VPN to ASA with ISE and Posture
Hello
I'll put up a new facility of ISE. I want to install AnyConnect 4.1 and use ISE for authentication & posture validation. I'm ok with the side of the authentication of things.
http://www.Cisco.com/c/en/us/support/docs/security/Adaptive-Security-app...
This configuration applies to time AnyConnect 3.1 & 4.x?
Any help would be appreciated.
Thank you
Hi Stuart,
Yes - this configuration applies as well to the AC3 and AC4.
The new feature of AC4 is available directly from ISE ability:
http://www.Cisco.com/c/en/us/support/docs/security/AnyConnect-secure-mob...
But the posture itself works in a similar way.
Thank you
Michal
Tags: Cisco Security
Similar Questions
-
ASA VPN with ISE and different backends WBS for authentication
Hello
I have an AAA-problem I hope to have a few problems help.
The problem ultimately is: how the ASA via ISE send Radius Access requests to different given OTP backends provided a connection to a certain group of Tunnel.
BACKGROUND:
I'll try to give you a brief picture of the scenario, this is what I currently have.
A VPN system (ASA 8.4 (4)) where I let my users to choose among 3 different methods of authentication being
(1) certificate (on chip card)
(2) token - token of the OTP (One Time Password provided via the smartphone application: using pledge of Nordic OTP-Edge transport server)
(3) SMS - OTP token (Nordic OTP - Edge transport server SMS OTP)
The choice corresponds to different groups of profiles/Tunnel connection.
Today, all authentication requests go directly to the OTP server and authorization goes directly to the AD via LDAP.
THE PROBLEM:
The problem occurs when I try to put in the ISE in the mixture.
What I obviously (?) would like to do is have all the network authentication/authorization to go through my ISE platform to take advantage of a centralized administration, monitoring etc.
Again I would need to use data bases different backend such as AD and Nordic OTP - Edge server, but then mandated by ISE.
For me to be able to know what back-end AAA to the proxy system, to somehow be able to distinguish the incoming Radius Access-requests.
WHAT WE CALL:
At the time of the ASA 8.4.3 Radius access request contains 2 new attributes, the name of Group of Tunnel and the Type of customer, when a VPN user connects.
http://www.Cisco.com/en/us/docs/security/ASA/asa84/configuration/guide/ref_extserver.html#wp1802187
QUESTION:
The seams, that I can achieve what I want by looking at the access request attribute Radius "Tunnel Group Name" and forward my request to different backends OTP for the authentication part therefore in theory. But, how do I actually go ahead and set that up in ISE?
I don't see this attribute when I look at the details of Radius Authentication for an authentication AAA of the ASA at the ISE.
Best regards
/ Mattias
I think you can hit the following problem:
CSCtz49846: ISE does not match the condition with VPN 146 Tunnel-Group-Name attribute
This issue is not specific to this attribute, as shown in the solution shown in the accompanying note
Workaround
Ensure that the attribute name does not include a '.' character. This also applies to some of the existing attributes in the dictionary of Cisco-VPN300. Attribute names should be changed so that they do not include a "." character.
-
VPN IPSec ASA with two ISP active
Hi ALL!
I have a question.
So I have ASA with 9.2 (1) SW connected to ISP with active SLA.
I need to configure redundant IPSec VPN via ISP2, while all other traffic must go through isps1. In case if one of the ISP goes down all including VPN traffic must be routed via ISP alive.
I have configured SLA and it works.
ciscoasa # display route performance
Route 0.0.0.0 isps1 0.0.0.0 10.175.2.5 5 track 1
Route isp2 0.0.0.0 0.0.0.0 10.175.3.5 10 track 2
Route isp2 172.22.10.5 255.255.255.255 10.175.3.5 1 excerpt 2Here we can see if isps1 and ISP2 are RISING, all traffic passes through isps1, but traffic intended for the remote peer IPSec 172.22.10.5 passes by ISP2.
