Defined by RADIUS split - include on SAA
We are in the process of migrating from a VPN architecture based on IOS AnyConnect SSL access to an ASA base.
Everything seems to work fine except for one thing. "We use a RADIUS defined by split - include to ensure that some users have access to only their networks using the cisco-avpair ' webvpn:split - include = #. #. #. # 255.255.255.0"which works well on the installation of IOS, but not on the ASA. I can verify that the AV pair is provided as part of the authentication process, the ASA (version 9.1 (6), btw) ignores and gives full access to the client using the ACL specified in the configuration.
Despite a few hours of googling and SEO Cisco AnyConnect ASA documentation, I find not a reference to this problem. I suspect that the AV pair in question is specific to the IOS, but impossible to find confirmation of this or the other.
Anyone encountered this?
Jody
Hi Jody,.
Looks like this pair of av is not available for ASA
http://www.Cisco.com/c/en/us/TD/docs/security/ASA/asa82/configuration/gu...
You can try to use
Cisco (AV) attribute value pair (ID # 26/9/1) as shown on the guide.
HTH
Averroès.
Tags: Cisco Security
Similar Questions
-
Cisco ISE: External RADIUS server
Hello
I send RADIUS of NHP NHP, another. I have already defined "External RADIUS servers".
So, how can I use this external RADIUS server to process my application?
Looking at the user guide, but did not find information on this parameter (for the rule after rule not simple)
Cela if anyone use this, please suggest me.
Thank you
Mathias
Please specify which version you are using. There were improvements to the functionality of the proxy in ISE 1.1.1
This can be used as follows:
-Define "External RADIUS server"
-Set the "Sequence of RADIUS server. This allows you to define a sequence of proxies that will send queries to until you get an answer
-In the authentication policy when the rules instead of the allowed protocols can select a "RADIUS server Sequence.
-
ISE Sponsor authentication via RADIUS
My client demand change us the way the sponsor users are authenticated and authorized to access portal Sponsor of ISE.
Their similar to the request of the ISE AD via a RADIUS server first. They said "avoid sending credentials of the AD to ISE directly. Under this condition,.
My research and limited knowledge give to assume I have to define a RADIUS Proxy
I think I can define an external RADIUS server, but I wonder if this creation, it would be available as a Source of identity for "portal Sponsor sequence.
If this is not the case, how can I add this? After that, what conditions or attributes should I look for to use in the 'strategy of group sponsor' in order to filter the name of user and password and allow access to employees and deny access to everyone?
I'd appreciate advice that you can give me to offer the best recommendation to the client.
Kind regards.
Daniel Escalante.
Hi sliman,.
Unfortunately, this document is not relevant to what Daniel is trying to achieve. There need to be able to refer to a RADIUS server as part of the Sponsor authentication process, that is not possible today. The only possibilities are that I have indicated in my original answer.
Richard
-
Remote VPN: split tunnel filtering
Hello!
The question is about the split tunnel filtering capabilities without using the vpn-filter.
Suppose, we have ASA configured for remote VPN tunneling with split without VPN filter.
- 10.0.0.0/8 is the private netwrok.
- 10.1.0.0/24 is the private network, defined in the split tunnel
- 172.16.1.0/24 is the VPN SECURE network
When the remote client connects, it receives the routes to the private network (10.1.0.0/24).
What happens if the remote client adds the route to a private network (which is not defined by a tunnel of split) by itself (e.g. 10.2.0.0/24)?
Our test LAB, we can see that the customer does not have access to 10.2.0.0/24.
Where the place in this case filtering?
- By default, all vehicles coming from VPN, bypasses all ACLs configured on interfaces ASA.
- Filter VPN is not configured.
- Nat0 don't traffic 10.0.0.0/8 to 172.16.1.0/24 NAT
- of the sh ip cry his on the VPN server, we can see, this ident is 0.0.0.0/0
- local ident (addr, mask, prot, port): (0.0.0.0/0.0.0.0/0/0)
- Remote ident (addr, mask, prot, port): (172.16.1.1/255.255.255.255/0/0)
The ACL of split tunnel is capable for remote client traffic filtering?
I understand that your question is in what regards the IPSec VPN Client, no AnyConnect VPN Client, however, I think that the behavior of the split tunnel is the same.
Here's the answer to your question:
A. AnyConnect applies the policy of tunnel in 2 ways:
Monitoring of track 1) and repair (for example if you change the routing table), AnyConnect will restore it to what has been configured.
(2) filtering (on platforms that support filter engines). Filtering ensures that even if you can perform a kind of injection of the route, the filters would block packets.
-
Accounting session via radius or syslog AnyConnect?
Hello
Someone at - it a method of accounting deployed to save Anyconnect session details? Are you a radius server or via recording messages to a syslog server?
If Yes can help you with the appropriate configuration? I seeks to save authentication successful and failed and duration of the session, connect and disconnect times.
I've been playing with Anyconnect is authenticating to AD via ACS 5.1 but can't seem to get the accounting details, I need. Similarly, I tried to catch the appropriate syslog messages but once again without much success.
Thanks a lot for any input, St.
What what you have configured for radius on ASA account management?
You can paste the o/p of the aaa Server show and see the tunnel-group race
Basically, all you need to define the radius server group and call this group under the tunnel-group settings.
. - Configure the AAA server group.
ciscoasa (config) # the RAD_SRV_GRP of the aaa-Server Protocol RADIUS
output ciscoasa(config-AAA-Server-Group) #.
. - Configure the AAA server.
ciscoasa (config) #-RAD_SRV_GRP (inside) host 192.168.1.2 aaa Server
ciscoasa(config-AAA-Server-Host) # key secretkey
output ciscoasa(config-AAA-Server-Host) #.
. - Configure the tunnel group to use the new configuration of AAA.
ciscoasa (config) # tunnel - group ExampleGroup1 General-attributes
ciscoasa (config) #accounting - server - group RAD_SRV_GRP.
Once done, you can then establish a session and check the detailed accounting package on ACS 5.x range > monitoring and reports > catalogue > aaa protocols > radius account management.
In case you don't see radius account management after following the above steps then please activate the RADIUS accouting and aaa debug ASA "debug". In this way, we can check whether or not ASA sends the details of the session accountinf to ACS.
Kind regards
Jatin kone
-Does the rate of useful messages-
-
Hi all
Can someone tell me what are the options I have, before I use the tunneling split of the SAA. Thank you
I don't want to use the split as last resorce tuneeling.
Thank you
We could also use a vpn filter to control the flow of traffic according to s ACLs on your ipsec tunnel. that IMO is the best way to control traffic!
-
Hi all
We have a router in 1841 with enable webvpn and the split tunneling. This router is also connected to a second office using a VTI. We would like the remote clients of webvpn (using anyconnect) accessing the remote network through VTI.
