IPSec Phase2 ASA5525 <>- problem of Cyberoam
After the cyberoam to the new software upgrade, we have problems with the IPSec connection.
For example: Phase 2 of the vpn is disconnect every 30, 40 or 60 seconds regularly for half a day. On the other half, it works OK without any problems. Problem occurs randomly...
Recently, we changed the encryption of the phase 2 of AES256 AES128, and it helped, but only for a period of 2 weeks. After this time he started swinging again :)
It looks more like a software bug rather than an incorrect configuration, but maby someone had similar issue and resolved it?
Phase 1
Encryption Algorithm aes256
Authentication algorithm sha1
Diffie-Hellman Group 5
Key to life 86400 seconds
Control peer after 30 seconds
Wait for the answer up to 120 seconds
When Peer is not current action Clear
Phase2
Encryption Algorithm aes128
Authentication algorithm sha1
Key life 3600
Mar 2 08:51:11 % Y.Y.Y.Y ASA-6-113009: AAA recovered in group policy by default (Policy1) for user = X.X.X.X
Mar 2 08:51:11 % Y.Y.Y.Y ASA-3-713902: Group = X.X.X.X, IP = X.X.X.X, fault QM WSF (P2 struct & 0x00007fff376dbfd0, mess id 0x5579d6cf).
Mar 2 08:51:11 % Y.Y.Y.Y ASA-3-713902: Group = X.X.X.X, IP = X.X.X.X, peer table correlator withdrawal failed, no match!
Mar 2 08:51:11 % Y.Y.Y.Y ASA-4-113019: Group = X.X.X.X, Username = X.X.X.X, IP = X.X.X.X, disconnected Session. Session type: LAN-to-LAN, duration: 0 h: 00 m: 00s, xmt bytes: 0, RRs bytes: 0, right: Phase 2 Mismatch
Mar 2 08:51:51 % Y.Y.Y.Y ASA-6-113009: AAA recovered in group policy by default (Policy1) for user = X.X.X.X
Mar 2 08:51:51 % Y.Y.Y.Y ASA-3-713902: Group = X.X.X.X, IP = X.X.X.X, fault QM WSF (P2 struct & 0x00007fff376dbfd0, mess id 0x5553b8bf).
Mar 2 08:51:51 % Y.Y.Y.Y ASA-3-713902: Group = X.X.X.X, IP = X.X.X.X, peer table correlator withdrawal failed, no match!
Mar 2 08:51:51 % Y.Y.Y.Y ASA-4-113019: Group = X.X.X.X, Username = X.X.X.X, IP = X.X.X.X, disconnected Session. Session type: LAN-to-LAN, duration: 0 h: 00 m: 00s, xmt bytes: 0, RRs bytes: 0, right: Phase 2 Mismatch
Mar 2 08:52:21 % Y.Y.Y.Y ASA-6-113009: AAA recovered in group policy by default (Policy1) for user = X.X.X.X
Mar 2 08:52:21 % Y.Y.Y.Y ASA-3-713902: Group = X.X.X.X, IP = X.X.X.X, fault QM WSF (P2 struct & 0x00007fff376dbfd0, mess id 0x4248eb0f).
Mar 2 08:52:21 % Y.Y.Y.Y ASA-3-713902: Group = X.X.X.X, IP = X.X.X.X, peer table correlator withdrawal failed, no match!
Mar 2 08:52:21 % Y.Y.Y.Y ASA-4-113019: Group = X.X.X.X, Username = X.X.X.X, IP = X.X.X.X, disconnected Session. Session type: LAN-to-LAN, duration: 0 h: 00 m: 00s, xmt bytes: 0, RRs bytes: 0, right: Phase 2 Mismatch
Mar 2 08:55:05 Y.Y.Y.Y % ASA-6-113009: AAA recovered in group policy by default (Policy1) for user = X.X.X.X
2 Mar 09:42:45 % Y.Y.Y.Y ASA-3-713902: Group = X.X.X.X, IP = X.X.X.X, fault QM WSF (P2 struct & 0x00007fff33abbc90, mess id 0x4e3ca0c5).
2 Mar 09:42:45 % Y.Y.Y.Y ASA-3-713902: Group = X.X.X.X, IP = X.X.X.X, peer table correlator withdrawal failed, no match!
2 Mar 09:42:55 % Y.Y.Y.Y ASA-3-713902: Group = X.X.X.X, IP = X.X.X.X, fault QM WSF (P2 struct & 0x00007fff33abbc90, mess id 0x4e3ca0c5).
