Comments on a different IP traffic
I have a NSA 4600. I have my comments on X 3 wireless traffic: V20. X 4 is my WAN Interface with a static ip address of x.x.x.161. I want to lead the Internet traffic of the network comments on an ip address different x.x.x.162. They are on the same subnet, so it won't let me create a new interface. Any ideas?
You will need to set up a NAT policy for this.
ORIGINAL SOURCE: subnet X 3 - V20
TRANSLATED from the SOURCE: x.x.x.x162
ORIGINAL DESTINATION: all
TRANSLATED DESTINATION: Original
ORIGINAL SERVICE: no
TRANSLATION SERVICE: Original
INCOMING INTERFACE: X 3 - v20
Coming OUT of the INTERFACE: 1 X (or whatever interface you use to the WAN)
Kevin
Tags: Dell Tech
Similar Questions
-
Import comments btw two different PDF files
I have a shared PDF file. I need to import a few of the comments provided in this PDF file to the next iteration. The documents may change in the next iteration to a certain extent. Is there is far from import these comments in the section/location of the next generated PDF file?
When you import comments, they appear in the same place as in the original. If the text changed location which is not serious, because they comments are in no way "connected" with the underlying content of the file.
-
Connect comments on a different network than the host
Hello
I just started to use VMWare instead of Virtual PC, and I'm stuck trying to do something that I used to have the installer.
I want to be able to connect to a virtual computer to a wireless network and independent of the host connection. In this case, the host will not be connected to a WLAN network, but the virtual machine will be.
Is this possible?
Thanks for any help.
Not regarding virtualization, I suspect unless you remove the .inf and .pnf files in the folder %systemrot%\inf of the guest for the VMware NICs and and add IDs PCI of its .inf file for the .inf for your wireless card that you have copied to here and also change the drivers referenced in the .inf for your wireless card file to be the VMware ones. Not tried this, just a theory and not a beautiful there :|
Guy Leech
VMware vExpert 2009
---
If you have found this device or any other answer useful please consider the use of buttons useful or Correct to award points.
-
ASA - that allows HTTP return traffic?
Hello
I'm just playing with a few ASA and ask yourself which allows return HTTP traffic in the firewall? Also, what other traffic is allowed by default as HTTP?
Traffic is from a security interface upper (inside, 100) to a lower (outside, 0) security interface. There is no ACLs not applied on all interfaces.
I ask because ICMP does not work unless inspection is on (global service-policy global_policy).
Thanks for any help.
Firewalls like ASA is with State so for TCP and UDP (albeit with UDP State is handled a little differently) if traffic is allowed a way it automatically allows him back.
So, when a connection is initiated, if it is permitted through the firewall that is recorded in the table of the State and when the return package arrives at the firewall level, if there is a matching entry, the traffic is allowed and there is no verification of the acl.
Registration is made on the IP source and destination port numbers, and for TCP it has also used the connection indicators.
ICMP uses ports so initially, that she could not be redirected and you had to allow him to return with an acl (if the traffic was less than the increase security level).
But then stateful inspection has been added for ICMP, as well, but you still must activate it Unlike TCP and UDP.
Jon
-
Cisco MSE 8510 MCU - comments PIN does not work
Hello
We have a few conferences on 8510 blade. Each conference is the main AXIS and the comments set up PIN. When I dial in the Conference, main SPINDLE works fine but the PIN prompt does not work.
I tried to deal with the PIN of an endpoint, then the guest PIN from the other end, but the Conference does not accept the feedback PIN. I can use the good main SPINDLE on the two end points.
Anyone know what may be the issue?
I just tested this without 8510, no problem at all.
Can you give us a screenshot of the configuration of your conference?
I had used the same digital ID for Chair and comments, with a different PIN for each. When I connected as Chairman, I went straight in. When I connected as a guest, I went straight in, but I got a quick saying saying President to arrive or to connect.
-
Requirements of the mobility for the comments of anchor WLC group
Hello-
I always assumed that you cannot create a tunnel between a local WLC and an anchor WLC comments that are in different groups of mobility. However, I was told recently (no more details) that it is possible. So I put to test this.
