TCP SYN Sweep excessively shooting host (3030.0)
Hi all
We've recently added a bunch of IP addresses to our internal networks (we initially only had them on the perimeter). As we implemented these IPS (running 5.x), we have seen a massive increase in the number of TCP SYN host sweep.
I looked a little further into the traffic, and it seems that much of this is traffic to port 80 on the external addresses (I'm guessing that its Web sites with ads, etc. that are originally most of these).
However, there are a lot of connections will apparently arbitrary ports to many different beaches of network. The part that worries me the most, is that a lot of the SYN scans addresses to internal AND external.
I could not determine the exact cause of the SYN scans, but it seems that the majority of our customers do.
I'm only a student, so my knowledge (and access to knowledge) are rather limited.
I was wondering if someone at - he had similar experiences? If so, is there a good way to eliminate false positives since potentially important alerts?
Best regards
Ryan
We use Intellitactics NSM as our SEM and it works very well for our environment (because it is relatively soft and we like to tinker).
I don't remember the exact changes we did, but that's what we have:
#sh conf | Start 3030
signatures 3030 0
scanning engine
50 unique
Tcp protocol
storage Axxb key
Specify-port-range Yes
1-24,26-79,81-442,444-2966,2968-65534 port range
The part of this signature working for us, it's that our platform (NSM) will create an alert when we see 100 of these signatures in a given period of time. That lets us know that some scanning time is underway (note that servers HTTP, DNS, FTP & busy will trigger this sig on back so filtering traffic & profiling is important).
Tags: Cisco Security
Similar Questions
-
The TCP/IP connection to the host localhost, port 1433 failed.
Hi, im using sql Server2000,
I said this in my program:
and gives me this exception:Class.forName("com.microsoft.sqlserver.jdbc.SQLServerDriver"); String url = "jdbc:sqlserver://localhost:1433;databaseName=Factura"; Connection conn = DriverManager.getConnection(url,"sa","");
How can I solve this?run: Got an exception! The TCP/IP connection to the host localhost, port 1433 has failed. Error: "connect timed out. Verify the connection properties, check that an instance of SQL Server is running on the host and accepting TCP/IP connections at the port, and that no firewall is blocking TCP connections to the port.". com.microsoft.sqlserver.jdbc.SQLServerException: The TCP/IP connection to the host localhost, port 1433 has failed. Error: "connect timed out. Verify the connection properties, check that an instance of SQL Server is running on the host and accepting TCP/IP connections at the port, and that no firewall is blocking TCP connections to the port.". at com.microsoft.sqlserver.jdbc.SQLServerException.makeFromDriverError(SQLServerException.java:171) at com.microsoft.sqlserver.jdbc.SQLServerConnection.connectHelper(SQLServerConnection.java:1033) at com.microsoft.sqlserver.jdbc.SQLServerConnection.login(SQLServerConnection.java:817) at com.microsoft.sqlserver.jdbc.SQLServerConnection.connect(SQLServerConnection.java:700) at com.microsoft.sqlserver.jdbc.SQLServerDriver.connect(SQLServerDriver.java:842) at java.sql.DriverManager.getConnection(DriverManager.java:582) at java.sql.DriverManager.getConnection(DriverManager.java:185) at factura.FacturaView.conexion(FacturaView.java:317) at factura.FacturaView.jTextField1KeyPressed(FacturaView.java:268) at factura.FacturaView.access$900(FacturaView.java:41) at factura.FacturaView$5.keyPressed(FacturaView.java:150) at java.awt.Component.processKeyEvent(Component.java:6225) at javax.swing.JComponent.processKeyEvent(JComponent.java:2801) at java.awt.Component.processEvent(Component.java:6044) at java.awt.Container.processEvent(Container.java:2041) at java.awt.Component.dispatchEventImpl(Component.java:4630) at java.awt.Container.dispatchEventImpl(Container.java:2099) at java.awt.Component.dispatchEvent(Component.java:4460) at java.awt.KeyboardFocusManager.redispatchEvent(KeyboardFocusManager.java:1850) at java.awt.DefaultKeyboardFocusManager.dispatchKeyEvent(DefaultKeyboardFocusManager.java:712) at java.awt.DefaultKeyboardFocusManager.preDispatchKeyEvent(DefaultKeyboardFocusManager.java:990) at java.awt.DefaultKeyboardFocusManager.typeAheadAssertions(DefaultKeyboardFocusManager.java:855) at java.awt.DefaultKeyboardFocusManager.dispatchEvent(DefaultKeyboardFocusManager.java:676) at java.awt.Component.dispatchEventImpl(Component.java:4502) at java.awt.Container.dispatchEventImpl(Container.java:2099) at java.awt.Window.dispatchEventImpl(Window.java:2478) at java.awt.Component.dispatchEvent(Component.java:4460) at java.awt.EventQueue.dispatchEvent(EventQueue.java:599) at java.awt.EventDispatchThread.pumpOneEventForFilters(EventDispatchThread.java:269) at java.awt.EventDispatchThread.pumpEventsForFilter(EventDispatchThread.java:184) at java.awt.EventDispatchThread.pumpEventsForHierarchy(EventDispatchThread.java:174) at java.awt.EventDispatchThread.pumpEvents(EventDispatchThread.java:169) at java.awt.EventDispatchThread.pumpEvents(EventDispatchThread.java:161) at java.awt.EventDispatchThread.run(EventDispatchThread.java:122) BUILD SUCCESSFUL (total time: 34 seconds)
Thank you...
Edited by: derok December 8, 2010 13:31
Edited by: derok December 8, 2010 21:14
Edited by: derok December 11, 2010 13:51
Edited by: derok December 11, 2010 13:52There's a sqlservr.exe is listening on port 1025:
What is the process (sqlservr.exe) that I need to connect to?Obviously. Have you tried?
-
I was told that the PIX 515E firewall is capable of BLOCKING malicious attacks as attack Dinal of Service. I learned again by CA engineers that it not are a NO product out there that is able to block attacks but rather notify the administrator only. I'd like your opinion on whether the PIX firewall can actually BLOCK attack or not. Thanks in advance.
The PIX has some features to prevent DOS attacks, but he can't block everything. For example, if someone launches an attack smurf or something that uses all of your available bandwidth, then the PIX obviously cannot do anything about it because the damage is already done at the time wherever traffic allows you the PIX.
For something like a TCP SYN attack on a host inside the PIX, then you can configure the static command to allow only a total number of connections through, and/or a number of half-open connections through the internal host, effectively protecting the Server internal. The PIX will refuse further attempts to connect over this limit.
The PIX also has a built-in limited to IDS. It can detect signatures of 59 common packages and can be configured to block these if they are considered. Signatures that he seeks only are based a package signatures, wide as a real IDS device can get nothing.
In short, no one can say yes, "The PIX prevents all attacks back", no box cannot do that, because it depends on what the attack back. If someone is flooding your available circuit bandwidth, you really get your ISP involved to block this traffic BEFORE it happens to you. Yes, host-based DOS attacks, the PIX should be able to block most of them with standard configuration controls.
-
It seems that whenever a mail server connects a mass mailing to clients I see this fire GIS.
I also see the SIG fires when "some" users surf to websites with rejected (DoubleClick, Akamai, etc..)
According to the DB, GIS to MySDN, this GIS is benign, as long as the traffic seen is internal.
Is this the case?
Do you mean the scan TCP SYN host (3030-0)? I never really found to be a useful signature, especially because it doesn't relate ports under analysis. It is prone to false positives as well because it fires on the return circulation (as a HTTP proxy, for example). Filtering can fix this if you are so inclined.
see these threads:
-
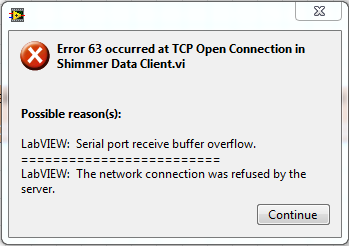
Hello
I can't establish a TCP/IP connection between my host and another PC. I use the 'Simple data Sever' and 'Customer of data Simple' screw delivered with LabVIEW. Error message is less than
The example screw working finw when I use them only on my host.
I can confirm the following:
- Good serial port
- Correct skill game
- The firewall on both computers is OFF
Any fix ideas?
Try a port number more than 50000. You use port numbers in user space. 2055 port is assigned to the Iliad-Odyssey Protocol and commplex-link 5001 is assigned. Don't know what eith erof here is or how they are commonly but you might be runnin celine a conflict. Ports 49152-65535 are reserved for dynamic/private use. You can get more information here about IP ports. It's worth a try. The other thing you could do is to install Wireshark on every PC and see if the package (TCP - SYN) is to learn by the client and the server.
