COA and Clarification of the ISE
Can someone clarify exactly what COA (change permission) is?
From my understanding, ISE can make an initial authentication and using the configured authorization policy but it is not considered COSTS.
If subsequently a posture or profiling check is performed for this authenticated, authorized session and a new policy applies to this existing session then this would be considered in COST.
This is why COA is feasible with advanced license because of the posture and profiling.
Thank you very much.
Graham
Hello
CoA is a feature that allows two-way communication in the radius Protocol. Before the scenario you had when the clients connect to the network, the n intiates a radius authentication session, and then you have received either an accept or reject.
With this agreement, after you receive reject it or accept. You can now put an end to an existing session, authenticate a user if their session information change and correspond to a different access policy (must as in the example if a customer makes inconsistent to consistent).
CoA, which is not entirely used for the advanced features of license. There are a few scenarios where cost can be committed, for example, if an administrator removes any end point of the database of the ISE. ISE will then interview the internal session cache to see if there is an active session and then will issue a certificate of authenticity.
Thank you
Tarik Admani
* Please note the useful messages *.
Tags: Cisco Security
Similar Questions
-
2 TB LUN and Clarification of the scope
I have a need to assign several VM in my environment of clients with 2 TB vmdk files, but I also want to be able to take snapshots of these servers.
Because of this I would expect the community could clarrify a few points for me by correcting one of my points/assumptions;
(1) VMFS data warehouses can be a maximum of 64 to in size.
(2) VMDK can include up to 2 TB in size.
(3) develop a VMFS datastore and LUN requires that he space / free vacuum at the end of the disc.
(4) creation of a store of data VMFS higher then 2 TB requires the creation and presentation for ESX (i) multiple LUNS and then link them together using extensions.
(5) to extend a LUN/VMFS beyond 2048 GB is bad news and can cause data corruption.
So in my situation it seems to me that I need to create a 2 TB LUN and a second unit logic to say 300 GB number, then link them together using a measure to create a store of VMFS data that spans the two LUNS and has a total of 2.3 TB of space. So I can create my 2 TB VMDK and still be able to take pictures.
Is there one way other or better to get my result?
Are there concerns with the help of extensions, it's what trade off?
Any other comments would be welcome.
See you soon,.
Paul
What is your process to separate the configuration of virtual disk file in the files of virtual disk storage?
Nothing special. When you create her select VM first data store. Then, when you create the virtual disk in the wizard, just select the second data store
What the penalty or drawback to the use of extensions?
They're just not necessary anymore. Extents should be used prior to ESX (i) 4.0 to resize a data store. With ESX(I) 4.0, it is now possible to resize/grow the store of data on the fly after resizing the underlying LUN without needing extensions. With extents, you lose that option. Basically, a data store extended is as a RAID 0 array.
You can also read http://www.yellow-bricks.com/2009/03/26/resizing-your-vmfs-the-right-way-exploring-the-next-version-of-esxvcenter/
André
-
Can I restore the backup Windows XP on a new computer with Windows 7 COA and upgrade to Windows 7?
Original title: upgrade question.
I currently have a PC running XP in a system with an IDE drive. The system has many applications that the company has moved the installation discs, so I need to move the contents of the entire disk to a new system. I was about to do the following:
System backup with a recovery boot disk, in this case a USB.
Restore the entire operating system to a new system that will have a SATA drive in it. The new system will have a COST for Windows 7.
Start the XP and upgrade to Windows 7.
My question is, will it work or the absence of the COA of XP on the new system will prevent me to install?
Any help would be appreciated.
Thank you
The fShort answer, "no, this will not work."
It is unclear what you mean by 'backup' and 'restore', but it seems that if you are referring to the creation of a disk image or a clone of disk on an external drive and then either restore the image or cloning to the new computer. Assuming that both of these computers was provided with Windows pre-installed, this process will almost certainly result in a facility that cannot be 'activated '. In addition, unless the software you use has something like Acronis Universal Restore, restore the image from your old computer to a player in a new computer with a different hardware simply will not work.
In addition, the lack of an XP license is not the issue. There are several problems with the process you describe, but basically, an "upgrade" from XP to Win 7 requires a "custom installation" which means that applications should be re-installed.
-
Need a Clarification on the installed component and run Simulator Configuration
Help!
I need clarification on what the plugin Eclipse is telling me. There are two parameters that are confusing me. For components installed (found under preferences/Window/BlackBerry JDE/Installed Components), I have a choice of 5.0.0 4.7.0,4.6.1, 4.6.0 4.5.0 and 4.3.0.
