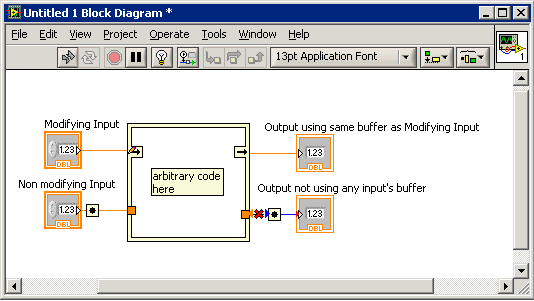
nodes to call groups, should be simple!
Hiya,
I am new to invoke nodes from today and I need default reset of a large group of objects at the end of my VI. I don't want to set different invoke nodes for each of them. Can I ask a refnum to a group of objects and how I would do?
See you soon
I don't think that there is a way to do exactly what you ask (Group). However, you can create a table of references and put the reset inside a loop for.
Lynn
Tags: NI Software
Similar Questions
-
Please help - should be simple!
--------------------------------------------------------------------------------
Maybe I haven´t been explaining this correctly, it should be really easy I changed things to make it easier now.
http://216.219.94.105/AJAX1.htm
I have four tabs that work very well and when we click on change the panels (if you click on 'Second panel' for example, you see the second Panel).
The problem is that I'm doing the two links from the first panel which is the sign that you see when you first load the page in your browser.
In my most simple English clearest case I want to make two links (or one is fine and I can work out how to do other) work (they don t at present).
What are the links, and how they should work? :
There are two links href (let´s we'll call 1 and 2 so that we know what we are talking about):
1. on me to see the second round table
2. click on me to see the third round table
What I want to do, is that when you click the 1 link, you should see the second panel (which actually mimics the same action than to click on the second link Panel in the Panel).
When you click on the link 2, you should see the third round table (which actually mimics the same action by clicking on the link third panel).
That s it - it should be simple enough but I Don t has the slightest idea how to do it! How can I do? Thank you very much in advance
Links:
<! - first Panel - >
< div class = "gw_aTab" >
<! - links - >
< h3 > it's the first round table < / h3 >
< a href = "" > click on me to see the second panel < /a > < br / >
< a href = "" > click on me to see the third panel < /a > < / div >Here´s response:
It's the first round table
Click on me to see the secondPanel
Click on me to see the thirdGroup of experts
The index starts at 0
-
Why jump nodes in my group originally from the root of the scene?
My project code is too big to post, so I'll try to explain the problem that I am facing. I'm creating a tool of graphic layout as part of the largest visualization tool which we build.
The problem I have is a group that I've positioned using layoutX, we jump to the origin whenever we do the graphic layout.
Here is the basic flow of the program:
- We create a graph of JUNG's Circle (vertices) and Lines (edge)
- JUNG layout classes allows us to generate a layout for the chart. The layout generates an x, position y for each vertex in the graph in a particular area. Say a box of 400 by 400.
- We use the positions generated to define the properties centerX, centerY of the circles. The lines are tied to the centers of the nodes they're going between, so they update automatically.
All this is done to present the original graphic layout. The user can select nodes and choose them to be prepared in a new way. This creates a sublayout on the Web. When the circles are selected move us to a group position in the exact spot where they were selected. The groups are made adjustable and can be moved across the canvas. Update the lines and circles do not move compared to the benchmark of their parent group. Only their container is moved inside sceneRoot.
The scengraph looks like:
VBox
Group: sceneRoot
Circles and lines that make up the original graph
Group: sublayout
Circles and selected lines
The problem comes when we try to make the layout of the selected nodes. We generate a subgraph of JUNG. Then we make the graphical layout with the subgraph to the circles that it contains new positions. We ask the page layout to generate a layout, the size of the sublayout group. This method works. JUNG generates new values for the positions of the circles. When we created the centers of the circles, the group goes to the top left corner - origin of the sceneRoot. In my view, the Group should not move at all. Is layoutX, there have been established and the circles are positioned relative to origin of sublayout. I can't understand why the group jumps to the origin. It should stay in place.
I thought about it!
The problem was by using a group as the root of the Web. Limits of the group are the sum of the limits of his childhood. This means that the limits of the group will change according to what is in it. When the VBox kicked out, it would move because the new bounding box. The fix was to use a component. A pane is resized according to the rules of pref/min/max and does not fear for the sum of its children. This is one containing more "solid".
