IPsec (ASA) on a stick
Hello
I have a requirement to terminate VPN site-to-site on ASA5545 unit such as IPsec on a stick and the road through the Internet router (2911) within the network and vice versa. For now, router Internet is with all the ACL and nat for the company. Sooner or later, all the ACL and nat must be migrated to the new ASA unit.
Anyone can share ideas on that?
Thank you
.
Hello
Yes... I agree with your proposed... design rather crossed and do all the workaround solution, this would be the right method that will make things much simpler...
Even if it would be better if you bring ASA between router and switch basis... I mean internet side by side (outside) interface of ASA will face to router and LAN (inside) interface will connect to the router base... then you can make site to site and anyconnect configured on the SAA itself and you can make the router just do routing to the internet... But based on your current production and the impact you can decide how you want to migrate...
Concerning
Knockaert
Tags: Cisco Security
Similar Questions
-
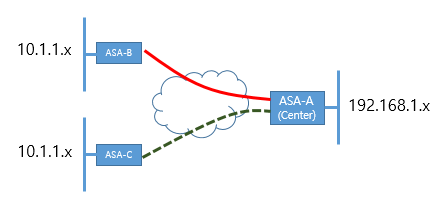
Currently, ASA - A (Center) and B has connected by VPN IPSec.
I would like a VPN establsh A ASA and ASA-C both.
But unfortunately, within the network range has same range B-ASA and ASA-C both. (10.1.1.x)
In this case, how can I connect IPSec VPN to ASA-B and C - ASA ASA - A at a time?
Thank you
Hello
You can go with policy subnet Nating ASA-C on another subnet on ASA - C (ex: 10.1.10.x) and use this as your ACL subnet subnet. It should work. Please search online for examples of configuration.
HTH
MS
-
Intercept-dhcp works to tunnel L2TP through IPsec ASA?
Hello
Is there anyone in the world operating a tunnel L2TP through IPsec on Cisco ASA for the native Windows clients and a Tunnel Split Configuration fully functional?
I created a tunnel L2TP through IPsec on the ASA 5520 9.1 (6) Version of the software running. My configuration is:
mask 172.23.32.1 - 172.23.33.255 255.255.252.0 IP local pool VPN_Users
ROUTING_SPLIT list standard access allowed 192.168.0.0 255.255.0.0
ROUTING_SPLIT list standard access allowed 172.16.0.0 255.248.0.0Crypto ipsec transform-set esp-aes-256 WIN10, esp-sha-hmac ikev1
transport mode encryption ipsec transform-set WIN10 ikev1
Crypto ipsec transform-set esp-3des esp-sha-hmac WIN7 ikev1
Crypto ipsec transform-set transport WIN7 using ikev1
Dynamic crypto map DYNMAP 10 set transform-set WIN10 WIN7 ikev1
Crypto dynamic-map DYNMAP 10 the value reverse-road
card crypto CMAP 99-isakmp dynamic ipsec DYNMAP
CMAP interface ipsec crypto mapCrypto isakmp nat-traversal 29
crypto ISAKMP disconnect - notify
Ikev1 enable ipsec crypto
IKEv1 crypto policy 10
preshared authentication
aes-256 encryption
sha hash
Group 2
life 86400
output
IKEv1 crypto policy 20
preshared authentication
3des encryption
sha hash
Group 2
life 86400
outputinternal EIK_USERS_RA group policy
EIK_USERS_RA group policy attributes
value of 12.34.56.7 DNS Server 12.34.56.8
VPN - connections 2
L2TP ipsec VPN-tunnel-Protocol ikev1
disable the password-storage
enable IP-comp
enable PFS
Split-tunnel-policy tunnelspecified
value of Split-tunnel-network-list ROUTING_SPLIT
ad.NYME.Hu value by default-field
Intercept-dhcp enable
the authentication of the user activation
the address value VPN_Users pools
outputattributes global-tunnel-group DefaultRAGroup
authentication-server-group challenger
accounting-server-group challenger
Group Policy - by default-EIK_USERS_RA
IPSec-attributes tunnel-group DefaultRAGroup
IKEv1 pre-shared-key *.