2 Mar 09:42:55 % Y.Y.Y.Y ASA-3-713902: Group = X.X.X.X, IP = X.X.X.X, peer table correlator withdrawal failed, no match!
Hi Adam,.
This seems to be a problem with the settings of Phase 2.
Please ensure that the policies are the same at both ends.
Also, if you could provide out of crypto ipsec of simultaneous debugging for two peers, that would be useful to identify the exact reason.
On the SAA, you could use Debug conditional for the same thing:
Debug condition crypto peers
Kind regards Aditya Please evaluate the useful messages.
Tags: Cisco Security
Similar Questions
-
VPN site to Site, Phase2, ISAKMP problem
Hi all
I have a problem to Setup vpn site to site on two Cisco1841 ((C1841-ADVSECURITYK9-M) 12.4 routers (3i)) Version.
I have seen several discussions with similar problems, but no help, and I couldn't find any problem solved also.
Please see two attached documents, the first one with samples of itineraries config the remote and and the second with the debug output.
I rechecked the configs on both routers, and it seems that both are very good.
The strange is that tunnel comes up all the time, but I have only 50% by the pings of the networks the. Pings from the local and remote peers goes with 100%.
Please see the errors on the document of debugging.
Second thing, please pay attention to the subnet mask of the local interface of the local router (255.255.255.224). Maybe it's the root of a problem, it is not in line with the access list that is with wildcard 0.0.0.255?
I think it's the only thing that I forgot to check today.
Maybe it's a bug of ios or something?
I appreciate any help to solve this problem.
Thank you in advance,
If your network is 255.255.255.224 255.255.255.224 should be in the ACL to change this in two ACLs of the interesting traffic.
Check this
* 6 sep 12:59:15.362: IPSEC (validate_transform_proposal): No IPSEC cryptomap is to address local y.y.y.y (local peer)
* 6 sep 12:59:15.366: ISAKMP:(0:36:SW:1): IPSec policy invalidated proposal
* 6 sep 12:59:15.366: ISAKMP:(0:36:SW:1): politics of ITS phase 2 is not acceptable! (local y.y.y.y (local peer) remote control (remote peer) x.x.x.x)
This isn't a question about the phase I, but with the phase 2. The ACL must be changed
LOCAL
access-list 100 permit ip 192.168.0.0 0.0.0.31 192.168.2.0 0.0.0.255
REMOTE
access-list 100 permit ip 192.168.2.0 0.0.0.255 192.168.0.0 0.0.0.31
Change that firs and then disable the SA and try again. I'm not sure why you receive only 50% of responses from the remote site
-
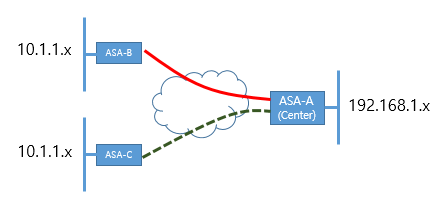
Currently, ASA - A (Center) and B has connected by VPN IPSec.
I would like a VPN establsh A ASA and ASA-C both.
But unfortunately, within the network range has same range B-ASA and ASA-C both. (10.1.1.x)
In this case, how can I connect IPSec VPN to ASA-B and C - ASA ASA - A at a time?
Thank you
Hello
You can go with policy subnet Nating ASA-C on another subnet on ASA - C (ex: 10.1.10.x) and use this as your ACL subnet subnet. It should work. Please search online for examples of configuration.
HTH
MS
-
IPSec VPN authentication problem against AD by RADIUS/ISA
As background, I have a VPN IPSec authentication against the local database upward and running with access to my internal network and work with zero issues.
So I would move offshore to the local database authentication and boince it is outside my ad. I am running 2003 server so I configure ISA Server RADIUS and think I have it properly configured. It is registered in the AD, I added my asa as a customer radius, customized remote access and connection request policies.
The test of authentication in the ASDM he succeeds with all users who need.
During the test through my client vpn on a remote computer, I get the connection terminated by a peer, no reason given.
It is said of the event on the domain controller logs
-l' user domain - user % name % has had access.
directly after this, there is an entry
-VPN-RADIUS-GP is denied access
where VPN-RADIUS-GP is the name of the tunnel group policy in my ASA.
