IPSec VPN connectivity problem
OK, I have the following Setup. An asa 5540 is the vpn server and some cisco vpn site-to-site 2811 routers allows you to connect to it. All cisco routers have the same ip address in their internal interface, so I'm nat'ing to another ip to connect to the vpn. It goes the same for servers behind. So we have
IP nat inside source static 10.0.10.10 10.1.89.10
IP nat inside source static 10.0.10.30 10.1.89.30
OU.10 is the et.30 router server. Vpn comes up, and I cannot pint from my internal network server say Server 10.0.20.10 leash. Server 10.0.20.10 I can ping both the ip nat' ed. However, I can't ping routers 10.0.20.10. Also, I try ping 10.1.89.10 on the router and it pings fine. The other 10.1.89.30 ping does not when 10.0.10.30 does. Help, please. I need the router to communicate with 10.0.20.10 break.
Thanks in advance.
Since you're natting, and you use the same LAN ip subnet in routers (very bad desgin) try using an extended ping of the address on the lan interface nat pool.
Tags: Cisco Security
Similar Questions
-
ASA 5510 IPSEC VPN connection problem
Hello
We have an ASA 5510 (ASA version 8.0) of remote access VPN configured and works most of the time, but there is a problem when you have more than one client that connects to the same office remotely. When the first VPN client is connected to the remote desktop, everything works fine, but when the second client connects to the VPN, it connects fine but do not get any traffice return to customer. I can see under monitor-> statistical VPN-> Sessions-> remote access-> Rx Bytes is 0. Both connections are from the same public IP address of the remote desktop. I changed some settings on NAT - T and a few other things, but without success.
Could someone help me please how to fix this?
Thank you very much.
Make sure that customers use because that probably her you're not. (default value is NAT - T).
Federico.
-
Coming out of the IPSec VPN connection behind Pix535 problem: narrowed down for NAT-Associates
Hello world
Previously, I've seen a similar thread and posted my troubles with the outbound VPN connections inside that thread:
https://supportforums.Cisco.com/message/3688980#3688980
I had the great help but unfortunatedly my problem is a little different and connection problem. Here, I summarize once again our configurations:
hostname pix535 8.0 (4)
all PC here use IP private such as 10.1.0.0/16 by dynamic NAT, we cannot initiate an OUTBOUND IPSec VPN (for example QuickVPN) at our offices, but the reverse (inbound) is very well (we have IPsec working long server /PP2P). I did a few tests of new yesterday which showed that if the PC a static NAT (mapped to a real public IP), outgoing connection VPN is fine; If the same PC has no static NAT (he hides behind the dynamic NAT firewall), outgoing VPN is a no-go (same IP to the same PC), so roughly, I have narrowed down our connection problem VPN is related to NAT, here are a few commands for NAT of our PIX:
interface GigabitEthernet0
Description to cable-modem
nameif outside
security-level 0
IP 70.169.X.X 255.255.255.0
OSPF cost 10
!
interface GigabitEthernet1
Description inside 10/16
nameif inside
security-level 100
IP 10.1.1.254 255.255.0.0
OSPF cost 10
!
!
interface Ethernet2
Vlan30 description
nameif dmz2
security-level 50
IP 30.30.30.30 255.255.255.0
OSPF cost 10
!
permit same-security-traffic inter-interface
permit same-security-traffic intra-interface......
Global interface 10 (external)
Global (dmz2) interface 10
NAT (inside) 0-list of access inside_nat0_outbound
NAT (inside) 10 inside8 255.255.255.0
NAT (inside) 10 Vlan10 255.255.255.0
NAT (inside) 10 vlan50 255.255.255.0
NAT (inside) 10 192.168.0.0 255.255.255.0
NAT (inside) 10 192.168.1.0 255.255.255.0
NAT (inside) 10 192.168.10.0 255.255.255.0
NAT (inside) 10 pix-inside 255.255.0.0Crypto isakmp nat-traversal 3600
-------
Results of packet capture are listed here for the same PC for the same traffic to Server VPN brach, the main difference is UDP 4500 (PC with static NAT has good traffic UDP 4500, does not have the same PC with dynamic NAT):
#1: when the PC uses static NAT, it is good of outgoing VPN:
54 packets captured
1: 15:43:51.112054 10.1.1.82.1608 > 76.196.10.57.443: S 1763806634:1763806634 (0) win 64240
2: 15:43:54.143028 10.1.1.82.1608 > 76.196.10.57.443: S 1763806634:1763806634 (0) win 64240
3: 15:44:00.217273 10.1.1.82.1608 > 76.196.10.57.443: S 1763806634:1763806634 (0) win 64240
4: 15:44:01.724938 10.1.1.82.1609 > 76.196.10.57.60443: S 2904546955:2904546955 (0) win 64240
5: 15:44:01.784642 76.196.10.57.60443 > 10.1.1.82.1609: S 2323205974:2323205974 (0) ack 2904546956 win 5808
6: 15:44:01.784886 10.1.1.82.1609 > 76.196.10.57.60443:. ACK 2323205975 win 64240
7: 15:44:01.785527 10.1.1.82.1609 > 76.196.10.57.60443: P 2904546956:2904547080 (124) ack 2323205975 win 64240
8: 15:44:01.856462 76.196.10.57.60443 > 10.1.1.82.1609:. ACK 2904547080 win 5808
9: 15:44:01.899596 76.196.10.57.60443 > 10.1.1.82.1609: P 2323205975:2323206638 (663) ack 2904547080 win 5808
10: 15:44:02.056897 10.1.1.82.1609 > 76.196.10.57.60443:. ACK 2323206638 win 63577
11: 15:44:03.495030 10.1.1.82.1609 > 76.196.10.57.60443: P 2904547080:2904547278 (198) ack 2323206638 win 63577
12: 15:44:03.667095 76.196.10.57.60443 > 10.1.1.82.1609:. ACK 2904547278 win 6432
13: 15:44:03.740592 76.196.10.57.60443 > 10.1.1.82.1609: P 2323206638:2323206697 (59) ack 2904547278 win 6432
14: 15:44:03.741264 10.1.1.82.1609 > 76.196.10.57.60443: P 2904547278:2904547576 (298) ack 2323206697 win 63518
15: 15:44:03.814029 76.196.10.57.60443 > 10.1.1.82.1609:. ACK 2904547576 win 7504
16: 15:44:06.989008 76.196.10.57.60443 > 10.1.1.82.1609: P 2323206697:2323207075 (378) ack 2904547576 win 7504
17: 15:44:06.990228 76.196.10.57.60443 > 10.1.1.82.1609: 2323207075:2323207075 F (0) ack 2904547576 win 7504
18: 15:44:06.990564 10.1.1.82.1609 > 76.196.10.57.60443:. ACK 2323207076 win 63140
19: 15:44:06.990656 10.1.1.82.1609 > 76.196.10.57.60443: P 2904547576:2904547613 (37) ack 2323207076 win 63140
20: 15:44:06.990854 10.1.1.82.1609 > 76.196.10.57.60443: 2904547613:2904547613 F (0) ack 2323207076 win 63140
21: 15:44:07.049359 76.196.10.57.60443 > 10.1.1.82.1609: R 2323207076:2323207076 (0) win 0
22: 15:44:17.055417 10.1.1.82.500 > 76.196.10.57.500: udp 276
23: 15:44:17.137657 76.196.10.57.500 > 10.1.1.82.500: udp 140
24: 15:44:17.161475 10.1.1.82.500 > 76.196.10.57.500: udp 224
25: 15:44:17.309066 76.196.10.57.500 > 10.1.1.82.500: udp 220
26: 15:44:17.478780 10.1.1.82.4500 > 76.196.10.57.4500: udp 80