Depending on which component I select when I go in the tab Configurations.../Simulator/course walk, I see a different mix of devices. In all cases, there is a default Simulator.
Initially, I assumed that each JDE component supports a mixture of different devices, and that is it compiled correctly, I would be assured that the app would work for all devices on the tab run Simulator Configuration. In my tests, I found theopposite. I also assume that, for each component of the JDE, there is a 'default' Simulator that was representative of all devices in the drop-down list run Configuration Simulator. In my tests, am not sure what actually represents the Simulator 'by default'.
Can someone clarify how to JDE and Configuration simulators run installed interact and a developer show how to ensure that their application is running on a mix of devices?
When I finally get to the point where I am ready to deliver, what are the points of decision of installation? Is it enough to simply require a specific version of an operating system (for example 4.7?) or do I have to create a grid and check the two model number and version of the operating system?
Thanks for your help.
"currentT shipping Curve 8330 come with OS 4.5" - they must be, as far as the carrier released a version 4.5.
"Your statement that most consumers do not upgrade surprised me too" - only I support! You might get a different opinion of someone else. But the question is why would? And our world app downloads indicate that he is did not upgraded phones out there.
"I guess you are right in this assumption of statementI you are right in this statement"
What is - an appropriate version of the BlackBerry JDE
Article number: DB-00537
http://www.BlackBerry.com/knowledgecenterpublic/livelink.exe/fetch/2000/348583/800738/800901/What_Is..."If there is some Curve 8330 there running 4.5 OS, it's a configuration supported." - correct
"Construction of the 4.3 OS will be one where the menu appears in the upper right and the built 4.5 OS will be one where the menu is out." Sounds good
-
The ISE comments and update of Broswer Security Portal
Hi, last week our assistance service received a constant steam of calls regarding our wireless of comments. For most people, the problem is that there are browser will not allow them on the portal. After a bit of investigation, we have established that what happens on devices with the latest browsers - IE11, Firefox 39 + and Chrome.
OS x and iOS devices and those devices with older browsers are working ok.
We run ISE 1.1.3.124 which is a certain number of revisions behind so I assume it is the question that 'ignore' safety standards in these new browsers.
My plan is to upgrade to version 1.2, and then to 1.3 which I had planned to do next month anyway, but I just wanted to see if there is a work around on the ISE, which can be implemented so that the upgrade is made a thoughtful and not rushed.
Thank you.
This problem is apparent on several Cisco - ISE and at least first Infrastructure products.
A couple of threads to discuss and provide workarounds:
ISE 1.3 (or 1.4) will fix it. In addition, ISE 1.2.1 Patch 7.
Here's the official Cisco ISE Bug ID.
-
1.3 the ISE and multiple licensing requirements
I am building a box of ISE 1.3 and I want to know if the following is feasible
I have an AD forrest who has several groups of configured users
- Corporate
- BYOD
- demo
What I want to do, use these groups to assign users wireless to the VLAN correct based on the membership of these groups AND the type of device they are connecting from.
for example User1 connects to the network wireless from a Mac. And they belong to the Group of corporate users. I would like to be put on the vlan corporate.
However, are they connect from their IPhone device and also belong to the Group BYOD, they get put on VLAN BYOD which has restricted access.
I guess I should add User1 to the company and the BYOD AD groups, then the terms of use to determine what type of device they use and then create a profile for authorization to manage this VLAN they deleted in. Then use airespace acl to determine what resources, they have access to.
Unfortunately, the interface has changed a bit from 1.2 to 1.3, and I don't know if this is feasible.
I advise to use the BYOD within the ISE feature that uses the device registration. All devices are on (default) RegisteredDevices group identity within the ISE, so that your authorization policy can look if EndPointIdentityGroup = ADGroup RegisteredDevices AND = BYOD then = BYOD VLAN + ACL.
Put your saved rule BYOD above all others in the list for your rule of Group of companies don't replace the BYOD.
-
I have a client that 5508 WLCs runs through the area, and I'm catching IEEE802.1x authentication for the enterprise WLAN and WebAuth for WLAN of comments... they PSK now :(
They have ad and ISE and NAC great interest, so my immediate thoughts are to integrate ISE AD and use ISE as RADIUS server for .1x on the WLC. Then use the WLC and ISE do WebAuth for comments... It's all of the standard stuff, but it gives the background.