-
Problem of Skype calls groups calls problem/video group
Hello
I use Skype on Samsung Galaxy A5 (A500FU) and I can not start a group call / or call groups like the button 'call' in the upper right corner is missing. Same problem with group video calls (call button is missing).
I use the latest version of Skype for Android - 6.33.0.575
Any ideas?
Thanks in advanceSkype has solved the problem in version 7.01.0.669 of 31.05.2016. After the update the Group calls (video & audio) work correctly.
I must say that I am really impressed with their customer service. I explained the problem in detail and in the next update, the problem has been resolved. All people using Skype on Samsung Galaxy A5 will be very happy

Thank you

-
How to use the node to call a library function to convert C++ source codes
Hi all
There are two dll name 'QMSL_WLAN_Transport.dll' and 'QCAMSL_MSVC10R.dll' and some codes c ++ to connect to the DUT. The two DLLs work together for communicaite with the DUT.
I am confused as how to use the node to call a library function to load the 'QCAMSL_MSVC10R.dll' function as
g_hResourceContext = QLIB_ConnectServer_UserDefinedTransport((HANDLE) USER_HANDLE, UserDefinedSend, UserDefinedReceive, UserDefinedFlushTxRx, true, true);
It seems that 'UserDefinedReceive, UserDefinedSend, UserDefinedFlushTxRx' Processaddress? And "UserDefinedReceive, UserDefinedSend, UserDefinedFlushTxRx"'s functions in 'QMSL_WLAN_Transport.dll '.
UserDefinedReceive = (_UserDefinedReceive)GetProcAddress(hUDT,"UserDefinedReceive"); UserDefinedSend = (_UserDefinedSend)GetProcAddress(hUDT,"UserDefinedSend"); UserDefinedFlushTxRx = (_UserDefinedFlushTxRx)GetProcAddress(hUDT,"UserDefinedFlushTxRx");
Attached DLLs and C++ code snippets.
Need help.
Thank you.
These parameters are reminders - pointers to functions that are called by the DLL - and there is no way to duplicate this purely in LabVIEW. Search this forum for the word "recall" and you will find similar questions (for other DLLs). You will need to write your own DLL (in C, C++, etc.) that implements these functions and provides a way to transfer data to LabVIEW.
-
Pass a variable to a text entry field in a URL (was: I feel like it should be simple but)
I think it should be simple, but I'm having a hard time finding how to pass a variable to a text entry field in a URL. I have a text input field ("enter your postal code') and a button that says 'Go '. When the user enters their zip and hit 'Go', I need the postcode, they came to pass in a URL to a new Web site so that they can see the offers in their region. This is a Flash 300 x 250 banner. Can someone help me?
I can download my FLA somewhere and link to it if needed!
Click on the frame that contains your go button and your textfield and paste Panel actions:
go.addEventListener (MouseEvent.CLICK, f);
function f(e:MouseEvent):void {}
navigateToURL (new URLRequest ("http://namebrandinsurance.com/auto/newResults.php?zip=" + zip.text + "& submit = submit"));
}
-
Threading and reuse of the node to call using reference of buffers (of the required adhesive tape)
I tried to get the following information in the public domain for years and now that I have the answers, I'll share with those who might be interested.
Caveat!
Wrap your head in tape before reading just for the sake of security.

My two questions were;
(1) may LV re - use tampons of VI calling when you use VI serve call by reference?
(2) is used when the use of call by reference UI thread?
1 when you call a VI using the call through the reference node, the data in the pane of the copied or is node connector - this online as it would be with a Subvi properly implemented?
Short answer: it's somewhere between the two.
Long answer:
The compiler does not know what will be called VI, but there a hint:
the reference connected to the node of the call by reference. He uses to get the 'Prototype' for the call. Therefore, for optimal performance, use a prototype that has the same 'characteristics placeness' as it is called VI. That said, users don't know what are the "characteristics of the placeness.
Before getting into the details, I will say that the overhead of these copies should not matter much unless it's a large data structure (a table with lots of items.) or a cluster/class with many fields or containing large networks etc..
Example 1:
If the prototype does not change the data, then the compiler assumes that the crux of the call by reference will not alter the data. However, at runtime, a check is made to see if the real called VI will modify the data. If Yes, then a copy is made and past so that the original data can be modified.
Example 2:
If the prototype contains an entry that is wired through an exit so that both input and output terminals can use the same buffer memory, but running an audit determines that the real called entry and exit VI do not share a buffer, then a copy will be made from output of the actual call to the original screws (combined input and output) buffer.