27: 15:44:17.550356 76.196.10.57.4500 > 10.1.1.82.4500: 64 udp
28: 15:44:17.595214 10.1.1.82.4500 > 76.196.10.57.4500: udp 304
29: 15:44:17.753470 76.196.10.57.4500 > 10.1.1.82.4500: udp 304
30: 15:44:17.763037 10.1.1.82.4500 > 76.196.10.57.4500: udp 68
31: 15:44:17.763540 10.1.1.82.4500 > 76.196.10.57.4500: udp 56
32: 15:44:18.054516 10.1.1.82.4500 > 76.196.10.57.4500: udp 68
33: 15:44:18.124840 76.196.10.57.4500 > 10.1.1.82.4500: udp 68
34: 15:44:21.835390 10.1.1.82.4500 > 76.196.10.57.4500: udp 72
35: 15:44:21.850831 10.1.1.82.4500 > 76.196.10.57.4500: udp 80
36: 15:44:21.901183 76.196.10.57.4500 > 10.1.1.82.4500: udp 72
37: 15:44:22.063747 10.1.1.82.1610 > 76.196.10.57.60443: S 938188365:938188365 (0) win 64240
38: 15:44:22.104746 76.196.10.57.4500 > 10.1.1.82.4500: udp 80
39: 15:44:22.122277 76.196.10.57.60443 > 10.1.1.82.1610: S 1440820945:1440820945 (0) ack 938188366 win 5808
40: 15:44:22.122536 10.1.1.82.1610 > 76.196.10.57.60443:. ACK 1440820946 win 64240
41: 15:44:22.123269 10.1.1.82.1610 > 76.196.10.57.60443: P 938188366:938188490 (124) ack 1440820946 win 64240
42: 15:44:22.187108 76.196.10.57.60443 > 10.1.1.82.1610:. ACK 938188490 win 5808
43: 15:44:22.400675 76.196.10.57.60443 > 10.1.1.82.1610: P 1440820946:1440821609 (663) ack 938188490 win 5808
44: 15:44:22.474600 10.1.1.82.1610 > 76.196.10.57.60443: P 938188490:938188688 (198) ack 1440821609 win 63577
45: 15:44:22.533648 76.196.10.57.60443 > 10.1.1.82.1610:. ACK 938188688 win 6432
46: 15:44:22.742286 76.196.10.57.60443 > 10.1.1.82.1610: P 1440821609:1440821668 (59) ack 938188688 win 6432
47: 15:44:22.742927 10.1.1.82.1610 > 76.196.10.57.60443: P 938188688:938189002 (314) ack 1440821668 win 63518
48: 15:44:22.802570 76.196.10.57.60443 > 10.1.1.82.1610:. ACK 938189002 win 7504
49: 15:44:25.180486 76.196.10.57.60443 > 10.1.1.82.1610: P 1440821668:1440821934 (266) ack 938189002 win 7504
50: 15:44:25.181753 76.196.10.57.60443 > 10.1.1.82.1610: 1440821934:1440821934 F (0) ack 938189002 win 7504
51: 15:44:25.181997 10.1.1.82.1610 > 76.196.10.57.60443:. ACK 1440821935 win 63252
52: 15:44:25.182134 10.1.1.82.1610 > 76.196.10.57.60443: P 938189002:938189039 (37) ack 1440821935 win 63252
53: 15:44:25.182333 10.1.1.82.1610 > 76.196.10.57.60443: 938189039:938189039 F (0) ack 1440821935 win 63252
54: 15:44:25.241869 76.196.10.57.60443 > 10.1.1.82.1610: R 1440821935:1440821935 (0) win 0#2: same PC with Dynamic NAT, VPN connection fails:
70 packets captured
1: 14:08:31.758261 10.1.1.82.1073 > 76.196.10.57.443: S 820187495:820187495 (0) win 64240
2: 14:08:34.876907 10.1.1.82.1073 > 76.196.10.57.443: S 820187495:820187495 (0) win 64240
3: 14:08:40.746055 10.1.1.82.1073 > 76.196.10.57.443: S 820187495:820187495 (0) win 64240
4: 14:08:42.048627 10.1.1.82.1074 > 76.196.10.57.60443: S 3309127022:3309127022 (0) win 64240
5: 14:08:42.120248 76.196.10.57.60443 > 10.1.1.82.1074: S 1715577781:1715577781 (0) ack 3309127023 win 5808
6: 14:08:42.120568 10.1.1.82.1074 > 76.196.10.57.60443:. ACK 1715577782 win 64240
7: 14:08:42.121102 10.1.1.82.1074 > 76.196.10.57.60443: P 3309127023:3309127147 (124) ack 1715577782 win 64240
8: 14:08:42.183553 76.196.10.57.60443 > 10.1.1.82.1074:. ACK 3309127147 win 5808
9: 14:08:42.232867 76.196.10.57.60443 > 10.1.1.82.1074: P 1715577782:1715578445 (663) ack 3309127147 win 5808
10: 14:08:42.405145 10.1.1.82.1074 > 76.196.10.57.60443:. ACK 1715578445 win 63577
11: 14:08:43.791340 10.1.1.82.1074 > 76.196.10.57.60443: P 3309127147:3309127345 (198) ack 1715578445 win 63577
12: 14:08:43.850450 76.196.10.57.60443 > 10.1.1.82.1074:. ACK 3309127345 win 6432
13: 14:08:44.028196 76.196.10.57.60443 > 10.1.1.82.1074: P 1715578445:1715578504 (59) ack 3309127345 win 6432
14: 14:08:44.058544 10.1.1.82.1074 > 76.196.10.57.60443: P 3309127345:3309127643 (298) ack 1715578504 win 63518
15: 14:08:44.116403 76.196.10.57.60443 > 10.1.1.82.1074:. ACK 3309127643 win 7504
16: 14:08:47.384654 76.196.10.57.60443 > 10.1.1.82.1074: P 1715578504:1715578882 (378) ack 3309127643 win 7504
17: 14:08:47.385417 76.196.10.57.60443 > 10.1.1.82.1074: 1715578882:1715578882 F (0) ack 3309127643 win 7504
18: 14:08:47.394068 10.1.1.82.1074 > 76.196.10.57.60443:. ACK 1715578883 win 63140
19: 14:08:47.394922 10.1.1.82.1074 > 76.196.10.57.60443: P 3309127643:3309127680 (37) ack 1715578883 win 63140
20: 14:08:47.395151 10.1.1.82.1074 > 76.196.10.57.60443: 3309127680:3309127680 F (0) ack 1715578883 win 63140
21: 14:08:47.457633 76.196.10.57.60443 > 10.1.1.82.1074: R 1715578883:1715578883 (0) win 0
22: 14:08:57.258073 10.1.1.82.500 > 76.196.10.57.500: udp 276
23: 14:08:57.336255 76.196.10.57.500 > 10.1.1.82.500: udp 40
24: 14:08:58.334211 10.1.1.82.500 > 76.196.10.57.500: udp 276
25: 14:08:58.412850 76.196.10.57.500 > 10.1.1.82.500: udp 40
26: 14:09:00.333311 10.1.1.82.500 > 76.196.10.57.500: udp 276
27: 14:09:00.410730 76.196.10.57.500 > 10.1.1.82.500: udp 40
28: 14:09:02.412561 10.1.1.82.1075 > 76.196.10.57.443: S 968016865:968016865 (0) win 64240
29: 14:09:04.349164 10.1.1.82.500 > 76.196.10.57.500: udp 276
30: 14:09:04.431648 76.196.10.57.500 > 10.1.1.82.500: udp 40
31: 14:09:05.442710 10.1.1.82.1075 > 76.196.10.57.443: S 968016865:968016865 (0) win 64240
32: 14:09:11.380427 10.1.1.82.1075 > 76.196.10.57.443: S 968016865:968016865 (0) win 64240
33: 14:09:12.349926 10.1.1.82.500 > 76.196.10.57.500: udp 276
34: 14:09:12.421502 10.1.1.82.1076 > 76.196.10.57.60443: S 3856215672:3856215672 (0) win 64240
35: 14:09:12.430794 76.196.10.57.500 > 10.1.1.82.500: udp 40
36: 14:09:12.481832 76.196.10.57.60443 > 10.1.1.82.1076: S 248909856:248909856 (0) ack 3856215673 win 5808
37: 14:09:12.527972 10.1.1.82.1076 > 76.196.10.57.60443:. ACK 248909857 win 64240
38: 14:09:12.529238 10.1.1.82.1076 > 76.196.10.57.60443: P 3856215673:3856215797 (124) ack 248909857 win 64240
39: 14:09:12.608275 76.196.10.57.60443 > 10.1.1.82.1076:. ACK 3856215797 win 5808
40: 14:09:12.658581 76.196.10.57.60443 > 10.1.1.82.1076: P 248909857:248910520 (663) ack 3856215797 win 5808
41: 14:09:12.664531 10.1.1.82.1076 > 76.196.10.57.60443: P 3856215797:3856215995 (198) ack 248910520 win 63577
42: 14:09:12.725533 76.196.10.57.60443 > 10.1.1.82.1076:. ACK 3856215995 win 6432
43: 14:09:12.880813 76.196.10.57.60443 > 10.1.1.82.1076: P 248910520:248910579 (59) ack 3856215995 win 6432
44: 14:09:12.892272 10.1.1.82.1076 > 76.196.10.57.60443: P 3856215995:3856216293 (298) ack 248910579 win 63518
45: 14:09:12.953029 76.196.10.57.60443 > 10.1.1.82.1076:. ACK 3856216293 win 7504
