VPN split tunneling issue?
Hi all
Can someone tell me what are the options I have, before I use the tunneling split of the SAA. Thank you
I don't want to use the split as last resorce tuneeling.
Thank you
We could also use a vpn filter to control the flow of traffic according to s ACLs on your ipsec tunnel. that IMO is the best way to control traffic!
Tags: Cisco Security
Similar Questions
-
Help: Customer Cisco VPN & Split Tunnel but not Internet
Hi Forum.
We are faced with this problem: after having successfully open a VPN connection with the Cisco VPN Client to a router Cisco, the rest of the world are not properly available more.
This is what has been verified / so far attempted to identify the problem on a Windows Vista computer:
-Router: Split Tunneling is allowed according to sysop
-On the VPN-Client: "allow Local Lan access" is checked
-On the Client (statistics): only STI VPN-rout configured listed unter "guarantee routes." "Local Lan routes" is empty.
-Calling 'http://www.google.com' in IE fails
-Call ' 74.125.232.116' (IE IP) IE works / ping the IP works.
-nslookup properly lists the current DNS server
-nslookup www.google.com resolves correctly the name of intellectual property
It seems that it is not that the connection with the rest of the Internet is deleted, but DNS resolution fails somehow, even though all signs point to the appropriate DNS server is in force and although the command line can resolve the name.
does anyone have a tip how to debug this correctly?
No worries Pat...
Sent by Cisco Support technique iPhone App
-Please evaluate solutions
-
Hello
First of all - thanks to all who post here. I often browse the forums and search for help here and its very useful, so a big pat on the back for all who contribute. My first post, so here goes...
I've got my ASA 5505 v8.2 configured to allow the AnyConnect. This works. Client can connect and access remote systems via VPN. What causes me a massive headache, is the customer loses internet connectivity. I played a bit with my config a bit so what I am about to post that I know for sure is incorrect, but any help is greatly appreciated.
Notes
1. the router was set up for a VPN site to site standard that is no longer functional, but as you can see all the settings are always in the router.
2. the router also a DMZ configuration has to allow access to the internet with the help of the DMZ to some customers
CONFIGURATION:
ASA Version 8.2 (5)
!
hostname MYHOST
activate mUUvr2NINofYuSh2 encrypted password
UNDrnIuGV0tAPtz2 encrypted passwd
names of
name x.x.x.x LIKES-SD
!
interface Ethernet0/0
switchport access vlan 2
!
interface Ethernet0/1
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
!
interface Ethernet0/7
switchport access vlan 7
!
interface Vlan1
nameif inside
security-level 100
192.168.101.1 IP address 255.255.255.0
!
interface Vlan2
nameif outside
security-level 0
IP x.x.x.x 255.255.0.0
!
interface Vlan7
prior to interface Vlan1
nameif DMZ
security-level 20
IP 137.57.183.1 255.255.255.0
!
passive FTP mode
clock timezone STD - 7
the obj_any_dmz object-group network
10 extended access-list allow ip 192.168.25.0 255.255.255.0 192.168.6.0 255.255.255.0
permit access ip host x.x.x.x 192.168.25.0 extended list no_nat 255.255.25 5.0
tunneling split list of permitted access standard 192.168.101.0 255.255.255.0
192.168.101.0 IP Access-list extended sheep 255.255.255.0 allow all
pager lines 24
Enable logging
debug logging in buffered memory
asdm of logging of information
Within 1500 MTU
Outside 1500 MTU
MTU 1500 DMZ
mask 192.168.101.125 - 192.168.101.130 255.255.255.0 IP local pool Internal_Range
ICMP unreachable rate-limit 1 burst-size 1
don't allow no asdm history
ARP timeout 14400
Global interface 10 (external)
NAT (inside) 0-list of access no_nat
NAT (inside) 1 access-list sheep
NAT (DMZ) 10 137.57.183.0 255.255.255.0
Route outside 0.0.0.0 0.0.0.0 x.x.x.x 1
Route inside 192.168.8.0 255.255.255.0 192.168.101.2 1
Timeout xlate 03:00
Timeout conn 01:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
Sunrpc timeout 0:10:00 h323 0:05:00 h225 mgcp from 01:00 0:05:00 mgcp-pat 0:05:00
Sip timeout 0:30:00 sip_media 0:02:00 prompt Protocol sip-0: 03:00 sip - disconnect 0:02:00
Timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
Floating conn timeout 0:00:00
dynamic-access-policy-registration DfltAccessPolicy
the ssh LOCAL console AAA authentication
http server enable 64000
http 0.0.0.0 0.0.0.0 inside
No snmp server location
No snmp Server contact
Server enable SNMP traps snmp authentication linkup, linkdown cold start
Crypto ipsec transform-set esp-aes-256 batus, esp-sha-hmac
life crypto ipsec security association seconds 28800
Crypto ipsec kilobytes of life - safety 4608000 association
correspondence address card crypto 100 10 batus
crypto batus 100 peer LIKES-SD card game
batus batus 100 transform-set card crypto
batus outside crypto map interface
Crypto ca trustpoint ASDM_TrustPoint1
registration auto
name of the object CN = MYHOST
ClientX_cert key pair
Configure CRL
string encryption ca ASDM_TrustPoint1 certificates
certificate 0f817951
308201e7 a0030201 30820150 0202040f 0d06092a 81795130 864886f7 0d 010105
05003038 31173015 06035504 03130e41 494d452d 56504e2d 42415455 53311d 30
1b06092a 864886f7 0d 010902 160e4149 4d452d56 504e2d42 41545553 301e170d
31333036 32373137 32393335 5a170d32 33303632 35313732 3933355a 30383117
30150603 55040313 0e41494d 452-5650 4e2d4241 54555331 1d301b06 092 d has 8648
86f70d01 0902160e 41494d 45 2d56504e 424154 55533081 9f300d06 092 2d has 8648
86f70d01 01010500 03818d 30818902 00 818100c 9 ff840bf4 cfb8d394 2 c 940430
1887f25a 49038aa0 1299cf10 bda2a436 227dcdbf f1c5566b c35c2f19 8b3514d3
4e24f5b1 c8840e8c 60e2b39d bdc0082f 08cce525 97ffefba d42bb087 81b9adb9
db0a8b2f b643e651 d17cd6f8 f67297f2 d785ef46 c3acbb39 615e1ef1 23db072c
783fe112 acd6dc80 dc38e94b 6e56fe94 d59d5d02 03010001 300 d 0609 2a 864886
8181007e f70d0101 05050003 29e90ea0 e337976e 9006bc02 402fd58a a1d30fe8
b2c1ab49 a1828ee0 488d1d2f 1dc5d150 3ed85f09 54f099b2 064cd 622 dc3d3821
fca46c69 62231fd2 6e396cd1 7ef586f9 f41205af c2199174 3c5ee887 42b684c9
7f4d2045 4742adb5 d70c3805 4ad13191 8d802bbc b2bcd8c7 8eec111b 761d89f3
63ebd49d 30dd06f4 e0fa25
quit smoking
crypto ISAKMP allow outside
crypto ISAKMP policy 40
preshared authentication
aes-256 encryption
sha hash
Group 5
life 86400
Telnet timeout 5
SSH 0.0.0.0 0.0.0.0 inside
SSH 0.0.0.0 0.0.0.0 DMZ
SSH timeout 10
Console timeout 0
a basic threat threat detection
Statistics-list of access threat detection
no statistical threat detection tcp-interception
SSL encryption rc4 - md5, rc4-aes128-sha1 aes256-3des-sha1 sha1 sha1
SSL-trust outside ASDM_TrustPoint1 point
WebVPN
allow outside
SVC disk0:/anyconnect-win-2.4.1012-k9.pkg 1 image
enable SVC
internal ClientX_access group strategy
attributes of Group Policy ClientX_access
VPN-tunnel-Protocol svc
Split-tunnel-network-list value split tunneling
access.local value by default-field
the address value Internal_Range pools
IPv6 address pools no
WebVPN
SVC mtu 1406
generate a new key SVC time no
SVC generate a new method ssl key
username privilege 15 encrypted password ykAxQ227nzontdIh ClientX
ClientX username attributes
VPN-group-policy ClientX_access
type of service admin
tunnel-group x.x.x.x type ipsec-l2l
tunnel-group ipsec-attributes x.x.x.x
pre-shared key *.
tunnel-group ClientX type remote access
attributes global-tunnel-group ClientX
address pool Internal_Range
Group Policy - by default-ClientX_access
type tunnel-group SSLClientProfile remote access
attributes global-tunnel-group SSLClientProfile
Group Policy - by default-ClientX_access
type tunnel-group ClientX_access remote access
!
class-map inspection_default
match default-inspection-traffic
!
!
type of policy-card inspect dns preset_dns_map
parameters
maximum message length automatic of customer
message-length maximum 512
Policy-map global_policy
class inspection_default
inspect the preset_dns_map dns
inspect the ftp
inspect h323 h225
inspect the h323 ras
inspect the rsh
inspect the rtsp
inspect esmtp
inspect sqlnet
inspect the skinny
inspect sunrpc
inspect xdmcp
inspect the sip
inspect the netbios
inspect the tftp
Review the ip options
!
global service-policy global_policy
context of prompt hostname
no remote anonymous reporting call
Cryptochecksum:e7d92a387d1c5f07e14b3c894d159ec1
: end
-----------------------
Thanks for any help!