-
HTTPS protocol between the client vpn and host of the internet through tunnel ipsec-parody
Hello
We have a cisco ASA 5505 and try to get the next job:
ip (192.168.75.5) - connected to the Cisco ASA 5505 VPN client
the customer gets a specific route for an internet address (79.143.218.35 255.255.255.255 192.168.75.1 192.168.75.5 100)
When I try to access the url of the client, I get a syn sent with netstat
When I try trace ASA package, I see the following:
1 FLOW-SEARCH ALLOW Not found no corresponding stream, creating a new stream
2 ROUTE SEARCH entry ALLOW in 0.0.0.0 0.0.0.0 outdoors
3 ACCESS-LIST Journal ALLOW Access-group outside_access_in in interface outside
outside_access_in list extended access permitted tcp everything any https eq
access-list outside_access_in note hyperion outside inside
4 IP-OPTIONS ALLOW 5 CP-PUNT ALLOW 6 VPN IPSec-tunnel-flow ALLOW 7 IP-OPTIONS ALLOW 8 VPN encrypt ALLOW outdoors upward upward outdoors upward upward drop (ipsec-parody) Parody of detected IPSEC When I try the reverse (i.e. from the internet host to vpn client), it seems to work:
1 FLOW-SEARCH ALLOW Not found no corresponding stream, creating a new stream
2 ROUTE SEARCH entry ALLOW in 192.168.75.5 255.255.255.255 outside
3 ACCESS-LIST Journal ALLOW Access-group outside_access_in in interface outside
outside_access_in of access allowed any ip an extended list
4 IP-OPTIONS ALLOW 5 VPN IPSec-tunnel-flow ALLOW 6 VPN encrypt ALLOW My question is why this phenomenon happens and how solve us this problem?
Thanks in advance, Sipke
our running-config:
: Saved
:
ASA Version 8.0 (4)
!
ciscoasa hostname
domain somedomain
activate the password - encrypted
passwd - encrypted
names of
name 10.10.1.0 Hyperion
name 164.140.159.x xxxx
name 192.168.72.25 xxxx
name 192.168.72.24 xxxx
name 192.168.72.196 xxxx
name 192.168.75.0 vpn clients
name 213.206.236.0 xxxx
name 143.47.160.0 xxxx
name 141.143.32.0 xxxx
name 141.143.0.0 xxxx
name 192.168.72.27 xxxx
name 10.1.11.0 xxxx
name 10.1.2.240 xxxx
name 10.1.1.0 xxxx
name 10.75.2.1 xxxx
name 10.75.2.23 xxxx
name 192.168.72.150 xxxx
name 192.168.33.0 xxxx
name 192.168.72.26 xxxx
name 192.168.72.5 xxxx
name 192.168.23.0 xxxx
name 192.168.34.0 xxxx
name 79.143.218.35 inethost
!
interface Vlan1
nameif inside
security-level 100
IP 192.168.72.254 255.255.255.0
OSPF cost 10
!
interface Vlan2
nameif outside
security-level 0
IP address 193.173.x.x 255.255.255.240
OSPF cost 10
!
interface Vlan3
Shutdown
nameif dmz
security-level 50
192.168.50.1 IP address 255.255.255.0
OSPF cost 10
!
interface Vlan23
nameif wireless
security-level 80
192.168.40.1 IP address 255.255.255.0
OSPF cost 10
!
interface Ethernet0/0
switchport access vlan 2
!
interface Ethernet0/1
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
switchport access vlan 3
!
interface Ethernet0/6
switchport access vlan 23
!
interface Ethernet0/7
!
passive FTP mode
clock timezone THATS 1
clock to summer time CEDT recurring last Sun Mar 02:00 last Sun Oct 03:00
DNS lookup field inside
DNS server-group DefaultDNS
domain pearle.local
permit same-security-traffic inter-interface
permit same-security-traffic intra-interface
object-group Protocol TCPUDP
object-protocol udp
object-tcp protocol
object-group service RDP - tcp
Remote Desktop Protocol Description
EQ port 3389 object
object-group service UDP - udp VC
range of object-port 60000 60039
object-group VC - TCP tcp service
60000 60009 object-port Beach
object-group service tcp Fortis
1501 1501 object-port Beach
Beach of port-object 1502-1502
Beach of port-object sqlnet sqlnet
1584 1584 object-port Beach
1592 1592 object-port Beach
object-group service tcp fortis
1592 1592 object-port Beach
Beach of port-object 1502-1502
1584 1584 object-port Beach
Beach of port-object sqlnet sqlnet
1501 1501 object-port Beach
1500 1500 object-port Beach
the DM_INLINE_NETWORK_1 object-group network
object-network 192.168.50.0 255.255.255.0
object-network 192.168.72.0 255.255.255.0
object-network 192.168.40.0 255.255.255.0
object-network VPN_Pool_2 255.255.255.0
the DM_INLINE_NETWORK_2 object-group network
object-network 192.168.50.0 255.255.255.0
object-network 192.168.72.0 255.255.255.0
object-group network inside-networks
object-network 192.168.72.0 255.255.255.0
WingFTP_TCP tcp service object-group
Secure FTP description
port-object eq 989
port-object eq 990
DM_INLINE_TCP_1 tcp service object-group
port-object eq ftp
port-object eq ftp - data
Group object WingFTP_TCP
DM_INLINE_TCP_2 tcp service object-group
port-object eq ftp
port-object eq ftp - data
Group object WingFTP_TCP
the DM_INLINE_NETWORK_3 object-group network
object-network 192.168.72.0 255.255.255.0
object-network VPN_Pool_2 255.255.255.0
the DM_INLINE_NETWORK_4 object-group network
object-network 192.168.72.0 255.255.255.0
object-network VPN_Pool_2 255.255.255.0
object-group network Oracle
network-object OracleTwo 255.255.224.0
network-object OracleOne 255.255.240.0
network-object OracleThree 255.255.224.0
the DM_INLINE_NETWORK_5 object-group network
network-object Grandvision 255.255.255.0
network-object Grandvision2 255.255.255.240
object-network Grandvision3 255.255.255.0
host of the object-Network Grandvision4
host of the object-Network GrandVision_PC
the DM_INLINE_NETWORK_6 object-group network
network-object Grandvision 255.255.255.0
network-object Grandvision2 255.255.255.240
object-network Grandvision3 255.255.255.0
host of the object-Network Grandvision4
host of the object-Network GrandVision_PC
the DM_INLINE_NETWORK_7 object-group network
network-object Grandvision 255.255.255.0
network-object Grandvision2 255.255.255.240
object-network Grandvision3 255.255.255.0
host of the object-Network GrandVision_PC
the DM_INLINE_NETWORK_8 object-group network
network-object Grandvision 255.255.255.0
network-object Grandvision2 255.255.255.240
object-network Grandvision3 255.255.255.0
host of the object-Network GrandVision_PC
object-group service DM_INLINE_SERVICE_2
the purpose of the ip service
EQ-3389 tcp service object
the DM_INLINE_NETWORK_9 object-group network
network-object OracleThree 255.255.0.0
network-object OracleTwo 255.255.224.0
network-object OracleOne 255.255.240.0
object-group service DM_INLINE_SERVICE_3
the purpose of the ip service
EQ-3389 tcp service object
Atera tcp service object-group
Atera Webbased monitoring description
8001 8001 object-port Beach
8002 8002 object-port Beach
8003 8003 object-port Beach
WingFTP_UDP udp service object-group
port-object eq 989
port-object eq 990
WingFTP tcp service object-group
Description range of ports for the transmission of data
object-port range 1024-1054
HTTPS_redirected tcp service object-group
Description redirect WingFTP Server
port-object eq 40200
Note to inside_access_in to access list ICMP test protocol inside outside
inside_access_in list extended access allow icmp 192.168.72.0 255.255.255.0 any
Note to inside_access_in to access list ICMP test protocol inside outside
access-list inside_access_in note HTTP inside outside
inside_access_in list extended access allowed object-group TCPUDP 192.168.72.0 255.255.255.0 any eq www
access-list inside_access_in note queries DNS inside to outside
inside_access_in list extended access allowed object-group TCPUDP 192.168.72.0 255.255.255.0 no matter what eq field
access-list inside_access_in note the HTTPS protocol inside and outside
inside_access_in list extended access permitted tcp 192.168.72.0 255.255.255.0 any https eq
Note to inside_access_in to access list ICMP test protocol inside outside
access-list inside_access_in note 7472 Epo-items inside outside
inside_access_in list extended access permitted tcp 192.168.72.0 255.255.255.0 any eq 7472
access-list inside_access_in note POP3 inside outside
inside_access_in list extended access permitted tcp 192.168.72.0 255.255.255.0 any eq pop3
inside_access_in list extended access permit udp host LifeSize-PE-HQ any object-group UDP - VC
inside_access_in list extended access permit tcp host LifeSize-PE-HQ all eq h323
access-list inside_access_in note video conference services
inside_access_in list extended access permit tcp host LifeSize-PE-HQ any object-group VC - TCP
inside_access_in list extended access permitted tcp 192.168.72.0 255.255.255.0 any
Note to inside_access_in to access list Fortis
inside_access_in list extended access permitted tcp 192.168.72.0 255.255.255.0 any object-group Fortis
access extensive list ip 192.168.40.0 inside_access_in allow 255.255.255.0 any
inside_access_in list extended access permitted tcp 192.168.40.0 255.255.255.0 any
inside_access_in list extended access permitted tcp 192.168.40.0 255.255.255.0 any eq www
inside_access_in list extended access permitted tcp 192.168.40.0 255.255.255.0 any https eq
inside_access_in allowed all Hyperion 255.255.255.0 ip extended access list
inside_access_in list extended access udp allowed any any eq isakmp
inside_access_in list extended access udp allowed any any eq ntp
inside_access_in list extended access udp allowed any any eq 4500
