RV320 static subnet ISP
Hi guys,.
First of all, I'm a guy from Layer 7 and have only basic knowledge on networks. With this knowledge, I have problems to set up a RV320 (v1.1.1.19 (2014-12-01)) with a static IP subnet of my ISP. I have a 29 subnet with a FritzBox cable as a modem cable simple (no firewall works etc. on the FritzBox). I have an IP address configured for the interface WAN1 (90.xxx.xxx.206). The second is configured as DMZ. Now, I would like to pass the remaining public IP addresses with different ports to dedicated DMZ servers.
To be more clear:
Modem cable (90.xxx.xxx.201)
WAN1 90.xxx.xxx.206 (subnet 90.xxx.xxx.200/29) GW: 90.xxx.xxx.201
WAN2 / DMZ: 10.0.0.0/24 (different 8-port Switch)
LAN1: 192.168.1.0/24 (different 24-port Switch)
There is no connection / (other than the RV320) Road between LAN and DMZ (separate interfaces configured on the VMware host computers)
I don't know if I have to configure the RV320 as gateway or router. The current settings are the entrance door. I have attached a small diagram to make things clearer (hopefully).
Thanks in advance.
Thomas
Hello
I created this document to set up something very similar to what you're asking here. I think that it will suit your needs very well.
Please see the attached document and let me know if it was helpful to you.
Tags: Cisco Support
Similar Questions
-
vSphere 5.5 kickstart to configure the static IP address
Hello people,
I spent some time trying an involuntary installation works correctly and adding features I want.
Right now I'm trying to run a command after installation and reset to configure a static ip address for the host.
I can say that the configuration file is the application, but does not have the IP address. Value DHCP when you are finished.
My KS.cfg file, can someone tell what I do wrong?
Thank you, romatlo
# Example scripted installation file
#
# Accept the VMWare end user license agreement
vmaccepteula
# Set the root for the mode DCUI and Technical Support password
rootpw tet_password1
# The installation media is in the CD drive
install firstdisk - overwritevmfs
# Define the DHCP network on the first network adapter
network - bootproto = dhcp - device = vmnic0 - addvmportgroup = 0
reset
firstboot % - interpreter = busybox
# Assign an IP address to the first VMkernel, used for the management
esxcli ip network interface ipv4 set - name = vmk0-= ipv4 interface 192.168.32.15 - mask = 255.255.255.0 - Gateway = 192.168.32.1 - type static = subnet
Memory, don't you must first create a VMkernel interface?
-name of the interface:-i The name of the VMkernel network interface to the IPv4 settings. This name must be an interface in the interface list command.
Ensure that vmk0 is listed when you run
list of network ip interface
In addition, what happens if you install ESXi manually and run this?
# Assign an IP address to the first VMkernel, used for the management
esxcli ip network interface ipv4 set - name = vmk0-= ipv4 interface 192.168.32.15 - mask = 255.255.255.0 - Gateway = 192.168.32.1 - type static = subnet
FYI in my KS.cfg I have this
network - bootproto = - 192.168.250.21 = static ip - gateway = 192.168.250.1 - nameserver = 192.168.250.6 - subnet mask = 255.255.255.0 - hostname = esxi5---.lab.local head = vmnic0 - addvmportgroup = 0
Instead of
network - bootproto = dhcp - device = vmnic0 - addvmportgroup = 0
and
esxcli ip network interface ipv4 set - name = vmk0-= ipv4 interface 192.168.32.15 - mask = 255.255.255.0 - Gateway = 192.168.32.1 - type static = subnet
-
Modem/router changed by ATT to ARRIS NVG589 and printer not print
ATT changed router/modem and printer does not work. I have a network behind a switch that is connected to the router. No IP settings changed. Computers have static IP addresses 162.193.xxx.xxx and printer 192.168.001.068. For the static subnet is 255.255.255.0. Before the passage of the modem is 255.255.255.48
Hello Roberto,
Thanks for posting your question on the forum of the Microsoft community.
As you said that ATT changed modem, I suggest you to contact them for the correct IP address.
Support ATT
http://www.att.com/eSupport/Thank you
-
Passive routes with OSPF on the PIX
Hello
Having just upgraded my PIX to software v8 finally hoping to participate in OSPF on the network.
The PIX have all many DMZ I want to advertise on OSPF to remove a * much * of fragile static routes but of course I would * not * advertise or get OSPF of these demilitarized. I thought I could do these interfaces passive - or better still, question:
router ospf 1
passive-interface defaultAnd then exempt only the internal interface.
However, (unlike IOS) it seems to be without notion of passive in the implementation of OSPF from the PIX - a place where I thought it would be very useful...
How to distribute the these DMZ on OSPF without advertising OSPF in them?
I had planned to use:
redistributed connected subnets
However, which redistributes things like the public interface of the Internet, I don't want to. In addition, even if there is a way to stop there including the public interface, it seems more prone to the error of the user than passive by default with one exception.
Any ideas? If this is not the case, can I restrict the interfaces in connected subnets redrawn?
Thanks for all the ideas!
Hi Peter,.
Thank you, Yes... I was suggesting to remove network dmz under the OSPF process commands. As you said, it used to really do what you want to do with the removal of the static since its disabling ospf for this network.
Start-up eigrp would seem to be a lot of extra work just to eliminate the static if that's what it will be used for, but it would allow you to make the passive interface that would not accomplish snd/RRs eigrp on the specific interface.
I just re-read your first message and I think I understand now what you're after - which goes back to your first survey of redistribution... you can redistribute static electricity and use a road map to control what roads you want to redistribute. You can then remove the networks for the demilitarized zone under router ospf process.
example:
access-list ospfredist standard permit 10.10.10.0 255.255.255.0
access-list ospfredist standard permit 192.168.10.0 255.255.255.0route-map static-ospf
match ip address ospfredistrouter ospf 10
redistribute static subnets route-map static-ospfthis should redistribute only the statics that you listed above.
hope this helps a bit.
-scott
-
Site to IP - sec site ASA 9.1 worm problem vs IOS
Hi all
I'm trying to set up the vpn site-to site between ASA and IOS, but unsuccessfully router,
newspapers are:
(1) this is not behind a nat device
(2) an encrypted packet received with no counterparty SA
networks are:
172.25.0.0 (inside ASA) A.A.A.A (outside of ASA) is required to connect to the address B.B.B.B router IOS with inside the network 192.168.1.0
Here are the configs:
ASA:
ASA 5505 # sh run
: Saved
:
ASA Version 9.0 (1)
!
hostname ASA 5505
KZ 1 domain name.
names of
vpn_pool_ASA-5505 192.168.172.2 mask - 255.255.255.0 IP local pool 192.168.172.100
local pool SAME_NET_ALA 172.25.66.200 - 172.25.66.210 255.255.255.0 IP mask
!
interface Ethernet0/0
switchport access vlan 2
10 speed
!
interface Ethernet0/1
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
!
interface Ethernet0/7
!
interface Vlan1
nameif inside
security-level 100
IP 172.25.66.15 255.255.255.0
!
interface Vlan2
nameif outside
security-level 0
address IP A.A.A.A 255.255.255.252
!
passive FTP mode
clock timezone ALMST 6
summer time clock ALMDT recurring last Dim Mar 0:00 last Sun Oct 0:00
DNS server-group DefaultDNS
KZ 1 domain name.
permit same-security-traffic inter-interface
permit same-security-traffic intra-interface
network obj_any object
subnet 0.0.0.0 0.0.0.0
network of the NETWORK_OBJ_172.25.66.0_24 object
172.25.66.0 subnet 255.255.255.0
network of the NETWORK_OBJ_192.168.172.0_25 object
subnet 192.168.172.0 255.255.255.128
network of the NETWORK_OBJ_172.25.66.192_27 object
subnet 172.25.66.192 255.255.255.224
network of the ALA_office object
subnet 192.168.1.0 255.255.255.0
network of the NETWORK_OBJ_172.25.0.0_16 object
172.25.0.0 subnet 255.255.0.0
Standard access list SAME_NET_ALA_splitTunnelAcl allow 172.25.66.0 255.255.255.0
SAME_NET_ALA_splitTunnelAcl list standard access allowed 10.0.0.0 255.0.0.0
Standard access list SAME_NET_ALA_splitTunnelAcl allow 172.0.0.0 255.0.0.0
list access VPN-OUT-INS scope ip 192.168.172.0 255.255.255.0 allow no matter what paper
VPN-IN-INS scope any allowed ip access list no matter what paper
extended VPN OUTPUT access list permits all ip 192.168.172.0 255.255.255.0 connect
access list permit VPN OUT ALL standard any4
standard access list net172 allow 172.25.0.0 255.255.0.0
access-list standard net10 allowed 10.0.0.0 255.0.0.0
outside_cryptomap list extended access permitted ip NETWORK_OBJ_172.25.66.0_24 object ALA_office
pager lines 24
Enable logging
asdm of logging of information
Within 1500 MTU
Outside 1500 MTU
no failover
ICMP unreachable rate-limit 1 burst-size 1
ICMP allow any inside
don't allow no asdm history
ARP timeout 14400
no permit-nonconnected arp
NAT (inside, outside) static source NETWORK_OBJ_172.25.66.0_24 NETWORK_OBJ_172.25.66.0_24 NETWORK_OBJ_192.168.172.0_25 NETWORK_OBJ_192.168.172.0_25 non-proxy-arp-search of route static destination
NAT (inside, outside) source static obj_any obj_any NETWORK_OBJ_172.25.66.192_27 NETWORK_OBJ_172.25.66.192_27 non-proxy-arp-search of route static destination
NAT (inside, outside) static source NETWORK_OBJ_172.25.66.0_24 NETWORK_OBJ_172.25.66.0_24 ALA_office ALA_office non-proxy-arp-search of route static destination
!
network obj_any object
NAT dynamic interface (indoor, outdoor)
!
