NAT-control over ASA 5540 v8.3.2?
Is there an equivalent command in 8.3.2 disable NAT; That is to say. no control NAT?
I think it was in v7.2 but can't find in in 8.3.2. I use this stricktly 5540 for a VPN IPSec lan lan 2 head of tunnel and do not NAT at all. If I disable NAT, I won't have to deal with the obnoxious ACL nat_0 which grows and grows and grows. Is this possible in 8.3.2?
Hello
The control of nat command has been removed in version 8.3
The command to control NAT is discouraged. In order to maintain the requirement that all traffic from a security interface than a security interface lower translate, a NAT rule will be inserted at the end of article 2 for each interface ban all remaining traffic. Nat-control command was used for NAT configurations defined with older versions of the Adaptive security appliance. The best practice is to use access rules to control access rather than rely on the absence of a NAT rule to prevent traffic through the Adaptive security device.
Click on the following link for nat-control migration information:
http://www.Cisco.com/en/us/partner/docs/security/ASA/asa83/upgrading/migrating.html#wp60212
Federico.
Tags: Cisco Security
Similar Questions
-
ASA - 5540 used for IPSec VPN only - I can do away with Nat 0?
I'll use an ASA 5540 as our head of VPN endpoint only - and not as a firewall.
Also, we have a class for our company internal address space routable B address, so we don't need NAT. I would like to disable the function NAT 0 if I can so I always add NAT 0 to ensure that the 5540 does not NAT.
Y at - it an easy way to disable the need using NAT 0?
Are there any of the draw to do that?
You can disable the use of nat 0 disabling the nat control.
To achieve this, go to the global configuration mode and use this command:
no nat control
To check whether you have it turned on, you can check it with:
SH run nat-control
See you soon!
-Butterfly
-
VPN Cisco ASA 5540 L2L - one-way traffic only for the pair to a network
Hello
I'm a little confused as to which is the problem. This is the premise for the problem I have face.
One of our big clients has a Cisco ASA5540 (8.2 (2)) failover (active / standby). Early last year, we have configured a VPN from Lan to Lan to a 3rd party site (a device of control point on their end). He worked until early this week when suddenly the connection problems.
Only 1 of the 3 networks the / guests can access a remote network on the other side. 2 others have suddenly stopped working. We do not know of any change on our side and the remote end also insists that their end configurations are correct (and what information they sent me it seems to be correct)
So essentially the encryption field is configured as follows:
access-list
line 1 permit extended ip 10.238.57.21 host 10.82.0.202 (hitcnt = 2)
access-listline 2 extended permit ip 10.207.0.0 255.255.0.0 10.82.0.200 255.255.255.252 (hitcnt = 198)
access-listline 3 extended permit ip 10.231.191.0 255.255.255.0 10.82.0.200 255.255.255.252 (hitcnt = 173) Free NAT has been configured as follows (names modified interfaces):
NAT (interface1) 0-list of access to the INTERIOR-VPN-SHEEP
the INTERIOR-VPN-SHEEP line 1 permit access list extended ip 10.231.191.0 255.255.255.0 10.82.0.200 255.255.255.252
permit for Access-list SHEEP-VPN-INSIDE line lengthened 2 ip host 10.238.57.21 10.82.0.202NAT (interface2) 0-list of access VPN-SHEEP
VPN-SHEEP line 1 permit access list extended ip 10.207.0.0 255.255.0.0 10.82.0.200 255.255.255.252
After the problem started only 10.207.0.0/16 network connections worked for the site remote 10.82.0.200/30. All other connections do not work.
There has been no change made on our side and on the side remote also insists there has been no change. I also checked how long the ASAs have been upward and how long the same device has been active in the failover. Both have been at the same time (about a year)
The main problem is that users of the 10.231.191.0/24 cant access remote network network. However, the remote user can initiate and implement the VPN on their side but usually get any return traffic. Ive also checked that the routes are configured correctly in the routers in core for the return of their connections traffic should go back to the firewall.
Also used of "packet - trace" event raising the VPN tunnel (even if it passes the phases VPN). For my understanding "packet - trace" alone with the IP source and destination addresses must activate the VPN connection (even if it generates no traffic to the current tunnel).