46: 14:09:12.955043 76.196.10.57.60443 > 10.1.1.82.1076: 248910579:248910579 F (0) ack 3856216293 win 7504
47: 14:09:12.955242 10.1.1.82.1076 > 76.196.10.57.60443:. ACK 248910580 win 63518
48: 14:09:12.955516 10.1.1.82.1076 > 76.196.10.57.60443: P 3856216293:3856216330 (37) ack 248910580 win 63518
49: 14:09:12.955730 10.1.1.82.1076 > 76.196.10.57.60443: 3856216330:3856216330 F (0) ack 248910580 win 63518
50: 14:09:13.019743 76.196.10.57.60443 > 10.1.1.82.1076: R 248910580:248910580 (0) win 0
51: 14:09:16.068691 10.1.1.82.500 > 76.196.10.57.500: udp 56
52: 14:09:16.227588 10.1.1.82.1077 > 76.196.10.57.60443: S 3657181617:3657181617 (0) win 64240
53: 14:09:16.283783 76.196.10.57.60443 > 10.1.1.82.1077: S 908773751:908773751 (0) ack 3657181618 win 5808
54: 14:09:16.306823 10.1.1.82.1077 > 76.196.10.57.60443:. ACK 908773752 win 64240
55: 14:09:16.307692 10.1.1.82.1077 > 76.196.10.57.60443: P 3657181618:3657181742 (124) ack 908773752 win 64240
56: 14:09:16.370998 76.196.10.57.60443 > 10.1.1.82.1077:. ACK 3657181742 win 5808
57: 14:09:16.411935 76.196.10.57.60443 > 10.1.1.82.1077: P 908773752:908774415 (663) ack 3657181742 win 5808
58: 14:09:16.417870 10.1.1.82.1077 > 76.196.10.57.60443: P 3657181742:3657181940 (198) ack 908774415 win 63577
59: 14:09:16.509388 76.196.10.57.60443 > 10.1.1.82.1077:. ACK 3657181940 win 6432
60: 14:09:16.708413 76.196.10.57.60443 > 10.1.1.82.1077: P 908774415:908774474 (59) ack 3657181940 win 6432
61: 14:09:16.887100 10.1.1.82.1077 > 76.196.10.57.60443: P 3657181940:3657182254 (314) ack 908774474 win 63518
62: 14:09:16.948193 76.196.10.57.60443 > 10.1.1.82.1077:. ACK 3657182254 win 7504
63: 14:09:19.698465 76.196.10.57.60443 > 10.1.1.82.1077: P 908774474:908774740 (266) ack 3657182254 win 7504
64: 14:09:19.699426 76.196.10.57.60443 > 10.1.1.82.1077: 908774740:908774740 F (0) ack 3657182254 win 7504
65: 14:09:20.060162 10.1.1.82.1077 > 76.196.10.57.60443:. ACK 908774741 win 63252
66: 14:09:20.062191 76.196.10.57.60443 > 10.1.1.82.1077: P 908774474:908774740 (266) ack 3657182254 win 7504
67: 14:09:20.063732 10.1.1.82.1077 > 76.196.10.57.60443:. ACK 908774741 win 63252
68: 14:09:20.063900 10.1.1.82.1077 > 76.196.10.57.60443: P 3657182254:3657182291 (37) ack 908774741 win 63252
69: 14:09:20.064098 10.1.1.82.1077 > 76.196.10.57.60443: 3657182291:3657182291 F (0) ack 908774741 win 63252
70: 14:09:20.127694 76.196.10.57.60443 > 10.1.1.82.1077: R 908774741:908774741 (0) win 0
70 packages shownWe had this problem of connection VPN IPsec from the years (I first thought it is restriction access problem, but it does not work or if I disable all access lists, experience of yesterday for the same restriction of the access-list shows longer than PC is not the cause). All suggestions and tips are greatly appreciated.
Sean
Hi Sean, please remove th lines highlighted in your pix and try and let me know, that these lines are not the default configuration of the PIX.
VPN-udp-class of the class-map
corresponds to the list of access vpn-udp-acl
vpn-udp-policy policy-map
VPN-udp-class
inspect the amp-ipsec
type of policy-card inspect dns migrated_dns_map_1
parameters
message-length maximum 768
Policy-map global_policy
class inspection_default
inspect the migrated_dns_map_1 dns
inspect the ftp
inspect h323 h225
inspect the h323 ras
inspect the http
inspect the netbios
inspect the rsh
inspect the rtsp
inspect the skinny
inspect sqlnet
inspect sunrpc
inspect the tftp
inspect the sip
inspect xdmcp
inspect the pptp
inspect the amp-ipsec
permit same-security-traffic inter-interface
permit same-security-traffic intra-interface
IP verify reverse path to the outside interface
Thank you
Rizwan James
-
Establish a IPsec VPN connection, but remote site can't ping main office
Hi, I set up connection from site to site IPsec VPN between cisco 892 (main site) router and linksys router wrv210 (remote site). My problem is that I can ping network router wrv210 lan of my main office where is cisco 892 router, but I cannot ping the main site of linksys wrv210 lan (my remote site).
My configuration on the cisco 892 router:
type of class-card inspect correspondence sdm-cls-VPNOutsideToInside-1
game group-access 103
type of class-card inspect correspondence sdm-cls-VPNOutsideToInside-3
game group-access 106
type of class-card inspect correspondence sdm-cls-VPNOutsideToInside-2
game group-access 105
type of class-card inspect correspondence sdm-cls-VPNOutsideToInside-5
game group-access 108
type of class-card inspect correspondence sdm-cls-VPNOutsideToInside-4
game group-access 107
type of class-card inspect correspondence sdm-cls-VPNOutsideToInside-7
group-access 110 match
type of class-card inspect correspondence sdm-cls-VPNOutsideToInside-6
game group-access 109
type of class-card inspect correspondence sdm-cls-VPNOutsideToInside-9
game group-access 112
type of class-card inspect correspondence sdm-cls-VPNOutsideToInside-8
game group-access 111
type of class-card inspect entire game SDM_AH
match the name of group-access SDM_AH
type of class-card inspect entire game SDM_ESP
match the name of group-access SDM_ESP
type of class-card inspect entire game SDM_VPN_TRAFFIC
match Protocol isakmp
match Protocol ipsec-msft
corresponds to the SDM_AH class-map
corresponds to the SDM_ESP class-map
type of class-card inspect the correspondence SDM_VPN_PT
game group-access 102
corresponds to the SDM_VPN_TRAFFIC class-map
type of class-card inspect entire game PAC-cls-insp-traffic
match Protocol cuseeme
dns protocol game
ftp protocol game
h323 Protocol game
https protocol game
match icmp Protocol
match the imap Protocol
pop3 Protocol game
netshow Protocol game
Protocol shell game
match Protocol realmedia
match rtsp Protocol
smtp Protocol game
sql-net Protocol game
streamworks Protocol game
tftp Protocol game
vdolive Protocol game
tcp protocol match
udp Protocol game
inspect the class-map match PAC-insp-traffic type
corresponds to the class-map PAC-cls-insp-traffic
type of class-card inspect correspondence sdm-cls-VPNOutsideToInside-10
game group-access 113
type of class-card inspect all sdm-service-ccp-inspect-1 game
http protocol game
https protocol game
type of class-card inspect entire game PAC-cls-icmp-access
match icmp Protocol
tcp protocol match
udp Protocol game
type of class-card inspect correspondence ccp-invalid-src
game group-access 100
type of class-card inspect correspondence ccp-icmp-access
corresponds to the class-ccp-cls-icmp-access card
type of class-card inspect correspondence ccp-Protocol-http
match class-map sdm-service-ccp-inspect-1
!
