Question of redundancy VPN l2l using 2811 as endpoint devices
I have a new implementation of VPN L2L passes using two 2811 s than VPN terminal devices. I'll try to use the HSRP address between the public interfaces of both routers as VPN peer address. The problem that I found during the test is that the tunnel will become active and debugs watch the HSRP address as an invalid address to form the tunnel. Have a work-around, or a better plan for redundancy on peering address using similar devices? Thanks in advance.
Take a look at this doc about IOS IPSec HA.
Tags: Cisco Security
Similar Questions
-
Using VPN L2L static and dynamic dedicated tunnels
We have an ASA 5510 running 8.0 at our company headquarters. We have remote sites who need to create VPN L2L at the HQ ASA tunnels. Some remote sites have static IP addresses and others have dynamic IP addresses.
I found documentation Cisco L2L static IP VPN tunnels and make them work. I found another Cisco documentation for static IP dynamic L2L VPN tunnels using the tunnel-group "DefaultL2LGroup".
My question is, can you have two types of tunnels on the same ASA L2L? If so, simply by using the definitions of "DefaultL2LGroup" tunnel-group and
of tunnel-group work? Is there a reason to not do? Is better technology (ASA HQ and a combination of ASA 5505 and 1861 at remote sites) available? Yes, you can have both types of tunnels L2L. If you use a PSK - remember that the IP address of the remote site is used to 'validate' to connect to Headquarters. As long as you use a sure PSK = 64 characters and all with upper/lower case alpha numeric - you should be OK.
A better way to do it - is to get the static IP addresses for the site that currently have DHCP from ISP.
HTH >
-
2811: connecting two VPN l2l ASA5505
Hello
We have a HQ site with a 2811 (w/ADVSECURITYK9-M) acting as the firewall. We currently have 1 ASA5505 with an established ipsec VPN l2l.
I'm trying to connect a 2nd ASA, but I noticed that I only add 1 cryptomap to the external interface.
A worm watch 1 Module of virtual private network... Surely this does not mean only 1 VPN?
Can I use a card encryption and add a second "peer set" & "corresponds to" address inside the card Cryptography itself?
Thank you
Jason
Yes, you add another poicy to your configuration encryption.
Thank you
Tarik Admani
* Please note the useful messages *. -
Design of VPN L2L ASA question
We expect to have more than 10,000 remote VPN L2L clients.
I see that each crypto card needs a statement of 'same game' and the IP address is the address of the remote peer VPN L2L.
:
EX:
card encryption UNI-POP 3 set peer 172.23.0.3
: . . .
card crypto UNI-POP 10000 set peer 172.26.0.250
:
I already feel that this will be a VERY long config, maybe too big to save/read/from memory.
:
Anyone would be a better approach?
Thank you
Frank
Frank,
If the remote end will run only from time to time, you should not have set peer statements and normally it would suffice to have a dynamic encryption card.
If the remote ends do not support certificates, it is possible to land on defaultl2l tunnel-group.
bsns-asa5505-19# sh run all tunnel-group
tunnel-group DefaultL2LGroup type ipsec-l2l
tunnel-group DefaultL2LGroup general-attributes
(...)
You need to test yourself to see if it will work.
I also agree in terms of more than one firewall. With devices for two in the load balancing or if possible 2pairs of devices in the failover cluster could be great way to have a decent charge by machine and equipment redundancy (ideal circumstances]);. I suggest you ping your system engineer for sure any deployment involving 5585, guys can usually give good advice (and discounts;]).