This is printing to the following command: "packet - trace entry interface1 tcp 10.231.191.100 1025 10.82.0.203 80.
Phase: 1
Type: ACCESS-LIST
Subtype:
Result: ALLOW
Config:
Implicit rule
Additional information:
MAC access listPhase: 2
Type: FLOW-SEARCH
Subtype:
Result: ALLOW
Config:
Additional information:
Not found no corresponding stream, creating a new streamPhase: 3
Type:-ROUTE SEARCH
Subtype: entry
Result: ALLOW
Config:
Additional information:
in 10.82.0.200 255.255.255.252 outsidePhase: 4
Type: ACCESS-LIST
Subtype: Journal
Result: ALLOW
Config:Access-group interface interface1
access-list extendedallow ip 10.231.191.0 255.255.255.0 10.82.0.200 255.255.255.252
Additional information:Phase: 5
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional information:Phase: 6
Type: INSPECT
Subtype: np - inspect
Result: ALLOW
Config:
class-map inspection_default
match default-inspection-traffic
Policy-map global_policy
class inspection_default
inspect the http
global service-policy global_policy
Additional information:Phase: 7
Type: FOVER
Subtype: Eve-updated
Result: ALLOW
Config:
Additional information:Phase: 8
Type: NAT-FREE
Subtype:
Result: ALLOW
Config:
NAT-control
is the intellectual property inside 10.231.191.0 255.255.255.0 outside 10.82.0.200 255.255.255.252
Exempt from NAT
translate_hits = 32, untranslate_hits = 35251
Additional information:-Phase 9 is a static nat of the problem to another network interface. Don't know why his watch to print.
Phase: 9
Type: NAT
Subtype: host-limits
Result: ALLOW
Config:
static (interface1, interface3) 10.231.0.0 10.231.0.0 255.255.0.0 subnet mask
NAT-control
is the intellectual property inside 10.231.0.0 255.255.0.0 interface3 all
static translation at 10.231.0.0
translate_hits = 153954, untranslate_hits = 88
Additional information:-Phase 10 seems to be the default NAT for the local network configuration when traffic is to the Internet
Phase: 10
Type: NAT
Subtype:
Result: ALLOW
Config:
NAT (interface1) 5 10.231.191.0 255.255.255.0
NAT-control
is the intellectual property inside 10.231.191.0 255.255.255.0 outside of any
dynamic translation of hen 5 (y.y.y.y)
translate_hits = 3048900, untranslate_hits = 77195
Additional information:Phase: 11
Type: VPN
Subtype: encrypt
Result: ALLOW
Config:
Additional information:Phase: 12
Type: VPN
Subtype: ipsec-tunnel-flow
Result: ALLOW
Config:
Additional information:Phase: 13
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional information:Phase: 14
Type: CREATING STREAMS
Subtype:
Result: ALLOW
Config:
Additional information:
New workflow created with the 1047981896 id, package sent to the next moduleResult:
input interface: interface1
entry status: to the top
entry-line-status: to the top
output interface: outside
the status of the output: to the top
output-line-status: to the top
Action: allowSo, basically, the connection should properly go to connect VPN L2L but yet is not. I tried to generate customer traffic of base (with the source IP address of the client network and I see the connection on the firewall, but yet there is absolutely no encapsulated packets when I check "crypto ipsec to show his" regarding this connection VPN L2L.) Its almost as if the firewall only transfers the packets on the external interface instead of encapsulating for VPN?
And as I said, at the same time the remote end can activate the connection between these 2 networks very well, but just won't get any traffic back to their echo ICMP messages.
access-list extended
allow ip 10.231.191.0 255.255.255.0 10.82.0.200 255.255.255.252
local ident (addr, mask, prot, port): (10.231.191.0/255.255.255.0/0/0)
Remote ident (addr, mask, prot, port): (10.82.0.200/255.255.255.252/0/0)
current_peer: y.y.y.y#pkts program: encrypt 0, #pkts: 0, #pkts digest: 0
#pkts decaps: 131, #pkts decrypt: 131, #pkts check: 131
compressed #pkts: 0, unzipped #pkts: 0
#pkts uncompressed: 0, comp #pkts failed: 0, #pkts Dang failed: 0
success #frag before: 0, failures before #frag: 0, #fragments created: 0
Sent #PMTUs: 0, #PMTUs rcvd: 0, reassembly: 20th century / of frgs #decapsulated: 0
#send errors: 0, #recv errors: 0If it was just a routing problem it would be a simple thing to fix, but it is not because I can see the connection I have to confirm it by the router base on the firewall, but they don't just get passed on to the VPN connection.