I'm trying one of my local WLCs SSID comments point to an anchor of WLC comments in a different group of mobility. I have a forthcoming maintenance window and I'm looking to anchor clients on a campus at anchor WLC on the campus on the other for the customer service does not lower. Each campus is that it's mobility group. Trying to set up I went to the "mobility anchors" screen for the SSID guest on one of the local WLCs and I cannot add anchor WLC on campus on the other because it is not in the drop-down list. This is because it is not in the same mobility group. So my question is how do customers of anchor across a local WLC in a group of mobility to a WLC anchor in another group of mobility?
To me it seems not possible without major configuration changes. I don't want to reconfigure / rebuild mobility groups.
Thank you
Chuck
Not only is it possible, that I recommend. However, you can be confusing to some concepts.
The mobility group is different from that of the field of mobility. Generally, I am referring to group mobility as these WLCs with the name of the default mobility group and the field of mobility than the entire list of mobility (where you can set up to 72 controllers belonging to various groups of mobility).
The point is that GroupA and WLCs of to WLCs 1-10 11-20 are GroupB, anchor to work, you at least need to add anchor to the mobility list wlc abroad and vice versa.
If you notice, when you add an entry of mobility to the list, it should ask you for mobility group. If you leave this field empty, it must default to that of the WLC, but on controllers GroupA, you could define GroupB controllers (and specific group b) and then you should now have the mobility between your controllers and configuration of the anchor will be your anchor in the menu...
Who is?
-
Private network between hosts in different regions
Dear guys,
I have just asked me if it would be possible that 2 hosts in different regions (EU-NA) can communicate on a virtual private network over the Wan.
How to perform I thought to arrive at:
-import the host NA in a cluster in the EU vcenter
-create a tmp DVS and attach 2 guests to the DVS
-create a private VLAN GP and configure 2 virtual machines with this PG = > they just have to communicate with each other, this is just a test
The question I have is this: given that the 2 hosts are in different regions, traffic of 2 VMs would go across the WAN using the DVS even?
Thanks in advance.
Daniele
I thought on it and it is not possible, DVS and a dummy network, we have L2 and we have no tools for the encapsulation of L2 to L3, I have no NSX.
I will give points me
Daniele
-
Migrating Forms 10g GR 11, 2 different host
Hi all
I'm Migrating Forms 10 g to 11 GR 2. I read a document for upgrading forms 10g to 11 GR 2, but there is no comment about the different host upgrade.
Also, there is only one way for the upgrade. Who is using "upgrade wizard".
Currently, here is my situation.
- I use forms 10g now on the server A.
- I installed 11 GR 2 forms on server B. It works well.
- There are a few files of forms compiled on ServerA.
- I want to migrate these forms and the configuration files in the server A to Server B.
If I can't use "upgrade wizard", I just copy the configuration files two server (formsweb.cfg and default.env) and paste the B server configuration files. But I think that it is not good idea to migrate.
Is there something else easy way and security for the upgrade.
Please answer to me thanks!
Let me start with the urgent comment: do NOT copy the configuration of earlier versions and drop them in the new environment. It's a bad idea for many reasons. The most obvious is because new version has new settings and changes, some of which are required.
I hope that, in your environment to version 10 you does not alter the [default] section of formsweb.cfg. If this is the case, then you can easily copy your sections in the file of the new version. However, before you do anything like that, make sure that you stop the Server Admin v11 and Managed Server (WLS_FORMS). Don't try to do it with them running or your changes likely will have lost to ignored. The default.env should be similar. You can replace the one-for-one entries, but do not replace the entries found in the file. Thus, for example, you can copy your old FORMS_PATH and drop it into the new file. Comment out the existing and use your instead. And so on.
OK, we can all calm down now.
The next thing to address is this statement "...". compiled form files on server A... ». You can also copy forms of update modules / generated from one version to the other. You need to rebuild 'X' (fmx, mmx, plx) of files in the new environment, using the new compiler.
As for using the upgrade wizard, there are some limitations to use, needing to be on the same machine. However, despite everything, my recommendation is that not use you it anyway. In most cases, you will have more success and much easier to maintain the environment if you do things manually. AU is especially useful when you have significant customizations and complex throughout the battery (SST, Web Cache, forms, reports, etc.). For typical configuration changes, manually create the new that's going to be the way to go. It will give you also a chance to clean by removing changes made previously which are no longer needed.