Office network 1: 192.168.10.0
Office 2 (remote) network: 192.168.11.0
I think split webvpn with tunneling installation is properly install, however I do not know how to get the 192.168.60.0 package (pool dhcp client webvpn) to 192.168.11.0 network.
Does someone have an idea?
Kind regards
Olivier
Router config:
interface Tunnel0
VTI description to the office 2
192.168.50.1 IP address 255.255.255.0
source of Dialer1 tunnel
ipv4 ipsec tunnel mode
destination 217.x.x.133 tunnel
tunnel path-mtu-discovery
protection of profile vti ipsec tunnel
!
interface FastEthernet0/0
LAN Interface Description
IP address 192.168.10.254 255.255.255.0
IP nat inside
IP virtual-reassembly in
automatic duplex
automatic speed
!
ATM0/0/0 interface
no ip address
No atm ilmi-keepalive
!
point-to-point interface ATM0/0/0.1
PVC 8/35
aal5mux encapsulation ppp Dialer
Dialer pool-member 1
!
!
interface Dialer1
Description for ADSL
the negotiated IP address
NAT outside IP
IP virtual-reassembly in
encapsulation ppp
Dialer pool 1
Authentication callin PPP chap Protocol
PPP chap hostname x
PPP chap password 7 x
!
IP pool local PoolVpnAdsl 192.168.60.1 192.168.60.10
IP forward-Protocol ND
!
IP nat inside source overload map route IspADSL interface Dialer1
IP route 0.0.0.0 0.0.0.0 Dialer1
IP route 192.168.11.0 255.255.255.0 192.168.50.2
!
exploitation forest esm config
access-list 10 permit 192.168.10.0 0.0.0.255
access-list 10 deny all
access ip-list 100 permit a whole
Dialer-list 1 ip protocol allow
!
allowed IspADSL 1 route map
corresponds to the IP 10
match interface Dialer1
!
WebVPN gateway GateSslAdsl
IP address 193.x.x.113 port 443
redirect http port 80
SSL trustpoint xxx
development
!
WebVPN context VpnSslAdsl
SSL authentication check all
!
!
policy_1 political group
functions compatible svc
SVC-pool of addresses "PoolVpnAdsl."
SVC Dungeon-client-installed
SVC split dns 'domain.dom '.
SVC split include 192.168.10.0 255.255.255.0
SVC split include 192.168.11.0 255.255.255.0
Primary dns 192.168.10.X SVC-Server
Group Policy - by default-policy_1
XauthRadius of AAA authentication list.
Gateway GateSslAdsl
development
Hi Olivier,.
You must change your extended '10' to an ACL ACL
"access-list 10 permit 192.168.10.0 0.0.0.255.
Please create an ACL 101 as shown below.
access-list 101 deny ip 192.168.60.0 0.0.0.255 192.168.11.0 0.0.0.255
access-list 101 deny ip 192.168.11.0 0.0.0.255 192.168.60.0 0.0.0.255
access-list 101 permit ip 192.168.10.0 0.0.0.255 any
Delete this line: IspADSL route map permit 1
Delete this line: corresponds to the IP 10
allowed IspADSL 1 route map
corresponds to the IP 101
In addition, please make sure you that you have a static route in place other end of TIV to push "192.168.60.0 0.0.0.255.
Let me know if it helps.
Thank you
Post edited by: Mohamed Rizwan
-
How would you define your industry sales promotion?
Sales promotion continues to become a term very Council. In the tech space it seems to be common around what sales promotion is in fact, other industries are trying to define. Promotion sales includes reseller partners (that is to say the manufacturing and life sciences), internal and external advisors (wealth management, IE), agents (IE asset management)? In addition, enablement will exceed supporting partner/Advisor/agent and include also allow the internal organization manage the recruitment of these resources?
How would you define the sales promotion, and how did you put it into practice?
Not sure that I even an answer to the question again... need her more ruminating. But as someone who has a background in marketing in the technology sector and now it feels like the term sales promotion has become synonymous with marketing consultant fighting to not bring the 'golden' son fast enough or often enough. The tools are powerful and what we as traders can provide these days is very different than even five years ago, but it seems that the 'Hunter' in sales is spent (particularly in small businesses) and was replaced by one or the other team of telequal who is really just taken stakeholders and call them to transmit a way (of sale) or the other (back to marketing) or by a team that wants to only call entering lead and very strongly censored conduit. Despite the engagement of leaders in the industry such as lead scoring Sirius is used rarely, or not at all, and when he is he has been transferred to provide the speed of do not have the quality of the leads. Scoring lead was swapped so far of his intention, that he can't spend perhaps the highest quality leads without any cables that respond to anything. Somewhere, lead quality became lost and quantity has led to a passing cables fire hose back, so assume sales marketing can only produce volume and not the quality and the cycle starts again.
I think that now it's time to redefine the sales promotion. Provision of tools for sales, it is a single component, of agreement and mutual understanding around what feeds the process, the agreement on an advance of what is, for trigger points that move from one stage in the cascade to another, ALS and feedback on both sides around what works and what is not form the backbone of successful activation. After that the process and tools are in place a robust feedback loop must be built, something that allows two parties to share (systematically) how things work in the field. Somewhere in the middle of this loop, it goes beyond just sales and marketing and even involves the product teams to help them better understand how the features and functionality of the products they design are really vibrate with customers. This feedback beyond the sales and marketing of the teams then form the basis for business enablement, truly enabling the success of the product and the company as a whole.
-
Hello
How to split a string and store in an associative array in pl/sql.function
My string like this
'1102,1101,1012,1011,1010,1009,1008,1007,1006,10005,1004,1003,1002,1001'
and assign it to the array list. According to
can someone please help
concerning
rYou can try the following. Although I recommend, it would be better to write the function code php as a java stored procedure parser and use the result. We have a class defined in Java String Tokenizer.
