Compromise Possible WTR54G
Could someone there answer for me. I changed the default router name used WAP security with a combination of number of very complex words to generate the SSID and activated filtering to allow only my laptop by address MAC access to the network. All of a sudden, I was unable to access the network or to the internet from my laptop. No matter what I did, the wireless network is not found.
I went into properties of the router and changed the security word and saved settings and everything worked fine.
Does this mean that my system has been hacked?
Well, once you are connected to your wireless network, there are (the wireless network profile) profile which is stored or backed up automatically to allow you to connect when you perform a reboot... You do not have to enter one of your network credentials more and you stay connected to your wireless network... If you are disconnected from your wireless network (perhaps a reason any) and you try to re - connect to your wireless network, you can no longer connect to it unless you delete your network profile which was origially stored when you first connected to your wireless network... Once the wireless network profile is removed you can select your SSID, tap on connect, enter your network key etil again connects, this is how it works...
However, after you change the SSID of your thought laptop which was a new wireless network and why has it connected to the new SSID with no problems...
Next time if you face the same problem please do.
For XP:
Click Start and goto the control panel and double-click on network connections, right click wireless network connection and click Properties.
Now, in this window, click on the second tab of wireless network and give a check mark on "use windows to configure my wireless" and then delete all network names present in the preferred networks window. Then click OK...
Right click on the wireless again network connection and then click View available wireless networks and try to re - connect to your network...
Now, it will give you the opportunity to put the network/wep key, make sure that you enter the correct network key and confirm...
It will connect...
For Vista:
Click Start > Control Panel > Network and Sharing Center > manage wireless networks, here to remove any present network and close the window.
Click on connect to a network and try to re - connect to your network, he must ask for your key/password network, enter the network and password correct key and click on connect...
It needs to connect... Once you're connected, you must restart the computer, it needs to connect to the Internet...
Tags: Linksys Routers
Similar Questions
-
I never had a problem with hotmail until now. I've been blackened compromise possible secruity. I was told my password has been cancelled and apply for another. Unfortunately if necessary my old password submitted to receive a new. When I finally found a way to recover by using the same address as before, but with a new password to my email that I had saved from the beginning had disappeared. Where at - it go? Insult to injury, I just received my first two emails from my windows live account. One was a spammer, that's why I was told I have locked in a first time, and the other was microsoft answers thank me to register but don't sponsor not why my email is apparently sent to another address. I said to visit the options I have. Futile. There must be a response and I believe that when I find what is wrong, it will be something simple but neglected. Something like a breach in Protocol that we all followed which allows for compatibillity between competeing components so that the computer can work with cohesion and with little delay. Kind of like internet explore works well with active x, but the msn does not work. All ducks must be in a line, and I'm afraid m9ne maybe not. I need a convenience store. I sent an e-mail to a friend here in my living room, and she has not received it. I had a friend in Detroit send me one yesterday he he not arive. My other three email accounts work perfectly? Weird. If you have any ideas I could try, it will be greatly appreciated. Thank you, Dusty
Hello
The question you have posted is related to windows live account and would be better suited to the community of windows live. Please visit the link below to find a community that will provide the support you want.
-
Expensive of Mozilla:
Every so often, characters Kanji happen on my browser tabs. I was in Okinawa for a year. They disappear once I closed and reopened. What is the cause? Image attached event.
Victory,
Sean SullivanThe extension of McAfee SiteAdvisor has been reported to cause problems with Chinese characters (CJK) text on tabs, so that you can disable this extension until McAfee publishes an update to resolve this issue.
- How to uninstall SiteAdvisor:
http://service.McAfee.com/faqdocument.aspx?ID=TS100162
See also these SUMO son:
- How to uninstall SiteAdvisor:
-
iMessage of my mam but she didn't type or something! I need help as soon as POSSIBLE.
I received an iMessage of my mam, who has an iPhone 4 (last update as of 26/08/16), saying 'can't talk right now... what's up?' and she claims that she didn't send the message to me and that his phone was turned off when this message has been sent. She's even scared on itself. By pure cautiosness, I blocked the number of my mam but iMessage sent his e-mail. Someone hacked into his e-mail account? I need answers as soon as POSSIBLE and I'm afraid that his personal information was given without his consent.
Hi JessicaChitas,
I totally understand your concern to get a message that says: they do not send the sender. What you should have your mam do first, is to change the password ID Apple ASAP. You can then follow the steps in this link. If you think that your ID Apple has been compromised
Following the steps in this link should allow you all keep safety your Apple ID thank you account to use the Apple Support communities to post your question. Have a great day.
-
OK I play yoville and people use your web browser to the Winsock Packet Editor Pro program and whenever I try to take advantage of by some stupid zynga yoville uses your web browser to make aditor package winsock to unplug my player im so sick of this shit I'm working all day I exspect to come yo and enjoy my game not for some fool to use your web browser to do a work program and disconnect my Player with access to cdata people can also use wpe to enter other account with any password or username is it possible to stop this work programme in your browser to stop these hackers of compromising accounts and ruin the fun of games zynga Ty for your kind support and I hope that you can help stop this program work on your browser and different game browsers would be better for all
If you are meaning http://wpepro.net, this tool does not use Firefox in the slightest. It uses the TCP/IP (part of Windows) Protocol to monitor networks (it can also be used negative).
Please update your Firefox Firefox 11, because the version you use is vulnerable to many known security vulnerabilities. After you do this, try to see if your problem is still ongoing.
-
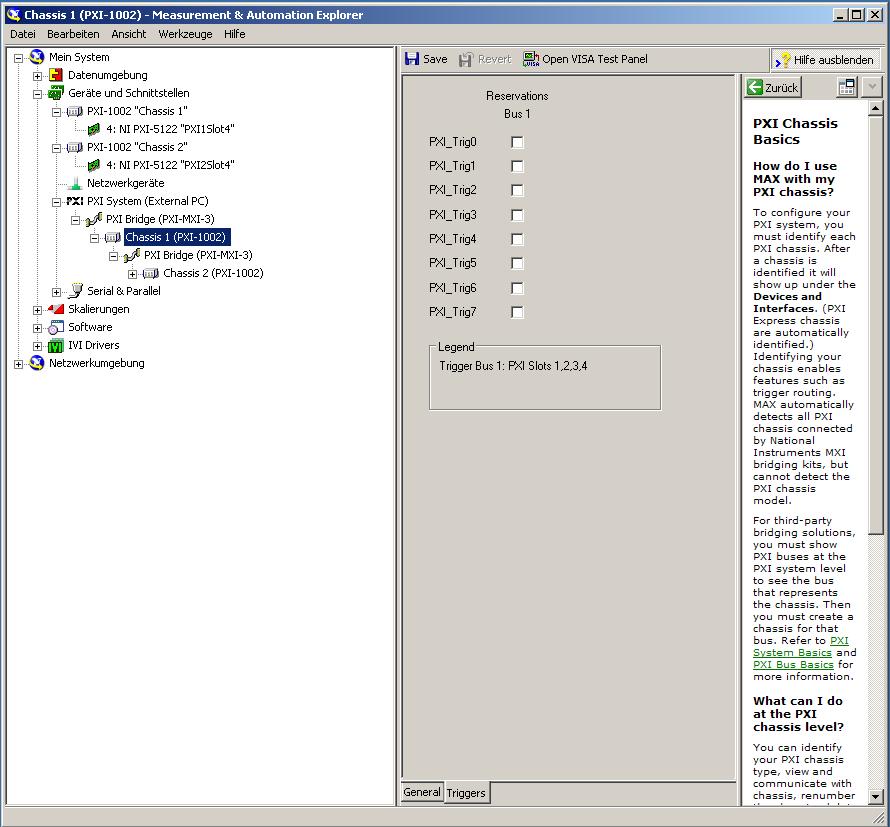
Is it possible to route signals of relaxation between two chassis PXI-1002 with the PXI-8335?