Could this happen due to a bug in the Software ASA? Would this be something with Checkpoint VPN device? (I have absolutely no experience with devices of control point)
If there is any essential information that I can give, please ask.
-Jouni
Jouni,
8.2.4.1 is the minimum - 8.2.4 had some issues (including TCP proxy).
If this does not resolve the problem - I suggest open TAC box to get to the bottom of this ;-)
Marcin
-
With the help of a Sony TV with the latest version of the Apple Tv software. Installed a bar of his Sony and now I don't have control over the sound in front of the Apple TV. I can reset the sound (low), but it is just slowly up to maximum volume. Using the Apple Remote or my normal remote control. Can I change the audio settings Apple TV? Grateful for the assistance.
Thank you
Mike
The noise increases even if you delete the siri away from the room.
-
C7280 - cannot scan. Error message indicates another program has control over the device
I open the HP Device Manager to do a scan. I accepted the parameters and the scanning started. But the part passing through the analysis, I stopped the scan that I realized that I wanted to change the resolution. I leave the Manager device and rebooted but when I did, I got to tell an error message:
'Cannot perform the function you have requested because another program has control over ice dev'.
I have nothing else open and so I can't work on what program has control over the printer.
C7280 Prtinter. Mac OS x 10.7.
The Device Manager has not been updated for Lion and there is still no specific Lion software for your printer.
So far, you have the choice of scanning with picture Capture or preview. I'm sorry.
-
The ' sort by ' disappeared in the menu toolbars. No need for control over the Organization of files and folders. Please advise.
* original title - I can't delete automatically rearrange the menu toolbars so that I can sort the folders and files that I have wish.*
Hello
· Were there any changes made to the computer until the problem occurred?
· Have you tried right click and check the context Menu?
· This happens for any particular folder?
Step 1:
You can check if the same thing happens in a new user account. To create a new user account
http://Windows.Microsoft.com/en-us/Windows7/create-a-user-account
Step 2:
If the new user account works fine then the old account has been corrupted, you can follow the link given below to fix the corrupted user profile.
http://Windows.Microsoft.com/en-us/Windows7/fix-a-corrupted-user-profile
Amrita M
Microsoft Answers Support Engineer
Visit our Microsoft answers feedback Forum and let us know what you think. -
PIX of migration of AAS and Nat-control
If I disable Nat-control, does that mean that incoming traffic via my external interface to a routable subnet on a DMZ is not subject to the stateful inspection?
Hi Jim
No it's not. You should always allow traffic with access lists, and when a connection is made from the outside to the demilitarized zone, it will always automatically be entered in the status table.
NAT and stateful inspection are 2 different things.
HTH
Jon
-
WRVS4400N ASA 5540 L2L IPSec connection
I have a remote WRVS4400N with a dynamic outside the address that opens a connection to an ASA 5540 with a static address.
I'm all set on the side of the ASA. My questions concern the 4400N. It does not seem to have a very robust configuration/configuration available for L2L tunnels. For one my encryption is limited to 3DES.
But I wonder if I'm missing something in the config. I have to configure L2L tunnels to two other firewalls. One firewall has 3 non-contiguous networks, and the other has 2. I have 5 tunnels configuration, this is the only way? What I'd like to see is 2 tunnels, one for each firewall distance, but then each tunnel would have access to networks (like on the side of the ASA), is anyway to do this? Perhaps a useful command line for this unit?
