Problem to apply conditions to the cuurent group - model of implementation of the RTF data
Hi allHere is my example of XML data generated by the report:
< DATA >
< DT >
< CORPORATION >
Vision of < NAME > < / NAME >
< EMPLOYEE >
< EMPNO > 6 < / EMPNO >
Walker Rich < ENAME > < / ENAME >
CLERK of < JOB > < / JOB >
< SAL > 100 < / SAL >
< Dept > IT < / Dept >
< / EMPLOYEE >
< EMPLOYEE >
< EMPNO > 5 < / EMPNO >
Russ Kepel < ENAME > < / ENAME >
CLERK of < JOB > < / JOB >
< SAL > 100 < / SAL >
< Dept > ACCNT < / Dept >
< / EMPLOYEE >
< / COMPANY >
< /DT >
< Main_XML >
rowset <>
Department < and >
< Dept > IT < / Dept >
< DName > Information technology < / DName >
< Text > welcome to the Dept IT < / text >
< / Department >
< / LINES >
rowset <>
Department < and >
< Dept > ACCNT < / Dept >
Accounting < DName > < / DName >
< Text > welcome to the accounting department < / text >
< / Department >
< / LINES >
< / Main_XML >
< / DATA >
I would need to create a rtf model to display the following for all employees:
EmpNo
Ename
Job
SAL
Name of Dept
text
Here is the design of rtf, I created which is does not give me the desired result:
<? for-each-group: USED; / EMPNO? >
EMP: EMPNO
ENAME
JOB
SAL
Dept
<? for-each - group:current-group(); / Dept? >
<? If: Dept = Dept? >
DName
Text
<? end if? >
<? end for each group -? >
<? end for each group -? >
Please guide me how can I apply a condition to the previous group data in the current group. Thanks in advance.
Try this:
Declare a variable external/first group
You can get rid of the second group and insert the DName field under Dept field and modify the code to include the following:
Insert the text field and modify the code to include the following:
Thank you
BIPuser
Tags: Business Intelligence
Similar Questions
-
Restrict the condition on the query data - help.
I want to restrict the query with the following condition data. I can't get the syntax right. Any help is appreciated
Select *...
Of...
where ps.name in ('black' or ('color' and not 'film') or ('film'))OAF - dev wrote:
I want to restrict the query with the following condition data. I can't get the syntax right. Any help is appreciatedSelect *...
Of...
where ps.name in ('black' or ('color' and not 'film') or ('film'))select * from ... where ps.name in ('black', 'color', 'film')list of all the options that you want to match before 'film', to 'film' last.
Published by: user142857 on November 16, 2009 13:04
-
Apply the Condition to the content of paragraph
Hello
I want to apply a condition to a paragraph. In some cases, I only want to apply the condition until paragraph return, but does not include the return. Here's a function that works for entire paragraphs, but I'm not sure what to use when I want to let the unconditional return. Any help would be appreciated.
function applyCondition (pgf, condName, includeReturn, doc) { condName = String(condName); var condFmt = doc.conditions.itemByName(condName) ; if (condFmt.isValid === false) { // If the condition does not exist, create it. doc.conditions.add ({name: condName}); } // Make sure the condition is visible. condFmt.visible = true; if (includeReturn === true) { // Apply the condition to the entire paragraph. pgf.applyConditions (condFmt, true); } else { // Apply the condition to the paragraph up to the return. } }Rick
Hi Rick
I think there must be a myriad of solutions for that one.
Probably the simplest is:
pgf.characters.itemByRange(0,-2).applyConditions (condFmt, true);
That's assuming that "TFP" is a reference to a paragraph of the object.
Concerning
Trevor
-
Apply the condition on the page to allow access if Javascript is enabled
Hi, is there a way I can put a condition on the page to allow access allow access only if java script is enabled?
I have a heavy use of Javascript to calculate different values in a page and want to ensure that if Javascript is not enabled in the browser they do not get to use the page.