Hello
as the subject says, I am interested in the delivery of a signal to trigger between two chassis PXI-1002. At present, these two chassis are connected by a MXI - 3 system using maps PXI-8335. The software is Labview 2010 sp1 and 380 NIScope drivers.
We want to keep (a PXI-5122 by chassis) scanners supply separated due to the requirements of our measure! The chassis are connected via cable to fiber optic. This explains why I can not just use the shutter release in Star, or connect via 'Trigger' or 'clk' cards (the inputs / outputs to the front of the cards).
I found a few examples, but they seem to all be designed for use with a chassis only, I'll call later to the examples that inspired me to this point. Each guide explaining the synchronization of several chassis systems seems to use another material or VI is not accesible to me. This makes me wonder if my hardware has the capacibilities I need.
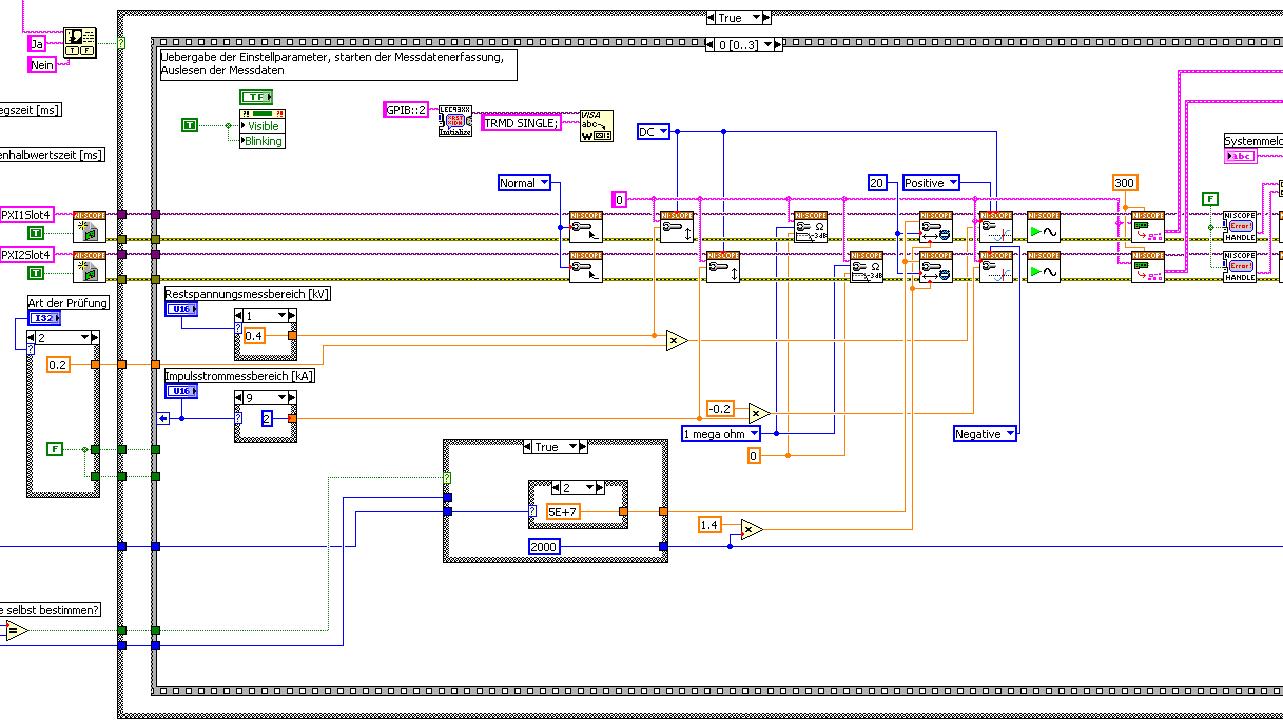
The first picture shows approximately where I started from (sorry I can't post VI, confidential...):
Only the middle part is interesting. Two sessions are initialized and manipulated parallel, trigger too. This has led to delays in the signals and should now be fixed. This apart from the VI works fine.
Goal is to trigger only on one channel but both devices! If possible, the device will trigger must be chooseable.
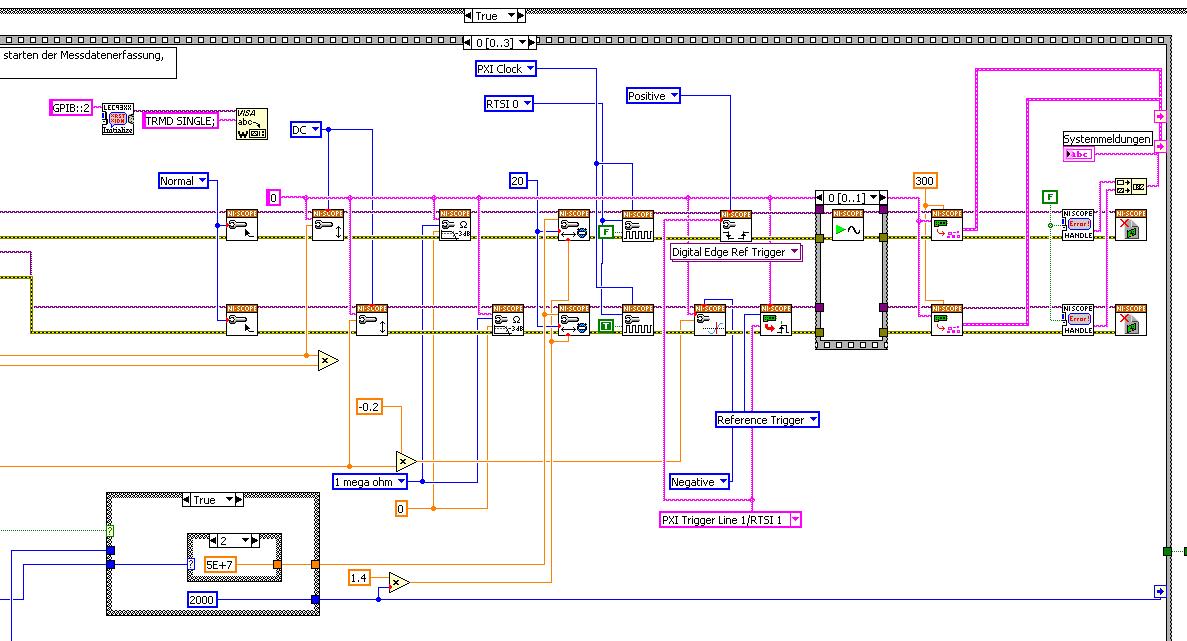
I started to rebuild the VI using the "EX Synchronization.vi 5xxx niScope' seeming spontaneity. The result is shown in the following image:
I tried different RTSI lines, but had no positive results. only the main channel has triggered.
