L2TP over ipsec ASA
Hello
I tried to set up the on ASA 5505-L2TP connection.
The phase 1 and Phase 2 are completed but Windows Client does not work.
This is the configuration:
Crypto ipsec transform-set L2TP-TS-SHA esp-3des esp-sha-hmac
Crypto ipsec transform-set transit mode L2TP-TS-SHA
Dynamic crypto map VPNCLIENT 65535 value transform-set L2TP-TS-SHA
internal DefaultRAGroup group strategy
attributes of Group Policy DefaultRAGroup
value of server DNS 192.168.1.2 192.168.1.14
Protocol-tunnel-VPN IPSec l2tp ipsec
the address value VPNClient-pool pools
attributes global-tunnel-group DefaultRAGroup
address VPNClient-pool pool
Group Policy - by default-DefaultRAGroup
password-management
IPSec-attributes tunnel-group DefaultRAGroup
pre-shared-key *.
tunnel-group DefaultRAGroup ppp-attributes
ms-chap-v2 authentication
Journal:
dec 13 17:48:08 [IKEv1]: Group = DefaultRAGroup, IP = 195.234.233.126, PHASE 2 COMPLETED (msgid = 00000002)
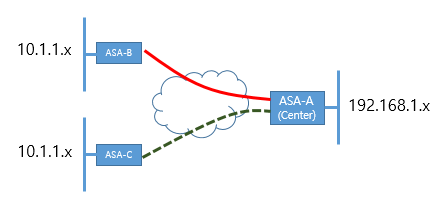
Can someone help me pls? Is behind a NAT device ASA? Also what version of the ASA are you running? Also, make sure that the settings on the client are right according to this doc: http://www.Cisco.com/en/us/products/ps6120/products_configuration_example09186a00807213a7.shtml Tags: Cisco Security Intercept-dhcp works to tunnel L2TP through IPsec ASA? Hello Is there anyone in the world operating a tunnel L2TP through IPsec on Cisco ASA for the native Windows clients and a Tunnel Split Configuration fully functional? I created a tunnel L2TP through IPsec on the ASA 5520 9.1 (6) Version of the software running. My configuration is: mask 172.23.32.1 - 172.23.33.255 255.255.252.0 IP local pool VPN_Users ROUTING_SPLIT list standard access allowed 192.168.0.0 255.255.0.0 Crypto ipsec transform-set esp-aes-256 WIN10, esp-sha-hmac ikev1 Crypto isakmp nat-traversal 29 internal EIK_USERS_RA group policy attributes global-tunnel-group DefaultRAGroup Now, the native Windows clients can connect using this group of tunnel: our - asa # show remote vpn-sessiondb Session type: IKEv1 IPsec User name: w10vpn Index: 1 However, real communication takes place above the tunnel if I 'Gateway on remote network use default'. If I disable this option among the preferences of the IPv4 of the virtual interface of VPN in Control Panel as described in the section 'Configuration of Tunnel of Split' of This DOCUMENT then Windows sends all packets through the channel, because it fails to extract from the ASA routing table. Split routing works perfectly when using legacy Cisco VPN Client with the same group policy, but does not work with L2TP over IPsec. As far as I can see, the 'intercept-dhcp' option is inefficient somehow. I even managed to intercept packets of the PPP virtual machine Windows XP interface, and I saw that windows sends its DHCP INFORM requests, but the ASA does not. My question is why? -J' made a mistake in the above configuration? -Can there be one option somewhere else in my config running that defuses intercept-dhcp? - Or is there a software bug in my version of firmware ASA? (BTW, I tried with several versions of different software without success? Hi, I have the same problem you have, but I was lucky enough to be able to install version 9.2 (4) on which this feature works very well. I'm suspecting that it is a bug, but I need to dig a little deeper. If I find something interesting I'll share it here. Microsoft L2TP over IPSEC client with AES encryption I configured L2TP over IPSec Cisco VPN router with Hastings 3des encryption is sha1 with diffie hellman Group 2 and I can't connect with success of Microsoft customers. but my question is why can I not connect when I am increasing the encryption with AES 256 and sha256 DH group 14, his looks that windows does not support advanced encryption. is it possiple to activate encryption aes with the highest level...? and how?. Hello To ensure that you get the best response to your concerns, we suggest that publish this request via the Web to Microsoft Developer network site. To do this, visit this link. Best regards. Problem of authenticating users on L2TP over IPSec tunnel I have a client with an old PIX-515e firewall with firmware 7.2 (4), and due to certain circumstances, I'm trying to configure L2TP over IPSec. I'm stuck at a "Error 691: the remote connection has been deinied because the user name and password combination, you have provided is not recognized, or the selected authentication protocol is not permitted on the remote access server." I have local installation of authentication for this connection, and I tried to use ms-chap-v2, chap and pap, and give the same results. I have confirmed the username and the password, but I can't after that. The PIX, I don't see "AAA user authenticaton rejected: reason = invalid password: local database: user = tetstuser". I can still see the password unencrypted on the screen, so I can copy and paste the username and password in the appropriate fields, and I still have this error. Does anyone have an idea where the problem lies perhaps? Thank you. Can you please change the user as described in the doc, I shared and as indicated by the Rohan peers and share the results of the tests? Kind regards Dinesh Moudgil PS Please rate helpful messages. L2TP over IPSEC VPN is supported in Cisco SRP 521w? I now try to configure a Cisco Small Business Pro SRP 521w for a branch office router, I try to get the router to connect to a VPN L2TP server inside my data center, but it seems to me that the client VPN L2TP function is not supported within the SRP 521w router. Can Cisco implementing in the future in the firmware for the router in SRP 521w client VPN L2TP? Hello This is correct, without L2TP over IPSec tunnels. (L2TP only supported on the primary Ethernet WAN interfaces). Kind regards Andy GRE over IPsec, ASA and NAT - t. I want to establish WILL IPsec tunnel between four branches and headquarters. In executive offices, I have router 1841 with the advanced security software. At Headquarters, I have a 7.2 ASA5510 as frontend with a IP address public and 1841 router behind him in the private address space. Given that the ASA does not support GRE tunnels, ASA may be endpoint for GRE over IPsec? If this isn't the case, ASA may pass through this tunnel to the router 1841 behind her, 1841 would be endpoint logic tunnel? What should I watch out for? The ASA and each 1841 support NAT - T, or just ASA? The ASA does not support GRE. The router would be the GRE tunnel endpoint. The ASA would be endpoint for IPSEC VPN. NAT - T should not be a matter of concern if the ASA and the remote routers directly connected to the internet. HTH. DMVPN & GRE over IPsec on the same physical interface Dear all, I am setting up two routers WAN, each router wan has a physical interface connecting to the branches and regional office by using the same provider. We will use the GRE over IPsec to connect to Office regional and DMVPN + EIGRP to branches. I would like to know if it is possible to configure tunnels for GRE over IPsec and DMVPN + EIGRP using the same source physical interface. Good answer, it's an urgent request and your response is much appreciated. Kind regards Hi Savio, It should work. We can configure dmvpn and gre-over-ipsec on ASA using the same physical interface. Kind regards NGO To confirm the network is GRE over IPSEC Hello world We have Cisco 4500 device