NAT source auto after (indoor, outdoor) dynamic one interface
group-access VPN-IN-INS in the interface inside
group-access VPN-IN-INS interface inside
Route outside 0.0.0.0 0.0.0.0 88.204.136.165 1
Route inside 10.0.0.0 255.0.0.0 172.25.66.1 2
Route inside 172.0.0.0 255.0.0.0 172.25.66.1 1
Timeout xlate 03:00
Pat-xlate timeout 0:00:30
Timeout conn 01:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
Sunrpc timeout 0:10:00 h323 0:05:00 h225 mgcp from 01:00 0:05:00 mgcp-pat 0:05:00
Sip timeout 0:30:00 sip_media 0:02:00 prompt Protocol sip-0: 03:00 sip - disconnect 0:02:00
Timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
Floating conn timeout 0:00:00
dynamic-access-policy-registration DfltAccessPolicy
identity of the user by default-domain LOCAL
the ssh LOCAL console AAA authentication
Enable http server
http 192.168.1.0 255.255.255.0 inside
http 172.25.66.16 255.255.255.255 inside
No snmp server location
No snmp Server contact
Server enable SNMP traps snmp authentication linkup, linkdown warmstart of cold start
Crypto ipsec transform-set ikev1 ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
Crypto ipsec transform-set ikev1 ESP-DES-SHA esp - esp-sha-hmac
Crypto ipsec transform-set ikev1 SHA-ESP-3DES esp-3des esp-sha-hmac
Crypto ipsec transform-set ikev1 esp ESP-DES-MD5-esp-md5-hmac
Crypto ipsec transform-set ikev1 ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
Crypto ipsec transform-set ikev1 ESP-3DES-MD5-esp-3des esp-md5-hmac
Crypto ipsec transform-set ikev1 ESP-AES-256-SHA esp-aes-256 esp-sha-hmac
Crypto ipsec transform-set ikev1 ESP-AES-128-SHA aes - esp esp-sha-hmac
Crypto ipsec transform-set ikev1 ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
Crypto ipsec transform-set ikev1 ESP-AES-128-MD5-esp - aes esp-md5-hmac
Crypto ipsec transform-set ikev1 ESP-AES-128-SHA-TRANS-aes - esp esp-sha-hmac
Crypto ipsec ikev1 transform-set ESP-AES-128-SHA-TRANS mode transit
Crypto ipsec transform-set ikev1 ESP-AES-128-MD5-TRANS-aes - esp esp-md5-hmac
Crypto ipsec ikev1 transform-set ESP-AES-128-MD5-TRANS mode transit
Crypto ipsec transform-set ikev1 ESP-AES-192-SHA-TRANS esp-aes-192 esp-sha-hmac
Crypto ipsec ikev1 transform-set ESP-AES-192-SHA-TRANS mode transit
Crypto ipsec transform-set ikev1 ESP-AES-192-MD5-TRANS esp-aes-192 esp-md5-hmac
Crypto ipsec ikev1 transform-set ESP-AES-192-MD5-TRANS mode transit
Crypto ipsec transform-set ikev1 ESP-AES-256-SHA-TRANS esp-aes-256 esp-sha-hmac
Crypto ipsec ikev1 transform-set ESP-AES-256-SHA-TRANS mode transit
Crypto ipsec transform-set ikev1 ESP-AES-256-MD5-TRANS esp-aes-256 esp-md5-hmac
Crypto ipsec ikev1 transform-set ESP-AES-256-MD5-TRANS mode transit
Crypto ipsec transform-set ikev1 ESP-3DES-SHA-TRANS esp-3des esp-sha-hmac
Crypto ipsec ikev1 transform-set ESP-3DES-SHA-TRANS mode transit
Crypto ipsec transform-set ikev1 ESP-3DES-MD5-TRANS esp-3des esp-md5-hmac
Crypto ipsec ikev1 transform-set ESP-3DES-MD5-TRANS mode transit
Crypto ipsec transform-set ikev1 ESP-DES-SHA-TRANS esp - esp-sha-hmac
Crypto ipsec ikev1 transform-set ESP-DES-SHA-TRANS mode transit
Crypto ipsec transform-set ikev1 ESP-DES-MD5-TRANS esp - esp-md5-hmac
Crypto ipsec ikev1 transform-set ESP-DES-MD5-TRANS mode transit
Crypto ipsec transform-set ikev1 Alma-series esp - aes esp-sha-hmac
Crypto ipsec ikev2 ipsec-proposal OF
encryption protocol esp
Esp integrity sha - 1, md5 Protocol
Crypto ipsec ikev2 proposal ipsec 3DES
Esp 3des encryption protocol
Esp integrity sha - 1, md5 Protocol
Crypto ipsec ikev2 ipsec-proposal AES
Esp aes encryption protocol
Esp integrity sha - 1, md5 Protocol
Crypto ipsec ikev2 ipsec-proposal AES192
Protocol esp encryption aes-192
Esp integrity sha - 1, md5 Protocol
Crypto ipsec ikev2 AES256 ipsec-proposal
Protocol esp encryption aes-256
Esp integrity sha - 1, md5 Protocol
Crypto ipsec pmtu aging infinite - the security association
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 pfs Group1 set
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 define ikev1 transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA MD5-ESP-3DES ESP-DES-SHA ESP-DES-MD5
card crypto outside_map 1 match address outside_cryptomap
outside_map game 1 card crypto peer B.B.B.B
card crypto outside_map 1 set ikev1 Alma-set transform-set
outside_map card crypto 65535-isakmp dynamic ipsec SYSTEM_DEFAULT_CRYPTO_MAP
outside_map interface card crypto outside
inside_map card crypto 65535-isakmp dynamic ipsec SYSTEM_DEFAULT_CRYPTO_MAP
inside crypto map inside_map interface
trustpool crypto ca policy
IKEv2 crypto policy 1
aes-256 encryption
integrity sha
Group 2 of 5
FRP sha
second life 86400
IKEv2 crypto policy 10
aes-192 encryption
integrity sha
Group 2 of 5
FRP sha
second life 86400
IKEv2 crypto policy 20
aes encryption
integrity sha
Group 2 of 5
FRP sha
second life 86400
IKEv2 crypto policy 30
3des encryption
integrity sha
Group 2 of 5
FRP sha
second life 86400
IKEv2 crypto policy 40
the Encryption
integrity sha
Group 2 of 5
FRP sha
second life 86400
Crypto ikev2 allow outside
Crypto ikev1 allow outside
IKEv1 crypto policy 1
preshared authentication
3des encryption
md5 hash
Group 2
life 86400
IKEv1 crypto policy 5
preshared authentication
aes encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 10
authentication crack
aes-256 encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 20
authentication rsa - sig
aes-256 encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 30
preshared authentication
aes-256 encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 40
authentication crack
aes-192 encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 50
authentication rsa - sig
aes-192 encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 60
preshared authentication
aes-192 encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 70
authentication crack
aes encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 80
authentication rsa - sig
aes encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 100
authentication crack
3des encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 110
authentication rsa - sig
3des encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 120
preshared authentication
3des encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 130
authentication crack
the Encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 140
authentication rsa - sig
the Encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 150
preshared authentication
the Encryption
sha hash
Group 2
life 86400
Telnet timeout 5
SSH 0.0.0.0 0.0.0.0 inside
SSH 0.0.0.0 0.0.0.0 outdoors
SSH timeout 5
Console timeout 0dhcpd outside auto_config
!
a basic threat threat detection
Statistics-list of access threat detection
no statistical threat detection tcp-interception
WebVPN
allow outside
No anyconnect essentials
internal web_access group policy
attributes of the strategy of group web_access
clientless ssl VPN tunnel-Protocol
WebVPN
the value of the URL - list PRTG
internal SAME_NET_ALA group policy
SAME_NET_ALA group policy attributes
value of server DNS 8.8.8.8
Ikev1 VPN-tunnel-Protocol
Split-tunnel-policy tunnelspecified
value of Split-tunnel-network-list SAME_NET_ALA_splitTunnelAcl
internal GroupPolicy1 group strategy
attributes of Group Policy GroupPolicy1
Ikev1 VPN-tunnel-Protocol
internal GroupPolicy_to_ALA group strategy
type tunnel-group SAME_NET_ALA remote access
attributes global-tunnel-group SAME_NET_ALA
address SAME_NET_ALA pool
Group Policy - by default-SAME_NET_ALA
IPSec-attributes tunnel-group SAME_NET_ALA
IKEv1 pre-shared-key *.
type tunnel-group web_access remote access
tunnel-group web_access General-attributes
Group Policy - by default-web_access
tunnel-group B.B.B.B type ipsec-l2l
attributes global-tunnel-group B.B.B.B
Group Policy - by default-GroupPolicy1
IPSec-attributes tunnel-Group B.B.B.B
IKEv1 pre-shared-key *.