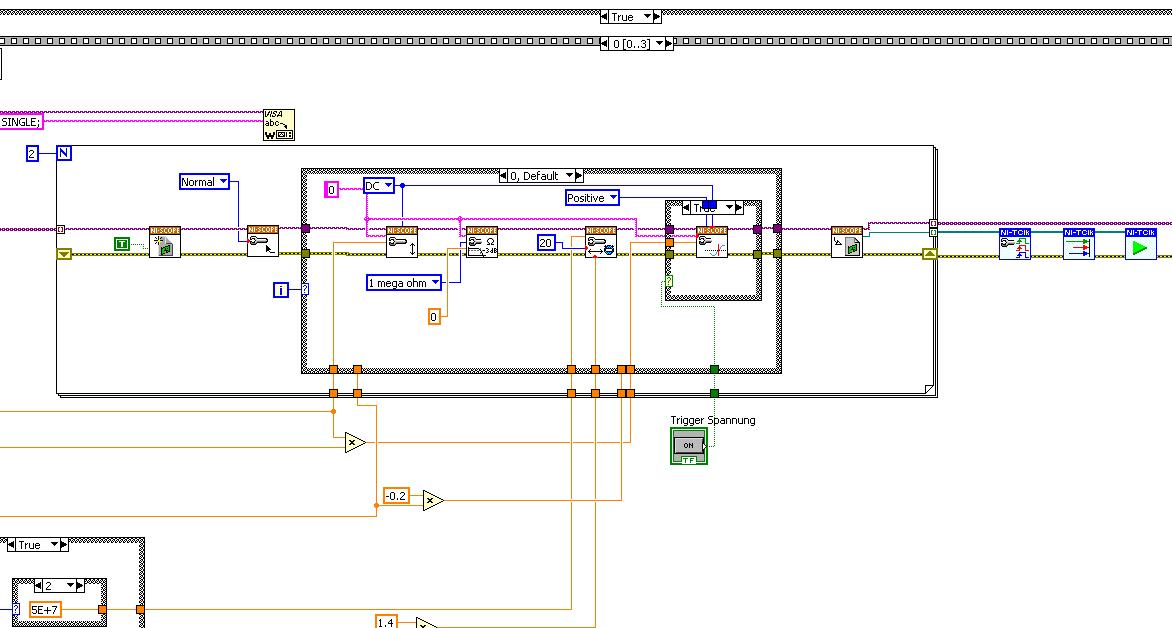
After this first approach, I looked in the "niScope EX .vi multi-Device configured Acquisition (TClk)" and other examples of TClk which seem to work for similar problems. The VI of reconstruction can be seen in the following images:
(Sorry, I had to use two photos..)
In this case, I didn't have no choice for trigger lines, it would automatically set the VI TClk. I tried to trigger on both devices, though. This second approach seemed promising to me, but it was an error:
"niTClk Synchronize.vi:1".
Index (starting at zero) of the session: 1
The error reported by the pilot of the instrument:
No registered trigger could be found between the
devices on the route.If you have a PXI chassis, the chassis correctly identify in
MAX and make sure that it has been configured correctly. If you use PCI
devices, make sure they are connected with a RTSI cable and that the cable RTSI
is saved to the MAX. Otherwise, make sure that there is an available trigger line
the trigger bus shared between devices.Source device: PXI1Slot4
Target unit: PXI2Slot4
Status code:-89125niTClk Synchronize.vi:1
Index (starting at zero) of the session: 1
The error reported by the pilot of the instrument:
No registered trigger could be found between the
devices on the route.If you have a PXI chassis, the chassis correctly identify in
MAX and make sure that it has been configured correctly. If you use PCI
devices, make sure they are connected with a RTSI cable and that the cable RTSI
is saved to the MAX. Otherwise, make sure that there is an available trigger line
the trigger bus shared between devices.Source device: PXI1Slot4
Target unit: PXI2Slot4
"Status code:-89125"
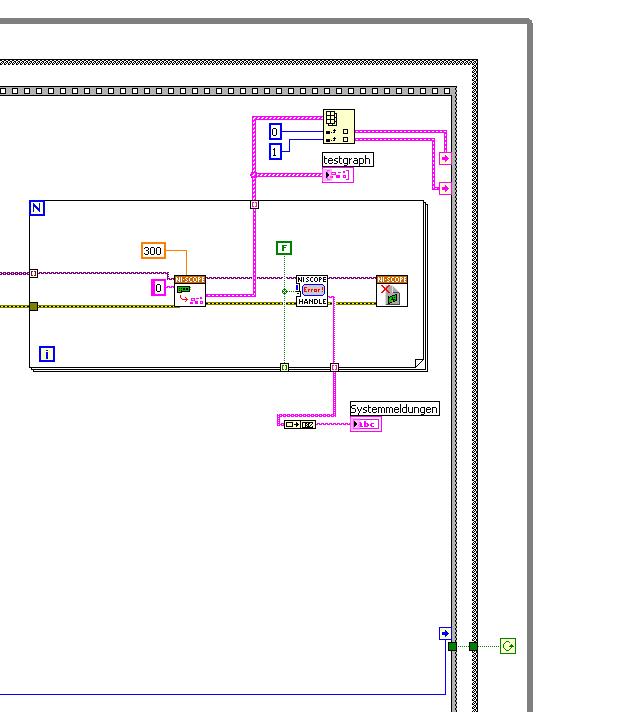
This error came back even after I've identified this drug as possible to the MAX, as shown in the screenshot:
In some of the textbooks, they showed how to get the MAX trigger lines, but as you can see, there is only booking options in my MAX. Whatever I do, I can't find options to define how to get my trigger signals...
In principle, it is possible to trigger instruments in different chassis, which is indicated in this Guide and others... the question that remains is can it be done with my set of components?
I understand that the use of multichassis compromised the integrity of the lines very adjusted as trigger in Star etc., so the configuration should be taken into account in some way, that my approach does not, I knew... But there must be a way to do this? And to start: to get just any signal from one device to the other trigger!
For any advice on this issue, I would be very thanfull!
Concerning
Max1744
Hi Max,.
Thanks for the detailed post and explanations of your application and requirements. You're right using TClk, because this is the optimal method to synchronize the 5122 digitizers. The original VI you worked with is unique for some of the legacy scanners and does not directly work with scanners based on the most recent CMS (for example the 5122). The good news is that you can synchronize these cards to separate chassis, but it will use the calendar 66xx and synchronization (T & S) cards in the chassis of the master and the slave, as indicated in the guide that you have accessed. These are needed because a common reference clock must be shared between them as well as a couple of tripping. MXI itself can not handle export triggers and clocks, so there is no way to do this without physically wiring between the chassis with cards T & S. Unfortunately, regardless of what specific method, you use for synchronization, it will take a material extra beyond what you currently have.