Using Apex 4.1.1
See you soon.Xrc xarg wrote:
Hi, is there a way I can put a condition on the page to allow access allow access only if java script is enabled?I have a heavy use of Javascript to calculate different values in a page and want to ensure that if Javascript is not enabled in the browser they do not get to use the page.
APEX is JavaScript-dependent, it is unlikely that users will even be able to log in and access this page, unless you already take steps throughout the application to allow it to work with JS disabled.
Also note that for security reasons all depends on the JS in the browser must be verified on the server when the page is sent.
-
apply restrictions for the non-linear curve fit
Hello Forum users,.
I am currently working on a VI control which is supposed to create a specific model of pressure inside a hollow tube to provide a test environment for pressure sensors. The details are many and complicated, so let's say I am sure that my formula to calculate this profile according to the pressures inside the hollow rings around this tube will work.
To find the correct pressure for each ring values, I've linked to a model VI containing this form to Lev. - Mar algorithm (the non-linear curve adjustment) and let it run.
Technically, there is no problem and Lev - Mar find values to adjust the function for the values (not perfectly sure, but close enough).
The problem is, however, that, since the device, once suitable values for the positioning and size of the rings are found, must be built, the simulated pressure rings perhaps intersect not between them. To apply this rule, I added a check to my VI of model and if the values passed to Lev - Mar breaking the rules, the VI model gives a matrix of zeros to follow him (I tried an empty array, but that only leads to error messages).
This solution did not work. Lev - Mar seems to ignore these cases always looks for values that break my rules (and if I put these values through my model VI, I get a matrix of zeros, as expected, so the audit seems to work).
Perhaps I misunderstood the algorithm of Lev - Mar and it does not actually check each possible defined coefficients of finds.
Is it possible to adapt to any function of a set of values while keeping the predefined boundary conditions?
Oh, before I forget:
I use LabVIEW version 8.2 in the Institute, because the workshop systems is not installed 8.5 for some reason any.
Thanks in advance
Thaliur
Hi Thaliur,
Thanks for posting on our forums.
I understand your request you expect the algorithm to ignore a case to all zeros in the table. However, it is not implemented like this.
Good news is, its source code can be edited and you could save your own personalized version of the algorithm of screws it is to you that you just add a check for a matrix of zeros or simply pass another parameter which indicates only a case of "broken rules". Then you would not have to continue the calculation.
If I misunderstood your question, please clarify this. You can also post a code for further explanation, if you wish.
Good luck with the project!
Peter
-
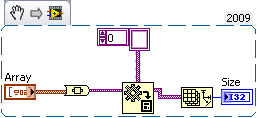
Problem of brick wall: clusters, the size of the reference table
Good morning forums,
I hit a brick wall with my application and I hope someone can help!
I have an array of clusters of size for an indeterminate period (the cluster is generic and data contained irrelevant.).
Entries to the VI are: a reference to the matrix and a Variant that contains the data.
My problem is that I need to determine the size of these two entries in table and I can't find a way to do it!
If the table contained a standard data type I can use the class name property to determine the data type and the size of the array returned by the property "select size" to determine the size of the dimension. With this information, I can throw the variant into the correct data type and use it to determine the size of the array. If the data is a cluster to the name class simply returns 'cluster' then I'm so not able to determine the size and can't get the Variant.
I'm not worried about the casting of data (once I've determined the size this bit is childless), I just need determine the size (and preferably number of dimensions) of the array. Is this possible?
Cheers for any help
J
Use 'Variant to data change' variant of an array of variant and take the importance of that.
Ed.
Opps missed the variable number of condition of dimensions, in this case, you want to "Format Picture" of OpenG as mentioned blawson.
-
Z230: Problems of mouse HP over the weekend.