inside_access_in list of allowed ip extended access any Oracle object-group
inside_access_in list extended access udp allowed any any eq 10000
access-list inside_access_in note PPTP inside outside
inside_access_in list extended access permit tcp any any eq pptp
access-list inside_access_in note WILL inside outside
inside_access_in list extended access will permit a full
Note to inside_access_in to access the Infrastructure of the RIM BES server list
inside_access_in list extended access permit tcp host BESServer any eq 3101
inside_access_in list extended access permit tcp any any DM_INLINE_TCP_2 object-group
inside_access_in list extended access permit tcp any any HTTPS_redirected object-group
access extensive list ip Hyperion 255.255.255.0 inside_access_in 255.255.255.0 allow VPN_Pool_2
inside_access_in list extended access permit udp any host 86.109.255.177 eq 1194
access extensive list ip 192.168.72.0 inside_access_in allow 255.255.255.0 DM_INLINE_NETWORK_7 object-group
access extensive list ip VPN_Pool_2 inside_access_in allow 255.255.255.0 any
inside_access_in list extended access deny ip any any inactive debug log
Note to outside_access_in to access list ICMP test protocol outside inside
outside_access_in list extended access permit icmp any one
access-list outside_access_in Note SMTP outside inside
outside_access_in list extended access permit tcp any any eq smtp
outside_access_in list extended access udp allowed any any eq ntp disable journal
access-list outside_access_in note 7472 EPO-items outside inside
outside_access_in list extended access permit tcp any any eq 7472
outside_access_in list extended access permit tcp any any object-group inactive RDP
outside_access_in list extended access permit tcp any any eq www
outside_access_in list extended access permit tcp any any HTTPS_redirected object-group
outside_access_in list extended access permitted tcp everything any https eq
access-list outside_access_in note hyperion outside inside
outside_access_in list extended access permitted tcp Hyperion 255.255.255.0 DM_INLINE_NETWORK_4 object-group
outside_access_in to access Hyperion 255.255.255.0 ip extended list object-group DM_INLINE_NETWORK_3 allow
outside_access_in list extended access permit tcp any host LifeSize-PE-HQ eq h323
outside_access_in list extended access permit tcp any host LifeSize-PE-HQ object-group VC - TCP
outside_access_in list extended access permit udp any host group-object-LifeSize-PE-HQ UDP - VC
outside_access_in of access allowed any ip an extended list
outside_access_in list extended access udp allowed any any eq 4500
outside_access_in list extended access udp allowed any any eq isakmp
outside_access_in list extended access udp allowed any any eq 10000
outside_access_in list extended access will permit a full
outside_access_in list extended access permit tcp any any eq pptp
outside_access_in list extended access permit tcp any any DM_INLINE_TCP_1 object-group
outside_access_in list extended access allowed object-group ip DM_INLINE_NETWORK_8 192.168.72.0 255.255.255.0 inactive
outside_access_in list extended access permit tcp any any Atera object-group
outside_access_in list extended access deny ip any any inactive debug log
outside_1_cryptomap list extended access allowed object-group Hyperion DM_INLINE_NETWORK_2 255.255.255.0 ip
outside_1_cryptomap to access extended list ip 192.168.50.0 allow Hyperion 255.255.255.0 255.255.255.0
access extensive list ip 192.168.72.0 inside_nat0_outbound allow Hyperion 255.255.255.0 255.255.255.0
inside_nat0_outbound list of allowed ip extended access all 193.172.182.64 255.255.255.240
inside_nat0_outbound list of allowed ip extended access all 192.168.72.192 255.255.255.192
inside_nat0_outbound list of allowed ip extended access all 192.168.72.0 255.255.255.0
access extensive list ip 192.168.72.0 inside_nat0_outbound allow 255.255.255.0 VPN_Pool_2 255.255.255.0
access extensive list ip 192.168.72.0 inside_nat0_outbound allow 255.255.255.0 DM_INLINE_NETWORK_5 object-group
inside_nat0_outbound list of allowed ip extended access all GrandVisionSoesterberg 255.255.255.0
inside_nat0_outbound list of allowed ip extended access any Swabach 255.255.255.0
access-list 200 scope allow tcp all fortis of fortis host object-group
access extensive list ip VPN_Pool_2 outside_nat0_outbound allow 255.255.255.0 DM_INLINE_NETWORK_9 object-group
outside_cryptomap_2 list extended access allowed object-group Hyperion DM_INLINE_NETWORK_1 255.255.255.0 ip
outside_cryptomap_2 to access extended list ip 192.168.50.0 allow Hyperion 255.255.255.0 255.255.255.0
Note Wireless_access_in of access list, select Hyperion / wifi access NAT rule.
Access extensive list ip 192.168.40.0 Wireless_access_in allow Hyperion inactive 255.255.255.0 255.255.255.0
Wireless_access_in list extended access deny ip 192.168.40.0 255.255.255.0 192.168.72.0 255.255.255.0
Comment by Wireless_access_in-list of the traffic Internet access
Access extensive list ip 192.168.40.0 Wireless_access_in allow 255.255.255.0 any
standard access list splittunnelclientvpn allow 192.168.72.0 255.255.255.0
splittunnelclientvpn list standard access allowed Hyperion 255.255.255.0
standard access list splittunnelclientvpn allow Pearleshare 255.255.255.0
splittunnelclientvpn list standard access allowed host 85.17.235.22
splittunnelclientvpn list standard access allowed OracleThree 255.255.224.0
standard access list splittunnelclientvpn allow 143.47.128.0 255.255.240.0
splittunnelclientvpn list standard access allowed host inethost
Standard access list SplittnlHyperion allow OracleThree 255.255.0.0
Standard access list SplittnlOOD allow OracleThree 255.255.0.0
Standard access list SplittnlOOD allow 143.47.128.0 255.255.240.0
access extensive list ip 192.168.72.0 outside_cryptomap allow 255.255.255.0 DM_INLINE_NETWORK_6 object-group
outside_cryptomap_1 list of allowed ip extended access all GrandVisionSoesterberg 255.255.255.0
outside_cryptomap_3 list of allowed ip extended access any Swabach 255.255.255.0
192.168.72.0 IP Access-list extended sheep 255.255.255.0 GrandVisionSoesterberg 255.255.255.0 allow
192.168.72.0 IP Access-list extended sheep 255.255.255.0 VPN_Pool_2 255.255.255.0 allow
pager lines 24
Enable logging
asdm of logging of information
Within 1500 MTU
Outside 1500 MTU
MTU 1500 dmz
MTU 1500 wireless
local pool VPN_DHCP 192.168.72.220 - 192.168.72.235 255.255.255.0 IP mask
mask 192.168.75.1 - 192.168.75.50 255.255.255.0 IP local pool VPN_Range_2
no failover
ICMP unreachable rate-limit 1 burst-size 1
ICMP allow any inside
ICMP allow all outside
ASDM image disk0: / asdm - 613.bin
don't allow no asdm history
ARP timeout 14400
Global 1 interface (outside)
NAT (inside) 0 access-list sheep
NAT (inside) 1 0.0.0.0 0.0.0.0
NAT (wireless) 1 192.168.40.0 255.255.255.0
public static tcp (indoor, outdoor) interface smtp smtp Mailsrv_Pearle_Europe netmask 255.255.255.255
public static tcp (indoor, outdoor) interface ftp ftp netmask 255.255.255.255 Pearle-DC02
public static 990 Pearle-DC02 990 netmask 255.255.255.255 interface tcp (indoor, outdoor)
static (inside, outside) tcp 3389 3389 Mailsrv_Pearle_Europe netmask 255.255.255.255 interface
public static tcp (indoor, outdoor) interface www Pearle-DC02 www netmask 255.255.255.255
public static 40200 Pearle-DC02 40200 netmask 255.255.255.255 interface tcp (indoor, outdoor)
public static tcp (indoor, outdoor) interface https Exchange2010 https netmask 255.255.255.255
public static tcp (indoor, outdoor) interface h323 h323 LifeSize-PE-HQ netmask 255.255.255.255
public static 60000 60000 LifeSize-PE-HQ netmask 255.255.255.255 interface tcp (indoor, outdoor)
public static 60001 LifeSize-PE-HQ 60001 netmask 255.255.255.255 interface tcp (indoor, outdoor)
public static 60002 LifeSize-PE-HQ 60002 netmask 255.255.255.255 interface tcp (indoor, outdoor)
public static 60003 LifeSize-PE-HQ 60003 netmask 255.255.255.255 interface tcp (indoor, outdoor)
public static 60004 LifeSize-PE-HQ 60004 netmask 255.255.255.255 interface tcp (indoor, outdoor)
public static 60005 LifeSize-PE-HQ 60005 netmask 255.255.255.255 interface tcp (indoor, outdoor)
public static 60006 LifeSize-PE-HQ 60006 netmask 255.255.255.255 interface tcp (indoor, outdoor)
public static 60007 LifeSize-PE-HQ 60007 netmask 255.255.255.255 interface tcp (indoor, outdoor)
public static 60008 LifeSize-PE-HQ 60008 netmask 255.255.255.255 interface tcp (indoor, outdoor)
public static 60009 LifeSize-PE-HQ 60009 netmask 255.255.255.255 interface tcp (indoor, outdoor)
public static (inside, outside) udp interface 60001 LifeSize-PE-HQ 60001 netmask 255.255.255.255
public static (inside, outside) udp interface 60002 LifeSize-PE-HQ 60002 netmask 255.255.255.255
public static (inside, outside) udp interface 60003 LifeSize-PE-HQ 60003 netmask 255.255.255.255
public static (inside, outside) udp interface 60004 LifeSize-PE-HQ 60004 netmask 255.255.255.255
public static (inside, outside) udp interface 60005 LifeSize-PE-HQ 60005 netmask 255.255.255.255