Marcin
-
VPN l2l failed inside on ASA 5520 (8.02)
VPN l2l is dropping packets to Phase 5 because of a rule configured. I have an isakmp his but the client cannot connect to the destination here in my network. I'll post my config to access list at the bottom of the Packet-trace output.
vpnASA01 # entry packet - trace within the icmp [10.0.0.243] 0 8 10.97.29.73 det
Phase: 1
Type: CAPTURE
Subtype:
Result: ALLOW
Config:
Additional information:
Direct flow from returns search rule:
ID = 0xc92087c8, priority = 12, area = capture, deny = false
hits = 85188209121, user_data = 0xc916a478, cs_id = 0 x 0, l3_type = 0 x 0
Mac SRC = 0000.0000.0000, mask is 0000.0000.0000
DST = 0000.0000.0000 Mac, mask is 0000.0000.0000
Phase: 2
Type: ACCESS-LIST
Subtype:
Result: ALLOW
Config:
Implicit rule
Additional information:
Direct flow from returns search rule:
ID = 0xc87f1f98, priority = 1, domain = allowed, deny = false
hits = 85193048387, user_data = 0 x 0, cs_id = 0 x 0, l3_type = 0 x 8
Mac SRC = 0000.0000.0000, mask is 0000.0000.0000
DST = 0000.0000.0000 Mac, mask is 0000.0000.0000
Phase: 3
Type: FLOW-SEARCH
Subtype:
Result: ALLOW
Config:
Additional information:
Not found no corresponding stream, creating a new stream
Phase: 4
Type:-ROUTE SEARCH
Subtype: entry
Result: ALLOW
Config:
Additional information:
in 10.0.0.0 255.0.0.0 inside
Phase: 5
Type: ACCESS-LIST
Subtype:
Result: DECLINE
Config:
Implicit rule
Additional information:
Direct flow from returns search rule:
ID = 0xc87f3670, priority = 111, domain = allowed, deny = true
hits = 67416, user_data = 0 x 0, cs_id = 0 x 0, flags = 0 x 4000, protocol = 0
SRC ip = 0.0.0.0 mask 0.0.0.0, port = 0 =
DST ip = 0.0.0.0 mask 0.0.0.0, port = 0 =
Result:
input interface: inside
entry status: to the top
entry-line-status: to the top
the output interface: inside
the status of the output: to the top
output-line-status: to the top
Action: drop
Drop-reason: flow (acl-drop) is denied by the configured rule
= ACCESS-LIST + Config =.
the object-group L2LVPN-blah_local network
network-object 10.97.29.73 255.255.255.255
the object-group L2LVPN-blah_remote network
network-object [10.0.0.240] 255.255.255.240INBOUND_OUTSIDE list of allowed ip extended access object-L2LVPN-blah_remote L2LVPN-blah_local group object
L2LVPN-blah_obj allowed extended ip access-list object-L2LVPN-blah_local group L2LVPN-blah_remote
access-list SHEEP extended permits all ip [10.0.0.243] 255.255.255.240
Route outside [10.0.0.240] [10.97.29.1] 255.255.255.240 1
address for correspondence card crypto outside-VPN 46 L2LVPN - blah_obj
peer set card crypto VPN-exterior 46 [10.0.0.243]
outside-VPN 46 transform-set esp-sha-aes-256 crypto card
outside-VPN interface card crypto outsideIPSec-l2l type tunnel-group [10.0.0.243]
IPSec-attributes of tunnel-group [10.0.0.243]
pre-shared-key *.[10.0.0.1] is to protect the global addresses of clients. Assume that these are still used in place of the current range of intellectual property. 10.0.0.240/28
===========================================
Thanks in advance.
Michael Garcia
Profit Systems, Inc..
Hi Michael,
-Is the IP peer really part of the network that make up the field of encryption?
-Is the ACL INBOUND_OUTSIDE applied (incoming) inside or outside interface (inbound)? It is the current form, it would need to be on the external interface.
-You specify the peer IP only in the ACL SHEEP, so all other traffic is NAT would and eventually denied because it does not match the field of encryption
Someone else may have a few ideas, but these are questions I have for the moment.
James
-
Redirect peer tunnel VPN L2L ina
Question of curiosity... I have 2 new ASA5515 which I put up for an improvement of the equipment. In the time before I swap them I am using them as a sort of laboratory of fortune to get him going to setup VPN L2L. I didn't use current IP addresses for the test environment, so I used false numbers.