We have several thin lines HPZ230 in our environment, and over the weekend, some of them decided to not recognize the HP USB mouse wired that came with the system. I tried disconnecting and reconnecting, restarting, even a restoration of the system on one of them to a week ago, however, none of this solves the problem. The only solution I have at the moment is to plug any other mouse brand in the PC that solves the problem for the other mice of the brand. I tried to return the updates of Windows who applied over the weekend, and again, this does not resolve the issue. I tried to reinstall the USB drivers as well with no luck on the HP mouse. The keyboards work fine, it's only a mouse problem.
Just had the same problem on a Dell PC with one of the same HP attached, mouse and it seems to affect Windows 8.1 and Windows 10. The mouse is misidentified as a HP USB - C for DisplayPort adapter. You can right click on the mouse in Device Manager, click on 'Update driver', then click on "Browse my computer for driver software", then "Let me pick from a list of drivers for devices on my computer. You will be offered an additional choice (I forgot the formulation that I am not the PC a plus, but it's a very bland USB device). What to choose and say hello to your mouse pointer.
-
Problem with remote access in a residential group
Having a problem with desktop sharing remote within a group of home access. I don't have problem of access to the desktop from the laptop, but for some reason I can't access the laptop from the desktop. I tried everything I could think of. Remote access is enabled on both PCs. Help, please. Thank you very much!
Hello
1. who is the operating system installed on the desktop and laptop computers?
2. what happens when you try to access the laptop from the desktop? You receive an error message?
3. What are troubleshooting you performed?
I suggest you follow these methods and check.
In a first step of troubleshooting, I suggest to run the troubleshooter to group on the source and the destination computer.
Step 1: Open the troubleshooter group living
If your computer has problems viewing computers or files shared in your collective housing, try to use the collective dwelling Troubleshooter to fix the problem
http://Windows.Microsoft.com/en-us/Windows7/open-the-HomeGroup-Troubleshooter
Step 2: Share files and folders on a group of houses in the laptop using the method proposed below. Try to access from desktop and check.
a. right click on the item you want to share, and then click share with.
b. Select Home Group (read/write)
c. this option share point with your entire Home Group and allows them to open, edit, or delete.
Share files with someone: http://Windows.Microsoft.com/en-us/Windows7/share-files-with-someone
See also:
Home Group: frequently asked questions
http://Windows.Microsoft.com/en-us/Windows7/HomeGroup-frequently-asked-questionsI hope this helps!
-
Multiplexing of signals microvolt and conditioning of the right signals
Hello
We have 22 signals in our system. We must be able to measure any subset of these 22 signals. Usually, we carry out a number of measures IV 4points of separate devices on a SUT (sample to be analyzed). Two of the 22 signals may represent the pair of voltage measure 4-point IV, depending on how it was KNOWN is bonded. The level of the signal of tensions is in the 100s in the uV range and I need a precision as much as possible, so the unit or same sup - uV numbers. So far, we had all the 22 signals connected to a box (selfmade) acting as a distribution point, where a connector (SMB) is available for each signal. We then manually choose which two of the 22 that signals will be connected to a differential amplifier silent instrumentation (also selfbuilt), according to it was KNOWN patterns of liaison. The amplifier with a gain of typically 1000, returns the signal to an acquisition card. The current (excitation) is read separately.
There is a problem with that. We need to manually switch the connectors in the distribution box to select a different device on it was KNOWN and flows to the amplifier. This is not good for a number of reasons that I can't go here.
Therefore, I would like to multiplex these 22 signals to several outputs (for future scalability) who will be wired for the conditioning of signals. There is no manual connection/disconnection of these signals in this way. The first question is: can a matrix switch or multiplexer be used to route signals reliable microvolt? If so, then what kind: electromechanical, Reed relay or a transistor? Is the thermal EMF in the specifications of multiplexer/matrix relay just a lag, or is - that noise?