!
type of policy-card inspect PCB-permits-icmpreply
class type inspect PCB-icmp-access
inspect
class class by default
Pass
type of policy-card inspect sdm-pol-VPNOutsideToInside-1
class type inspect sdm-cls-VPNOutsideToInside-1
inspect
class type inspect sdm-cls-VPNOutsideToInside-2
Pass
class type inspect sdm-cls-VPNOutsideToInside-3
Pass
class type inspect sdm-cls-VPNOutsideToInside-4
Pass
class type inspect sdm-cls-VPNOutsideToInside-5
Pass
class type inspect sdm-cls-VPNOutsideToInside-6
inspect
class type inspect sdm-cls-VPNOutsideToInside-7
Pass
class type inspect sdm-cls-VPNOutsideToInside-8
Pass
class type inspect sdm-cls-VPNOutsideToInside-9
inspect
class type inspect sdm-cls-VPNOutsideToInside-10
Pass
class class by default
drop
type of policy-map inspect PCB - inspect
class type inspect PCB-invalid-src
Drop newspaper
class type inspect PCB-Protocol-http
inspect
class type inspect PCB-insp-traffic
inspect
class class by default
drop
type of policy-card inspect PCB-enabled
class type inspect SDM_VPN_PT
Pass
class class by default
drop
!
security of the area outside the area
safety zone-to-zone
zone-pair security PAC-zp-self-out source destination outside zone auto
type of service-strategy inspect PCB-permits-icmpreply
zone-pair security PAC-zp-in-out source in the area of destination outside the area
type of service-strategy inspect PCB - inspect
source of PAC-zp-out-auto security area outside zone destination auto pair
type of service-strategy inspect PCB-enabled
sdm-zp-VPNOutsideToInside-1 zone-pair security source outside the area of destination in the area
type of service-strategy inspect sdm-pol-VPNOutsideToInside-1
!
!
crypto ISAKMP policy 1
BA 3des
md5 hash
preshared authentication
Group 2
lifetime 28800
ISAKMP crypto key address 83.xx.xx.50 xxxxxxxxxxx
!
!
Crypto ipsec transform-set ESP-3DES esp-3des esp-md5-hmac
!
map SDM_CMAP_1 1 ipsec-isakmp crypto
Description NY_NJ
the value of 83.xx.xx.50 peer
game of transformation-ESP-3DES
match address 101
!
!
!
!
!
interface BRI0
no ip address
no ip redirection
no ip unreachable
no ip proxy-arp
penetration of the IP stream
encapsulation hdlc
Shutdown
Multidrop ISDN endpoint
!
!
interface FastEthernet0
!
!
interface FastEthernet1
!
!
interface FastEthernet2
!
!
interface FastEthernet3
!
!
interface FastEthernet4
!
!
interface FastEthernet5
!
!
FastEthernet6 interface
!
!
interface FastEthernet7
!
!
interface FastEthernet8
no ip address
no ip redirection
no ip unreachable
no ip proxy-arp
penetration of the IP stream
automatic duplex
automatic speed
!
!
interface GigabitEthernet0
Description $ES_WAN$ $FW_OUTSIDE$
IP address 89.xx.xx.4 255.255.255.xx
no ip redirection
no ip unreachable
no ip proxy-arp
penetration of the IP stream
NAT outside IP
IP virtual-reassembly
outside the area of security of Member's area
automatic duplex
automatic speed
map SDM_CMAP_1 crypto
!
!
interface Vlan1
Description $ETH - SW - LAUNCH INTF-INFO-FE 1 to $$$ $ES_LAN$ $FW_INSIDE$
IP 192.168.0.253 255.255.255.0
no ip redirection
no ip unreachable
no ip proxy-arp
penetration of the IP stream
IP nat inside
IP virtual-reassembly
Security members in the box area
IP tcp adjust-mss 1452
!
!
IP forward-Protocol ND
IP http server
local IP http authentication
IP http secure server
IP http timeout policy slowed down 60 life 86400 request 10000
!
!
IP nat inside source overload map route SDM_RMAP_1 interface GigabitEthernet0
IP route 0.0.0.0 0.0.0.0 89.xx.xx.1
!
SDM_AH extended IP access list
Note the category CCP_ACL = 1
allow a whole ahp
SDM_ESP extended IP access list
Note the category CCP_ACL = 1
allow an esp
!
recording of debug trap
Note access-list 1 INSIDE_IF = Vlan1
Note category of access list 1 = 2 CCP_ACL
access-list 1 permit 192.168.0.0 0.0.0.255
Access-list 100 category CCP_ACL = 128 note
access-list 100 permit ip 255.255.255.255 host everything
access-list 100 permit ip 127.0.0.0 0.255.255.255 everything
access-list 100 permit ip 89.xx.xx.0 0.0.0.7 everything
Note access-list 101 category CCP_ACL = 4
Note access-list 101 IPSec rule
access-list 101 permit ip 192.168.0.0 0.0.0.255 192.168.7.0 0.0.0.255
Note access-list 102 CCP_ACL category = 128
access-list 102 permit ip host 83.xx.xx.50 all
Note access-list 103 CCP_ACL category = 0
Note access-list 103 IPSec rule
access-list 103 allow ip 192.168.7.0 0.0.0.255 192.168.0.0 0.0.0.255
Note access-list 104 CCP_ACL category = 2
Note access-list 104 IPSec rule
access-list 104 deny ip 192.168.0.0 0.0.0.255 192.168.7.0 0.0.0.255
access-list 104. allow ip 192.168.0.0 0.0.0.255 any
Note access-list 105 CCP_ACL category = 0
Note access-list 105 IPSec rule
access-list 105 allow ip 192.168.7.0 0.0.0.255 192.168.0.0 0.0.0.255
Note access-list 106 CCP_ACL category = 0
Note access-list 106 IPSec rule
access-list 106 allow ip 192.168.7.0 0.0.0.255 192.168.0.0 0.0.0.255
Note access-list 107 CCP_ACL category = 0
Note access-list 107 IPSec rule
access-list 107 allow ip 192.168.7.0 0.0.0.255 192.168.0.0 0.0.0.255
Note access-list 108 CCP_ACL category = 0
Note access-list 108 IPSec rule
access-list 108 allow ip 192.168.7.0 0.0.0.255 192.168.0.0 0.0.0.255
Note access-list 109 CCP_ACL category = 0
Note access-list 109 IPSec rule
access-list 109 allow ip 192.168.7.0 0.0.0.255 192.168.0.0 0.0.0.255
Note access-list 110 CCP_ACL category = 0
Note access-list 110 IPSec rule
access-list 110 permit ip 192.168.7.0 0.0.0.255 192.168.0.0 0.0.0.255
Note access-list 111 CCP_ACL category = 0
Note access-list 111 IPSec rule
access-list 111 allow ip 192.168.7.0 0.0.0.255 192.168.0.0 0.0.0.255
Note access-list 112 CCP_ACL category = 0
Note access-list 112 IPSec rule
access-list 112 allow ip 192.168.7.0 0.0.0.255 192.168.0.0 0.0.0.255
Note access-list 113 CCP_ACL category = 0
Note access-list 113 IPSec rule
access-list 113 allow ip 192.168.7.0 0.0.0.255 192.168.0.0 0.0.0.255
not run cdp
!