!
class-map inspection_default
match default-inspection-traffic
!
!
type of policy-card inspect dns preset_dns_map
parameters
maximum message length automatic of customer
message-length maximum 512
Policy-map global_policy
class inspection_default
inspect the preset_dns_map dns
inspect the ftp
inspect h323 h225
inspect the h323 ras
Review the ip options
inspect the netbios
inspect the rsh
inspect the rtsp
inspect the skinny
inspect esmtp
inspect sqlnet
inspect sunrpc
inspect the tftp
inspect the sip
inspect xdmcp
inspect the icmp
inspect the http
!
context of prompt hostname
no remote anonymous reporting call
Cryptochecksum:932099620805dc22d9e48a5e04314887
: endand router IOS:
R1921_center #sh run
Building configuration...Current configuration: 6881 bytes
!
! Last configuration change to 12:22:45 UTC Friday, August 29, 2014 by yerzhan
version 15.2
horodateurs service debug datetime msec
Log service timestamps datetime msec
no password encryption service
!
hostname R1921_center
!
boot-start-marker
boot-end-marker
!
!
logging buffered 51200 warnings
!
AAA new-model
!
!
AAA authentication login userauthen local
AAA authorization groupauthor LAN
!
!
!
!
!
AAA - the id of the joint session
!
IP cef
!
!
!
!!
!
!
!
"yourdomain.com" of the IP domain name
No ipv6 cef
!
Authenticated MultiLink bundle-name Panel
!
!
Crypto pki trustpoint TP-self-signed-260502430
enrollment selfsigned
name of the object cn = IOS - Self - signed - certificate - 260502430
revocation checking no
rsakeypair TP-self-signed-260502430
!
!
TP-self-signed-260502430 crypto pki certificate chain
certificate self-signed 01
30820229 30820192 A0030201 02020101 300 D 0609 2A 864886 F70D0101 05050030
2 060355 04031325 494F532D 53656 C 66 2 AND 536967 6E65642D 43657274 30312E30
69666963 32363035 30323433 30301E17 313331 31323630 35343131 0D 6174652D
355A170D 2E302C06 1325494F 03550403 32303031 30313030 30303030 5A 303031
532D 5365 6C662D53 69676E65 642D 4365 72746966 69636174 652 3236 30353032
06092A 86 4886F70D 01010105 34333030 819F300D 00308189 02818100 0003818D
C178A16C 26637 HAS 32 E2FE6EB2 DE63FC5D 2F4096D2 1A223CAF 52A122A1 F152F0E0
D2305008 FA312D36 E055D09C 487A01D5 629F8DE4 42FF0444 4B3B107A 730111B 6
F6439BA2 970EFE71 C9127F72 F93603E0 11B3F622 73DB1D7C 1889D57C 88C3B141
ED39B0EA 377CE1F7 610F9C76 FC9C843F A81AEFFE 07917A4B 2946032B 207160B 9
02030100 01A 35330 03551 D 13 51300F06 0101FF04 05300301 01FF301F 0603551D
23041830 1680146B B9F671FA BDD822DF 76802EEA 161D18D6 1 060355 9B8C4030
1D0E0416 04146BB9 F671FABD D822DF76 802EEA16 1D18D69B 8C40300D A 06092, 86
01010505 00038181 00B0C56F F1F4F85C 5FE7BF24 27D1DF41 7E9BB9CE 4886F70D
0447910A E780FA0D 07209827 3A969CD0 14AAA496 12929830 0D17F684 7F841261
56365D9C AA15019C ABC74D0A 3CD4E002 F63AA181 B3CC4461 4E56E58D C8237899
29F48CFA 67C4B84B 95D456C3 F0CF858D 43C758C3 C285FEF1 C002E2C5 DCFB9A8A
6A1DF7E3 EE675EAF 7A608FB7 88
quit smoking
license udi pid CISCO1921/K9 sn FCZ1748C14U
!
redundancy
!
!
!
!
!
!
!
crypto ISAKMP policy 1
BA 3des
md5 hash
preshared authentication
Group 2
!
crypto ISAKMP policy 3
BA 3des
preshared authentication
Group 2
!
crypto ISAKMP policy 5
BA aes 256
preshared authentication
Group 2
PSK - KEY key crypto isakmp A.A.A.A address
PSK - KEY crypto isakmp key address 6 0.0.0.0
!
Configuration group crypto isakmp ALA-EMP-VPN client
key *. *. *. *
DNS 8.8.8.8
domain cisco.com
pool ippool
ACL 101
netmask 255.255.255.0
!
!
Crypto ipsec transform-set esp-3des esp-md5-hmac dmvpn_alad
transport mode
Crypto ipsec transform-set esp-3des esp-md5-hmac RIGHT
tunnel mode
Crypto ipsec transform-set esp-3des esp-md5-hmac TRIPSECMAX
transport mode
Crypto ipsec transform-set AES - SHA aes - esp esp-sha-hmac
tunnel mode
!
Profile of crypto ipsec MAXPROFILE
game of transformation-TRIPSECMAX
!
!
Crypto ipsec profile dmvpn_profile
Set transform-set dmvpn_alad
!
!
Crypto-map dynamic dynmap 10
Set transform-set RIGHT
market arriere-route
!
!
!
map clientmap client to authenticate crypto list userauthen
card crypto clientmap isakmp authorization list groupauthor
client configuration address map clientmap crypto answer
20 ipsec-isakmp crypto map clientmap
defined by peer A.A.A.A
game of transformation-AES-SHA
match address VPN_ASA_PAV
!
!
!
!
!
interface Loopback1
IP 10.10.10.10 address 255.255.255.255
!interface tunnels2
IP 192.168.101.1 255.255.255.240
no ip redirection
authentication of the PNDH IP NHRPMAX
dynamic multicast of IP PNDH map
PNDH id network IP-4679
dissemination of IP ospf network
IP ospf hello-interval 30
IP ospf priority 10
source of tunnel GigabitEthernet0/1
multipoint gre tunnel mode
tunnel key 4679
!
the Embedded-Service-Engine0/0 interface
no ip address
Shutdown
!
interface GigabitEthernet0/0
Description to_LAN
IP 192.168.1.253 255.255.255.0
IP nat inside
IP virtual-reassembly in
automatic duplex
automatic speed
!
interface GigabitEthernet0/1
Description to_ISP
address IP B.B.B.B 255.255.255.252
NAT outside IP
IP virtual-reassembly in
automatic duplex
automatic speed
clientmap card crypto
!
router ospf 100
Auto-cout reference-bandwidth 1000
0 message digest authentication box
area 192.168.1.0 digest authentication message
redistribute static subnets
passive-interface default
no passive-interface Tunnel1
network of 10.10.10.10 0.0.0.0 area 192.168.1.0
network 192.168.1.0 0.0.0.255 area 192.168.1.0
192.168.222.0 network 0.0.0.15 area 0
!
router ospf 1
router ID 1.1.1.1
redistribute static subnets
passive-interface default
no passive-interface tunnels2
network of 10.10.10.10 0.0.0.0 area 192.168.1.0
network 192.168.1.0 0.0.0.255 area 192.168.1.0
192.168.101.0 network 0.0.0.15 area 0
!
IP local pool ippool 192.168.33.1 192.168.33.20
IP forward-Protocol ND
!
IP http server
23 class IP http access
local IP http authentication
IP http secure server
IP http timeout policy slowed down 60 life 86400 request 10000
!
overload of IP nat inside source list 111 interface GigabitEthernet0/1
IP nat inside source static tcp 192.168.1.11 22 Expandable 8022 B.B.B.B
IP route 0.0.0.0 0.0.0.0 B.B.B.C
!
extended ACL - NAT IP access list
deny ip 192.168.1.0 0.0.0.255 172.25.0.0 0.0.255.255
allow an ip
IP extended ACL - VPN access list
ip permit 192.168.1.0 0.0.0.255 172.25.0.0 0.0.255.255
VPN_ASA_PAV extended IP access list
ip permit 192.168.1.0 0.0.0.255 172.25.66.0 0.0.0.255
!
access-list 101 permit ip 192.168.1.0 0.0.0.255 192.168.33.0 0.0.0.255
access-list 111 deny ip 192.168.1.0 0.0.0.255 192.168.33.0 0.0.0.255
access ip-list 111 allow a whole
!