My question is: can I go back and change the IP address peer and address local/remote without having to tear them up to specifications plant again?
-Do I have reprint just the type of Tunnel-Group IPsec-l2l X.X.X.X command with the IP address?
I know that there are a few other of the region that I have to change the IP of both peers, but just of my question is, I can do or do I have to start over?
-Jon
Jon
You should not reconfigure from scratch if that's what you're asking.
You just need to change the peer IPs everywhere where they appear in your configuration.
Jon
-
Recovery site - redundant VPN peers
Hello all, thank you in advance for your expertise.
We put in place a recovery site disaster that will host the redundant copies of our servers and critical data in Kansas City. When disaster strikes, our headquarters site would be totally gone.
We currently have 7 locations that communicate to our HQ via VPN tunnels (whether on a circuit of the Internet or on a circuit of Cox Communications Ethernet WAN). Branch sites each can an ISR of Cisco 2821 router. At Headquarters and on the DR site, we use a Cisco ASA 5510 to terminate VPN tunnels and do everything that our column spinal routing. Routing on the ASA and branch routers is all static, using a routing protocol would be a nice update in the future... any ideas? We use IPSEC VPN lan lan tunnels 2, no GRE/VPN is used because it is not terminated by the ASA.
What is the best way to configure my routers for branch to automatically or manually failover to connect to one ASA different site of DR?
In addition, if my seat is still in place, but either my Internet or Cox headquarters ethernet circuit breaks down. How can I re - route all traffic in a loop to the seat on the right remains a circuit?
Is there a better way to do what I want to accomplish? BGP is not an option at this point due to its complexity.
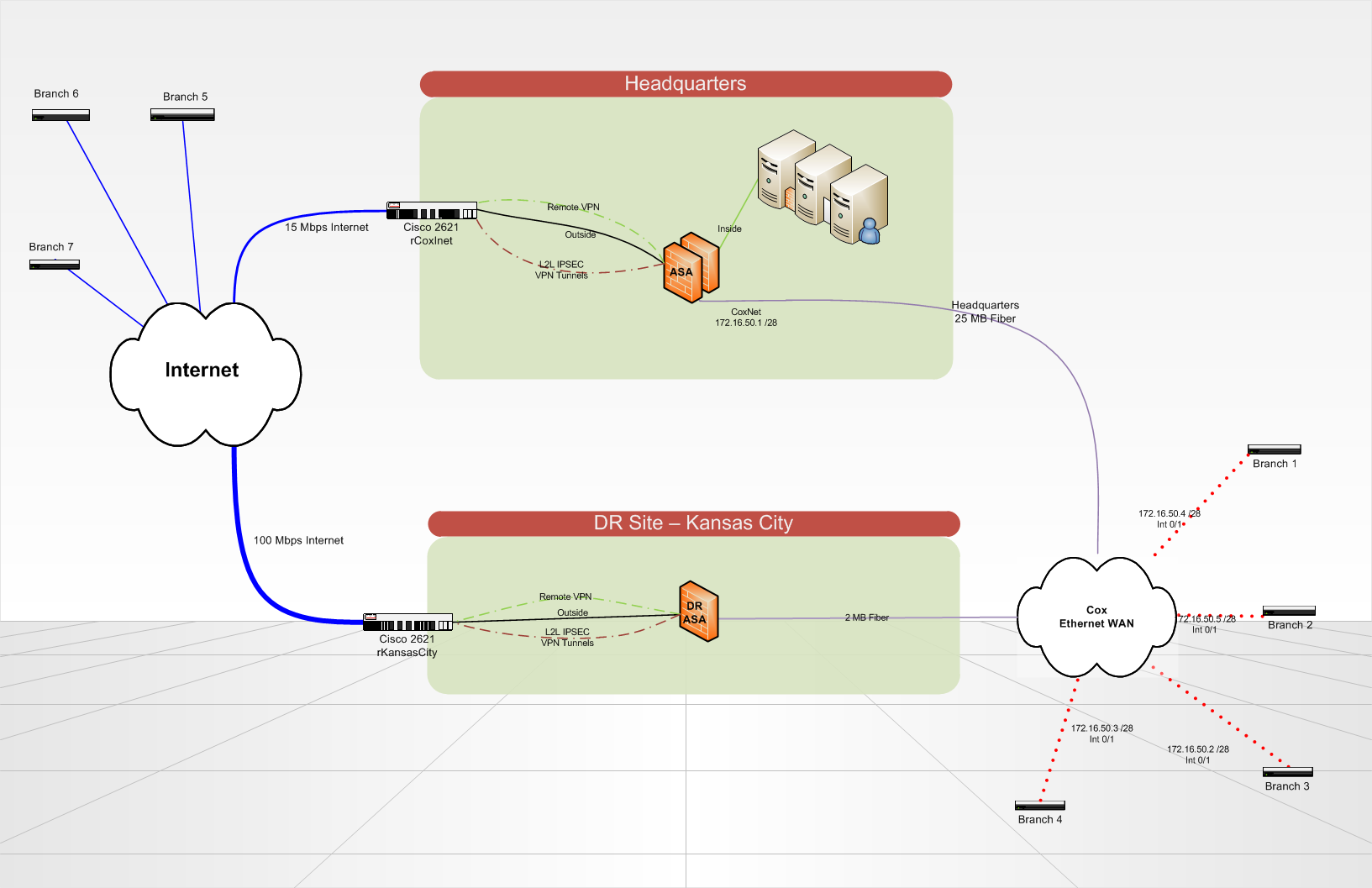
Lucas,
To circumvent the two point separately.
The best way to provide active / standby time of reundancy is preferred peer in cryptographic cards (on the ISR routers).