Now, we come to the interesting bit... they want to run BYOD. They are involved in the financial markets, so the BYOD must be tightly controlled. They ask on ISE coupled with the NAC, but I am not convinced that I need the NAC since the arrival of the ISE1.3. Of course, I will examine three (min) SSID, corporate knowledge, comments and BYOD, just logically distinct. I have nothing that ISE 1.2 cannot press the company and comments but BYOD must full profiling and reclamation prohibition or device before access to the net.
Someone at - he comments or suggestions? Is ISE 1.3 enough NAC-like that I don't need more, or if this is not the case, what additional benefits does that ISE can support
Thanks for your advice/comments/experiences
Jim
Hi Jim -.
Version 1.3 offers an integrated PKI and a significantly improved services reviews experience. The internal PKI is nice if the customer does not have a PKI solution in place. Don't forget however that the PKI ISE internal can only issue certificates to BYOD devices which have boarded through the ISE BYOD "flow", you cannot use the ISE PKI to issue certificates to computers in the domain.
With regard to the NAC: you need to specify exactly what is needed here. If you were to make "posture assessment" then ISE can do for machines based on Windows and OSX. You can check for things like: A / V, a/s, status of the firewall, Windows hotfixes. If you want to make the posture on mobile devices, so you will need to integrate ISE with MDM (mobile device management) solution such as: Airwatch, Mobile, Extend360 iron, etc. ISE may question the MDM for things like: the device is protected with a PIN, is the rooted device, is the encrypted device, etc.
I hope this helps!
Thank you for evaluating useful messages!
-
1.2 of the ISE and iPEP required certificates
Hello
For version 1.1.x of ISE, there are a few constraints on the certificates used for iPEP and Admin:
Both EKU attributes must be disabled, if the two attributes, EKU are disabled in the certificate of Inline Posture, or the two attributes, EKU must be activated, if the server attribute is enabled in the certificate Postur Inline.
- [http://www.cisco.com/en/US/products/ps11640/products_configuration_example09186a0080bea904.shtml]
- The same applies for iPEP ISE 1.2? For ISE 1.2 User Guide and Setup Guide material does not mention anything about EKU and the attributes of specific certificate...
- Any thoughts?
- Thank you
- Octavian
Validation of EKU has been removed in version 1.2
"If you configure ISE for services like Inline Policy Enforcement Point (iPEP), the model used to generate the ISE server identity certificate must contain attributes to authenticate client and server if you use ISE Version 1.1.x or earlier." This allows the admin and inline nodes to mutually authenticate each other. The validation of the EKU for iPEP was removed in ISE Version 1.2, which makes this less relevant requirement. »
Source:
http://www.Cisco.com/en/us/products/ps11640/products_tech_note09186a0080bff108.shtml
-
Hi guys,.
I'm having a lot of trouble to translate what I know PS6000 table to the new M4100x. Here's what I'm building:
I want my iSCSI traffic that is completely isolated from all other traffic, and I want to use the CMC network to run the Board. It must be a simple configuration, but Dell documentation for which is worse than useless. It confuses and everyone who's read it confuses. Why is this?
It seems that I should be able to assign the IP addresses of management using the MCC according to DELL:
Step 1. Initialize the storage
* Once in the CMC right-click on storage open storage gui initialization.
* Member name: MY_SAN01
* Member, IP: 192.168.101.10
* Member gateway: 192.168.101.254
Group name: MY_SAN
Group IP address: 192.168.101.11
Group of Memebersip password: groupadmin
* Password Admin group: groupadminIt sounds simple enough, and when I apply this I guess I will be disconnected my M4110x simply because it currently resides on a separate network (net 2 in the image above). Now how to set up the IP address of my CMC (net0 in the picture above) network management?
Step 2. Set ip management port
According to the documentation of Dell, I have:
To set the management port:
* Open a telnet (ssh) session on a computer or console that has access to the PS-M4110 range. The array must be configured beforehand.
* Connect the PS-M4110 modules using the following racadm command: racadm Server 15 connect
* Connect to the PS-M4110 array as grpadminOnce I am in:
Activate the management controller ports using the following commands in the CLI:
0 > member select MY_SAN01
1. (array1) > eth select 1
2. (array1 eth_1) > 10.10.10.17 ipaddress netmask 255.255.255.0
3. (array1 eth_1) > upward
4. (array1 eth_1) > exit
5. (array1) > grpparams
6. (array1 (grpparams)) > network management-ipaddress 10.10.10.17(array1 (grpparams)) > exit
My interpretation is correct? Now my questions:
1. in step 2. SubStep 1 - How can I know what ethernet interface to use? Step 1 automatically assume eth0?