I should also mention that, even with this behavior "are trying to get along with the prototype", it is not always possible to obtain good performance as a Subvi ordinary call. For example, if you have a situation where the prototype does not change the data and passes it through to an exit and then the compiler must assume that the data is changed (because, as in example 2, there are screws that may change even if the called real VI is not).
And there are a few caveats:
(1) this behavior "using a prototype" was new for 2009. Before that, we used a method more naïve data of passage that took all the entries will be changed and no outputs don't share a buffer with an entry.
(2) this behavior can be changed in future versions, if we find additional optimizations.
(3) this behavior is the same that we use for the dynamic distribution live (when you use the classes in LV)
(4) If you want to create a VI can be used as a prototype, you can use the features of the Structure in Place to control the "characteristics of the placeness', namely the element nodes in and out of the border, the function"Mark as modifier"border nodes (note the pencil icon on the item), and the node always one copy.
(5) the prototype is only the first reference ever connected to the node of the call by reference. So if you make a new prototype VI, you can just make a reference out of it plug into the crux of the call by reference. I suggest to remove the node from the call by reference and file a new.
(6) for remote calls, we still "making copies" by transmitting data over a network.
I hope that this helps, if you want information/clarification, so feel free to ask.
2 - is the call made by the reference to run in the user interface thread node? If the call is made by a remote machine via ethernet, thread that host (the computer that makes the call by reference) runs on and thread that executes the target (the machine that contains the file VI) on?
In the case of premises, the appeal made by the reference node does not require the user interface thread and may work in some thread the VI wants to run in.
When you call a remote VI, the appeal made by the reference node uses the UI thread (detailed below) on both the client and the server.
The client uses the UI thread to send the request to the server and there still when the response comes back. The user interface thread is not blocked during the time between the two.
The server receives the TCP message in the UI thread, and then starts the call to the UI thread. The server also uses the user interface thread to send the response to the client. The user interface thread is not blocked on the server during execution of the VI.
I hope that people find it when they need it!
Ben
-
How to use the node function call library for a function in the dll with the data SUB type
Hi all
I would ask for your kind help
I am facing a problem with the call library node.
I have a C++ (stdcall) function, which has Sub as data type
XXXX error code (hwnd, lid, getValue, * Sub data1, * Sub data2)
data1 and data2 types are constantly changing based on the value of 'getValue '.
Mainly I can use the call library node several times and adapt each node according to the types of data data1, data2 and extract the values and use in the code. Here is no question. Real question is:
My question:
How can I use a node of library time call and make a case according to the 'getvalue', who will control the data1, data2 data type. Here I really seeking solutions.
My tests:
I used varaints as entry to the libray call node of the data1, data2 and selected parameters in the call libraby node as "Adapt to type. Here labview just crashed.
I appreciate your suggestions to feedbackand.
Thank you
Karine
You must allocate enough space for data1 and data2, and then pass a pointer to this space. An easy way to do this is the function to initialize table. Set the U8 type and size for the number of bytes required. Pass this array to the function as a pointer of table data.
After the function call returns, you need to extract the data in the table. You can do it manually, but a simple approach is to use the array of bytes to a string. Then, in a housing structure, use Unflatten chain to convert the string to the correct data type. This method also converts the "endianness" which will be probably necessary; Be sure to only set all entries for unflatten correctly.
-
Windows scam Call-What should I do?
Hello, I just fell for a scam Microsoft Cold Calling. They told me to check my observer of events, and then go to www.support.me. They then told me to enter a 6-digit number and click on "connect to technician. I did, but then they realized I was only 16 years old and I was not the owner of the computer or the person paying for the internet. They sounded so irritated, told me to call at the time where my parents came home and told me to turn off my computer. There was no sign of moving the mouse and nothing has been downloaded. I turned off the PC and disconnected from the power supply and the internet immediately. They have planted a virus on my computer or obtained control of it? Or they want just money? I'll take to a computer repair shop. Which will solve all the problems?
Hello
It's a SCAM!