public static (inside, outside) udp interface 60006 LifeSize-PE-HQ 60006 netmask 255.255.255.255
public static (inside, outside) udp interface 60007 LifeSize-PE-HQ 60007 netmask 255.255.255.255
public static (inside, outside) udp interface 60008 LifeSize-PE-HQ 60008 netmask 255.255.255.255
public static (inside, outside) udp interface 60009 LifeSize-PE-HQ 60009 netmask 255.255.255.255
public static (inside, outside) udp interface 60010 LifeSize-PE-HQ 60010 netmask 255.255.255.255
public static (inside, outside) udp interface 60011 LifeSize-PE-HQ 60011 netmask 255.255.255.255
public static (inside, outside) udp interface 60012 LifeSize-PE-HQ 60012 netmask 255.255.255.255
public static (inside, outside) udp interface 60013 LifeSize-PE-HQ 60013 netmask 255.255.255.255
public static (inside, outside) udp interface 60014 LifeSize-PE-HQ 60014 netmask 255.255.255.255
public static (inside, outside) udp interface 60015 LifeSize-PE-HQ 60015 netmask 255.255.255.255
public static (inside, outside) udp interface 60016 LifeSize-PE-HQ 60016 netmask 255.255.255.255
public static (inside, outside) udp interface 60017 LifeSize-PE-HQ 60017 netmask 255.255.255.255
public static (inside, outside) udp interface 60018 LifeSize-PE-HQ 60018 netmask 255.255.255.255
public static (inside, outside) udp interface 60019 LifeSize-PE-HQ 60019 netmask 255.255.255.255
public static (inside, outside) udp interface 60020 LifeSize-PE-HQ 60020 netmask 255.255.255.255
public static (inside, outside) udp interface 60021 60021 LifeSize-PE-HQ netmask 255.255.255.255
public static (inside, outside) udp interface 60022 LifeSize-PE-HQ 60022 netmask 255.255.255.255
public static (inside, outside) udp interface 60023 LifeSize-PE-HQ 60023 netmask 255.255.255.255
public static (inside, outside) udp interface 60024 LifeSize-PE-HQ 60024 netmask 255.255.255.255
public static (inside, outside) udp interface 60025 LifeSize-PE-HQ 60025 netmask 255.255.255.255
public static (inside, outside) udp interface 60026 LifeSize-PE-HQ 60026 netmask 255.255.255.255
public static (inside, outside) udp interface 60027 LifeSize-PE-HQ 60027 netmask 255.255.255.255
public static (inside, outside) udp interface 60028 LifeSize-PE-HQ 60028 netmask 255.255.255.255
public static (inside, outside) udp interface 60029 LifeSize-PE-HQ 60029 netmask 255.255.255.255
public static (inside, outside) udp interface 60030 LifeSize-PE-HQ 60030 netmask 255.255.255.255
public static (inside, outside) udp interface 60031 LifeSize-PE-HQ 60031 netmask 255.255.255.255
public static (inside, outside) udp interface 60032 LifeSize-PE-HQ 60032 netmask 255.255.255.255
public static (inside, outside) udp interface 60033 LifeSize-PE-HQ 60033 netmask 255.255.255.255
public static (inside, outside) udp interface 60034 LifeSize-PE-HQ 60034 netmask 255.255.255.255
public static (inside, outside) udp interface 60035 LifeSize-PE-HQ 60035 netmask 255.255.255.255
public static (inside, outside) udp interface 60036 LifeSize-PE-HQ 60036 netmask 255.255.255.255
public static (inside, outside) udp interface 60037 LifeSize-PE-HQ 60037 netmask 255.255.255.255
public static (inside, outside) udp interface 60038 LifeSize-PE-HQ 60038 netmask 255.255.255.255
public static (inside, outside) udp interface 60039 LifeSize-PE-HQ 60039 netmask 255.255.255.255
public static (inside, outside) udp interface 60040 60040 LifeSize-PE-HQ netmask 255.255.255.255
public static Mailsrv_Pearle_Europe 7472 netmask 255.255.255.255 7472 interface tcp (indoor, outdoor)
public static LanSweep-XP netmask 255.255.255.255 8001 8001 interface tcp (indoor, outdoor)
public static 8002 8002 LanSweep-XP netmask 255.255.255.255 interface tcp (indoor, outdoor)
public static LanSweep-XP netmask 255.255.255.255 8003 8003 interface tcp (indoor, outdoor)
static (inside, outside) 193.173.12.194 tcp https Pearle-DC02 https netmask 255.255.255.255
inside_access_in access to the interface inside group
Access-group outside_access_in in interface outside
Access-group Wireless_access_in in wireless interface
Route outside 0.0.0.0 0.0.0.0 193.173.12.206 1
Route outside OracleThree 255.255.224.0 193.173.12.198 1
Route outside 143.47.128.0 255.255.240.0 193.173.12.198 1
Route inside 172.27.0.0 255.255.255.0 Pearle-DC02 1
Timeout xlate 03:00
Timeout conn 01:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
Sunrpc timeout 0:10:00 h323 0:05:00 h225 mgcp from 01:00 0:05:00 mgcp-pat 0:05:00
Sip timeout 0:30:00 sip_media 0:02:00 prompt Protocol sip-0: 03:00 sip - disconnect 0:02:00
Timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
dynamic-access-policy-registration DfltAccessPolicy
AAA authentication LOCAL telnet console
the ssh LOCAL console AAA authentication
Enable http server
http 192.168.40.0 255.255.255.0 Wireless
http 192.168.1.0 255.255.255.0 inside
http 192.168.72.0 255.255.255.0 inside
http GrandVisionSoesterberg 255.255.255.0 inside
SNMP-server host inside 192.168.33.29 survey community public version 2 c
location of Server SNMP Schiphol
contact Server SNMP SSmeekes
SNMP-Server Public community
Server enable SNMP traps snmp authentication linkup, linkdown cold start
Crypto ipsec transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
Crypto ipsec transform-set ESP-DES-SHA esp - esp-sha-hmac
Crypto ipsec transform-set ESP-DES-MD5 esp - esp-md5-hmac
Crypto ipsec transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
Crypto ipsec transform-set ESP-3DES-MD5-esp-3des esp-md5-hmac
Crypto ipsec transform-set ESP-AES-256-SHA 256 - aes - esp esp-sha-hmac
Crypto ipsec transform-set ESP-AES-128-SHA aes - esp esp-sha-hmac
Crypto ipsec transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
Crypto ipsec transform-set ESP-AES-128-MD5-esp - aes esp-md5-hmac
Crypto ipsec transform-set esp-SHA-ESP-3DES-3des esp-sha-hmac
Crypto ipsec transform-set esp-aes-256 GRANDVISION esp-md5-hmac
life crypto ipsec security association seconds 28800
Crypto ipsec kilobytes of life - safety 4608000 association
Dynamic crypto map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set pfs
Crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 value transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA MD5-ESP-3DES ESP-DES-SHA ESP-DES-MD5
Dynamic crypto map SYSTEM_DEFAULT_CRYPTO_MAP 65535 define security association lifetime 28800 seconds
cryptographic kilobytes 4608000 life of the set - the association of security of the 65535 SYSTEM_DEFAULT_CRYPTO_MAP of the dynamic-map
card crypto outside_map0 1 match address outside_cryptomap_1
outside_map0 card crypto 1jeu pfs
outside_map0 card crypto 1jeu peer 212.78.223.182
outside_map0 card crypto 1jeu transform-set ESP ESP-3DES-SHA-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-ESP ESP-3DES-MD5 MD5-DES-SHA ESP-DES-MD5
outside_map0 map 1 lifetime of security association set seconds 28800 crypto
card crypto outside_map0 1 set security-association life kilobytes 4608000
card crypto game 2 outside_map0 address outside_cryptomap_2
outside_map0 crypto map peer set 2 193.173.12.193
card crypto outside_map0 2 game of transformation-ESP ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5-DES-SHA ESP-DES-MD5
life card crypto outside_map0 2 set security-association seconds 28800
card crypto outside_map0 2 set security-association life kilobytes 4608000
card crypto outside_map0 3 match address outside_1_cryptomap
outside_map0 card crypto 3 set pfs
outside_map0 card crypto 3 peers set 193.172.182.66
outside_map0 crypto map 3 the value transform-set ESP-3DES-SHA
life card crypto outside_map0 3 set security-association seconds 28800
card crypto outside_map0 3 set security-association life kilobytes 4608000
card crypto outside_map0 game 4 address outside_cryptomap
outside_map0 card crypto 4 peers set 213.56.81.58
outside_map0 4 set transform-set GRANDVISION crypto card
life card crypto outside_map0 4 set security-association seconds 28800
card crypto outside_map0 4 set security-association life kilobytes 4608000
card crypto outside_map0 5 match address outside_cryptomap_3
outside_map0 card crypto 5 set pfs
outside_map0 crypto card 5 peers set 86.109.255.177
outside_map0 card crypto 5 game of transformation-ESP ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5-DES-SHA ESP-DES-MD5
life card crypto outside_map0 5 set security-association seconds 28800
card crypto outside_map0 5 set security-association life kilobytes 4608000
Crypto map outside_map0 65535 ipsec-isakmp dynamic SYSTEM_DEFAULT_CRYPTO_MAP
outside_map0 interface card crypto outside
crypto ISAKMP allow inside
crypto ISAKMP allow outside
crypto ISAKMP enable dmz
crypto ISAKMP enable wireless
crypto ISAKMP policy 5
preshared authentication
3des encryption
sha hash
Group 2
life 86400
Telnet 192.168.72.0 255.255.255.0 inside
Telnet timeout 5
SSH 192.168.72.0 255.255.255.0 inside
SSH GrandVisionSoesterberg 255.255.255.0 inside
SSH 213.144.239.0 255.255.255.192 outside
SSH timeout 5
Console timeout 0
management-access inside
dhcpd dns 194.151.228.18 is 10.10.1.100
dhcpd outside auto_config
!