In your group strategy, you specified the ACLs that should be used for split Tunneling, but you forgot to change the policy, so the ASA always uses tunnel-all. Here's what you'll need:
attributes of Group Policy ClientX_access
Split-tunnel-network-list value split tunneling
Split-tunnel-policy tunnelspecified
--
Don't stop once you have upgraded your network! Improve the world by lending money to low-income workers:
http://www.Kiva.org/invitedBy/karsteni -
Remote VPN: split tunnel filtering
Hello!
The question is about the split tunnel filtering capabilities without using the vpn-filter.
Suppose, we have ASA configured for remote VPN tunneling with split without VPN filter.
- 10.0.0.0/8 is the private netwrok.
- 10.1.0.0/24 is the private network, defined in the split tunnel
- 172.16.1.0/24 is the VPN SECURE network
When the remote client connects, it receives the routes to the private network (10.1.0.0/24).
What happens if the remote client adds the route to a private network (which is not defined by a tunnel of split) by itself (e.g. 10.2.0.0/24)?
Our test LAB, we can see that the customer does not have access to 10.2.0.0/24.
Where the place in this case filtering?
- By default, all vehicles coming from VPN, bypasses all ACLs configured on interfaces ASA.
- Filter VPN is not configured.
- Nat0 don't traffic 10.0.0.0/8 to 172.16.1.0/24 NAT
- of the sh ip cry his on the VPN server, we can see, this ident is 0.0.0.0/0
- local ident (addr, mask, prot, port): (0.0.0.0/0.0.0.0/0/0)
- Remote ident (addr, mask, prot, port): (172.16.1.1/255.255.255.255/0/0)
The ACL of split tunnel is capable for remote client traffic filtering?
I understand that your question is in what regards the IPSec VPN Client, no AnyConnect VPN Client, however, I think that the behavior of the split tunnel is the same.
Here's the answer to your question:
A. AnyConnect applies the policy of tunnel in 2 ways:
Monitoring of track 1) and repair (for example if you change the routing table), AnyConnect will restore it to what has been configured.
(2) filtering (on platforms that support filter engines). Filtering ensures that even if you can perform a kind of injection of the route, the filters would block packets.
-
Router Cisco client VPN SPlit tunnel does not work
Hello!
I have configured the Cisco VPN CLient on a 2821 router, and it works fine.
I could access the inside resourses normally >
the problem is that when I connect with VPN I lost internet connectivity?What wrong with my setup?
Below the current configuration of the router.
Kind regards!CISCO2821 #sh run
Building configuration...
Current configuration: 5834 bytes
!
version 12.4
horodateurs service debug datetime msec
Log service timestamps datetime msec
no password encryption service
!
hostname CISCO2821
!
boot-start-marker
start the flash c2800nm-adventerprisek9 - mz.124 - 20.T.bin system
boot-end-marker
!
forest-meter operation of syslog messages
logging buffered 51200 warnings
!
AAA new-model
!
!
connection local VPN-LOCAL-AUTHENTIC AAA authentication
local AAA authorization network VPN-LOCAL-AUTHOR
!
!
AAA - the id of the joint session
!
dot11 syslog
IP source-route
!
!
IP cef
!
!
"yourdomain.com" of the IP domain name
8.8.8.8 IP name-server
No ipv6 cef
!
Authenticated MultiLink bundle-name Panel
!
!
voice-card 0
No dspfarm
!
!
username secret privilege 0 vpn 5 $1$ tCf1$ XAxQWtDRYdfy9g3JpVSvZ.
Archives
The config log
hidekeys
!
!
crypto ISAKMP policy 44
BA aes
preshared authentication
Group 2
life 44444
!
ISAKMP crypto group configuration of VPN client
key VPNVPNVPN
VPN-pool
ACL VPN-ACL-SPLIT
Max-users 5000
!
!
ISAKMP crypto ISAKMP-VPN-profile
identity VPN group match
list of authentication of client VPN-LOCAL-AUTHENTIC
VPN-LOCAL-AUTHOR of ISAKMP authorization list.
client configuration address respond
Configuration of VPN client group
virtual-model 44
!
!
Crypto ipsec transform-set VPN - SET esp - aes esp-sha-hmac
!
Crypto ipsec VPN-profile
transformation-VPN-SET game
Set isakmp VPN ISAKMP-PROFILE
!
!
interface GigabitEthernet0/0
IP 192.168.2.214 255.255.255.0
NAT outside IP
IP virtual-reassembly
IP tcp adjust-mss 1412
automatic duplex
automatic speed
!
interface GigabitEthernet0/1
IP 192.168.1.1 255.255.255.0
IP nat inside
IP virtual-reassembly
IP tcp adjust-mss 1412
automatic duplex
automatic speed
!
interface FastEthernet0/0/0
no ip address
Shutdown
automatic duplex
automatic speed
!
type of interface virtual-Template44 tunnel
IP unnumbered GigabitEthernet0/0
ipv4 ipsec tunnel mode
Tunnel ipsec VPN-PROFILE protection profile
!
interface Dialer0
no ip address
IP mtu 1452
IP virtual-reassembly
Shutdown
!
local pool IP VPN-POOL 192.168.1.150 192.168.1.250
IP forward-Protocol ND
IP http server
IP 8081 http port
23 class IP http access
local IP http authentication
no ip http secure server
IP http timeout policy slowed down 60 life 86400 request 10000
!
!
IP nat inside source list ACL - NAT interface GigabitEthernet0/0 overload
!
IP access-list standard ACL-TELNET
allow a
!
extended ACL - NAT IP access list
ip permit 192.168.1.0 0.0.0.255 any
IP extended ACL-VPN-SPLIT access list
ip permit 192.168.1.0 0.0.0.255 192.168.1.0 0.0.0.255
scope of access to IP-VPN-ACL-SPLIT list
!
control plan
!
exec banner ^ C
% Warning of password expiration.
-----------------------------------------------------------------------
Professional configuration Cisco (Cisco CP) is installed on this device
and it provides the default username "cisco" single use. If you have
already used the username "cisco" to connect to the router and your IOS image
supports the option "unique" user, that user name is already expired.
You will not be able to connect to the router with the username when you leave
This session.
It is strongly recommended that you create a new user name with a privilege level
15 using the following command.
username
secret privilege 15 0 Replace
and with the username and password you want use.
-----------------------------------------------------------------------
Line con 0
exec-timeout 0 0
Synchronous recording
line to 0
line vty 0 4
ACL-TELNET access class in
exec-timeout 30 0
privilege level 15
Synchronous recording
transport input telnet ssh
line vty 5 15
ACL-TELNET access class in
exec-timeout 30 0
privilege level 15
Synchronous recording
transport input telnet ssh
line vty 16 988
ACL-TELNET access class in
exec-timeout 30 0
Synchronous recording
transport input telnet ssh
!
Scheduler allocate 20000 1000
end
CISCO2821 #.
I think that you made a mistake with your ACL name. the ACL applied is "VPN-ACL-SPLIT" which is an empty ACL. You must switch to that of "ACL-VPN-SPLIT" that has the entry "ip 192.168.1.0 allow 0.0.0.255 192.168.1.0 0.0.0.255" inside.
-
Hi all
What is the best way to install a split tunneling on a network, Cisco ASA 5510 I with cisco vpn client.
Thank you
This is the on the split tunneling configuration guide:
http://www.Cisco.com/en/us/products/ps6120/products_configuration_example09186a0080702999.shtml
Hope that helps.
-
AnyConnect SSL VPN Split tunneling problem
Hello
We have home users that VPN in on a regular basis, but when they VPN in they cannot print locally or to connect to local resources. Is there a way to activate the split for all remote users VPN tunneling? It is not possible to add all the remote subnets, especially since I don't know which subnets are used and it would be a question of management. I noticed that when I connect to the House a new route is added to my PC, who prefers the VPN link.
I noticed one of the options with the client Anyconnect is 'enable local LAN access (if configured) '. Can I use?
Thanks in advance.
Hello
According to my understanding, you need to connect to your local printers while you are connected to the ASA via SSL VPN.
You can do this by creating a policy of exclusion of tunnel split on SAA and the local lan access on the client option, or you can use the profile AnyConnect allowing local lan access.
Please find the link below: -.
I hope it helps.
Thank you
Shilpa
-
VPN split tunnel with 1811W and IAS RADIUS problems
I am very new to the implementation of a VPN IPSEC with a Cisco router. I know very well on the way to do it with a PIX / ASA, but the controls are a bit different in IOS, where my questions. Here is what is happening, I can connect to the VPN with the Cisco VPN Client. I would assign it an address of my ip pool that I created, but when I try to access the remote network somehow, I can't. I ran a tracert and what is really weird, is that I get the external IP address of the 1811W as my first jump when I list an internal IP address of the remote network (it also fixes the device FULL domain name, so I know that my DNS configuration is correct). I will list my config to the 1811W as well as the screenshot of the tracert. I've removed all the passwords that are encrypted, but they are there in the router config and I am able to connect to the network and click the IAS server behind it. Please excuse the config as we took it during another TI provider so that it can have a few additional entries that may not be necessary that I have not yet cleaned.