This configuration works just at the moment when isps1 or isp2 is down or if a static route for 172.22.10.5 deleted. Where two Internet service providers are increasing to ASA does not send the next remote IPSec datagrams.
ciscoasa # display running nat
NAT (inside, isp2) source static obj-INSIDE_LAN obj-INSIDE_LAN destination static obj-REMOTE_LAN obj-REMOTE_LAN no-proxy-arp-search to itinerary
NAT (inside isps1) source static obj-INSIDE_LAN obj-INSIDE_LAN destination static obj-REMOTE_LAN obj-REMOTE_LAN no-proxy-arp-search to itineraryCrypto ipsec transform-set ikev1 ESP-AES-256-SHA esp-aes-256 esp-sha-hmac
Crypto ipsec pmtu aging infinite - the security association
card crypto cm_vpnc 10 correspondence address acl_vpn
card crypto cm_vpnc 10 set pfs
peer set card crypto cm_vpnc 10 172.22.10.5
card crypto cm_vpnc 10 set transform-set ESP-AES-256-SHA ikev1
86400 seconds, duration of life card crypto cm_vpnc 10 set - the security association
card crypto cm_vpnc interface isps1
cm_vpnc interface isp2 crypto card
trustpool crypto ca policy
isps1 enable ikev1 crypto
isp2 enable ikev1 crypto
IKEv1 crypto policy 1
preshared authentication
aes-256 encryption
sha hash
Group 2
life 86400ciscoasa # show ip
System of IP addresses:
Subnet mask IP address name interface method
Vlan1 in 192.168.2.1 255.255.255.0 CONFIG
Isps1 Vlan2 10.175.2.10 255.255.255.0 CONFIG
Isp2 Vlan3 10.175.3.10 255.255.255.0 CONFIGThe main question why?
Thank you in advance,
Anton
Hi anton,.
If you check the log message on your ASA R301-IS , he's trying to build the tunnel VPN with both IP and it receives packets of asymmetrically your distance ciscoasa.
TO avoid this asymmetrical connection, point your IP from peers as primary & secondary on your R301-EAST
set peer 10.175.3.10 10.175.2.10
Delete the track on your routing entries
Route isp2 172.22.10.5 255.255.255.255 10.175.3.5
This should work for you.
Similalry lower your ISP 2, you should see VPN tunnel is mounted with isps1 one.
HTH
Sandy
-
ASA with firepower and Licensing Service
Hello
If I buy an ASA with the power of Fire Service (e.g. 5516-X) should which licenses I buy?
I understand that I need to order a license for the Service of firepower. E.g. IPS, URLS, and AMP.
Should I order a license management FireSIGHT, too? The centre of mandatory FireSIGHT management? This license is necessary?
Concerning
You will need the license of control (CTRL). It is free and automatically included with any package of power of fire SKU (i.e. ASA5516-FPWR-K9).
Then you must add the IPS, URLS or AMP (or combination of both) services in term 1, 3 or 5 years.
FireSIGHT Management Center is not required for entry-level (5506, 5508 or 5516) models. It is optional on those you can use the entry firesight level integrated in ASDM for the model.
For all other models, it is necessary. If you manage more than a simple ASA (even an HA pair) it is recommended even for the entry level models that you will be so power sync policies through them all.
-
Guest access with ISE and WLC LWA
Hi guys,.
Our company try to implement access as guest with dan ISE WLC with the local Web authentication method. But there is problem that comes with the certificate. This is the scenario:
1. the clients are trying to connect wifi with guest SSID
2. once it connects, you can open the browser and try to open a Web page (example: cisco.com)
3, because guests didn't connect, so this link redirect to "ISE Guest Login Page" (become): url
)
4. If there is no Login to ISE not installed comments Page, no reliable connection of message message, but it will be fine is they "Add Exception and install the certificate".

5. once the Guest Login Page will appear and you can enter their username and password.

6 connection success and they will be redirected to www.cisco.com and there pop-up 1.1.1.1 (IP of the Virtual Interface WLC) with the logout button.
The problem occur in scenario 6, after the success of the opening session, the Web page with the address and the error of certificate ISE IP to 1.1.1.1 is appear.