!
!
!
allowed SDM_RMAP_1 1 route map
corresponds to the IP 104
--------------------------------------------------------
I only give your router cisco 892 because there is nothnig much to change on linksys wrv210 router.
Hope someone can help me. See you soon
You can run a "ip inspect log drop-pkt" and see if get you any what FW-DROP session corresponding to the traffic you send Linksys to the main site. Zone based firewall could be blocking traffic initiated from outside to inside.
-
IPSec VPN: connected to the VPN but cannot access resources
Hello
I configured a VPN IPSec on two ISP with IP SLA configured, there is a redundancy on the VPN so that if address main is it connect to the VPN backup.
QUESTIONS
-Connect to the primary address and I can access resources
-backup address to connect but can not access resources for example servers
I want a way to connect to backup and access on my servers resources. Please help look in the config below
configuration below:
interface GigabitEthernet0/0
LAN description
nameif inside
security-level 100
IP 192.168.202.100 255.255.255.0
!
interface GigabitEthernet0/1
Description CONNECTION_TO_DOPC
nameif outside
security-level 0
IP address 2.2.2.2 255.255.255.248
!
interface GigabitEthernet0/2
Description CONNECTION_TO_COBRANET
nameif backup
security-level 0
IP 3.3.3.3 255.255.255.240
!
!
interface Management0/0
Shutdown
No nameif
no level of security
no ip address
management only
!
boot system Disk0: / asa831 - k8.bin
boot system Disk0: / asa707 - k8.bin
passive FTP mode
clock timezone WAT 1
DNS domain-lookup outside
DNS server-group DefaultDNS
Name-Server 4.2.2.2
permit same-security-traffic inter-interface
permit same-security-traffic intra-interface
network of object obj-200
192.168.200.0 subnet 255.255.255.0
Description LAN_200
network of object obj-202
192.168.202.0 subnet 255.255.255.0
Description LAN_202
network of the NETWORK_OBJ_192.168.30.0_25 object
subnet 192.168.30.0 255.255.255.128
network of the RDP_12 object
Home 192.168.202.12
Web server description
service object RDP
source eq 3389 destination eq 3389 tcp service
network obj012 object
Home 192.168.202.12
the Backup-PAT object network
192.168.202.0 subnet 255.255.255.0
NETWORK LAN UBA description
the DM_INLINE_NETWORK_1 object-group network
object-network 192.168.200.0 255.255.255.0
object-network 192.168.202.0 255.255.255.0
the DM_INLINE_NETWORK_2 object-group network
network-object object obj-200
network-object object obj-202
access-list extended INSIDE_OUT allow ip 192.168.200.0 255.255.255.0 any
access-list extended INSIDE_OUT allow ip 192.168.202.0 255.255.255.0 any
OUTSIDE_IN list extended access permit icmp any any idle state
OUTSIDE_IN list extended access permit tcp any object obj012 eq inactive 3389
gbnltunnel_splitTunnelAcl standard access list allow 192.168.200.0 255.255.255.0
standard access list gbnltunnel_splitTunnelAcl allow 192.168.202.0 255.255.255.0
BACKUP_IN list extended access permit icmp any any idle state
access extensive list ip 196.216.144.0 encrypt_acl allow 255.255.255.192 192.168.202.0 255.255.255.0
pager lines 24
Enable logging
asdm of logging of information
Within 1500 MTU
Outside 1500 MTU
backup of MTU 1500
Backup2 MTU 1500
local pool GBNLVPNPOOL 192.168.30.0 - 192.168.30.100 255.255.255.0 IP mask
no failover
ICMP unreachable rate-limit 1 burst-size 1
ICMP allow any backup
ASDM image disk0: / asdm-645 - 206.bin
don't allow no asdm history
ARP timeout 14400
NAT (inside, outside) static static source NETWORK_OBJ_192.168.30.0_25 destination DM_INLINE_NETWORK_1 DM_INLINE_NETWORK_1 NETWORK_OBJ_192.168.30.0_25
NAT (inside, outside) static source DM_INLINE_NETWORK_2 DM_INLINE_NETWORK_2 NETWORK_OBJ_192.168.30.0_25 NETWORK_OBJ_192.168.30.0_25 non-proxy-arp-search of route static destination
!
network of object obj-200
NAT dynamic interface (indoor, outdoor)
network of object obj-202
dynamic NAT (all, outside) interface
network obj012 object
NAT (inside, outside) interface static service tcp 3389 3389
the Backup-PAT object network
dynamic NAT interface (inside, backup)
!
NAT source auto after (indoor, outdoor) dynamic one interface
Access-group interface inside INSIDE_OUT
Access-group OUTSIDE_IN in interface outside
Access-group BACKUP_IN in the backup of the interface
Route outside 0.0.0.0 0.0.0.0 2.2.2.2 1 followed by 100
Backup route 0.0.0.0 0.0.0.0 3.3.3.3 254
Timeout xlate 03:00
Pat-xlate timeout 0:00:30
Timeout conn 01:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
Sunrpc timeout 0:10:00 h323 0:05:00 h225 mgcp from 01:00 0:05:00 mgcp-pat 0:05:00
Sip timeout 0:30:00 sip_media 0:02:00 prompt Protocol sip-0: 03:00 sip - disconnect 0:02:00
Timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
Floating conn timeout 0:00:00
dynamic-access-policy-registration DfltAccessPolicy
WebVPN
value of the URL-list GBNL-SERVERS
identity of the user by default-domain LOCAL
the ssh LOCAL console AAA authentication
AAA authentication http LOCAL console
AAA authentication enable LOCAL console
http server enable 441
http 192.168.200.0 255.255.255.0 inside
http 192.168.202.0 255.255.255.0 inside
http 192.168.2.0 255.255.255.0 inside
http 192.168.30.0 255.255.255.0 inside
http 0.0.0.0 0.0.0.0 outdoors
http 0.0.0.0 0.0.0.0 backup
No snmp server location
No snmp Server contact
Server enable SNMP traps snmp authentication linkup, linkdown warmstart of cold start
ALS 10 monitor
type echo protocol ipIcmpEcho 31.13.72.1 interface outside
NUM-package of 5
Timeout 3000
frequency 5
Annex monitor SLA 10 life never start-time now
Crypto ipsec transform-set ikev1 ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
Crypto ipsec transform-set ikev1 ESP-DES-SHA esp - esp-sha-hmac
Crypto ipsec transform-set ikev1 SHA-ESP-3DES esp-3des esp-sha-hmac
Crypto ipsec transform-set ikev1 esp ESP-DES-MD5-esp-md5-hmac
Crypto ipsec transform-set ikev1 ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
Crypto ipsec transform-set ikev1 ESP-3DES-MD5-esp-3des esp-md5-hmac
Crypto ipsec transform-set ikev1 ESP-AES-256-SHA esp-aes-256 esp-sha-hmac
Crypto ipsec transform-set ikev1 ESP-AES-128-SHA aes - esp esp-sha-hmac
Crypto ipsec transform-set ikev1 ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
Crypto ipsec transform-set ikev1 ESP-AES-128-MD5-esp - aes esp-md5-hmac
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 pfs Group1 set
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 define ikev1 transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA MD5-ESP-3DES ESP-DES-SHA ESP-DES-MD5
card crypto IPSec_map 10 corresponds to the address encrypt_acl
card crypto IPSec_map 10 set peer 196.216.144.1
card crypto IPSec_map 65535-isakmp dynamic ipsec SYSTEM_DEFAULT_CRYPTO_MAP
outside_map card crypto 65535-isakmp dynamic ipsec SYSTEM_DEFAULT_CRYPTO_MAP
inside_map card crypto 65535-isakmp dynamic ipsec SYSTEM_DEFAULT_CRYPTO_MAP
inside crypto map inside_map interface
ipsec_map card crypto 65535-isakmp dynamic ipsec SYSTEM_DEFAULT_CRYPTO_MAP
ipsec_map interface card crypto outside
gbnltunnel card crypto 65535-isakmp dynamic ipsec SYSTEM_DEFAULT_CRYPTO_MAP
backup of crypto gbnltunnel interface card
Crypto ca trustpoint ASDM_TrustPoint0
Terminal registration
name of the object CN = GBNLVPN.greatbrandsng.com, O = GBNL, C = ng
Configure CRL
Crypto ikev1 allow inside
Crypto ikev1 allow outside
Crypto ikev1 enable backup
IKEv1 crypto policy 10
authentication crack
aes-256 encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 20
authentication rsa - sig
aes-256 encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 30
preshared authentication
aes-256 encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 40
authentication crack
aes-192 encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 50
authentication rsa - sig
aes-192 encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 60
preshared authentication
aes-192 encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 70
authentication crack
aes encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 80
authentication rsa - sig
aes encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 90
preshared authentication
aes encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 100
authentication crack
3des encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 110
authentication rsa - sig
3des encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 120
preshared authentication
3des encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 130
authentication crack
the Encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 140
authentication rsa - sig
the Encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 150
preshared authentication
the Encryption
sha hash
Group 2
life 86400
enable client-implementation to date
!