As one of your needs looks like it is necessary to retain wiring between the chassis directly, you may need to consider to synchronize using 1588 or GPS protocols. 1588 Protocol is a system for synchronization on the network while GPS course use antennas and locks for a common wireless signal. Although these synchronization methods may allow you to keep your chassis isolated, they will also require some manual configuration because you would be able to use the TClk synchronization and so the level of synchronization you can get between the cards may not be as good that can physically wire signals between the chassis using T & S cards.
Hope this helps,
-
Account compromised Hotmail - password reset does not work!
A few days ago my account Hotmail "sent" emails to all my contacts, even if the emails are not in my sent items folder. To prevent this from happening again, I installed antivirus software and also deleted all my contacts from Hotmail. I could access the account for a day or two, but now, without warning, I can not access my TI at all. When I try to log on I get a screen "your account has been blocked. I have a second email address, to which I ask a verification code sent to unlock my Hotmail. When I enter the code, I get a screen "Reset your password". I have reset a strong password and save, then resubmit my secondary e-mail address, then continue. I wonder for a phone number as another option of password recovery, but I ignore this screen and click on continue. I get then tell screen ' authorized error 401 - no server: access denied due to credentials not valid. You are not authorized to view this directory or page using the credentials you provided "."
Makes no sense to me!
I installed Avast antivirus and Microsoft Security Essentials but neither picked up a virus on my system.
Help, please! I really need to access my account!
Hello
First of all you must have a significant anti-virus program on the computer at one time much
less running. Even if disabled they will always load parts of themselves into a memory that
can cause strange issues while actually reduce safety. Even the remains of a
uninstalled antivirus may cause problems.Uninstall Avast or MSE (both are excellent)
Avast uninstall tool http://www.avast.com/eng/avast-uninstall-utility.html
MSE clean uinstalls without a removal tool
---------------------------------------------------------------------------------------------------------------
Answers is a peer group supported and unfortunately has no real influence on Hotmail.
HotMail has its own Forums, so you can ask your questions there.
Windows Live Solution Center - HotMail - HotMail Forums Solutions
http://windowslivehelp.com/
Hotmail - Forums
http://windowslivehelp.com/forums.aspx?ProductID=1Hotmail - Solutions
http://windowslivehelp.com/solutions.aspx?ProductID=1How to contact Windows Live Hotmail Support
http://email.about.com/od/hotmailtips/Qt/et_hotmail_supp.htmWindows Live Hotmail Top issues and Support information
http://support.Microsoft.com/kb/316659/en-usError message "your account has been locked" when trying to connect
http://windowslivehelp.com/thread.aspx?ThreadId=77be7d82-a0e9-49c7-b46d-040ec654a9e2Compromised account - access unauthorized account - how to recover your account
http://windowslivehelp.com/solution.aspx?SolutionID=6ea0c7b3-1473-4176-b03f-145b951dcb41Hotmail hacked? Take these steps
http://blogs.msdn.com/b/securitytipstalk/archive/2010/07/07/Hotmail-hacked-take-these-steps.aspxIf we had the same problem that we would have to use the links above and these methods.
===========================================================
More information:
If someone is Spoofing emails that appear to come from you then they probably never
had access to your e-mail account. Instead, they have either a copy of your contacts
list or just an email from you or one of you where you were one of the recipients. Those
could be gleaned either your computer, the computer of a friend, or hacking
any site or intercept an email on your behalf or to you (you may not be the main)
(beneficiary).Once they have this information there is nothing you can do to avoid that they don't
send usurped messages. Warn your friends that is happening and they
can be entitled to install rules such as parodies are treated as SPAM or JUNK
mail.I've even seen usurped by email that appears to be from a valid user name however
This name doesn't have an e-mail account on the mail system used in parody.
As SpiritX - AT - realmail.com may be a valid account, however, parody used
SpiritX - AT - wrongmail.com. The latter could still be considered an email address valid
SpiritX if it was allowed through JUNK and JUNK e-mail filtering. (The - AT - has been used
instead of so that those addresses would not be filtered by auto responses.
as if by magic.)============================================================
Proceed to a very thorough check for malware and then change your password by e-mail.
The reason why you want to do this is to make sure no more hacking your computer is
still in effect (if it has been hacked). You have changed the password once but I would
Change it again after these checks.It is possible for a person to send the email that 'seems' to be of your
account but that is not really - called "Spoofing." That means its 'Possible' emails
were not really you, although they may have your contact list. Have someone
who receives the e-mails to check the header to see where he is actually sent by and
NOT only the answer to the address.How to read the message headers
http://www.emailaddressmanager.com/tips/header.htmlWhat Email Headers can tell you about the origin of Spam
http://email.about.com/cs/spamgeneral/a/spam_headers.htmE-mail spoofing
http://en.Wikipedia.org/wiki/E-mail_spoofingE-mail spoofing and Phishing
http://www.mailsbroadcast.com/email.broadcast.FAQ/46.email.spoofing.htmUnderstanding E-mail Spoofing
http://www.windowsecurity.com/articles/email-spoofing.htmlFraudulent emails (false)
http://pages.eBay.com/education/spooftutorial/Google search - email Spoofing
http://www.Google.com/search?hl=en&EI=FB1nS9DiNo7CsQPNhKGdAw&SA=X&Oi=spell&resnum=0&CT=result&CD=1&ved=0CAgQBSgA&q=email+spoofing&spell=1=============================================
If you need search malware here's my recommendations - they will allow you to
scrutiny and the withdrawal without ending up with a load of spyware programs running
resident who can cause as many questions as the malware and may be more difficult to detect as the
cause.No one program cannot be used to detect and remove any malware. Added that often easy
to detect malicious software often comes with a much harder to detect and remove the payload. Then
its best to be thorough than paying the high price later now too. Check with them to one
extreme overkill point and then run the cleaning only when you are sure that the system is clean.It can be made repeatedly in Mode safe - F8 tap that you start, however, you must also run
the regular windows when you can.Download malwarebytes and scan with it, run MRT and add Prevx to be sure that he is gone.
(If Rootkits run UnHackMe)Download - SAVE - go to where you put it-right on - click RUN AS ADMIN
Malwarebytes - free
http://www.Malwarebytes.org/products/malwarebytes_freeRun the malware removal tool from Microsoft
Start - type in the search box-> find MRT top - right on - click RUN AS ADMIN.
You should get this tool and its updates via Windows updates - if necessary, you can
Download it here.Download - SAVE - go to where you put it-right on - click RUN AS ADMIN
(Then run MRT as shown above.)Microsoft Malicious - 32-bit removal tool
http://www.Microsoft.com/downloads/details.aspx?FamilyId=AD724AE0-E72D-4F54-9AB3-75B8EB148356&displaylang=enMicrosoft Malicious removal tool - 64 bit
http://www.Microsoft.com/downloads/details.aspx?FamilyId=585D2BDE-367F-495e-94E7-6349F4EFFC74&displaylang=enalso install Prevx to be sure that it is all gone.