My other question concerns the tunnel-groups I've implemented on my ASA, and I do not want to use the proper names... However I can't seem to find a way to allow this to happen on the side of 4400N... I mean, I need a way to create a 'keyword' identifier or a "firewall identifier" on the 4400N and I do not see an appropriate field in the web interface. Someone at - it ideas?
Thanks in advance.
Hi WS, the WRVS router does not support a complete tunnel configuration or routes to have a multi site configuration. You would need a separate tunnel for each location.
Traditionally, the WRVS router was not a good game on any platform ASA. In most cases, I saw when a tunnel has put in place will be the router WRVS crash in an hour or less due to low memory. If you run a scenario where the WRVS stops responding or the tunnel down, this is the likely scenario.
I highly recommend is not to use the WRVS router for all tunnel with the ASA. If you are looking to stay in the field of small business, a RV220W or a RV042 router would be a much more suitable match.
-Tom
Please mark replied messages useful -
The profile number vpn that can be created in cisco asa 5540
Hi all
Want to know if there is a limit to how many anyconnect vpn profiles that can be created in a cisco asa 5540? TIA!
https://www.Cisco.com/c/en/us/TD/docs/security/ASA/asa80/configuration/g...
Maximum connection profiles
The maximum number of connection profiles (tunnel groups) that can support a safety device is a function of the maximum number of concurrent sessions of VPN for the + 5 platform. For example, an ASA5505 can support a maximum of 25 concurrent sessions of VPN to 30 tunnel groups (25 + 5). Attempt to add a group of additional tunnel beyond the results of limit in the following message: "ERROR: the limit of 30 groups configured tunnel has been reached.
Table 32-2specifies the maximum VPN sessions and profiles of connection for each platform ASA.
Table 32-2 maximum VPN Sessions and profiles of connection by ASA platform
5505 database / security more5510/base/security Plus552055405550Maximum VPN sessions
10/25
250
750
5000
5000
Maximum connection profiles
15/30
255
755
5005
5005
-
VPN site to site by using the host name on cisco asa 5540 - dyndns
Can someone help me configure VPN site to site on cisco asa 5540. The other end is seen configured dyndns and so should set up her counterpart with the host name.
If the other end is a dynamic IP address, you must configure a dynamic map and then use in the encryption card
See the following example.
-
How can I get an ASA 5540 return to the default configuration?
Is there an easy way to re-apply the default that comes with a new ASA 5540? I would like to have the our ASA 5540 to return to its default to 192.168.1.1 inside the interface and act as a DHCP server, so I connect a PC to start the initial configuration using the ASDM.
The ASA 5540 is running on asa723 - k8.bin.
factory default setting
http://www.Cisco.com/en/us/docs/security/ASA/asa72/command/reference/c4_72.html#wp2039866
a simple "write erase/recharge" would also do the trick.
-
I have a HP Deskjet F340 all-in-one, connected to an Imac running Mac OS x 10.6.8. I just upgraded to this operating system. I downloaded and installed the latest HP soft ware, but had reset the printer to operate. Now it prints like crazy, but when I click Print on the file menu, I get a box that allows me to PRINT, CANCEL, or SCHEDULED. I have no control over the number of copies, or the pages I want to print from the file. I used to get a menu that allowed me to make these choices, but since updates, I can't find it anywhere. Any help would be appreciated.
In the print window, click the arrow next to the name of the printer to make it point upwards.
-
IPSec tunnel do not come between two ASA - 5540 s.
I've included the appropriate configuration of the two ASA lines - 5540 s that I'm trying to set up a tunnel of 2 lan lan between. The first few lines show the messages that are generated when I try to ping another host on each side.
Did I miss something that will prevent the tunnel to come?