-- Define function to split string into tokens FUNCTION get_token( p_input_string IN VARCHAR2, -- input string p_token_number IN PLS_INTEGER, -- token number p_delimiter IN VARCHAR2 DEFAULT ',' -- separator character ) RETURN VARCHAR2 IS v_temp_string VARCHAR2(32767) := p_delimiter || p_input_string ; v_pos1 PLS_INTEGER ; v_pos2 PLS_INTEGER ; BEGIN v_pos1 := INSTR( v_temp_string, p_delimiter, 1, p_token_number ) ; IF v_pos1 > 0 THEN v_pos2 := INSTR( v_temp_string, p_delimiter, 1, p_token_number + 1) ; IF v_pos2 = 0 THEN v_pos2 := LENGTH( v_temp_string ) + 1 ; END IF ; RETURN( SUBSTR( v_temp_string, v_pos1+1, v_pos2 - v_pos1-1 ) ) ; ELSE RETURN NULL ; END IF ; EXCEPTION WHEN OTHERS THEN RAISE; END get_token; -- Call the above function in loop for a string with N tokens DECLARE TYPE assoc_arr_str_typ IS TABLE OF VARCHAR2(100) INDEX BY PLS_INTEGER; str_arr assoc_arr_str_typ; v_str VARCHAR2(200) := '1102,1101,1012,1011,1010,1009,1008,1007,1006,10005,1004,1003,1002,1001' ; v_token VARCHAR2(4) ; i PLS_INTEGER := 1 ; BEGIN LOOP v_token := get_token( v_str, i , ',') ; EXIT WHEN v_token IS NULL ; dbms_output.put_line( v_token ) ; str_arr(i) := v_token; i := i + 1 ; END LOOP ; END ; /Published by: GG 24 March 2011 09:51
-
How to measure a radius of a rectangle in AI CS5 pls
Can someone please tell me step by step how to measure the radius of the corner in a rectangle with rounded corners it please?
Most likely, I need the base for a new user level steps.
Thank you.
First question. How has the rounded Rectangle created? Using the Rectangle tool you rounding? If you have used this method, and then by the Opt (Alt) - clicking, you will get a dialog box allowing to set the RADIUS. (This also has shows where the measuring tool is hidden under the pipette)
If you have already completed the rectangle or imported and apply effect > convert to shape > rounded Rectangle, the you'll another dialogue box in which you can define the RADIUS.
You can continue to modify this option by double-clicking the line of effect of Rectangle rounded in the appearance Panel to retrieve the dialog box. If any rectangle to another program or a file that you have been given then probably the best way is to drag guides of leaders for the anchor points that define the curve and use the measure tool to measure the distance between the intersection of anchor points and path.
-
VPN site to Site btw Pix535 and 2811 router, can't get to work
Hi, everyone, I spent a few days doing a VPN site-to site between PIX535 and 2811 router but returned empty-handed, I followed the instructions here:
http://www.Cisco.com/en/us/products/ps9422/products_configuration_example09186a0080b4ae61.shtml
#1: config PIX:
: Saved
: Written by enable_15 to the 18:05:33.678 EDT Saturday, October 20, 2012
!
8.0 (4) version PIX
!
hostname pix535
!
interface GigabitEthernet0
Description to cable-modem
nameif outside
security-level 0
address IP X.X.138.132 255.255.255.0
OSPF cost 10
!
interface GigabitEthernet1
Description inside 10/16
nameif inside
security-level 100
IP 10.1.1.254 255.255.0.0
OSPF cost 10
!
outside_access_in of access allowed any ip an extended list
access extensive list ip 10.1.0.0 inside_nat0_outbound allow 255.255.0.0 10.20.0.0 255.255.0.0
inside_nat0_outbound list of allowed ip extended access all 10.1.1.192 255.255.255.248
outside_cryptomap_dyn_60 list of allowed ip extended access all 10.1.1.192 255.255.255.248
access extensive list ip 10.1.0.0 outside_1_cryptomap allow 255.255.0.0 10.20.0.0 255.255.0.0
pager lines 24
cnf-8-ip 10.1.1.192 mask - 10.1.1.199 IP local pool 255.255.0.0
Global interface 10 (external)
15 1.2.4.5 (outside) global
NAT (inside) 0-list of access inside_nat0_outbound
NAT (inside) 15 10.1.0.0 255.255.0.0
Access-group outside_access_in in interface outside
Route outside 0.0.0.0 0.0.0.0 X.X.138.1 1
Crypto ipsec transform-set ESP-DES-MD5 esp - esp-md5-hmac
Crypto ipsec transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
Crypto ipsec transform-set ESP-AES-256-SHA 256 - aes - esp esp-sha-hmac
Crypto ipsec transform-set ESP-3DES-MD5-esp-3des esp-md5-hmac
Crypto ipsec transform-set esp-SHA-ESP-3DES-3des esp-sha-hmac
Crypto ipsec transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
Crypto ipsec transform-set ESP-AES-128-SHA aes - esp esp-sha-hmac
Crypto ipsec transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
Crypto ipsec transform-set ESP-AES-128-MD5-esp - aes esp-md5-hmac
Crypto ipsec transform-set ESP-DES-SHA esp - esp-sha-hmac
life crypto ipsec security association seconds 28800
Crypto ipsec kilobytes of life - safety 4608000 association
Crypto-map dynamic outside_dyn_map 20 the value transform-set ESP-3DES-SHA MD5-ESP-3DES ESP-DES-MD5
life together - the association of security crypto dynamic-map outside_dyn_map 20 28800 seconds
Crypto-map dynamic outside_dyn_map 20 kilobytes of life together - the association of safety 4608000
Crypto-map dynamic outside_dyn_map 40 value transform-set ESP-3DES-SHA MD5-ESP-3DES ESP-DES-SHA
life together - the association of security crypto dynamic-map outside_dyn_map 40 28800 seconds
Crypto-map dynamic outside_dyn_map 40 kilobytes of life together - the association of safety 4608000
Dynamic crypto map outside_dyn_map 60 match address outside_cryptomap_dyn_60
Crypto-map dynamic outside_dyn_map 60 value transform-set ESP-3DES-MD5 ESP-3DES-SHA ESP-DES-MD5 ESP-DES-SHA
life together - the association of security crypto dynamic-map outside_dyn_map 60 28800 seconds
Crypto-map dynamic outside_dyn_map 60 kilobytes of life together - the association of safety 4608000
Dynamic crypto map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set pfs
Crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 value transform-set ESP-SHA-3DES ESP-MD5-3DES ESP-DES-SHA ESP-DES-MD5
Dynamic crypto map SYSTEM_DEFAULT_CRYPTO_MAP 65535 define security association lifetime 28800 seconds
cryptographic kilobytes 4608000 life of the set - the association of security of the 65535 SYSTEM_DEFAULT_CRYPTO_MAP of the dynamic-map
card crypto outside_map 1 match address outside_1_cryptomap
outside_map game 1 card crypto peer X.X.21.29
card crypto outside_map 1 set of transformation-ESP-DES-SHA
outside_map map 1 lifetime of security association set seconds 28800 crypto
card crypto outside_map 1 set security-association life kilobytes 4608000
outside_map card crypto 65534 isakmp ipsec dynamic SYSTEM_DEFAULT_CRYPTO_MAP
map outside_map 65535-isakmp ipsec crypto dynamic outside_dyn_map
outside_map interface card crypto outside
ISAKMP crypto identity hostname
crypto ISAKMP allow outside
crypto ISAKMP policy 10
preshared authentication
the Encryption
sha hash
Group 1
life 86400
crypto ISAKMP policy 20
preshared authentication
3des encryption
sha hash
Group 2
life 86400
crypto ISAKMP policy 65535
preshared authentication
3des encryption
sha hash
Group 2
life 86400
Crypto isakmp nat-traversal 3600
internal GroupPolicy1 group strategy
cnf-vpn-cls group policy internal
attributes of cnf-vpn-cls-group policy
value of 10.1.1.7 WINS server
value of 10.1.1.7 DNS server 10.1.1.205
Protocol-tunnel-VPN IPSec l2tp ipsec
field default value x.com
sean U/h5bFVjXlIDx8BtqPFrQw password user name is nt encrypted
IPSec-attributes tunnel-group DefaultRAGroup
pre-shared-key secret1
RADIUS-sdi-xauth
tunnel-group DefaultRAGroup ppp-attributes
ms-chap-v2 authentication
tunnel-group cnf-vpn-cls type remote access
tunnel-group global cnf-vpn-cls-attributes
cnf-8-ip address pool
Group Policy - by default-cnf-vpn-cls
tunnel-group cnf-CC-vpn-ipsec-attributes
pre-shared-key secret2
ISAKMP ikev1-user authentication no
tunnel-group cnf-vpn-cls ppp-attributes
ms-chap-v2 authentication
tunnel-group X.X.21.29 type ipsec-l2l
IPSec-attributes tunnel-Group X.X.21.29
Pre-shared key SECRET
!