Download - SAVE - go to where you put it-right on - click RUN AS ADMIN
Prevx - Home - free - small, fast, exceptional CLOUD protection, working with others
security programs. It is a single scanner, VERY EFFICIENT, if it finds something to come back
here or use Google to see how to remove.
http://www.prevx.com/ <-->
http://info.prevx.com/downloadcsi.asp <-->Choice of PCmag editor - Prevx-
http://www.PCMag.com/Article2/0, 2817,2346862,00.aspTry the demo version of Hitman Pro:
Hitman Pro is a second scanner reviews, designed to save your computer from malicious software
(viruses, Trojans, rootkits, etc.). who infected your computer despite safe
what you have done (such as antivirus, firewall, etc.).
http://www.SurfRight.nl/en/hitmanpro--------------------------------------------------------
If necessary here are some free online scanners to help the
http://www.eset.com/onlinescan/
-----------------------------------
Original version is now replaced by the Microsoft Safety Scanner
http://OneCare.live.com/site/en-us/default.htmMicrosoft safety scanner
http://www.Microsoft.com/security/scanner/en-us/default.aspx----------------------------------
http://www.Kaspersky.com/virusscanner
Other tests free online
http://www.Google.com/search?hl=en&source=HP&q=antivirus+free+online+scan&AQ=f&OQ=&AQI=G1--------------------------------------------------------
Also follow these steps for the General corruption of cleaning and repair/replace damaged/missing
system files.Run DiskCleanup - start - all programs - Accessories - System Tools - Disk Cleanup
Start - type this into the search-> find COMMAND to top box and RIGHT CLICK-
RUN AS ADMINEnter this at the command prompt - sfc/scannow
How to analyze the log file entries that the Microsoft Windows Resource Checker
(SFC.exe) program generates in Windows Vista cbs.log
http://support.Microsoft.com/kb/928228Run checkdisk - schedule it to run at the next startup, then apply OK then restart your way.
How to run the check disk at startup in Vista
http://www.Vistax64.com/tutorials/67612-check-disk-Chkdsk.html-----------------------------------------------------------------------
If we find Rootkits use this thread and other suggestions. (Run UnHackMe)
I hope this helps and happy holidays!
Rob Brown - Microsoft MVP<- profile="" -="" windows="" expert="" -="" consumer="" :="" bicycle="" -="" mark="" twain="" said="" it="">
-
My Hotmail account has been compromised and sends spam to all my contacts!
I want to delete this account. I went through the steps to remove and it says "account closed" but it is always send spam to everyone on my contact list.
Hello
Proceed to a very thorough check for malware and then change your email password (If
the account is still very active).It is possible for a person to send the email that 'seems' to be of your
account but that is not really - called "Spoofing." That means its 'Possible' emails
were not really you, although they may have your contact list. Have someone
who receives the e-mails to check the header to see where he is actually sent by and
NOT only the answer to the address.How to read the message headers
http://www.high-speed-Internet-Access-Guide.com/articles/email-headers.htmlE-mail spoofing
http://en.Wikipedia.org/wiki/E-mail_spoofingE-mail spoofing and Phishing
http://www.mailsbroadcast.com/email.broadcast.FAQ/46.email.spoofing.htmUnderstanding E-mail Spoofing
http://www.windowsecurity.com/articles/email-spoofing.htmlFraudulent emails (false)
http://pages.eBay.com/education/spooftutorial/Google search - email Spoofing
http://www.Google.com/search?hl=en&EI=FB1nS9DiNo7CsQPNhKGdAw&SA=X&Oi=spell&resnum=0&CT=result&CD=1&ved=0CAgQBSgA&q=email+spoofing&spell=1=============================================
Answers is a peer group supported and unfortunately has no real influence on Hotmail.
HotMail has its own Forums, so you can ask your questions there.
Windows Live Solution Center - HotMail - HotMail Forums Solutions
http://windowslivehelp.com/
Hotmail - Forums
http://windowslivehelp.com/forums.aspx?ProductID=1Hotmail - Solutions
http://windowslivehelp.com/solutions.aspx?ProductID=1How to contact Windows Live Hotmail Support
http://email.about.com/od/hotmailtips/Qt/et_hotmail_supp.htmWindows Live Hotmail Top issues and Support information
http://support.Microsoft.com/kb/316659/en-usCompromised account - access unauthorized account - how to recover your account
http://windowslivehelp.com/solution.aspx?SolutionID=6ea0c7b3-1473-4176-b03f-145b951dcb41Hotmail hacked? Take these steps
http://blogs.msdn.com/b/securitytipstalk/archive/2010/07/07/Hotmail-hacked-take-these-steps.aspx=============================================
If you need search malware here's my recommendations - they will allow you to
scrutiny and the withdrawal without ending up with a load of spyware programs running
resident who can cause as many questions as the malware and may be more difficult to detect as the
cause.No one program cannot be used to detect and remove any malware. Added that often easy
to detect malicious software often comes with a much harder to detect and remove the payload. Then
its best to be thorough than paying the high price later now too. Check with them to one
extreme overkill point and then run the cleaning only when you are sure that the system is clean.It can be made repeatedly in Mode safe - F8 tap that you start, however, you must also run
the regular windows when you can.Download malwarebytes and scan with it, run MRT and add Prevx to be sure that he is gone.
(If Rootkits run UnHackMe)Download - SAVE - go to where you put it-right on - click RUN AS ADMIN
Malwarebytes - free
http://www.Malwarebytes.org/products/malwarebytes_freeRun the malware removal tool from Microsoft
Start - type in the search box-> find MRT top - right on - click RUN AS ADMIN.
You should get this tool and its updates via Windows updates - if necessary, you can
Download it here.Download - SAVE - go to where you put it-right on - click RUN AS ADMIN
(Then run MRT as shown above.)Microsoft Malicious - 32-bit removal tool
http://www.Microsoft.com/downloads/details.aspx?FamilyId=AD724AE0-E72D-4F54-9AB3-75B8EB148356&displaylang=enMicrosoft Malicious removal tool - 64 bit
http://www.Microsoft.com/downloads/details.aspx?FamilyId=585D2BDE-367F-495e-94E7-6349F4EFFC74&displaylang=enalso install Prevx to be sure that it is all gone.
Download - SAVE - go to where you put it-right on - click RUN AS ADMIN
Prevx - Home - free - small, fast, exceptional CLOUD protection, working with others
security programs. It is a single scanner, VERY EFFICIENT, if it finds something to come back
here or use Google to see how to remove.
http://www.prevx.com/ <-->
http://info.prevx.com/downloadcsi.asp <-->Choice of PCmag editor - Prevx-
http://www.PCMag.com/Article2/0, 2817,2346862,00.aspTry the demo version of Hitman Pro:
Hitman Pro is a second scanner reviews, designed to save your computer from malicious software
(viruses, Trojans, rootkits, etc.). who infected your computer despite safe
what you have done (such as antivirus, firewall, etc.).
http://www.SurfRight.nl/en/hitmanpro--------------------------------------------------------
If necessary here are some free online scanners to help the
http://www.eset.com/onlinescan/
-----------------------------------
Original version is now replaced by the Microsoft Safety Scanner
http://OneCare.live.com/site/en-us/default.htmMicrosoft safety scanner
http://www.Microsoft.com/security/scanner/en-us/default.aspx----------------------------------
http://www.Kaspersky.com/virusscanner
Other tests free online
http://www.Google.com/search?hl=en&source=HP&q=antivirus+free+online+scan&AQ=f&OQ=&AQI=G1--------------------------------------------------------
Also follow these steps for the General corruption of cleaning and repair/replace damaged/missing
system files.Run DiskCleanup - start - all programs - Accessories - System Tools - Disk Cleanup
Start - type this into the search-> find COMMAND to top box and RIGHT CLICK-
RUN AS ADMINEnter this at the command prompt - sfc/scannow
How to analyze the log file entries that the Microsoft Windows Resource Checker
(SFC.exe) program generates in Windows Vista cbs.log
http://support.Microsoft.com/kb/928228Run checkdisk - schedule it to run at the next startup, then apply OK then restart your way.