I know that it happened when you can has no Page of Login of WLC certificate...
My Question is, is there a way of tunneling WLC certificate to EHT? Or what we can do for ISE validate certificate WLC, invited didn't need to install the certificate WLC / root certificate before you connect to the Wifi?
THX 4 your answer and sorry for my bad English...
Do not mix WLC with ISE comments Portal local Web authentication. Choose one or the other. I suggest the portal + WLC CWA.
-
Hi all
My apologies if this is a trivial question, but I spent considerable time trying to search and had no luck.
I encountered a problem trying to set up a temporary L2L VPN from a Subscriber with CISCO2911 sitting behind the router of the ISP of an ASA. ISP has informed that I can't ignore their device and complete the circuit Internet on the Cisco for a reason, so I'm stuck with it. The Setup is:
company 10.1.17.1 - y.y.y.y - router Internet - z.z.z.z - ISP - LAN - 10.x.x.2 - XXX1 - ASA - 10.1.17.2 - CISCO2911 - 10.1.15.1 LAN
where 10.x.x.x is a corporate LAN Beach private network, y.y.y.y is a public ip address assigned to the external interface of the ASA and the z.z.z.z is the public IP address of the ISP router.
I have forwarded ports 500, 4500 and ESP on the ISP router for 10.1.17.2. The 2911 config attached below, what I can't understand is what peer IP address to configure on the SAA, because if I use z.z.z.z it will be a cause of incompatibility of identity 2911 identifies himself as 10.1.17.2...
! ^ ^ ^ ISAKMP (Phase 1) ^ ^ ^!
crypto ISAKMP policy 5
BA 3des
md5 hash
preshared authentication
Group 2
lifetime 28800
isakmp encryption key * address no.-xauth y.y.y.y! ^ ^ ^ IPSEC (Phase 2) ^ ^ ^!
crymap extended IP access list
IP 10.1.15.0 allow 0.0.0.255 10.0.0.0 0.255.255.255
Crypto ipsec transform-set ESP-3DES-SHA 3rd-esp esp-sha-hmac
card crypto 1 TUNNEL VPN ipsec-isakmp
defined peer y.y.y.y
game of transformation-ESP-3DES-SHA
match the address crymapGi0/2 interface
card crypto VPN TUNNELHello
debug output, it seems he's going on IPSEC States at the tunnel of final bud QM_IDLE's.
What I noticed in your configuration of ASA box, it's that you're usig PFS but not on 2911 router.
So I suggest:
no card crypto OUTSIDE_map 4 don't set pfs <-- this="" will="" disable="" pfs="" on="" asa="">
Then try tunnel initiate.
Kind regards
Jan
-
VPN IPSEC ASA with counterpart with dynamic IP and certificates
Hello!
Someone please give me config the work of the ASA for ASA Site to Site IPSEC VPN with counterpart with dynamic IP and authentication certificates.
He works with PSK authentication. But the connection landed at DefaultRAGroup instead of DefaultL2LGroup with certificate
authentication.
Should what special config I ask a DefaultRAGroup to activate the connection?
Thank you!
The ASA uses parts of the client cert DN to perform a tunnel-group lookup to place the user in a group. When "peer-id-validate req" is defined the ASA also tries to compare the IKE ID (cert DN) with the actual cert DN (also received in IKE negotiation), if the comparison fails the connection fails. know you could set "peer-id-validate cert" for the time being and the ASA will try to compare the values but allow the connection if it cannot.
In general I would suggest using option "cert."
With nocheck, we are simply not strict on IKE ID matchin the certificate, which is normally not a problem of security :-)
-
VPN split tunnel with 1811W and IAS RADIUS problems
I am very new to the implementation of a VPN IPSEC with a Cisco router. I know very well on the way to do it with a PIX / ASA, but the controls are a bit different in IOS, where my questions. Here is what is happening, I can connect to the VPN with the Cisco VPN Client. I would assign it an address of my ip pool that I created, but when I try to access the remote network somehow, I can't. I ran a tracert and what is really weird, is that I get the external IP address of the 1811W as my first jump when I list an internal IP address of the remote network (it also fixes the device FULL domain name, so I know that my DNS configuration is correct). I will list my config to the 1811W as well as the screenshot of the tracert. I've removed all the passwords that are encrypted, but they are there in the router config and I am able to connect to the network and click the IAS server behind it. Please excuse the config as we took it during another TI provider so that it can have a few additional entries that may not be necessary that I have not yet cleaned.