The second question is: what card/signal acquisition solution (so no selfmade equipment and legacy) products OR only using the same line that the matrix/mux can reach 1uV accuracy of treatment? For us, offset offset is not a problem since we measure the device in 2 quadrants and later cancel it in the software but the noise (and get the accuracy) is important. Our amplifier has a background noise of 3nV/sqrtHz and a bandwidth of 15 kHz. The system to replace must be comparable. I have the choice between:
- the SCXI based ones, instrumentation isolation (4ch) 1121 or 1122 amplifier modules (16 channels), with a ground noise that I calculate 20 and 30nV/sqrtHz respectively. They already have some functions of multiplexing btw.
- the PXI 628 x with a background noise that I calculate through 10nV/sqrtHz
- the PXI 446 x with the noise floor low 8nV/sqrtHz as stated in the technical data sheet
Module 4-way universal 24-bit NI 9219, who works with 2 samples per second has a very low noise total, but at a very low sampling frequency and I can't consider comparable to what we have now. In addition, the system must be able to have a few kHz bandwidth for dynamic action in the future.
Y at - it any other ideas?
Greetings
Aleksandar Andreski
-
Original title: I have installed Windows Vista SP1. I accept the conditions and the installation ends... but there is no SP1 is installed. I tried a few times, but the same story.
I have installed Windows Vista SP1. I accept the conditions and the installation ends... but there is no SP1 is installed. I tried a few times, but the same story. I'm I did somenthing evil?
Hello
Thanks for posting in the Microsoft Community.
If I understand correctly that you have problems with the installation of Windows Vista Service Pack 1.
Please answer these questions:
It shows in system properties?
To open system properties:
(a) click Start, right click on computer
(b) click on properties
(c) see if it shows Windows Vista with service pack 1 on windows edition.
Hope the helps of information. We know if you need help. We will be happy to help you.
-
I have reported this problem on my PC at home that connects to the internet. My laptop runs Vista Home Premium and I can't connect to the internet. I took my laptop on a trip, tried to connect to the wireless network that was free to the place we are. Could not connect, and after this initial test, the following is displayed after the start of "failed to connect to the Windows Service, Windows cannot connect to the system event notification service. This problem prevents limited users to logon to the system. As administratvie user, you can view the system event log to see why the service did not respond. "(have no idea how or what it means) when I go to the task bar you want to connect to a network, it is said:" the dependency service or group could not start"and if I go ahead and press"connect to a network"it says it can't find. I search for computers on the network (who I'm sitting next to) and then try to diagnose the problem and it cannot. I have limited knowledge of this type of problem. Anyone have this problem and how to fix it?
Hi ptkein,
Thanks for posting your question on the Forums of Windows Vista.
Option 1: You can download and install the latest network card drivers and see if that can solve the problem.
Option 2: Follow the link below to fix network connection problems
http://Windows.Microsoft.com/en-us/Windows-Vista/troubleshoot-network-connection-problems
Option 3: Follow the link below to solve Internet connection problems
http://Windows.Microsoft.com/en-us/Windows-Vista/troubleshoot-Internet-connection-problems
Option 4: To verify if a third party application is a cause, follow this link (http://windows.microsoft.com/en-us/windows-vista/Advanced-startup-options-including-safe-mode) for this boot to the desktop using the safe mode with networking option and try to install the network. If the problem is resolved, you will need to perform a clean boot by following the steps in the following article to refine the exact source and isolate it: http://support.microsoft.com/kb/929135
Let me know if it worked.
Hope it will be useful.
Thank you and best regards,
Kadoch - Microsoft Support
Visit our Microsoft answers feedback Forum and let us know what you think.
-
While from my account on my computer Win 7 Ultimate I get constantly interrupted with the following error, having appeared on the screen.
RunDll error (X) there is a problem from C:\Users\ "X" the specified Module could not be found.
I saw the file tree and (newly) noticed that there are a number of directories that show a locked state.
I tried then access these locked directories showing locked and have encountered the error
C:\Users\ (X) 'X' is not accessible, access is denied.