tunnel-group DefaultRAGroup ppp-attributes
No chap authentication
no authentication ms-chap-v1
ms-chap-v2 authentication
outputNow, the native Windows clients can connect using this group of tunnel:
our - asa # show remote vpn-sessiondb
Session type: IKEv1 IPsec
User name: w10vpn Index: 1
Assigned IP: 172.23.32.2 public IP address: 12.34.56.9
Protocol: IKEv1 IPsecOverNatT L2TPOverIPsecOverNatT
License: Another VPN
Encryption: IKEv1: (1) 3DES IPsecOverNatT: (1) L2TPOverIPsecOverNatT AES256: (1) no
Hash: IKEv1: (1) IPsecOverNatT SHA1: (1) L2TPOverIPsecOverNatT SHA1: (1) no
TX Bytes: 1233 bytes Rx: 10698
Group Policy: Group EIK_USERS_RA Tunnel: DefaultRAGroup
Connect time: 15:12:29 UTC Friday, April 8, 2016
Duration: 0: 00: 01:00
Inactivity: 0 h: 00 m: 00s
Result of the NAC: unknown
Map VLANS: VLAN n/a: noHowever, real communication takes place above the tunnel if I 'Gateway on remote network use default'. If I disable this option among the preferences of the IPv4 of the virtual interface of VPN in Control Panel as described in the section 'Configuration of Tunnel of Split' of This DOCUMENT then Windows sends all packets through the channel, because it fails to extract from the ASA routing table. Split routing works perfectly when using legacy Cisco VPN Client with the same group policy, but does not work with L2TP over IPsec.
As far as I can see, the 'intercept-dhcp' option is inefficient somehow. I even managed to intercept packets of the PPP virtual machine Windows XP interface, and I saw that windows sends its DHCP INFORM requests, but the ASA does not. My question is why?
-J' made a mistake in the above configuration?
-Can there be one option somewhere else in my config running that defuses intercept-dhcp?
- Or is there a software bug in my version of firmware ASA? (BTW, I tried with several versions of different software without success?
Hi, I have the same problem you have, but I was lucky enough to be able to install version 9.2 (4) on which this feature works very well. I'm suspecting that it is a bug, but I need to dig a little deeper. If I find something interesting I'll share it here.
-
Problems with ACL in config IPSec ASA-5504
I'm putting a tunnel IPSec between two ASA - 5540 s. There is a PC (SunMed_PC) behind the ASA-5540-B and a laptop (laptop-GHC) behind the ASA-5540-A. If the card encryption allows all IP, through the outside_cryptomap ACL, then the tunnel rises a FTP session is established.
But, when I restrict the following FTP, error message traffic is generated:
... Group = 164.72.1.147, IP = 164.72.1.147, IPSec tunnel rejecting: no entry for crypto for proxy card proxy remote 164.72.1.155/255.255.255.255/6/0 local 164.72.1.135/255.255.255.255/6/21 on the interface to the outside
Here's the configs giving only the relevant controls. I added the ACL 100 and "access-group 100 in the interface inside", but the error has not changed.
No idea what I'm missing?
CRO-ASA5540-A
names of
164.72.1.135 GHC_Laptop description name to test the VPN
164.72.1.155 SunMed_pc description name to test the VPN
!
interface GigabitEthernet0/0
nameif inside
security-level 100
IP 164.72.1.129 255.255.255.240
!
!
interface GigabitEthernet0/3
nameif outside
security-level 0
IP 164.72.1.145 255.255.255.248
!
passive FTP mode
DM_INLINE_TCP_1 tcp service object-group
port-object eq ftp
port-object eq ftp - data
access-list extended permits outside_cryptomap tcp ftp eq host GHC_Laptop host SunMed_pc object-group DM_INLINE_TCP_1
access-list 100 scope ip allow a whole
ASDM image disk0: / asdm - 603.bin
Access-group 100 in the interface inside
Crypto ipsec transform-set esp-SHA-ESP-3DES-3des esp-sha-hmac
card crypto outside_map0 1 match address outside_cryptomap
outside_map0 card crypto 1jeu peer 164.72.1.147
outside_map0 card crypto 1jeu transform-set ESP-3DES-SHA
outside_map0 card crypto 1jeu nat-t-disable
outside_map0 interface card crypto outside
crypto ISAKMP allow outside
crypto ISAKMP policy 5
preshared authentication
3des encryption
sha hash
Group 2
life 86400
Group Policy Lan-2-Lan_only internal
attributes of Lan-2-Lan_only-group policy
VPN-filter no
Protocol-tunnel-VPN IPSec
tunnel-group 164.72.1.147 type ipsec-l2l
tunnel-group 164.72.1.147 General-attributes
Group Policy - by default-Lan-2-Lan_only
IPSec-attributes tunnel-group 164.72.1.147
pre-shared-key *.