track 10 rtr 100 accessibility
!
Track 100 rtr 10 accessibility
Telnet 192.168.200.0 255.255.255.0 inside
Telnet 192.168.202.0 255.255.255.0 inside
Telnet timeout 5
SSH 192.168.202.0 255.255.255.0 inside
SSH 192.168.200.0 255.255.255.0 inside
SSH 0.0.0.0 0.0.0.0 inside
SSH 0.0.0.0 0.0.0.0 outdoors
SSH 0.0.0.0 0.0.0.0 backup
SSH timeout 30
SSH group dh-Group1-sha1 key exchange
Console timeout 0
management-access inside
a basic threat threat detection
threat detection statistics
a statistical threat detection tcp-interception rate-interval 30 burst-400-rate average rate 200
WebVPN
allow outside
enable backup
activate backup2
internal gbnltunnel group policy
attributes of the strategy of group gbnltunnel
Ikev1 VPN-tunnel-Protocol
Split-tunnel-policy tunnelspecified
greatbrandsng.com value by default-field
Group Policy 'Group 2' internal
type of remote access service
type tunnel-group gbnltunnel remote access
tunnel-group gbnltunnel General-attributes
address GBNLVPNPOOL pool
Group Policy - by default-gbnltunnel
gbnltunnel group of tunnel ipsec-attributes
IKEv1 pre-shared-key *.
type tunnel-group GBNLSSL remote access
type tunnel-group GBNL_WEBVPN remote access
attributes global-tunnel-group GBNL_WEBVPN
Group Policy - by default-gbnltunnel
tunnel-group 196.216.144.1 type ipsec-l2l
IPSec-attributes tunnel-group 196.216.144.1
IKEv1 pre-shared-key *.
!
class-map inspection_default
match default-inspection-traffic
!
!
type of policy-card inspect dns preset_dns_map
parameters
maximum message length automatic of customer
message-length maximum 512
Policy-map global_policy
class inspection_default
inspect the preset_dns_map dns
inspect the ftp
inspect h323 h225
inspect the h323 ras
inspect the rsh
inspect the rtsp
inspect esmtp
inspect sqlnet
inspect the skinny
inspect sunrpc
inspect xdmcp
inspect the sip
inspect the netbios
inspect the tftp
Review the ip options
inspect the icmp
!
global service-policy global_policy
context of prompt hostname
no remote anonymous reporting call
HPM topN enable
Cryptochecksum:6004bf457c9c0bc1babbdbf1cd8aeba5
: end
When you say that "the external interface is downwards using failover techniques" you mean this failover occurred because the ASA is no longer able to reach the 31.13.72.1? Not that the actual interface is broken?
If this is the case, then the NATing is your problem. Since you're using the same VPN pool for VPN connections the ASA cannot distinguish between the two streams of traffic if the external interface is still in place. The SLA tracking only removes a route in the routing table, but does not affect what happens in the NAT process.
try to change the NAT statement follows him and the test (don't forget to remove the other statements to exempt of NAT for this traffic during the test):
NAT (inside,any) static static source NETWORK_OBJ_192.168.30.0_25 destination DM_INLINE_NETWORK_1 DM_INLINE_NETWORK_1 NETWORK_OBJ_192.168.30.0_25
If this does not work, I would either turn off the external interface when a failover occurs, or create a second connection profile that contains a separate mass of IP for the VPN connection and ask users to connect using this profile when a failover takes place. Don't forget to create Nat exempt instructions for this traffic also.
--
Please note all useful posts
-
IPSec VPN connectivity between multiple subnet for the unique subnet
Hello
I have headquarters where several VLANs are running and branch has a subnet.following is subnet details
Head office subnets
192.168.0.0
192.168.101.0
192.168.50.0
192.168.10.0
192.168.20.0
192.168.30.0 all are 24
branch
192.168.1.0/24
Headquarters I have PIX and branch, I have cisco router 2600. I want my subnet all headquarters access to my office of general management of the LAN
I want to create an ipsec vpn, my question is that I can combine several subnets of headquarters in a subnet because I want ot get rid of several ACL entries
Hello
Well, if we look at the site of the Directorate. He has only the single network and even with the destination network that overlap, it shouldn't be a problem. If a host on the network of agencies needs to connect to another host to local subnets will connect directly to him and the traffic flow through the router.
I don't know if there should be no problem on the PIX side or the other.
But to be honest, it's a very small amount of networks, and I don't see a particular reason, that I would not configure each network specifically, even if it should procude a few lines more to the ACL. Personally, I prefer to be as specific as possible in configurations to avoid any problems.
-Jouni
-
VPN connection problem: keep connection
I'm having a problem with the maintenance of VPN connection. I connect okay but the line VPN disconnects after about 2 minutes each time. I use XP Professional V2002, Service Pack 3. I have disabled the WIndows firewall, as I have F-Secure software suite with its active firewall. I connect laptop wireless via a Belkin router. I had no problem for months up until August when suddenly this problem appeared. I have disabled firewall F-secure, but that did not help. I also disabled the firewall on the router, but again without success. Can you please help?
Hi Rashmis,
Thanks for visiting the site of the community of Microsoft Windows XP. The question you have posted is related to VPN issues and would be better suited to the Technet community. Please visit the link below to find a community that will provide the support you want. http://social.technet.Microsoft.com/forums/en/categories/
Shawn - Support Engineer - MCP, MCDST
Microsoft Answers Support Engineer
Visit our Microsoft answers feedback Forum and let us know what you think -
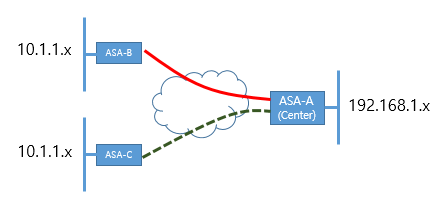
Currently, ASA - A (Center) and B has connected by VPN IPSec.
I would like a VPN establsh A ASA and ASA-C both.
But unfortunately, within the network range has same range B-ASA and ASA-C both. (10.1.1.x)
In this case, how can I connect IPSec VPN to ASA-B and C - ASA ASA - A at a time?
Thank you
Hello
You can go with policy subnet Nating ASA-C on another subnet on ASA - C (ex: 10.1.10.x) and use this as your ACL subnet subnet. It should work. Please search online for examples of configuration.
HTH
MS
-
ASA 5505 ASDM VPN connection problem
Hello
We are running a version of firewall ASA 5505 8.4 (4) 1. The ASDM version is 6.4 (9).
The problem is when the creation of remote access VPN connection, it works fine for about 2-3 days.
After that, the VPN client cannot connect more and gives the error code 789.