Tracert:
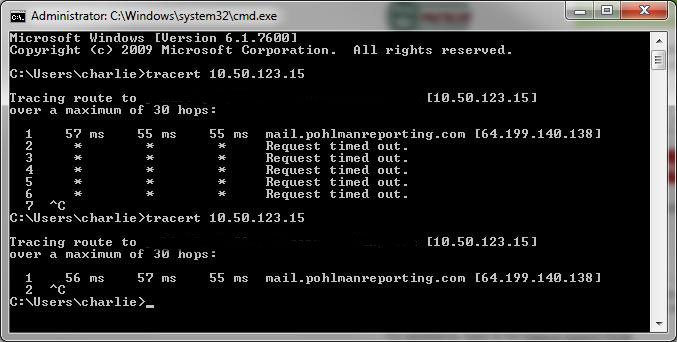
And here's the full config:
Building configuration...
Current configuration: 9320 bytes
!
version 12.4
no service button
horodateurs service debug datetime msec
Log service timestamps datetime localtime show-time zone
encryption password service
!
hostname RTR01
!
boot-start-marker
boot-end-marker
!
logging buffered 8192
enable password 7
!
AAA new-model
!
!
AAA authentication login userauthen local radius group
AAA authorization groupauthor LAN
!
!
AAA - the id of the joint session
clock TimeZone Central - 6
!
SSID dot11 internal
VLAN 5
open authentication
authentication wpa key management
Comments-mode
WPA - psk ascii 7
!
dot11 ssid public access
VLAN 10
open authentication
!
!
!
IP cef
No dhcp use connected vrf ip
DHCP excluded-address 192.168.1.1 IP 192.168.1.10
DHCP excluded-address IP 192.168.1.20 192.168.1.254
!
public IP dhcp pool
import all
network 192.168.1.0 255.255.255.0
default router 192.168.1.1
DNS-server 10.50.123.15 207.69.188.186
!
!
no ip domain search
IP domain name pohlmanreporting.com
!
Authenticated MultiLink bundle-name Panel
!
Crypto pki trustpoint TP-self-signed-3986412950
enrollment selfsigned
name of the object cn = IOS - Self - signed - certificate - 3986412950
revocation checking no
rsakeypair TP-self-signed-3986412950
!
!
TP-self-signed-3986412950 crypto pki certificate chain
certificate self-signed 01
quit smoking
!
!
password username admin privilege 15 7
username cisco password 7
username secret privilege 15 ssetech 5
Archives
The config log
!
!
!
!
crypto ISAKMP policy 1
BA 3des
md5 hash
preshared authentication
Group 2
!
crypto ISAKMP policy 10
BA 3des
preshared authentication
Group 2
!
Configuration group VPNGROUP crypto isakmp client
me?
DNS 10.50.123.15
domain domain.com
pool VPNPOOL
ACL 110
include-local-lan!
!
Crypto ipsec transform-set esp-3des-md5 esp-3des esp-md5-hmac
Crypto ipsec transform-set esp-des-md5 esp - esp-md5-hmac
Crypto ipsec transform-set esp-3des esp-sha-hmac TRANS_3DES_SHA
Crypto ipsec transform-set esp-3des esp-sha-hmac RIGHT
!
crypto dynamic-map EXA_DYNAMIC_MAP 10
Set transform-set RIGHT
market arriere-route
!
!
card crypto client EXT_MAP of authentication list userauthen
card crypto isakmp authorization list groupauthor EXT_MAP
crypto card for the EXT_MAP client configuration address respond
card crypto EXT_MAP 10-isakmp dynamic ipsec EXA_DYNAMIC_MAP
!