GRE tunnel and next hop is that ASA makes the IPSEC VPN over WAN. If this type of network is called free WILL on the right of IPSEC? Also when I do on 4500 sh int tu0 reliability 255/255, txload 79/255, rxload 121/255 5 minute input rate 2228000 bps, 790 packets/s 5 minute output rate 780000 bps, 351 packets/s Need to understand which shows that data transmitted by tunnel LIKING which is not encrypted right? To verify ipsec ASA which is encrypted data that we do sh right its isakmp crypto? When we apply crypto map on the physical interface ASA here? Thank you Mahesh If your GRE tunnel protection applied to this topic, so I think that the transmitted data is encrypted. GRE over ipsec simply means the application of the protection of tunnel to tunnel will otherwise it's just a simple GRE tunnel. Side that Show crypto isakmp his, you can also check if the traffic from one site to another is using GRE or not by issuing crypto ipsec to show its, it will tell you the number of Protocol and it should say 47. And if you use the protection tunnel command to set the ipsec tunnel, you will not need to define cryptographic cards more. Hi all I am setting up IPSEC tunnel GRE... I am able to get neighbors OSPF looked through the GRE tunnel, but when traffic is sent through the gre tunnel it does not encrypt and transmit through plaintext despite she buy from loopback interfaces Here is my config Config of R1 Crypto ipsec transform-set test aes - esp esp-sha-hmac test card crypto-address Ethernet0/0 GRE extended IP access list interface Ethernet0/0 interface Loopback0 Tunnel1 interface ----------------------------------------------------------- crypto ISAKMP policy 10 GR extended IP access list interface Ethernet0/0 interface Loopback0 Tunnel1 interface ------------------------------------------- Hello With p2p GRE over IPsec solution, all traffic between sites is encapsulated in a GRE p2p package before the process of encryption. More info on this link: http://www.Cisco.com/c/en/us/TD/docs/solutions/Enterprise/WAN_and_MAN/P2... Kind regards Aditya Please evaluate the useful messages and mark the correct answers. GRE over IPSec tunnel cannot pass traffic through it I am trying to configure a GRE over IPSec tunnel between sites, we use the router cisco 7613 SUP720 (IOS: s72033-advipservicesk9_wan - mz.122 - 18.SXF15a.bin) and 3845 router (IOS:c3845 - advsecurityk9 - mz.124 - 25c.bin), we are facing problems when we use the tunnel because traffic is not passing through it. the configuration was working when we were using two routers cisco 3845 (IOS:c3845 - advsecurityk9 - mz.124 - 25c.bin), but for some reason, it doesn't work anymore when I paste the configuration on the new 7613 router. Head office crypto ISAKMP policy 10 interface Serial0/1/0:0 access-list 100 permit gre 167.134.216.90 host 167.134.216.8 Router eigrp 100 Directorate-General of the crypto ISAKMP policy 10 Tunnel1 interface interface Serial1/0/0:1 access-list 100 permit gre 167.134.216.89 host 167.134.216.90 ER-7600 #sh crypto isakmp his ER-3845 #sh crypto isakmp his ER-3845 #sh active cryptographic engine connections Algorithm of address State IP Interface ID encrypt decrypt ER-7600 #sh active cryptographic engine connections Algorithm of address State IP Interface ID encrypt decrypt I had this error on the er-3845: % CRYPTO-4-RECVD_PKT_NOT_IPSEC: Rec'd package not an IPSEC packet and this one on the IPSEC (epa_des_crypt) UH-7600: decrypted packet has no control of his identity Please help, it's so frustrating... Thanks in advance Oscar Here is a document from cisco, mentioning clearly for a card encryption on the two physical as tunnel interface well. http://www.Cisco.com/en/us/Tech/tk583/TK372/technologies_configuration_example09186a008009438e.shtml It may be useful Manish Setting KeepAlive on GRE over IPSEC tunnel Hello world Need to know if there are benefits of the KeepAlive on GRE over IPSEC implementation that goes over the Wan. ? We currently have no KeepAlive on GRE tunnel. If we config KeepAlive on both ends of the ACCORD it will cause any overload or the CPU load? Thank you MAhesh If you use a routing on the GRE tunnel protocol you should use KeepAlive WILL not, but I would probably recommend use KeepAlive WILL anyway for the following reasons: 1. the overload caused by the GRE KeepAlive is quite small, it should not affect the ability to pass traffic 2. If you ever want to use tracking interface for roads or the static routes that you can interface WILL detect it descend as quickly as possible I know that your IPSec device is separate, so I'd probably also enable KeepAlive on the IPSec tunnel as well. VAC It's lab that I did today, and offcouse, I am able to understand this laboratory bus are confusion 1. Why do we use a card encryption on both interfaces (phiycal tunnel interface or interface) 2. when I remove the interface tunnel encryption card I have this message ( R2691 #* 01:12:54.243 Mar 1: ISAKMP: (1002): purge node 2144544879 ) Please tell me what is the meaning of this message 3. but I do not see vpn works great. It comes to cryto his and crypto isakmp his R2691 #sh crypto ipsec his Interface: Serial0/0 Crypto map tag: vpn, local addr 30.1.1.21 protégé of the vrf: (none) local ident (addr, mask, prot, port): (30.1.1.21/255.255.255.255/47/0) Remote ident (addr, mask, prot, port): (10.1.1.1/255.255.255.255/47/0) 10.1.1.1 current_peer port 500 LICENCE, flags is {origin_is_acl}, #pkts program: 65, #pkts encrypt: 65, #pkts digest: 65 #pkts decaps: 66, #pkts decrypt: 66, #pkts check: 66 compressed #pkts: 0, unzipped #pkts: 0 #pkts uncompressed: 0, #pkts compr. has failed: 0 #pkts not unpacked: 0, #pkts decompress failed: 0 Errors in #send 2, #recv 0 errors local crypto endpt. : 30.1.1.21, remote Start crypto. : 10.1.1.1 Path mtu 1500, mtu 1500 ip, ip mtu IDB Serial0/0 current outbound SPI: 0xDBF65B0E (3690355470) SAS of the esp on arrival: SPI: 0x44FF512B (1157583147) transform: esp-3des esp-md5-hmac. running parameters = {Tunnel} Conn ID: 5, flow_id: SW:5, crypto card: vpn calendar of his: service life remaining (k/s) key: (4598427/3368) Size IV: 8 bytes support for replay detection: Y Status: ACTIVE the arrival ah sas: SAS of the CFP on arrival: outgoing esp sas: SPI: 0xDBF65B0E (3690355470) transform: esp-3des esp-md5-hmac. running parameters = {Tunnel} Conn ID: 6, flow_id: SW:6, crypto card: vpn calendar of his: service life remaining (k/s) key: (4598427/3368) Size IV: 8 bytes support for replay detection: Y Status: ACTIVE outgoing ah sas: outgoing CFP sas: R2691 #sh crypto isakmp his IPv4 Crypto ISAKMP Security Association status of DST CBC State conn-id slot 30.1.1.21 10.1.1.1 QM_IDLE 1002 ASSETS 0 ISAKMP Crypto IPv6 security association. How can 2: I know it using GRE over IPsec. I also join my topology on which I made lab Also beyond what I remember, in the old codes he was required to have a card encryption on tunnel and physical interface, but now is not. Since we use GRE over IPSEC, so for the verification of the tunnel I'll do the following steps: (1.) to check if the tunnel interface is in place. "show ip int br". 2.) check if the statistics of tunnel are increasing and packages are browsing through it. 'show interface '. 