Avoid scams to phone for tech support
http://www.Microsoft.com/security/online-privacy/avoid-phone-scams.aspxIn the United States, you can contact the FBI, Attorney general, the police authorities and consumer
Watch groups. Arm yourself with knowledge.The Internet Crime Complaint Center (IC3) is a partnership between the Federal Bureau of Investigation
(FBI) and the National White Collar Crime Center (NW3C), funded in part by the Bureau of Justice Assistance
(BJA).
http://www.ic3.gov/complaint/default.aspxNo, Microsoft wouldn't you not solicited. Or they would know if errors exist on your
computer. So that's the fraud or scams to get your money or worse to steal your identity.Avoid scams that use the Microsoft name fraudulently - Microsoft is not unsolicited
phone calls to help you fix your computer
http://www.Microsoft.com/protect/fraud/phishing/msName.aspxScams and hoaxes
http://support.Microsoft.com/contactus/cu_sc_virsec_master?ws=support#tab3Microsoft Support Center consumer
https://consumersecuritysupport.Microsoft.com/default.aspx?altbrand=true&SD=GN&ln=en-us&St=1&wfxredirect=1&gssnb=1Microsoft technical support
http://support.Microsoft.com/contactus/?ws=support#TAB0Microsoft - contact technical support
http://Windows.Microsoft.com/en-us/Windows/help/contact-support=======================================================================
Search for malware and if none found you are probably OK. However, the real danger is obtained
computer information such as credit cards, banks and any other information that allows them to
to steal money or identity. If there is this type of information on the computer then you have to leave
your parents know of the issue, you should do anyway.As you say the story it doesn't sound like they had access to your computer for more than one
minute or two, or not at all. If that's true, you are so so good.If you need search malware here's my recommendations - they will allow you to
scrutiny and the withdrawal without ending up with a load of spyware programs running
resident who can cause as many questions as the malware and may be harder to detect as
the cause.No one program cannot be used to detect and remove any malware. Added that often easy
to detect malicious software often comes with a much harder to detect and remove the payload. Then
its best to be thorough than paying the high price later now too. Check with them to one
extreme overkill point and then run the cleaning only when you are sure that the system is clean.It can be made repeatedly in Mode safe - F8 tap that you start, however, you must also run
the regular windows when you can.TDSSKiller.exe. - Download the desktop - so go ahead and right-click on it - RUN AS ADMIN
It will display all the infections in the report after you run - if it will not run changed the name of
TDSSKiller.exe to tdsskiller.com. If she finds something or not does not mean that you should not
check with the other methods below.
http://support.Kaspersky.com/viruses/solutions?QID=208280684Download malwarebytes and scan with it, run MRT and add Prevx to be sure that he is gone.
(If Rootkits run UnHackMe)Download - SAVE - go to where you put it-right on - click RUN AS ADMIN
Malwarebytes - free
http://www.Malwarebytes.org/products/malwarebytes_freeSuperAntiSpyware Portable Scanner - free
http://www.SUPERAntiSpyware.com/portablescanner.HTML?tag=SAS_HOMEPAGERun the malware removal tool from Microsoft
Start - type in the search box-> find MRT top - right on - click RUN AS ADMIN.
You should get this tool and its updates via Windows updates - if necessary, you can
Download it here.Download - SAVE - go to where you put it-right on - click RUN AS ADMIN
(Then run MRT as shown above.)Microsoft Malicious - 32-bit removal tool
http://www.Microsoft.com/downloads/details.aspx?FamilyId=AD724AE0-E72D-4F54-9AB3-75B8EB148356&displaylang=enMicrosoft Malicious removal tool - 64 bit
http://www.Microsoft.com/downloads/details.aspx?FamilyId=585D2BDE-367F-495e-94E7-6349F4EFFC74&displaylang=enalso install Prevx to be sure that it is all gone.
Download - SAVE - go to where you put it-right on - click RUN AS ADMIN
Prevx - Home - free - small, fast, exceptional CLOUD protection, working with others
security programs. It is a single scanner, VERY EFFICIENT, if it finds something to come back
here or use Google to see how to remove.
http://www.prevx.com/ <-->
http://info.prevx.com/downloadcsi.asp?prevx=Y <-->Choice of PCmag editor - Prevx-
http://www.PCMag.com/Article2/0, 2817,2346862,00.aspTry the demo version of Hitman Pro:
Hitman Pro is a second scanner reviews, designed to save your computer from malicious software
(viruses, Trojans, rootkits, etc.). who infected your computer despite safe
what you have done (such as antivirus, firewall, etc.).
http://www.SurfRight.nl/en/hitmanpro--------------------------------------------------------
If necessary here are some free online scanners to help the
http://www.eset.com/onlinescan/
-----------------------------------
Original version is now replaced by the Microsoft Safety Scanner
http://OneCare.live.com/site/en-us/default.htmMicrosoft safety scanner
http://www.Microsoft.com/security/scanner/en-us/default.aspx----------------------------------
http://www.Kaspersky.com/virusscanner
Other tests free online
http://www.Google.com/search?hl=en&source=HP&q=antivirus+free+online+scan&AQ=f&OQ=&AQI=G1--------------------------------------------------------
After the removal of malicious programs:
Also follow these steps for the General corruption of cleaning and repair/replace damaged/missing
system files.Run DiskCleanup - start - all programs - Accessories - System Tools - Disk Cleanup
RUN - type in the box-
sfc/scannow
Then run checkdisk (chkdsk).