You can choose to establish VPN to HQ and only if HQ is not aid you to DR, when HQ is you will EVENTUALLY return to it.
The answer to share of your questions may also be the preferred option by peers (and several counterparts in a crypto map entry).
This being said, you can try to send OSPF traffic to IPsec tunnel (and using the neighbor command to avoid the manipulation of mcast in pure IPsec).
Docs:
HTH,
Marcin
P. S.
If you want my personal opion, chaning ASAs in HQ and DR sites and put you in routers could make DMVPN or DVTI-ASIT scenario which gives you a lot more features ;-)
-
Go simple configuration of vpn L2L comply with security requirements
Hello
I have successfully install a L2L connection (5510, 7.2) and a 3rd party (SonicWall).
Security requirements are such that (contractors) to our office users to connect to various devices to the 3rd party, BUT nothing to the 3rd party must connect to what be it at our office.
I tried an outbound ACL (access-group L2L-RESTRICT the interface inside) inside the interface. But the funny thing is that I'm getting hits on the declarations of refusal on the ACL, although tests show no problems for you connect to multiple hosts to our site of the 3rd party. My ACL config looks like the following:
<..snip..>
Note to L2L-RESTRICT access-list * ATTENTION * WITH CAUTION - RESTRICTIONS ON the 3rd PARTY VPN L2L
L2L-RESTRICT access-list scope allow icmp 192.168.16.0 255.255.255.0 10.180.21.0 255.255.255.0 echo-reply
deny access list L2L-RESTRICT the scope ip 192.168.16.0 255.255.255.0 no matter what newspaper
Note to L2L-RESTRICT access-list > NOTE< last="" line="" *must*="" be="" permit="" any="">
L2L-RESTRICT access-list scope ip allow a whole
!
L2L-RESTRICT the interface inside access-group
<..snip..>
Their network is obviously 192.168.16.x and they won't be able to use a vlan from different source as "interesting traffic" ACL won't allow it. So that sounds good in theory
I have it configured correctly? Is there a better way?
Thanks in advance,
Mike
Mike,
It seems that you might be able to assign a VPN ACL filter via a group assigned to each tunnel L2L policy. I have never done this personally before, but looks like it would work...