!
!
Bridge IRB
!
!
!
interface FastEthernet0
IP 64.199.140.138 255.255.255.248
IP access-group denied-hack-attack in
no ip redirection
no ip unreachable
no ip proxy-arp
NAT outside IP
IP virtual-reassembly
route IP cache flow
automatic duplex
automatic speed
No cdp enable
card crypto EXT_MAP
!
interface FastEthernet1
REDUNDANT INET CONNECTION description
no ip address
automatic duplex
automatic speed
!
interface FastEthernet2
!
interface FastEthernet3
!
interface FastEthernet4
!
interface FastEthernet5
!
FastEthernet6 interface
!
interface FastEthernet7
!
interface FastEthernet8
!
interface FastEthernet9
!
interface Dot11Radio0
Description 802. 11B / G interface
no ip address
!
encryption vlan 5 tkip encryption mode
!
SSID internal
!
public access SSID
!
Base speed - 1.0 2.0 basic basic-5, 5 6.0 9.0 basic-11, 0 12.0 18.0 24.0 36.0 48.0
channel 2462
root of station-role
!
interface Dot11Radio0.5
encapsulation dot1Q 5
No cdp enable
Bridge-Group 1
Bridge-group subscriber-loop-control 1
Bridge-Group 1 covering-disabled people
Bridge-Group 1 block-unknown-source
No source of bridge-Group 1-learning
unicast bridge-Group 1-floods
!
interface Dot11Radio0.10
encapsulation dot1Q 10
IP 192.168.1.1 255.255.255.0
IP access-group 130 to
IP nat inside
IP virtual-reassembly
No cdp enable
!
interface Dot11Radio1
description of the 802 interface. 11A
no ip address
Shutdown
Speed - Basic6.0 9.0 basic - 12.0 18.0 basic-24, 0-36.0 48.0 54.0
root of station-role
!
interface Vlan1
no ip address
Bridge-Group 1
!
interface Async1
no ip address
encapsulation sheet
!
interface BVI1
IP 10.50.123.1 255.255.255.0
IP access-group 105 to
IP nat inside
IP virtual-reassembly
IP tcp adjust-mss 1452
!
local IP VPNPOOL 192.168.130.1 pool 192.168.130.50
IP route 0.0.0.0 0.0.0.0 64.199.140.137
IP route 10.60.52.0 255.255.255.0 10.50.123.2
!
!
IP http server
local IP http authentication
IP http secure server
IP http timeout policy inactive 600 life 86400 request 10000
IP nat POOL 64.199.140.138 pool 64.199.140.142 netmask 255.255.255.248
overload of IP nat inside source list 120 interface FastEthernet0
IP nat inside source map of route-nat interface FastEthernet0 overload
IP nat inside source static tcp 10.50.123.14 21 64.199.140.138 21 expandable
IP nat inside source static tcp 10.50.123.11 25 64.199.140.138 25 expandable
IP nat inside source static tcp 10.50.123.11 80 64.199.140.138 80 extensible
IP nat inside source static tcp 10.50.123.11 143 64.199.140.138 143 extensible
IP nat inside source static tcp 10.50.123.11 443 64.199.140.138 443 extensible
IP nat inside source static tcp 10.50.123.10 64.199.140.138 1723 1723 extensible
IP nat inside source static tcp 10.50.123.14 21 64.199.140.139 21 expandable
IP nat inside source static tcp 10.50.123.18 80 64.199.140.139 80 extensible
IP nat inside source static tcp 10.50.123.18 443 64.199.140.139 443 extensible
IP nat inside source static tcp 10.50.123.18 64.199.140.139 3389 3389 extensible
IP nat inside source static tcp 10.50.123.14 80 64.199.140.141 80 extensible
IP nat inside source static tcp 10.50.123.14 443 64.199.140.141 443 extensible
IP nat inside source static 10.50.123.40 expandable 64.199.140.142
!