How to run the check disk at startup in Vista
http://www.Vistax64.com/tutorials/67612-check-disk-Chkdsk.html-----------------------------------------------------------------------
If we find Rootkits use this thread and other suggestions. (Run UnHackMe)
I hope this helps.
Rob Brown - Microsoft MVP<- profile="" -="" windows="" expert="" -="" consumer="" :="" bicycle="" -="" mark="" twain="" said="" it="">
-
I can move emails from one folder to another, but is it possible to move an entire folder to another folder?
Hello
I'm sorry, but we cannot help you with Hotmail issues in this Feedback Forum for answers
Please repost your question in Hotmail in the Hotmail Forums the link below
http://windowslivehelp.com/product.aspx?ProductID=1
ForumsConsult with Microsoft Certified Solutions____________________________________________For the different Forums for Windows Live Applications, select the link belowWelcome to Windows Live Solution Center -
need to get password for the other by e-mail as soon as possible please help
Hello
Are you referring to Hotmail?
If so read the information below:
for further information, repost your hotmail question in the forums of hotmail in the link below and read the information contained in this response on the reset of your password
http://windowslivehelp.com/product.aspx?ProductID=1
ForumsConsult with Microsoft Certified Solutionsreset your Windows Live ID password "If you are unable to remember your Windows Live ID password, you can request a password reset online.You can reset your password by using the password reset page and selecting the appropriate option. Note that each option will provide you with a reset of your password link
- Click Reset your password provided by the selected link.
- Type your Windows Live ID.
- Type the characters in the image, and click Next.
- You will receive a list of delivery options based on the password reset information we partner on behalf of Live ID.
- Send me that a reset link will be send to that a password reset message to all the e-mail addresses associated with your Windows Live account.
- Send a code for my mobile phone will send a code number on your mobile phone. You will need to enter the code in the web form and continue through the password reset process.
- Use as my trusted PC automatically starts the password resets streams.
- Customer support will take you to our validation process where you will be asked a number of questions about your account to prove your ownership.
- We take seriously the security of account and passing the validation process can be difficult. Agents to follow strict guidelines on validate the information you provide. The validation process is pass or fail. The agents will not inform you on what information is correct, incorrect or missing. This process is to prevent hackers help to engineer social access to your account.
- The secret to pass the validation process is to provide more information as possible. Your information is more accurate, more you have chances to pass validation.
- Answer as many questions as possible.
- Provide more specific information that you can. For any question that can have many answers, answer 3 to 5 instead of 1. An example of this would be records Hotmail, Messenger, contacts or e-mail subject lines.
- In the unfortunate case that the account has been hacked and changed information, agents will validate ownership of account based on information associated with the account before the compromise. Thus, you should use the information that you believe that you had attached to the account even though you know it has changed.
- Finally, if an agent responds with a failed validation, then add additional information to the existing rather than create a new folder. This will allow agents to aggregate the information you provide, they can make it through many cases.
Please note that to reset your password by Email, SMS or Trusted PC, requires that you have updated your Windows Live account with this information.
You can set your password reset information by logging into your account and update the password reset information section.
For more information on the configuration of your password reset information go here.
If you are unable to access your account for any other reason, please visit our issues page, Windows Live, Hotmail and Messenger Service sign of problemsof connection.
UN-update not possible to boot
I stupidly allowed MS to upgrade my system. After 92 updates, he forced a reboot that failed completely. I got the normal safe mode, Windows, everything is hundy dory options, but none of them work. Like a wanker, I re-installed XP Pro from my (SP3) CD and now I is even more a possible restoration.
If someone has suffered this explosion of bomb cluster munitions, or am I just lucky?
Let's cut to the Chase. See...
Cleaning a compromised system
http://TechNet.Microsoft.com/en-us/library/cc700813.aspxPersonal data backup (which none should be considered 100% reliable at this point) then format the HARD disk and do a clean install of Windows. Please note that give repair install (upgrade AKA on-site) will NOT fix it!
HOW to do a clean install of Windows XP: see method 1 and http://michaelstevenstech.com/cleanxpinstall.html#steps in http://support.microsoft.com/kb/978307
Once installed the clean, you will have the equivalent of a "new computer" in order to take care of everything on the next page before connecting the machine to the internet or one local network (i.e. other computers) otherwise and before connecting a flash drive, card SD or any other external disk to the computer:
4 steps to help protect your new computer before going online
http://www.Microsoft.com/security/pypc.aspxOther useful references include:
HOW to get a computer that is running Windows XP Gold (no Service Pack) fully patched (after a clean install)
http://groups.Google.com/group/Microsoft.public.windowsupdate/MSG/3f5afa8ed33e121cHOW TO get a computer that is running Windows XP SP1 (a) or SP2 fully patched (after a clean install)
http://groups.Google.com/group/Microsoft.public.WindowsXP.General/MSG/a066ae41add7dd2bTip: After getting the computer fully patched, download/install KB971029 manually:http://support.microsoft.com/kb/971029
NB: No matter what Norton or McAfee free trial which is preinstalled on the computer when you bought will be reinstalled (but invalid) when Windows is reinstalled. You MUST uninstall the trial for free AND download/run the removal tool appropriate prior to installing the updates, Windows Service Packs or IE upgrades AND BEFORE installing your new anti-virus application (which will require WinXP SP3 must be installed).
Norton Removal Tool
FTP://ftp.Symantec.com/public/english_us_canada/removal_tools/Norton_Removal_Tool.exeMcAfee Consumer product removal tool
http://download.McAfee.com/Products/Licensed/cust_support_patches/MCPR.exeSee also:
Risks & benefits of P2P file sharing
http://www.Microsoft.com/protect/data/downloadfileshare/filesharing.aspx
http://blogs.technet.com/MMPC/archive/2008/10/06/the-cost-of-free-software.aspxMeasures to help prevent spyware
http://www.Microsoft.com/security/spyware/prevent.aspxMeasures to help prevent computer worms
http://www.Microsoft.com/security/worms/prevent.aspxAvoid fake security software!
http://www.Microsoft.com/security/antivirus/rogue.aspxIf you need help, please start a new thread in this forum: http://social.answers.microsoft.com/Forums/en-US/xprepair/threads
Good luck!