Tracert:
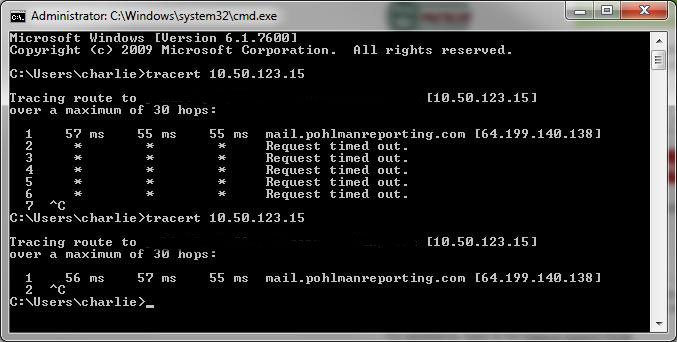
And here's the full config:
Building configuration...
Current configuration: 9320 bytes
!
version 12.4
no service button
horodateurs service debug datetime msec
Log service timestamps datetime localtime show-time zone
encryption password service
!
hostname RTR01
!
boot-start-marker
boot-end-marker
!
logging buffered 8192
enable password 7
!
AAA new-model
!
!
AAA authentication login userauthen local radius group
AAA authorization groupauthor LAN
!
!
AAA - the id of the joint session
clock TimeZone Central - 6
!
SSID dot11 internal
VLAN 5
open authentication
authentication wpa key management
Comments-mode
WPA - psk ascii 7
!
dot11 ssid public access
VLAN 10
open authentication
!
!
!
IP cef
No dhcp use connected vrf ip
DHCP excluded-address 192.168.1.1 IP 192.168.1.10
DHCP excluded-address IP 192.168.1.20 192.168.1.254
!
public IP dhcp pool
import all
network 192.168.1.0 255.255.255.0
default router 192.168.1.1
DNS-server 10.50.123.15 207.69.188.186
!
!
no ip domain search
IP domain name pohlmanreporting.com
!
Authenticated MultiLink bundle-name Panel
!
Crypto pki trustpoint TP-self-signed-3986412950
enrollment selfsigned
name of the object cn = IOS - Self - signed - certificate - 3986412950
revocation checking no
rsakeypair TP-self-signed-3986412950
!
!
TP-self-signed-3986412950 crypto pki certificate chain
certificate self-signed 01
quit smoking
!
!
password username admin privilege 15 7
username cisco password 7
username secret privilege 15 ssetech 5
Archives
The config log
!
!
!
!
crypto ISAKMP policy 1
BA 3des
md5 hash
preshared authentication
Group 2
!
crypto ISAKMP policy 10
BA 3des
preshared authentication
Group 2
!
Configuration group VPNGROUP crypto isakmp client
me?
DNS 10.50.123.15
domain domain.com
pool VPNPOOL
ACL 110
include-local-lan!
!
Crypto ipsec transform-set esp-3des-md5 esp-3des esp-md5-hmac
Crypto ipsec transform-set esp-des-md5 esp - esp-md5-hmac
Crypto ipsec transform-set esp-3des esp-sha-hmac TRANS_3DES_SHA
Crypto ipsec transform-set esp-3des esp-sha-hmac RIGHT
!
crypto dynamic-map EXA_DYNAMIC_MAP 10
Set transform-set RIGHT
market arriere-route
!
!
card crypto client EXT_MAP of authentication list userauthen
card crypto isakmp authorization list groupauthor EXT_MAP
crypto card for the EXT_MAP client configuration address respond
card crypto EXT_MAP 10-isakmp dynamic ipsec EXA_DYNAMIC_MAP
!
!
!
Bridge IRB
!
!
!
interface FastEthernet0
IP 64.199.140.138 255.255.255.248
IP access-group denied-hack-attack in
no ip redirection
no ip unreachable
no ip proxy-arp
NAT outside IP
IP virtual-reassembly
route IP cache flow
automatic duplex
automatic speed
No cdp enable
card crypto EXT_MAP
!
interface FastEthernet1
REDUNDANT INET CONNECTION description
no ip address
automatic duplex
automatic speed
!
interface FastEthernet2
!
interface FastEthernet3
!
interface FastEthernet4
!
interface FastEthernet5
!
FastEthernet6 interface
!
interface FastEthernet7
!
interface FastEthernet8
!
interface FastEthernet9
!
interface Dot11Radio0
Description 802. 11B / G interface
no ip address
!
encryption vlan 5 tkip encryption mode
!
SSID internal
!
public access SSID
!
Base speed - 1.0 2.0 basic basic-5, 5 6.0 9.0 basic-11, 0 12.0 18.0 24.0 36.0 48.0
channel 2462
root of station-role
!
interface Dot11Radio0.5
encapsulation dot1Q 5
No cdp enable
Bridge-Group 1
Bridge-group subscriber-loop-control 1
Bridge-Group 1 covering-disabled people
Bridge-Group 1 block-unknown-source
No source of bridge-Group 1-learning
unicast bridge-Group 1-floods
!
interface Dot11Radio0.10
encapsulation dot1Q 10
IP 192.168.1.1 255.255.255.0
IP access-group 130 to
IP nat inside
IP virtual-reassembly
No cdp enable
!
interface Dot11Radio1
description of the 802 interface. 11A
no ip address
Shutdown
Speed - Basic6.0 9.0 basic - 12.0 18.0 basic-24, 0-36.0 48.0 54.0
root of station-role
!
interface Vlan1
no ip address
Bridge-Group 1
!
interface Async1
no ip address
encapsulation sheet
!
interface BVI1
IP 10.50.123.1 255.255.255.0
IP access-group 105 to
IP nat inside
IP virtual-reassembly
IP tcp adjust-mss 1452
!
local IP VPNPOOL 192.168.130.1 pool 192.168.130.50
IP route 0.0.0.0 0.0.0.0 64.199.140.137
IP route 10.60.52.0 255.255.255.0 10.50.123.2
!
!
IP http server
local IP http authentication
IP http secure server
IP http timeout policy inactive 600 life 86400 request 10000
IP nat POOL 64.199.140.138 pool 64.199.140.142 netmask 255.255.255.248
overload of IP nat inside source list 120 interface FastEthernet0
IP nat inside source map of route-nat interface FastEthernet0 overload
IP nat inside source static tcp 10.50.123.14 21 64.199.140.138 21 expandable
IP nat inside source static tcp 10.50.123.11 25 64.199.140.138 25 expandable
IP nat inside source static tcp 10.50.123.11 80 64.199.140.138 80 extensible
IP nat inside source static tcp 10.50.123.11 143 64.199.140.138 143 extensible
IP nat inside source static tcp 10.50.123.11 443 64.199.140.138 443 extensible
IP nat inside source static tcp 10.50.123.10 64.199.140.138 1723 1723 extensible
IP nat inside source static tcp 10.50.123.14 21 64.199.140.139 21 expandable
IP nat inside source static tcp 10.50.123.18 80 64.199.140.139 80 extensible
IP nat inside source static tcp 10.50.123.18 443 64.199.140.139 443 extensible
IP nat inside source static tcp 10.50.123.18 64.199.140.139 3389 3389 extensible
IP nat inside source static tcp 10.50.123.14 80 64.199.140.141 80 extensible
IP nat inside source static tcp 10.50.123.14 443 64.199.140.141 443 extensible
IP nat inside source static 10.50.123.40 expandable 64.199.140.142
!
deny-hack-attack extended IP access list
permit udp 10.0.0.0 0.255.255.255 any eq snmp
deny udp any any eq snmp
deny udp any any eq tftp
deny udp any any eq bootpc
deny udp any any eq bootps
deny ip 172.16.0.0 0.15.255.255 all
deny ip 192.168.0.0 0.0.255.255 everything
allow an ip
!
recording of debug trap
record 10.50.123.15
access-list 99 allow 10.0.0.0 0.255.255.255
access-list 99 allow 69.63.100.0 0.0.1.255
access-list 102 permit ip 10.50.123.0 0.0.0.255 10.60.52.0 0.0.0.255
access-list 105 deny ip any host 69.63.101.225
105 ip access list allow a whole
access-list 110 permit ip 10.50.123.0 0.0.0.255 192.168.130.0 0.0.0.255
access-list 111 deny ip 10.50.123.0 0.0.0.255 10.10.0.0 0.0.255.255
access-list 111 deny ip 10.50.123.0 0.0.0.255 10.60.52.0 0.0.0.255
access-list 111 allow ip 10.50.123.0 0.0.0.255 any
access-list 112 deny ip 10.50.123.0 0.0.0.255 172.0.0.0 0.0.0.255
access ip-list 112 allow a whole
access-list 120 allow ip 192.168.1.0 0.0.0.255 any
access-list 130 allow udp 192.168.1.0 0.0.0.255 host 10.50.123.10 eq field
access list 130 permit tcp 192.168.1.0 0.0.0.255 host 10.50.123.10 eq field
access list 130 permit tcp 192.168.1.0 0.0.0.255 host 10.50.123.16 eq www
access list 130 permit tcp 192.168.1.0 0.0.0.255 host 10.50.123.16 eq 443
access-list 130 deny ip any 10.0.0.0 0.255.255.255
access-list 130 ip allow a whole
SNMP-server community no RO
!