I then tried to change the security permissions on these locked folders... Right click... Properties... Security... Edit... User "X"... Allow check... Apply... OK.
AND yet once I met the other mistake
Error (X), there was an error applying security... An error has occurred applying security information to: C:\Users\ 'X' access denied.
So that's where I'm stuck... I get errors. I'm doing the Correct (I think) security fixes and I am met with a stonewall by the computer? I'm I have done this correctly? The computer is damaged by a virus? (I don't think), I have use controls many security I.e.... IOBIT Malware, AVG Antivirus, Rootkit, Microsoft, etc. and regular analyses. In fact I probably spend more time computer maintenance then enjoyment... :-)
Thank you all who may be able to help or know a workaround for this problem... Thanks a lot for your comments.
........ Content of the lead in double...
I already posted this Question under Security, issues of privacy and also accounts, but it seems that the error also happens with IE explore 11. The error comes back constantly, but more often in the browser.
Entitled RunDll error: there was a problem starting C:\Users\X the specified Module could not be found. Well that begins my account on my computer Win 7 Ultimate I get constantly interrupted with the following error, having appeared on the screen.
RunDll error (X) there is a problem from C:\Users\ "X" the specified Module could not be found.
I saw the file tree and (newly) noticed that there are a number of directories that show a locked state.
I tried then access these locked directories showing locked and have encountered the error
C:\Users\ (X) 'X' is not accessible, access is denied.
I then tried to change the security permissions on these locked folders... Right click... Properties... Security... Edit... User "X"... Allow check... Apply... OK.
AND yet once I met the other mistake
Error (X), there was an error applying security... An error has occurred applying security information to: C:\Users\ 'X' access denied.
So that's where I'm stuck... I get errors. I'm doing the Correct (I think) security fixes and I am met with a stonewall by the computer? I'm I have done this correctly? The computer is damaged by a virus? (I don't think), I have use controls many security I.e.... IOBIT Malware, AVG Antivirus, Rootkit, Microsoft, etc. and regular analyses. In fact I probably spend more time computer maintenance then enjoyment... :-)
Thank you all who may be able to help or know a workaround for this problem... Thanks a lot for your comments.
Hi Barry,.
Sorry for the late reply.
The Internet Explorer cannot be uninstalled. However you can disable/enable what works as the resettlement.
How to repair or reinstall Internet Explorer in Windows
https://support.Microsoft.com/en-us/KB/318378?WA=wsignin1.0
Keep us informed on the issue.
-
An error occurred applying attributes to the file. Access is denied?
Hello
I use Windows 7. I reinstall my Windows 7 and since then, most of my file become encrypted (Green shows in Explorer).
I came across a strange behavior where I am not able to use or to decrypt files. I dint knew the encryption.
I am the administrator on my computer running Windows 7. I get the following error
--------
An error occurred applying attributes to the file.
Access is denied.
--------I have no key encryption nor do I created everything.
I tried the following:
When I right click on the file > properties > go to advance > uncheck the encryption > apply changes > continue (user account control) > I get this..."An error occurred applying attributes to the file:
C:\Program Files\Windows Collaboration
Access is denied.
Ignore. Ignore everything. Try again. Cancel. »
It is a small very annoying problem that I need to have go further, any help would be appreciated!
Points to note:
Safe MODE does not help.
I am logged on as administrator, what makes it more frustrating.I do not know of the all other folders that Act up like this.
Please let me know what happens! THESE FILES ARE VERY IMPORTANT
Hello
1. what security software is installed on the computer?
2. what version of windows 7 is installed on the computer?
3. of what exact file you try to remove the encryption?
4. have you installed windows on the C partition or another partition?
Method 1.
To resolve this issue, give the system security principal of full control on the System Volume Information folder.
NOTE: The System Volume Information folder is a hidden operating system folder. To display the folder in Windows Explorer, follow these steps:
1. in the Tools menu, click Folder Options.