!
: end
----------------------------------------------------------------------------------------------------------
ROC-ASA5540-B # sh run
ASA Version 8.0 (3)
!
names of
name 164.72.1.135 GHC_laptop
name 164.72.1.155 SunMed_PC
!
interface GigabitEthernet0/0
nameif inside
security-level 100
IP 164.72.1.153 255.255.255.248
!
interface GigabitEthernet0/3
nameif outside
security-level 0
IP 164.72.1.147 255.255.255.248
!
passive FTP mode
DM_INLINE_TCP_1 tcp service object-group
port-object eq ftp
port-object eq ftp - data
outside_cryptomap list extended access permit tcp host host SunMed_PC GHC_laptop object-group DM_INLINE_TCP_1
access-list 100 scope ip allow a whole
ASDM image disk0: / asdm - 603.bin
Access-group 100 in the interface inside
Route outside 164.72.1.128 255.255.255.240 GHC-Medical 1
Crypto ipsec transform-set esp-SHA-ESP-3DES-3des esp-sha-hmac
card crypto outside_map0 1 match address outside_cryptomap
outside_map0 card crypto peer GHC-Medical 1jeu
outside_map0 card crypto 1jeu transform-set ESP-3DES-SHA
outside_map0 card crypto 1jeu nat-t-disable
outside_map0 interface card crypto outside
crypto ISAKMP allow outside
crypto ISAKMP policy 4
preshared authentication
3des encryption
sha hash
Group 2
life 86400
internal Lan-2-Lan group strategy
Lan Lan 2-strategy of group attributes
Protocol-tunnel-VPN IPSec
tunnel-group 164.72.1.145 type ipsec-l2l
tunnel-group 164.72.1.145 General-attributes
strategy-group-by default 2 Lan Lan
IPSec-attributes tunnel-group 164.72.1.145
pre-shared-key *.
: end
Your acl mapped on the card encryption is suspect on the first device:
access-list extended permits outside_cryptomap tcp ftp eq host GHC_Laptop host SunMed_pc object-group DM_INLINE_TCP_1
The source port should not be defined because it
is dynamic.
The second acl appears corrected:
outside_cryptomap list extended access permit tcp host host SunMed_PC GHC_laptop object-group DM_INLINE_TCP_1
-
Here's the scenario...
I have a client site with a network of VPN Cisco ASA 5505 with one IPSec tunnel to a VPN HQ.
I would like to introduce a 2nd tunnel from the customer site to another location of HQ who announces the same set of routes.
An ASA VPN point of view, what is the best way to do it?
Charge or a balancing approach active / standby will be acceptable.
IM curious to know how 2 static VPN tunnels will work side by side with the same cryptographic cards? It will even work?
I can it influence the use of good old routing mode?
Help! : P
Thank you!
D
Yes, that's where the second pair must be added.
-
Hello
During the configuration of ipsec between ASA and SRI 1811 tunnel, I have a few
negative questions:
PC host (192.168.56.1) <----->(in 192.168.56.56) ASA (excluding x.x.x.56)
<------->(off x.x.x.55) SRI (lo 192.168.55.55)
When I ping from SRI to ASA everyting is ok:
Source ip 192.168.56.1 SRI # ping 192.168.55.55
Type to abort escape sequence.
Send 5, echoes ICMP 100 bytes to 192.168.56.1, time-out is 2 seconds:
Packet sent with a source address of 192.168.55.55
.!!!!