class-map inspection_default
match default-inspection-traffic
!
!
!
global service-policy global_policy
context of prompt hostname
Cryptochecksum:9780edb09bc7debe147db1e7d52ec39c
: end
#2: 2811 router config:
!
! Last configuration change to 09:15:32 PST Friday, October 19, 2012 by cnfla
! NVRAM config update at 13:45:03 PST Tuesday, October 16, 2012
!
version 12.4
horodateurs service debug datetime msec
Log service timestamps datetime msec
no password encryption service
!
hostname THE-2800
!
!
Crypto pki trustpoint TP-self-signed-1411740556
enrollment selfsigned
name of the object cn = IOS - Self - signed - certificate - 1411740556
revocation checking no
rsakeypair TP-self-signed-1411740556
!
!
TP-self-signed-1411740556 crypto pki certificate chain
certificate self-signed 01
308201A 8 A0030201 02020101 3082023F 300 D 0609 2A 864886 F70D0101 04050030
2 060355 04031326 494F532D 53656 C 66 2 AND 536967 6E65642D 43657274 31312F30
69666963 31343131 37343035 6174652D 3536301E 170 3132 31303136 32303435
30335A 17 0D 323030 31303130 30303030 305A 3031 06035504 03132649 312F302D
4F532D53 5369676E 656C662D 43 65727469 66696361 74652 31 34313137 65642D
34303535 3630819F 300 D 0609 2A 864886 01050003, 818, 0030, 81890281 F70D0101
8100F75F F1BDAD9B DE9381FD 7EAF9685 CF15A317 165B 5188 1 B 424825 9C66AA28
C990B2D3 D69A2F0F D745DB0E 2BB4995D 73415AC4 F01B2019 C4BCF9E0 84373199
E599B86C 17DBDCE6 47EBE0E3 8DBC90B2 9B4E217A 87F04BF7 A182501E 24381019
A61D2C05 5404DE88 DA2A1ADC A81B7F65 C318B697 7ED69DF1 2769E4C8 F3449B33
010001A 3 67306530 1 130101 FF040530 030101FF 30120603 0F060355 35AF0203
1104 B 0 300982 074C412D 32383030 551D 551 2304 18301680 14B56EEB 301F0603
88054CCA BB8CF8E8 F44BFE2C B77954E1 52301 D 06 04160414 B56EEB88 03551D0E
054CCABB 8CF8E8F4 4BFE2CB7 7954E152 300 D 0609 2A 864886 F70D0101 04050003
81810056 58755 56 331294F8 BEC4FEBC 54879FF5 0FCC73D4 B964BA7A 07D 20452
E7F40F42 8B 355015 77156C9F AAA45F9F 59CDD27F 89FE7560 F08D953B FC19FD2D
310DA96E A5F3E83B 52D515F8 7B4C99CF 4CECC3F7 1A0D4909 BD08C373 50BB53CC
659 4246 2CB7B79F 43D94D96 586F9103 9B4659B6 5C8DDE4F 7CC5FC68 C4AD197A 4EC322 C
quit smoking
!
!
!
crypto ISAKMP policy 1
preshared authentication
ISAKMP crypto key address SECRET X.X.138.132 No.-xauth
!
!
Crypto ipsec transform-set the-2800-trans-set esp - esp-sha-hmac
!
map 1 la-2800-ipsec policy ipsec-isakmp crypto
ipsec vpn Description policy
defined by peer X.X.138.132
the transform-set the-2800-trans-set value
match address 101
!
!
!
!
!
!
interface FastEthernet0/0
Description WAN side
address IP X.X.216.29 255.255.255.248
NAT outside IP
IP virtual-reassembly
automatic duplex
automatic speed
No cdp enable
No mop enabled
card crypto 2800-ipsec-policy
!
interface FastEthernet0/1
Description side LAN
IP 10.20.1.1 255.255.255.0
IP nat inside
IP virtual-reassembly
full duplex
automatic speed
No mop enabled
!
IP nat inside source map route sheep interface FastEthernet0/0 overload
access-list 10 permit X.X.138.132
access-list 99 allow 64.236.96.53
access-list 99 allow 98.82.1.202
access list 101 remark vpn tunnerl acl
Note access-list 101 category SDM_ACL = 4
policy of access list 101 remark tunnel
access-list 101 permit ip 10.20.0.0 0.0.0.255 10.1.0.0 0.0.255.255
access-list 110 deny ip 10.20.0.0 0.0.0.255 10.1.0.0 0.0.255.255
access-list 110 permit ip 10.20.0.0 0.0.0.255 any
public RO SNMP-server community
!
!
!
sheep allowed 10 route map
corresponds to the IP 110
!
!
!
!
WebVPN gateway gateway_1
IP address X.X.216.29 port 443
SSL trustpoint TP-self-signed-1411740556
development
!
WebVPN install svc flash:/webvpn/svc.pkg
!
WebVPN gateway-1 context
title 'b '.
secondary-color white
color of the title #CCCC66
text-color black
SSL authentication check all
!
!
policy_1 political group
functions compatible svc
SVC-pool of addresses "WebVPN-Pool."