!
!
map of route-nat allowed 10
corresponds to the IP 111
!
!
!
RADIUS-server host 10.50.123.13 auth-port 1645 acct-port 1646 hits 7
!
control plan
!
Bridge Protocol ieee 1
1 channel ip bridge
!
Line con 0
exec-timeout 120 0
line 1
Modem InOut
StopBits 1
Speed 115200
FlowControl hardware
line to 0
line vty 0 4
location * Access Virtual Terminal allowed only from internal network *.
access-class 99 in
exec-timeout 0 0
connection of authentication userauthen
transport input telnet ssh
!
max-task-time 5000 Planner!
WebVPN cef
!
WebVPN context Default_context
SSL authentication check all
!
no go
!
!
endYou must also create NAT exemption for traffic between your internal network to the VPN Client pool.
You have the following NAT 2 instructions:
overload of IP nat inside source list 120 interface FastEthernet0
IP nat inside source map of route-nat interface FastEthernet0 overloadFor the 120 access list, please add the following:
120 extended IP access list
1 refuse the ip 10.50.123.0 0.0.0.255 192.168.130.0 0.0.0.255
Uses of "-nat ' ACL 111 route map, please also add the following:
111 extended IP access list
1 refuse the ip 10.50.123.0 0.0.0.255 192.168.130.0 0.0.0.255
Then ' delete ip nat trans * "after the above changes and try to connect again.
Hope that helps.
-
Best Soho - Split Tunnel VPN router
Hi - I'm looking for some advice for a soho router.
Basically the main feature, I'm looking for is to run, which I think is a VPN split tunnel, so that all internal clients route default traffic out to the gateway of the ISP. However, if the traffic is destined for a list of several specific subnets (x.x.x.x/24, y.y.y.y/24 etc.), then it should establish a tunnel to an only PPTP/IPSEC host and route remote traffic for these subnets via the tunnel. To be clear, that these subnets (x.x.x.x and y.y.y.y) is not attached to the end of the tunnel - which is a gateway device that will route them further.
I've been watching the various VPN router offers and is not clear to me if I can do it with a RV - 042, BEFVP41 or something like the other thing SRP521W I must be able to manipulate the routing tables directly on.
As an additional note, I have complete control over the end of SOHO - but simply an account at the end of the tunnel with (it is a service provider). The idea is to use public services for 90% of the traffic, but if customers want to access a specific set of addresses, it will forward this specific traffic through the tunnel.
Thanks in advance...
On current view, do not touch the RPS with a bargepole.
Adding access to additional subnets through a VPN tunnel is pretty standard, routing will be automatic if the VPN was established, but you must ensure that
1. politics VPN at BOTH ENDS allows your local subnet to access these networks
2. your subnet is not incompatible with other subnets or roads that can be used on remote networks
3. assuming you're OK so far, remote subnets must have a route is added to the default gateway to point to your subnet via intermediate networks
Good luck!
-
Hello
I don't know what could be held, vpn users can ping to the outside and inside of the Cisco ASA interface but can not connect to servers or servers within the LAN ping.
is hell config please kindly and I would like to know what might happen.
hostname horse
domain evergreen.com
activate 2KFQnbNIdI.2KYOU encrypted password
2KFQnbNIdI.2KYOU encrypted passwd
names of
ins-guard
!
interface GigabitEthernet0/0
LAN description
nameif inside
security-level 100
192.168.200.1 IP address 255.255.255.0
!
interface GigabitEthernet0/1
Description CONNECTION_TO_FREEMAN
nameif outside
security-level 0
IP 196.1.1.1 255.255.255.248
!
interface GigabitEthernet0/2
Description CONNECTION_TO_TIGHTMAN
nameif backup
security-level 0
IP 197.1.1.1 255.255.255.248
!
interface GigabitEthernet0/3
Shutdown
No nameif
no level of security
no ip address
!
interface Management0/0
Shutdown
No nameif
no level of security
no ip address
management only
!
boot system Disk0: / asa844-1 - k8.bin
boot system Disk0: / asa707 - k8.bin
passive FTP mode
clock timezone WAT 1
DNS server-group DefaultDNS
domain green.com
network of the NETWORK_OBJ_192.168.2.0_25 object
Subnet 192.168.2.0 255.255.255.128
network of the NETWORK_OBJ_192.168.202.0_24 object
192.168.202.0 subnet 255.255.255.0
network obj_any object
subnet 0.0.0.0 0.0.0.0
the DM_INLINE_NETWORK_1 object-group network
object-network 192.168.200.0 255.255.255.0
object-network 192.168.202.0 255.255.255.0
the DM_INLINE_NETWORK_2 object-group network
object-network 192.168.200.0 255.255.255.0
object-network 192.168.202.0 255.255.255.0
access-list extended INSIDE_OUT allow ip 192.168.202.0 255.255.255.0 any
access-list extended INSIDE_OUT allow ip 192.168.200.0 255.255.255.0 any
Access extensive list permits all ip a OUTSIDE_IN
gbnlvpntunnel_splitTunnelAcl standard access list allow 192.168.200.0 255.255.255.0
standard access list gbnlvpntunnel_splitTunnelAcl allow 192.168.202.0 255.255.255.0
gbnlvpntunnell_splitTunnelAcl standard access list allow 192.168.200.0 255.255.255.0
standard access list gbnlvpntunnell_splitTunnelAcl allow 192.168.202.0 255.255.255.0
pager lines 24
Enable logging
asdm of logging of information
Within 1500 MTU
Outside 1500 MTU
backup of MTU 1500
mask of local pool VPNPOOL 192.168.2.0 - 192.168.2.100 IP 255.255.255.0
no failover
ICMP unreachable rate-limit 1 burst-size 1
ASDM image disk0: / asdm-645 - 206.bin
don't allow no asdm history
ARP timeout 14400
NAT (inside, outside) static source NETWORK_OBJ_192.168.202.0_24 NETWORK_OBJ_192.168.202.0_24 NETWORK_OBJ_192.168.2.0_25 NETWORK_OBJ_192.168.2.0_25 non-proxy-arp-search of route static destination
NAT (inside, backup) static source NETWORK_OBJ_192.168.202.0_24 NETWORK_OBJ_192.168.202.0_24 NETWORK_OBJ_192.168.2.0_25 NETWORK_OBJ_192.168.2.0_25 non-proxy-arp-search of route static destination
NAT (inside, outside) static source DM_INLINE_NETWORK_1 DM_INLINE_NETWORK_1 NETWORK_OBJ_192.168.2.0_25 NETWORK_OBJ_192.168.2.0_25 non-proxy-arp-search of route static destination
NAT (inside, backup) static source DM_INLINE_NETWORK_2 DM_INLINE_NETWORK_2 NETWORK_OBJ_192.168.2.0_25 NETWORK_OBJ_192.168.2.0_25 non-proxy-arp-search of route static destination
!