ASA # sh isa his
ITS enabled: 1
Generate a new key SA: 0 (a tunnel report Active 1 and 1 to generate a new key during the generate a new key)
Total SA IKE: 1
1 peer IKE: x.x.x.55
Type: L2L role: answering machine
Generate a new key: no State: MM_ACTIVE
But in the vice versa ipsec tunnel is not established:
ASA # erase isa his
PC host # ping-c 2 192.168.55.55
PING 192.168.55.55 (192.168.55.55) 56 (84) bytes of data.
-192.168.55.55 - ping statistics
2 packets transmitted, 0 received, 100% packet loss, time 1010ms
and on the SAA, I saw track debugging messages:
Jun 02 03:18:07 [IKEv1]: unable to find political initiator IKE: Intf inside.
CBC: 192.168.56.1, Dst: 192.168.55.55
Jun 02 03:18:16 [IKEv1 DEBUG]: pitcher: received a message key acquisition, spi
0 x 0
Jun 02 03:18:16 [IKEv1]: unable to find political initiator IKE: Intf inside.
CBC: 192.168.56.1, Dst: 192.168.55.55
Jun 02 03:18:17 [IKEv1 DEBUG]: pitcher: received a message key acquisition, spi
0 x 0
Can someone help me with this problem?
Thank you.
Hello, I just noticed you are using a dynamic map, may I ask the reason for this?
I don't think you can be the "initiator" of a VPN session when using dynamic crypto maps, if you put the address of the remote peer, what benefit you earn using the dynamic encryption card?
Concerning
Farrukh
-
VPN IPSec ASA with two ISP active
Hi ALL!
I have a question.
So I have ASA with 9.2 (1) SW connected to ISP with active SLA.
I need to configure redundant IPSec VPN via ISP2, while all other traffic must go through isps1. In case if one of the ISP goes down all including VPN traffic must be routed via ISP alive.
I have configured SLA and it works.
ciscoasa # display route performance
Route 0.0.0.0 isps1 0.0.0.0 10.175.2.5 5 track 1
Route isp2 0.0.0.0 0.0.0.0 10.175.3.5 10 track 2
Route isp2 172.22.10.5 255.255.255.255 10.175.3.5 1 excerpt 2Here we can see if isps1 and ISP2 are RISING, all traffic passes through isps1, but traffic intended for the remote peer IPSec 172.22.10.5 passes by ISP2.
This configuration works just at the moment when isps1 or isp2 is down or if a static route for 172.22.10.5 deleted. Where two Internet service providers are increasing to ASA does not send the next remote IPSec datagrams.
ciscoasa # display running nat
NAT (inside, isp2) source static obj-INSIDE_LAN obj-INSIDE_LAN destination static obj-REMOTE_LAN obj-REMOTE_LAN no-proxy-arp-search to itinerary
NAT (inside isps1) source static obj-INSIDE_LAN obj-INSIDE_LAN destination static obj-REMOTE_LAN obj-REMOTE_LAN no-proxy-arp-search to itineraryCrypto ipsec transform-set ikev1 ESP-AES-256-SHA esp-aes-256 esp-sha-hmac
Crypto ipsec pmtu aging infinite - the security association
card crypto cm_vpnc 10 correspondence address acl_vpn
card crypto cm_vpnc 10 set pfs
peer set card crypto cm_vpnc 10 172.22.10.5
card crypto cm_vpnc 10 set transform-set ESP-AES-256-SHA ikev1
86400 seconds, duration of life card crypto cm_vpnc 10 set - the security association
card crypto cm_vpnc interface isps1
cm_vpnc interface isp2 crypto card
trustpool crypto ca policy
isps1 enable ikev1 crypto
isp2 enable ikev1 crypto
IKEv1 crypto policy 1
preshared authentication
aes-256 encryption
sha hash
Group 2
life 86400ciscoasa # show ip
System of IP addresses:
Subnet mask IP address name interface method
Vlan1 in 192.168.2.1 255.255.255.0 CONFIG
Isps1 Vlan2 10.175.2.10 255.255.255.0 CONFIG
Isp2 Vlan3 10.175.3.10 255.255.255.0 CONFIGThe main question why?
Thank you in advance,
Anton
Hi anton,.
If you check the log message on your ASA R301-IS , he's trying to build the tunnel VPN with both IP and it receives packets of asymmetrically your distance ciscoasa.