-
Do not do a ping ASA inside IP port of the remote site VPN L2L with her
The established VPN L2L OK between ASA-1/ASA-2:
ASA-2# see the crypto isakmp his
KEv1 SAs:
ITS enabled: 1
Generate a new key SA: 0 (a tunnel report Active 1 and 1 to generate a new key during the generate a new key)
Total SA IKE: 1
1 peer IKE: 207.140.28.102
Type: L2L role: answering machine
Generate a new key: no State: MM_ACTIVE
There are no SAs IKEv2
QUESTION: 3750-2, we ping 3750-1 (10.10.2.253) are OK, but not ASA-1 inside port (10.10.2.254).
Debug icmp ASA-1 data:
ASA-1 debug icmp trace #.
trace of icmp debug enabled at level 1
Echo ICMP Internet request: 10.100.2.252 server: 10.10.2.253 ID = 400 seq = 0 len = 72
ICMP echo response from the server: 10.10.2.253 Internet: 10.100.2.252 ID = 400 seq = 0 len = 72
Echo ICMP Internet request: 10.100.2.252 server: 10.10.2.253 ID = 400 seq = 1 len = 72
ICMP echo response from the server: 10.10.2.253 Internet: 10.100.2.252 ID = 400 seq = 1 len = 72
Echo request ICMP 10.100.2.252 to 10.10.2.254 ID = 401 seq = 0 len = 72
Echo request ICMP 10.100.2.252 to 10.10.2.254 ID = 401 seq = 1 len = 72
Echo request ICMP 10.100.2.252 to 10.10.2.254 ID = 401 seq = 2 len = 72
Make sure you have access to the administration # inside
lt me know f This allows.
-
Summary:
We strive to establish a two-way VPN L2L tunnel with a partner. VPN traffic is one-to-many towards our partner, and our partner they need of a many-to-one to us (they need to access a host on our network). In addition, our partner has many VPN, so they force us to use a separate NAT with two private hosts addresses, one for each direction of the tunnel.
My initial configuration of the tunnel on my grown up side of Phase 1, but not IPSec. Partner ran debug that revealed that my host did not address NAT'd in the NAT policy. We use an ASA5520, ver 7.0.
Here is the config:
# #List of OUR guests
the OURHosts object-group network
network-host 192.168.x.y object
# Hosts PARTNER #List
the PARTNERHosts object-group network
network-host 10.2.a.b object
###ACL for NAT
# Many - to - many outgoing
access-list extended NAT2 allowed ip object-group OURHosts-group of objects PARTNERHosts
# One - to - many incoming
VIH3 list extended access permit ip host 192.168.c.d PARTNERHosts object-group
# #NAT
NAT (INSIDE) 2-list of access NAT2
NAT (OUTSIDE) 2 172.20.n.0
NAT (INSIDE) 3 access-list VIH3
NAT (OUTSIDE) 3 172.20.n.1
# #ACL for VPN
access list permits extended VPN ip object-group objects PARTNERHosts OURHosts-group
access allowed extended VPN ip host 192.168.c.d PARTNERHosts object-group list
# #Tunnel
tunnel-group
type ipsec-l2l card
<#>crypto is the VPN address card crypto
<#>the value transform-set VPN card
<#>crypto defined peer I realize that the ACL for the VPN should read:
access allowed extended VPN ip host 172.20.n.0 PARTNERHosts object-group list
access allowed extended VPN ip host 172.20.n.1 PARTNERHosts object-group list
.. . If the NAT was working properly, but when this ACL is used, Phase 1 is not even negotiating, so I know the NAT is never translated.
What am I missing to NAT guests for 172.20 addresses host trying to access their internal addresses via the VPN?
Thanks in advance.