In this case, the VPN clients are clients of Windows 7 from different remote networks with the same problem scenario.
Windows 8.1 clients cannot connect at all and show the same error code...
All connections go through the keys defaultragroup and preshare match on both sides.
When the user to connect attemps I receive the following text in the log of the ASDM:
6 April 10, 2015 10:52:39 group = DefaultL2LGroup, IP = 5.240.31.116, P1 retransmit msg sent to the WSF MM5 April 10, 2015 10:52:39 group = DefaultL2LGroup, IP = 5.240.31.116, in double Phase 1 detected package. Retransmit the last packet.5 April 10, 2015 10:53:03 IP = 5.240.31.116, encrypted packet received with any HIS correspondent, dropWhen I implemented the remote login through ASDM I followed the instructions according to the following link:The steps were a little different, but almost the same, given that these instructions show an old versionI'm interested in trying the steps according to this link but not sure this will help me solve the problem id:Any help would be appreciated!Thank youHello
If you use local authentication (user name and password on the SAA), so why you would need this threshold?
tunnel-group DefaultRAGroup ppp-attributes
No chap authentication
ms-chap-v2 authentication
!Remove it and try.
-
ASA 5505 IPSEC VPN connected but cannot access the local network
ASA: 8.2.5
ASDM: 6.4.5
LAN: 10.1.0.0/22
Pool VPN: 172.16.10.0/24
Hi, we purcahsed a new ASA 5505 and try to configure IPSEC VPN via ASDM; I simply run the wizards, installation vpnpool, split tunnelling, etc.
I can connect to the ASA using the cisco VPN client and internet works fine on the local PC, but it can not access the local network (can not impossible. ping remote desktop). I tried the same thing on our Production ASA(those have both Remote VPN and Site-to-site VPN working), the new profile, I created worked very well.
Here is my setup, wrong set up anything?
ASA Version 8.2 (5)
!
hostname asatest
domain XXX.com
activate 8Fw1QFqthX2n4uD3 encrypted password
g9NiG6oUPjkYrHNt encrypted passwd
names of
!
interface Ethernet0/0
switchport access vlan 2
!
interface Ethernet0/1
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
!
interface Ethernet0/7
!
interface Vlan1
nameif inside
security-level 100
IP 10.1.1.253 255.255.252.0
!
interface Vlan2
nameif outside
security-level 0
address IP XXX.XXX.XXX.XXX 255.255.255.240
!
passive FTP mode
clock timezone PST - 8
clock summer-time recurring PDT
DNS server-group DefaultDNS
domain vff.com
vpntest_splitTunnelAcl list standard access allowed 10.1.0.0 255.255.252.0
access extensive list ip 10.1.0.0 inside_nat0_outbound allow 255.255.252.0 172.16.10.0 255.255.255.0
pager lines 24
Enable logging
timestamp of the record
logging trap warnings
asdm of logging of information
logging - the id of the device hostname
host of logging inside the 10.1.1.230
Within 1500 MTU
Outside 1500 MTU
IP local pool 172.16.10.1 - 172.16.10.254 mask 255.255.255.0 vpnpool
no failover
ICMP unreachable rate-limit 1 burst-size 1
don't allow no asdm history
ARP timeout 14400
Global 1 interface (outside)
NAT (inside) 0-list of access inside_nat0_outbound
NAT (inside) 1 0.0.0.0 0.0.0.0
Route outside 0.0.0.0 0.0.0.0 XXX.XXX.XXX.XXX 1
Timeout xlate 03:00
Timeout conn 01:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
Sunrpc timeout 0:10:00 h323 0:05:00 h225 mgcp from 01:00 0:05:00 mgcp-pat 0:05:00
Sip timeout 0:30:00 sip_media 0:02:00 prompt Protocol sip-0: 03:00 sip - disconnect 0:02:00
Timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
Floating conn timeout 0:00:00
dynamic-access-policy-registration DfltAccessPolicy
AAA-server protocol nt AD
AAA-server host 10.1.1.108 AD (inside)
NT-auth-domain controller 10.1.1.108
Enable http server
http 10.1.0.0 255.255.252.0 inside
No snmp server location
No snmp Server contact
Server enable SNMP traps snmp authentication linkup, linkdown cold start
Crypto ipsec transform-set esp-SHA-ESP-3DES-3des esp-sha-hmac
Crypto ipsec transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
Crypto ipsec transform-set ESP-DES-SHA esp - esp-sha-hmac
Crypto ipsec transform-set ESP-DES-MD5 esp - esp-md5-hmac
Crypto ipsec transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
Crypto ipsec transform-set ESP-3DES-MD5-esp-3des esp-md5-hmac
Crypto ipsec transform-set ESP-AES-256-SHA 256 - aes - esp esp-sha-hmac
Crypto ipsec transform-set ESP-AES-128-SHA aes - esp esp-sha-hmac
Crypto ipsec transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
Crypto ipsec transform-set ESP-AES-128-MD5-esp - aes esp-md5-hmac
life crypto ipsec security association seconds 28800
Crypto ipsec kilobytes of life - safety 4608000 association
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 pfs Group1 set
Crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 value transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA MD5-ESP-3DES ESP-DES-SHA ESP-DES-MD5
outside_map card crypto 65535-isakmp dynamic ipsec SYSTEM_DEFAULT_CRYPTO_MAP
outside_map interface card crypto outside
crypto ISAKMP allow outside
crypto ISAKMP policy 10
preshared authentication
3des encryption
sha hash
Group 2
life 86400
Telnet timeout 5
SSH 10.1.0.0 255.255.252.0 inside
SSH timeout 20
Console timeout 0
dhcpd outside auto_config
!
a basic threat threat detection
Statistics-list of access threat detection
no statistical threat detection tcp-interception
WebVPN
internal group vpntest strategy
Group vpntest policy attributes
value of 10.1.1.108 WINS server
Server DNS 10.1.1.108 value
Protocol-tunnel-VPN IPSec l2tp ipsec
disable the password-storage
disable the IP-comp
Re-xauth disable
disable the PFS
IPSec-udp disable
IPSec-udp-port 10000
Split-tunnel-policy tunnelspecified
value of Split-tunnel-network-list vpntest_splitTunnelAcl
value by default-domain XXX.com
disable the split-tunnel-all dns
Dungeon-client-config backup servers
the address value vpnpool pools
admin WeiepwREwT66BhE9 encrypted privilege 15 password username
username user5 encrypted password privilege 5 yIWniWfceAUz1sUb
the encrypted password privilege 3 umNHhJnO7McrLxNQ util_3 username
tunnel-group vpntest type remote access
tunnel-group vpntest General attributes
address vpnpool pool
authentication-server-group AD
authentication-server-group (inside) AD
Group Policy - by default-vpntest
band-Kingdom
vpntest group tunnel ipsec-attributes
pre-shared-key BEKey123456
NOCHECK Peer-id-validate
!