SVC Dungeon-client-installed
SVC split include 10.20.0.0 255.255.0.0
Group Policy - by default-policy_1
Gateway gateway_1
development
!
!
end
#3: test Pix to the router:
ITS enabled: 1
Generate a new key SA: 0 (a tunnel report Active 1 and 1 to generate a new key during the generate a new key)
Total SA IKE: 1
1 peer IKE: X.X.21.29
Type: user role: initiator
Generate a new key: no State: MM_WAIT_MSG2
> DEBUG:
!12:07:14 pix535:Oct 22 Oct 22 12:20:28 EDT: % PIX-vpn-3-713902: IP = X.X.21.29, Removing peer to peer table has not, no match22 Oct 12:07:14 pix535: 22 Oct 12:20:28 EDT: % PIX-vpn-4-713903: IP = X.X.21.29, error: cannot delete PeerTblEntry#4: test the router to pix:LA - 2800 #sh crypto isakmp hisIPv4 Crypto ISAKMP Security Associationstatus of DST CBC State conn-id slotX.X.138.132 X.X.216.29 MM_KEY_EXCH 1017 ASSETS 0> debug. Next payload is 0LA - 2800 #ping 10.1.1.7 source 10.20.1.1Type to abort escape sequence.Send 5, echoes ICMP 100 bytes to 10.1.1.7, time-out is 2 seconds:Packet sent with a source address of 10.20.1.1Oct 22 16:24:33.945: ISAKMP: (0): profile of THE request is (NULL)22 Oct 16:24:33.945: ISAKMP: created a struct peer X.X.138.132, peer port 50022 Oct 16:24:33.945: ISAKMP: new created position = 0x488B25C8 peer_handle = 0 x 8000001322 Oct 16:24:33.945: ISAKMP: lock struct 0x488B25C8, refcount 1 to peer isakmp_initiator22 Oct 16:24:33.945: ISAKMP: 500 local port, remote port 50022 Oct 16:24:33.945: ISAKMP: set new node 0 to QM_IDLE22 Oct 16:24:33.945: ISAKMP: find a dup her to the tree during the isadb_insert his 487720 A 0 = call BVA22 Oct 16:24:33.945: ISAKMP: (0): cannot start aggressive mode, try the main mode.22 Oct 16:24:33.945: ISAKMP: (0): pair found pre-shared key matching 70.169.138.132Oct 22 16:24:33.945: ISAKMP: (0): built of NAT - T of the seller-rfc3947 IDOct 22 16:24:33.945: ISAKMP: (0): built the seller-07 ID NAT - tOct 22 16:24:33.945: ISAKMP: (0): built of NAT - T of the seller-03 IDOct 22 16:24:33.945: ISAKMP: (0): built the seller-02 ID NAT - t22 Oct 16:24:33.945: ISAKMP: (0): entry = IKE_MESG_FROM_IPSEC, IKE_SA_REQ_MM22 Oct 16:24:33.945: ISAKMP: (0): former State = new State IKE_READY = IKE_I_MM1Oct 22 16:24:33.945: ISAKMP: (0): Beginner Main Mode ExchangeOct 22 16:24:33.945: ISAKMP: (0): package X.X.138.132 my_port 500 peer_port 500 (I) sending MM_NO_STATE22 Oct 16:24:33.945: ISAKMP: (0): sending a packet IPv4 IKE.22 Oct 16:24:34.049: ISAKMP (0:0): packet received dport 500 sport Global 500 (I) MM_NO_STATE X.X.138.13222 Oct 16:24:34.049: ISAKMP: (0): entry = IKE_MESG_FROM_PEER, IKE_MM_EXCH22 Oct 16:24:34.049: ISAKMP: (0): former State = new State IKE_I_MM1 = IKE_I_MM2Oct 22 16:24:34.049: ISAKMP: (0): treatment ITS payload. Message ID = 0Oct 22 16:24:34.049: ISAKMP: (0): load useful vendor id of treatmentOct 22 16:24:34.049: ISAKMP: (0): provider ID seems the unit/DPD but major incompatibility of 123Oct 22 16:24:34.049: ISAKMP: (0): provider ID is NAT - T v2Oct 22 16:24:34.049: ISAKMP: (0): load useful vendor id of treatmentOct 22 16:24:34.049: ISAKMP: (0): provider ID seems the unit/DPD but major incompatibility of 19422 Oct 16:24:34.053: ISAKMP: (0): pair found pre-shared key matching 70.169.138.132Oct 22 16:24:34.053: ISAKMP: (0): pre-shared key local found22 Oct 16:24:34.053: ISAKMP: analysis of the profiles for xauth...22 Oct 16:24:34.053: ISAKMP: (0): audit ISAKMP transform 1 against the policy of priority 122 Oct 16:24:34.053: ISAKMP: DES-CBC encryption22 Oct 16:24:34.053: ISAKMP: SHA hash22 Oct 16:24:34.053: ISAKMP: default group 122 Oct 16:24:34.053: ISAKMP: pre-shared key auth22 Oct 16:24:34.053: ISAKMP: type of life in seconds22 Oct 16:24:34.053: ISAKMP: life (IPV) 0 x 0 0 x 1 0 x 51 0x8022 Oct 16:24:34.053: ISAKMP: (0): atts are acceptable22 Oct 16:24:34.053: ISAKMP: (0): Acceptable atts: real life: 022 Oct 16:24:34.053: ISAKMP: (0): Acceptable atts:life: 022 Oct 16:24:34.053: ISAKMP: (0): fill atts in his vpi_length:422 Oct 16:24:34.053: ISAKMP: (0): fill atts in his life_in_seconds:8640022 Oct 16:24:34.053: ISAKMP: (0): return real life: 8640022 Oct 16:24:34.053: ISAKMP: (0): timer life Started: 86400.Oct 22 16:24:34.053: ISAKMP: (0): load useful vendor id of treatmentOct 22 16:24:34.053: ISAKMP: (0): provider ID seems the unit/DPD but major incompatibility of 123Oct 22 16:24:34.053: ISAKMP: (0): provider ID is NAT - T v2Oct 22 16:24:34.053: ISAKMP: (0): load useful vendor id of treatmentOct 22 16:24:34.053: ISAKMP: (0): provider ID seems the unit/DPD but major incompatibility of 19422 Oct 16:24:34.053: ISAKMP: (0): entry = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE22 Oct 16:24:34.053: ISAKMP: (0): former State = new State IKE_I_MM2 = IKE_I_MM2Oct 22 16:24:34.057: ISAKMP: (0): package X.X.138.132 my_port 500 peer_port 500 (I) sending MM_SA_SETUP22 Oct 16:24:34.057: ISAKMP: (0): sending a packet IPv4 IKE.22 Oct 16:24:34.057: ISAKMP: (0): entry = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE22 Oct 16:24:34.057: ISAKMP: (0): former State = new State IKE_I_MM2 = IKE_I_MM322 Oct 16:24:34.181: ISAKMP (0:0): packet received dport 500 sport Global 500 (I) MM_SA_SETUP X.X.138.13222 Oct 16:24:34.181: ISAKMP: (0): entry = IKE_MESG_FROM_PEER, IKE_MM_EXCH22 Oct 16:24:34.181: ISAKMP: (0): former State = new State IKE_I_MM3 = IKE_I_MM4Oct 22 16:24:34.181: ISAKMP: (0): processing KE payload. Message ID = 0Oct 22 16:24:34.217: ISAKMP: (0): processing NONCE