules, and it won't do the research.
-
Hello
I have cisco ISE 1.0, which I want to spend 1.3 ISE. According to the upgrade path, I would need to follow this process
1.0 > 1.1 (apply the latest patch) 1.2 > 1.3
The bundle 1.0 to 1.1 is deferred. So I think to install a new 1.3 ISE as a virtual appliance and then configure it from there. I have not too clued up on ISE so I was wondering is there a way to backup on ISE 1.0 and 1.3 restoration?
If this is not the case, what would be the best approach?
Thank you
Wow 1.0 to 1.4 is a big leap in functionality. You run this in your production network?
Authentication and authorization should continue to work that you have configured the.
On the top of my head
-you come on duty return to the AD domain (if you have joined in the first place). Make sure you have the credentials of the service account to do.
-Comments and other portals have been completely redesigned. If you have made any customizations, you're probably better it demolition and reconstruction by using the new tools of the portal generator.
-Depending on whether you have advanced Base 1.0 licenses will take you through basic or Apex with 1.3 / 1.4.
-ISE has a ton of other features that may or may not apply in your environment.
Maybe you are looking for
-
Help me to fix error code 0 x 80020000 on Mac OS 10.11.5 (15F34) El captain
When I try to burn a DVD on my laptop MacBook Pro on my Super writer, I get the error code 0 x 80020000. I have Mac OS 10.11.5 (15F34) El captain. I tried to use a lower speed 2 x, change of name of file (no dashes, underscores) and ran disk utility,
-
How can I leave Firefox automatically starts in mode full screen (Mac PowerPC with Firefox 3.6)
I use a Mac Mini (PowerPC) as media-computer for our Narrowcasting screen. It's an old mini with Max OS X 10.5.8 and Firefox 3.6.28. This works very well for a few years. But whenever there is a power failure the mini boots itself again and Firefox i
-
prolific usb-to-serial com port driver problem. I can't load the driver appropriate for that. What should I do?
-
I can't copy QB to my flash drive.
I can't copy QB to my flash drive. He said: I need the permission of the administrator and I am the admin. It was suggested to get the permission from windows, but I do not understand. How will I know if I am the admin. for windows?Thank you
-
Installation of Win 8 Officejet 4500 problem
I tried to install my HP Offiejet 4500 on my new computer laptop win8. Extraction of pilot ends as soon as a message and everything stops. I placed an image of the message here. Any solution please?