dhcpd address 192.168.72.253 - 192.168.72.253 inside
!
dhcpd address dmz 192.168.50.10 - 192.168.50.50
dhcpd enable dmz
!
dhcpd address wireless 192.168.40.10 - 192.168.40.99
dhcpd dns 194.151.228.18 wireless interface
dhcpd activate wireless
!
a basic threat threat detection
host of statistical threat detection
statistical threat detection port
Statistical threat detection Protocol
Statistics-list of access threat detection
no statistical threat detection tcp-interception
Group Policy "pearle_vpn_Hyp only" internal
attributes of Group Policy "pearle_vpn_Hyp only".
value of server WINS 192.168.72.25
value of server DNS 192.168.72.25
Protocol-tunnel-VPN IPSec l2tp ipsec
Split-tunnel-policy tunnelspecified
value of Split-tunnel-network-list SplittnlHyperion
Split-dns value pearle.local
internal pearle_vpn_OOD_only group policy
attributes of the strategy of group pearle_vpn_OOD_only
value of Split-tunnel-network-list SplittnlOOD
internal pearle_vpn group policy
attributes of the strategy of group pearle_vpn
value of server WINS 192.168.72.25
value of server DNS 192.168.72.25
Protocol-tunnel-VPN IPSec l2tp ipsec svc
Split-tunnel-policy tunnelspecified
value of Split-tunnel-network-list splittunnelclientvpn
Pearle.local value by default-field
Split-dns value pearle.local
username anyone password encrypted password
username something conferred
VPN-group-policy pearle_vpn_OOD_only
type of remote access service
tunnel-group 193 type ipsec-l2l
tunnel-group 193 ipsec-attributes
pre-shared-key *.
tunnel-group 193.173.12.193 type ipsec-l2l
IPSec-attributes tunnel-group 193.173.12.193
pre-shared-key *.
NOCHECK Peer-id-validate
type tunnel-group pearle_vpn remote access
tunnel-group pearle_vpn General-attributes
address pool VPN_Range_2
Group Policy - by default-pearle_vpn
pearle_vpn group of tunnel ipsec-attributes
pre-shared-key *.
type tunnel-group Pearle_VPN_2 remote access
attributes global-tunnel-group Pearle_VPN_2
address pool VPN_Range_2
strategy-group-by default "pearle_vpn_Hyp only".
IPSec-attributes tunnel-group Pearle_VPN_2
pre-shared-key *.
tunnel-group 213.56.81.58 type ipsec-l2l
IPSec-attributes tunnel-group 213.56.81.58
pre-shared-key *.
tunnel-group 212.78.223.182 type ipsec-l2l
IPSec-attributes tunnel-group 212.78.223.182
pre-shared-key *.
tunnel-group 86.109.255.177 type ipsec-l2l
IPSec-attributes tunnel-group 86.109.255.177
pre-shared-key *.
!
class-map inspection_default
match default-inspection-traffic
!
!
type of policy-card inspect dns preset_dns_map
parameters
message-length maximum 512
Policy-map global_policy
class inspection_default
inspect the preset_dns_map dns
inspect the ftp
inspect h323 h225
inspect the h323 ras
inspect the rsh
inspect the rtsp
inspect the skinny
inspect sunrpc
inspect xdmcp
inspect the sip
inspect the netbios
inspect the tftp
inspect the pptp
!
global service-policy global_policy
context of prompt hostname
Cryptochecksum:7d4d9c7ca7c865d9e40f5d77ed1238eb
: end
ASDM image disk0: / asdm - 613.bin
ASDM BESServer 255.255.255.255 inside location
ASDM VPN_Pool_2 255.255.255.0 inside location
ASDM OracleTwo 255.255.224.0 inside location
ASDM OracleOne 255.255.240.0 inside location
ASDM OracleThree 255.255.224.0 inside location
ASDM location Exchange2010 255.255.255.255 inside
ASDM location Grandvision 255.255.255.0 inside
ASDM Grandvision2 255.255.255.240 inside location
ASDM Grandvision3 255.255.255.0 inside location
ASDM Grandvision4 255.255.255.255 inside location
ASDM GrandVision_PC 255.255.255.255 inside location
ASDM location LanSweep-XP 255.255.255.255 inside
ASDM GrandVisionSoesterberg 255.255.255.0 inside location
ASDM location Pearle-DC02 255.255.255.255 inside
ASDM location Pearle-WDS 255.255.255.255 inside
ASDM location Swabach 255.255.255.0 inside
ASDM GrandVisionSoesterberg2 255.255.255.0 inside location
don't allow no asdm history
Where is that host (inethost)? Inside of the ASA, or on the internet (on the outside)?
If it is outside, you must configure the NAT for the pool of vpn as you turn on the SAA.
NAT (outside) 1 192.168.75.0 255.255.255.0
-
Someone has a lot of experience with the 'TCP Hijack' signature on the IDS sensors? I checked the NSDB and docs IDS for the engine in question, but neither go into details on how to determine if alerts are false or true positives.
Any comments would be much appreciated.
Thank you very much
Matt
Under the version of Cisco IDS 3.x, Hamid 3250 only looked at a few ports (TCP 21, 23, 513 and 514, if I remember correctly).
With the introduction of version 4.x, the signature was no longer limited to these ports. Thus, at least here, we were see a large number of "false positives" involving the web proxy traffic and NetBIOS traffic. BTW, I have no idea if the signature has been coupled to the ports under version 5.x (someone?).
The logic that we apply to all alarm hamid 3250 we see here is based on two factors: intent and feasibility.
Although it is theoretically possible to divert most oriented session TCP connections between a client and a server, there are some that simply make no sense.
If you take alarms involving TCP port 80, what would be the point to divert someone connecting to a web server? Anything sensitive that someone could do this using a browser is done via HTTPS (SSL/TLS aka), so Cryptography will eliminate the threat of hijacking it. So now you re left with web access unsecure. what you are more likely to find if divert you this? Someone looking at the comic strip Dilbert, or something as I imagine... I think you will agree that, therefore, there is no intention at all.
As with any attack of diversion, the feasibility is quite low. Most of these attacks requires that the hijacker be in the same domain as the intended victim. That being said, it goes without saying that you aren t also see cache poisoning attacks ARP or TCP Syn flooding (or another DoS attack against the victim), you aren t see a valid hijack alarm. Of course, the problem here is that these activities usually occur in an area that is not supervised by a NIDS, then you will need other corroborating data to see (HIDS/NNIDS, router logs).
In all cases, these alarms are not very useful on their own. When they become valuable, in my opinion, is when they appear in concert with other alarms (e.g. Hamid 7105 - imbalance of ARP requests).
I hope this helps.
Alex Arndt
-
I have a question about the TCP/IP communication. Let's say I have a device cisco running with off http server. If I send a TCP syn packet to the device with the port of destination 80/443(any non-listening port), the device responds by TCP RESET? Or it will simply fall package without any acknowledgement?
I think it will be different from a device to:
ASA will drop connection refused the services is not running, to do send reset use the command "resetoutside service" send reset to a TCP packet refused to the external interface.
Default access points will reset
Default routers will reset
Default switches will reset
Kind regards
PS please rate and mark as right
-
ACE - probe on VIP sfarm TCP port failed
Hello
I noticed that AS addresses for TCP SYN sent by external device (in my example: GSS device) to the virtual IP address of a serverfarm is perfected OUTOFSERVICE - due to the failure rservers (ARP failed).
A context is configured on the ACE module that is in bridge mode. VIP serverfarm is listening on a TCP port.
Do you know why the AS sends TCP SYN ACK, even if all the rservers in the serverfarm are declining?
How address this situation and to define the ACE to respond on these request only if VIP is ACTIVE because of the State CONTINUES to sfarm?
Krzysztof salvation,
What version of ACE are you running?
When ACE meets the keepalive GSS what is the status of VIP (in-service or out-of-service) in show-service policy
It could be a bug like the one below:
CSCtz42618 VIP on port 443 accepts the connection when all real servers are down
Kind regards
Kanwal
-
Host Update Utility always useful to patch 4.1?
So, apparently, that the host update utility provided with vSphere 4.0 client does not support upgrading a version 4.0.x of ESXi 4.1 and you must do so by vCLI for those of us who do not have vCenter. Fine.
While it is a regular update patches? Currently, the host update utility seems to grind through a sweep of the host of a host 4.1 for a long time then says it is up to date, but it is not clear if this is because there is no update 4.1 out again, or he is simply lying because he made the version 4.0 updates checks only. If she is not really checked 4.1 updates, how users free regular ESXi without vCenter supposed to update and maintain their hosts? Is VMware we expected trolling through the downloads pages periodically to check if there is a new version of build manually update or expect that you subscribe to the explosion of e-mail complete VMware just so that we can update notifications?