2. am I correct in using the same IP address for both step 2 - substep 2 and substep 6? Or do I have to assign a different IP address for these? 10.10.10.18 maybe.
3. step 2 - substep 6, it doesn't seem to be that a network mask is that correct?
4. comparison of the ps6000e - I set up an IP address for each controller (so 2) and then assigned an IP address for the group. It's 3 IP addresses. For this M4110, it seems that I have only one controller. Is this correct? The specifications make a point that there are 2 controllers. What happened to the IP address of the controller of the 2nd?
CLOSE-UPS
I intend on building a VMware cluster using the algorithm of multiple paths of DELL and I built it to the DSC, but a technician Dell put in place the table initially and have not set up a dedicated management port. Required configuration routing traffic on the net iSCSI management. It is not recommended, and I don't want to set up this way.
Currently, he is a blocking problemand I need to go beyond this ASAP. I work with a large system integrator in Texas and plan on the order that these systems built this way on their part. This means that I must be able to explain to them how to proceed. This issue is standing in the way of progress, and I really hope I can get a satisfactory response from this forum. Thanks for any helpful answers.
I think I have the answers to my own questions:
1. YES. Step 1 automatically assume eth0. There are TWO Ethernet interfaces and eth1 is disabled by default, and unless you use step 2 to set the management port this second Ethernet interface is never used.
2. No. I can't use the same IP address for both lines. In lower level 6 I need to use a different IP address on the same network 10.10.10.18 would work fine.
3. YES. It is correct. Lower level 6 assumes the network mask that I have included in the point 2.
4. it's tricky. There is NO WAY to configure Active/active on these tables. There are 2 controllers, but one "still asleep," unless the other fails. Actually, the IP address is assigned to an Abstraction Layer, it maintains. When fails another controller "awakens" and just starting to accept traffic and it doesn't care what its IP address.
Another point. Now that my table is initialized and my interfaces are configured, I need to know what IP address to point my ESXi hosts for their storage. Use the IP address of the group assigned in step 1. It is 192.168.101.11 (there is typo in the original post).
-
Check the ISE for the VPN Cisco posture
Hello community,
first of all thank you for taking the time to read my post. I have a deployment in which requires the characteristic posture of controls for machines of VPN Cisco ISE. I know that logically once a machine on the LAN, Cisco ISE can detect and apply controls posture on clients with the Anyconnect agent but what about VPN machines? The VPN will end via a VPN concentrator, which then connects to an ASA5555X that is deployed as an IPS only. Are there clues to this?
Thank you!
The Cisco ASA Version 9.2.1 supports the change in RADIUS authorization (CoA) (RFC 5176). This allows for the gesticulations of users against the ISE Cisco VPN without the need of an IPN. Once a VPN user connects, the ASA redirects web traffic to the LSE, where the user is configured with a Network Admission Control (NAC) or Web Agent. The agent performs specific controls on the user's computer to determine its conformity against one together configured posture rules, such as the rules of operating system (OS) patches, AntiVirus, registry, Application, or Service.
The posture validation results are then sent to the ISE. If the machine is considered the complaint, then the ISE can send a RADIUS CoA to the ASA with the new set of authorization policies. After validation of the successful posture and CoA, the user is allowed to access internal resources.
-
Number of COA and Vista express upgrade - MODUSLINK
I finally managed to get hold of someone at Moduslink on my request to upgrade to vista now show invalid. It seems that I gave the wrong number of COA from the recovery disk came with the laptop. NO, this isn't what they want - they want one on the sticker of microsoft on the bottom of the laptop that starts with a triple 000.
If you gave a wrong number then you will have to contact them on 00800 666 44 666 and they erase the application and you can re apply after 24 hours and, hopefully, everything should work. Be prepared to wait a while on the phone that they are very busy. According to them, if all goes well, then the product should be sent in time 4-6 weeks.
Hi Gordon
Thanks for sharing this info with us. I remember that someone has asked for the number of COA.
The number of COA starts with 000 :)
It might be useful for others who want to upgrade Vista -
Mail on El Capitan has problem with answer and respond to the
I just upgraded from Yosemite to El Capitan (10.11.2) on my MacBook Pro 15 in late 2008, and everything seems to work fine (so far) with this exception.