Ive tried a lot of literature and a few forums and have not yet find any explanation as to why this would happen as username trying to authenticate to the ISA
Anyone have any ideas?
Thank you
Mac
group-policy VPN-Radius-GP external server-group VPN_Radius_Auth password aaaaaaaaaaaaaaaaaaaaaa
It is a group-foreign policy, by definition, that it is defined on the AAA server group policy, so the ASA sends a radius access request to retrieve the attributes of group policy.
See for example http://www.cisco.com/en/US/docs/security/asa/asa72/configuration/guide/vpngrp.html#wp1133706
If this isn't what you want, then just remove the group policy and use internal (as the "q101 VPN GP" you).
HTH
Herbert
-
ASA 5510 IPSEC VPN connection problem
Hello
We have an ASA 5510 (ASA version 8.0) of remote access VPN configured and works most of the time, but there is a problem when you have more than one client that connects to the same office remotely. When the first VPN client is connected to the remote desktop, everything works fine, but when the second client connects to the VPN, it connects fine but do not get any traffice return to customer. I can see under monitor-> statistical VPN-> Sessions-> remote access-> Rx Bytes is 0. Both connections are from the same public IP address of the remote desktop. I changed some settings on NAT - T and a few other things, but without success.
Could someone help me please how to fix this?
Thank you very much.
Make sure that customers use because that probably her you're not. (default value is NAT - T).
Federico.
-
IPSec VPN connectivity problem
OK, I have the following Setup. An asa 5540 is the vpn server and some cisco vpn site-to-site 2811 routers allows you to connect to it. All cisco routers have the same ip address in their internal interface, so I'm nat'ing to another ip to connect to the vpn. It goes the same for servers behind. So we have
IP nat inside source static 10.0.10.10 10.1.89.10
IP nat inside source static 10.0.10.30 10.1.89.30
OU.10 is the et.30 router server. Vpn comes up, and I cannot pint from my internal network server say Server 10.0.20.10 leash. Server 10.0.20.10 I can ping both the ip nat' ed. However, I can't ping routers 10.0.20.10. Also, I try ping 10.1.89.10 on the router and it pings fine. The other 10.1.89.30 ping does not when 10.0.10.30 does. Help, please. I need the router to communicate with 10.0.20.10 break.
Thanks in advance.
Since you're natting, and you use the same LAN ip subnet in routers (very bad desgin) try using an extended ping of the address on the lan interface nat pool.
-
IPSec security association local crypto Start
Hi all
This is my first post here, and I hope not to violate the rules of the forum. I have a problem with ipsec (actually it's my first "date" with Cisco crypto tools). Here's the situation: I got 2 cisco routers (1751) with IOS c1700-advsecurityk9 - mz.123 - 19. I'm tryin to secure the connection between two devices (in laboratory conditions) with ipsec in tunnel mode. Everything works fine, until my interest to start over GRE tunnel Cryptography. When I go up the tunnel, I put the 'encryption
card' to the tunnel device, and my troubles begin. The traffic between two endpoits (correspondence with the access list for traffic 'interesting') disappeared. After a little investigation, I found this: (I'll paste part of the configuration of the router 'A')
crypto ISAKMP policy 5
BA aes 256
preshared authentication
life 360
address cryptographic key crypto isakmp 20.20.20.2
!
Crypto ipsec transform-set esp - aes 256 esp-md5-hmac London
Crypto ipsec df - bit clear
!
London 5-isakmp ipsec crypto map
defined by peer 20.20.20.2
game of transformation-London
corresponds to the crypt of the address
!
Tunnel1 interface
bandwidth 100
IP 20.20.20.1 255.255.255.252
IP 1400 MTU
route IP cache flow
load-interval 30
CDP enable
tunnel source 10.10.10.4
tunnel destination 10.10.10.3
key 1 tunnel
tunnel path-mtu-discovery
card crypto London
!
Paris #show crypto ipsec his
Interface: Tunnel1
Tag crypto map: London, local addr. 10.10.10.4
current_peer: 20.20.20.2:500
[Cup]
endpt local crypto. : 10.10.10.4, remote Start crypto. : 20.20.20.2
Path mtu 1400, ip mtu 1400, ip mtu IDB Tunnel1
current outbound SPI: 0
[Cup]
I think that the question is coming because of "Local addr. 10.10.10.4 "it could be ' 20.20.20.1 '.
and the "crypto local Start: 10.10.10.4 'must be ' 20.20.20.1'." So I blame this for a reason of the case
because the tunnel must be done between 20.20.20.1 and 20.20.20.2 NOT between 10.10.10.4 <=>20.20.20.2.
