Networking Concepts advanced on Switch virtual: Vlan-association
I have a network configuration problem, and I need to implement it on my virtual switch.
I have Vlan Setup with a primary and the association vlan. The goal of this configuration is to isolate members vlan and to prohibit any communication between members of the same Vlan.
The configuration is the following:
VLAN 201
name NewHostnig
private - vlan primary school
private - vlan association 202
!
VLAN 202
name NewHostingIsolated
!
interface FastEthernet2/13
FW description
switchport access vlan 201
switchport private - vlan mapping 201 202
switchport mode private - vlan promiscuity
events-the link status logging
interface FastEthernet2/14
Description Client_www
Description access vlan 201
organizing switchport private vlan Association 201 202
switchport private - vlan mapping 201 202
switchport mode private - vlan host
events-the link status logging
Can I set this up on my virtual switch?
Thanks for your help
Cisco PVLANS (Private VLANS) are not supported at the moment on ESX 3.5 vswitchs. Would be a nice feature, but we will have to wait and see
Tags: VMware
Similar Questions
-
DNS will work within a private network that includes only a virtual switch?
I have a private network defined in free ESXi 5.5 using only one virtual switch.
Virtual machines on this virtual switch can ssh them using their IP addresses.
I have configured the DNS on one of the virtual machines in this private network, but it will not
resolve hostnames to IP addresses.
Simple question, DNS can run on a private network that is composed
only a switch virtual ESXi?
Yes it will work, but you first need to register all the names of virtual machines and the IP address on the DNS server and point the entry of DNS server on the virtual machines to IP address of the DNS server that you deployed.
-
Issue of V-Switch virtual network, possible configuration of VLAN
A screenshot of doc word of my virtual network is attached. I'm trying to get my external labeled Virtual Switch (vSwitch2) talk to the VM (vSwitch0) network switch. My goal here is to be able to connect a physical PC into the switch labeled vmnic1 external physical and be able to convert a virtual PC VM via a cross over cable. I don't know that it would be in the same subnet as the network of VM vmic0. Do I have to install some kind of vlan etc... The physical box with XP on it can perhaps start with DHCP and enter an IP address on the same subnet bridged somehow of the external vmnic1 in the VM Network vmnic0. What is the easiest more quick to make this work? Please see the attachment. Thanks in advance for your help
Post edited by: vite@1
You will need to open a new question, if that's what you're talking about.
-KjB
VMware vExpert
-
way which restrict what networks is connected to a virtual computer simultaneously
Hello
We try to combine the two clusters of different vsphere into one in order to get the best use of our computing resources. Each group has its own set of networks inside. In order to consolidate the two clusters, we would need to present the two networks on the same cluster together. Group A has a unique network and Cluster B has 4 networks located behind a firewall for use off-production.
Our team of network security was a concern for someone to create a virtual machine with two network cards for a vNIC originally in Group A network connection and an another vNIC connect to a network in Cluster B which is located behind the firewall by creating a bridge between two networks that could bypass the firewall.
Is there a way to deny the ability to have the network of Group A and B cluster network be on the same VM? Almost like a rule of affinity when you do not allow two different networks on the same VM? I couldn't find anything on this point and do not know if this is even a feature support, but I thought I'd see if anyone knew.
We are running vSphere 5.0 U3 and want to move to vSphere 6 shortly. We also use switch Cisco Nexus 1000v for both groups.
Thanks in advance!
-Michael
Welcome to the community - if I understand your question, you want to move all hosts in single cluster - if it is the case that the answer is no - if anyone has the ability to create the VM in this cluster they will be able to connect to any network in this cluster - if you put two separate cluster, you would be able to assign permissions to each cluster that allows users the ability to create machines only virtual only within their group.
-
Make a little a bood by setting the switch 1 VLAN other than ALL - lost to ESXi management
Hi all
As the title says, I mucked this up a little bit. I have two virtual switches configured, one with all my virtual machines on three cards attached network, and the other with the management and interface card NETWORK attached.