network obj_any object
dynamic NAT interface (inside, backup)
Access-group interface inside INSIDE_OUT
Access-group OUTSIDE_IN in interface outside
Route outside 0.0.0.0 0.0.0.0 196.1.1.2 1 track 10
Route outside 0.0.0.0 0.0.0.0 197.1.1.2 254
Timeout xlate 03:00
Pat-xlate timeout 0:00:30
Timeout conn 01:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
Sunrpc timeout 0:10:00 h323 0:05:00 h225 mgcp from 01:00 0:05:00 mgcp-pat 0:05:00
Sip timeout 0:30:00 sip_media 0:02:00 prompt Protocol sip-0: 03:00 sip - disconnect 0:02:00
Timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
Floating conn timeout 0:00:00
dynamic-access-policy-registration DfltAccessPolicy
identity of the user by default-domain LOCAL
Enable http server
http 192.168.200.0 255.255.255.0 inside
http 192.168.202.0 255.255.255.0 inside
No snmp server location
No snmp Server contact
Server enable SNMP traps snmp authentication linkup, linkdown cold start
monitor SLA 100
type echo protocol ipIcmpEcho 212.58.244.71 interface outside
Timeout 3000
frequency 5
monitor als 100 calendar life never start-time now
Crypto ipsec transform-set ikev1 ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
Crypto ipsec transform-set ikev1 ESP-DES-SHA esp - esp-sha-hmac
Crypto ipsec transform-set ikev1 SHA-ESP-3DES esp-3des esp-sha-hmac
Crypto ipsec transform-set ikev1 esp ESP-DES-MD5-esp-md5-hmac
Crypto ipsec transform-set ikev1 ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
Crypto ipsec transform-set ikev1 ESP-3DES-MD5-esp-3des esp-md5-hmac
Crypto ipsec transform-set ikev1 ESP-AES-256-SHA esp-aes-256 esp-sha-hmac
Crypto ipsec transform-set ikev1 ESP-AES-128-SHA aes - esp esp-sha-hmac
Crypto ipsec transform-set ikev1 ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
Crypto ipsec transform-set ikev1 ESP-AES-128-MD5-esp - aes esp-md5-hmac
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 pfs Group1 set
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 define ikev1 transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA MD5-ESP-3DES ESP-DES-SHA ESP-DES-MD5
outside_map card crypto 65535-isakmp dynamic ipsec SYSTEM_DEFAULT_CRYPTO_MAP
outside_map interface card crypto outside
backup_map card crypto 65535-isakmp dynamic ipsec SYSTEM_DEFAULT_CRYPTO_MAP
backup of crypto backup_map interface card
Crypto ikev1 allow outside
Crypto ikev1 enable backup
IKEv1 crypto policy 10
authentication crack
aes-256 encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 20
authentication rsa - sig
aes-256 encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 30
preshared authentication
aes-256 encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 40
authentication crack
aes-192 encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 50
authentication rsa - sig
aes-192 encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 60
preshared authentication
aes-192 encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 70
authentication crack
aes encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 80
authentication rsa - sig
aes encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 90
preshared authentication
aes encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 100
authentication crack
3des encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 110
authentication rsa - sig
3des encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 120
preshared authentication
3des encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 130
authentication crack
the Encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 140
authentication rsa - sig
the Encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 150
preshared authentication
the Encryption
sha hash
Group 2
life 86400
!
track 10 rtr 100 accessibility
Telnet 192.168.200.0 255.255.255.0 inside
Telnet 192.168.202.0 255.255.255.0 inside
Telnet timeout 5
SSH 192.168.202.0 255.255.255.0 inside
SSH 192.168.200.0 255.255.255.0 inside
SSH 0.0.0.0 0.0.0.0 outdoors
SSH timeout 15
SSH group dh-Group1-sha1 key exchange
Console timeout 0
management-access inside
a basic threat threat detection
Statistics-list of access threat detection
no statistical threat detection tcp-interception
WebVPN
internal group vpntunnel strategy
Group vpntunnel policy attributes
Ikev1 VPN-tunnel-Protocol
Split-tunnel-policy tunnelspecified
value of Split-tunnel-network-list vpntunnel_splitTunnelAcl
field default value green.com
internal vpntunnell group policy
attributes of the strategy of group vpntunnell
Ikev1 VPN-tunnel-Protocol
Split-tunnel-policy tunnelspecified
value of Split-tunnel-network-list gbnlvpntunnell_splitTunnelAcl
field default value green.com
Green user name encrypted BoEFKkDtbnX5Uy1Q privilege 15 password
attributes of user name THE
VPN-group-policy gbnlvpn
tunnel-group vpntunnel type remote access
tunnel-group vpntunnel General attributes
address VPNPOOL pool
strategy-group-by default vpntunnel
tunnel-group vpntunnel ipsec-attributes
IKEv1 pre-shared-key *.
type tunnel-group vpntunnell remote access
tunnel-group vpntunnell General-attributes
address VPNPOOL2 pool
Group Policy - by default-vpntunnell
vpntunnell group of tunnel ipsec-attributes
IKEv1 pre-shared-key *.
!
class-map inspection_default
match default-inspection-traffic
!
!
type of policy-card inspect dns migrated_dns_map_1
parameters
maximum message length automatic of customer
message-length maximum 512
Policy-map global_policy
class inspection_default
inspect the migrated_dns_map_1 dns
inspect the ftp
inspect h323 h225
inspect the h323 ras
inspect the rsh
inspect the rtsp
inspect esmtp
inspect sqlnet
inspect the skinny
inspect sunrpc
inspect xdmcp
inspect the sip
inspect the netbios
inspect the tftp
Review the ip options
!
global service-policy global_policy
context of prompt hostname
no remote anonymous reporting call
call-home
Profile of CiscoTAC-1
no active account
http https://tools.cisco.com/its/service/oddce/services/DDCEService destination address
email address of destination [email protected] / * /
destination-mode http transport
Subscribe to alert-group diagnosis
Subscribe to alert-group environment
Subscribe to alert-group monthly periodic inventory
monthly periodicals to subscribe to alert-group configuration
daily periodic subscribe to alert-group telemetry
Cryptochecksum:7c1b1373bf2e2c56289b51b8dccaa565
Hello
1 - Please run these commands:
"crypto isakmp nat-traversal 30.
"crypto than dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 Road opposite value.
The main issue here is that you have two roads floating and outside it has a better than backup metric, that's why I added the command 'reverse-road '.
Please let me know.
Thank you.
-
Windows - Internet access, no split Tunnel L2TP VPN Clients does not
Greetings!
I have four ASA 5505 that I configured with 4 site to site VPN tunnels (works perfectly) to connect to our company facilities 4. The ASA is also configured with remote access L2TP/IPsec so that a specific group of users of portable computers can connect to and access to all facilities. It also works very well except for one important exception - my split tunnel setting doesn't seem to work, because I can't connect to the Internet outside the VPN resources.
I accept the inherent risk of allowing tunnels to split from a security point of view since I take the necessary steps to secure the systems used for remote access. I would appreciate any feedback on how to get the job of split tunnel.
Here is the configuration:
: Saved
:
ASA Version 1.0000 11
!
SGC hostname
domain somewhere.com
names of
COMMENTS COMMENTS LAN 192.168.2.0 name description
name 75.185.129.13 description of SGC - external INTERNAL ASA
name 172.22.0.0 description of SITE1-LAN Ohio management network
description of SITE2-LAN name 172.23.0.0 Lake Club Network
name 172.24.0.0 description of training3-LAN network Southwood
description of training3 - ASA 123.234.8.124 ASA Southwoods name
INTERNAL name 192.168.10.0 network Local INTERNAL description
description of name 192.168.11.0 INTERNAL - VPN VPN INTERNAL Clients
description of Apollo name 192.168.10.4 INTERNAL domain controller
description of DHD name 192.168.10.2 Access Point #1
description of GDO name 192.168.10.3 Access Point #2
description of Odyssey name 192.168.10.5 INTERNAL Test Server
CMS internal description INTERNAL ASA name 192.168.10.1
name 123.234.8.60 description of SITE1 - ASA ASA management Ohio
description of SITE2 - ASA 123.234.8.189 Lake Club ASA name
description of training3-VOICE name Southwood Voice Network 10.1.0.0
name 172.25.0.0 description of training3-WIFI wireless Southwood
!
interface Vlan1
nameif outside
security-level 0
IP address dhcp setroute
!
interface Vlan2
nameif INSIDE
security-level 100
255.255.255.0 SGC-internal IP address
!
interface Vlan3
nameif COMMENTS
security-level 50
IP 192.168.2.1 255.255.255.0
!
interface Ethernet0/0
Time Warner Cable description
!
interface Ethernet0/1
switchport access vlan 2
switchport trunk allowed vlan 2-3
switchport vlan trunk native 2
switchport mode trunk
!
interface Ethernet0/2
switchport access vlan 2
switchport trunk allowed vlan 2-3
switchport vlan trunk native 2
switchport mode trunk
!
interface Ethernet0/3
switchport access vlan 2
switchport trunk allowed vlan 2-3
switchport vlan trunk native 2
switchport mode trunk
!
interface Ethernet0/4
switchport access vlan 2
switchport trunk allowed vlan 2-3
switchport vlan trunk native 2
switchport mode trunk
!
interface Ethernet0/5
switchport access vlan 2
switchport trunk allowed vlan 2-3
switchport vlan trunk native 2
switchport mode trunk
!
interface Ethernet0/6
Description for Wireless AP Trunk Port
switchport access vlan 2
switchport trunk allowed vlan 2-3
switchport vlan trunk native 2
switchport mode trunk
!
interface Ethernet0/7
Description for Wireless AP Trunk Port
switchport access vlan 2
switchport trunk allowed vlan 2-3
switchport vlan trunk native 2
switchport mode trunk
!