Have anyone an idea why this is happen?
At the other site, the sittuation is the same:
crypto ISAKMP policy 5
BA aes 256
preshared authentication
life 360
address cryptographic key crypto isakmp 20.20.20.1
!
!
Crypto ipsec transform-set esp - aes 256 esp-md5-hmac paris
Crypto ipsec df - bit clear
!
map of Paris 5 ipsec-isakmp crypto
defined by peer 20.20.20.1
transformation-betting game
corresponds to the crypt of the address
!
Tunnel1 interface
bandwidth 100
IP 20.20.20.2 255.255.255.252
IP 1400 MTU
no ip-cache cef route
load-interval 30
CDP enable
tunnel source 10.10.10.3
tunnel destination 10.10.10.4
key 1 tunnel
card crypto Paris
!
London #show crypto ipsec his
Interface: Tunnel1
Tag crypto map: Paris, local addr. 10.10.10.3
current_peer: 20.20.20.1:500
[Cup]
local crypto endpt. : 10.10.10.3, remote Start crypto. : 20.20.20.1
Path mtu 1400, ip mtu 1400, ip mtu IDB Tunnel1
current outbound SPI: 0
[Cup]
Once again the same question, "local addr. 10.10.10.3' and ' Start local crypto. : 10.10.10.3'.
London #debug crypto ipsec
Sep 20 16:23:30.075: IPSEC (sa_request):,.
(Eng. msg key.) Local OUTGOING = 10.10.10.3, distance = 20.20.20.1.
Sep 20 16:24:00.071: IPSEC (key_engine): request timer shot: count = 1,.
local (identity) = 10.10.10.3, distance = 20.20.20.1.
local_proxy = 192.168.252.0/255.255.255.252/0/0 (type = 4),
remote_proxy = 192.168.253.0/255.255.255.0/0/0 (type = 4)
London isakmp crypto #show her
conn-id State DST CBC slot
20.20.20.1 10.10.10.3 MM_KEY_EXCH 2 0
The IKE/ISAKMP is trying to establish a connection with BAD source address, and the IPSec Phase2 could NOT been finished.
All suggestions are welcome!
Thanks in advance for your efforts to answare this question.
Best regards
Danail Petrov
P.s. excuse my English
Danail
I am pleased that you have found a solution to your problem. Tunnel protection is a good feature, and I'm happy that you found.
Thanks for posting to the forum and stating that you have a solution and that is the solution. It allows the most useful forum when we read about a problem and then see what fixed the problem.
I encourage you to continue your participation in the forum.
HTH
Rick
-
Cisco ASA - l2l IPSEC tunnel two dynamic hosts
Hello
I have two firewall Cisco ASA an i want to made a l2l between two ipsec tunnel, the problem is that both parties have a dynamic IP, on both sides I have configured dyndns, can I did an ipsec tunnel using dyndns name such as address peer?
Hello
ASA supports only the RFC compliant method for updates used with dynamic DNS, not updates HTTP, such as dyndns.org and others use.
i.e. https://tools.cisco.com/bugsearch/bug/CSCsk25102/?reffering_site=dumpcrOn ASA, it is not possible to configure the tunnel between two dynamic peers.
You will need to have a static end to configure static to dynamic IP.For routers, you can follow this link.
I hope this helps.Kind regards
Dinesh MoudgilPS Please rate helpful messages.
-
I have an old Mac Mini running 10.7.5 server and I'll try to get everything set up correctly, so I can use L2TP VPN and I tried the rest of this guide (https://macminicolo.net/lionservervpn) and I can connect when I'm on my internal network, but not over the Internet and I do not know (at least I hope) that it is something simple that I am wrong in my setup.
- My internal home network use the IP range 192.168.1.100 - 192.168.1.200
- All necessary ports are transmitted in both my router and firewall of the Mac
- L2TP VPN Passthrough is enabled in my router
- I installed for my Sophos antivirus, but I do not think that interferes with anything
- I have the IP address range for the VPN to use as 192.168.2.100 - 192.168.2.105 (because this should be different that my network internal, right?)
- If my NO - IP dynamic DNS host name is "xxxxxx.ddns.net" then what is the hostname must be set on in the server application, right?