2. on the view tab, clear the Hide protected operating system files check box.
Follow the steps in this article and give full control permission to the folder. Appropriating a file or a folder: http://technet.microsoft.com/en-us/library/cc753659.aspx
Method 2.
I would like to create a new user account and check if the problem still persists.
Create a user account: http://windows.microsoft.com/en-IN/windows7/Create-a-user-account
If the problem does not occur in the new user account, you can transfer the files from the damaged to the new user account by using the article user account "difficulty a user profile is corrupted.
Difficulty a user profile is corrupted: http://Windows.Microsoft.com/en-us/Windows7/fix-a-corrupted-user-profile
Method 3.
You can run the Microsoft Safety Scanner to make sure that the computer is virus-free.
Microsoft safety scanner: http://www.microsoft.com/security/scanner/en-us/default.aspx
Warning of Security Scanner: there could be a loss of data while performing an analysis using the Microsoft safety scanner to eliminate viruses as appropriate.
For more information: the file must be decrypted by the user who encrypted the file. The files are encrypted using the Encrypting File System (EFS) are accessible only to the person who encrypted the file, regardless of the other permissions on the file.
I suggest you to visit these links for more information:
http://Windows.Microsoft.com/en-us/Windows7/encrypt-or-decrypt-a-folder-or-file
http://Windows.Microsoft.com/en-us/Windows7/use-a-smart-card-for-file-encryption
http://Windows.Microsoft.com/en-us/Windows7/what-is-encrypting-file-system-EFS
I hope this helps.
-
Problem with VPN client connecting the PIX of IPSec.
PIX # 17 Sep 14:58:51 [IKEv1 DEBUG]: IP = Y, IKE Peer included IKE fragmentation capability flags: Main Mode: real aggressive Mode: false
Sep 17 14:58:51 [IKEv1]: IP = Y, landed on tunnel_group connection
Sep 17 14:58:51 [IKEv1 DEBUG]: Group = X, IP = Y, IKE SA proposal # 1, transform # 13 entry overall IKE acceptable matches # 1
Sep 17 14:58:58 [IKEv1]: Group = X, Username = X, IP = Y, the authenticated user (X).
Sep 17 14:58:58 [IKEv1]: Group = X, Username = X, IP = Y, mode of transaction attribute not supported received: 5
Sep 17 14:58:58 [IKEv1]: Group = X, Username = X, Y = IP, Type of customer: Client Windows NT Version of the Application: 5.0.06.0160
Sep 17 14:58:58 [IKEv1]: Group = Xe, Username = X, IP = Y, assigned private IP 10.0.1.7 remote user address
Sep 17 14:58:58 [IKEv1 DEBUG]: Group = X, Username = X, IP = Y, fast Mode resumed treatment, Cert/Trans Exch/RM IDDM
Sep 17 14:58:58 [IKEv1]: Group = X, Username = X, IP = Y, PHASE 1 COMPLETED
Sep 17 14:58:58 [IKEv1]: IP = Y, Keep-alive type for this connection: DPD
Sep 17 14:58:58 [IKEv1 DEBUG]: Group = X, Username = X, Y = IP, timer to generate a new key to start P1: 6840 seconds.
Sep 17 14:58:58 [IKEv1]: Group = X, Username = X, Y = IP, data received in payload ID remote Proxy Host: address 10.0.1.7, protocol 0, Port 0
Sep 17 14:58:58 [IKEv1]: Group = X, Username = X, IP = Y, received data IP Proxy local subnet in payload ID: address 0.0.0.0 Mask 0.0.0.0, protocol 0, Port 0
Sep 17 14:58:58 [IKEv1]: Group = X, Username = X, IP = Y, his old QM IsRekeyed not found addr
Sep 17 14:58:58 [IKEv1]: Group = X, Username = X, Y = IP, remote peer IKE configured crypto card: outside_dyn_map
Sep 17 14:58:58 [IKEv1 DEBUG]: Group = X, Username = X, Y = IP, IPSec processing SA payload
Sep 17 14:58:58 [IKEv1 DEBUG]: Group = X, Username = X, Y = IP, IPSec SA proposal # 14, turn # 1 entry overall SA IPSec acceptable matches # 20
Sep 17 14:58:58 [IKEv1]: Group = X, Username = X, IP = Y, IKE: asking SPI!
