Redundant VPN design
Hi all
I need a solution for this implementation:
2 sites
2 internet connections each site (different suppliers)
1 ASA in each site
I need a config that allows me to have redundant VPN connections from one site to the other. I need to have a VPN using the, say, internet connection A of site 1 and internet connection from site 2 and if the internet connection A of site 1 goes down the VPN connect by using the internet connection B from site 1 to site 2 A internet connection. This must be done without user intervention.
If I can't do it with the ASA which can use to achieve this scenario? Another router (2900), a kind of load balancing?
I would like to use the ASA because I have a lot of inbound NAT configured and keeping addresses public IP on the SAA outside interface would be great.
Thank you, best regards.
Yes.
You can apply the same card encryption on both interfaces.
Also... If you have multiple VPN peers, they end on the same card encryption as well.
If you for example need many VPN Site to Site tunnels, you create a single card encryption with sequence numbers different to accept VPN connections.
Federico.
Tags: Cisco Security
Similar Questions
-
Question of redundancy VPN l2l using 2811 as endpoint devices
I have a new implementation of VPN L2L passes using two 2811 s than VPN terminal devices. I'll try to use the HSRP address between the public interfaces of both routers as VPN peer address. The problem that I found during the test is that the tunnel will become active and debugs watch the HSRP address as an invalid address to form the tunnel. Have a work-around, or a better plan for redundancy on peering address using similar devices? Thanks in advance.
Take a look at this doc about IOS IPSec HA.
-
Redundancy VPN by destination?
Hi all, I am trying to set up a vpn for one of my clients. they must have the same tunnel vpn with same source - destination traffic but destined for two different periods of public inquiry. so this should have sort of a primary vpn if it don't then a secondary vpn must support. This isn't the redundant Internet access provider scenario.
A network - B - vpn - terminate on X (most preffered)
A network - B - vpn - terminate on Y (less preferred)
On the ASA, you can do it with the primary encryption card with a higher priority than backup, but using the same ACL. If the first card cannot peer, the other will be implemented. It should be lower setting on the IPSec Security Association lifetime for this. You can also only defining the hub in single are created and the rays or receive only so that you do not have a RADIUS, creating a new SA when you do not want that it is for me.
-
Double firewall, config VPN design question?
All,
I'm looking to implement a design of double firewall with different suppliers, i.e. Cisco at the front and another seller behind that. The Cisco ASA will manage the ends of the VPN. It's a design recommended to us.
The reason was the front towards the firewall (cisco) will block most of the noise, and then the second firwall will make inspection of the IPS etc. Apparently, this is also done incase there are vulnerabilities with the first provider. The DMZ interface will in fact come the second firewall.
I am currently working, what if all remote users terminate their VPN at the edge of the ASAs, what is the best way have to move towards the second firwall, then again on the internet so we can apply the policy to users / and inspection?
There are no facilities on the front to ASAs IPS inspection, just a bog without visibility L7 stock Firewall (as this responsibility will lie with the second firewall).
Looking for information so that I can start looking...
The MCV is a great place to start.
http://www.Cisco.com/en/us/solutions/ns340/ns414/ns742/ns1128/landing_iEdge.html
-
I usually deal with issues of LAN/WAN, but have very little experience with the design of the VPN. I would like to know if I have the right idea or if there is a better solution to target.
Scenario:
There is a staff with two remote offices. Remote offices have 10 to 20 people each with little or no planned growth and different firewall solutions. HQ has 40-50 people anticipating exceptional growth and a PIX 515E. The manager would like to remote offices and remote access VPN site to site VPN for the traveler. His biggest concern is the speed through the site to site tunnels.
My solution:
Place a hub routers of the 800 series with sets of features VPN and firewalls and VPN 3005 behind the PIX to HQ in remote controls.
This seems sufficient? Other recommendations?
No I don't think so. This should be good only for the 515.