I thought that I have would combine the lot in a single switch and have the cards connected to the simple switch. Everything is VLAN'ed switch0 was set up at the trunk all the VLANS, as was the segment of management - although this should be in one VLAN specific. I've updated the Switch0 simply use the VLAN segment management and connectivity quickly lost the device to ESXi. All virtual machines on their VLAN specific are OK on the second switch.
How can I return a network access ESXi?
Console access is available, but I seem to have lost Out Light control will have to physically go to the machine.
What a prick!
Chris
Couple of questions to understand the actions performed by you:
I've updated the Switch0 simply use the VLAN management segment, and quickly lost connectivity to the device ESXi--> do you mean WHAT VLAN ID changed to 18 0 (none)?
The virtual switch was set to pass all THE VLAN the Port VMkernal (Management Network Group) has been updated with "All THE VLAN", I went it to the VLAN (18)-->, you gave VLAN ID as 18 and your single NIC - VMNIC 0 is interconnection to VLAN 18?
In simple words - you physical NIC 0 visibility to VLAN 18 or not (you will have to ask Admin network) - double else check your wiring asks that you made at the time of Installation
For this kind of connectivity issues - you need problems like RSA/ILO/DRAC remote console based on the style of the material.
-
Hello
I'm install esx 5.1.
I have 3 vlan (prod, vmotion, vmkernel). I am glad that when I put vlan dcui (yellow form) correct, that I can not ping host esx. If Iremove vlan tag I can ping esx host.
I suspect that someone does not work on the switch (not run by me).
How can I help the team network? What game on the switch port network team must be defined?
Thank you
Jonh
asanet wrote:
Hello
I'm install esx 5.1.
I have 3 vlan (prod, vmotion, vmkernel). I am glad that when I put vlan dcui (yellow form) correct, that I can not ping host esx. If Iremove vlan tag I can ping esx host.
I suspect that someone does not work on the switch (not run by me).
How can I help the team network? What game on the switch port network team must be defined?
Thank you
Jonh
Your network team should create a 'trunk' for physical network ports used by ESXi. On the trunk, they should allow these 3 VLAN mentioned above. Now, I guess they did but you "VMkernel" VLANS is equal to your regular administration VLAN, which is also be the VLAN native.
So I think that there is nothing 'wrong' with your configuration, it's just an implementation detail... If the "management VLANS" also happens be the VLAN native side effect is that you do not need to specify a VLAN ID on the portgroup.
More details can be found here: VMware KB: example configuration of the virtual switch VLAN tagging (VST Mode)
-
VMware Distributed Switch with VLAN
Hi again,
A lot of work with VLAN now.

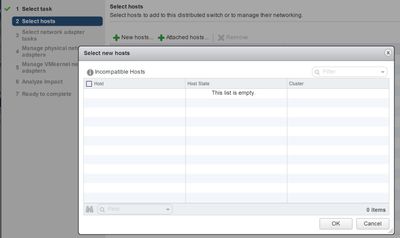
But just a quick Questions. Is there a documentation or HowTo Guides how to set up vSphare VMware Distributed Switch with several VLANS on a Switch GS724Tv4?
But soon, I try to add a host or network, it is empty.
This is probably an easy problem of VMware, but I try here first to see if someone has document guide HowTo so I can start with.
Thank you
Christian
Never mind about this,
I found the problem on my own, but perhaps a documentation would be great to have. But it's a good start to have the right license of VMware, before you start.

* I was just out of luck when I thought *.
/ Christian
-
In addition to all my switches Cisco Catalyst (successful), I have a bunch of Linksys SD205 unmanaged switches on my local network.
I want to configure my network for VLANs, which means I have all my managed Cisco switches will change to a "Routing" configuration This configuration works well with Cisco Catalyst switches
Question: the SD205 can operate in this environment? I know I can't put one of the ports on the SD205 to be 'delivery', but I would like to connect the SD205 to a port of Cisco, which is "effective", so that the devices on the SD205 can communicate to the rest of the world.