Sep 17 14:58:58 [IKEv1]: Group = X, Username = X, Y = IP, IPSec initiator of the substitution of regeneration of the key duration to 2147483 to 7200 seconds
Sep 17 14:58:58 [IKEv1 DEBUG]: Group = X, Username = X, IP = Y, passing the Id of the Proxy:
Remote host: 10.0.1.7 Protocol Port 0 0
Local subnet: 0.0.0.0 mask 0.0.0.0 Protocol Port 0 0
Sep 17 14:58:58 [IKEv1 DEBUG]: Group = X, Username = X, IP = notification sending answering MACHINE service LIFE of the initiator
Sep 17 14:58:58 [IKEv1]: Group = X, Username = X, IP = Y, the security negotiation is complete for the user (slalanne) answering machine, Inbound SPI = 0 x 6
044adb5, outbound SPI = 0xcd82f95e
Sep 17 14:58:58 [IKEv1 DEBUG]: Group = X, Username = X, Y = IP, timer to generate a new key to start P2: 6840 seconds.
Sep 17 14:58:58 [IKEv1]: Group = X, Username = X, IP = Y, adding static route to the customer's address: 10.0.1.7
Sep 17 14:58:58 [IKEv1]: Group = X, Username = X, IP = Y, PHASE 2 COMPLETED (msgid = c4d80320)
PIX # 17 Sep 14:59:40 [IKEv1]: Group = X, Username = X, Y = IP, Connection over for homologous X. Reason: Peer terminate remote Proxy 10.0.1.7, 0.0.0.0Sep Proxy Local 17 14:59:40 [IKEv1 DEBUG]: Group = X, Username = X, IP = Y, IKE removing SA: 10.0.1.7 Remote Proxy, Proxy Local 0.0.0.0
Sep 17 14:59:40 [IKEv1]: IP = Y, encrypted packet received with any HIS correspondent, drop
Then debugging IPSec are also normal.
Now this user is a disconnect and other clients to connect normally. the former user is trying to connect to the site and here is the difference in debugging:
Sep 17 14:25:22 [IKEv1]: Group = X, Username = X, Y = IP, tunnel IPSec rejecting: no entry card crypto for remote proxy proxy 10.0.1.8/255.255.255.255/0/0 local 0.0.0.0/0.0.0.0/0/0 on the interface outside
Sep 17 14:25:22 [IKEv1]: Group = X, Username = X, IP = Y, error QM WSF (P2 struct & 0x2a5fd68, mess id 0x16b59315).
Sep 17 14:25:22 [IKEv1 DEBUG]: Group = X, Username = X, IP = O, case of mistaken IKE responder QM WSF (struct & 0x2a5fd68), :
QM_DONE, EV_ERROR--> QM_BLD_MSG2, EV_NEGO_SA--> QM_BLD_MSG2, EV_IS_REKEY--> QM_BL
D_MSG2, EV_CONFIRM_SA--> QM_BLD_MSG2, EV_PROC_MSG--> QM_BLD_MSG2, EV_HASH_OK--> QM_
BLD_MSG2, NullEvent--> QM_BLD_MSG2, EV_COMP_HASH
Sep 17 14:25:22 [IKEv1]: Group = X, Username = X, IP = Y, peer table correlator withdrawal failed, no match!