RUN - type in the box-
Chkdsk /f /r
-----------------------------------------------------------------------
If we find Rootkits use this thread and other suggestions. (Run UnHackMe)
================================
For extreme cases:
Norton Power Eraser - eliminates deeply embedded and difficult to remove crimeware
This traditional antivirus analysis does not always detect. Because the Norton Power Eraser
uses aggressive methods to detect these threats, there is a risk that it can select some
legitimate programs for removal. You should use this tool very carefully and only after
you have exhausted other options.
http://us.Norton.com/support/DIY/index.jsp================================
If you are in North America, you can call 866-727-2338 for virus and spyware help
infections. See http://www.microsoft.com/protect/support/default.mspx for more details. For
international information, see your subsidiary local Support site.Microsoft support - Virus and Security Solution Center
http://support.Microsoft.com/contactus/cu_sc_virsec_master?ws=support#TAB0I hope this helps.
Rob Brown - Microsoft MVP<- profile="" -="" windows="" expert="" -="" consumer="" :="" bicycle="" -="" mark="" twain="" said="" it="">
-
Why 10.2.0.4.0 is called Group patch 3?
I've been 10.2.0.1.0 to 10.2.0.4.0 passage. The YES said summary screen
"Oracle Database 10 g Release 2 Patch set 3 10.2.0.4.0 '.
Why is this? Is not this group of patches 4?
10 gr 2 database administrator guide, I've read about "Release Number Format.
The fourth digit on the left is called "Specific component version number" (do not know why they have not just named group number of patches). They did not mention how many group of hotfixes is determined.Hello
Very simple:
10.2.0.1.0 - release base
10.2.0.2.0 - patches 1 group
10.2.0.3.0 - 2 group of patches
10.2.0.4.0 - 3 Group of patchesHerald tiomela
http://htendam.WordPress.com -
Cannot call groups, cannot discuss in groups, cannot accept calls
Wow, it's frustrating. For the past 2 weeks, I have not been able to make group calls. I can call people, but no groups, the buttons are gray.
When someone calls me, in a group call, I can't accept the call, there is no button to accept, see attached.
Group messages are not delivered.
My ability to do business is totally dependent on Skype and now it is messed up.
Any help? I already uninstalled and reinstalled, which did not help.
This problem is solved on its own a few days ago. He just started working again.
-
Way to do so only certain people can call groups
I was wondering if there was a way to make sure only certain people/roles can call a moderate group of Skype. Thank you

I thought about it
-
Mysterious user account appeared in the Administrators group - should I remove it?
I recently noticed that a user account has been done on my computer in the Administrators group. The account name is a random combination of 12 characters of letters, and I know that I did not. In addition, no one else was using my computer. What is the hidden "Super-Administrator" account or is this a sign that my computer has been hacked? In other words, should I delete the account?
I am running Vista Business and I recently installed Vista Service Pack 2, but I don't know if this is related.
Also, I searched for an answer on the internet for an hour and found nothing.
Hello
Create a new ADMIN account with the same password 1 - always keep an unused ADMIN account to fix
and test.Make a Restore Point - delete the account - do another restore point and check the system for malware.
How to create a Vista System Restore Point
http://www.Vistax64.com/tutorials/76332-system-restore-point-create.htmlHow to make a Vista system restore
http://www.Vistax64.com/tutorials/76905-System-Restore-how.html download malwarebytes and scan with it, run MRT and add Prevx to be sure that he is gone. (If Rootkits run UnHackMe)Download - SAVE - go to where you put it-right on - click RUN AS ADMIN
Malwarebytes - free
http://www.Malwarebytes.org/Run the malware removal tool from Microsoft
Start - type in the search box-> find MRT top - right on - click RUN AS ADMIN.
You should get this tool and its updates via Windows updates - if necessary, you can download it here.