So far, I have not crowned success, then - maybe - they won't work in a shared resource environment. Someone at - it a definitive answer? If they simply can't do it, I will stop wasting my time!
Thank you
# A unmanaged switch is not compatible 802. 1 q. It will pass any frame ethernet that was 802. 1 q tagged. The only executives who pass through a switch are unmarked, frames that is the VLAN port on the catalyst native.
If you want to use unmanaged switches, you have to connect to a port configured in mode access, Member of a single VLAN. For example, you can configure a port on the catalyst for access VLAN 10 mode and connect a switch to that port. All devices connected to the switch unmanaged will be VLAN 10. This as you can do.
But several VLANS: alert the unmanaged switches is impossible because all frames ethernet on the switch must not be tagged.
-
PowerConnect M6220 problem without tag switch of VLAN
Good afternoon.
I do not have much knowledge of networks and need help.
M6220 have this connected to a HP ProCurve switch switch connected by a trunk.
My problem is that I can not pass the 10 untagged procurve VLAN to the M6220 switch, can you help me?
M6220 has firmware version 1.
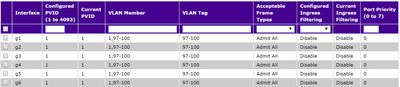
Thank youOn a network connection VLAN native is the VLAN used to send and receive packets not marked. Here is an example of the configuration.
Console (config-if-article gi1/0/1) #interface item in gi1/0/24
trunk mode console (config-if-article gi1/0/24) #switchport
Console (config-if-article gi1/0/24) #switchport trunk vlan 10 native
trunk allowed vlan #switchport console (config-if-article gi1/0/24) add 10,11,12,13If trunk mode does not work, you can also try to use the general mode.
Console (config-if-article gi1/0/1) #interface item in gi1/0/24
mode console (config-if-article gi1/0/24) general #switchport
Console (config-if-article gi1/0/24) #switchport general pvid 10
Console (config-if-article gi1/0/24) #switchport general allowed vlan add 10 untagged
Console (config-if-article gi1/0/24) #switchport general allowed vlan add 11,12,13 tagHope this helps
-
Mini of the UCS + 4 switches, no VLAN
Hi all
I have a mini UCS with 6324 modules e/s with B200 m3 x 5 blades, each ESXi 6.0 running.
I want to uplink the UCS mini with four cables to four switches separated for traffic, and I wish that each host ESXi b200 see four separate vmincs, one on each network. The switches have no VLAN, but running DHCP. I want to get DHCP from each card.
How can I go on the correspondences between the vNIC? Groups of LAN Pin?
Hi Alex,
That is right. You can also implement Layer 2 disjoint explained in the guide below for more secure access.
http://www.Cisco.com/c/en/us/solutions/collateral/data-center-virtualiza...
I hope this helps.
Qiese Sa'di
-
Dear all,
A week ago, I upgraded both my two machines VMWare Win 7 to win 10, as well as the host operating system. also from 7 to 10.
Now once every 1 or 2 days, one or both the two vmwares aura an esclamation mark on the network status icon in the lower right corner and West no connection.
The host operating system is NOT having any problems with the network.
The solution is to disable and reactive the adapter to virtual machines, or repair of running Network Diagnostics where she'll tell me that it s has reinstated the connection to the bridge. But obviously I´d prefer the VM´s to be on the internet 24/7 without my intervention.
I have another computer on the same router on which I did the same thing, but with this I m not having these problems. A different and not connected equipment via the VPN running on the host OS, which is the case with the machine that s had questions.
But even once, the host operating system is not having issues, the two VM´s aren´t always the two to have this problem, and this never happened when he was all Win 7.
I ve disabled some nights windows defender analysis and TCP/IP V6, but neither helped.
Want to see some of the information from the last network diagnostics / repair or some log file, or you already know what would be the solution to my problem?