3.) check if crypto ACL includes only interesting traffic listed as GRE counterparts. (4.) If Yes, check the IPSEC Security Association statistics. "See the crypto ipsec his." If all of them are correct statistical evidence with respective counters increase traffic is passing by GRE and then by wrapping in IPSEC. I hope this helps. Kind regards Anuj Microsoft L2TP VPN to ASA 5520 I am trying to configure an L2TP VPN connection on an XP laptop. On the SAA, I use the DefaultRAGroup and the DfltGrpPolicy. I put DefaultRAGroup to use a pre-shared key, and set the authentication of users on ACS_Radius. Our ACS server is associated with AD. Anyone know if I can use ACS to authenticate this user type or do I have to create local accounts on the SAA? When I try to connect from the laptop, I get error 789. On the ASA, I see this: Group = DefaultRAGroup, IP = 63.xxx.xxx.xxx, PHASE 1 COMPLETED Group = DefaultRAGroup, IP = 63.xxx.xxx.xxx, error QM WSF (P2 struct & 0xcddc7d28, mess id 0x46986b08). Group = DefaultRAGroup, IP = 63.xxx.xxx.xxx, peer of withdrawal of correlator table failed, no match! Group = DefaultRAGroup, username =, IP = 63.xxx.xxx.xxx, disconnected Session. Session type: IKE, duration: 0 h: 00 m: 00s, xmt bytes: 0, RRs bytes: 0, right: Phase 2 Mismatch On the one hand, it seems that the laptop is not sending the username and password. I've tried a lot of different combos on the side of microsoft MSCHAP and MSCHAPv2, both of them or all of them individually and matched this setting on the SAA. No matter what, I get the same error. Anyone have any ideas? Yes... I have never trusted guys for the configuration, I got the following errors: 1 L2TP requires a mode of transport must be of the type of IPSEC traffic used, your config seems to refer to the one, yet it is not defined: Crypto ipsec transform-set esp-3des esp-md5-hmac TRANS_ESP_3DES_SHA Crypto ipsec transform-set Transit mode TRANS_ESP_3DES_SHA<-(needed> 2. the present set of transformation is not attached to dynamic cryptography so not used: Crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 value transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA MD5-ESP-3DES ESP-DES-SHA ESP-DES-MD5 It should look like: Crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 value transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA MD5-ESP-3DES ESP-DES-SHA ESP-DES-MD5 TRANS_ESP_3DES_SHA Finally, it is just to clear up, make sure that your server ACS_Radius is indeed enabled for authentication MS-CHAPv2 of ASA and the l2tp client, otherwise it will fail always. Hello world I have a 8.4 ASA Recently, I have setup a "L2tp Vpn" connection, but I m facing a lot of question actually I m not able to connect any of windows client (windows 7 & 8) below is my setup and debugging I did Any help would be appreciated, thank you in advance MY SETUP L2TP 2 Configure ISAKMP policy IKEv1 crypto policy 65535 3 configure an address pool mask IP local pool L2TP_POOL-WHO 10.30.255.1 - 10.30.255.6 255.255.255.248 username privilege the mschap password l2tp SGC 0 4. define group policy 5 set the tunnel group attributes global-tunnel-group DefaultRAGroup IPSec-attributes tunnel-group DefaultRAGroup tunnel-group DefaultRAGroup ppp-attributes 6. ipsec settings 7. dynamic crypto map configuration 8. create a map entry and associated crypto dynamic with her map map mymap 65535-isakmp ipsec crypto dynamic dynmap 9. connect the crypto in interface map mymap outside crypto map interface 10 enable isakmp on interface crypto ISAKMP allow outside ****************** ***************************** FWASA-VICT1 (config) # 01 August at 20:35 [IKEv1] IP = 197.217.68.99, IKE_DECODE RECEIPT Message (msgid = 0) with payloads: HDR SA (1) the seller (13) of the SELLER (13) + seller (13) + seller (13) + seller (13) + seller (13) ++ SELLER (13) + (0) NONE total length: 384 Hi man, As you can see in the output: -. Phase 1 is done and QM WSF error indicates the issue with transform-set or crypto-access list. You could try as well as authentication using PAP. Kind regards PS Please rate helpful messages. Currently, ASA - A (Center) and B has connected by VPN IPSec. I would like a VPN establsh A ASA and ASA-C both. But unfortunately, within the network range has same range B-ASA and ASA-C both. (10.1.1.x) In this case, how can I connect IPSec VPN to ASA-B and C - ASA ASA - A at a time? Thank you Hello You can go with policy subnet Nating ASA-C on another subnet on ASA - C (ex: 10.1.10.x) and use this as your ACL subnet subnet. It should work. Please search online for examples of configuration. HTH MS Unwanted on the desktop folder A new folder is on my desk that contains copies of all other folders located on my desktop. If I didn't put on my desk, it is also copied to this new mystery folder. Do not just throw it in the trash and l see what happens. Anyone has any idea where Satellite Pro P200 - 1EE: Question about two partitions on the disk with Vista Hello I've had my laptop for 2 months now and when I click on computer to watch my hard drive there are two; 1 called vista (: c) and other data (: E).Why is it two hard disks?And called Vista one 21.5 GB free and the other has 71.2 GB free.So if we Missing pictures for backup and restore I had the apple store yesterday help me to back up my phone on iCloud. They replaced my phone (broken screen) and I asked the guy about 4 times if all my photos would be restored. I paid for extra iCloud there and for space so I could back up everyth IPhoto lost in translation 7 5 Lion os10 Tiger Received an old 17 Imac A1195 ¨from a friend. It was running under Tiger I've updated the memory of 2 Gig, re the disk formatted and installed os 10.7.5 Lion IPhoto has disappeared and no way to recover it as tiger is no longer recognizable. So I'm s I only had the default printers on Windows XP and my Canon MG6150 installed. All printers on the printers/faxes folder in Control Panel have dissappeared can anyone provide the answer so I can print again
dec 13 17:48:08 [IKEv1]: rules of classification IKEQM_Active() Add L2TP: ip <195.234.233.126>mask <0xFFFFFFFF>port<15334>
dec 13 17:48:11 [IKEv1 DECODER]: IP = 195.234.233.126, IKE Responder starting QM: id msg = 00000003
dec 13 17:48:11 [IKEv1]: IP = 195.234.233.126, IKE_DECODE RECEIPT Message (msgid = 3) with payloads: HDR HASH (8) HIS (1) + (10) NUNCIO + ID (5) + ID (5) ++ NAT - OA (131) + NONE (0) overall length: 312
dec 13 17:48:11 [IKEv1 DEBUG]: Group = DefaultRAGroup, IP = 195.234.233.126, processing hash payload
dec 13 17:48:11 [IKEv1 DEBUG]: Group = DefaultRAGroup, IP = 195.234.233.126, SA payload processing
dec 13 17:48:11 [IKEv1 DEBUG]: Group = DefaultRAGroup, IP = 195.234.233.126, nonce payload processing
dec 13 17:48:11 [IKEv1 DEBUG]: Group = DefaultRAGroup, IP = 195.234.233.126, payload processing ID
dec 13 17:48:11 [IKEv1 DECODER]: Group = DefaultRAGroup, IP = 195.234.233.126, ID_IPV4_ADDR received ID
192.168.236.25
dec 13 17:48:11 [IKEv1]: Group = DefaultRAGroup, IP = 195.234.233.126, data received in payload ID remote Proxy Host: address 195.234.233.126, Protocol 17, Port 0
dec 13 17:48:11 [IKEv1 DEBUG]: Group = DefaultRAGroup, IP = 195.234.233.126, payload processing ID
dec 13 17:48:11 [IKEv1 DECODER]: Group = DefaultRAGroup, IP = 195.234.233.126, ID_IPV4_ADDR received ID
94.88.180.84
dec 13 17:48:11 [IKEv1]: Group = DefaultRAGroup, IP = 195.234.233.126, data received in payload ID local Proxy Host: address 172.16.34.1, Protocol 17 Port 1701
dec 13 17:48:11 [IKEv1]: Group = DefaultRAGroup, IP = 195.234.233.126, detected L2TP/IPSec session.