- When I try to connect to the VPN via Internet using my PC, I have be active in the newspaper and I have that at the bottom of the post
If there is no information there that I do not forget to add, please let me know
Apr 6 23:19:18 servername raccoon [1240]: connection.
Apr 6 23:19:18 servername raccoon [1240]: IPSec phase 1 started (initiated by peers).
Apr 6 23:19:18 servername raccoon [1240]: IKE Packet: receive a success. (Answering machine, 1 Main Mode message).
Apr 6 23:19:18 servername raccoon [1240]: IKE Packet: forward the success. (Answering machine, 2 main Mode message).
Apr 6 23:19:18 servername raccoon [1240]: IKE Packet: receive a success. (Answering machine message in Main Mode 3).
Apr 6 23:19:18 servername raccoon [1240]: IKE Packet: forward the success. (Answering machine message in Main Mode 4).
Apr 6 23:19:18 servername raccoon [1240]: IKEv1 phase 1 AUTH: success. (Answering machine, Mode main Message 5).
Apr 6 23:19:18 servername raccoon [1240]: IKE Packet: receive a success. (Answering machine message in Main Mode 5).
Apr 6 23:19:18 servername raccoon [1240]: IKEv1 phase 1 answering machine: success. (Answering machine, Main Mode).
Apr 6 23:19:18 servername raccoon [1240]: IKE Packet: forward the success. (Answering machine, Main Mode 6 message).
Apr 6 23:19:18 servername raccoon [1240]: IKE Packet: forward the success. (Information message).
Apr 6 23:19:18 servername raccoon [1240]: IKEv1-Information Notice: pass success. (- ISAKMP SECURITY ASSOCIATION).
Apr 6 23:19:18 servername raccoon [1240]: IPSec phase 1 established (initiated by peers).
Apr 6 23:19:18 servername raccoon [1240]: IPSec Phase2 started (initiated by peers).
Apr 6 23:19:18 servername raccoon [1240]: IKE Packet: receive a success. (Answering machine message of Quick Mode 1).
Apr 6 23:19:18 servername raccoon [1240]: IKE Packet: forward the success. (Answering machine message of Quick Mode 2).
Apr 6 23:19:18 servername raccoon [1240]: IKE Packet: receive a success. (Answering machine message from fast Mode 3).
Apr 6 23:19:18 servername raccoon [1240]: IKEv1 answering Phase2: success. (Answering machine, fast Mode).
Apr 6 23:19:18 servername raccoon [1240]: IPSec Phase2 established (initiated by peers).
Apr 6 23:19:18 servername raccoon [1240]: IPSec Phase2 started (initiated by peers).
Apr 6 23:19:18 servername raccoon [1240]: IKE Packet: receive a success. (Answering machine message of Quick Mode 1).
Apr 6 23:19:18 servername raccoon [1240]: IKE Packet: forward the success. (Answering machine message of Quick Mode 2).
Apr 6 23:19:18 servername raccoon [1240]: IKE Packet: receive a success. (Answering machine message from fast Mode 3).
Apr 6 23:19:18 servername raccoon [1240]: IKE Packet: receive a success. (Information message).
Apr 6 23:19:18 servername raccoon [1240]: IKEv1 answering Phase2: success. (Answering machine, fast Mode).
Apr 6 23:19:18 servername raccoon [1240]: IPSec Phase2 established (initiated by peers).
Apr 6 23:19:21 servername raccoon [1240]: IPSec Phase2 started (initiated by peers).
So, it turns out that it was a Windows problem, apparently I just need to make the adjustments detailed here (https://support.apple.com/en-us/HT202384) on my Windows PC and I was finally able to connect. I figured this out when I actually tried to connect to the VPN using my iPad and I saw that it connected without a problem, I just wanted to reply to my post wrap someone else has this problem and I hope that this post will help
-
BIND THE SINGLE TUNNEL ON ASA IP ADDRESS
Hi all
BACKGROUND
We have a VPN site-to put in place between two ASAs by using IPSEC.
PROBLEM
We will refer to this configuration as a site A and site B. The site has, we have an obligation to ensure that all traffic from a single host goes through the VPN tunnel while all the other guests to site A have local access to the internet and do not cross the L2L tunnel. We study the best solution for this, including the possibilities of VLANS, static NATs and ACL. Also on the client device, we'll need to bind a MAC address to ensure the same local IP address is returned every time via DHCP, although if the client device sits in its own VIRTUAL local network for example then binding MAC address is not required. It is not possible to configure a static IP address on the host device.