TO avoid this asymmetrical connection, point your IP from peers as primary & secondary on your R301-EAST
set peer 10.175.3.10 10.175.2.10
Delete the track on your routing entries
Route isp2 172.22.10.5 255.255.255.255 10.175.3.5
This should work for you.
Similalry lower your ISP 2, you should see VPN tunnel is mounted with isps1 one.
HTH
Sandy
-
How to configure bandwidth allowed on the VPN IPSec ASA tunnels?
ASA 5505 8.2.1
ASA 5520 8.4
We currently have a tunnel set up between 2 ASAs
is 1 - possible to assign 1.5 Mbps of Bandwidth (BW) to this tunnel? Then if Tunnel number 2 is set up I could assign 2 Mbit to this one for example?
I'm not talking to prioritize certain type of traffic on the IPsec tunnel, I'm talking about Tunnel 1 to 1.5 Mbps of BW guaranteed for all traffic that passes through it. Same for tunnel 2
Then
2-How do to control the quantity of biological weapons in an IPsec tunnel?
Please provide documentation possible
Thank you
Johnny
Hello! Please consult this document:
https://supportforums.Cisco.com/docs/doc-1230
___
HTH. Please rate this post if this has been helpful. If it solves your problem, please mark this message as "right answer".
-
VPN IPSEC ASA with counterpart with dynamic IP and certificates
Hello!
Someone please give me config the work of the ASA for ASA Site to Site IPSEC VPN with counterpart with dynamic IP and authentication certificates.
He works with PSK authentication. But the connection landed at DefaultRAGroup instead of DefaultL2LGroup with certificate
authentication.
Should what special config I ask a DefaultRAGroup to activate the connection?
Thank you!
The ASA uses parts of the client cert DN to perform a tunnel-group lookup to place the user in a group. When "peer-id-validate req" is defined the ASA also tries to compare the IKE ID (cert DN) with the actual cert DN (also received in IKE negotiation), if the comparison fails the connection fails. know you could set "peer-id-validate cert" for the time being and the ASA will try to compare the values but allow the connection if it cannot.
In general I would suggest using option "cert."
With nocheck, we are simply not strict on IKE ID matchin the certificate, which is normally not a problem of security :-)
-
GRE over IPsec, ASA and NAT - t.
I want to establish WILL IPsec tunnel between four branches and headquarters. In executive offices, I have router 1841 with the advanced security software. At Headquarters, I have a 7.2 ASA5510 as frontend with a IP address public and 1841 router behind him in the private address space. Given that the ASA does not support GRE tunnels, ASA may be endpoint for GRE over IPsec? If this isn't the case, ASA may pass through this tunnel to the router 1841 behind her, 1841 would be endpoint logic tunnel? What should I watch out for? The ASA and each 1841 support NAT - T, or just ASA?
The ASA does not support GRE.
The router would be the GRE tunnel endpoint. The ASA would be endpoint for IPSEC VPN. NAT - T should not be a matter of concern if the ASA and the remote routers directly connected to the internet.
HTH.
-
Hello
I tried to set up the on ASA 5505-L2TP connection.
The phase 1 and Phase 2 are completed but Windows Client does not work.
This is the configuration:
Crypto ipsec transform-set L2TP-TS-SHA esp-3des esp-sha-hmac
Crypto ipsec transform-set transit mode L2TP-TS-SHADynamic crypto map VPNCLIENT 65535 value transform-set L2TP-TS-SHA
internal DefaultRAGroup group strategy
attributes of Group Policy DefaultRAGroup
value of server DNS 192.168.1.2 192.168.1.14
Protocol-tunnel-VPN IPSec l2tp ipsec
the address value VPNClient-pool poolsattributes global-tunnel-group DefaultRAGroup
address VPNClient-pool pool
Group Policy - by default-DefaultRAGroup
password-management
IPSec-attributes tunnel-group DefaultRAGroup
pre-shared-key *.