!
privilege level 3 mode exec cmd command perfmon
privilege level 3 mode exec cmd ping command
mode privileged exec command cmd level 3
logging of the privilege level 3 mode exec cmd commands
privilege level 3 exec command failover mode cmd
privilege level 3 mode exec command packet cmd - draw
privilege show import at the level 5 exec mode command
privilege level 5 see fashion exec running-config command
order of privilege show level 3 exec mode reload
privilege level 3 exec mode control fashion show
privilege see the level 3 exec firewall command mode
privilege see the level 3 exec mode command ASP.
processor mode privileged exec command to see the level 3
privilege command shell see the level 3 exec mode
privilege show level 3 exec command clock mode
privilege exec mode level 3 dns-hosts command show
privilege see the level 3 exec command access-list mode
logging of orders privilege see the level 3 exec mode
privilege, level 3 see the exec command mode vlan
privilege show level 3 exec command ip mode
privilege, level 3 see fashion exec command ipv6
privilege, level 3 see the exec command failover mode
privilege, level 3 see fashion exec command asdm
exec mode privilege see the level 3 command arp
command routing privilege see the level 3 exec mode
privilege, level 3 see fashion exec command ospf
privilege, level 3 see the exec command in aaa-server mode
AAA mode privileged exec command to see the level 3
privilege, level 3 see fashion exec command eigrp
privilege see the level 3 exec mode command crypto
privilege, level 3 see fashion exec command vpn-sessiondb
privilege level 3 exec mode command ssh show
privilege, level 3 see fashion exec command dhcpd
privilege, level 3 see the vpnclient command exec mode
privilege, level 3 see fashion exec command vpn
privilege level see the 3 blocks from exec mode command
privilege, level 3 see fashion exec command wccp
privilege see the level 3 exec command mode dynamic filters
privilege, level 3 see the exec command in webvpn mode
privilege control module see the level 3 exec mode
privilege, level 3 see fashion exec command uauth
privilege see the level 3 exec command compression mode
level 3 for the show privilege mode configure the command interface
level 3 for the show privilege mode set clock command
level 3 for the show privilege mode configure the access-list command
level 3 for the show privilege mode set up the registration of the order
level 3 for the show privilege mode configure ip command
level 3 for the show privilege mode configure command failover
level 5 mode see the privilege set up command asdm
level 3 for the show privilege mode configure arp command
level 3 for the show privilege mode configure the command routing
level 3 for the show privilege mode configure aaa-order server
level mode 3 privilege see the command configure aaa
level 3 for the show privilege mode configure command crypto
level 3 for the show privilege mode configure ssh command
level 3 for the show privilege mode configure command dhcpd
level 5 mode see the privilege set privilege to command
privilege level clear 3 mode exec command dns host
logging of the privilege clear level 3 exec mode commands
clear level 3 arp command mode privileged exec
AAA-server of privilege clear level 3 exec mode command
privilege clear level 3 exec mode command crypto
privilege clear level 3 exec command mode dynamic filters
level 3 for the privilege cmd mode configure command failover
clear level 3 privilege mode set the logging of command
privilege mode clear level 3 Configure arp command
clear level 3 privilege mode configure command crypto
clear level 3 privilege mode configure aaa-order server
context of prompt hostname
no remote anonymous reporting call
Cryptochecksum:447bbbc60fc01e9f83b32b1e0304c6b4
: end
Captures we can see packets going from the pool to the internal LAN, but we do not reply back packages.
The routing must be such that for 172.16.10.0/24 packages should reach the inside interface of the ASA.
On client machines or your internal LAN switch, you need to add route for 172.16.10.0/24 pointing to the inside interface of the ASA.
-
I don't know what is happening or what Miss me...
I set up a vpn connection to my remote offices with a 5505. My main office, I have a 5510.
My remote offices, I can PING my main Office Server. However, when I go to set up a VPN through windows network sharing Center I can't get the connection to connect...
Am I doing something wrong or what step am I missing?
Thank you!!
Can you try to add this:
permit same-security-traffic inter-interface
permit same-security-traffic intra-interfaceI'd put it on two unless you have a reason not to. If there is no love after that we will break down the pppoe and vpn configuration.
Matt
-
ASA 5505 ipsec vpn connection fails
Hello
I'm trying to configure a Cisco ASA 5505 for Remote Clients.
I use the ASDM interface and used assistants start and ipsec for my setup, but im hit a stumbling block.
To last make it work 2 days I have tried a number of configuration changes to try to make this work but didn't, so I did a factory reset and passed by the assistants, once again, I have a clean Setup that I hope someone can help me.
Currently I have an IP public static 81.137.x.x and I use a Netgear ADSL router, which transfers (UDP 500) VPN traffic to 192.168.171.35 (port wan on the ASA 5505).
The Cisco ASA has a default address of 192.168.1.1
I use the Cisco Client 5.0.06.0160.
I have configured the client to use authentication group with the same credentials as configuration through the wizard and im using Transparent Tunneling IPSec over UDP.
I have attached 2 documents
running_config.txt - what is shows the current configuration of ASA
Journal - View.txt - display of error messages displayed in the real-time log viewer when I try to connect from the remote client.
I'm not sure if I need to do on the other that additional configurations for my setup simply run the wizards.
Any help would be appreciated.
Thank you
Hello Philippe,
According to the lines in the journal, there is a problem of routing for ip vpn applicant address. ASA couldn't find the definition of route suitable for the return traffic. Add a default route to unknown destinations could solve this problem. As I see you are using modem netgear as a default gateway for your ASA. I write example of command line for this purpose.
Route outside 0.0.0.0 0.0.0.0 NetGear_LAN_IP_Address 1
Ufuk Güler
-
Ipad Cisco ipsec VPN connects but not access to the local network
Hi guys,.
I am trying to connect our ipads to vpn to access network resources. IPSec cisco ipad connects but not lan access and cannot ping anything not even not the interfaces of the router.
If I configure the vpn from cisco on a laptop, it works perfectly, I can ping all and can access resources on the local network if my guess is that the traffic is not going in the tunnel vpn between ipad and desktop.
Cisco 877.
My config is attached.
Any ideas?
Thank you
Build-in iPad-client is not useful to your configuration.
You have three options:
(1) remove the ACL of your vpn group. Without split tunneling client will work.
2) migrate legacy config crypto-map style. Here, you can use split tunneling
3) migrate AnyConnect.
The root of the problem is that the iPad Gets the split tunneling-information. But instead of control with routing traffic should pass through the window / the tunnel and which traffic is allowed without the VPN of the iPad tries to build a set of SAs for each line in your split-tunnel-ACL. But with the model-virtual, SA only is allowed.
-
Hello
We have a server to remote client, on which we need to connect via VPN. My VPN is able to connect. But any application that needs to connect via VPN does not work. I also can't ping on remote servers. While for others its works very well. I can't understand the problem, I tried to reinstall the VPN client.
I am using windows XP pro and the client VPN CISCO 4.0.3.
Hello
Your Windows XP question is more complex than what is generally answered in the Microsoft Answers forums. It is better suited for the IT Pro TechNet public. Please post your question in the forum TechNet for assistance:
TechNet Windows XP Service Pack 3 (SP3)
Hope the helps of information.
-
Client VPN connectivity problems
I use the cisco VPN client to connect to our network, located behind a 515E. The client is authenticated and gets an ip address but cannot ping or connect with one of the hosts. The connection is to a network of customers that is also behind a 515E. I have successfully connected using the same policy to other places and have had no problem. What confuses me, is that we have used to have a Netscreen firewall before and he had a netscreen vpn client which connected since their network with a problem. Is that something they need for their firewall so that we can get through the traffic?
Try to turn on NAT - T on your pix, by setting up:
ISAKMP nat-traversal 20
and configure the client vpn accordingly:
http://www.Cisco.com/warp/public/471/cvpn_3k_nat.html#conf_client
I think these discussions are useful:
Maybe you are looking for
-
Warranty for Alu 2 500 GB StorE
Hello Never needing support for my Toshiba products before I'm lost trying to find how can I RMA my drive of 500 GB Toshiba Store Alu 2, who died on me.Also, I don't have the drive and the cable on the left, I put the box in a cell he came in origina
-
Hello. I wanted to run Visual Studio 2010 Express edition on my Vista Home Premium, but ran into way too many problems. First of all, download have not installed because of a problem with the installation of .NET framework v4.0. Then I tried to VS 20
-
I have a Windows Server 2008 R2 domain and a Windows XP Pro workstation that has been attached to the domain and then disconnected. I am trying to create a VBS script to add a domain user to the local Administrators group. I log on my computer as a l
-
Still for a long time, I can't install the update of security KB2416447 on my Windows XP.
Still for a long time, I can't install the update of security KB2416447. But because Microsoft NET Framework 1.1 SP1 is missing on my PC, so I try to install Windows XPSP1a express but then I see the error message on the language is different. So I s
-
Failure of button contextual properties
"When I right click on an icon or shortcut to display the properties, the message"windows Explorer has failed and needs to restart. Using the results of keyboard shortcut in the same failure. All solutions?