dec 13 17:48:11 [IKEv1 DEBUG]: Group = DefaultRAGroup, IP = 195.234.233.126, payload NAT Original address of treatment
dec 13 17:48:11 [IKEv1]: Group = DefaultRAGroup, IP = 195.234.233.126, QM IsRekeyed its already be regenerated
dec 13 17:48:11 [IKEv1]: Group = DefaultRAGroup, IP = 195.234.233.126, error QM WSF (P2 struct & 0xd7f0b8d0, mess id 0x3)!
dec 13 17:48:11 [IKEv1 DEBUG]: Group = DefaultRAGroup, IP = 195.234.233.126, case of mistaken IKE responder QM WSF (struct & 0xd7f0b8d0)
dec 13 17:48:11 [IKEv1 DEBUG]: Group = DefaultRAGroup, IP = 195.234.233.126, sending clear/delete with the message of reason
dec 13 17:48:11 [IKEv1]: Group = DefaultRAGroup, IP = 195.234.233.126, peer table correlator Removing failed, no match!
dec 13 17:48:12 [IKEv1 DECODER]: IP = 195.234.233.126, IKE Responder starting QM: id msg = 00000003
dec 13 17:48:12 [IKEv1]: IP = 195.234.233.126, IKE_DECODE RECEIPT Message (msgid = 3) with payloads: HDR HASH (8) HIS (1) + (10) NUNCIO + ID (5) + ID (5) ++ NAT - OA (131) + NONE (0) overall length: 312
dec 13 17:48:12 [IKEv1 DEBUG]: Group = DefaultRAGroup, IP = 195.234.233.126, processing hash payload
dec 13 17:48:12 [IKEv1 DEBUG]: Group = DefaultRAGroup, IP = 195.234.233.126, SA payload processing
dec 13 17:48:12 [IKEv1 DEBUG]: Group = DefaultRAGroup, IP = 195.234.233.126, nonce payload processing
dec 13 17:48:12 [IKEv1 DEBUG]: Group = DefaultRAGroup, IP = 195.234.233.126, payload processing ID
dec 13 17:48:12 [IKEv1 DECODER]: Group = DefaultRAGroup, IP = 195.234.233.126, ID_IPV4_ADDR received ID
192.168.236.25
dec 13 17:48:12 [IKEv1]: Group = DefaultRAGroup, IP = 195.234.233.126, data received in payload ID remote Proxy Host: address 195.234.233.126, Protocol 17, Port 0
dec 13 17:48:12 [IKEv1 DEBUG]: Group = DefaultRAGroup, IP = 195.234.233.126, payload processing ID
dec 13 17:48:12 [IKEv1 DECODER]: Group = DefaultRAGroup, IP = 195.234.233.126, ID_IPV4_ADDR received ID
94.88.180.84
dec 13 17:48:12 [IKEv1]: Group = DefaultRAGroup, IP = 195.234.233.126, data received in payload ID local Proxy Host: address 172.16.34.1, Protocol 17 Port 1701
dec 13 17:48:12 [IKEv1]: Group = DefaultRAGroup, IP = 195.234.233.126, detected L2TP/IPSec session.
dec 13 17:48:12 [IKEv1 DEBUG]: Group = DefaultRAGroup, IP = 195.234.233.126, payload NAT Original address of treatment
dec 13 17:48:12 [IKEv1]: Group = DefaultRAGroup, IP = 195.234.233.126, QM IsRekeyed its already be regenerated
dec 13 17:48:12 [IKEv1]: Group = DefaultRAGroup, IP = 195.234.233.126, error QM WSF (P2 struct & 0xd8b55468, mess id 0x3)!
dec 13 17:48:12 [IKEv1 DEBUG]: Group = DefaultRAGroup, IP = 195.234.233.126, case of mistaken IKE responder QM WSF (struct & 0xd8b55468)
dec 13 17:48:12 [IKEv1 DEBUG]: Group = DefaultRAGroup, IP = 195.234.233.126, sending clear/delete with the message of reason
dec 13 17:48:12 [IKEv1]: Group = DefaultRAGroup, IP = 195.234.233.126, peer table correlator Removing failed, no match!Similar Questions
ROUTING_SPLIT list standard access allowed 172.16.0.0 255.248.0.0
transport mode encryption ipsec transform-set WIN10 ikev1
Crypto ipsec transform-set esp-3des esp-sha-hmac WIN7 ikev1
Crypto ipsec transform-set transport WIN7 using ikev1
Dynamic crypto map DYNMAP 10 set transform-set WIN10 WIN7 ikev1
Crypto dynamic-map DYNMAP 10 the value reverse-road
card crypto CMAP 99-isakmp dynamic ipsec DYNMAP
CMAP interface ipsec crypto map
crypto ISAKMP disconnect - notify
Ikev1 enable ipsec crypto
IKEv1 crypto policy 10
preshared authentication
aes-256 encryption
sha hash
Group 2
life 86400
output
IKEv1 crypto policy 20
preshared authentication
3des encryption
sha hash
Group 2
life 86400
output
EIK_USERS_RA group policy attributes
value of 12.34.56.7 DNS Server 12.34.56.8
VPN - connections 2
L2TP ipsec VPN-tunnel-Protocol ikev1
disable the password-storage
enable IP-comp
enable PFS
Split-tunnel-policy tunnelspecified
value of Split-tunnel-network-list ROUTING_SPLIT
ad.NYME.Hu value by default-field
Intercept-dhcp enable
the authentication of the user activation
the address value VPN_Users pools
output
authentication-server-group challenger
accounting-server-group challenger
Group Policy - by default-EIK_USERS_RA
IPSec-attributes tunnel-group DefaultRAGroup
IKEv1 pre-shared-key *.