-
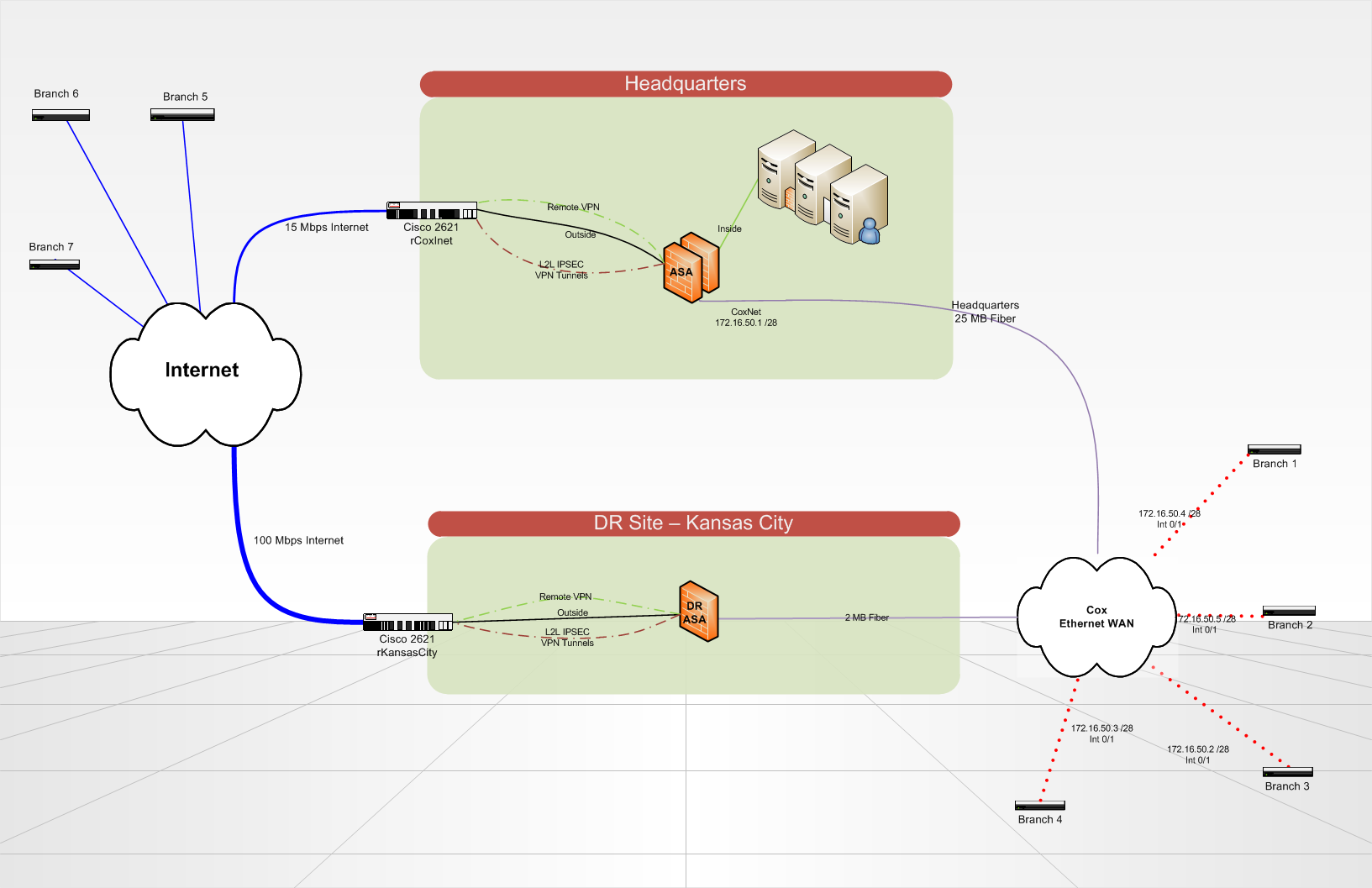
Recovery site - redundant VPN peers
Hello all, thank you in advance for your expertise.
We put in place a recovery site disaster that will host the redundant copies of our servers and critical data in Kansas City. When disaster strikes, our headquarters site would be totally gone.