deny-hack-attack extended IP access list
permit udp 10.0.0.0 0.255.255.255 any eq snmp
deny udp any any eq snmp
deny udp any any eq tftp
deny udp any any eq bootpc
deny udp any any eq bootps
deny ip 172.16.0.0 0.15.255.255 all
deny ip 192.168.0.0 0.0.255.255 everything
allow an ip
!
recording of debug trap
record 10.50.123.15
access-list 99 allow 10.0.0.0 0.255.255.255
access-list 99 allow 69.63.100.0 0.0.1.255
access-list 102 permit ip 10.50.123.0 0.0.0.255 10.60.52.0 0.0.0.255
access-list 105 deny ip any host 69.63.101.225
105 ip access list allow a whole
access-list 110 permit ip 10.50.123.0 0.0.0.255 192.168.130.0 0.0.0.255
access-list 111 deny ip 10.50.123.0 0.0.0.255 10.10.0.0 0.0.255.255
access-list 111 deny ip 10.50.123.0 0.0.0.255 10.60.52.0 0.0.0.255
access-list 111 allow ip 10.50.123.0 0.0.0.255 any
access-list 112 deny ip 10.50.123.0 0.0.0.255 172.0.0.0 0.0.0.255
access ip-list 112 allow a whole
access-list 120 allow ip 192.168.1.0 0.0.0.255 any
access-list 130 allow udp 192.168.1.0 0.0.0.255 host 10.50.123.10 eq field
access list 130 permit tcp 192.168.1.0 0.0.0.255 host 10.50.123.10 eq field
access list 130 permit tcp 192.168.1.0 0.0.0.255 host 10.50.123.16 eq www
access list 130 permit tcp 192.168.1.0 0.0.0.255 host 10.50.123.16 eq 443
access-list 130 deny ip any 10.0.0.0 0.255.255.255
access-list 130 ip allow a whole
SNMP-server community no RO
!
!
!
map of route-nat allowed 10
corresponds to the IP 111
!
!
!
RADIUS-server host 10.50.123.13 auth-port 1645 acct-port 1646 hits 7
!
control plan
!
Bridge Protocol ieee 1
1 channel ip bridge
!
Line con 0
exec-timeout 120 0
line 1
Modem InOut
StopBits 1
Speed 115200
FlowControl hardware
line to 0
line vty 0 4
location * Access Virtual Terminal allowed only from internal network *.
access-class 99 in
exec-timeout 0 0
connection of authentication userauthen
transport input telnet ssh
!
max-task-time 5000 Planner!
WebVPN cef
!
WebVPN context Default_context
SSL authentication check all
!
no go
!
!
endYou must also create NAT exemption for traffic between your internal network to the VPN Client pool.
You have the following NAT 2 instructions:
overload of IP nat inside source list 120 interface FastEthernet0
IP nat inside source map of route-nat interface FastEthernet0 overloadFor the 120 access list, please add the following:
120 extended IP access list
1 refuse the ip 10.50.123.0 0.0.0.255 192.168.130.0 0.0.0.255
Uses of "-nat ' ACL 111 route map, please also add the following:
111 extended IP access list
1 refuse the ip 10.50.123.0 0.0.0.255 192.168.130.0 0.0.0.255
Then ' delete ip nat trans * "after the above changes and try to connect again.
Hope that helps.
-
VPN IPSEC ASA with overlap proxy-ID
All,
Currently I have a VPN from a single network ASA spoke to a single hub of AAS, so I set up my access lists so that the source is specific to speak it (for example 192.168.1.0/24) and I use the word "any" key for destination. I need to add a few more VPN connections, so can I just add lower inside specific networks to any instruction in the card encryption. See below.
outside_10_cryptomap list extended access allowed object-group home-networks-networks another ip
outside_20_cryptomap list of allowed ip extended access object-group network inside everything
card crypto outside_map 10 correspondence address outside_10_cryptomap
card crypto outside_map 10 set peer 1.1.1.1
outside_map card crypto 10 the transform-set ESP-3DES-MD5 value
card crypto outside_map 20 match address outside_20_cryptomap
card crypto outside_map 20 peers set 2.2.2.2
outside_map card crypto 20 the transform-set ESP-3DES-MD5 value
Gregory
Now I come to think of it, I remember a problem with less specific entries in the ACL before more specific entries.