boot system Disk0: / asa821-11 - k8.bin
Disk0: / config.txt boot configuration
passive FTP mode
clock timezone IS - 5
clock to summer time EDT recurring
DNS domain-lookup outside
INTERNAL DNS domain-lookup
DNS domain-lookup GUEST
DNS server-group DefaultDNS
Name-Server 4.2.2.2
domain somewhere.com
permit same-security-traffic inter-interface
permit same-security-traffic intra-interface
DM_INLINE_TCP_1 tcp service object-group
EQ port 3389 object
port-object eq www
EQ object of the https port
EQ smtp port object
the DM_INLINE_NETWORK_1 object-group network
network-object SITE1-LAN 255.255.0.0
network-object SITE2-LAN 255.255.0.0
network-object training3-LAN 255.255.0.0
object-group training3-GLOBAL network
Southwood description Global Network
network-object training3-LAN 255.255.0.0
network-object training3-VOICE 255.255.0.0
network-object training3-WIFI 255.255.0.0
DM_INLINE_TCP_2 tcp service object-group
EQ port 5900 object
EQ object Port 5901
object-group network INTERNAL GLOBAL
Description Global INTERNAL Network
network-object INTERNAL 255.255.255.0
network-object INTERNALLY-VPN 255.255.255.0
access-list outside_access note Pings allow
outside_access list extended access permit icmp any CMS-external host
access-list outside_access note that VNC for Camille
outside_access list extended access permit tcp any host CMS-external object-group DM_INLINE_TCP_2
access-list outside_access note INTERNAL Services
outside_access list extended access permit tcp any host CMS-external object-group DM_INLINE_TCP_1
DefaultRAGroup_splitTunnelAcl list standard access allowed INTERNAL 255.255.255.0
access-list sheep extended ip INTERNAL 255.255.255.0 allow INTERNAL VPN 255.255.255.0
access-list extended sheep allowed ip IN-HOUSE-GLOBAL SITE1-LAN 255.255.0.0 object-group
access-list extended sheep allowed ip IN-HOUSE-GLOBAL SITE2-LAN 255.255.0.0 object-group
access-list extended sheep allowed ip object-IN-HOUSE-GLOBAL object group training3-GLOBAL
access-list INTERNAL-to-SITE1 extended permit ip IN-HOUSE-GLOBAL SITE1-LAN 255.255.0.0 object-group
access-list INTERNAL-to-training3 extended permitted ip object-IN-HOUSE-GLOBAL object group training3-GLOBAL
access-list INTERNAL-to-SITE2 extended permit ip IN-HOUSE-GLOBAL SITE2-LAN 255.255.0.0 object-group
no pager
Enable logging
exploitation forest asdm warnings
Debugging trace record
Outside 1500 MTU
MTU 1500 INTERNAL
MTU 1500 COMMENTS
192.168.11.1 mask - local 192.168.11.25 pool IN-HOUSE VPN IP 255.255.255.0
no failover
ICMP unreachable rate-limit 1 burst-size 1
ASDM image disk0: / asdm - 623.bin
enable ASDM history
ARP timeout 14400
Global 1 interface (outside)
(INTERNAL) NAT 0 access-list sheep
NAT (INTERNAL) 1 0.0.0.0 0.0.0.0
NAT (GUEST) 1 0.0.0.0 0.0.0.0
5900 5900 Camille netmask 255.255.255.255 interface static tcp (GUEST, outdoor)
3389 3389 Apollo netmask 255.255.255.255 interface static tcp (INDOOR, outdoor)
public static tcp (INDOOR, outdoor) interface www Apollo www netmask 255.255.255.255
public static tcp (INDOOR, outdoor) interface https Apollo https netmask 255.255.255.255
public static tcp (INDOOR, outdoor) interface smtp smtp Apollo netmask 255.255.255.255
5901 puppy 5901 netmask 255.255.255.255 interface static tcp (GUEST, outdoor)
Access-group outside_access in interface outside
Timeout xlate 0:05:00
Timeout conn 01:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
Sunrpc timeout 0:10:00 h323 0:05:00 h225 mgcp from 01:00 0:05:00 mgcp-pat 0:05:00
Sip timeout 0:30:00 sip_media 0:02:00 prompt Protocol sip-0: 03:00 sip - disconnect 0:02:00
Timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
dynamic-access-policy-registration DfltAccessPolicy
RADIUS protocol AAA-server Apollo
Apollo (INTERNAL) AAA-server Apollo
Timeout 5
key *.
AAA authentication enable LOCAL console
the ssh LOCAL console AAA authentication
AAA authentication LOCAL telnet console
AAA authentication http LOCAL console
Enable http server
http 0.0.0.0 0.0.0.0 INTERNAL
http 0.0.0.0 0.0.0.0 COMMENTS
No snmp server location
No snmp Server contact
Community SNMP-server
Server enable SNMP traps snmp authentication linkup, linkdown cold start
Crypto ipsec transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
Crypto ipsec transform-set ESP-DES-SHA esp - esp-sha-hmac
Crypto ipsec transform-set ESP-DES-MD5 esp - esp-md5-hmac
Crypto ipsec transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
Crypto ipsec transform-set ESP-3DES-MD5-esp-3des esp-md5-hmac
Crypto ipsec transform-set ESP-AES-256-SHA 256 - aes - esp esp-sha-hmac
Crypto ipsec transform-set ESP-AES-128-SHA aes - esp esp-sha-hmac
Crypto ipsec transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
Crypto ipsec transform-set ESP-AES-128-MD5-esp - aes esp-md5-hmac
Crypto ipsec transform-set esp-3des esp-sha-hmac TRANS_ESP_3DES_SHA
Crypto ipsec transform-set transit mode TRANS_ESP_3DES_SHA
Crypto ipsec transform-set esp-SHA-ESP-3DES-3des esp-sha-hmac
life crypto ipsec security association seconds 28800
Crypto ipsec kilobytes of life - safety 4608000 association
SYSTEM_DEFAULT_CRYPTO_MAP game 65535 dynamic-map crypto transform-set ESP-3DES-SHA TRANS_ESP_3DES_SHA
correspondence address 1 card crypto outside_map INTERNAL SITE1
card crypto outside_map 1 set of peer SITE1 - ASA
card crypto outside_map 1 set of transformation-ESP-3DES-SHA
address for correspondence card crypto outside_map 2 INTERNAL training3
outside_map 2 peer training3 - ASA crypto card game
card crypto outside_map 2 game of transformation-ESP-3DES-SHA
address for correspondence outside_map 3 card crypto INTERNAL SITE2
game card crypto outside_map 3 peers SITE2 - ASA
card crypto outside_map 3 game of transformation-ESP-3DES-SHA
outside_map card crypto 65535-isakmp dynamic ipsec SYSTEM_DEFAULT_CRYPTO_MAP
outside_map interface card crypto outside
crypto ISAKMP allow outside
crypto ISAKMP policy 10
preshared authentication
3des encryption
sha hash
Group 2
life 86400
delimiter group @.
Telnet training3 - ASA 255.255.255.255 outside
Telnet SITE2 - ASA 255.255.255.255 outside
Telnet SITE1 - ASA 255.255.255.255 outside
Telnet 0.0.0.0 0.0.0.0 INTERNAL
Telnet 0.0.0.0 0.0.0.0 COMMENTS
Telnet timeout 60
SSH enable ibou
SSH training3 - ASA 255.255.255.255 outside
SSH SITE2 - ASA 255.255.255.255 outside
SSH SITE1 - ASA 255.255.255.255 outside
SSH 0.0.0.0 0.0.0.0 INTERNAL
SSH 0.0.0.0 0.0.0.0 COMMENTS
SSH timeout 60
Console timeout 0
access to the INTERNAL administration
Hello to tunnel L2TP 100
interface ID client DHCP-client to the outside
dhcpd dns 4.2.2.1 4.2.2.2
dhcpd ping_timeout 750
dhcpd outside auto_config
!
address INTERNAL 192.168.10.100 dhcpd - 192.168.10.200
dhcpd Apollo Odyssey interface INTERNAL dns
dhcpd somewhere.com domain INTERNAL interface
interface of dhcpd option 150 ip 10.1.1.40 INTERNAL
enable dhcpd INTERNAL
!
dhcpd address 192.168.2.100 - 192.168.2.200 COMMENTS
dhcpd dns 4.2.2.1 4.2.2.2 interface COMMENTS
enable dhcpd COMMENTS
!a basic threat threat detection
statistical threat detection port
Statistical threat detection Protocol
Statistics-list of access threat detection
a statistical threat detection tcp-interception rate-interval 30 burst-400-rate average rate 200
NTP server 192.43.244.18 prefer external source
WebVPN
allow outside
CSD image disk0:/securedesktop-asa-3.4.2048.pkg
SVC disk0:/sslclient-win-1.1.4.179.pkg 1 image
SVC disk0:/anyconnect-win-2.4.1012-k9.pkg 2 image
enable SVC
Group Policy DefaultRAGroup INTERNAL
attributes of Group Policy DefaultRAGroup
Server DNS 192.168.10.4 value
Protocol-tunnel-VPN l2tp ipsec
Split-tunnel-policy tunnelspecified
value of Split-tunnel-network-list DefaultRAGroup_splitTunnelAcl
value by default-domain somewhere.com
Group Policy DefaultWEBVPNGroup INTERNAL
attributes of Group Policy DefaultWEBVPNGroup
VPN-tunnel-Protocol webvpn
Group Policy DefaultL2LGroup INTERNAL
attributes of Group Policy DefaultL2LGroup
Protocol-tunnel-VPN IPSec l2tp ipsec
Group Policy DefaultACVPNGroup INTERNAL
attributes of Group Policy DefaultACVPNGroup
VPN-tunnel-Protocol svc
attributes of Group Policy DfltGrpPolicy
value of 192.168.10.4 DNS Server 4.2.2.2
VPN - 25 simultaneous connections
VPN-idle-timeout no
Protocol-tunnel-VPN IPSec
Split-tunnel-policy tunnelspecified
value of Split-tunnel-network-list DefaultRAGroup_splitTunnelAcl
value by default-domain somewhere.com
the value INTERNAL VPN address pools
chip-removal-disconnect disable card
WebVPN
SVC keepalive no
client of dpd-interval SVC no
dpd-interval SVC bridge no
value of customization DfltCustomization
attributes global-tunnel-group DefaultRAGroup
VPN INTERNAL address pool
Group Policy - by default-DefaultRAGroup
IPSec-attributes tunnel-group DefaultRAGroup
pre-shared-key *.