Does anyone have recommendations as to how best to configure this requirement.
Thank you
You are right that the ASA, for now, does not support the DHCP reservations. If your only option to get what you want to work is to place the customer in a VLAN separated where you can assign a distinct scope (as you mentioned)
--
Please note all useful posts
-
ASA - a Site with self-signed certificates
Team,
ASA version 9.1 (3), ASDM 7.1 (4) on 5505.
I have a pair of Cisco ASA 5505 that I am trying to establish a tunnel. I do everything with PSK. IKEv2 with AES256 IPSec. No problem...
However, I learned that I can auto-signer certificates and use them to authenticate each firewall to another. I tried for hours... Generating of certs in all combinations and options, and the export of the P12 in the other firewall, by adding in - no problem
I have self signed CERTS, so there is no CA.
Then I'll be back in the connection profile and remove the PSK - flip on to RSA - SIG in the IKE Policy.
Does anyone have this working with the ASA version, I'm running and care apart from your snippets of configuration especially how you created the pair of keys, self-signed one, exported and adding in the adjacent firewall?
I don't want to use PSK for authentication.
Help!
I never used this way without a CA so I can't guarantee that it will work, but one thing is often forgotten with digital certificates: you assigned the ID-Cert cert in the crypto-plan?
--
Don't stop once you have upgraded your network! Improve the world by lending money to low-income workers:
http://www.Kiva.org/invitedBy/karsteni -
Need to patch to get IPsec to start working in Internet instant Mesasenger - I fought this for about 3 months. I can't do a Messenger call for more than a minute before having to re - connect - it's driving me crazy - fix your product - Paul * address email is removed from the privacy *. Settings information (network security) Diagnostics that can block connections:
filter name: Messaging microsoft instant - name for the provider context: windows Instant Messenger - provider name: Microsoft Corp.Provider - description: Microsoft Windows Firewall: IPsec provider
Hi paulrhea,-What version of the operating system are you using?-You are able to go online with no problems?-Have you been able to use the Messenger without any problem before?If you use Windows 7 or Windows Vista, follow the suggestion given here.Try to disable the firewall for the moment and check if it helps fix the problem.If the problem is resolved, you may need to contact the manufacturer of the program for the settings that can be changed or if there are other updates for this program.
Note: Firewall can keep the computer worm, pirates etc. Therefore, be sure to turn on the firewall once you are finished with the test.
If it is Windows Firewall, see the article below:
Allow a program to communicate through Windows Firewall
Additional reference on:
-
LRT224 with IPSEC problem - not
Hi, I have the following router Linksys LRT224.
I want to configure the IPSEC tunnel (by user or group).
The OpenVpn works great for users, but it is limited to 5! That's why I want more Tunnel VPN.
Then I configured the IPSEC tunnel and I connect very well either in the Tunnel, the VPN group.
The problem is:
-The client cannot ping of the network
-LRT224 /VPN:
Synthesis of information, always check pending connection to the Tunnel and the Client IPSEC (Schrew) is well served, the newspaper I (c2gips1) [2] IP:660 #61: [created Tunnel] ISAKMP Security Association established
-When I use the VPN group, I see the customer connected, but I couldn't ping from the client to the network router/subnet and vice versa
In advanced routing, I can see the IP address of the connected client...
I also use the doc http://support.linksys.com/en-eu/support/business/LRT224 ...
in the configuration of VPN network schrew, I put:
Auto Config: Disabled and use an existing adapter and current address
Please let me know... help! Thank you
I have done some testing and think it's great. With this feature, you can have a 45 addition VPN tunnels as you mention. I tested with two devices connected at the same time as different IPSec tunnels and the two were able to ping on the Remote LAN devices.
Material used:
- LRT224
- Windows 7 x 64 Desktop
- HP Jet 7 Tablet
- LAPN300
- Galaxy S4
VPN client:
LRT224 VPN Client for the Configuration of the gateway:
Shew VPN Client configuration:
-
Problems to connect via the Cisco VPN client IPSec of for RV180W small business router
Hello
I tried to configure my router Cisco of RV180W as a customer VPN IPSec, but have encountered a problem that I hope someone can help me with. "" I managed to do the work of configuration so that the Cisco's VPN IPSec client authenticates successfully with the XAUTH user, I put on the router, but during the negotiation, the client ends with the following, which appears several times on the router error message: ' Mar 20 Oct 19:41:53 2015 (GMT + 0000): [r1] [IKE] ERROR: local configuration for
> [34360] has no config mode. I've read around the internet and a number of people seem to say that the Cisco VPN Client is not compatible with the router, but the same thing happens to my iPhone VPN client.