tunnel-group DefaultRAGroup ppp-attributes
ms-chap-v2 authenticationJournal:
dec 13 17:48:08 [IKEv1]: Group = DefaultRAGroup, IP = 195.234.233.126, PHASE 2 COMPLETED (msgid = 00000002)
dec 13 17:48:08 [IKEv1]: rules of classification IKEQM_Active() Add L2TP: ip <195.234.233.126>mask <0xFFFFFFFF>port<15334>
dec 13 17:48:11 [IKEv1 DECODER]: IP = 195.234.233.126, IKE Responder starting QM: id msg = 00000003
dec 13 17:48:11 [IKEv1]: IP = 195.234.233.126, IKE_DECODE RECEIPT Message (msgid = 3) with payloads: HDR HASH (8) HIS (1) + (10) NUNCIO + ID (5) + ID (5) ++ NAT - OA (131) + NONE (0) overall length: 312
dec 13 17:48:11 [IKEv1 DEBUG]: Group = DefaultRAGroup, IP = 195.234.233.126, processing hash payload
dec 13 17:48:11 [IKEv1 DEBUG]: Group = DefaultRAGroup, IP = 195.234.233.126, SA payload processing
dec 13 17:48:11 [IKEv1 DEBUG]: Group = DefaultRAGroup, IP = 195.234.233.126, nonce payload processing
dec 13 17:48:11 [IKEv1 DEBUG]: Group = DefaultRAGroup, IP = 195.234.233.126, payload processing ID
dec 13 17:48:11 [IKEv1 DECODER]: Group = DefaultRAGroup, IP = 195.234.233.126, ID_IPV4_ADDR received ID
192.168.236.25
dec 13 17:48:11 [IKEv1]: Group = DefaultRAGroup, IP = 195.234.233.126, data received in payload ID remote Proxy Host: address 195.234.233.126, Protocol 17, Port 0
dec 13 17:48:11 [IKEv1 DEBUG]: Group = DefaultRAGroup, IP = 195.234.233.126, payload processing ID
dec 13 17:48:11 [IKEv1 DECODER]: Group = DefaultRAGroup, IP = 195.234.233.126, ID_IPV4_ADDR received ID
94.88.180.84
dec 13 17:48:11 [IKEv1]: Group = DefaultRAGroup, IP = 195.234.233.126, data received in payload ID local Proxy Host: address 172.16.34.1, Protocol 17 Port 1701
dec 13 17:48:11 [IKEv1]: Group = DefaultRAGroup, IP = 195.234.233.126, detected L2TP/IPSec session.
dec 13 17:48:11 [IKEv1 DEBUG]: Group = DefaultRAGroup, IP = 195.234.233.126, payload NAT Original address of treatment
dec 13 17:48:11 [IKEv1]: Group = DefaultRAGroup, IP = 195.234.233.126, QM IsRekeyed its already be regenerated
dec 13 17:48:11 [IKEv1]: Group = DefaultRAGroup, IP = 195.234.233.126, error QM WSF (P2 struct & 0xd7f0b8d0, mess id 0x3)!
dec 13 17:48:11 [IKEv1 DEBUG]: Group = DefaultRAGroup, IP = 195.234.233.126, case of mistaken IKE responder QM WSF (struct & 0xd7f0b8d0), : QM_DONE EV_ERROR--> QM_BLD_MSG2 EV_IS_REKEY--> QM_BLD_MSG2, EV_CONFIRM_SA--> QM_BLD_MSG2, EV_PROC_MSG--> QM_BLD_MSG2, EV_HASH_OK--> QM_BLD_MSG2, NullEvent--> QM_BLD_MSG2, EV_COMP_HASH--> QM_BLD_MSG2, EV_VALIDATE_MSG
dec 13 17:48:11 [IKEv1 DEBUG]: Group = DefaultRAGroup, IP = 195.234.233.126, sending clear/delete with the message of reason
dec 13 17:48:11 [IKEv1]: Group = DefaultRAGroup, IP = 195.234.233.126, peer table correlator Removing failed, no match!