payload. Message ID = 022 Oct 16:24:34.217: ISAKMP: (0): pre-shared key found peer corresponding to X.X.138.132Oct 22 16:24:34.217: ISAKMP: (1018): load useful vendor id of treatmentOct 22 16:24:34.217: ISAKMP: (1018): provider ID is the unitOct 22 16:24:34.217: ISAKMP: (1018): load useful vendor id of treatmentOct 22 16:24:34.217: ISAKMP: (1018): provider ID seems the unit/DPD but major incompatibility of 55Oct 22 16:24:34.217: ISAKMP: (1018): provider ID is XAUTHOct 22 16:24:34.217: ISAKMP: (1018): load useful vendor id of treatmentOct 22 16:24:34.217: ISAKMP: (1018): addressing another box of IOS!Oct 22 16:24:34.221: ISAKMP: (1018): load useful vendor id of treatment22 Oct 16:24:34.221: ISAKMP: (1018): vendor ID seems the unit/DPD but hash mismatch22 Oct 16:24:34.221: ISAKMP: receives the payload type 2022 Oct 16:24:34.221: ISAKMP: receives the payload type 2022 Oct 16:24:34.221: ISAKMP: (1018): entry = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE22 Oct 16:24:34.221: ISAKMP: (1018): former State = new State IKE_I_MM4 = IKE_I_MM422 Oct 16:24:34.221: ISAKMP: (1018): send initial contact22 Oct 16:24:34.221: ISAKMP: (1018): ITS been pre-shared key, using id ID_IPV4_ADDR type authentication22 Oct 16:24:34.221: ISAKMP (0:1018): payload IDnext payload: 8type: 1address: X.X.216.29Protocol: 17Port: 500Length: 1222 Oct 16:24:34.221: ISAKMP: (1018): the total payload length: 12Oct 22 16:24:34.221: ISAKMP: (1018): package X.X.138.132 my_port 500 peer_port 500 (I) sending MM_KEY_EXCH22 Oct 16:24:34.221: ISAKMP: (1018): sending a packet IPv4 IKE.22 Oct 16:24:34.225: ISAKMP: (1018): entry = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE22 Oct 16:24:34.225: ISAKMP: (1018): former State = new State IKE_I_MM4 = IKE_I_MM5...22 Oct 16:24:38.849: ISAKMP: (1017): purge the node 19855474022 Oct 16:24:38.849: ISAKMP: (1017): purge the node 81238000222 Oct 16:24:38.849: ISAKMP: (1017): purge node 773209335...Success rate is 0% (0/5)# THE-2800Oct 22 16:24:44.221: ISAKMP: (1018): transmit phase 1 MM_KEY_EXCH...22 Oct 16:24:44.221: ISAKMP (0:1018): increment the count of errors on his, try 1 5: retransmit the phase 1Oct 22 16:24:44.221: ISAKMP: (1018): transmit phase 1 MM_KEY_EXCHOct 22 16:24:44.221: ISAKMP: (1018): package X.X.138.132 my_port 500 peer_port 500 (I) sending MM_KEY_EXCH22 Oct 16:24:44.221: ISAKMP: (1018): sending a packet IPv4 IKE.22 Oct 16:24:44.317: ISAKMP (0:1018): packet received dport 500 sport Global 500 (I) MM_KEY_EXCH X.X.138.132Oct 22 16:24:44.317: ISAKMP: (1018): package of phase 1 is a duplicate of a previous package.Oct 22 16:24:44.321: ISAKMP: (1018): retransmission jumped to the stage 1 (time elapsed since the last transmission 96)22 Oct 16:24:48.849: ISAKMP: (1017): serving SA., his is 469BAD60, delme is 469BAD6022 Oct 16:24:52.313: ISAKMP (0:1018): packet received dport 500 sport Global 500 (I) MM_KEY_EXCH X.X.138.132Oct 22 16:24:52.313: ISAKMP: (1018): package of phase 1 is a duplicate of a previous package.Oct 22 16:24:52.313: ISAKMP: (1018): retransmission due to phase 1 of retransmissionOct 22 16:24:52.813: ISAKMP: (1018): transmit phase 1 MM_KEY_EXCH...22 Oct 16:24:52.813: ISAKMP (0:1018): increment the count of errors on his, try 2 of 5: retransmit the phase 1Oct 22 16:24:52.813: ISAKMP: (1018): transmit phase 1 MM_KEY_EXCHOct 22 16:24:52.813: ISAKMP: (1018): package X.X138.132 my_port 500 peer_port 500 (I) sending MM_KEY_EXCH22 Oct 16:24:52.813: ISAKMP: (1018): sending a packet IPv4 IKE.Oct 22 16:24:52.913: ISAKMP: (1018): package of phase 1 is a duplicate of a previous package.Oct 22 16:24:52.913: ISAKMP: (1018): retransmission jumped to the stage 1 (time elapsed since the last transmission of 100)22 Oct 16:25:00.905: ISAKMP (0:1018): packet received dport 500 sport Global 500 (I) MM_KEY_EXCH X.X.138.13222 Oct 16:25:00.905: ISAKMP: node set 422447177 to QM_IDLE..... (local 1 X. X.216.29, remote X.X.138.132)22 Oct 16:25:03.941: ISAKMP: (1018): SA is still budding. New application of ipsec in the annex22 Oct 16:25:03.941: ISAKMP: error during the processing of HIS application: failed to initialize SA22 Oct 16:25:03.941: ISAKMP: error while processing message KMI 0, error 2.Oct 22 16:25:12.814: ISAKMP: (1018): transmit phase 1 MM_KEY_EXCH...22 Oct 16:25:12.814: ISAKMP (0:1018): increment the count of errors on his, try 4 out 5: retransmit the phase 1Oct 22 16:25:12.814: ISAKMP: (1018): transmit phase 1 MM_KEY_EXCHOct 22 16:25:12.814: ISAKMP: (1018): package X.X.138.132 my_port 500 peer_port 500 (I) sending MM_KEY_EXCH22 Oct 16:25:12.814: ISAKMP: (1018): sending a packet IPv4 IKE.Oct 22 16:25:22.814: ISAKMP: (1018): transmit phase 1 MM_KEY_EXCH...22 Oct 16:25:22.814: ISAKMP (0:1018): increment the count of errors on his, try 5 of 5: retransmit the phase 1Oct 22 16:25:22.814: ISAKMP: (1018): transmit phase 1 MM_KEY_EXCHOct 22 16:25:22.814: ISAKMP: (1018): package X.X.138.132 my_port 500 peer_port 500 (I) sending MM_KEY_EXCH22 Oct 16:25:22.814: ISAKMP: (1018): sending a packet IPv4 IKE.Oct 22 16:25:32.814: ISAKMP: (1018): transmit phase 1 MM_KEY_EXCH...22 Oct 16:25:32.814: ISAKMP: (1018): peer does not paranoid KeepAlive.......22 Oct 16:25:32.814: ISAKMP: (1018): removal of reason ITS status of 'Death by retransmission P1' (I) MM_KEY_EXCH (post 70.169.138.132)
22 Oct 16:25:32.814: ISAKMP: (1018): removal of reason ITS status of 'Death by retransmission P1' (I) MM_KEY_EXCH (post 70.169.138.132)