!
!
!
!
control plan
!
!
!
Line con 0
line to 0
line 2
no activation-character
No exec
preferred no transport
transport output pad rlogin lapb - your MOP v120 udptn ssh telnet
StopBits 1
line vty 0 4
exec-timeout 0 0
privilege level 15
transport input telnet ssh
line vty 5 15
exec-timeout 0 0
privilege level 15
transport input telnet ssh
!
Scheduler allocate 20000 1000
!
endThe biggest problem is the incompatibility in the VPN access lists.
The ASA said
outside_cryptomap list extended access permitted ip NETWORK_OBJ_172.25.66.0_24 object ALA_office
The router said
ip permit 192.168.1.0 0.0.0.255 172.25.0.0 0.0.255.255
Match them. If it still does not work then please post the revised configurations.
HTH
Rick
-
VPN site-to-site between ASA 5505 and 2911
Hi all
I'm trying to setup VPN S2S. A.a.a.a of ip for the router 2911 office, remote office ASA 5505 8.4 (3) with ip b.b.b.b, but no luck.
2911 config:
!
version 15.2
horodateurs service debug datetime msec
Log service timestamps datetime msec
encryption password service
!
host name 2911
!
boot-start-marker
Boot system flash c2900-universalk9-mz. Spa. 152 - 2.T.bin
boot-end-marker
!
!
Min-length 10 Security passwords
logging buffered 51200 warnings
!
No aaa new-model
!
!
min-threshold queue spd IPv6 62
Max-threshold queue spd IPv6 63
No ipv6 cef
the 5 IP auth-proxy max-login-attempts
max-login-attempts of the IP 5 admission
!
!
!
DHCP excluded-address IP 192.168.10.1 192.168.10.99
DHCP excluded-address IP 192.168.22.1 192.168.22.99
DHCP excluded-address IP 192.168.33.1 192.168.33.99
DHCP excluded-address IP 192.168.44.1 192.168.44.99
DHCP excluded-address IP 192.168.55.1 192.168.55.99
192.168.10.240 IP dhcp excluded-address 192.168.10.254
DHCP excluded-address IP 192.168.22.240 192.168.22.254
DHCP excluded-address IP 192.168.33.240 192.168.33.254
DHCP excluded-address IP 192.168.44.240 192.168.44.254
DHCP excluded-address IP 192.168.55.240 192.168.55.254
!
desktop IP dhcp pool
import all
network 192.168.33.0 255.255.255.0
router by default - 192.168.33.254
192.168.10.10 DNS server 202.50.246.41 202.50.246.42
local domain name
-192.168.10.10 NetBIOS name server
h-node NetBIOS node type
!
wi - fi IP dhcp pool
import all
network 192.168.44.0 255.255.255.0
192.168.10.10 DNS server 202.50.246.41 202.50.246.42
local domain name
router by default - 192.168.44.254
-192.168.10.10 NetBIOS name server
h-node NetBIOS node type
!
DMZ IP dhcp pool
import all
network 192.168.55.0 255.255.255.0
192.168.10.10 DNS server 202.50.246.41 202.50.246.42
local domain name
router by default - 192.168.55.254
-192.168.10.10 NetBIOS name server
h-node NetBIOS node type
!
IP dhcp pool voip
import all
network 192.168.22.0 255.255.255.0
192.168.10.10 DNS server 202.50.246.41 202.50.246.42
local domain name
router by default - 192.168.22.254
-192.168.10.10 NetBIOS name server
h-node NetBIOS node type
!
IP dhcp pool servers
import all
network 192.168.10.0 255.255.255.0
default router 192.168.10.254
192.168.10.10 DNS server 202.50.246.41 202.50.246.42
local domain name
-192.168.10.10 NetBIOS name server
h-node NetBIOS node type
!
!
IP domain name of domain
name-server IP 192.168.10.10
IP cef
connection-for block 180 tent 3-180
Timeout 10
VLAN ifdescr detail
!
Authenticated MultiLink bundle-name Panel
!
!
Crypto pki token removal timeout default 0
!
Crypto pki trustpoint TP-self-signed-3956567439
enrollment selfsigned
name of the object cn = IOS - Self - signed - certificate - 3956567439
revocation checking no
rsakeypair TP-self-signed-3956567439
!
!
TP-self-signed-3956567439 crypto pki certificate chain
certificate self-signed 01 nvram:IOS - Self-Sig #1.cer
license udi pid sn CISCO2911/K9
!
!
the FULL_NET object-group network
full range of the network Description
192.168.10.0 255.255.255.0
192.168.11.0 255.255.255.0
192.168.22.0 255.255.255.0
192.168.33.0 255.255.255.0
192.168.44.0 255.255.255.0
!
object-group network limited
description without servers and router network
192.168.22.0 255.255.255.0
192.168.33.0 255.255.255.0
192.168.44.0 255.255.255.0
!
VTP version 2
password username admin privilege 0 password 7
!
redundancy
!
!
!
!
!
no passive ftp ip
!
!
crypto ISAKMP policy 10
BA aes 256
sha512 hash
preshared authentication
ISAKMP crypto key admin address b.b.b.b
invalid-spi-recovery crypto ISAKMP
!
!
Crypto ipsec transform-set esp - aes esp-sha-hmac SET
!
!
!
10 map ipsec-isakmp crypto map
the value of b.b.b.b peer
Set transform-set
match address 160
!
!
!
!
!
Interface Port - Channel 1
no ip address
waiting-150 to
!
Interface Port - channel1.1
encapsulation dot1Q 1 native
IP 192.168.11.254 255.255.255.0
IP nat inside
IP virtual-reassembly in
!
Interface Port - channel1.10
encapsulation dot1Q 10
IP address 192.168.10.254 255.255.255.0
IP nat inside
IP virtual-reassembly in
!
Interface Port - channel1.22
encapsulation dot1Q 22
IP 192.168.22.254 255.255.255.0
IP nat inside
IP virtual-reassembly in
!
Interface Port - channel1.33
encapsulation dot1Q 33
IP 192.168.33.254 255.255.255.0
IP nat inside
IP virtual-reassembly in
!
Interface Port - channel1.44
encapsulation dot1Q 44
IP 192.168.44.254 255.255.255.0
IP nat inside
IP virtual-reassembly in
!
Interface Port - channel1.55
encapsulation dot1Q 55
IP 192.168.55.254 255.255.255.0
IP nat inside
IP virtual-reassembly in
!
the Embedded-Service-Engine0/0 interface
no ip address
Shutdown
!
interface GigabitEthernet0/0
Description $ETH-LAN$$ETH-SW-LAUNCH$$INTF-INFO-GE $ 0/0
no ip address
Shutdown
automatic duplex
automatic speed
!
interface GigabitEthernet0/1
no ip address
automatic duplex
automatic speed
channel-group 1
!
interface GigabitEthernet0/2
Description $ES_LAN$
no ip address
automatic duplex
automatic speed
channel-group 1
!
interface GigabitEthernet0/0/0
IP address a.a.a.a 255.255.255.224
NAT outside IP
IP virtual-reassembly in
automatic duplex
automatic speed
crypto map
!
IP forward-Protocol ND
!
no ip address of the http server
23 class IP http access
local IP http authentication
IP http secure server
IP http timeout policy slowed down 60 life 86400 request 10000
!
overload of IP nat inside source list NAT_INTERNET interface GigabitEthernet0/0/0
IP nat inside source udp 500 interface GigabitEthernet0/0/0 500 a.a.a.a static
IP route 0.0.0.0 0.0.0.0 xxx.xxx.xxx.xxx
!
NAT_INTERNET extended IP access list
refuse the object-group ip FULL_NET 192.168.17.0 0.0.0.255
refuse the object-group ip FULL_NET 192.168.1.0 0.0.0.255
permit ip FULL_NET object-group everything
!
access-list 1 permit 192.168.44.100
access-list 23 allow 192.168.10.7
access-list 23 permit 192.168.44.0 0.0.0.255
access-list 100 permit ip 192.168.10.0 0.0.0.255 192.168.17.0 0.0.0.255
access-list 160 permit ip 192.168.10.0 0.0.0.255 192.168.17.0 0.0.0.255
!
!
!
control plan
!
!
!
Line con 0
password password 7
opening of session
line to 0
line 2
no activation-character
No exec
preferred no transport
transport of entry all
transport output pad rlogin lapb - your MOP v120 udptn ssh telnet
StopBits 1
line vty 0 4
access-class 23 in
privilege level 15
local connection
entry ssh transport
line vty 5 15
access-class 23 in
privilege level 15
local connection
entry ssh transport
!