Thanks in advance!
Best regards
Jazzl
Well, I thought that a vm was having this problem a lot more often than the other, so I looked for error messages in windows journal, showing that the network problem - have to with DHCP btw - always spent 2 minutes after an event regarding slui.exe, not found on the other machine.
What I also noticed was that the problematic vm had lost its activation of windows with the upgrade to win 10 (win 10 has limits to how much the same license can be run as virtual machines), is is not the case for the more successful one.
Then I copied the good machine, which contains the same as the other, changed mac and uuid and now it s showing that enabled, no problem so far.
-
Hello guys.
Is there a diagram that I made, using for my self this question.
As you can see, I have a physical server with 2 NIC I don't want to use a VM (with Snort) as IPS / IDS system for inbound traffic on the management of VLANS. Is it possible to use this VM in this way (as an IPS/IDS, VM with two NIC without any routing work?)? Maybe you have a suggestion, how can I achieve this, as easy as possible? Maybe you have an opinion, what OS unix system do I use?
Thank you for your time and your answers. Any useful information is much appreciated.
Yes, it should work. You need to look out for, it's that the 'outgoing' NIC is not connected to the same physical switch as the entrant and that there is no link between these two physical switches, because this would create a loop of layer 2 on the network.
I haven't worked much with Linux, but I don't see that you would have a problem to find some Linux/Unix with the possibility to bridge two network cards and use some software IPS to inspect the traffic.
-
VNetwork Distributed Switch virtual cards
Trying to get my head around e-cards in the distributed switch.
In standard switch, I understand the hierarchy like this:
vSwitch (upper level)
groups (including the kernel) port (2nd level)
physical cards (identical to "vmnic..") (join vSwitch)
I do not understand the hierarchy for the distributed switches. The use of the term virtual card throws me a loop for. I consult the virtual map of term as something that you "attach" to something (vswitch etc...), not something you add. For example, when I go in manage e-cards and select migrate existing adapters, I give you the choice of console and vmotion. I find the console and vmotion as groups of ports and not e-cards. Any help to understand this would be appreciated.
Thank you
From page 36 of the Guide de Configuration ESX (http://www.vmware.com/pdf/vsphere4/r40_u1/vsp_40_u1_esx_server_config.pdf):
Virtual network cards manage services network host on a vNetwork Distributed Switch.
You can configure the console service and VMkernel virtual cards for an ESX host by a partner
vNetwork Distributed Switch or by creating new virtual maps or the migration of existing virtual cards.
When you migrate a virtual network adapter, you should migrate the service or VMkernel console since a standard vSwitch to a group of ports in the vNetwork Distributed Switch.
-
-
Private network between two or more virtual machines?
I've been running an educational network configuration kind of base on esxi to work to teach their colleagues how running things. To do this I create a separate switch, connect the virtual machines to (only) the switch and run Ethereal on a machine with network in promiscous mode.
Now, I would do it on my laptop. Can I do this with the merger? Can I network machines without connecting to the host (to ensure that there is no additional noise)? Can I configure a NIC in promiscous mode?
sflanders wrote:
I think the important part of the question is in regards to the networking VMs as they see, but not the host (btw merger networking of information: http://communities.vmware.com/docs/DOC-2527). Basically, it boils down to the host option only and the answer is no.
In fact, the answer is yes because after that Virtual Machines are started can be simply down the vmnet1 network card and thus isolate the virtual machines between them.
In other words on the network of Machines target virtual host-only and then start them up to the point where they receive their IP address DHCP host-only server, then in a Terminal on Mac (/ Applications/Utilities /) use the following command in low only Ethernet adapter of the host host.
sudo ifconfig vmnet1 down
Now the target of the Virtual Machines will be able to communicate only with each other and not the host.
Note: You must down only Ethernet adapter of the host host after the virtual machines have acquired their IP addresses, because if you down the adapter before the Virtual Machines will not receive their IP addresses.