22 Oct 16:25:32.814: ISAKMP: Unlocking counterpart struct 0x488B25C8 for isadb_mark_sa_deleted(), count 0
22 Oct 16:25:32.814: ISAKMP: delete peer node by peer_reap for X.X.138.132: 488B25C8
22 Oct 16:25:32.814: ISAKMP: (1018): error suppression node 1112432180 FALSE reason 'IKE deleted.
22 Oct 16:25:32.814: ISAKMP: (1018): error suppression node 422447177 FALSE reason 'IKE deleted.
22 Oct 16:25:32.814: ISAKMP: (1018): node-278980615 error suppression FALSE reason 'IKE deleted.
22 Oct 16:25:32.814: ISAKMP: (1018): entry = IKE_MESG_INTERNAL, IKE_PHASE1_DEL
22 Oct 16:25:32.814: ISAKMP: (1018): former State = new State IKE_I_MM5 = IKE_DEST_SA
22 Oct 16:26:22.816: ISAKMP: (1018): purge the node 1112432180
22 Oct 16:26:22.816: ISAKMP: (1018): purge the node 422447177
22 Oct 16:26:22.816: ISAKMP: (1018): purge the node-278980615
22 Oct 16:26:32.816: ISAKMP: (1018): serving SA., its A 487720, 0 =, delme = A 487720, 0
The PIX is also used VPN client, such as the VPN Cicso 5.0 client access, works very well. Router is used as a server SSL VPN, too much work
I know there are a lot of data here, I hope that these data may be useful for diagnostic purposes.
All suggestions and tips are greatly appreciated.
Sean
Recommended action:
On the PIX:
no card crypto outside_map 1
!
crypto ISAKMP policy 5
preshared authentication
3des encryption
sha hash
Group 2
life 86400
!
card crypto outside_map 10 correspondence address outside_1_cryptomap
crypto outside_map 10 peer X.X.216.29 card game
outside_map crypto 10 card value transform-set ESP-3DES-SHA
life safety association set card crypto outside_map 10 28800 seconds
card crypto outside_map 10 set security-association life kilobytes 4608000
!
tunnel-group X.X.216.29 type ipsec-l2l
IPSec-attributes tunnel-Group X.X.216.29
Pre-shared key SECRET
!
On the router:
crypto ISAKMP policy 10
preshared authentication
Group 2
3des encryption
!
Crypto ipsec transform-set esp-SHA-ESP-3DES-3des esp-sha-hmac
output
!
card 10 la-2800-ipsec policy ipsec-isakmp crypto
ipsec vpn Description policy
defined by peer X.X.138.132
game of transformation-ESP-3DES-SHA
match address 101
!
No crypto card-2800-ipsec-policy 1
Let me know how it goes.
Portu.
Please note all useful posts
Post edited by: Javier Portuguez
-
WEBVPN and AD group membership
I desperately need some advice with my design of authentication of WEBVPN.
How to restrict specific users to connect only to certain profile connection alias?
For example. Let's say I have the GROUP A and GROUP B GROUP C as an alias, available in the drop down below to the SSL login screen. In AD, I have 3 groups of security, the same. How can I make sure that only members of the group a security group can authenticate to the GROUP a connection profile and not the others. Ideally, I'd like to achieve with the Radius Authentication, but I couldn't find an attribute that has been passed along that I can pre-selection against. Any suggestions are appreciated. Thank you.
You can use the ldap mapping to authenticate your users against AD with ldap and retrieve the memberOf and this value map to the value of the IETF-class which includes the SAA this to activate Group locking, allowing only users belonging to a specific tunnel group strategy to connect to this strategy of tunnel group.
-
Hi guys
Is there a way to create a background including the foregound bluured are in a talking circle? Hard to explain but I'm sure I saw it done a lot. For example, I would put the subject of an interview in a circle, then the outside of the circle is bluured.
I'm using Premiere Pro CS4.
Any help appreciated.
If it's a perfect circle, you can use (favorite Colin effect) circle (its under Generate)
Put the clip twice in a supermposing timeline the other.
Add fast blur and Gaussian blur to the V1 clip. Blur the pixels of contour repeat clip and ticks.
Apply the Cicle effect to the element in V2.
Define the RADIUS, the pen and to stencil Alpha blend mode game. Fact
Now, if there must be an ellipse.
Clip Drop in V1 and V2.
Add a blur to V1
Add the effect of matte for V2
Now, draw an ellipse in the Titler.
That decline in V3 and add a blur to feather out.
The value hidden by approach V3.
Fact.
-
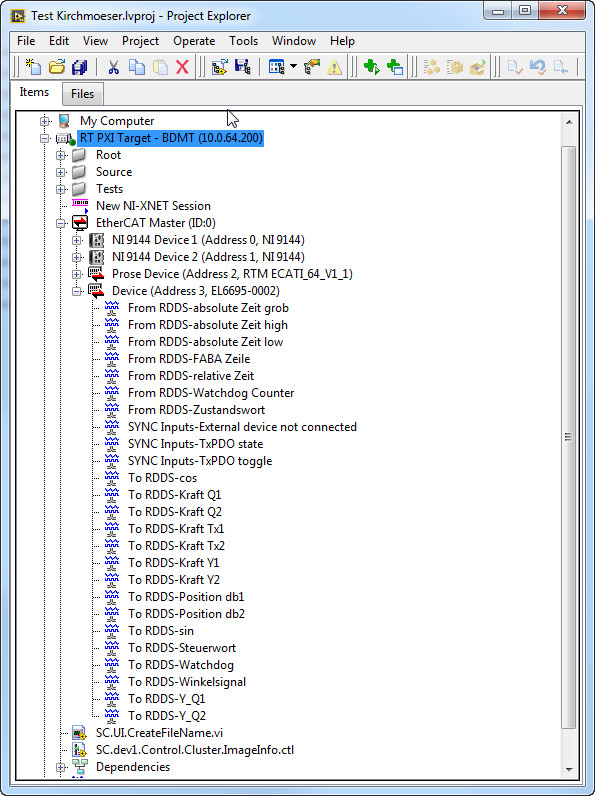
AOP of EtherCAT Slave not load completely from XML file
Hi all
I'm trying to import an XML file of Beckhoff device profile for the EL 6695 EtherCAT Slave in the LabVIEW project.