Sep 17 14:25:22 [IKEv1]: IP = Y, encrypted packet received with any HIS correspondent, dropHere is the config VPN... and I don't see what the problem is:
Dynamic crypto map outside_dyn_map 20 match address outside_cryptomap_dyn_20
Crypto-map dynamic outside_dyn_map 20 the transform-set ESP-DES-MD5 value
life together - the association of security crypto dynamic-map outside_dyn_map 20 seconds 7200
map outside_map 65535-isakmp ipsec crypto dynamic outside_dyn_map
outside_map interface card crypto outside
ISAKMP crypto identity hostname
crypto ISAKMP allow outside
crypto ISAKMP policy 20
preshared authentication
the Encryption
md5 hash
Group 2
life 7200
crypto ISAKMP policy 65535
preshared authentication
the Encryption
sha hash
Group 2
life 86400outside_cryptomap_dyn_20 list of allowed ip extended access any 10.0.1.0 255.255.255.248
attributes global-tunnel-group DefaultRAGroup
authentication-server-group (outside LOCAL)
Type-X group tunnel ipsec-ra
tunnel-group X general attributes
address pool addresses
authentication-server-group (outside LOCAL)
Group Policy - by default-X
tunnel-group X ipsec-attributes
pre-shared-key *.
context of prompt hostnamemask of 10.0.1.6 - 10.0.1.40 IP local pool 255.255.255.0
Please remove the acl of the dynamic encryption card crypto, it causes odd behavior
try to use split instead of the acl acl in dynamic crypto map, and let me know how it goes
-
Problems with VPN tunnels after the upgrade to PIX 7.0
It seems that Cisco has revamped the VPN process on the new Version of PIX 7.0.
After I've upgraded, I noticed that AH (i.e. ah-sha-hmac, ah-md5-hmac) was no longer supported and all my container transformation games OH no were not converted.
Another question, if you have enabled on Versieon 6.3, names when you upgrade, tunnel groups will be created (formerly "identity isakmp crypto, crypto key
isakmp peer ') which will include a hostname (hostname of identity) instead of IP as it was to the point 6.3. Guess what... Nothing works! Having to delete and recreate it using the IP address. See an example...
tunnel-group OTHER_END type ipsec-l2l
IPSec-attributes tunnel-group OTHER_END
pre-shared-key *.
The above does not work... Having to recreate using the IP address mapped to OTHER_END...
tunnel-group 2.2.2.2 type ipsec-l2l
2.2.2.2 tunnel-group ipsec-attributes
pre-shared-key *.
Furthermore, I have problems with my racoon and freeswan extranet... Did someone recently updated with success and other gateways VPN provider (i.e. checkpoint, Freeswan and Racoon) work?
We found the solution for this problem. It appeared that the perfect forward secrecy is enabled at the other side. If a 'card crypto outside_map 10 set pfs' is necessary. With the pix 6.3 version that appears not to make the difference, the vpn works even with pfs disabled on the side of pix.
Maybe you are looking for
-
macOS keeps the nagging on the activation of Siri
Hey all,. I installed Sierra and I think I rushed. Should have waited. I don't want to use Siri at all, so I went into system preferences and disabled, but he began to appear in the dialog box 'Do you want to activate Siri?' - and hit 'Cancel' help o
-
Finder windows does not display the content
I have a Pre MacBrook, retina, 13-inch, early 2013 with a 2.6 GHz Intel Core i5, 8 GB memory, OS x 10.9.5. Today, my Finder became unstable. When I open a Finder window, it is empty and sometimes even shows the desktop or parts of the application 'th
-
Satellite L10 - problems with my Wi - Fi button
Hi guys. I'm new to this forum so please be gentle with me. My Satellite L10 cut last week and I have problems getting the wireless on again.I was on the button since but without success. Everyone knows that before and someone has suggestions or cons
-
I use 2 timed loop and a while loop in the same case statement. When I called the case the first time, it runs as expected. However, when I call the case subsequent times, the loops initially timed races and has indicated that there is an end loop