The host only allows virtual machines to see the host, but it really shouldn't be any other "noise". Why do you have to be concerned about this?
On the question of the noise, I think that VMware Fusion actually uses virtual hubs, no virtual switches (even if by mistake, VMware calls virtual switches), there is a risk of bleeding, and this has been discussed ad nauseam and various forums.
-
Best wireless network installation with the switch TP-Link
Hi all
Few question numpty maybe, but what follows... We just moved to a new (larger) home with thick walls and I want to set up a new wireless network.
The current installation is:
Fiber cable entering the House in the basement and connected the modem to the service provider that provides 150 mb internet. I changed the capacity wireless on the ISP's modem and connecting an airport extreme (2014 model) via the LAN to the modem. The extreme is in the office but on the 3rd floor is having connection problems than you can imagine. All rooms have access points CAT5e who all meet in the basement. I have two spare Aiport express and two Apple TV that I would use. Also I bought a TP-LINK 1000mbps (16 channels) Network Switch.
Could someone please tell how the best set-up of my home network. For example, the Airport Express to the 3rd floor connected to the switch (wired) network or to an extreme in the Office? Apple TV also connected to the network switch?
I would like to end up with a solid wireless network that passes without problem from extreme to Express necessary each time you walk and you want to use an Apple TV for television on the ground floor and one in our room.
Many thanks and apologies once more for this very basic question... I have expanded my front (extreme Express) wireless network but just don't know how best to use the switch.
Thank you
The simplest up set... which is almost always the best game in place... would be to connect the switch 16 ports to the modem/router and then connect devices to the switch. In other words, if your modem/router has 16 + Ethernet ports, the simplest network configuration would be to plug as many devices as possible directly to the modem/router.
Other variants are possible, for example, the network might look like this:
Internet > Modem/Router > AirPort Extreme > switch > devices... or, you can connect certain devices to ports Ethernet on the AirPort Extreme and some to the ports on the switch. One thing to keep in mind however... If there is a problem... Troubleshooting may not be easy since it will be difficult to know where the problem actually lies. Much easier to all have, or of possible devices, connect to the switch.
Unfortunately, the AirPort Express devices will be of real bottlenecks on your network. These devices are notoriously slow as well as wireless, and even if they work well, the speed will be does not exceed 100 Mbps... since it's the speed of the port to the AirPort Express. In fact, I expect each Express to provide a wireless signal in the range of 50-60 Mbps.
Another thing to keep in mind of the wireless network is that Macs will usually a good work of tilting automatically to the point of wireless to the other as moving from one place to the other in the House... but the iPhones, iPads, PCs, and other mobile devices will do that very well... If they do at all.
So with these devices, you will need to get used to temporarily disable the WiFi on the device and the device when you move in one region to the other, and then turn WiFi on must generally then pick up the signal from a nearby wireless access point.
Maybe you are looking for
-
The problem seems to be related to Firefox, IE looks ok. Returned to a well known previous restore point did not help. Running Windows 7, FF6.0.2 Java is up to date. Before I did system restore, FF crashes frequently these questions of text entry. Af
-
Satellite Pro U200 - how to activate the bluetooth connection
How to activate the bluetooth connection?
-
HP Pavilion dv6-2173-cl: driver nvidia suitable for my laptop
Hello I had problems with the nvidia driver in the tpast and I just want to make sure that given the number of my laptop model and the hardware ID below, I have the right driver. Driver for PCI\VEN_10DE & DEV_0A68 & CC_0300Driver for PCI\VEN_10DE & D
-
I'm on 7v, I try to add a member and don't remember the password to add. I have an access grpadmin.I looked and looked. with nothing does not.
-
My Photosmart C7250 stopped seeing my Netgear WPN824v3, but can still see others. It sees.
I have a printer HP wireless who worked for always through my modem wireless Netgear WPN824v3. However, for the past 2 weeks my printer will not see the modem. He sees no other in the region. I rebooted everything a million times and even moved the p