4 IP = 10.10.1.147, error: cannot delete PeerTblEntry
3 IP = 10.10.1.147, Removing peer to peer table has not, no match!
6 IP = 10.10.1.147, P1 retransmit msg sent to the WSF MM
5 IP is 10.10.1.147, in double Phase 1 detected package. Retransmit the last packet.
6 IP = 10.10.1.147, P1 retransmit msg sent to the WSF MM
5 IP is 10.10.1.147, in double Phase 1 detected package. Retransmit the last packet.
4 IP = 10.10.1.147, error: cannot delete PeerTblEntry
3 IP = 10.10.1.147, Removing peer to peer table has not, no match!
6 IP = 10.10.1.147, Queuing KEY-ACQUIRE messages are treated when SA P1 is finished.
6 IP = 10.10.1.147, Queuing KEY-ACQUIRE messages are treated when SA P1 is finished.
6 IP = 10.10.1.147, Queuing KEY-ACQUIRE messages are treated when SA P1 is finished.
5 IP = 10.10.1.147, IKE initiator: New Phase 1, Intf inside, IKE Peer 10.10.1.147 address Proxy local 10.10.1.135, Proxy address remote 10.10.1.155, Card Crypto (outside_map0)
ROC-ASA5540-A # sh run
!
ASA Version 8.0 (3)
!
CRO-ASA5540-A host name
names of
10.10.1.135 GHC_Laptop description name to test the VPN
10.10.1.155 SunMed_pc description name to test the VPN
!
interface GigabitEthernet0/0
Speed 100
full duplex
nameif inside
security-level 100
IP 10.10.1.129 255.255.255.240
!
interface GigabitEthernet0/3
nameif outside
security-level 0
IP 10.10.1.145 255.255.255.248
!
!
outside_2_cryptomap list extended access permit ip host host GHC_Laptop SunMed_pc
!
ASDM image disk0: / asdm - 603.bin
!
Route outside 255.255.255.248 10.10.1.152 10.10.1.147 1
!
Crypto ipsec transform-set esp-SHA-ESP-3DES-3des esp-sha-hmac
card crypto game 2 outside_map0 address outside_2_cryptomap
outside_map0 crypto map peer set 2 10.10.1.147
card crypto outside_map0 2 the value transform-set ESP-3DES-SHA
outside_map0 card crypto 2 set nat-t-disable
outside_map0 interface card crypto outside
crypto ISAKMP allow outside
crypto ISAKMP policy 5
preshared authentication
3des encryption
sha hash
Group 2
life 86400
!
Group Policy Lan-2-Lan_only internal
attributes of Lan-2-Lan_only-group policy
VPN-filter no
Protocol-tunnel-VPN IPSec
tunnel-group 10.10.1.147 type ipsec-l2l
IPSec-attributes tunnel-group 10.10.1.147
pre-shared-key *.
!
ROC-ASA5540-A #.
----------------------------------------------------------
ROC-ASA5540-B # sh run
: Saved
:
ASA Version 8.0 (3)
!
name of host ROC-ASA5540-B
!
names of
name 10.10.1.135 GHC_laptop
name 10.10.1.155 SunMed_PC
!
interface GigabitEthernet0/0
Speed 100
full duplex
nameif inside
security-level 100
IP 10.10.1.153 255.255.255.248
!
interface GigabitEthernet0/3
nameif outside
security-level 0
IP 10.10.1.147 255.255.255.248
!
outside_cryptomap list extended access permit ip host host SunMed_PC GHC_laptop
!
ASDM image disk0: / asdm - 603.bin
!
Crypto ipsec transform-set esp-SHA-ESP-3DES-3des esp-sha-hmac
card crypto outside_map2 1 match address outside_cryptomap
outside_map2 card crypto 1jeu peer 10.10.1.145
outside_map2 card crypto 1jeu transform-set ESP-3DES-SHA
outside_map2 card crypto 1jeu nat-t-disable
outside_map2 interface card crypto outside
crypto ISAKMP allow inside
crypto ISAKMP policy 5
preshared authentication
3des encryption
sha hash
Group 2
life 86400
!
internal Lan-2-Lan group strategy
Lan Lan 2-strategy of group attributes
Protocol-tunnel-VPN IPSec
tunnel-group 10.10.1.145 type ipsec-l2l
IPSec-attributes tunnel-group 10.10.1.145
pre-shared-key *.
!
ROC-ASA5540-B #.
On the ASA of ROC-ASA5540-B, you have "isakmp allows inside", it should be "enable isakmp outside."
Please reconfigure the ASA and let me know how it goes.
Kind regards
Arul
* Please note the useful messages *.
-
Hello
I have the following scenario: -.