Scheduler allocate 20000 1000
!
end
The ASA config:
: Saved : ASA Version 8.4(3) ! hostname C domain-name domain enable password password encrypted passwd passwd encrypted names ! interface Ethernet0/0 ! interface Ethernet0/1 shutdown ! interface Ethernet0/2 shutdown ! interface Ethernet0/3 shutdown ! interface Ethernet0/4 shutdown ! interface Ethernet0/5 switchport access vlan 100 ! interface Ethernet0/6 switchport trunk allowed vlan 2,6 switchport mode trunk ! interface Ethernet0/7 shutdown ! interface Vlan1 description INTERNET mac-address 1234.5678.0001 nameif WAN security-level 0 ip address b.b.b.b 255.255.255.248 standby c.c.c.c ospf cost 10 ! interface Vlan2 description OLD-PRIVATE mac-address 1234.5678.0102 nameif OLD-Private security-level 100 ip address 192.168.17.2 255.255.255.0 standby 192.168.17.3 ospf cost 10 ! interface Vlan6 description MANAGEMENT mac-address 1234.5678.0106 nameif Management security-level 100 ip address 192.168.1.2 255.255.255.0 standby 192.168.1.3 ospf cost 10 ! interface Vlan100 description LAN Failover Interface ! boot system disk0:/asa843-k8.bin ftp mode passive clock timezone NZST 12 clock summer-time NZDT recurring 1 Sun Oct 2:00 3 Sun Mar 2:00 dns domain-lookup WAN dns server-group DefaultDNS name-server 208.67.222.222 domain-name domain same-security-traffic permit intra-interface object network obj-192.168.17.0 subnet 192.168.17.0 255.255.255.0 object network obj-192.168.10.0 subnet 192.168.10.0 255.255.255.0 object network obj-192.168.2.0 subnet 192.168.2.0 255.255.255.0 object network obj-192.168.9.0 subnet 192.168.9.0 255.255.255.0 object network obj-192.168.33.0 subnet 192.168.33.0 255.255.255.0 object network obj-192.168.44.0 subnet 192.168.44.0 255.255.255.0 object network obj_any object network obj_any-01 object network NETWORK_OBJ_192.168.10.0_24 subnet 192.168.10.0 255.255.255.0 object network NETWORK_OBJ_192.168.17.0_24 subnet 192.168.17.0 255.255.255.0 object network subnet-00 subnet 0.0.0.0 0.0.0.0 object-group protocol TCPUDP protocol-object udp protocol-object tcp object-group service RDP tcp description RDP port-object eq 3389 object-group network DM_INLINE_NETWORK_1 network-object 192.168.17.0 255.255.255.0 network-object 192.168.10.0 255.255.255.0 network-object 192.168.33.0 255.255.255.0 network-object 192.168.44.0 255.255.255.0 object-group network DM_INLINE_NETWORK_2 network-object 192.168.10.0 255.255.255.0 network-object 192.168.33.0 255.255.255.0 network-object 192.168.44.0 255.255.255.0 object-group network subnet-17 network-object 192.168.17.0 255.255.255.0 object-group network subnet-2 network-object 192.168.2.0 255.255.255.0 object-group network subnet-9 network-object 192.168.9.0 255.255.255.0 object-group network subnet-10 network-object 192.168.10.0 255.255.255.0 access-list LAN_nat0_outbound extended permit ip 192.168.17.0 255.255.255.0 192.168.10.0 255.255.255.0 access-list LAN_nat0_outbound extended permit ip 192.168.17.0 255.255.255.0 192.168.9.0 255.255.255.0 access-list LAN_IP standard permit 192.168.17.0 255.255.255.0 access-list WAN_access_in extended permit ip any any log debugging access-list WAN_access_in extended permit tcp any object-group RDP any object-group RDP log debugging access-list WAN_access_in extended permit icmp x.x.x.x 255.255.255.248 192.168.10.0 255.255.255.0 access-list MANAGEMENT_access_in extended permit ip any any log debugging access-list OLD-PRIVATE_access_in extended permit ip any any log debugging access-list OLD-PRIVATE_access_in extended permit icmp any object-group DM_INLINE_NETWORK_1 access-list 101 extended permit tcp host 192.168.10.7 any eq 3389 log debugging access-list WAN_1_cryptomap extended permit ip 192.168.1.0 255.255.255.0 192.168.10.0 255.255.255.0 access-list WAN_1_cryptomap extended permit ip 192.168.17.0 255.255.255.0 192.168.9.0 255.255.255.0 access-list WAN_cryptomap_2 extended permit ip 192.168.1.0 255.255.255.0 192.168.10.0 255.255.255.0 access-list CiscoVPNClient_splitTunnelAcl standard permit 192.168.17.0 255.255.255.0 access-list LAN_access_in extended permit ip any any log debugging access-list WAN_nat0_outbound extended permit ip 192.168.17.0 255.255.255.0 192.168.10.0 255.255.255.0 access-list WAN_nat0_outbound extended permit ip 192.168.17.0 255.255.255.0 192.168.2.0 255.255.255.0 access-list WAN_nat0_outbound extended permit ip 192.168.17.0 255.255.255.0 192.168.9.0 255.255.255.0 access-list WAN_2_cryptomap extended permit ip 192.168.17.0 255.255.255.0 192.168.10.0 255.255.255.0 access-list WAN_2_cryptomap extended permit ip 192.168.17.0 255.255.255.0 192.168.9.0 255.255.255.0 access-list LAN_IP_inbound standard permit 192.168.10.0 255.255.255.0 access-list inside_nat0_outbound extended permit ip 192.168.10.0 255.255.255.0 192.168.17.0 255.255.255.0 access-list vpnusers_splitTunnelAcl extended permit ip 192.168.17.0 255.255.255.0 any access-list nonat-in extended permit ip 192.168.17.0 255.255.255.0 192.168.2.0 255.255.255.0 pager lines 24 logging enable logging buffer-size 52000 logging monitor informational logging trap informational logging asdm informational logging from-address syslog logging recipient-address admin level errors logging host OLD-Private 192.168.17.110 format emblem logging debug-trace logging permit-hostdown mtu WAN 1500 mtu OLD-Private 1500 mtu Management 1500 ip local pool VPN_Admin_IP 192.168.1.150-192.168.1.199 mask 255.255.255.0 ip local pool vpnclient 192.168.2.1-192.168.2.5 mask 255.255.255.0 failover failover lan unit primary failover lan interface failover Vlan100 failover polltime interface 15 holdtime 75 failover key ***** failover interface ip failover 192.168.100.1 255.255.255.0 standby 192.168.100.2 icmp unreachable rate-limit 1 burst-size 1 icmp permit 192.168.10.0 255.255.255.0 WAN icmp permit host x.x.x.x WAN icmp permit 192.168.17.0 255.255.255.0 WAN icmp permit host c.c.c.c WAN icmp permit host a.a.a.a WAN icmp deny any WAN icmp permit 192.168.10.0 255.255.255.0 OLD-Private icmp permit 192.168.17.0 255.255.255.0 OLD-Private icmp permit host a.a.a.a OLD-Private icmp permit host 192.168.10.0 Management icmp permit host 192.168.17.138 Management icmp permit 192.168.1.0 255.255.255.0 Management icmp permit host 192.168.1.26 Management icmp permit host a.a.a.a Management asdm image disk0:/asdm-647.bin no asdm history enable arp timeout 14400 nat (OLD-Private,any) source static subnet-17 subnet-17 destination static subnet-10 subnet-10 no-proxy-arp nat (OLD-Private,any) source static subnet-17 subnet-17 destination static subnet-2 subnet-2 no-proxy-arp nat (OLD-Private,any) source static subnet-17 subnet-17 destination static subnet-9 subnet-9 no-proxy-arp nat (Management,WAN) source static NETWORK_OBJ_192.168.17.0_24 NETWORK_OBJ_192.168.17.0_24 destination static NETWORK_OBJ_192.168.10.0_24 NETWORK_OBJ_192.168.10.0_24 no-proxy-arp route-lookup ! object network subnet-00 nat (OLD-Private,WAN) dynamic interface access-group WAN_access_in in interface WAN access-group OLD-PRIVATE_access_in in interface OLD-Private access-group MANAGEMENT_access_in in interface Management route WAN 0.0.0.0 0.0.0.0 x.x.x.x 1 timeout xlate 3:00:00 timeout pat-xlate 0:00:30 timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02 timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00 timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00 timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute timeout tcp-proxy-reassembly 0:01:00 timeout floating-conn 0:00:00 dynamic-access-policy-record DfltAccessPolicy user-identity default-domain LOCAL aaa authentication ssh console LOCAL aaa local authentication attempts max-fail 10 http server enable http b.b.b.b 255.255.255.255 WAN http 0.0.0.0 0.0.0.0 WAN no snmp-server location no snmp-server contact snmp-server enable traps snmp authentication linkup linkdown coldstart service resetoutside crypto ipsec ikev1 transform-set OFFICE esp-aes esp-sha-hmac crypto map WAN_map 1 