-
Captivate 8 Drag and Drop several legends of text for your comments
Hello
I am creating an interaction with an element with which the learner can drag for four different images representing the different categories of data classification. The idea of the interaction is for the learner to discover each of the four different categories, by trial and error. I want them to provide comments through text captions that the answer is right or wrong, but each piece of comments will be different and the user should be able to drag the item several times until they found the right answer. I can't fwork how to do this.
I just upgraded to Captivate 8 week last, after having previously used Captivate 5. Therefore, I've never used the installation drag - déposer and I don't know if he's going to do what I'm trying to achieve or if it's something I could achieve with shares advanced instead, or if it is not possible to do. I tried searching for similar topics, but either did not understand the answer or scenarios seemed different. I don't really know where everything is still 8 Captivate, and while I have used certain actions in Captivate 5 tip, I'm not that comfortable with them, so simple is good. The interaction doesn't have to be reported on.
Is anyone able to help me please?
Thanks in advance for your help.
Hello
According to my understanding, you have a source element that can drag and drop on 4 different targets (different images). For every drop of a sort of legend should appear on stage the feedback to the corresponding user from the target source. (Correct me if I'm wrong)
This can be achieved with Drag and drop interaction.
1. Insert the source 4times and overlap each other (since you can drag and drop 1 number 4 times, you must have this element to work as a source of slippage 4 up to 4 items).
2. make the 4 elements as drag source and group them into a single type. (With the help of add option)
3. you have your 4 images on stage and Mark as targets of drag.
4. Insert the rear power legends and put them near their targets. Disable their 'Visible output' flag on Bill pro forma.
5. now match the Correct ANS on stage.i.e of one of the source type to a target correct years.
6. Select each target and open their box "Actions of the object". (from Panel drag / move)
7. uncheck the ' accept all the ' option and the value of count 1. Add the action of 'travel' to show their legends of Feedback now under Drag source Type. (which were hidden). This should be through "Advanced Actions.
8. now after for each target open the dialog box 'Good years' drag and drop the Panel. (it will be under options and so visible from the source or target is selected)
9. here under the table, you can see that the value of count is 4. This is to reduce the value to 1. (double-click to change)
Interaction is now ready. Please don't answer if that's what you wanted to achieve and if you do all the steps above.
Derrick
-
Owner MBP - audit 'stealth mode '.
Under Firewall of MBP, I checked "automatically allow signed software to receive incoming connections. In addition, "block all incoming connections", and "Enable stealth mode" is unchecked. Should I check "Activate the stealth mode" and if so, how will that affect software updates?
It is a comment on why you might, or might not, to use the firewall Applicationintegrated.
The firewall is blocking incoming network traffic, regardless of the origin, on a per-application basis. By default it is off, and when activated, allows digitally signed by Apple and that applications applications, listening on the network. It does not block outbound traffic, it can distinguish different incoming traffic sources, nor it filters content traffic.
No matter how it is configured, the firewall is not, as some imagine, a malware or privacy filter. If that's what you expect it to do, we forget. All it will do is bombard you with unnecessary alerts.
Consider scenarios in which you might expect the firewall to be useful.
1. you turn on file sharing, and you allow the guest access to some records. This means that you want people on your local network, but not foreigners, to be able to access these folders without having to enter a password. In the default configuration, the firewall will allow that to happen. The router prevents foreigners access to actions, if the firewall application is activated or not. But if your laptop and connect to an untrusted network as a public access point, the firewall will still allow access to anyone, that is not what you want. It does not protect you in this scenario.
2 install. you a Trojan horse that steals your data and download on a remote server without knowing it. The firewall, no matter how it is configured, does not block outgoing traffic. It does nothing to protect against this threat.
3. a more likely scenario: the web browser or the router is compromised by an attacker. The attack redirects all web traffic to a fake server. The firewall does not protect against this threat.
4. you use a public web server. Your router passes requests for TCP connection on port 80 on your Mac, and connections are accepted by the built-in web server, which is work together by Apple. The firewall application, always configured as described above, will do this. An attacker hacks into the system and tries to divert port 80 and to replace the web server integrated with that determines itself. The good news is that the firewall will protect you; It blocks incoming connections on the malicious server and notifies you. But the bad news is that you have been rooted. Forward who can do these things can just as easily turn off the firewall, in which case it does not protect you after all.