I posted a query similar to a return of the week, and although I've seen some answers, they only suggested that "no" was the answer.
It is very frustrating - Update Manager is a pain in the butt and "cancel the job, restart your server, put in maintenance mode manually and try again", advice that I usually get, somewhat defeats all ideals "automatically patch your environment" Update Manager pushes.
You can never vihostupdater.pl command-line if you were aware. Its a real pain.
-
Hello
I'm developing a C++ Client for consistency and using the TCP protocol * Extend to connect to the Cache.
I am able to run multiple nodes on the same machine.
My goal is to add more machines to this configuration (is another machine called cluster or node?).
I would like to have a configuration as explained below:
NamedCache: AQRCache
Cache Type: Close cover (Local and distributed/remote)
HOST_A:
TCP * extend A
Node 1
Node 2
C++customera performer on Host_A talk to TCP * Extend_A.
HOST_B:
TCP * extend_B
Node 3
Node 4
C++clientrunning on Host_B B talk to TCP * Extend_B.
Host_C:
TCP * extend_C
Node 5
Node 6
C++clientC running on Host_C talk to TCP * Extend_C.
Other Clients in C++:
C++clientrunning on Host_D talk to TCP * Extend_A.
C++clientE running on Host_E talk to TCP * Extend_A.
C++clientF running on Host_F talk to TCP * Extend_A.
Issues related to the:
1. to add more machines, if I am running an instance on another machine with the same configuration file, it will work?
2. is it possible to run separate TCP * Proxy extend on each host and it will be part of the same cluster?
3 or should all customers C++ must talk to only TCP * extend Proxy?
Thank you
NS1. to add more machines, if I am running an instance on another machine with the same configuration file, it will work?
Yes, you can add other machines/nodes using the same configuration file.
2. is it possible to run separate TCP * Proxy extend on each host and it will be part of the same cluster?
Yes, you can run several proxy nodes in a single cluster. Just about every production cluster has several proxy nodes.
3 or should all customers C++ must talk to only TCP * extend Proxy?
No, there is no reason to force all C++ clients to connect to a single proxy. In fact you might consider to configure each client with the complete list of proxy servers. Each customer is going to randomly select a server to connect, ensuring that a single proxy is not overloaded.
Also take a look at this document: http://coherence.oracle.com/display/COH35UG/Best+Practices+for+Coherence+Extend
Thank you
Patrick -
What are the causes an IP internal to "attack" multiple public IP addresses?
We had to many TCP SYN host sweep. Could someone share what could cause the above? Follow copies of the alert details.
evIdsAlert: eventId = 1216742775473866070 = severity = informational Cisco vendor
Author:
hostId: ips
appName: sensorApp
appInstanceId: 403
time: August 8, 2008 19:18:53 UTC offset = 480 timeZone = GMT-08:00
signature: description = TCP SYN host Sweep id = 3030 = S2 version
subsigId: 0
marsCategory: probe/SpecificPorts
interfaceGroup: vs0
VLAN: 0
participants:
striker:
addr: 172.16.5.111 locality = OUT
Port: 3958
target:
addr: 69.63.178.11 locality = OUT
OS: idSource = unknown type = unknown = relevant
target:
addr: 64.62.193.70 locality = OUT
OS: idSource = unknown type = unknown = relevant
target:
addr: 77.67.127.41 locality = OUT
OS: idSource = unknown type = unknown = relevant
target:
addr: 64.215.162.27 locality = OUT
OS: idSource = unknown type = unknown = relevant
target:
addr: 65.55.15.242 locality = OUT
OS: idSource = unknown type = unknown = relevant
target:
addr: 77.67.127.10 locality = OUT
OS: idSource = unknown type = unknown = relevant
target:
addr: 69.63.176.167 locality = OUT
OS: idSource = unknown type = unknown = relevant
target:
addr: 65.242.27.32 locality = OUT
OS: idSource = unknown type = unknown = relevant
target:
addr: 64.209.118.140 locality = OUT
OS: idSource = unknown type = unknown = relevant
target:
addr: 77.67.127.25 locality = OUT
OS: idSource = unknown type = unknown = relevant
target:
addr: 207.200.64.225 locality = OUT
OS: idSource = unknown type = unknown = relevant
target:
addr: 207.68.179.219 locality = OUT
OS: idSource = unknown type = unknown = relevant
target:
addr: 65.55.13.158 locality = OUT
OS: idSource = unknown type = unknown = relevant
target:
addr: 63.217.8.128 locality = OUT
OS: idSource = unknown type = unknown = relevant
target:
addr: 66.151.244.212 locality = OUT
OS: idSource = unknown type = unknown = relevant
target:
addr: 207.200.64.161 locality = OUT
OS: idSource = unknown type = unknown = relevant
alertDetails: InterfaceAttributes: = 'Unknown' physical context = 'Unknown' bottom of basket = "GigabitEthernet0/1 ';
riskRatingValue: 31 targetValueRating = average attackRelevanceRating = relevant
threatRatingValue: 31
Interface: GigabitEthernet0/1 context unknown physical = unknown = backplane = GigabitEthernet0/1
Protocol: tcp
Scans when detected on the network local are "mostly" false positives, that's the official word from Cisco:
"Benign triggers.
Scan host 3030 and 3032 signatures detect behaviors that cannot be observed from sources outside the local network, but are normal behaviors for sources within the local network. »
You can filter these signatures of the LAN hosts using event Action filters or tune the signature (using the source / dest. fields inside).
Concerning
Farrukh
-
Cisco IOS 12.3.5a vs IOS 12.3.3c
I have an ongoing execution of 2621 IP address, firewall, IDS, and NAT I opened the appropriate ports to allow a PCAnywhere client via the host inside the firewall. It works fine on IOS 12.3.3c and below. The connection starts, but does not end when executing 12.3.5a. Is it a problem with Cisco plan police control which became available in the version of IOS 12.3.4T or more, or is there a bug in the 12.3.5 undocumented code?
There is a bug documented in 12.3 (5) with FW IOS does not allow connections initiated from outside to start to internal hosts. Basically the Firewall ignores the package of TCP SYN - ACK, returning from the inside, the host for the 3-way connection never ends. Initiated by inside outbound connections are not affected.
Bug ID is CSCec78231, you can read about it here:
http://www.Cisco.com/cgi-bin/support/Bugtool/onebug.pl?BugID=CSCec78231&submit=search
Stick with 12.3 (3) at the moment, already should be resolved in 12.3 (6) when it comes out.
-
After upgrade no more VPNS to v3.6.3 (hub)
Once we have updated version of 3.6.1 to 3.6.3 concentrator we are more able to set up a VPN session.
Hereby the newspapers from the hub and the Cisco VPN Client.
For security reasons, I replaced the following information:
Concentrators c.c.c.c = IP address
ISP of the assigned client IP = w.w.w.w.
The client IP address assigned (from pool) Concentratot = internal g.g.g.g
Primary DNS/WINS=D1.D1.D1.D1
Secondary DNS/WINS=D2.D2.D2.D2
Journal of the hub:
2002-08-10 183 14:20:24.840 SEV = 5 IP/49 RPT = 5
Transmitting station TCP SYN - ACK to client.w, port TCP dest 1677 pkt
10/08/2002 184 14:20:24.850 SEV = 5 RPT IP/50 = 9
Head of network TCP ACK from client.w, port TCP source 1677 pkt
185 10/08/2002 14:20:24.890 SEV = 5 RPT IP/50 = 10
Head of network TCP ACK from client.w, port TCP source 1677 pkt
186 10/08/2002 14:20:25.190 SEV = 5 RPT IP 41 = 5
Established client.w, the TCP source 1677 port TCP session.
188 10/08/2002 14:20:37.170 SEV = 4 RPT IKE/52 = 5.w
User group [TestGroup] [testuser]
(Testuser) user authenticated.
10/08/2002 189 14:20:37.280 SEV = 5 RPT IKE/184 = 5.w
User group [TestGroup] [testuser]
Client OS: Windows NT
The client Application version: 3.6.2 (Rel) of
192 10/08/2002 14:20:37.620 SEV = 4 RPT IKE/119 = 5.w
User group [TestGroup] [testuser]
PHASE 1 IS COMPLETE
2002-08-10 193 14:20:37.630 SEV = 5 RPT IKE/25 = 5.w
User group [TestGroup] [testuser]
Data received from the Proxy host remote ID supported:
Address g.g.g.g, protocol 0, Port 0
196-10/08/2002 14:20:37.630 SEV = 5 RPT IKE/24 = 5.w
User group [TestGroup] [testuser]
Data received from the Proxy host local ID supported:
Address c.c.c.c, protocol 0, Port 0
199-10/08/2002 14:20:37.630 SEV = 5 RPT IKE/66 = 5.w
User group [TestGroup] [testuser]
Remote peer IKE configured for SA: ESP-AES128-SHA
201 10/08/2002 14:20:37.630 SEV = IKE/0 4 RPT = 5.w
User group [TestGroup] [testuser]
All the proposals of the IPSec Security Association has deemed unacceptable!