tunnel-group DefaultRAGroup ppp-attributes
No chap authentication
no authentication ms-chap-v1
ms-chap-v2 authentication
output
Assigned IP: 172.23.32.2 public IP address: 12.34.56.9
Protocol: IKEv1 IPsecOverNatT L2TPOverIPsecOverNatT
License: Another VPN
Encryption: IKEv1: (1) 3DES IPsecOverNatT: (1) L2TPOverIPsecOverNatT AES256: (1) no
Hash: IKEv1: (1) IPsecOverNatT SHA1: (1) L2TPOverIPsecOverNatT SHA1: (1) no
TX Bytes: 1233 bytes Rx: 10698
Group Policy: Group EIK_USERS_RA Tunnel: DefaultRAGroup
Connect time: 15:12:29 UTC Friday, April 8, 2016
Duration: 0: 00: 01:00
Inactivity: 0 h: 00 m: 00s
Result of the NAC: unknown
Map VLANS: VLAN n/a: no
crypto ISAKMP policy 10
BA aes
preshared authentication
Group 5
test key crypto isakmp 192.168.1.2 address
test 10 map ipsec-isakmp crypto
defined peer 192.168.1.2
Set transform-set test
match address WILL
allow gre 10.0.10.0 0.0.0.255 10.0.20.0 0.0.0.255
No switchport
IP 192.168.1.1 255.255.255.0
crypto map test
IP 10.0.10.1 255.255.255.0
IP ospf 1 zone 0
10.0.100.2 IP address 255.255.255.0
IP ospf 1 zone 0
source of tunnel Ethernet0/0
tunnel destination 192.168.1.1
end
R2 config
BA aes
preshared authentication
Group 5
test key crypto isakmp 192.168.1.1 address
!
!
Crypto ipsec transform-set test aes - esp esp-sha-hmac
!
!
!
test card crypto-address Ethernet0/0
test 10 map ipsec-isakmp crypto
defined peer 192.168.1.1
Set transform-set test
match address GR
!
allow gre 10.0.20.0 0.0.0.255 10.0.10.0 0.0.0.255
No switchport
IP 192.168.1.2 255.255.255.0
crypto map test
IP 10.0.20.1 255.255.255.0
IP ospf 1 zone 0
10.0.100.1 IP address 255.255.255.0
IP ospf 1 zone 0
source of tunnel Ethernet0/0
tunnel destination 192.168.1.2
end
BA aes
preshared authentication
Group 5
ISAKMP crypto key T3ST001 address 0.0.0.0 0.0.0.0
!
!
Crypto ipsec transform-set IPSec_PLC aes - esp esp-sha-hmac
transport mode
!
map PLC - CUM 10 ipsec-isakmp crypto
defined by peer 167.134.216.89
game of transformation-IPSec_PLC
match address 100
!
!
!
Tunnel1 interface
bandwidth 1984
IP 167.134.216.94 255.255.255.252
Mtu 1476 IP
load-interval 30
source of tunnel Serial0/1/0:0
tunnel destination 167.134.216.89
IP 167.134.216.90 255.255.255.252
card crypto PLC - CUM
network 167.134.216.92 0.0.0.3
BA aes
preshared authentication
Group 5
ISAKMP crypto key T3ST001 address 0.0.0.0 0.0.0.0
!
!
Crypto ipsec transform-set IPSec_PLC aes - esp esp-sha-hmac
transport mode
!
map PLC - CUM 10 ipsec-isakmp crypto
defined by peer 167.134.216.90
game of transformation-IPSec_PLC
match address 100
bandwidth 1984
IP 167.134.216.93 255.255.255.252
Mtu 1476 IP
load-interval 30
source of tunnel Serial1/0/0:1
tunnel destination 167.134.216.90
bandwidth 1984
IP 167.134.216.89 255.255.255.252
IP access-group 101 in
load-interval 30
no fair queue
card crypto PLC - CUM
conn-id State DST CBC slot
167.134.216.89 167.134.216.90 QM_IDLE 3 0
status of DST CBC State conn-id slot
167.134.216.89 167.134.216.90 QM_IDLE 3 0 ACTIVE
3 Serial0/1/0: 167.134.216.90 0 HMAC_SHA + AES_CBC 0 0 value
3001 Serial0/1/0: 167.134.216.90 0 set AES + SHA 0 0
3002 Serial0/1/0: 167.134.216.90 0 set AES + SHA 61 0
3 Serial1/0/0:1 167.134.216.89 set HMAC_SHA + AES_CBC 0 0
2000 Serial1/0/0:1 167.134.216.89 set HMAC_SHA + 0 66 AES_CBC
2001 Serial1/0/0:1 167.134.216.89 set HMAC_SHA + AES_CBC 0 0
~~~~~~~~~~~~~~~~~~~~~~
-----------------------------
preshared authentication
3des encryption
sha hash
Group 2
life 86400
--------------------------------
4. configure the authentication method
--------------------------------------
Locally on ASA
------------------
attrib l2tp username
VPN-group-policy DefaultRAGroup
Protocol-tunnel-VPN l2tp ipsec
------------------------
internal DefaultRAGroup group strategy
attributes of Group Policy DefaultRAGroup
the address value L2TP_POOL-WHO pools
Protocol-tunnel-VPN l2tp ipsec
------------------------
address-pool L2TP_POOL-OMS
Group Policy - by default-DefaultRAGroup
IKEv1 pre-shared-key *.
no authentication ms-chap-v1
ms-chap-v2 authentication
------------------------------
Crypto ipsec transform-set RIGHT ikev1 aes - esp esp-sha-hmac
IKEv1 crypto ipsec transform-set RIGHT transit mode
---------------------------------
Crypto-map dynamic dynmap 1 set transform-set RIGHT ikev1
------------------------------------------------------------
-----------------------------------
------------------------------
Debug crypto ikev1
******************
FWASA-VICT1 (config) # 01 August at 20:54:25 [IKEv1] group = DefaultRAGroup, IP = 197.217.68.99, error QM WSF (P2 struct & 0xb074f010, mess id 0 x 4)!
01 August at 20:54:25 [IKEv1] group = DefaultRAGroup, IP = 197.217.68.99, peer table correlator Removing failed, no match!
01 August at 20:54:30 [IKEv1] group = DefaultRAGroup, IP = 197.217.68.99, error QM WSF (P2 struct & 0xb074f010, mess id 0 x 4)!
01 August at 20:54:30 [IKEv1] group = DefaultRAGroup, IP = 197.217.68.99, peer table correlator Removing failed, no match!
01 August at 20:54:34 [IKEv1] group = DefaultRAGroup, IP = 197.217.68.99, error QM WSF (P2 struct & 0xb074f010, mess id 0 x 4)!
01 August at 20:54:34 [IKEv1] group = DefaultRAGroup, IP = 197.217.68.99, peer table correlator Removing failed, no match!
01 August at 20:54:43 [IKEv1] group = DefaultRAGroup, IP = 197.217.68.99, error QM WSF (P2 struct & 0xb074f010, mess id 0 x 4)!