Is it possible that this can be implemented? Below, I have attached the full configuration files and the log files. Thank you much in advance.
Router log file (I changed the IP
addresses > respectively as well as references to MAC addresses) Mar 20 Oct 20:03:10 2015 (GMT + 0000): [r1] [IKE] INFO: floating ports NAT - T with counterpart
> [44074]
Mar 20 Oct 20:03:10 2015 (GMT + 0000): [r1] [IKE] WARNING: notification to ignore INITIAL-CONTACT> [44074] because it is admitted only after the phase 1.
Mar 20 Oct 20:03:10 2015 (GMT + 0000): [r1] [IKE] INFO: NAT - D payload does not match for> [4500]
Mar 20 Oct 20:03:10 2015 (GMT + 0000): [r1] [IKE] INFO: NAT - D payload does not match for> [44074]
Mar 20 Oct 20:03:10 2015 (GMT + 0000): [r1] [IKE] INFO: received unknown Vendor ID
Mar 20 Oct 20:03:10 2015 (GMT + 0000): [r1] [IKE] INFO: received Vendor ID: CISCO-UNITY
Mar 20 Oct 20:03:10 2015 (GMT + 0000): [r1] [IKE] INFO: NAT detected: is located behind a device. NAT and alsoPeer is behind a NAT device
Mar 20 Oct 20:03:10 2015 (GMT + 0000): [r1] [IKE] INFO: request sending Xauth for> [44074]
Mar 20 Oct 20:03:10 2015 (GMT + 0000): [r1] [IKE] INFO: ISAKMP Security Association established for> [4500] - > [44074] with spi = >.
Mar 20 Oct 20:03:15 2015 (GMT + 0000): [r1] [IKE] INFO: receives the type of the attribute 'ISAKMP_CFG_REPLY' of> [44074]
Mar 20 Oct 20:03:15 2015 (GMT + 0000): [r1] [IKE] INFO: login successful for the user "myusername".
Mar 20 Oct 20:03:15 2015 (GMT + 0000): [r1] [IKE] INFO: myusername XAuthUser connected from the IP>
Mar 20 Oct 20:03:15 2015 (GMT + 0000): [r1] [IKE] INFO: sending of information Exchange: Notify payload [10381]
Mar 20 Oct 20:03:15 2015 (GMT + 0000): [r1] [IKE] INFO: receives the type of the attribute 'ISAKMP_CFG_REQUEST' of> [44074]
Mar 20 Oct 20:03:15 2015 (GMT + 0000): [r1] [IKE] ERROR: local configuration for> [44074] has no config mode
Mar 20 Oct 20:03:15 2015 (GMT + 0000): [r1] [IKE] ERROR: local configuration for> [44074] has no config mode
Mar 20 Oct 20:03:15 2015 (GMT + 0000): [r1] [IKE] ERROR: local configuration for> [44074] has no config mode
Mar 20 Oct 20:03:15 2015 (GMT + 0000): [r1] [IKE] ERROR: local configuration for> [44074] has no config mode
Mar 20 Oct 20:03:15 2015 (GMT + 0000): [r1] [IKE] WARNING: ignored attribute 5
Mar 20 Oct 20:03:15 2015 (GMT + 0000): [r1] [IKE] ERROR: local configuration for> [44074] has no config mode
Mar 20 Oct 20:03:15 2015 (GMT + 0000): [r1] [IKE] ERROR: local configuration for> [44074] has no config mode
Mar 20 Oct 20:03:15 2015 (GMT + 0000): [r1] [IKE] ERROR: local configuration for> [44074] has no config mode
Mar 20 Oct 20:03:15 2015 (GMT + 0000): [r1] [IKE] ERROR: local configuration for> [44074] has no config mode
Mar 20 Oct 20:03:15 2015 (GMT + 0000): [r1] [IKE] ERROR: local configuration for> [44074] has no config mode
Mar 20 Oct 20:03:15 2015 (GMT + 0000): [r1] [IKE] ERROR: local configuration for> [44074] has no config mode
Mar 20 Oct 20:03:15 2015 (GMT + 0000): [r1] [IKE] WARNING: attribute ignored 28683
Mar 20 Oct 20:03:15 2015 (GMT + 0000): [r1] [IKE] ERROR: local configuration for> [44074] has no mode config
Mar 20 Oct 20:03:15 2015 (GMT + 0000): [r1] [IKE] WARNING: attribute ignored 28684
Mar 20 Oct 20:03:15 2015 (GMT + 0000): [r1] [IKE] ERROR: local configuration for> [44074] has no config mode
Mar 20 Oct 20:03:15 2015 (GMT + 0000): [r1] [IKE] ERROR: local configuration for> [44074] has no mode config
Mar 20 Oct 20:03:15 2015 (GMT + 0000): [r1] [IKE] ERROR: remove the invalid payload with doi:0.