We currently have 7 locations that communicate to our HQ via VPN tunnels (whether on a circuit of the Internet or on a circuit of Cox Communications Ethernet WAN). Branch sites each can an ISR of Cisco 2821 router. At Headquarters and on the DR site, we use a Cisco ASA 5510 to terminate VPN tunnels and do everything that our column spinal routing. Routing on the ASA and branch routers is all static, using a routing protocol would be a nice update in the future... any ideas? We use IPSEC VPN lan lan tunnels 2, no GRE/VPN is used because it is not terminated by the ASA.
What is the best way to configure my routers for branch to automatically or manually failover to connect to one ASA different site of DR?
In addition, if my seat is still in place, but either my Internet or Cox headquarters ethernet circuit breaks down. How can I re - route all traffic in a loop to the seat on the right remains a circuit?
Is there a better way to do what I want to accomplish? BGP is not an option at this point due to its complexity.
Lucas,
To circumvent the two point separately.
The best way to provide active / standby time of reundancy is preferred peer in cryptographic cards (on the ISR routers).
You can choose to establish VPN to HQ and only if HQ is not aid you to DR, when HQ is you will EVENTUALLY return to it.
The answer to share of your questions may also be the preferred option by peers (and several counterparts in a crypto map entry).
This being said, you can try to send OSPF traffic to IPsec tunnel (and using the neighbor command to avoid the manipulation of mcast in pure IPsec).
Docs:
HTH,
Marcin
P. S.
If you want my personal opion, chaning ASAs in HQ and DR sites and put you in routers could make DMVPN or DVTI-ASIT scenario which gives you a lot more features ;-)
-
I have two sites with 2921 IPSec routers. Each router has 3 ethernet interfaces. A local area network, Internet, and an Ethernet based private circuit.
I need the site to site VPN between these routers, on the private circuit. However, this circuit fails on rare opportunity, so I want to have a VPN failover to review the Internet as a backup.
Doesn't matter to me if it's the primary failover / secondary or if there are load balanced with failover. What is essential, is that if a circuit fails, my remote site continues to communicate with the main office.
HSRP looks like I need two routers and I don't have one of the HSRP Protocol monitors several LAN interfaces.
I opened a case with TAC, but it has been a week without any progress.
Certainly, it is not so hard to do.
Hey Joe,
Router eigrp 100
Network 10.250.1.0 0.0.0.3 #10.250.1.1 is the IP address of the tunnel12
Network 10.250.1.4 0.0.0.3 #10.250.1.5 is the ip address of the tunnel122
network 192.168.1.0 # is the LAN segment that must be routed.
Remote router...
Router eigrp 100
Network 10.250.1.8 0.0.0.3 #10.250.1.9 is the IP address of the tunnel0
Network 10.250.1.12 0.0.0.3 #10.250.1.13 is the IP address of the tunnel1
network 192.168.12.0 # is the LAN segment that must be routed.
The two parties should normally be in the same subnet NW
for example if
You 12 is connected to tu0
then
one side have 10.250.1.1 and the other 10.250.1.2
If tu122 is connected to tu1
then
10.250.1.5 and the other side is 10.250.1.6
the two eigrp network should be the same
-
We have a VPN connection from site to site with a remote network and want to know if there is anyway to set a secondary IP address peer who would use VPNS to connect in case the primary became unavailable
Configuration of counterpart of backup for tunnel vpn on the same crypto map
Problem
You want to use several counterparts backup for a single vpn tunnel.
Solution
Configuration of several counterparts is equivalent to provide a list of relief. For each tunnel, the security apparatus tried to negotiate with the first peer in the list.
If this peer does not respond, the security apparatus made his way to the bottom of the list until a peer responds, or there is no peer more in the list.
The SAA must have a card encryption already configured as the primary counterpart. The secondary counterpart could be added after the primary.
This example configuration shows the primary counterpart as X.X.X.X and Y.Y.Y.Y as peer backup:
ASA (config) #crypto map mymap 10 peer set X.X.X.X Y.Y.Y.Y
http://www.Cisco.com/en/us/products/ps6120/products_tech_note09186a00807...