01 August-20:54:43 [IKEv1] group = DefaultRAGroup, IP = 197.217.68.99, peer table correlator Removing failed, no match!
Debugging debug crypto isakmp 7
Debug crypto ipsec 7
*****************************
01 August 20:35 [IKEv1 DEBUG] IP = 197.217.68.99, SA payload processing
01 August 20:35 [IKEv1] Phase 1 failure: incompatible types of attributes of class Group Description: RRs would be: unknown Cfg would: Group 2
01 August 20:35 [IKEv1] Phase 1 failure: incompatible types of attributes of class Group Description: RRs would be: unknown Cfg would: Group 2
01 August 20:35 [IKEv1] Phase 1 failure: incompatible types of attributes of class Group Description: RRs would be: unknown Cfg would: Group 2
01 August 20:35 [IKEv1] Phase 1 failure: incompatible types of attributes of class Group Description: RRs would be: unknown Cfg would: Group 2
01 August 20:35 [IKEv1] Phase 1 failure: incompatible types of attributes of class Group Description: RRs would be: unknown Cfg would: Group 2
01 August 20:35 [IKEv1] Phase 1 failure: incompatible types of attributes of class Group Description: RRs would be: unknown Cfg would: Group 2
01 August 20:35 [IKEv1] Phase 1 failure: incompatible types of attributes of class Group Description: RRs would be: unknown Cfg would: Group 2
01 August 20:35 [IKEv1] Phase 1 failure: incompatible types of attributes of class Group Description: RRs would be: unknown Cfg would: Group 2
01 August 20:35 [IKEv1] Phase 1 failure: incompatible types of attributes of class Group Description: RRs would be: unknown Cfg would: Group 2
01 August 20:35 [IKEv1] Phase 1 failure: incompatible types of attributes of class Group Description: RRs would be: unknown Cfg would: Group 2
01 August 20:35 [IKEv1 DEBUG] IP = 197.217.68.99, Oakley proposal is acceptable
01 August 20:35 [IKEv1 DEBUG] IP = 197.217.68.99, payload processing VID
01 August 20:35 [IKEv1 DEBUG] IP = 197.217.68.99, payload processing VID
01 August 20:35 [IKEv1 DEBUG] IP = 197.217.68.99, received NAT - Traversal RFC VID
01 August 20:35 [IKEv1 DEBUG] IP = 197.217.68.99, payload processing VID
01 August 20:35 [IKEv1 DEBUG] IP = 197.217.68.99, received NAT-Traversal worm 02 VID
01 August 20:35 [IKEv1 DEBUG] IP = 197.217.68.99, payload processing VID
01 August 20:35 [IKEv1 DEBUG] IP = 197.217.68.99, received Fragmentation VID
01 August 20:35 [IKEv1 DEBUG] IP = 197.217.68.99, payload processing VID
01 August 20:35 [IKEv1 DEBUG] IP = 197.217.68.99, payload processing VID
01 August 20:35 [IKEv1 DEBUG] IP = 197.217.68.99, payload processing VID
01 August 20:35 [IKEv1 DEBUG] IP = 197.217.68.99, IKE SA payload processing
01 August 20:35 [IKEv1] Phase 1 failure: incompatible types of attributes of class Group Description: RRs would be: unknown Cfg would: Group 2
01 August 20:35 [IKEv1] Phase 1 failure: incompatible types of attributes of class Group Description: RRs would be: unknown Cfg would: Group 2
01 August 20:35 [IKEv1] Phase 1 failure: incompatible types of attributes of class Group Description: RRs would be: unknown Cfg would: Group 2
01 August 20:35 [IKEv1] Phase 1 failure: incompatible types of attributes of class Group Description: RRs would be: unknown Cfg would: Group 2
01 August 20:35 [IKEv1] Phase 1 failure: incompatible types of attributes of class Group Description: RRs would be: unknown Cfg would: Group 2
01 August 20:35 [IKEv1] Phase 1 failure: incompatible types of attributes of class Group Description: RRs would be: unknown Cfg would: Group 2
01 August 20:35 [IKEv1] Phase 1 failure: incompatible types of attributes of class Group Description: RRs would be: unknown Cfg would: Group 2
01 August 20:35 [IKEv1] Phase 1 failure: incompatible types of attributes of class Group Description: RRs would be: unknown Cfg would: Group 2
01 August 20:35 [IKEv1] Phase 1 failure: incompatible types of attributes of class Group Description: RRs would be: unknown Cfg would: Group 2
01 August 20:35 [IKEv1] Phase 1 failure: incompatible types of attributes of class Group Description: RRs would be: unknown Cfg would: Group 2
01 August 20:35 [IKEv1 DEBUG] IP = 197.217.68.99, IKE SA proposal # 1, transform # 5 entry IKE acceptable Matches # 3 overall
01 August 20:35 [IKEv1 DEBUG] IP = 197.217.68.99, build the payloads of ISAKMP security
01 August 20:35 [IKEv1 DEBUG] IP = 197.217.68.99, constructing the payload of NAT-Traversal VID worm RFC
01 August 20:35 [IKEv1 DEBUG] IP = 197.217.68.99, construction of Fragmentation VID + load useful functionality
01 August 20:35 [IKEv1] IP = 197.217.68.99, IKE_DECODE SEND Message (msgid = 0) with payloads: HDR, HIS (1), SELLER (13) of the SELLER (13) + (0) NONE total length: 124
01 August at 20:35:01 [IKEv1] IP = 197.217.68.99, IKE_DECODE RECEIPT Message (msgid = 0) with payloads: HDR + KE (4) NUNCIO (10) + NAT - D (20), NAT - D (20) & NONE (0) overall length: 260
01 August at 20:35:01 [IKEv1 DEBUG] IP = 197.217.68.99, processing ke payload
01 August at 20:35:01 [IKEv1 DEBUG] IP = 197.217.68.99, payload processing ISA_KE
01 August at 20:35:01 [IKEv1 DEBUG] IP = 197.217.68.99, nonce payload processing
01 August at 20:35:01 [IKEv1 DEBUG] IP = 197.217.68.99, payload NAT-discovery of treatment
01 August at 20:35:01 [IKEv1 DEBUG] IP = 197.217.68.99, NAT discovery hash calculation
01 August at 20:35:01 [IKEv1 DEBUG] IP = 197.217.68.99, payload NAT-discovery of treatment
01 August at 20:35:01 [IKEv1 DEBUG] IP = 197.217.68.99, NAT discovery hash calculation
01 August at 20:35:01 [IKEv1 DEBUG] IP = 197.217.68.99, building ke payload
01 August at 20:35:01 [IKEv1 DEBUG] IP = 197.217.68.99, building nonce payload
01 August at 20:35:01 [IKEv1 DEBUG] IP = 197.217.68.99, build payloads of Cisco Unity VID
01 August at 20:35:01 [IKEv1 DEBUG] IP = 197.217.68.99, constructing payload V6 VID xauth
01 August at 20:35:01 [IKEv1 DEBUG] IP = 197.217.68.99, Send IOS VID
01 August at 20:35:01 [IKEv1 DEBUG] IP = 197.217.68.99, ASA usurpation IOS Vendor ID payload construction (version: 1.0.0 capabilities: 20000001)