~ Robear Dyer (PA Bear) ~ MS MVP (that is to say, mail, security, Windows & Update Services) since 2002 ~ WARNING: MS MVPs represent or work for Microsoft
An old e-mail address is permanently removable which has been compromised?
my e-mail address 'live' as compromised. I now use a new hotmail address. Is it possible to permanently remove my old address of the system
View all Windows Live and Hotmail questions in the appropriate forum found here:
http://windowslivehelp.com/Apparent compromise Windows XP operating system files
During a scan, antiviral regular which was initiated by the provider of the antiviral software, the scan did not work properly (i.e., it is still indicating that the scan is in progress, but nothing happens - no status progress which is now 50 + hours). Contact the vendor of the antiviral software, they gave me the steps to perform a disk cleanup and then a reboot of the mode without failure followed by steps to remove TEMP files. At halfway through the disk cleanup process, a pop-up window has stated that: "Windows - files required for Windows File Protection is running properly have been replaced by unrecognized versions.» To maintain system stability, Windows must restore the original versions of these files. Insert your Windows XP Professional Service Pack 3 CD now. "The Windows disks have not inserted according to the instructions, but instead, I contacted the antiviral software vendor to make sure that there is no unintended consequence. The software provider antiviral indicated that Microsoft should be contacted as there can be some files that have been compromised that stopped the disk cleanup. Windows XP (version 2005) operating system was pre-installed by the company of Toshiba laptop. Question: I should restart the disk cleanup process as described by the antiviral software provider, and if there is another popup window indicating the information as mentioned above, service pack of Windows XP CD should be inserted? Note: I was told Toshiba CD provided by them for the laptop contains the Windows XP operating system software. The two provided Toshiba CD entitled, "Recovery and Applications/drivers DVD Satellite A100/A105 Series." Question: Are there possible negative conseguences because the provided CD/DVDs have possible applications and drivers on them? Thank you.
Friend Software
Hello
· What is the name of the antiviral software that you use to run the virus scan?
· You have security software installed on your computer?
Check out the link that contains information about what is protection of files below. Link: Description of the Windows File Protection feature: http://support.microsoft.com/kb/222193
1. I suggest to run the auditor of system files on the computer, you can check the link below: Description of Windows XP and Windows Server 2003 System File Checker (Sfc.exe): http://support.microsoft.com/kb/310747
2. during the file system check scan if you are prompted to insert a CD Windows XP SP then you can follow the steps from the link below:http://support.microsoft.com/kb/900910
3. once the Analysis System File Checker is complete. You can run Disk Cleanup.
With regard to:
Samhrutha G S - Microsoft technical support.
Visit our Microsoft answers feedback Forum and let us know what you think.
Problems of Virus and security possible - Win32/PowerRegScheduler
Operating program: XP Home edition
Model: Samsung N140
Question: The problems of security and viral infection
Hello
I'm sorry that I don't really have a great understanding of the computer virus so I don't know what information is relevant. I think most of what follows suggests an infection by the virus:
I recently updated my free version of AVG Anti-Virus Free in the new 2011 edition. During installation, it has encountered an error (I don't remember details, possibly missing dll files) so I decided to cancel, restart my laptop and try again. When my laptop from loading until he said that there was a problem one windows had begun a check disk on drive C. It became clear and if I booted up and installed the AVG software.
This seems to be the point at which the following problems started. It may have been independent, but it seems to me as an opportunity where my laptop's security has been compromised.
Since the installation, I have a number of security issues. I first noticed security warning balloon popping up at startup alert me that my firewall or my anti-virus software has been active in. I have not installed a firewall and account on the firewall of a security xp at this time. My laptop has anti-malware/spyware called "Spybot Search and Destroy". As mentioned earlier that my anti-virus is AVG Free edition. The firewall when checked reading disabled until the computer was nearing completion with respect to the start of all substantive programmes and anti-virus and anti-malware programs would read the same thing, are they loaded at all. (Also, I'm not sure if this is relevant, sorry again, but the menu at the top of the AVG Software bar flashes briefly when you hover over a button, briefly displaying a sign different menu under: S)
As I try to keep my computer up to date for all programs, I check the windows updates regularly. For the first two weeks (before the avg installation problems), I didn't have a problem, but more recently Windows Update stopped several times to answer once started and only after several attempts to close the program and then restarting it again it will work
After reading briefly on latest threats virus (Win32/Sality.AM, containing similar symptoms) I decided to use the Windows Live OneCare safety scanner. He detected a medium threat program: Win32/power Reg Scheduler. This program did not appear when I ran this scan before and nothing appeared on an AVG scan at all.
All the details are:
Program: Win32/power Reg Scheduler
c:\Program InstallShield installation information\ {f31bc49f-ab7b-4a53-a399-eb7331b585bc} \data1.cab
After a failed attempt to delete it also says:
detected: (inshld #0004)-[rsrcemb]
Any advice on how to remove the virus if it is indeed a would be useful and appreciated. I would like to use anti-virus software to remove it but the AVG software does not locate a problem and care scanner a Windows Live is unable to clean it up. If it does not seek to be a virus no matter what other help to solve security problems would be useful.
Thanks for any help and I'm sorry for the length of this article. I would like to shorten but I don't really know what that is and is not important.
MrPanda
What happened is that when the installation failed, left it "garbage" files that are trying to work, but can not function properly. These files are what caused the error that you are experiencing. My advice is first perform an uninstall of the avg anti-virus (I say this because to say what your first post, you had a corrupted/defective update of the old version (2010 I guess)). After uninstall you AVG AV, double check that all the avg files have been properly removed. After that, install AVG AV of the downloaded installation. Here is a link to the avg homepage, they have the free download on the cover page:
http://free.Avg.com/us-en/homepage
I hope this helps! If it isn't, feel free to write me at:
E-mail address is removed from the privacy *.
I'll do what I can to help out you.
I have a problem with 2 computers and its kind of a large. Hard to know where to start so I'll keep it short, but I think it may concern even Microsoft, because it involves the use of what I believe to be false "terms of service" or small print and I knew even where the source of this problem is, but I really need help! Myself and others use laptops we bought together. We live in a family, but laptops, a TOSHIBA and a HP/COMPAQ F700 satellite, as well as what I call a wireless router belong to the USA! We are connected through this wireless device, a PRISM which is perhaps a bit older, but of course seems to work, it is plugged into a modem cable motorola belonging to someone else in the House. To make things moving along, he came to our attention that A: our systems periodically change without our permission, by that I mean that the toshiba that was purchased at walmart brand new, came with an Intel Celeron, and I think THAT the wireless card IS an atheros brand. I KNOW that was the case with the Compaq regarding the wireless adapter, and Compaq was bought at a rent to own store and came with a 1 GB ram AMD processor. For some reason, we are under some form of control Admin, and our system is changing periodically on BOTH computers to say his family chipset intel and our wireless adapters will go to realtek USB 2.0, once again on BOTH computers. When this happens, our user accounts admin, that we had as an administrator user accounts AND I have unlocked the hidden via the cmd prompt and hold SHIFT + ENTER thing, will be signed in some way limit our ability to do things. LAST FEW DETAILS, I promise you: the so-called matrix memory of intel as magically appeared with software RAID of surveillance and we saw our event logs, which we prob didn't know existed, being transferred by a remote user, and we have never consulted the remote adjustment, except in order to turn them off, as well as file sharing options. However they continue to change when this happens. Yesterday, to finish that, I found strange things after doing a thing of complete system repair, not for the first time, this time on the compaq. After the repair, which seemed fine at first, I was embarrassed to find a few shortcuts readme present in the recently amended on the start menu folder. I followed them to the folder locations that led me to the prog. files, THE SIMS 2, and various subfolders with S.W.R. claiming to be from MICROSOFT and don't mention any particular O.S. except with reference to .NET and some virtualization programs that we noticed the menu running task. OH, I shouldn't forget that with the processor changes in both pc, THEY BOTH now say that they ar x 86 client or PC workstation and a recent attempt on the repair of the system or pressing f8 on the toshiba somehow led me to a weird command prompt which began with X : ?? I'm prob a few things set aside even if it is really long, but the SIMS 2 folder is very disturbing because a person who lives here once gave us a CD on an old computer that has not been used for at least 3 years and we have certainly not installed this game WE NEITHER of these new computers. I SUSPECT SOME things but don't know what to do. I TRIED to get our product off the coast of the TOSHIBA key but was said previously by a repairman it seems to have BEEN DELETED! The records in question, according to me, are always on both pc and we executed the software suggested, including microsoft security databases, s.s.and destroy, and the malewarebytes thing, as well as to have a repair shop gives us some tips. They said several things, like the toshiba tried to boot from the drive cd/DVD, then boot pxe or something and someone had changed the wake on lan option, and maybe other things I do not remember. OK SORRY FOR ALL this THAT REALLY, but I wanted to make sure that I gave as much information as possible because we never wanted our PC clone, virtualized, or something like that, whatever realtek usb 2.0 is, it's another icon of the wireless connection in the tray on the lower right AND THE COMPAQ is REMAINED CONNECTED WITH the off switch wireless? Help!