When I try to reply to a message, a message window opens with nothing entered. No to the:, no subject:, nothing in the body of the email from the original. Just empty in all areas. When I try to close the window with the red button, it does nothing, so now I have a useless window I can't close. I can fill in the To and subject to the fields, but when I try to tab or the mouse in the body of the email, the cursor disappears.
My only way to dispel this is so close to what point mail accidents. I have attached the crash debugging information below.
Does anyone know why it would act this way? I looked at the symptoms and have rebuilt my Inbox, but continues to be the same thing. Any suggestion would be appreciated. Clearly, I can't be the only one to experience this.
Thanks for your help,
Dana
Mail Crash problem Details:
Process: Mail [5900] Path: /Applications/mail.app/Contents/MacOS/mail Identifier: com Apple.mail Version: 9.2 (3112) Update information: Mail-3112000000000000 ~ 1 Code type: X 86-64 (native) Parent process: ??? [1] Responsible: Mail [5900] ID of the user: 70 s Date/time: 2015-12-27 15:48:56.189-0800 OS version: Mac OS X 10.11.2 (15 C 50) Report Version: 11 Anonymous UUID: ADF110C8-9D0A-27F4-E6CF-7D03D74A4136 Sleep/wake UUID: 13378DBA-6987-4A23-B7D5-6B5725129890 Time since started awake: 37000 seconds
Wake time: 1 200 seconds Integrity of system protection: enabled
Discussion crashed: 16 send queue: NSOperationQueue 0x7f9a5d870f20: NSOperation 0x7f9a5da03ae0 (QOS: LEGACY) Exception type: EXC_CRASH (SIGABRT) Exception codes: 0 x 0000000000000000, 0 x 0000000000000000 Note the exception: EXC_CORPSE_NOTIFY Request for clarification:
Reason for termination due to an untrapped exception 'NSInternalInconsistencyException' app,: "this method should be called on the main thread.
Abort() called
ending with an exception uncaught of print type
I use the response and answer all several times a day every day and have not seen an accident as you mention.
Any chance you can post the log of crash _entire_, rather than just the beginning of it?
-
Seeking clarification on the SFD in AKM Brushless Servo Drives
Dear members,
I'm looking for clarification on the smart feedback device (SFD) installed in the series of servomotors AKM. There is little information available on this subject in the specifications. It appeared that it offers a very high resolution, information on the position of the rotor high precision signals.
1. how exactly is the PCG provides the position of the rotor?
2. is there a provision to contract low resolution effect Hall of EPD type feedback?
Thank you.
Ansari07
Hi Ansari07,
I don't think that this level of control is possible with the AKD. The reader is supposed to close its own current loop on board for the control of switching and outputs of phase. The AKD offer couple, speed or modes of control position, and you can talk to it by Ethernet on the service port, via a field such as EtherCAT or CANOpen bus, or with an analogue signal +-10V or step/dir commands.
I don't think you can get around all of the internal firmware in the AKD and get direct control of how current passes through the phases.
Best regards
Nate
-
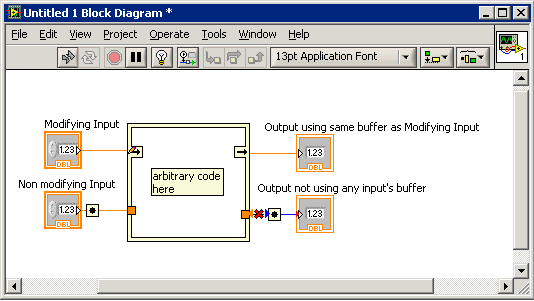
Threading and reuse of the node to call using reference of buffers (of the required adhesive tape)
I tried to get the following information in the public domain for years and now that I have the answers, I'll share with those who might be interested.
Caveat!
Wrap your head in tape before reading just for the sake of security.

My two questions were;
(1) may LV re - use tampons of VI calling when you use VI serve call by reference?
(2) is used when the use of call by reference UI thread?
1 when you call a VI using the call through the reference node, the data in the pane of the copied or is node connector - this online as it would be with a Subvi properly implemented?
Short answer: it's somewhere between the two.
Long answer:
The compiler does not know what will be called VI, but there a hint:
the reference connected to the node of the call by reference. He uses to get the 'Prototype' for the call. Therefore, for optimal performance, use a prototype that has the same 'characteristics placeness' as it is called VI. That said, users don't know what are the "characteristics of the placeness.