Patrick
Here is the order of operations for NAT on the firewall:
1 nat 0-list of access (free from nat)
2. match the existing xlates
3. match the static controls
a. static NAT with no access list
b. static PAT with no access list
4. match orders nat
a. nat [id] access-list (first match)
b. nat [id] [address] [mask] (best match)
i. If the ID is 0, create an xlate identity
II. use global pool for dynamic NAT
III. use global dynamic pool for PAT
If you can try
(1) a static NAT with an access list that will have priority on instruction of dynamic NAT
(2) as you can see on 4A it uses first match with NAT and access list so theoretically Exchange autour should do the trick.
I don't see any negative consequences? -Well Yes, you could lose all connectivity. I don't think that will happen, but I can't promise if you do absolutely not this after-hours.
Jon
-
If anyone can help with control of packet - trace to migrate to l2l ipsec vpn
on ASA (one)
ciscoasa # packet - trace entry outside tcp 10.10.1.2 12345 192.168.1.2 80
ASA (one)
Ip address inside - 192.168.1.2
Destination port 80
ASA (b)
Inside - 10.10.1.2 ip address
Port source 12345
Hello
So if your host 'inside' is 192.168.1.2 and the 'outside' host is 10.10.1.2 then you could just what follows
Packet-trace entry inside tcp 192.168.1.2 12345 10.10.1.2 80
If the goal is just to test the VPN negotiation then the ports are not really important, but naturally tested traffic with "packet - tracer" must be authorized by your interface "inside" ACL. The essential is that the source address and destination match the VPN L2L (Crypto ACL) configurations
Generally you would use NAT0 for these networks the and remote so NAT should not be a problem to test from that direction. I suppose there might be rare situations where using the command in this sense is not possible
-Jouni
-
Hi all
I need a solution for this implementation:
2 sites
2 internet connections each site (different suppliers)
1 ASA in each site
I need a config that allows me to have redundant VPN connections from one site to the other. I need to have a VPN using the, say, internet connection A of site 1 and internet connection from site 2 and if the internet connection A of site 1 goes down the VPN connect by using the internet connection B from site 1 to site 2 A internet connection. This must be done without user intervention.
If I can't do it with the ASA which can use to achieve this scenario? Another router (2900), a kind of load balancing?
I would like to use the ASA because I have a lot of inbound NAT configured and keeping addresses public IP on the SAA outside interface would be great.
Thank you, best regards.
Yes.
You can apply the same card encryption on both interfaces.
Also... If you have multiple VPN peers, they end on the same card encryption as well.
If you for example need many VPN Site to Site tunnels, you create a single card encryption with sequence numbers different to accept VPN connections.
Federico.
-
Hi all
I need to create a VPN L2L tunnel between us and another local company. We use a 3845 router and the other carrier uses a 3745 router. I created a lot of VPN tunnels in the past using NAT. In this case, I don't have to. is it possible for a tunnel VPN work with the same configuration without using NAT. My router and the device being connected to all have a public IP address on the same subnet.
Thank you
Stevan
Hello
Yes, you can create L2L without having to use NAT.
See the examples of configuration (under VPN Site to Site with PIX/IOS):
http://www.Cisco.com/en/us/partner/products/HW/vpndevc/ps2030/prod_configuration_examples_list.html
Before that, you have probably more experience configuration tunnel as shown in the url below:
Rgds,
AK
-
Direct specific ports down a VPN L2L
I have a client who is trying to use an ISP hosted web filtering and content management a gateway, the ISP wants to use and L2L ISPEC VPN on site at their front door to control the traffic. Today we have the tunnel with an ACL test for peripheral test side customer down the tunnel, but that it blocks all traffic that is not being analyzed. The problem is that they are on an ASA 5510 with 8.2.2. You cannot add ports tcp in the ACL sheep, it error when you try to apply the nat 0 access-list statement sheep (inside). We can define the ports to go down the VPN traffic interesting ACL with number, but there is no way to send just the web ports down the VPN and allow the other ports on regular overflow interface NAT I was look in 8.4 and see if it allows a policy NAT (twice the NAT for virtual private networks) to set a port to a range of IPS (IE (: nat static destination WEBINSPECT-WEBINSPECT (indoor, outdoor) static source a whole) but who only define as web ports.