match address WAN_1_cryptomap crypto map WAN_map 1 set pfs crypto map WAN_map 65535 ipsec-isakmp dynamic SYSTEM_DEFAULT_CRYPTO_MAP crypto map Office 2 match address WAN_1_cryptomap crypto map Office 2 set peer a.a.a.a crypto map Office interface WAN crypto map MAP 10 set peer a.a.a.a crypto map MAP 10 set ikev1 transform-set OFFICE crypto ikev2 enable WAN crypto ikev1 enable WAN crypto ikev1 policy 10 authentication pre-share encryption 3des hash sha group 2 lifetime 86400 crypto ikev1 policy 30 authentication pre-share encryption des hash sha group 1 lifetime 86400 telnet timeout 5 ssh a.a.a.a 255.255.255.255 WAN ssh timeout 30 ssh version 2 console timeout 0 dhcpd auto_config OLD-Private ! threat-detection basic-threat threat-detection statistics host threat-detection statistics access-list threat-detection statistics tcp-intercept rate-interval 30 burst-rate 400 average-rate 200 ntp server 129.6.15.28 source WAN prefer webvpn group-policy DfltGrpPolicy attributes vpn-tunnel-protocol ikev1 ssl-client ssl-clientless group-policy admin internal group-policy admin attributes dns-server value 208.67.222.222 156.154.70.1 vpn-tunnel-protocol ikev1 group-policy GroupPolicy_a.a.a.a internal group-policy GroupPolicy_a.a.a.a attributes vpn-tunnel-protocol ikev1 ikev2 group-policy CiscoVPNClient internal group-policy CiscoVPNClient attributes vpn-idle-timeout 30 vpn-session-timeout none vpn-tunnel-protocol ikev1 l2tp-ipsec ssl-clientless split-tunnel-policy tunnelspecified split-tunnel-network-list value CiscoVPNClient_splitTunnelAcl username admin password password encrypted privilege 15 tunnel-group admin type remote-access tunnel-group admin general-attributes address-pool vpnclient authorization-server-group LOCAL default-group-policy admin tunnel-group a.a.a.a type ipsec-l2l tunnel-group a.a.a.a general-attributes default-group-policy GroupPolicy_a.a.a.a tunnel-group a.a.a.a ipsec-attributes ikev1 pre-shared-key ***** ikev2 remote-authentication pre-shared-key ***** ikev2 local-authentication pre-shared-key ***** tunnel-group CiscoVPNClient type remote-access tunnel-group CiscoVPNClient general-attributes address-pool vpnclient default-group-policy CiscoVPNClient tunnel-group CiscoVPNClient ipsec-attributes ikev1 pre-shared-key ***** ! class-map inspection_default match default-inspection-traffic ! ! policy-map type inspect dns preset_dns_map parameters message-length maximum client auto message-length maximum 512 policy-map global_policy class inspection_default inspect dns preset_dns_map inspect ftp inspect h323 h225 inspect h323 ras inspect rsh inspect rtsp inspect esmtp inspect sqlnet inspect skinny inspect sunrpc inspect xdmcp inspect sip inspect netbios inspect tftp inspect ip-options inspect icmp ! service-policy global_policy global smtp-server 192.168.17.10 prompt hostname context no call-home reporting anonymous call-home contact-email-addr admin contact-name admin profile CiscoTAC-1 no active : end asdm image disk0:/asdm-647.bin asdm location c.c.c.c 255.255.255.255 WAN asdm location 192.168.17.2 255.255.255.255 WAN asdm location a.a.a.a 255.255.255.255 OLD-Private no asdm history enable
ASA:
# show crypto ipsec his
There is no ipsec security associations
# show crypto isakmp his
There are no SAs IKEv1
There are no SAs IKEv2
2911:
#show crypto ipsec his
Interface: GigabitEthernet0/0/0
Tag crypto map: map, addr a.a.a.a local
protégé of the vrf: (none)
local ident (addr, mask, prot, port): (192.168.10.0/255.255.255.0/0/0)
Remote ident (addr, mask, prot, port): (192.168.17.0/255.255.255.0/0/0)
current_peer b.b.b.b port 500
LICENCE, flags is {origin_is_acl},
#pkts program: encrypt 0, #pkts: 0, #pkts digest: 0
#pkts decaps: 0, #pkts decrypt: 0, #pkts check: 0
compressed #pkts: 0, unzipped #pkts: 0
#pkts uncompressed: 0, #pkts compr. has failed: 0
#pkts not unpacked: 0, #pkts decompress failed: 0
Errors of #send 4, #recv errors 0
local crypto endpt. : a.a.a.a, remote Start crypto. : b.b.b.b
Path mtu 1500, mtu 1500 ip, ip mtu IDB GigabitEthernet0/0/0
current outbound SPI: 0x0 (0)
PFS (Y/N): N, Diffie-Hellman group: no
SAS of the esp on arrival:
-Other - arrival ah sas:
-More-
-More - CFP sas on arrival:
-More-
-More - outgoing esp sas:
-More-
-More - out ah sas:
-More-
-More - out CFP sas:
Thanks for your time,
Nick
Please add
map Office 2 set transform-set OFFICE ikev1 crypto
If it is not helpful, please enable debug crypto ipsec 255 and paste here.
HTH. Please rate if it was helpful. "Correct answer" will be also pleasant.
-
Annyconnect customers can reach inside of the authorized apps but NO ICMP
Hi community expensive cisco.I have a Setup with Cisco asa 8.4 and customers connection to a server on the inside interface.All provide very fine, can reach all applications and all that, BUT, the ICMP would go through.I checked doucble, server recevives fine the echo icmp message and good answers.It's my ASA that blocks the response to echo, due to problem NAT packets according to the newspapers:6 June 26, 2014 16:00:06 302020 172.16.23.1 AAA 1. BBB. CCC.1 0 built ICMP incoming connections for 172.16.23.1/1(LOCAL\customer1 faddr) gaddr AAA. BBB. CCC.1/0 laddr AAA. BBB. CCC.1/0 (customer1)3 June 26, 2014 16:00:07 305006 AAA. BBB. CCC.1 172.16.23.1 failed to create LOCAL regular translation for icmp src everything: AAA. BBB. CCC.1 dst OUTSIDE:172.16.23.1(LOCAL\customer1) (type 0, code 0)6 June 26, 2014 16:00:08 302021 172.16.23.1 AAA 1. BBB. 0 connection disassembly ICMP for faddr 172.16.23.1/1(LOCAL\customer1 CCC.1) gaddr AAA. BBB. CCC.1/0 laddr AAA. BBB. CCC.1/0 (customer1)Here is an excerpt of my config:network of the VPN_POOL_CLTS object172.16.23.0 subnet 255.255.255.0network of the INSIDE_SERVERS_NET objectsubnet YYYY. BBB. CCC.0 255.255.255.0any description of the NAT interface overloading dynamic source NAT (all, OUTSIDE)NAT (-all), source VPN_POOL_CLTS VPN_POOL_CLTS static non-proxy-arpI think that there is a NAT problem, so I would add the line to follow before the two first lines of NAT configuration:NAT (INSIDE, OUTSIDE) source static INSIDE_SERVERS_NET INSIDE_SERVERS_NET no proxy-arpDon't you think that this will solve the problem?Why all traffic flows would work but the ICMP?Thank you all for reading.Hi Florian.
If you look at the values of logging for icmp deny
305006
% ASA-3-305006 error message: {(statique sortant | identité | portmap | régulière) failed to create the translation of Protocol src interface_name : source_address / source_port [( idfw_user )] dst interface_name : dest_address / dest_port [( idfw_user )]}
Explanation Protocol (TCP, UDP or ICMP) A failed to create a translation through the ASA. The ASA does not packets through which are intended for network addresses or dissemination. The ASA provides this checking for addresses that are explicitly identified with static controls. For inbound traffic, the ASA rejects the translation of IP address identified as a network or broadcast address.
The ASA does not apply PAT to all types of ICMP messages. It applies only the packets of echo and response to echo ICMP PAT (types 8 and 0). Specifically, only ICMP echo packets or echo response create a PAT translation. Thus, when other types of ICMP messages are removed, this message is generated.
The ASA uses the global IP address and the mask of static controls configured to differentiate it from the IP addresses of network or broadcast IP addresses. If the global IP address is a valid network with a netmask corresponding address, then the ASA does not have a translation for the network or broadcast with incoming packets IP addresses.
For example:
public static 10.2.2.128 (Interior, exterior) 10.1.1.128 netmask 255.255.255.128The ASA responds to global addresses 10.2.2.128 as a network address and 10.2.2.255 as the broadcast address. Without an existing translation, the ASA rejects the incoming packets intended for 10.2.2.128 or 10.2.2.255 and logs this message.