Before getting into the details, I will say that the overhead of these copies should not matter much unless it's a large data structure (a table with lots of items.) or a cluster/class with many fields or containing large networks etc..
Example 1:
If the prototype does not change the data, then the compiler assumes that the crux of the call by reference will not alter the data. However, at runtime, a check is made to see if the real called VI will modify the data. If Yes, then a copy is made and past so that the original data can be modified.
Example 2:
If the prototype contains an entry that is wired through an exit so that both input and output terminals can use the same buffer memory, but running an audit determines that the real called entry and exit VI do not share a buffer, then a copy will be made from output of the actual call to the original screws (combined input and output) buffer.
I should also mention that, even with this behavior "are trying to get along with the prototype", it is not always possible to obtain good performance as a Subvi ordinary call. For example, if you have a situation where the prototype does not change the data and passes it through to an exit and then the compiler must assume that the data is changed (because, as in example 2, there are screws that may change even if the called real VI is not).
And there are a few caveats:
(1) this behavior "using a prototype" was new for 2009. Before that, we used a method more naïve data of passage that took all the entries will be changed and no outputs don't share a buffer with an entry.
(2) this behavior can be changed in future versions, if we find additional optimizations.
(3) this behavior is the same that we use for the dynamic distribution live (when you use the classes in LV)
(4) If you want to create a VI can be used as a prototype, you can use the features of the Structure in Place to control the "characteristics of the placeness', namely the element nodes in and out of the border, the function"Mark as modifier"border nodes (note the pencil icon on the item), and the node always one copy.
(5) the prototype is only the first reference ever connected to the node of the call by reference. So if you make a new prototype VI, you can just make a reference out of it plug into the crux of the call by reference. I suggest to remove the node from the call by reference and file a new.
(6) for remote calls, we still "making copies" by transmitting data over a network.
I hope that this helps, if you want information/clarification, so feel free to ask.
2 - is the call made by the reference to run in the user interface thread node? If the call is made by a remote machine via ethernet, thread that host (the computer that makes the call by reference) runs on and thread that executes the target (the machine that contains the file VI) on?
In the case of premises, the appeal made by the reference node does not require the user interface thread and may work in some thread the VI wants to run in.
When you call a remote VI, the appeal made by the reference node uses the UI thread (detailed below) on both the client and the server.
The client uses the UI thread to send the request to the server and there still when the response comes back. The user interface thread is not blocked during the time between the two.
The server receives the TCP message in the UI thread, and then starts the call to the UI thread. The server also uses the user interface thread to send the response to the client. The user interface thread is not blocked on the server during execution of the VI.
I hope that people find it when they need it!
Ben
-
I have XP Pro 32 bit COA and I need to download & install XP Pro 64 bit
I have XP Pro 32 bit COA and I need to download & install XP Pro 64 bit
Please I need the link to download
Thank you
Cannot be done. The 32 bit license that comes with your PC is valid for a copy of 32-bit Windows.
Maybe you are looking for
-
So my 5s will not store all photos taken with the built-in Photo App. I can shoot and store the video with the built in app but no pictures. If I use the photo taking function in the Facebook app, the phone will take and store the image in the area o
-
Windows 7 does not load on the laptop. Satellite L series
Not sure what happened all of a sudden with my laptop, but it does not load windows. This is the error msg I get: Intel UNDI, PXE - 2.0 (build 083)Copyright (C) 1997-2000 Intel Corporation For Atheros PCIE Ethernet Controller v2.0.0.9 (15/12/09) Chec
-
Specific blue screen stop error Code
Hello. I have a Dell Inspiron 6000, running Windows XP Home edition 2000 (SP3). I had Norton Internet Security for years, so the registry is checked every day, with some minor repairs may be needed. Didn't need to defragment (less than 1% fragmented
-
How cut you the boot of Lenovo music?
I thought it would be embarrassing to start in class because of this awkward air it plays. This isn't music from windows, which I turned off. It's the Lenovo screen music. Thank you.
-
Interconnection SFP SFP + and XENPAK / X 2
Is it possible to connect: SFP + and XENPAK / X 2, for example 10 G-FPS-SR (Cat2960X or Cat3560X) and XENPAK - 10 GB - SR (Cat6500) or X 2-10 GB-SR (Cat3750E)? SFP + and SFP, SFP - 10 G - SR (Cat2960X or Cat3560X) e.g. and GLC-SX-MM (Cat6500 or Cat37