HTH
If useful rates
Sent by Cisco Support technique iPhone App
-
I have a scenario where I have 2 ISPS connected to a different 800 router. Inside network is a single a (10.10.10.0/24). It is a single office and this unique office has a L2L tunnel with another office (office-2). How configure failover and load balancing, and always keep the tunnel if one ISP goes down?
ciscobigcat,
I just asked one of the experts switch that I worked with and he told me the 4500 s cannot handle GRE tunnel even if they are L3 switches. So that would not work for you. 6500 or even the 3700 series switches should be able to do it without problem, but you should talk to your representative local sales to confirm.
You can absolutely send a tunnel through another tunnel. The concept is that build you a GRE tunnel between closure of the router behind the ASA closure on Router 1. Then you build plain ipsec between routers-1 tunnel and the ASA that match all ip traffic between the closure on Router-1 for the closure of the router behind the ASA.
-
ASA5505 configure VPN primary and backup
Dear experts,
I would like to ask you a few question that now I didn't get any primary VPN and backup connection, how can we do on this is sue? (I mean that when the primary reduction, then backup connection is automatically)
Could you advice me how can I do?
Best regards
Rechard_hk
I guess we should have asked for a bit more information, it seems Marwan and I responded almost at the same time, and I'm sure he'll provide great info.
I had more geared towards a scenario of a firewall failure fault tolerance or an ISP connection failed in an architecture Fw DOUBLE and DOUBLE tis.
Assuming that you want to have redundant firewall design, is when you look into the firewall active / standby to provide firewall redundancy, but when it comes to connections continues with VPN when one firewall fails, this is with characteristic State in place.
IM providing links for reference belloe to get an idea of fws active and reserve but ASA5505 is the only model who is a stateless person, it is not dynamic which means connections will have to re - perform when one firewall fails.
Also to implement two firewalls for the implementation of the changeover you need security more license to enable the active feature and reserve. This license will also include the activation of support DMZ and power create a VLAN to 20, as well as support Double TIS.
Example of active / standby
Comparison of the ASA - Look into Ipsec more license and features.
http://www.Cisco.com/en/us/products/ps6120/prod_models_comparison.html
On the other hand you may have in the future a backup ISP link, not only do you have active failover / standby but you can also have a backup ISP must link primary link fails with ALS and follow-up of Staic routing.
Rgds
Jorge
-
I do a search in the search of the best solution for switching between two ASA and hoped that someone wants to point me in the right direction.
The situation is this, we got:
-Head Office 2:
Each is equipped with an ASA 5505
-10 branches
Each is equipped with a 887 integrated services router.
Each is BranchOffice must have a redundant VPN connection at the headquarters of these two, and they all need to use the first person as main and the other in high school. In case of failure, all branches need to use the second connection VPN going the second seat.
In my research, I'm looking for the best possible solution, with faster failover, but have no idea where to start my research.
I hope someone has a good answer for this one.
Thank you very much in advance,
Kind regards
Dwayne
I do not understand why people continue to use ASA devices for VPN endpoint. the ASA is NOT designed for complex VPN scenarios. It is designed for simple scenarios. In terms of VPN by using comparison, ASA is a person with a basic education while Cisco IOS is like a person with a college degree.
For the scenario, you will be much better using Cisco IOS routers everywhere, where you can implement the GRE/IPSec or DMVPN. Both cases will be sastify to your needs.
-
Branch 5505, 1 circuit ISP, Dual - peer VPN Configuration for Data Center & Track Options
Hi all
I have a data center with two lines of ISP redundancy and two ASA 5520 for redundancy VPN to my branches. Each of my branches has 1 ASA 5505 with a base license and 1 ISP circuit. Currently all my VPN tunnels are built for data center main circuit ISP only, so if one goes down, I'm toast. I need to fix this. Problem is, I don't know how I can control failover on 5505 with 1 single line branch. Please see my picture for an example of how he looks at it right now.