202-10/08/2002 14:20:37.630 SEV = 4. RPT = 5 IKEDBG/0
Error of QM WSF (P2 struct & 0x1d150bc, mess id 0xbac8f29).
203-10/08/2002 14:20:37.630 SEV = 4 IKEDBG/65 RPT = 5.w
User group [TestGroup] [testuser]
History of mistake IKE responder QM WSF (struct & 0x1d150bc)
, : QM_DONE, EV_ERROR
QM_BLD_MSG2, EV_NEGO_SA
QM_BLD_MSG2, EV_IS_REKEY
QM_BLD_MSG2, EV_CONFIRM_SA
209 10/08/2002 14:20:37.640 SEV = 5 IP/43 RPT = 5
Remove entry TCP peripheral pour.w IDE oucederomsurlesecondport 1677
Journal of the client:
5 14:20:24.786 08/10/02 Sev = Info/6 DIALER / 0 x 63300002
Start the connection.
6 14:20:24.796 08/10/02 Sev = Info/4 CM / 0 x 63100002
Start the login process
7 14:20:24.796 08/10/02 Sev = Info/4 CM / 0 x 63100004
Establish a connection using Ethernet
8 14:20:24.796 08/10/02 Sev = Info/4 CM / 0 x 63100026
Attempt to connect with the server "c.c.c.c.
9 14:20:24.796 10/08/02 Sev = Info/6 CM / 0 x 63100033
Awarded the local TCP port 1677 for the TCP connection.
10 14:20:24.866 10/08/02 Sev = Info/4 CM/0x6310002D
TCP connection on port 10001 with Server "c.c.c.c.
11 14:20:24.996 08/10/02 Sev = Info/4 CM / 0 x 63100026
Attempt to connect with the server "c.c.c.c.
12 14:20:24.996 08/10/02 Sev = Info/6 IKE/0x6300003B
Try to establish a connection with c.c.c.c.
13 14:20:25.017 08/10/02 Sev = Info/4 IKE / 0 x 63000013
SEND to > ISAKMP OAK AG (SA, KE, NO, ID, VID, VID, VID) to c.c.c.c
14 14:20:25.347 08/10/02 Sev = Info/6 IPSEC/0x6370001F
TCP SYN sent to c.c.c.c, src port 1677, port dst 10001
15 14:20:25.347 08/10/02 Sev = Info/6 IPSEC/0x6370001C
TCP SYN - ACK received from c.c.c.c, src port 10001, port dst 1677
16 14:20:25.347 08/10/02 Sev = Info/6 IPSEC / 0 x 63700020
TCP ACK sent c.c.c.c, src port 1677, port dst 10001
17 14:20:25.347 08/10/02 Sev = Info/4 IPSEC / 0 x 63700014
Remove all keys
18 14:20:25.597 08/10/02 Sev = Info/5 IKE/0x6300002F
Received packet of ISAKMP: peer = c.c.c.c
19 14:20:25.597 08/10/02 Sev = Info/4 IKE / 0 x 63000014
RECEIVING< isakmp="" oak="" ag="" (sa,="" ke,="" non,="" id,="" hash,="" vid,="" vid,="" vid,="" vid,="" vid)="" from="">
20 14:20:25.597 08/10/02 Sev = Info/5 IKE / 0 x 63000059
Useful load Vendor ID = 12F5F28C457168A9702D9FE274CC0100
21 14:20:25.597 08/10/02 Sev = Info/5 IKE / 0 x 63000001
Peer is a compatible peer Cisco-Unity
22 14:20:25.597 08/10/02 Sev = Info/5 IKE / 0 x 63000059
Useful load Vendor ID = 09002689DFD6B712
23 14:20:25.597 08/10/02 Sev = Info/5 IKE / 0 x 63000001
Peer supports XAUTH
24 14:20:25.597 08/10/02 Sev = Info/5 IKE / 0 x 63000059
Useful load Vendor ID = AFCAD71368A1F1C96B8696FC77570100
25 14:20:25.597 08/10/02 Sev = Info/5 IKE / 0 x 63000001
Peer supports the DPD
26 14:20:25.597 08/10/02 Sev = Info/5 IKE / 0 x 63000059
Useful load Vendor ID = 4048B7D56EBCE88525E7DE7F00D6C2D3C0000000
27 14:20:25.597 10/08/02 Sev = Info/5 IKE / 0 x 63000059
Useful load Vendor ID = 1F07F70EAA6514D3B0FA96542A500306
28 14:20:25.617 08/10/02 Sev = Info/4 IKE / 0 x 63000013
SEND to > ISAKMP OAK AG * (HASH, NOTIFY: STATUS_INITIAL_CONTACT) to c.c.c.c
29 14:20:25.778 08/10/02 Sev = Info/5 IKE/0x6300002F
Received packet of ISAKMP: peer = c.c.c.c
30 14:20:25.778 08/10/02 Sev = Info/4 IKE / 0 x 63000014
RECEIVING< isakmp="" oak="" trans="" *(hash,="" attr)="" from="">
31 14:20:25.778 08/10/02 Sev = Info/4 CM / 0 x 63100015
Launch application xAuth
32 14:20:34.671 08/10/02 Sev = Info/4 CM / 0 x 63100017
xAuth application returned
33 14:20:34.671 08/10/02 Sev = Info/4 IKE / 0 x 63000013
SEND to > ISAKMP OAK TRANS *(HASH, ATTR) to c.c.c.c
34 14:20:37.194 08/10/02 Sev = Info/5 IKE/0x6300002F
Received packet of ISAKMP: peer = c.c.c.c
35 14:20:37.194 08/10/02 Sev = Info/4 IKE / 0 x 63000014
RECEIVING< isakmp="" oak="" trans="" *(hash,="" attr)="" from="">
36 14:20:37.194 08/10/02 Sev = Info/4 CM/0x6310000E
ITS established Phase 1. 1. ITS phase 1 in the system
37 14:20:37.194 08/10/02 Sev = Info/4 IKE / 0 x 63000013
SEND to > ISAKMP OAK TRANS *(HASH, ATTR) to c.c.c.c
38 14:20:37.204 08/10/02 Sev = Info/5 IKE/0x6300005D
Customer address a request from firewall to hub
39 14:20:37.204 08/10/02 Sev = Info/5 IKE/0x6300005C
Firewall policy: product = Cisco integrated customer, capacity = (centralized Protection Policy).
40 14:20:37.214 08/10/02 Sev = Info/4 IKE / 0 x 63000013
SEND to > ISAKMP OAK TRANS *(HASH, ATTR) to c.c.c.c
41 14:20:37.375 08/10/02 Sev = Info/5 IKE/0x6300002F
Received packet of ISAKMP: peer = c.c.c.c
42 14:20:37.375 08/10/02 Sev = Info/4 IKE / 0 x 63000014
RECEIVING< isakmp="" oak="" trans="" *(hash,="" attr)="" from="">
43 14:20:37.375 08/10/02 Sev = Info/5 IKE / 0 x 63000010
MODE_CFG_REPLY: Attribute = INTERNAL_IPV4_ADDRESS:, value = g.g.g.g
44 14:20:37.375 10/08/02 Sev = Info/5 IKE / 0 x 63000010
MODE_CFG_REPLY: Attribute = INTERNAL_IPV4_DNS (1):, value = d1.d1.d1.d1
45 14:20:37.375 08/10/02 Sev = Info/5 IKE / 0 x 63000010
MODE_CFG_REPLY: Attribute = INTERNAL_IPV4_DNS (2):, value = d2.d2.d2.d2
46 14:20:37.375 08/10/02 Sev = Info/5 IKE / 0 x 63000010
MODE_CFG_REPLY: Attribute = INTERNAL_IPV4_NBNS (1) (a.k.a. WINS):, value = d1.d1.d1.d1
47 14:20:37.375 08/10/02 Sev = Info/5 IKE / 0 x 63000010
MODE_CFG_REPLY: Attribute = INTERNAL_IPV4_NBNS (2) (a.k.a. WINS):, value = d2.d2.d2.d2
48 14:20:37.375 08/10/02 Sev = Info/5 IKE/0x6300000E
MODE_CFG_REPLY: Attribute = MODECFG_UNITY_BANNER, value = WARNING:
Any use of this system may be recorded or monitored without further notice, and newspapers that results can be used as evidence in court.
If you are not authorized to use this system disconnect now!