01 August at 20:35:01 [IKEv1 DEBUG] IP = 197.217.68.99, build payloads VID
01 August at 20:35:01 [IKEv1 DEBUG] IP = 197.217.68.99, Send Altiga/Cisco VPN3000/Cisco ASA GW VID
01 August at 20:35:01 [IKEv1 DEBUG] IP = 197.217.68.99, NAT-discovery payload construction
01 August at 20:35:01 [IKEv1 DEBUG] IP = 197.217.68.99, NAT discovery hash calculation
01 August at 20:35:01 [IKEv1 DEBUG] IP = 197.217.68.99, NAT-discovery payload construction
01 August at 20:35:01 [IKEv1 DEBUG] IP = 197.217.68.99, NAT discovery hash calculation
01 August at 20:35:01 [IKEv1] IP = 197.217.68.99, connection landed on tunnel_group DefaultRAGroup
01 August at 20:35:01 [IKEv1 DEBUG] group = DefaultRAGroup, IP = 197.217.68.99, Generating keys for answering machine...
01 August at 20:35:01 [IKEv1] IP = 197.217.68.99, IKE_DECODE SEND Message (msgid = 0) with payloads: HDR + KE (4) + (10) NUNCIO seller (13) + the seller (13) + the seller (13) + the seller (13) NAT - D (20) + NAT - D (20) & NONE (0) total length: 304
01 August at 20:35:02 [IKEv1] IP = 197.217.68.99, IKE_DECODE RECEIPT Message (msgid = 0) with payloads: HDR + ID (5) + HASH (8) + (0) NONE total length: 64
01 August at 20:35:02 [IKEv1 DEBUG] group = DefaultRAGroup, IP = 197.217.68.99, payload processing ID
01 August at 20:35:02 [IKEv1 DEBUG] group = DefaultRAGroup, IP = 197.217.68.99, processing hash payload
01 August at 20:35:02 [IKEv1 DEBUG] group = DefaultRAGroup, IP = 197.217.68.99, calculation of hash for ISAKMP
01 August at 20:35:02 [IKEv1] group = DefaultRAGroup, IP = 197.217.68.99, status of automatic NAT detection: remote endpoint IS behind a NAT device this end is behind a NAT device
01 August at 20:35:02 [IKEv1] IP = 197.217.68.99, connection landed on tunnel_group DefaultRAGroup
01 August at 20:35:02 [IKEv1 DEBUG] group = DefaultRAGroup, IP = 197.217.68.99, construction of payload ID
01 August at 20:35:02 [IKEv1 DEBUG] group = DefaultRAGroup, IP = 197.217.68.99, build payloads of hash
01 August at 20:35:02 [IKEv1 DEBUG] group = DefaultRAGroup, IP = 197.217.68.99, calculation of hash for ISAKMP
01 August at 20:35:02 [IKEv1 DEBUG] group = DefaultRAGroup, IP = 197.217.68.99, building dpd vid payload
01 August at 20:35:02 [IKEv1] IP = 197.217.68.99, IKE_DECODE SEND Message (msgid = 0) with payloads: HDR + ID (5) + HASH (8), SELLER (13) + (0) NONE total length: 84
01 August at 20:35:02 [IKEv1] group = DefaultRAGroup, IP = 197.217.68.99, PHASE 1 COMPLETED
01 August at 20:35:02 [IKEv1] IP = 197.217.68.99, type Keep-alive for this connection: None
01 August at 20:35:02 [IKEv1] IP = 197.217.68.99, Keep-alives configured on, but the peer does not support persistent (type = None)
01 August at 20:35:02 [IKEv1 DEBUG] group = DefaultRAGroup, IP = 197.217.68.99, timer to generate a new key to start P1: 21600 seconds.
01 August at 20:35:03 [IKEv1] IP = 197.217.68.99, IKE_DECODE RECEIPT Message (msgid = 1) with payloads: HDR HASH (8) HIS (1) + (10) NUNCIO + ID (5) + ID (5) + NAT - OA (21) ++ NAT - OA (21) + (0) NONE total length: 324
01 August at 20:35:03 [IKEv1 DEBUG] group = DefaultRAGroup, IP = 197.217.68.99, processing hash payload
01 August at 20:35:03 [IKEv1 DEBUG] group = DefaultRAGroup, IP = 197.217.68.99, SA payload processing
01 August at 20:35:03 [IKEv1 DEBUG] group = DefaultRAGroup, IP = 197.217.68.99, nonce payload processing
01 August at 20:35:03 [IKEv1 DEBUG] group = DefaultRAGroup, IP = 197.217.68.99, payload processing ID
01 August at 20:35:03 [IKEv1] group = DefaultRAGroup, IP = 197.217.68.99, data received in payload ID remote Proxy Host: address 192.168.5.122, Protocol 17 Port 1701
01 August at 20:35:03 [IKEv1 DEBUG] group = DefaultRAGroup, IP = 197.217.68.99, payload processing ID
01 August at 20:35:03 [IKEv1] group = DefaultRAGroup, IP = 197.217.68.99, data received in payload ID local Proxy Host: address 41.63.166.15, Protocol 17 Port 1701
01 August at 20:35:03 [IKEv1] group = DefaultRAGroup, IP = 197.217.68.99, detected L2TP/IPSec session.
01 August at 20:35:03 [IKEv1 DEBUG] group = DefaultRAGroup, IP = 197.217.68.99, payload NAT Original address of treatment
01 August at 20:35:03 [IKEv1 DEBUG] group = DefaultRAGroup, IP = 197.217.68.99, payload NAT Original address of treatment
01 August at 20:35:03 [IKEv1] group = DefaultRAGroup, IP = 197.217.68.99, QM IsRekeyed its not found old addr
01 August at 20:35:03 [IKEv1 DEBUG] group = DefaultRAGroup, IP = 197.217.68.99, only Tunnel UDP-encapsulated and UDP-encapsulated-Transport mode NAT-Traversal-defined selection
01 August at 20:35:03 [IKEv1] group = DefaultRAGroup, IP = 197.217.68.99, remote peer IKE configured crypto card: dynmap
01 August at 20:35:03 [IKEv1 DEBUG] group = DefaultRAGroup, IP = 197.217.68.99, payload processing IPSec SA
01 August at 20:35:03 [IKEv1 DEBUG] group = DefaultRAGroup, IP = 197.217.68.99, IPSec SA proposal # 1, turn # 1 entry overall SA IPSec acceptable matches # 1
01 August at 20:35:03 [IKEv1] group = DefaultRAGroup, IP = 197.217.68.99, IKE: asking SPI!
IPSEC: HIS embryonic new created @ 0xb2b4ef98.