I do not have an ASA test to use, but I guess that vpn l2l will be only by IP and I can not define a port tunnel.
In any case, it is a strange, but the ideas are welcome. I don't think it's possible, but I thought I'd see if anyone encountered at the front.
Hello
Well to give you a simple example where we use the double NAT / manual transmission NAT to handle traffic
For example a configuration example I just did on my 8.4 (5) ASA
The following configuration will
- Set the 'object' that contains the source network for NAT
- Set the 'object' that contains the service for NAT
- Define the real NAT
The real NAT is going to make any connection from the network under 'Wireless' network object to the destination port TCP/80 will be sent 'WAN' interface without NAT
Of course it is the next step with VPN L2L network under 'network wireless of the object' would correspond to the ACL of VPN L2L. But that seemed straight forward for you already
the subject wireless network
10.0.255.0 subnet 255.255.255.0
service object WWW
Service tcp destination eq www
NAT (WLAN, WAN) static source without WIRE WIRELESS WWW WWW service
The following configuration will
- Define the "object-group", that defines networks of the source of the rule by default PAT for Internet traffic
- Set the 'object' for the PAT address (could just use 'interface' instead of the 'object')
- Define the real NAT
The NAT configuration will just make a rule by default PAT for the wireless network. The key thing to note here is that we use the setting "auto after." This basically inserts the NAT rule to the priority of the very bottom of the ASA.
object-group, network WIRELESS-network
object-network 10.0.255.0 255.255.255.0
network of the PAT object - 1.1.1.1
host 1.1.1.1
NAT (WLAN, WAN) after the automatic termination of wireless - NETWORK PAT dynamic source - 1.1.1.1
Now we can use the command "packet - trace" to confirm that the NAT works as expected.
WWW TEST-TRAFFIC
ASA (config) # packet - trace 12355 1.2.3.4 entry WLAN tcp 10.0.255.100 80
Phase: 1
Type: UN - NAT
Subtype: static
Result: ALLOW
Config:
NAT (WLAN, WAN) static source without WIRE WIRELESS WWW WWW service
Additional information:
NAT divert on the output WAN interface
Untranslate 1.2.3.4/80 to 1.2.3.4/80
Phase: 2
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional information:
Phase: 3
Type: NAT
Subtype:
Result: ALLOW
Config:
NAT (WLAN, WAN) static source without WIRE WIRELESS WWW WWW service
Additional information:
Definition of static 10.0.255.100/12355 to 10.0.255.100/12355
Phase: 4
Type: HOST-LIMIT
Subtype:
Result: ALLOW
Config:
Additional information:
Phase: 5
Type: NAT
Subtype: rpf check
Result: ALLOW
Config:
NAT (WLAN, WAN) static source without WIRE WIRELESS WWW WWW service
Additional information:
Phase: 6
Type: USER-STATISTICS
Subtype: user-statistics
Result: ALLOW
Config:
Additional information:
Phase: 7
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional information:
Phase: 8
Type: USER-STATISTICS
Subtype: user-statistics
Result: ALLOW
Config:
Additional information:
Phase: 9
Type: CREATING STREAMS
Subtype:
Result: ALLOW
Config:
Additional information:
New workflow created with the 1727146 id, package sent to the next module
Result:
input interface: WLAN
entry status: to the top
entry-line-status: to the top
the output interface: WAN
the status of the output: to the top
output-line-status: to the top
Action: allow
TEST FTP - TRAFFIC
ASA (config) # packet - trace entry tcp 10.0.255.100 WLAN 12355 1.2.3.4 21
Phase: 1
Type:-ROUTE SEARCH
Subtype: entry
Result: ALLOW
Config:
Additional information:
in 0.0.0.0 0.0.0.0 WAN
Phase: 2
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional information:
Phase: 3
Type: INSPECT
Subtype: inspect-ftp
Result: ALLOW
Config:
class-map inspection_default
match default-inspection-traffic
Policy-map global_policy
class inspection_default
inspect the ftp
global service-policy global_policy
Additional information:
Phase: 4
Type: NAT
Subtype:
Result: ALLOW
Config:
NAT (WLAN, WAN) after the automatic termination of wireless - NETWORK PAT dynamic source - 1.1.1.1
Additional information:
Definition of dynamic 10.0.255.100/12355 to 1.1.1.1/12355
Phase: 5
Type: HOST-LIMIT
Subtype:
Result: ALLOW
Config:
Additional information:
Phase: 6
Type: NAT
Subtype: rpf check
Result: ALLOW
Config:
NAT (WLAN, WAN) after the automatic termination of wireless - NETWORK PAT dynamic source - 1.1.1.1
Additional information:
Phase: 7
Type: USER-STATISTICS
Subtype: user-statistics
Result: ALLOW
Config:
Additional information:
Phase: 8
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional information:
Phase: 9
Type: USER-STATISTICS
Subtype: user-statistics
Result: ALLOW
Config:
Additional information:
Phase: 10
Type: CREATING STREAMS
Subtype:
Result: ALLOW
Config:
Additional information:
New workflow created with the 1727154 id, package sent to the next module
Result:
input interface: WLAN
entry status: to the top
entry-line-status: to the top
the output interface: WAN
the status of the output: to the top
output-line-status: to the top
Action: allow
As you can see traffic TCP/80 corresponds to rule on the other. And the FTP used for example corresponds to rule by default PAT as expected.
If you want to know a little more about the new NAT 8.3 format + you can check a document I created
https://supportforums.Cisco.com/docs/doc-31116
Hope this helps you, please mark it as answered in the affirmative or rate of answer.
Naturally ask more if necessary
-Jouni
-
I was wondering if there is a way to allow only one side of a vpn tunnel to create connections?
Example I have a vpn tunnel going to a site with servers that I manage. I want to be able to get on the servers (via rdp, ssh, etc.) and allow the return of traffic but I don't want the servers to be able to reach me (via rdp, ssh, etc.).
Any ideas?
I use a cisco ASA5540
Hello
You have alteast 2 possibilities
- You can configure a filter ACL on the L2L VPN connection VPN
- Long-term a solution a little messier. Mainly due to the ACL filter of VPN L2L having a slightly different configuration than the usual ACL interface format
- You can turn off (if not already disabled) feature that allows to bypass your 'outer' interface ACL all traffic entering from a VPN connection. In this way, you can control incoming VPN L2L with ACL 'outside' interface traffic.
- connections are allowed as any other Internet connection in the "outside" interface ACL if its fairly simple to manage.
If this is something you are looking for I can tell you how to get to one of them.
-Jouni
- You can configure a filter ACL on the L2L VPN connection VPN
Maybe you are looking for
-
Firefox does not open after 3 attempts and then end task in task W10 Manager
I uninstalled and reinstalled several times with Firefox, I used %APPDATA%\microsoft\windows\sendto as Mozilla instructed, deleted programs etc all to nothing done. Please note that I am not computer savvy and a simplified solution would be appreciat
-
Add to iTunes as read text track
I want to use the function "add to iTunes as track of text read" in order to create a narrative of a YouTube video that I do. But I'm not sure if it's legal, am I allowed to do this and put it on YouTube? I know that some people are already using it
-
My screen orientation is implemented alone
This is all portrait view and I can't understand how files to see landscape. Help!
-
My PC no longer sees my HP Photosmart C4340
My situation recently: I had the HP Photosmart C4340 long already. Good machine. I've never installed color ink cartridge since I never need color printing and use only black ink for black and white printing. I don't print much, only about 3-10 pages
-
BlackBerry screen 10 flashing after update to OS 10.3.1.1565
Hello I've updated my passport blackberry software yesterday to version 10.3.1.1565, and after the update, something was wrong with my phone. Everytime I open request for example photos, BBM messages etc. quick flashing screen... sometimes the screen