5. you spin a Minecraft server on the local network. It listens on a high-numbered port. You, as an administrator, have reconfigured the firewall to pass this traffic. A hacker can connect to a standard account on the server. It figures how crash Minecraft, or he's waiting just as leave you it, and it then binds his, malicious, Minecraft server to the same port. The firewall will block its server, and because he is not a Director, he cannot do something. In this scenario, the security is genuine.
6. here's a more realistic scenario in which you might be right to turn on the firewall. Your MacBook has the share of active services. You want to have these services available to others on a home network or desktop. When you are on these networks, the firewall should be turned off. When you move to an untrusted network, you can disable all services, or turn on the firewall with a default configuration to block. Blocking is easier: a simple click instead of several.
-
Airport Extreme - poor score from Consumer Reports
In the notes of June 2016 of routers by Consumer Reports, the Apple Airport Extreme was ranked 7th of 14 rated routers.
Linksys (EA8500) AC260 ranked 1st with an overall Score of 89
The Apple Airport Extreme ME918LL/A 7th place with an overall score of only 67 & wasn't 1 of 4 routers "recommended" by Consumer Reports.
I have currently 2 5th generation Apple Airport extreme with the 2nd 1 put in place as an 'extension' of the 1st (hard wired).
Am currently in the market for an Apple Airport Extreme 3rd - also to be used as an 'extension' of the 1st (also to be wired).
I had years of service with my current 2 extremes without any major problems.
But, I must say, this weak side causes me to rethink the purchase of one 3rd extreme.
In addition to an Apple 6 more belonging to both myself and my wife and one old iPad 3 belonging to my wife, I don't have any other products Apple. I use Dell computers & have never owned a Mac.
The qUESTIONs ARE:
Should I worry about buying the new Apple Airport Extreme Base Station?
The Appreciation of Linksys #1 is $60 more ($240) that extreme already expensive ($180).
Is - it's worth the extra $$$?
Different brands of routers can be 'mixed' and used as in "extensions" of a 5th generation Apple Airport Extreme Base Station?
Should I worry about buying the new Apple Airport Extreme Base Station?
Perhaps. The current product was introduced more than 3 years ago, and Apple did not of any material changes since that time. Because it usually takes about a year to develop a new product, the technology in the "current" AirPort Extreme is probably 4 years old.
Your next question might be... Apple plans to introduce new models soon? The answer is that we do not know.
The Appreciation of Linksys #1 is $60 more ($240) that extreme already expensive ($180).
Is - it's worth the extra $$$?
I have not used this model, but another user might have a few comments.
Different brands of routers can be 'mixed' and used as in "extensions" of a 5th generation Apple Airport Extreme Base Station?
Yes and no.
Yes, if the routers are only connected together using a connection wired Ethernet cable.
Not in general, if you ask to have different brands "extend" the signal of wireless connection to other brands
-
Cannot install the driver update WLAN on tecra M2
Dear Sir.
I wanted to install the update of the wlan driver intel 2200 BG on a tecra M2: when I want to run the installer it says: "impossible to recover all of the adapter-specific information to perform installation operations: the following file is not found: C\:documents and settings\...\...\SetupWLD.ini.
Anyone have a solution?Thanks in advance
Dr. weekx R
Hello
I read many comments on the different problems with Intel card that you have. If you have any problems and WLAN works perfectly maybe it will be better to leave and don t no matter what. :)
-
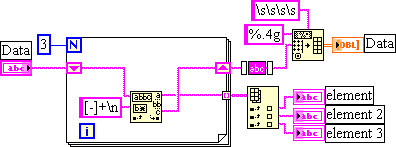
How to read a combination of strings and data data file
Hello
I'm having the combination of strings and datas to read a data file. I'm reading the file name, the time constants and comments in four indicators separate string (lines for comments varies for different files). And read the data in a 2D array. How can I do this? Y at - it a function that can serch of special characters in the spreadsheet file, so I can locate exactly where I should start reading the specific data. Here's how the data file is displayed. Thank you very much.