Mar 20 Oct 20:03:15 2015 (GMT + 0000): [r1] [IKE] INFO: purged-Association of ISAKMP security with proto_id = ISAKMP and spi =>.
Mar 20 Oct 20:03:15 2015 (GMT + 0000): [r1] [IKE] INFO: myusername XAuthUser Logged Out of the IP>
Mar 20 Oct 20:03:16 2015 (GMT + 0000): [r1] [IKE] INFO: ISAKMP Security Association deleted for> [4500] - > [44074] with spi = > The router configuration
IKE policy
VPN strategy
Client configuration
Hôte : < router="" ip=""> >
Authentication group name: remote.com
Password authentication of the Group: mysecretpassword
Transport: Enable Transparent Tunneling; IPSec over UDP (NAT/PAT)
Username: myusername
Password: mypassword
Please contact Cisco.
Correct, the RV180 is not compatible with the Cisco VPN Client. The Iphone uses the Cisco VPN Client.
You can use the PPTP on the RV180 server to connect a PPTP Client.
In addition, it RV180 will allow an IPsec connection to third-party customers 3. Greenbow and Shrew Soft are 2 commonly used clients.
-
Hi all. I have a problem with an IPSec tunnel that I am trying to create between two sites. Transformations and pre-shared keys have been configured, and the tunnel came briefly last night. The problem is that I can't ping across the tunnel's private network. I send a ping and it shuts the public rather than be encrypted in the tunnel. Both sides are using rfc1918 address... but those different spaces therefore routing should not be a problem in this regard. I specify interesting traffic for IPSec using one as follows:
IPSEC extended access list
IP 172.16.86.0 allow 0.0.0.255 192.168.0.0 0.0.255.255
refuse an entire ip
and the card encryption uses "corresponds to the address IPSEC."
The ACL IPSEC shows no match. Someone at - it ideas? Thank you.
It seems that the order of the two lines in the access list 111 is back. Because the first line is more general than the second, the other will never get used and you'll always have NAT traffic to your 172.16.86.0 hosts, even if the traffic is destined for an 192.168 address through the VPN. Swap the two lines, and I bet it'll start working.
Note that you must be careful when you make changes to an ACL used for NAT and VPN, since the withdrawal of such a list is equivalent to "license ip any any" cause by you be disconnected and locked out of the router, if you are remotely. It is safer to remove NAT and/or the card encryption interface in question before making changes to a remote router.
HTH - good luck!
Maybe you are looking for
-
I had to reformat and reload my OS. I managed to download and reinstall Yosemite which I had already purchased from the app store, but now I'm stuck trying to find El Capitan. This has been removed from the app store two days when they made availab
-
Obtaining of S.M.A.R.T. error when you try to reinstall El Capitan
Bought end of 2012 Model: iMac 21,5 " Version: 10.11.4 OS El Capitan Recently, I deleted the data on my hard drive in the hope of "reset" of the computer to its factory settings. Clear data wasn't a problem, but the reinstallation of the operating sy
-
My default hard disk is almost full and I plan to update. What is the maximum size that this model could overcome? Very well is 2-3 to? Another question. I replaced my optical drive to a box with a 250 GB SSD HARD drive inside. I installed my new ope
-
Problems with a systems restore
I did a system restore on my laptop Dell Inspiron 9400, but she wiped my Logitech, camera and my HP, printer, model no: 5515. I down loaded the disc that came with the camera, and all was well until I got a blue page bring warning me that a serious e
-
Windows crashes when you watch videos
Windows crashes when I look at the videos and it will start working by itself after a while. Help, please