A net - network 172.20.82.0/24 (under my control)
B ' net - network audience (beyond my control)
I have a lot of servers on the Net (172.20.82.0/24) network I would PAT behind a public IP address before it is sent over a virtual private network to the remote site (Net (B). By some read far quickly, my understanding is that I'm going to need to: -.
(a) conduct an "indoor/outdoor" PAT on the Net 'interesting' traffic to my address of PAT Public front I then...
(b) apply the new address Public PAT crypto and ACL "NAT 0".
i.e.
one)
access-list allowed NET_A_PAT 172.20.82.0 255.255.255.0 NET_B_NETWORK NET_B_NETMASK
NAT (inside) 20 access-list NET_A_PAT
MY_PUBLIC_PAT overall, 20 (outdoor)
then (b)
NO_NAT list extended access permit ip host MY_PUBLIC_PAT NET_B_NETWORK NET_B_NETMASK
CRYPTO_MAP list extended access permit ip host MY_PUBLIC_PAT NET_B_NETWORK NET_B_NETMASK
First question is - is it good? I think it is, but I'm just wanting clarification.
Second question is: I is also launching a 'standard' CARESS on the 'outside' of the SAA for internet traffic normal (Internet) interface - navigation etc. If I play a PAT inside and outside as shown above, not then try and pass packets encrypted using my 'new' PAT instead of the IP Address of the remote VPN endpoint interface? Or take it to process my first PAT crypto then re - wrap by using the 'real' outside interface IP PAT?
Hope I'm reasonably clear - thanks in advance.
(a) correct
(b) in part reason, crypto ACL is correct, however, you don't need NAT 0 ACL like you do a PAT.
Second question - no, PAT comes first, then it will encrypt the packet with the IP Address of the interface that is the VPN endpoint.
-
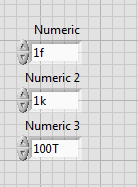
Digital control over several orders of magnitude
Hi all,
I'm trying to get a digital control with a suitable addition to the order of magnitude.
For example, I have a front panel for an osziloscope, sometimes that samples on some ns, sometimes a few seconds, sometimes a few milivolts, sometimes a few volts, who knows, right

I was playing around with the digital control units, but it doesn't quite fit my needs. I can't change the prefix of a unit on the duration, for example of microseconds to seconds, but then I change the issue as well, because on change the prefix, the previous number is only multiplied by the factor according to, for example, 1000, so 5 became US 5th-6s. So change the record length of the default value of 500 ms to 100 ns would require two klicks type, and I can instead just type "100th-9', which is good too."However, I would like to have a digital control from 0 to 1000 combined with for example a button for prefix i.e. nano, micro, mili etc. and combine this values internally, i.e. of mulitplying accordingly. But I couldn't set the increment to "3 orders of magnitude" even with the option to log scale.
I know, I could use an enum with the names and values according to, but this is not very satisfactory.
So perhaps the question would be: is it possible to combine two digital controls or the value for the prefix, in a suitable and easy way? Or how do you manage the digital values over several orders of magnitude in a case like mine?
Thanks for your replies in advance.
Best,
bastlwastl
Display format is SI units
It helps in these situations

Maybe you are looking for
-
Slideshow of photos in HD - DVD?
Greetings, I created a slide show of Photos of about 300 images of high resolution and to burn the show on DVD in HD quality. Is it possible to do that with my existing software or should I buy a separate software to achieve this? I tried to export
-
20/02/2013 all impressions was normal. 21/02/2013 not only printing did not work, but PDF files did not appear correctly. Is this a new version of Firefox? I got the PDF reset so that it now works, but not printing. In the Comcast e-mail, the date mo
-
When you add items to a project can then remove the clips? I'm trying to free up space on my hard drive. Thank you.
-
I want to choose the following code (it was shipped) and run similar to the arduino (what it runs instantely from active power, without having to activate OR on my labtop). How can I do this? Is this all just a question of execution of the loop in re
-
How will I know what form a table is a long section of the mathscript code? IE is a table one row or column, or a matrix. Often, I get the error that produced the home, regardless of what form, I develop controls in. I really need an accurate way to