I brought changes to the Beckhoff as XML files so that all the 'user-defined AOP"is also included, when I connect this slave of my LabVIEW project.
Screenshot below will give you an idea on my LabVIEW project.
In the screenshot, you can see the entries of the AO responsible for the EL 6695 ethercat slave.
The main problem here is that entered the AOP list / output entered is incomplete. I have 100 + entries "Of DDR" and even outputs.
Please let me know if anyone has an idea about this.
Thanks in advance!
Rahul.
Germany
Hi Raul,
Sorry for the end frequency! China observed holidays these days.
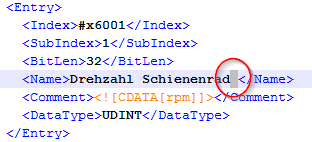
Finally, I found the cause of this problem! It's because of the extra 'space' behind the text of the name of the entry.
If all the entries after the entry of this issue will be ignored by LabVIEW. LabVIEW currently has some limitation to detect this. I go to your comments this problem to the right team to solve this problem in the future! Please see the attached XML, I modified according to your version.
Sorry to have caused you so much pain because of this!
Wendy
-
Problems with typedef uInt32 and NI Vision
Hello
I'm having a small problem my request against the headers provided by NI Vision acquisition 15.0 and CVI 2012SP1 of construction. The problem seems to be contradictory typedefs in the files of headers associated with the types of 'SESSION_ID' and 'uInt32 '. In NIIMAQdx.h, it is the following:
#ifndef _NI_uInt32_DEFINED_
#define _NI_uInt32_DEFINED_
#if defined (_MSC_VER)
typedef unsigned long uInt32;
#else
typedef unsigned int uInt32;
#endif
#endifNow, _MSC_VER is not defined, so we get defined as an unsigned int uInt32. In niimaq.h there is:
#ifndef _NI_uInt32_DEFINED_
#define _NI_uInt32_DEFINED_
#if defined (_MSC_VER)
typedef unsigned long uInt32;
#elif __GNUC__
#if __x86_64__
typedef unsigned int uInt32;
#else
typedef unsigned long uInt32;
#endif
#endif
#endifWhich neither _MSC_VER or __GNUC__ being defined, does nothing except set _NI_uInt32_DEFINED_ who prevernts to be set by another heading. niimaq.h also has this in it:
typedef uInt32 id_interface;
typedef uInt32 SESSION_ID;
typedef uInt32 EVENT_ID.
typedef uInt32 PULSE_ID;
typedef uInt32 BUFLIST_ID;
typedef Int32 IMG_ERR;
typedef uInt16 IMG_SYNC;
typedef uInt32 GUIHNDL;This means that, by itself, a module which includes niimaq.h build because uInt32 never gets defined. You can include NIIMAQdx.h in front of her then she cand defrine uInt32 (as an unsigned int), that works, except that nivision.h has this line int he:
typedef unsigned long SESSION_ID;
Yet once they do compile due to the conflicting types (unsigned int versus long unsigned). It seems that there is no way to include niimaq.h, nivision.h and NIIMAQdx.h in the same .c file, regardless of the order, without certain types of conflicts or unknown. Comparison of return to an older version (3.9.1), I see in NIMAQdx.h,
#ifndef _NI_uInt32_DEFINED_
#define _NI_uInt32_DEFINED_
typedef unsigned long uInt32;
#endifWhich is nice and simple. niimaq.h also has the same code in it too much OR-IMAQ 4.6.1. Does this mean that I can "fix" it by defining _MSC_VER, indeed put
#define _MSC_VER 1300
At the top of my .c file gets in effect of things to build, but I'm wary to do this because I know there are other things that seem out of it.
Any ideas or is the solution to restore an older version of the Acquisition of the Vision? Thank you.
Hi Tanner!, thanks for the reply. I use the Debug, not 32-bit mode. The code example you provided does not build in my configuration. The problem is this code in niimaq.h
typedef uInt32 id_interface;
typedef uInt32 SESSION_ID;
typedef uInt32 EVENT_ID.
typedef uInt32 PULSE_ID;
typedef uInt32 BUFLIST_ID;
typedef Int32 IMG_ERR;
typedef uInt16 IMG_SYNC;
typedef uInt32 GUIHNDL;And the reason is that an Int32 and uInt32 are not defined (although uInt16 is defined). On another PC with NI Vision 2009 installed it relies very well, but it does not work on this PC with IMAQ 15.0.
Play with it, I think the problem is that CVI 2012 SP1 isn't definition _MSC_VER or __GNUC__, whereas CVI 2013SP1 __GNUC__ defined as 4 (and indefinite _MSC_VER leaves). As __GNUC__ is defined, then in niimaq.h, uInt32 is defined as unsigned long (for 32 bit), and all is happy with CVI 2013, so the problem seems to be related to the combination of the ICB 2012 and versions more recent the IMAQ.
Maybe you are looking for
-
Somehow my IPod running 9.3.3s date and time has been changed and when I went to search it says "trust" to something and I did so I could seek, whenever I tried something else, it pops up again and im wondering how to untrust these things, I set my d
-
When sending photos of Photos the Mail app opens but the picture is at the top, and when I type my message, it starts from the bottom. How do I type my message at the top and move the photo down? (El capitan, Mail 9.1, 1.2 Photos) Also I can't find m
-
How can I configure a static IP address in Windows Server 2008?
original title: set static IP of Server 2008 I have a Server 2008 R2 from a CD of demo loaded on a Dell computer.When I start my Poweredge 1950 server, I get these messages:' F/W initialization devices 0% '.info on the RAID drivers"(HA-0 9Bus 2 Dev 1
-
What version of Windows Movie Maker is one that has all the features
Hello I wonder what is the best version of windows movie maker? Which version has the most options, is easy to use and can create HD videos? In addition, Vista, or windows XP? I'm a newbie total movie maker and would appreciate any help for localiza