So the problem is that the data center LAN my branch has to go to is identical regardless of which circuit of data center is in the. And I know the ASA rules say only 1 VPN tunnel can be active at a time if flow are the same. So in this case, I know you usually do:
card crypto outside_map 1 set 12.x.xxx.20 50.xxx.xx.190 counterpart
and then configure route followed to control when cut down the primary counterpart and turn back up by peers. But where I have only 1 ISP on the side of the branch, I'll only have 1 default route: route outside 0.0.0.0 0.0.0.0 3.3.3.2 1, will be used that the active end counterpart is the primary or the secondary data center. Also, since I did not have a second track, I can't configure followed on the main road with an SLA that defines the trigger conditions, because there is nothing to ensure the follow-up of the routing.
How is - a would handle a situation like this? Are there other features that can be taken off the roads? I really need to be able to define "num-package 5 ' in ALS so my sites are not beat all day, but once again, without something to follow, I can't really set up a meaningful SLAS. Any help is appreciated.
Thanks for the additional explanation. It helps to clarify your environment. EIGRP running on the Remote would be a nice option, but I'm not sure that it is supported on the SAA. I ran EIGRP to remote peers using IOS routers (using the two ACCORD with IPsec and VTI tunnels tunnels) and it was very effective. But on the SAA, I believe that we must seek an alternative.
It seems to me that using reverse road Injection as part of your VPN site-to-site should work. With IPP the ASA inserts a static route to remote resources when the VPN tunnel is negotiated and traffic can flow. If you redistribute the static in EIGRP EIGRP then must learn the ways of any ASA a currently active tunnel. And who should provide the dynamic rollover you need.
HTH
Rick
-
Configure several IPSec VPN between Cisco routers
I would like to create multiple ipsec VPN between 3 routers. Before applying it, I would like to check on the config I wrote to see if it works. It's just on RouterA configuration for virtual private networks to RouterB, and RouterC.
As you can apply in a cyptomap by interface, I say with the roadmap, that it should be able to manage traffic for both routers. Or is there a better way to do it?
RouterA - 1.1.1.1
RouterB - 2.2.2.2
RouterC - 3.3.3.3
RouterA
crypto ISAKMP policy 10
BA 3des
preshared authentication
Group 2
ISAKMP crypto key RouterB address 2.2.2.2
ISAKMP crypto keys RouterC address 3.3.3.3
invalid-spi-recovery crypto ISAKMP
ISAKMP crypto keepalive 5 10 periodicals
ISAKMP crypto nat keepalive 30
!
life crypto ipsec security association seconds 28800
!
Crypto ipsec transform-set AES - SHA esp - aes 256 esp-sha-hmac
!
outsidemap 20 ipsec-isakmp crypto map
defined peer 2.2.2.2
game of transformation-AES-SHA
match address 222
outsidemap 30 ipsec-isakmp crypto map
defined peer 3.3.3.3
game of transformation-AES-SHA
match address 333
!
interface GigabitEthernet0/0
Description * Internet *.
NAT outside IP
outsidemap card crypto
!
interface GigabitEthernet0/1
Description * LAN *.
IP 1.1.1.1 255.255.255.0
IP nat inside
!
IP nat inside source map route RouterA interface GigabitEthernet0/0 overload
!
access-list 222 allow ip 1.1.1.0 0.0.0.255 2.2.2.0 0.0.0.255
access-list 223 deny ip 1.1.1.0 0.0.0.255 2.2.2.0 0.0.0.255
access-list 223 allow ip 1.1.1.0 0.0.0.255 any
access-list 333 allow ip 1.1.1.0 0.0.0.255 3.3.3.0 0.0.0.255
access-list 334 deny ip 1.1.1.0 0.0.0.255 3.3.3.0 0.0.0.255
access-list 334 allow ip 1.1.1.0 0.0.0.255 any
!
!
RouterA route map permit 10
corresponds to the IP 223 334
Hi Chris,
The two will remain active.
The configuration you have is for several ste VPN site is not for the redundant VPN.
The config for the redundant VPN is completely different allows so don't confuse is not with it.