When the suspected IP address is an IP address from the host, configure a separate static command with a host mask in front of the static subnet command (the first matching rule for static controls). The following static commands cause the ASA answer to the 10.2.2.128 as a host address:
public static 10.2.2.128 (Interior, exterior) 10.2.2.128 netmask 255.255.255.255
public static 10.2.2.128 (Interior, exterior) 10.2.2.128 netmask 255.255.255.128The translation can be created by the traffic started inside host with the IP address in question. Because the ASA considers a network or IP address of dissemination as a host with a static configuration of subnet IP address overlap, the two static controls network address translation must be the same.
Recommended not required action.
302020
Error Message % ASA-6-302020: Built {in | out} bound connection ICMP for faddr { faddr |} icmp_seq_num } [( idfw_user )] gaddr { gaddr |} cmp_type } laddr laddr [( idfw_user )]
Session year ICMP explanation has been created in the fast path when ICMP stateful has been activated using the icmp command inspect.
Recommended not required action.
So the rule similar like below would solve your problem.
NAT (inside, outside) static source OBJ_INTERNAL OBJ_INTERNAL OBJ_VPN OBJ_VPN non-proxy-arp-search of route static destination
Concerning
Knockaert
-
It is possible to allow (configure) transfer of intellectual property realized emissions from a hosts specified as a source on a running 6.3 PIX firewall?
I've seen this done on IOS, but could not find a reference for him for the PIX.
Thank you.
This is probably more information that you have always dreamed about the topic. Sorry, but I got on a roll...
By default, for inbound traffic, the PIX will deny the translations for destiny IP that is identified as a network address or broadcast address. The PIX will use the global IP and mask configured 'static' regularly different IP network/broadcast IP. If the global IP is a valid network with a corresponding address mask network then the PIX prevents the xlate to network/broadcast IPs with incoming packet. For example,.
public static 100.1.1.128 (Interior, exterior) 10.1.1.128 netmask 255.255.255.128
Global address 100.1.1.128 is considered to be 100.1.1.255 as a broadcast address and network address. Without existing xlate, PIX will deny incoming packet destined to 100.1.1.128 or 100.1.1.255 and following syslog is saved.
305006: Dst IP is IP nework/dissemination, translation creation failed for icmp src 3rd: 100.2.1.99 internal dst: 100.2.1.128 (type 8, code 0)
To work around this in cases where the IP is really an IP host, a static separate with host mask must be set up and in front of the static subnet (first game rule for static). The following static method will force the PIX to consider 100.1.1.128 as a host address.
public static 100.1.1.128 (Interior, exterior) 10.1.1.128 netmask 255.255.255.255
public static 100.1.1.128 (Interior, exterior) 10.1.1.128 netmask 255.255.255.128
Note, the xlate can be created by the traffic starts from within host with the IP address in question.
Slightly a bit clear?
Scott
-
Allowing ICMP and Telnet via a PIX 525
We are trying to build a new block of distribution to our backbone WAN. We are experiencing a problem when establishing ICMP and Telnet via the PIX. The following is known:
1 Ping and telnet to the 6509 and internal network works very well for the PIX.
2 Ping the 7206 for the PIX works just fine.
3 debug normal to see activity track ICMP for connections ICMP for the PIX of the network 6509 and internal; However, the debug shows nothing - no activity - during attempts to ping at a.b.5.18. (see below).
In short, all connections seem to be fine between the three devices, however, we can get ICMP and Telnet work correctly through the PIX.
The layout is:
6509 (MSFC) - PIX 525-7206
IP:a.b.5.1 - a.b.5.2 a.b.5.17 - a.b.5.18
255.255.255.0 255.255.255.240 255.255.255.240
(both)
networks: a.b.5.0 a.b.5.16
255.255.255.240 255.255.255.240
6509:
interface VlanX
Description newwan-bb
IP address a.b.5.1 255.255.255.0
no ip redirection
router ospf
Log-adjacency-changes
redistribute static subnets metric 50 metric-type 1
passive-interface default
no passive-interface Vlan9
((other networks omitted))
network a.b.5.0 0.0.0.255 area 0
default information are created
PIX 525:
ethernet0 nameif outside security0
nameif ethernet1 inside the security100
nameif ethernet2 security10 failover
hostname XXXXXX
domain XXX.com
fixup protocol ftp 21
fixup protocol http 80
fixup protocol h323 1720
fixup protocol rsh 514
fixup protocol rtsp 554
fixup protocol smtp 25
fixup protocol sqlnet 1521
fixup protocol sip 5060
fixup protocol 2000 skinny
names of
access ip-list 102 permit a whole
access-list 102 permit icmp any one
access-list 102 permit icmp any any echo
access-list 102 permit icmp any any echo response
access-list 102 permit icmp any any source-quench
access-list 102 permit everything all unreachable icmp
access-list 102 permit icmp any one time exceed
103 ip access list allow a whole
access-list 103 allow icmp a whole
access-list 103 permit icmp any any echo
access-list 103 permit icmp any any echo response
access-list 103 permit icmp any any source-quench
access-list 103 allow all unreachable icmp
access-list 103 allow icmp all once exceed
pager lines 24
opening of session
timestamp of the record
logging buffered stored notifications
interface ethernet0 100full
interface ethernet1 100full
interface ethernet2 100full
Outside 1500 MTU
Within 1500 MTU
failover of MTU 1500
IP address outside a.b.5.17 255.255.255.240
IP address inside a.b.5.2 255.255.255.240
failover from IP 192.168.230.1 255.255.255.252
alarm action IP verification of information
alarm action attack IP audit
history of PDM activate
ARP timeout 14400
Global 1 interface (outside)
NAT (inside) 1 0.0.0.0 0.0.0.0 0 0
Access-group 103 in external interface
Route outside 0.0.0.0 0.0.0.0 a.b.5.18 1
Route inside a.0.0.0 255.0.0.0 a.b.5.1 1
Inside a.b.0.0 255.240.0.0 route a.b.5.1 1
Timeout xlate 03:00
Timeout conn 01:00 half-closed 0: 10:00 udp 0:02:00 CPP 0: h323 from 10:00 0:05:00 sip 0:30:00 sip_media 0:02:00
Timeout, uauth 0:05:00 absolute
GANYMEDE + Protocol Ganymede + AAA-server
RADIUS Protocol RADIUS AAA server
No snmp server location
No snmp Server contact
SNMP-Server Community public
No trap to activate snmp Server
enable floodguard
No sysopt route dnat
Telnet a.0.0.0 255.0.0.0 outdoors
Telnet a.0.0.0 255.0.0.0 inside
Telnet a.b.0.0 255.240.0.0 inside
Telnet a.b.5.18 255.255.255.255 inside
Telnet timeout 5
SSH timeout 5
Terminal width 80
Recognizing any help on proper routing through a PIX 525, given that all this is for a network internal.
on the 6509, why the int has a 24 subnet mask, when everything has a 28? If you try the 6500 ping.18, he thinks that it is on a local network, and there no need to route through the pix
Your access lists are confusing.
access-list # ip allowed any one should let through, and so everything that follows are redundant statements.
for the test,.
alloweverything ip access list allow a whole
Access-group alloweverything in interface outside
should the pix act as a router - you are effectively disabling all firewall features.
-
Ontario Regulation distributes dynamic routes via VPN S2S
Hi halijenn / experts
(1) please let me know if IPP works on a Site in tunnel
(2) I have a behind remote ASA 10.10.1.0 and 10.10.2.0 network that must be distributed to another branch ASA with S2S ASA remote via OSPF
3) there is an L3 Switch behind the ASA of the branch and Switch L3 there is a router that has a default route pointing router WAN
Router WAN
|
|
Users-> router-> L3 Switch-> ASA-> Internet-> remote ASA branch (10.10.1.0, 2.0)Note: 10.10.1.0 2.0 AND are already configured in the ACL Crypto at the ends.
Users are able to reach the 10.10.2.X network to the remote end.
Now for the 10.10.2.0 static routes are already there in the router and the switch finally pointing the ASA branch however as the network grows, it is impossible in the router behind the switch to add static whenever routes (such as the default route to router WAN points). This is why in order to learn routes dynamically, I will add an ospf process to the ASA to branch with the following configuration. Please let me know if iam correct when I add IPP and other OSPF commands to the ASA of the branch. (hope I have nothing to do on ASA remote associated with IPP or OSPF?)
I take just an example of a remote host 1 10.10.1.4. Inside ASA interface leading to users is 172.16.1.0/24
access-list redistribute allowed standard host 10.10.1.4 255.255.255.255
router ospf 1
network 172.16.1.0 255.255.255.0 area 0
Journal-adj-changes
redistribute static subnets redistribute route mapIn addition, I will also be allowing the order for IPP in the encryption of the VPN S2S said card.
Please help me understand if I'm wrong
Pls set the OSPF firstly on the SAA process before removing the static routes. Once you have confirmed that the OSPF is configured correctly and the roads are in the OSPF database, then you can delete the static routes. Static routes will always take precedence over OSPF because it has higher metric. Please keep the default route configured on the SAA.