Thank you for your gracious reply. It certainly sounds to me like your computers are compromised. As I said, the only way to fix now is to restore as long as the plant once more after you back up your data and then set them up by the suggestions below. It costs you nothing but time. I'll also give you my general information on the configuration of the network wireless safely. Unfortunately, you must have control of the wireless router to do this. If you do not, then consider doing your own Internet connection and wireless router. Addition to the steps of General safety below, make sure that file/printer sharing is DISABLED.
The result of all this is to keep on the front of your mind is that security, physical access to a machine trumps all. If you do not trust the people with whom you live and/or people who visit them, you have to keep the computer with you or in a locked environment that no one else can enter. And of course the locks can be chosen. Or find the best people to live with. I understand that this is not possible in your real world, but I'm telling you all the options.Computer security - any computer running an operating system is accessible by a person with 1) physical access; (2) time; (3) jurisdiction; (4) tools of. There are a few things you can do to make it a little more difficult but:
1. define a password in the BIOS that must be entered before starting the operating system. Also to set the supervisor password in the BIOS so the BIOS configuration cannot be entered without it.
2. starting at the BIOS, change the order of boot to hard drive first.
3. set strong passwords on all accounts, including the built-in XP administrator account (it is disabled by default in Vista).
4. If you leave your own account connected, use Windows key + L to lock the computer (or set the screen/power economy saver) when you step away from the computer and require a password to use.
5. do the other accounts of users limited in XP Home, regular user accounts in XP Pro. All users must be on a Standard account in Vista with an administrator account (called something like 'Tech' or 'CompAdmin') only used for purposes of elevation.
6. If more than one person uses the computer user set permissions/restrictions:
If you have XP/Vista/Windows 7 Home, you don't have the built-in ability to create fine-grained limits. In XP and Vista, you can use the Security Console or MVP Doug Knox or the program MS SteadyState to set restrictions as you wish. SteadyState now supports Vista but not Windows 7. Mr. Knox security console may still work in Win7.
http://www.dougknox.com
http://www.Microsoft.com/Windows/products/winfamily/SharedAccess/default.mspx
Information about SteadyState - http://aumha.net/viewtopic.php?t=27570
SteadyState support - http://social.microsoft.com/forums/en-US/windowssteadystate/threads/
SteadyState How - to (not supported in Windows 7 still) - http://www.howtogeek.com/howto/6520/windows-steadystate/Please understand that these are technical answers to what is essentially a technical problem and there are ways around these precautions. It is a problem of family / interpersonal which cannot be solved by technical means.
Establishing a safe wireless router - have a computer connected to the router with an ethernet cable. Examples given are for a Linksys router. See the manual of your router or the router mftr's Web site. for the parameters by default if you don't have a Linksys. Open a browser such as Internet Explorer or Firefox and in the address bar type:
http://192.168.1.1 [Enter] (it is default IP address of the router, which varies from router to router then check your manual)
This will bring you to the login screen of the router. The default username is blank and the Linksys default password is "admin" without the quotes. Enter this information. You are now in the configuration of the router utility. Your configuration utility may be slightly different from mine. The first thing to do is to change the password by default because everyone knows the default passwords for different routers.
Click the Administration link at the top of the page. Enter your new password. MAKE A NOTE SOMEWHERE THAT YOU WILL NOT LOSE. Re-enter the password to confirm it, and then click Save settings at the bottom of the page. The router will reboot and show you the box of connection again. Do not fill in the user name and put it in your new password to enter the configuration utility.
Now, click on the link wireless at the top of the page. Change the network name (SSID) wireless by default to something, you'll recognize. I suggest that my clients not use their surname as the SSID. For example, you might want to name your network wireless network "CastleAnthrax" or similar. ;-)
Click on save settings and when you get the prompt that your changes were successful, click the wireless security link which is just beside the Basic Wireless Settings link (where you changed your SSID). Most computers purchased during the last 4 years have the wireless hardware that will support WPA2-Personal (also known as WPA2-PSK). This is the desired encryption level. If your wireless hardware is older, use WPA. Don't use WEP, because who is easily broken within minutes. So go ahead and set the Security Mode WPA2-Personal. Do this and enter a password. For example, you could use the password ' here be dragons, beware you scurvy dogs! The password is what you enter on all computers that are allowed to connect to the wireless network. MAKE A NOTE SOMEWHERE THAT YOU WILL NOT LOSE.
At this point, your router is set up and if the computer that you use to configure the router will normally connect wireless, disconnect the ethernet cable and wireless of the computer should see your new network. Enter the password that you have created (exactly as you wrote it with all capital letters and punctuation) to join the network and start surfing.
If you want to develop me on this or have any other questions, feel free to ask. MS - MVP - Elephant Boy computers - don't panic!
Maybe you are looking for
-
Is it possible to change the burner DVD drive on a 1900 303 satellite Player Recorder DVDs and CDs?If so it's just a dealer option, I'm pretty handy with this work, also what software would be necessary.
-
So I don't know if it's something that's arisen because of something I did, or something through updates. But I think I have basically a castrated command selection. I'm doing a secure Chat where anyone who is added into a candidate rather that just
-
Exhibiting in context sensitive help display bug
Hello I found a bug, but just didn't know where to report so I'm posting it here. (What is the suitable channel for bug reports)? When I wriggle-over "before software final Position" on the property of an axis node SoftMotion, context-sensitive help
-
The firewall of windows 7 actually works? I tried to block certain IP addresses; He does not
Original title: firewall The firewall of windows 7 actually works? I ask because I tried to block certain IP addresses; I created a rule for outbound custom where I entered the IP addresses and set it for all applications. However, when I go on a web
-
WIN8 - screen - blue DRIVER_OVERRAN_STACK_BUFFER
Separated from this thread. Mine does, too, but more often. At least once per 5 minutes or more. It's getting a bit boring and when I am able to connect quickly enough (and even when I have an open application or something that I'm trying or even ope