RCS: 0XB1BBEC58,
Direction: inbound
SPI: 0X8DFBC25E
Session ID: 0 x 01236000
VPIF num: 0x00000002
Tunnel type: ra
Protocol: esp
Life expectancy: 240 seconds
01 August at 20:35:03 [IKEv1 DEBUG] group = DefaultRAGroup, IP = 197.217.68.99, IKE got SPI engine key: SPI = 0x8dfbc25e
01 August at 20:35:03 [IKEv1 DEBUG] group = DefaultRAGroup, IP = 197.217.68.99, quick mode of oakley constucting
01 August at 20:35:03 [IKEv1 DEBUG] group = DefaultRAGroup, IP = 197.217.68.99, empty building hash payload
01 August at 20:35:03 [IKEv1 DEBUG] group = DefaultRAGroup, IP = 197.217.68.99, building the IPSec Security Association Management
01 August at 20:35:03 [IKEv1 DEBUG] group = DefaultRAGroup, IP = 197.217.68.99, construction of support useful Nuncio IPSec
01 August at 20:35:03 [IKEv1 DEBUG] group = DefaultRAGroup, IP = 197.217.68.99, constructing the ID of the proxy
01 August at 20:35:03 [IKEv1 DEBUG] group = DefaultRAGroup, IP = 197.217.68.99, transmission Proxy Id:
Remote host: 197.217.68.99 Protocol Port 17 0
Local host: 10.30.21.2 Protocol 17 Port 1701
01 August at 20:35:03 [IKEv1 DEBUG] group = DefaultRAGroup, IP = 197.217.68.99, construction of payload NAT Original address
01 August at 20:35:03 [IKEv1 DEBUG] group = DefaultRAGroup, IP = 197.217.68.99, construction of payload NAT Original address
01 August at 20:35:03 [IKEv1] group = DefaultRAGroup, IP = 197.217.68.99, payload NAT Original address sending NAT-Traversal
01 August at 20:35:03 [IKEv1 DEBUG] group = DefaultRAGroup, IP = 197.217.68.99, build payloads of hash qm
01 August at 20:35:03 [IKEv1] IP = 197.217.68.99, IKE_DECODE SEND Message (msgid = 1) with payloads: HDR HASH (8) HIS (1) + (10) NUNCIO + ID (5) + ID (5) + NAT - OA (21) ++ NAT - OA (21) + NONE (0) overall length: 188
01 August at 20:35:04 [IKEv1] IP = 197.217.68.99, IKE_DECODE RECEIPT Message (msgid = 2) with payloads: HDR HASH (8) HIS (1) + (10) NUNCIO + ID (5) + ID (5) + NAT - OA (21) ++ NAT - OA (21) + (0) NONE total length: 324
01 August at 20:35:04 [IKEv1 DEBUG] group = DefaultRAGroup, IP = 197.217.68.99, processing hash payload
01 August at 20:35:04 [IKEv1 DEBUG] group = DefaultRAGroup, IP = 197.217.68.99, SA payload processing
01 August at 20:35:04 [IKEv1 DEBUG] group = DefaultRAGroup, IP = 197.217.68.99, nonce payload processing
01 August at 20:35:04 [IKEv1 DEBUG] group = DefaultRAGroup, IP = 197.217.68.99, payload processing ID
01 August at 20:35:04 [IKEv1] group = DefaultRAGroup, IP = 197.217.68.99, data received in payload ID remote Proxy Host: address 197.217.68.99, Protocol 17, Port 0
01 August at 20:35:04 [IKEv1 DEBUG] group = DefaultRAGroup, IP = 197.217.68.99, payload processing ID
01 August at 20:35:04 [IKEv1] group = DefaultRAGroup, IP = 197.217.68.99, data received in payload ID local Proxy Host: address 10.30.21.2, Protocol 17 Port 1701
01 August at 20:35:04 [IKEv1] group = DefaultRAGroup, IP = 197.217.68.99, detected L2TP/IPSec session.
01 August at 20:35:04 [IKEv1 DEBUG] group = DefaultRAGroup, IP = 197.217.68.99, payload NAT Original address of treatment
01 August at 20:35:04 [IKEv1 DEBUG] group = DefaultRAGroup, IP = 197.217.68.99, payload NAT Original address of treatment
01 August at 20:35:04 [IKEv1] IP = 197.217.68.99, rejecting new IPSec security association negotiation for peer 197.217.68.99. A negotiation was underway for local 10.30.21.2/255.255.255.255, remote Proxy 197.217.68.99/255.255.255.255 Proxy
01 August at 20:35:04 [IKEv1] group = DefaultRAGroup, IP = 197.217.68.99, error QM WSF (P2 struct & 0xb1fe13a8, mess id 0 x 2)!
01 August at 20:35:04 [IKEv1 DEBUG] group = DefaultRAGroup, IP = 197.217.68.99, case of mistaken IKE responder QM WSF (struct & 0xb1fe13a8)
01 August at 20:35:04 [IKEv1 DEBUG] group = DefaultRAGroup, IP = 197.217.68.99, sending clear/delete with the message of reason
01 August at 20:35:04 [IKEv1] group = DefaultRAGroup, IP = 197.217.68.99, peer table correlator Removing failed, no match!
01 August at 20:35:05 [IKEv1] IP = 197.217.68.99, IKE_DECODE RECEIPT Message (msgid = 2) with payloads: HDR HASH (8) HIS (1) + (10) NUNCIO + ID (5) + ID (5) + NAT - OA (21) ++ NAT - OA (21) + (0) NONE total length: 324
01 August at 20:35:05 [IKEv1 DEBUG] group = DefaultRAGroup, IP = 197.217.68.99, processing hash payload
01 August at 20:35:05 [IKEv1 DEBUG] group = DefaultRAGroup, IP = 197.217.68.99, SA payload processing
01 August at 20:35:05 [IKEv1 DEBUG] group = DefaultRAGroup, IP = 197.217.68.99, nonce payload processing
01 August at 20:35:05 [IKEv1 DEBUG] group = DefaultRAGroup, IP = 197.217.68.99, payload processing ID
01 August at 20:35:05 [IKEv1] group = DefaultRAGroup, IP = 197.217.68.99, data received in payload ID remote Proxy Host: address 197.217.68.99, Protocol 17, Port 0
01 August at 20:35:05 [IKEv1 DEBUG] group = DefaultRAGroup, IP = 197.217.68.99, payload processing ID
01 August at 20:35:05 [IKEv1] group = DefaultRAGroup, IP = 197.217.68.99, data received in payload ID local Proxy Host: address 10.30.21.2, Protocol 17 Port 1701
01 August at 20:35:05 [IKEv1] group = DefaultRAGroup, IP = 197.217.68.99, detected L2TP/IPSec session.
01 August at 20:35:05 [IKEv1 DEBUG] group = DefaultRAGroup, IP = 197.217.68.99, payload NAT Original address of treatment
01 August at 20:35:05 [IKEv1 DEBUG] group = DefaultRAGroup, IP = 197.217.68.99, payload NAT Original address of treatment
01 August at 20:35:05 [IKEv1] IP = 197.217.68.99, rejecting new IPSec security association negotiation for peer 197.217.68.99. A negotiation was underway for local 10.30.21.2/255.255.255.255, remote Proxy 197.217.68.99/255.255.255.255 Proxy
01 August at 20:35:05 [IKEv1] group = DefaultRAGroup, IP = 197.217.68.99, error QM WSF (P2 struct & 0xb074f010, mess id 0 x 2)!
01 August at 20:35:05 [IKEv1 DEBUG] group = DefaultRAGroup, IP = 197.217.68.99, case of mistaken IKE responder QM WSF (struct & 0xb074f010)
01 August at 20:35:05 [IKEv1 DEBUG] group = DefaultRAGroup, IP = 197.217.68.99, sending clear/delete with the message of reason
01 August at 20:35:05 [IKEv1] group = DefaultRAGroup, IP = 197.217.68.99, peer table correlator Removing failed, no match!
01 August at 20:35:02 [IKEv1] group = DefaultRAGroup, IP = 197.217.68.99, PHASE 1 COMPLETED
Please try to use ESP-3DES and HMAC-SHA-ESP to turn together and tell us how it rates.
Dinesh MoudgilMaybe you are looking for