49 14:20:37.375 08/10/02 Sev = Info/5 IKE/0x6300000D
MODE_CFG_REPLY: Attribute = MODECFG_UNITY_SAVEPWD:, value = 0x00000000
50 14:20:37.375 08/10/02 Sev = Info/5 IKE/0x6300000D
MODE_CFG_REPLY: Attribute = MODECFG_UNITY_PFS:, value = 0x00000000
51 14:20:37.375 08/10/02 Sev = Info/5 IKE/0x6300000E
MODE_CFG_REPLY: Attribute = APPLICATION_VERSION, value = Cisco Systems, Inc. / VPN 3000 Concentrator Version 3.6.3.Rel created by vmurphy on October 4, 2002 16:23
52 14:20:37.425 08/10/02 Sev = Info/4 CM / 0 x 63100019
Data in mode Config received
53 14:20:37.465 08/10/02 Sev = Info/5 IKE / 0 x 63000055
Has received a request for Driver IP address c.c.c.c, GW IP = c.c.c.c key
54 14:20:37.465 08/10/02 Sev = Info/4 IKE / 0 x 63000013
SEND to > ISAKMP OAK QM * (HASH, SA, NO, ID, ID) to c.c.c.c
55 14:20:37.465 08/10/02 Sev = Info/5 IKE / 0 x 63000055
Received a key demand driver for IP 10.10.10.255, GW IP = c.c.c.c
56 14:20:37.465 08/10/02 Sev = Info/4 IKE / 0 x 63000013
SEND to > ISAKMP OAK QM * (HASH, SA, NO, ID, ID) to c.c.c.c
57 14:20:37.675 08/10/02 Sev = Info/5 IKE/0x6300002F
Received packet of ISAKMP: peer = c.c.c.c
58 14:20:37.675 08/10/02 Sev = Info/4 IKE / 0 x 63000014
RECEIVING< isakmp="" oak="" info="" *(hash,="" notify:status_resp_lifetime)="" from="">
59 14:20:37.675 08/10/02 Sev = Info/5 IKE / 0 x 63000044
Answering MACHINE-LIFE notify has value of 86400 seconds
60 14:20:37.675 10/08/02 Sev = Info/5 IKE / 0 x 63000046
This SA has already been living for 13 seconds, setting expiration 86387 seconds now
61 14:20:37.705 08/10/02 Sev = Info/5 IKE/0x6300002F
Received packet of ISAKMP: peer = c.c.c.c
62 14:20:37.705 08/10/02 Sev = Info/4 IKE / 0 x 63000014
RECEIVING< isakmp="" oak="" info="" *(hash,="" del)="" from="">
63 14:20:37.705 08/10/02 Sev = Info/5 IKE/0x6300003C
A receipt a payload to DELETE for IKE SA with Cookies = 2CDEFD1BD3EFB19215350D42094312B8
64 14:20:37.705 08/10/02 Sev = Info/5 IKE / 0 x 63000017
Marking of IKE SA delete (COOKIES = 2CDEFD1BD3EFB192 15350D42094312B8) reason = DEL_REASON_PEER_DELETION
65 14:20:38.066 08/10/02 Sev = Info/4 IPSEC / 0 x 63700014
Remove all keys
66 14:20:38.066 08/10/02 Sev = Info/6 IPSEC/0x6370002B
Sent packets of 6, 0 were fragmented.
67 14:20:38.066 08/10/02 Sev = Info/6 IPSEC/0x6370001D
TCP RST from c.c.c.c, src port 10001, port dst 1677
68 14:20:38.366 08/10/02 Sev = Info/4 CM / 0 x 63100012
ITS phase 1 deleted before first Phase 2 SA is caused by "DEL_REASON_PEER_DELETION". 0 ITS phase 1 currently in the system
69 14:20:38.366 08/10/02 Sev = Info/5 CM / 0 x 63100029
Initializing CVPNDrv
70 14:20:38.366 08/10/02 Sev = Info/4 CM / 0 x 63100031
Reset the TCP connection on port 10001
71 14:20:38.366 08/10/02 Sev = Info/6 CM / 0 x 63100034
Removed the local TCP port 1677 for the TCP connection.
72 14:20:38.416 08/10/02 Sev = WARNING/3 DIALER/0xE3300008
GI VPNStart callback doesn't have a 'CM_IKE_RECEIVED_DELETE_NOTIFICATION' (15 h).
73 14:20:39.418 08/10/02 Sev = Info/4 IPSEC / 0 x 63700012
Delete all keys associated with peer c.c.c.c
74 14:20:39.418 08/10/02 Sev = Info/4 IPSEC / 0 x 63700012
Delete all keys associated with peer c.c.c.c
75 14:20:39.418 08/10/02 Sev = Info/6 IPSEC / 0 x 63700022
TCP RST sent to c.c.c.c, src port 1677, port dst 10001
76 14:20:39.418 08/10/02 Sev = Info/4 IPSEC / 0 x 63700014
Remove all keys
77 14:20:39.418 08/10/02 Sev = Info/6 IPSEC/0x6370002B
Sent 4 packets, 0 were fragmented.
When I look at the proposals of active IKE SA or configurations all seems ok (so everything worked fine with 3.6.1. Concentrator release).
Any suggestion would be appreciated.
Marcel
OK, I tried it myself and ran into the same issue. AES seems to be broken in 3.6.3. A bug has been created (CSCdy88797) and will be corrected shortly, but for now, you need to use 3.6.1 or change the encryption algorithms if you simply use 3.6.3.
Sorry about that.
-
Hi guys,.
I am currently ut setting for the first time on a Cisco ASA 5505 Cisco AnyConnect SSL VPN.
I enclose my topology.
I ran the wizard of the ASDM on the ASA2 I want to use for my VPN connections.
Everything works fine except that I can't access any internal computer servers on my network.
I do a specific configuration because my servers have a different default gateway of the ASA that I use for my VPN?
I have since the ASA2 the 192.168.10.0 network.
my remote ip address of the pool is 10.0.0.1-10.0.0.10/24
config (I've included what, in my view, is necessary, please let me know if you need to see more):
ASA 2.0000 Version 8
Sysopt connection permit VPN
tunnel of splitting allowed access list standard 192.168.10.0 255.255.255.0
network of the NETWORK_OBJ_10.0.0.0 object
10.0.0.0 subnet 255.255.255.0
NAT (inside, outside) static source any any static destination NETWORK_OBJ_10.0.0.0 NETWORK_OBJ_10.0.0.0 non-proxy-arp-search to itinerary
internal GroupPolicy_vpn group strategy
attributes of Group Policy GroupPolicy_vpn
value of 192.168.10.20 WINS server
value of server DNS 192.168.10.15
client ssl-VPN-tunnel-Protocol ikev2
Split-tunnel-policy tunnelspecified
Split-tunnel-network-list value split tunnel
domain.local value by default-field
WebVPN
User PROFILE of value type profiles AnyConnect
type tunnel-group tunnel_vpn remote access
tunnel-group tunnel_vpn General-attributes
address ra_vpn_pool pool
Group Policy - by default-GroupPolicy_vpn
tunnel-group tunnel_vpn webvpn-attributes
activation of the Group tunnel_vpn alias
!
Thanks in advance!
Hello
The unit behind your ASAs on the internal LAN should really be a router switch or L3 and not a basic L2 switch.
You now have an asymmetric routing on your network, and this is the reason why the connection of the VPN device will not work.
The problem comes from the fact that internal devices use the ASA1 for the default gateway. When trying to connect to the VPN Client, the following happens
- Client VPN armed sends TCP SYN that happens by the VPN with the ASA2
- ASA2 passes the TCP SYN to the server
- Server responds with TCP SYN ACK for the VPN Client and sends this information to the ASA1 as the destination host is in another network (vpn pool)
- ASA1 sees the TCP SYN ACK, but never saw the TCP SYN so he abandoned the connection.
To work around the problem, you need to essentially configure TCP State Bypass on the ASA1 although I wouldn't really say that, but rather to change the configuration of the network so that traffic makes this way to start.
An option, even if not the best, would be to set the LAN of the ASA2 to ASA1 on some physical ports and set up a new network connection between them (not the same 192.168.10.x/yy). In this way the ASA1 would see the entire conversation between servers and VPN Clients and there are no problems with the flow of traffic.
But as I said it probably still isn't the best solution, but in my opinion better than having recourse to special configurations ASA1.
There could be a 'special' configuration on the ASA2 that you could use to make the Client VPN connections operate in their current configuration, without changing anything in the physical topology.
You can change the NAT for VPN Clients configuration so that the VPN ALL users would actually PATed to 192.168.10.4 IP address when they connect to your internal network. Given that the server would see the connection coming from the same network segment, they would know to forward traffic back with the ASA2 rather than ASA1 like her today.
If this is not an ideal solution.
No source (indoor, outdoor) nat static any any static destination NETWORK_OBJ_10.0.0.0 NETWORK_OBJ_10.0.0.0 non-proxy-arp-search to itinerary
the object of the LAN network
192.168.10.0 subnet 255.255.255.0
NAT (exterior, Interior) 1 dynamic source NETWORK_OBJ_10.0.0.0 destination static LAN LAN interface
Hope this helps
-Jouni
Maybe you are looking for
-
My browser to search was hacked, how do I get rid of this. It does not work in Internet Explorer. Please help cause I don't want to use IE I don't have to. I have tried different anti virus programs but its still here. Michael
-
Anyway keep a Skype conversation history?
So I was wondering if it was possible to keep the old Skype conversations, as back up a Skype folder and then once you have reinstalled Skype, being able to put it in and have all your conversations / conversations that were super old. When I'm spent
-
Why do I get a message to upgrade my iphone to 9.2.1 when it should be 9.2.1
I just got a dialog box that suggests that I have upgraded to IOS 9.2.1. The problem is that the version of IOS in my iPhone is already to 9.2.1. What is going on?
-
Camera HDR-AS50 disconnects right after that QR Code is scanned
Hello I have problems connecting my new ActionCam AS50 on my Android (Samsung Alpha) phone. Steps to follow: (1) first of all make sure that WIFI is on in the camera. (2) then I scan the QR code. (3) it asks me to connect. I say ok (4) it is said con
-
How to update Windows after re-installing Vista 32 bit.
I reinstalled Vista Home Premium 32-bit on my Dell E521 and 105 recommended updates to consider. Should I install all and hope for the best, or is there a better way to ensure that only the most recent updates are included? Tips appreciated. Thank