Disable ISAKMP keepalive
tunnel-group DefaultRAGroup ppp-attributes
No chap authentication
no authentication ms-chap-v1
ms-chap-v2 authentication
attributes global-tunnel-group DefaultWEBVPNGroup
VPN INTERNAL address pool
Group Policy - by default-DefaultWEBVPNGroup
tunnel-group 123.234.8.60 type ipsec-l2l
IPSec-attributes tunnel-group 123.234.8.60
pre-shared-key *.
tunnel-group 123.234.8.124 type ipsec-l2l
IPSec-attributes tunnel-group 123.234.8.124
pre-shared-key *.
tunnel-group 123.234.8.189 type ipsec-l2l
IPSec-attributes tunnel-group 123.234.8.189
pre-shared-key *.
type tunnel-group DefaultACVPNGroup remote access
attributes global-tunnel-group DefaultACVPNGroup
VPN INTERNAL address pool
Group Policy - by default-DefaultACVPNGroup
!
class-map inspection_default
match default-inspection-traffic
!
!
type of policy-card inspect dns preset_dns_map
parameters
message-length maximum 512
Policy-map global_policy
class inspection_default
inspect the preset_dns_map dns
inspect the ftp
inspect h323 h225
inspect the h323 ras
inspect the netbios
inspect the rsh
inspect the rtsp
inspect the skinny
inspect esmtp
inspect sqlnet
inspect sunrpc
inspect the tftp
inspect the sip
inspect xdmcp
inspect the http
inspect the they
!
global service-policy global_policy
context of prompt hostname
Cryptochecksum:423c807c0d63cb3e9aeceda977053f84
: end
ASDM image disk0: / asdm - 623.bin
ASDM location Camille 255.255.255.255 INTERNAL
ASDM location INTERNAL CGT-external 255.255.255.255
ASDM location INTERNAL SITE1-LAN 255.255.0.0
ASDM location INTERNAL SITE2-LAN 255.255.0.0
ASDM location INTERNAL training3-LAN 255.255.0.0
ASDM location INTERNAL training3 - ASA 255.255.255.255
ASDM location INTERNAL GDO 255.255.255.255
ASDM location INTERNAL SITE1 - ASA 255.255.255.255
ASDM location INTERNAL SITE2 - ASA 255.255.255.255
ASDM location INTERNAL training3-VOICE 255.255.0.0
ASDM location puppy 255.255.255.255 INTERNAL
enable ASDM historyI should also mention that my test clients are a combination of Windows XP, Windows 7, and Windows Mobile. Other that in specifying the preshared key and forcing L2TP/IPsec on the client side, the VPN settings on clients are the default settings with the help of MS-CHAP/MS-CHAPv2.
You must configure * intercept-dhcp enable * in your group strategy:
attributes of Group Policy DefaultRAGroup
attributes of Group Policy DefaultRAGroup
Server DNS 192.168.10.4 value
Protocol-tunnel-VPN l2tp ipsec
Split-tunnel-policy tunnelspecified
value of Split-tunnel-network-list DefaultRAGroup_splitTunnelAcl
value by default-domain somewhere.comIntercept-dhcp enable
-Latptop VPN clients (which I assume are on windows computers) is also the * use on remote network default gateway * box unchecked. It is located on the Advanced tab of VPN client TCP/IP properties. Select Client VPN > properties > Networking > TCP/IP Internet Protocol > properties > advanced and uncheck the box.
Alex
-
Easy VPN between two ASA 9.5 - Split tunnel does not
Hi guys,.
We have set up a site to site vpn using easy configuration vpn between ver 9.5 race (1) two ASA. The tunnels are up and ping is reached between sites. I also configured split tunnel for internet traffic under the overall strategy of the ASA easy vpn server. But for some unknown reason all the customer same internet traffic is sent to the primary site. I have configured NAT to relieve on the side of server and client-side. Please advise if no limitation so that the installation program.
Thank you and best regards,
Arjun T P
I have the same question and open a support case.
It's a bug in the software 9.5.1. See the bug: CSCuw22886
-
Web VPN/SSL - general Split Tunnel capable?
When I look through some examples of configuration for IOS Web VPN - it seems you attract to the filling of a web page of web sites that users can go to. I would be rather thin client act as client light 4.x CVPN - divided for example tunnel with access to a resource internal resource. Is this possible with Cisco VPN Web? Also - with is WebVPN any ability of the NAC?
I'm not sure IOS SSL vpn, but on the asa webvpn, there is a complete client ssl option. With this, you can either create a tunnel, or all split tunnel and the only defined networks. I hope that answers your question.
-
VPN, Internet and a Split Tunnels traffic
Please attached photo because I hope that explains what I really want to do, but here's the break down.
When a VPN Client connects to remote access to 1-ASA5510 I want all Internet traffic to send to 2 - ASA5510 instead of back to the default route. When it comes out 2-ASA5510, it passes through the content filter. 2 - ASA5510 has Split Tunnel put in place and we are trying to do away with Tunnel from SPlit.
I hope this is clear enough.
Any ideas would be helpful
Dan
Dan,
Difficult but doable! First of all, there is a nice feature in the ASA that allows configuration of remote proxy based on VPN profile by: -.
Group Policy <> attributes
use a MSIE-proxy-server method
Internet Explorer-proxy server value x.x.x.x
activate Internet Explorer-proxy local-bypass
Well Yes you guessed it - works only on Microsoft Internet Explorer.
I don't think that any policy based routing would work for you - bad luck.
But you can try another feature - traffic through the tunnel, which is normally used in the topllogy of EasyVPN: -.
Configuration of the ASA at the bottom, I probably would test this with the IP address of the 2651 router!
HTH.
-
Hello everyone
I have setup a VPN connection, which I can connect to. For all customers of connection, I want to give them an IP (from a subnet maybe) and let them use this IP address for all that they do.
Therefore, this:
and not current:

My inside is 192.168.1.0
My VPN IP pool is 192.168.30.5 - 200
My server (DNS, files, Web site) is 192.168.1.222Here's my setup. I scored what I thought might have something to do with it:
ASA Version 9.2 (1)
!
ciscoasa hostname
activate 8Ry2YjIyt7RRXU24 encrypted password
volatile xlate deny tcp any4 any4
volatile xlate deny tcp any4 any6
volatile xlate deny tcp any6 any4
volatile xlate deny tcp any6 any6
volatile xlate deny udp any4 any4 eq field
volatile xlate deny udp any4 any6 eq field
volatile xlate deny udp any6 any4 eq field
volatile xlate deny udp any6 any6 eq field
2KFQnbNIdI.2KYOU encrypted passwd
names of
pool of IP local IP-pool 192.168.30.5 - 192.168.30.200 mask 255.255.255.0
!
interface Ethernet0/0
switchport access vlan 2
!
interface Ethernet0/1
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
!
interface Ethernet0/7
!
interface Vlan1
nameif inside
security-level 100
IP 192.168.1.253 255.255.255.0
!
interface Vlan2
nameif outside
security-level 0
IP address dhcp setroute
!
boot system Disk0: / asa921 - k8.bin
passive FTP mode
permit same-security-traffic intra-interface
network obj_any object
subnet 0.0.0.0 0.0.0.0
network of the object Server-25
Home 192.168.1.222
Description of the test server
network of the object server-80
Home 192.168.1.222
Description of the test server
network of the object server-443
Home 192.168.1.222
Description of the test server
network of the object server-2525
Home 192.168.1.222
Description of the test server
network of the object server-993
Home 192.168.1.222
Description of the test server
network of the object server-6001
Home 192.168.1.222
Description of the test server
network of the object server-6002
Home 192.168.1.222
Description of the test server
network of the object server-6003
Home 192.168.1.222
Description of the test server
network of the object server-6004
Home 192.168.1.222
Description of the test server
network of the VPN HOST object
192.168.30.0 subnet 255.255.255.0
the object to the Interior-net network
host 192.168.1.0
the VPN server object network
Home 192.168.1.222
outside_access_in list extended access permit tcp any object Server-25 eq smtp
outside_access_in list extended access permit tcp any object server-2525 2525 eq
outside_access_in list extended access permit tcp any object server-80 eq www
outside_access_in list extended access permit tcp any object server-443 https eq
outside_access_in list extended access permit tcp any object server-993 993 eq
outside_access_in list extended access permit tcp any object server-6001 eq 6001
outside_access_in list extended access permit tcp any object server-6002 6002 eq
outside_access_in list extended access permit tcp any object server-6003 eq 6003
outside_access_in list extended access permit tcp any object server-6004 eq 6004
outside_access_in to access ip 192.168.1.0 scope list allow 255.255.255.0 192.168.30.0 255.255.255.0
permit access-list Split-Tunnel-ACL standard 192.168.30.0 255.255.255.0
no pager
Enable logging
asdm of logging of information
Within 1500 MTU
Outside 1500 MTU
ICMP unreachable rate-limit 1 burst-size 1
ASDM image disk0: / asdm - 721.bin
don't allow no asdm history
ARP timeout 14400
no permit-nonconnected arp
NAT (indoor, outdoor) Interior-net Interior-NET static source static destination HOST-VPN-VPN-HOST
NAT VPN VPN-server destination (indoor, outdoor) static static source HOST-VPN-VPN-HOST
!