Download - SAVE - go to where you put it-right on - click RUN AS ADMIN
(Then run MRT as shown above.)Microsoft Malicious - 32-bit removal tool
http://www.Microsoft.com/downloads/details.aspx?FamilyId=AD724AE0-E72D-4F54-9AB3-75B8EB148356&displaylang=enMicrosoft Malicious removal tool - 64 bit
http://www.Microsoft.com/downloads/details.aspx?FamilyId=585D2BDE-367F-495e-94E7-6349F4EFFC74&displaylang=enalso install Prevx to be sure that it is all gone.
Download - SAVE - go to where you put it-right on - click RUN AS ADMIN
Prevx - Home - free - small, fast, exceptional CLOUD protection, working with other security programs. It comes
a scan only, VERY EFFICIENT, if it finds something to come back here or use Google to see how to remove.
http://www.prevx.com/ <-->
http://info.prevx.com/downloadcsi.asp <-->Choice of PCmag editor - Prevx-
http://www.PCMag.com/Article2/0, 2817,2346862,00.asp--------------------------------------------------------
If necessary here are some free online scanners to help the
http://www.eset.com/onlinescan/
http://www.Kaspersky.com/virusscanner
Other tests free online
http://www.Google.com/search?hl=en&source=HP&q=antivirus+free+online+scan&AQ=f&OQ=&AQI=G1--------------------------------------------------------
Also do to the General corruption of cleaning and repair/replace damaged/missing system files.
Run DiskCleanup - start - all programs - Accessories - System Tools - Disk Cleanup
Start - type this in the search box-> find COMMAND at the top and RIGHT CLICK – RUN AS ADMIN
Enter this at the command prompt - sfc/scannow
How to analyze the log file entries that the Microsoft Windows Resource Checker (SFC.exe) program
generates in Windows Vista cbs.log
http://support.Microsoft.com/kb/928228Run checkdisk - schedule it to run at the next startup, then apply OK then restart your way.
How to run the check disk at startup in Vista
http://www.Vistax64.com/tutorials/67612-check-disk-Chkdsk.html-----------------------------------------------------------------------
If we find Rootkits use this thread and other suggestions. (Run UnHackMe)
I hope this helps.
Rob - bicycle - Mark Twain said it is good.
-
Only specific groups should get authenticated on ISE instead of the entire announcement
Hello friends,
I have integrated ISE to RFA, but all users of the AD are get authenticated against my network devices and get landed in exec mode, if these users have privileges to perform the configuration, network admins are able to do it because I defined the names of groups admin in the authorization policy, now I want to set only the names of specific groups in the authentication instead of the name of ads policy is it possible to do?
Thanks in advance.
Best regards / Tash
This does not work, have you added the groups you wan't to check for membership in the menu external identity Sources / Active Directory/AD-name/groups? Those that you add, you should see when you press on the + sign next to 'if' and select the name you gave your definition of external advertising.
-
Hi all
I want to install Oracle 11 g on linux Server 6.
I have some confusion regarding the creation of groups in linux
What is the difference between dba & oinstall group.
For the installation of database do I need to create the two groups?
What is the importance of creating groups.
Also in the event that we need to create the two groups then that should be the main group & that one must be secondary.
Thank you.
oinstall is the owner of the software group and inventory.
DBA is the management group.
Oracle is normally installed with oinstall as the primary group and dba as the additional group.
Hemant K Collette
Maybe you are looking for
-
Impossible to restart my Mac Book Pro, blocked by the old printer icon
I can't reboot my mac to complete book download updates because it is blocked by the former icon of the printer that I can not delete - have deleted the program, but the icon remains open but out of order on the toolbar can anyone help Jules
-
Satellite Pro NB10t-A-108 - Windows 8 PRO is equal to 8.1 Windows
http://www.Toshiba.de/discontinued-p...o-nb10t-a-108/ Satellite Pro NB10t-A-108. PU143E-00200FGR.In German: Windows 8 64-bit (one) auf Empfohlenes update Windows 8 Pro. Intel® Celeron®. What means "Windows 8 Pro" on the Internetside Thoshiba?Is equiv
-
I have problems using the command 'writing of the waveform to the file. Perhaps the problem lies elsewhere. The problem is that even if the path is correct on my front panel indicator, a file is never created. The path to the file is created by using
-
My laptop does not do anything on the screen
My laptop does not appear anything just blank black screen when I start my system
-
Search, find and open a file list
I have a list of files in a spreadsheet without the extension, and I want to simultaneously open pdf files associated with them. The files are on a server in different directories.It is a unique file name. Is it possible to automate the windows with