Best,
Richard
filename.dat
14:59 12/31/2009
--------------------------------------------------
Sample = 2451
Frequency = 300, time of waiting = 2500
Temperature = 20
--------------------------------------------------
a few comments
a few comments
a few comments
a few comments
a few comments
--------------------------------------------------7.0000E + 2 1.5810E - 5
7.0050E + 2 1.5400E - 5
7.0100E + 2 1.5500E - 5
7.0150E + 2 1.5180E - 5....
Here's a (big) hint.
I would like to give you an excerpt, but I've not updated this machine yet. It's a pretty boring delimiter, if you know what's good for you, you start to use commas, tabs or simple spaces (my order of preference). It is far too easy start add or remove spaces and then you need to use more complex methods to obtain data from worksheet.
-
ID in a virtualized environment
Can someone develop an IDS solution for a virtualized environment?
I have ESX/ESXi - highly virtualized blade servers. IM using the blade passes under chassis e/s - no pass-through.
The requirement is to run a service IDS such as VM-on-VM traffic is controlled. The traffic flow can be between two virtual machines on the same blade, 2 virtual machines on two separate blades in the same chassis, or two separate virtual machines on two hunts...
In this case, I see 3 streams of traffic off of the bat...
blade even: vm-on-vm traffic is enabled by a hypervisor type switch (vDS 1000v or vmware).
different blades in the same chassis: vm-on-vm traffic will leave blade and can be set by hardware chassis (blade chassis I/O) switch.
different chassis: vm-on-vm traffic will have to go to ToR (maybe same end of line).
NOTE: If the VMs are on different VLANS, traffic will always be at the end-of-line/agg switches (the limit of L3/L2).
So, given all of these possible flows, what is the best way to go about deploying IDS service? Implementation? Virtual or physical? etc...
Thank you!
You're right, dragging the flow of vm virtual machine out of the box for the inspection of the IPS and stuffing then reconnect will be a bottleneck of bandwidth. I doubt that it would cost you more CPU to move these pieces sttings to launch an IPS sensor inside the box (ala Sourcefire).
To minimize the bandwidth bottleneck, you can add Ethernet interfaces to your ESXi server and even to group several togther if you need more bandwidth, a single pair can offer.
-Bob
-
Hi all
What are the criteria for determining whether to use the local network VIRTUAL auth failure or the guest VLAN?
What happens if a non - 802.1 x client connects to the port, tell a seller... 802. 1 x does not occur, then is he then comments crossing vlan?
What happens if a salesperson brings a 802. 1 x PC capable and connects it... the identification fails, but I want the seller to go in the VLAN comments in any case, I could give them a temporary user name / maybe PW to authenticate with? Hmmm...
Thanks in advance.
Hello
The local network VIRTUAL Auth-Fail is called if an Access-Reject is received from the Radius Server to the
authentication of the user or machine. The local network VIRTUAL Auth-Fail will be called after a certain number of failures
not after the first failure of authentication. It is a configurable value.
The VLAN comments is called otherwise EAPoL traffic comes from the customer who connects.
You can set the VLAN Auth failure and the VLAN comments on the same VLAN ID if you want to
users who have disabled begging him or a person with invalid credentials (or no credentials).
-Jesse
Maybe you are looking for
-
Follow links do not change after you have visited... out no grizzled.
In the past few days I noticed that when I click on a link on my regular web pages, the links do not appear as having been followed.
-
Problem strange battery over 4 days old Satellite L750
Hi all I just brought a new labtop 4 days ago and the battery seems to have a problem. The battery takes 16 hours full of 99%. In the Toshiba PC health monitor, it shows battery health decline full 'good' to 'just' and still going down... Did you guy
-
Hello just unpacked my new z370 entered without bones. Just installed win7 Home premium and searched here full driver package... but there is only video drivers! can u tell me where I can find the full driver package? Thanks in advance XSnailX
-
HP Envy Notebook PC 4-1110us: plugged in, does not support
" Is my model of laptop ' HP Envy 4-1110us laptop "so that I can't remove the battery from the laptop. My battery is displayed 0% but when I connect it to the charger it does not load. Based on electric energy to work. If I remove the charger will st
-
Good afternoon friends... I have the RV042 router, I use that one single Connection Internet, I use the intellectual property of the group like this 192.168.95.x, my DHCP implementation using 192.168.95.120 to 192.168.95.240, but at this moment I hav