network obj_any object
NAT dynamic interface (indoor, outdoor)
network of the object Server-25
NAT (inside, outside) interface static tcp smtp smtp service
network of the object server-80
NAT (inside, outside) interface static tcp www www service
network of the object server-443
NAT (inside, outside) interface static tcp https https service
network of the object server-2525
NAT (inside, outside) interface static 2525 2525 tcp service
network of the object server-993
NAT (inside, outside) interface static tcp 993 993 service
network of the object server-6001
NAT (inside, outside) interface static tcp 6001 6001 service
network of the object server-6002
NAT (inside, outside) interface static tcp 6002 6002 service
network of the object server-6003
NAT (inside, outside) interface static 6003 6003 tcp service
network of the object server-6004
NAT (inside, outside) interface static service tcp 6004 6004
Access-group outside_access_in in interface outside
Timeout xlate 03:00
Pat-xlate timeout 0:00:30
Timeout conn 01:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
Sunrpc timeout 0:10:00 h323 0:05:00 h225 mgcp from 01:00 0:05:00 mgcp-pat 0:05:00
Sip timeout 0:30:00 sip_media 0:02:00 prompt Protocol sip-0: 03:00 sip - disconnect 0:02:00
Timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
Floating conn timeout 0:00:00
dynamic-access-policy-registration DfltAccessPolicy
RADIUS AAA server HSS-auth-server protocol
allow only
AAA-server HSS-auth-server (inside) host 192.168.1.222
Timeout 5
key *.
identity of the user by default-domain LOCAL
Enable http server
http 192.168.1.0 255.255.255.0 inside
No snmp server location
No snmp Server contact
Crypto ipsec transform-set ikev1 ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
Crypto ipsec transform-set ikev1 ESP-DES-SHA esp - esp-sha-hmac
Crypto ipsec transform-set ikev1 SHA-ESP-3DES esp-3des esp-sha-hmac
Crypto ipsec transform-set ikev1 esp ESP-DES-MD5-esp-md5-hmac
Crypto ipsec transform-set ikev1 ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
Crypto ipsec transform-set ikev1 ESP-3DES-MD5-esp-3des esp-md5-hmac
Crypto ipsec transform-set ikev1 ESP-AES-256-SHA esp-aes-256 esp-sha-hmac
Crypto ipsec transform-set ikev1 ESP-AES-128-SHA aes - esp esp-sha-hmac
Crypto ipsec transform-set ikev1 ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
Crypto ipsec transform-set ikev1 ESP-AES-128-MD5-esp - aes esp-md5-hmac
Crypto ipsec pmtu aging infinite - the security association
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 define ikev1 transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA MD5-ESP-3DES ESP-DES-SHA ESP-DES-MD5
outside_map card crypto 65535-isakmp dynamic ipsec SYSTEM_DEFAULT_CRYPTO_MAP
outside_map interface card crypto outside
trustpool crypto ca policy
Crypto isakmp nat-traversal 30
Crypto ikev1 allow outside
IKEv1 crypto policy 10
authentication crack
aes-256 encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 20
authentication rsa - sig
aes-256 encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 30
preshared authentication
aes-256 encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 40
authentication crack
aes-192 encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 50
authentication rsa - sig
aes-192 encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 60
preshared authentication
aes-192 encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 70
authentication crack
aes encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 80
authentication rsa - sig
aes encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 90
preshared authentication
aes encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 100
authentication crack
3des encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 110
authentication rsa - sig
3des encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 120
preshared authentication
3des encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 130
authentication crack
the Encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 140
authentication rsa - sig
the Encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 150
preshared authentication
the Encryption
sha hash
Group 2
life 86400
Telnet timeout 5
SSH stricthostkeycheck
SSH timeout 5
SSH group dh-Group1-sha1 key exchange
Console timeout 0interface ID client DHCP-client to the outside
dhcpd outside auto_config
!
a basic threat threat detection
Statistics-list of access threat detection
no statistical threat detection tcp-interception
internal HSSvpn group strategy
attributes of Group Policy HSSvpn
value of server WINS 192.168.1.222
value of server DNS 192.168.1.222
Ikev1 VPN-tunnel-Protocol
Split-tunnel-policy tunnelall
Split-tunnel-network-list value Split-Tunnel-ACL
HSS.dk value by default-field
activate dns split-tunnel-all
type tunnel-group HSSvpn remote access
attributes global-tunnel-group HSSvpn
address IP-pool pool
HSS-auth-server authentication-server-group
Group Policy - by default-HSSvpn
password-management
IPSec-attributes tunnel-group HSSvpn
IKEv1 pre-shared-key *.
tunnel-group HSSvpn ppp-attributes
No chap authentication
no authentication ms-chap-v1
ms-chap-v2 authentication
!
class-map inspection_default
match default-inspection-traffic
!
!
type of policy-card inspect dns preset_dns_map
parameters
maximum message length automatic of customer
message-length maximum 512
Policy-map global_policy
class inspection_default
inspect the preset_dns_map dns
inspect the ftp
inspect h323 h225
inspect the h323 ras
inspect the rsh
inspect the rtsp
inspect esmtp
inspect sqlnet
inspect the skinny
inspect sunrpc
inspect xdmcp
inspect the sip
inspect the netbios
inspect the tftp
Review the ip options
!
global service-policy global_policy
context of prompt hostname
no remote anonymous reporting call
Cryptochecksum:c85ff8bf61669bef56b4dad704a4930a
: endHello
Change Split Tunnel VPN in full Tunnel VPN, you have really do much in your configuration.
Seems that have already changed you the 'tunnelspecified' 'tunnelall' in configurations of the 'group policy' . You can delete the setup but that defines the ACL of Split Tunnel
attributes of Group Policy HSSvpn
No split-tunnel-network-list value Split-Tunnel-ACLSeems that you use an internal AAA server to manage authentication rather than on the SAA. I guess if you want to assign a specific IP address for VPN user/username, then it must be done on the side Server?
If you had the "username" on the SAA configurations you can set it up under its framework which "username" IP address gets when he or she connects with the VPN Client.
As naturally as you start using the complete Tunnel and all traffic from the VPN Client starts to get in the tunnel to the ASA you will need a NAT for VPN Client users Internet traffic. You can configure this NAT like this for example:
network of the VPN-POOL object
192.168.30.0 subnet 255.255.255.0interface of VPN-POOL dynamic NAT (outside, outside) after auto source
Note that this is a manual of NAT / double NAT statement real "nat" IS NOT inserted under the 'object' , but the 'object' is rather created it can be used in the "nat" command. I see that your other dynamic PAT configurations are configured with NAT Auto / object NAT network. You can do this like that too if you wish. Personally I do like that.
But as I said before, it seems that you have already configured the VPN to be full of Tunnel. It is perhaps not as it is? While it is connected with VPN, you should be able to check the secure routes (or something like that) section to see if it says "0.0.0.0" If Yes, then it should be tunneling all traffic.
Hope this helps :)
-Jouni
Maybe you are looking for
-
Hello I must have changed a parameter, so that the 'Clear' and 'Junk' buttons above the mail pane disappeared, and a button 'Archive' appeared instead. It is true that for my mail via Gmail (IMAP), but when I opened an e-mail from my account (POP), I
-
Skype to Skype video calls from ipad
Please help. I used Skype Office for several years to make video calls. Purchased iPad. Skype Donloaded. Can connect, but cannot add contacts. I have a credit on my account. Where can I add contacts
-
If I download the new version this will compromise the documents filed, I have in the old version?
I need to download a more recent version of a document that I need to update. However, I have several important documents deposited in the old version. If I download the new version it will compromise these elders?
-
W500 TPM or Bitlocker question
Hello - I have a new W500 laptop. Win7 64 bit 8 GB RAM 300 GB HDD Processor 3.06 Ghz Dual Core When I restart or turn off the laptop is seems not stopped correctly. It does not restart. The only way I can get it lit again is to hold the button for 10
-
Cannot delete the program data files
I need to remove some log files for a program that I was running. The files are in the program data, but when I try to delete the logs I get the following message: File access denied You need permission to perform this action Your must be authorized