dec 13 17:48:12 [IKEv1 DECODER]: IP = 195.234.233.126, IKE Responder starting QM: id msg = 00000003
dec 13 17:48:12 [IKEv1]: IP = 195.234.233.126, IKE_DECODE RECEIPT Message (msgid = 3) with payloads: HDR HASH (8) HIS (1) + (10) NUNCIO + ID (5) + ID (5) ++ NAT - OA (131) + NONE (0) overall length: 312
dec 13 17:48:12 [IKEv1 DEBUG]: Group = DefaultRAGroup, IP = 195.234.233.126, processing hash payload
dec 13 17:48:12 [IKEv1 DEBUG]: Group = DefaultRAGroup, IP = 195.234.233.126, SA payload processing
dec 13 17:48:12 [IKEv1 DEBUG]: Group = DefaultRAGroup, IP = 195.234.233.126, nonce payload processing
dec 13 17:48:12 [IKEv1 DEBUG]: Group = DefaultRAGroup, IP = 195.234.233.126, payload processing ID
dec 13 17:48:12 [IKEv1 DECODER]: Group = DefaultRAGroup, IP = 195.234.233.126, ID_IPV4_ADDR received ID
192.168.236.25
dec 13 17:48:12 [IKEv1]: Group = DefaultRAGroup, IP = 195.234.233.126, data received in payload ID remote Proxy Host: address 195.234.233.126, Protocol 17, Port 0
dec 13 17:48:12 [IKEv1 DEBUG]: Group = DefaultRAGroup, IP = 195.234.233.126, payload processing ID
dec 13 17:48:12 [IKEv1 DECODER]: Group = DefaultRAGroup, IP = 195.234.233.126, ID_IPV4_ADDR received ID
94.88.180.84
dec 13 17:48:12 [IKEv1]: Group = DefaultRAGroup, IP = 195.234.233.126, data received in payload ID local Proxy Host: address 172.16.34.1, Protocol 17 Port 1701
dec 13 17:48:12 [IKEv1]: Group = DefaultRAGroup, IP = 195.234.233.126, detected L2TP/IPSec session.
dec 13 17:48:12 [IKEv1 DEBUG]: Group = DefaultRAGroup, IP = 195.234.233.126, payload NAT Original address of treatment
dec 13 17:48:12 [IKEv1]: Group = DefaultRAGroup, IP = 195.234.233.126, QM IsRekeyed its already be regenerated
dec 13 17:48:12 [IKEv1]: Group = DefaultRAGroup, IP = 195.234.233.126, error QM WSF (P2 struct & 0xd8b55468, mess id 0x3)!
dec 13 17:48:12 [IKEv1 DEBUG]: Group = DefaultRAGroup, IP = 195.234.233.126, case of mistaken IKE responder QM WSF (struct & 0xd8b55468), : QM_DONE EV_ERROR--> QM_BLD_MSG2 EV_IS_REKEY--> QM_BLD_MSG2, EV_CONFIRM_SA--> QM_BLD_MSG2, EV_PROC_MSG--> QM_BLD_MSG2, EV_HASH_OK--> QM_BLD_MSG2, NullEvent--> QM_BLD_MSG2, EV_COMP_HASH--> QM_BLD_MSG2, EV_VALIDATE_MSG
dec 13 17:48:12 [IKEv1 DEBUG]: Group = DefaultRAGroup, IP = 195.234.233.126, sending clear/delete with the message of reason
dec 13 17:48:12 [IKEv1]: Group = DefaultRAGroup, IP = 195.234.233.126, peer table correlator Removing failed, no match!Can someone help me pls?
Is behind a NAT device ASA? Also what version of the ASA are you running?
Also, make sure that the settings on the client are right according to this doc:
http://www.Cisco.com/en/us/products/ps6120/products_configuration_example09186a00807213a7.shtml
-
VPN IPSEC ASA with overlap proxy-ID
All,
Currently I have a VPN from a single network ASA spoke to a single hub of AAS, so I set up my access lists so that the source is specific to speak it (for example 192.168.1.0/24) and I use the word "any" key for destination. I need to add a few more VPN connections, so can I just add lower inside specific networks to any instruction in the card encryption. See below.
outside_10_cryptomap list extended access allowed object-group home-networks-networks another ip
outside_20_cryptomap list of allowed ip extended access object-group network inside everything
card crypto outside_map 10 correspondence address outside_10_cryptomap
card crypto outside_map 10 set peer 1.1.1.1
outside_map card crypto 10 the transform-set ESP-3DES-MD5 value
card crypto outside_map 20 match address outside_20_cryptomap
card crypto outside_map 20 peers set 2.2.2.2
outside_map card crypto 20 the transform-set ESP-3DES-MD5 value
Gregory
Now I come to think of it, I remember a problem with less specific entries in the ACL before more specific entries.