Hope that confirms it.
-
I deployed my vCenter for my ESXi machine via an OVF file. When a vCenter boots he says no networking was detected because I do not use a DHCP server, then I put the IP and the static subnet. Since I can not ping from the host (windows 7), I can't access the web console Help http://< IP >: 5480 to continue with Setup. I didn't need virtual machines to have access to the internet. All of my virtual machines are on a 12. network. vCenter can only ping the ESXi server, but no one else.
Finally figured it out! VCenter unit had a random MAC address are entrusted to him, and once I changed it to be the same vmnic0, I could ping and connect to the web page of the console.
-
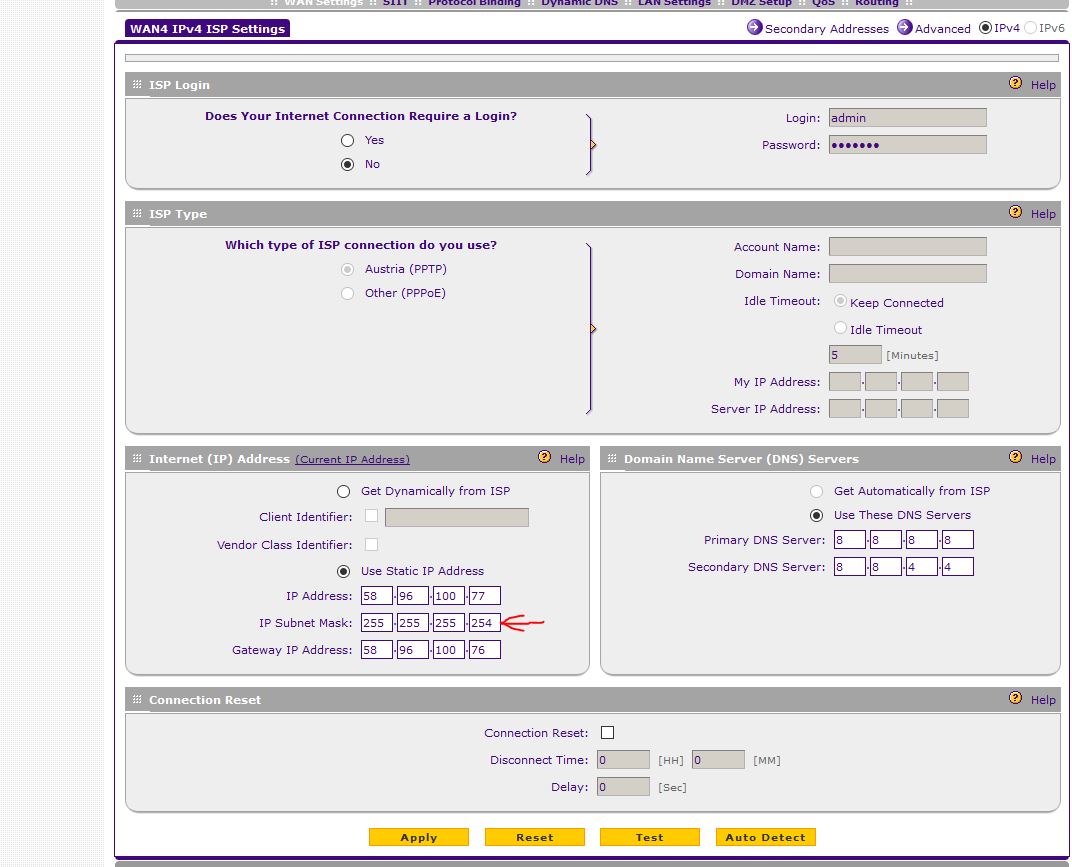
I can't add/subnet mask 31 255.255.255.254 ISP WAN > static IP setting in VPN Firewall SRX5308
Hello
I can't add/subnet mask 31 255.255.255.254 ISP WAN > static IP setting in VPN Firewall SRX5308. When I try to apply it, I get the popup error message like "invalid IP subnet mask. Please enter 0/128/192/224/240/248/252 for octet 4 ". I try to add provider NTU fiber optic internet service in one of the 4 WAN settings. The vendor gave me a 31 block IP and the subnet as 255.255.255.254 mask. It is a limitation in this firewall? I have to ask the provider to give me a 30 block the IP instead? With 30 block IP subnet mask will be 255.255.255.252 who is authorized by this firewall setting. I tried this on another (SnapGear SG560) firewall and it works without any problem. See the screenshots below. Can someone please?
concerning
Ridwan
/ 31 would be used in specific scenarios where you * really * need to keep the address space and on links only point to point. To be honest I've never met anyone, or any ISP that uses it. It works on point to point, because, well, there no need to broadcast address because there are only two devices on the link (one on each side of the cable)... IP address ranges would be;. 0-. 1,.2-. 3, etc.
Most (if not all) Netgear devices will prevent you from setting 31, but you will probably be able to use without problem in all 30 cases, according to the setup of the ISP I do not think that it would cause you problems really. But if you can, I would certainly ask a 30 instead.
-
Configuration of the devices on the same subnet to have a static IP address
Hello. First of all, I'm new here, so Hello to everyone. I'm pretty much a newbie on everything about routers and I would like an answer to a problem that has been bothering me for a while.
I have a Linksys WAG120N Wireless - N ADSL2 + Modem Router. The firmware version is V1.00.12.
I run a Windows machine that is attached to the router which has a certain subnet address. On this same machine, I run a Virtual Machine on Linux, which has its own address, 192.168.1.102.
I noticed that whenever I have shut down the computer and then reactivate them later, they gain another address, which makes it annoying for me to communicate with each other (by, for example, try to load a Web page hosted on the physical machine virtual computer) without knowing the real address, which, as I said earlier, seems to change every time.
I would like to know if there is a way (with my model of router) to configure so that address subnet of these two machines remains the same, regardless of whether or not they have been stopped and restarted.
Is this possible? If Yes, could you please tell me where to find this option in the control panel?
Have you set the DNS server? You must configure at least one DNS server. Configure as DNS server 192.168.1.1 on your computer.
Otherwise, with DHCP enabled, open a command prompt window and type "ipconfig/all". Copy the full output in your next post.
Then configure the static IP address, check if you have the internet, otherwise, run "ipconfig/all" again and also after the full release. Which should show the problem.
-
public static IP on the same subnet of both internet and local
I need to configure my little guy with ip static on the same subnet on the side of the router/internet and the side room, but it does not.
I will allow me to dhcp on the side of the router/internet and then statically assign an ip address from the same subnet on the local side, but then it does not pass on my dhcp server dhcp queries.
suggestions?
Yes. Configure the WRT with a LAN inside your main LAN IP address. Disable the DHCP server on the WRT. Wire then a main WRT to your local area network LAN port. Do not use the internet port on the WRT.
-
Only 1 of the 2 computers in my LAN recognizes my static IP address assigned by my ISP - HELP!
I have an IP address from my ISP, but only one of the two computers in my LAN presents this static IP address in the "ipconfig" and it connects to the internet, the other computer Watch has "169.254.XXX.XXX' IP address and does not connect to the internet. How can I fix it? I don't know much about the TCP/IP settings. OS is XP Pro SP3. I have a DSL router from single port connected to a simple switch 5 ports, then two CAT5 cables will switch on both computers.
Thanks for your help!
derisk
Hello
Two computers cannot connect to the same connection using the same IP address. Each computer on the network must have its own unique IP address.
You need to get a cable/DSL router. Configure the WAN port (Internet) side with your static IP address and connect all the computers the and other equipment network on the side of the router LAN.
Generally, it looks like this, http://www.ezlan.net/network/router.jpg
P.S. You don't need to use the wireless if you do not, it is very difficult to find a new wireless router.
Jack-MVP Windows Networking. WWW.EZLAN.NET
Maybe you are looking for
-
I hear that Wi Fi help raises charges of phone service to sky rocket. No information on it there?
I hear that Wi Fi help raises charges of phone service to sky rocket. No information on it there?
-
Re: Satellite L500D-164 Driver for XP
I can't find a driver for XP. Are there of web graphics drivers audio, cam, etc. Can someone help me?
-
I have: Scilab 5.4.0 (64-bit) LabVIEW 2012 (64-bit) LabVIEW Scilab Gateway (64-bit) Why shouldn't the scilab script work? I get error 1046. I tried to drop a matlab script and changing server as suggested in post. Thank you...
-
"When I try to connect wirelessly" linsky "my pc tells me that it has detected a problem with linsky @ shuts down the system. Have tried to reset wireless, also disabled the system for several minutes @ and then restarted. Still nothing.
-
CMD Batch script - Echo % variable %.
I have a small problem with a batch file that I'm working on. Here's a simple example: I would get the string 'THERE' as my result. But the result I get is just 'HELLO. ' set hello=there set a=h set b=ello set result=%a%%b% echo %result% I tried some