In the redundant VPN configuration both peers are defined in the same card encryption.
Traffic that should be passed through the tunnel still depend on the access list, we call in the card encryption.
This access-lsist is firstly cheked and as a result, the traffic is passed through the correct tunnel
HTH!
Concerning
Regnier
Please note all useful posts
-
DMVPN Design using ISP by modem redundancy alongside with rays.
I'm working on a new DMVPN configuration with a 3745 on hub site and a 1941 speak it. I have internet via gsm for the first line speaks it and a DSL for backup on talk.
I have a tunnel on the spokes and the hub interfaces. Currently my VPN tunnel is coming up fine, however we are planing to do a failover from the ISP next with rays. given that in the tunnel interface, I can define only a "tunnel source interface" which is the cell interface gsm, I don't know how to use my ISP one another for the same tunnel interface because it will always launch gsm traffic.
that I have to create another interface of tunnel with same hub site, or do I need another hub as backup?
is their any other way to create the loopback interface and initiate this loopback traffic?
Does anyone have any suggestions on how I have to design? or someone has an idea what could be the problem?
Thank you.
Hello
There are many designs to implement A high-availability in DMVPN. Basically, the design decisions are based on infrastructure, budget, and if you are looking to implement HA for devices DMVPN, ISP links or both.
on your scenario, you seem to be looking to implement redundancy for DMVPN HA ISP on the right talk. This scenario can be achieved by a single pivot double-cloud design, with double-hub it may also be more highly available.
The elements of design for your scenario:
-2 interfaces tunnel using two interfaces physical sources talked about it.
-two interfaces of tunnel in the hub, they can share the same physical interface.
-Point-key: using of protocols of dynamic routing in the two clouds with different 'links between costs', so that the main connection at lower cost, and the second connection has the higher cost (to use at default)
I hope this helps you
------------------
Mercury Alshboul -
Redundancy in VPN site-to-site connection
Hi all
We have a requirement of redundancy between two layout 2900 cisco routers.
Router 1(1.1.1.1)--------------------------------------------------(3.3.3.3)
(2.2.2.2)-------------------------------------------------- Router 2
The scenario is Router 1 we have 2 ISP IE in 2 interfaces, we set up 2 IPs (1.1.1.1 and 2.2.2.2).
In Router 2, we have only 1 PSI (3.3.3.3)
Site to site VPN is configured between Router 1 and Router 2 between IPs 1.1.1.1 and 3.3.3.3.Now the requirement is to have 2 ISP in ROUTER1.
Default route is configured in two individual ISP routers. So, if necessary I can configure a different default route with a higher priority for the secondary link to Router 1.
So is it possible to set 2 FPS peer in Router 2?
I had checked on the internet but couldn't find any configuration cisco router (I'm ASA firewall configuration)
The commands to set two peers I found in internet in ASA East - Crypto outside_map 10 card set counterpart 1.1.12.2.2.2.1 is not supported in my router.
Can you please help me find the command configure 2 peers in the Router 2.
Thank you and best regards,
Rituporna Sama
Hi Rituporna,
Yes, you need the key isakmp to the two peers.
The remotepeer of peer set that appears first in the list will also act as a primary counterpart.
Kind regards
Aditya
Please evaluate the useful messages and mark the correct answers.
Maybe you are looking for
-
I bought a Macbook with a German keyboard in Germany. I can change it to keyboard United States?
I bought a Macbook with a German keyboard in Germany. I can change it to keyboard United States?
-
An anti virus for multipoint Server 2011?
I am a teacher using multipoint Server 2011 with computing devices of N. I can't install 2011 anti virus trend micro titanium or kasperskey anti virus 2011 on my work stations please help...
-
How can I tell what video card will be compatible?
Hi, I think I need a new video card, but I don't really know what the new card will be compatible with my computer, a m9077c of HP that works with Vista.I see there a Nvidia Geforce 8500 gt in there now, but looking for new to buy, I see things like
-
I have a 9800 that prints x 2345
I have a 9800 that prints x 2345. What should you do?