So it should work, but you must make sure that the most specific comes before the less specific that you seem to have done with your config.
Jon
-
How to control the activity of the client-to-site (IPSEC ASA)
I have a client to site VPN configuration on my 5505 according to directives of the Chapter35 of the ASA8.x configuration guide.
One thing I am not sure about is how can I control what VPN users can connect to? I see nothing in the config that binds inside the interface so that prevents them to connect to the DMZ as well? How to limit connectivity so they can only connect to a host on the inside? or a host on the inside and the other on the DMZ?
Thank you
According to me, is what you're looking for.
It will be useful.
-
L2l between an ASA 5505 and WatchGuard XTM330 with dynamic IP
Hi guys,.
I looked for a solution on this one but can't find inappropriate, most of the discussions were old and with dead links to the solution.
We have an ASA 5505 with static IP address on the outside and a customer who have a WatchGuard XTM330 with dynamic IP address to the outside.
Is it possible to have an L2L VPN between our ASA and the WatchGuard when he has a dynamic IP?
I have no experience on the series of WatchGuard,
so, I am very grateful for any answer!
Thanks in advance and have a nice day
BR
Robin
Hi Robin,
Here are the links you can make reference when configuring static to the dynamic VPN tunnel: -.
http://www.Cisco.com/c/en/us/support/docs/security/ASA-5500-x-series-next-generation-firewalls/112075-dynamic-IPSec-ASA-router-CCP.htmlThis one is with Pix on the remote side, but the configuration will remain the same on the local side: -.
http://www.WatchGuard.com/docs/4-6-Firebox-CiscoPix.PDFKind regards
Dinesh MoudgilPS Please rate helpful messages.
-
To confirm the network is GRE over IPSEC
Hello world
We have Cisco 4500 device GRE tunnel and next hop is that ASA makes the IPSEC VPN over WAN.
If this type of network is called free WILL on the right of IPSEC?
Also when I do on 4500 sh int tu0
reliability 255/255, txload 79/255, rxload 121/255
5 minute input rate 2228000 bps, 790 packets/s
5 minute output rate 780000 bps, 351 packets/s
Need to understand which shows that data transmitted by tunnel LIKING which is not encrypted right?
To verify ipsec ASA which is encrypted data that we do sh right its isakmp crypto?
When we apply crypto map on the physical interface ASA here?
Thank you
Mahesh
If your GRE tunnel protection applied to this topic, so I think that the transmitted data is encrypted. GRE over ipsec simply means the application of the protection of tunnel to tunnel will otherwise it's just a simple GRE tunnel.
Side that Show crypto isakmp his, you can also check if the traffic from one site to another is using GRE or not by issuing crypto ipsec to show its, it will tell you the number of Protocol and it should say 47. And if you use the protection tunnel command to set the ipsec tunnel, you will not need to define cryptographic cards more.
Maybe you are looking for
-
Virus and Malware eradicating for iPhone 6 s
I suspect that my iPhone 6 can be infected by viruses, spyware or malware. Please can someone advise what I need to do to confirm if this is the case, and what can I do to eradicate them from my iPhone?
-
A month ago (or more), I wanted to update my client Skype to the latest version. The downloaded installation program, seems to start installing and then stopped with the message:"We have problems connecting to download server. ." To download an alter
-
I bought this software for my laptop and did not notice that she was to be used on SP2. I have only the SP1 of Vista, what kind of questions will come I face.
-
I have a card PCI WMP600N I was able to connect to my Belkin router which I use as the router instead of my Virginmedia Superhub, which was ran in Modem mode. When I went to the computer this morning I couldn't connect to the internet even if the net
-
How do I know when the garbage collector/timer icon is active
Hello I want to listen to changes on the phone screen, I saw peter made a suggestion in another thread a couple of years ago which resulted in using locateDfference, however, it signals a potential hole in his suggestion where, in the case where the