So it should work, but you must make sure that the most specific comes before the less specific that you seem to have done with your config.
Jon
-
some computers are not authenticated successfully with ISE and join comments vlan
Hello
We have deployed ISE in a company and set the workstations for authentication of the computer. When jobs are authentication, they are placed in the VLAN Data (5), if they fail, then they must be placed in the VLAN (50). WiredAutoConfig service as supplicant is set with gpo to all the workstations have the same settings.
Certificate of the ISE is signed by our internal CA and workstations have also imported CA in their trusted CA list.
The problem is that few jobs are placed in the VLAN. Previously on these workstations, we got a pop-up as below. When you click on 'connect' work stations have been placed properly in the data VLAN (5). We do not get this security alert more on these machines and they just join them VLAN that is don't want we want.
However, most of the workstations is authenticated successfully.

switchports configuration:
switchport access vlan 5
switchport mode access
switchport voice vlan 6
authentication event fail following action method
action of death event authentication server allow vlan 5
action of death event authentication server allow voice
no response from the authentication event action allow vlan 50
living action of the server reset the authentication event
multi-domain of host-mode authentication
authentication order dot1x mab
authentication priority dot1x mab
Auto control of the port of authentication
periodic authentication
authentication violation replace
MAB
MLS qos trust dscp
dot1x EAP authenticator
dot1x tx-time 10
spanning tree portfast
spanning tree enable bpduguardJournal of ISE authentication;
Everyone is in a similar situation?
I guess that the machines in the domain have the root CA certificate checked under the 'Protected EAP Properties' window?
-
LT2P configuration vpn cisco asa with the internet machine windows/mac issue
Dear all,
I have properly configured configuration vpn L2TP on asa 5510 with 8.0 (4) version of IOS.
My internet does not work when I connect using the vpn. Even if I give power of attorney or dns or I remove the proxy
It does not work. only the resources behind the firewall, I can access. I use the extended access list
I tried also with the standard access list.
Please please suggest what error might be.
Thank you
JV
Split for L2TP over IPSec tunnel tunnel is not configured on the head end (ASA), it must be configured on the client itself, in accordance with the following Microsoft article:
-
IPSec VPN between ASAs with same subnet for disaster recovery
Hello
I need some clarification from you guys.
To do disaster EasyVPN tunnels for the Cisco ASA 5505 firewall recovery site. Now, there is only one main site and 3 remote sites.
Dr., must use the same subnet that it is on the main site because virtual machines Vmware will be replicated to DR.
For the DR we use Double-Take software.
What is the best solution for this? I think we could use NAT of Destination on ASAs. Other sites (HQ and remote control) will be directed to only address NAT of the
DR and not real which is the same as on the main site.
So guys, will this work? We are using IPSec VPN? In packet - trace on ASA, I see that the package is the first using a NAT, and then encrypted, so it should work, Yes?
I hope someone can confirm this.
I can confirm that this will work certainly,
for prior type natting see 8.3:
http://www.Cisco.com/en/us/products/ps6120/products_configuration_example09186a0080b37d0b.shtml#diag
for 8.3 and later it is also achievable.
-
Hello, I was hoping someone might have an example of a site to site VPN configuration where the ASA is statically NATting its internal network. Basically the same configuration like this, but instead of "not nat", the ASA is NATting. So instead of the remote site, connect to the local network 10.10.10.0/24, ASA would be NAT at 172.16.17.0/24 for example.
http://www.Cisco.com/en/us/products/ps9422/products_configuration_example09186a0080b4ae61.shtml
Thank you.
Mike
It's not very complicated, just keep in mind that NAT is done before the encryption.
So if you your network 10.10.10.0/24 nat internal to 172.16.17.0/24:
public static 172.16.17.0 (Interior, exterior) 10.10.10.0 netmask 255.255.255.0
You can use the address translated into your crypto-ACL:
REMOTE VPN ip 172.16.17.0 access list allow REMOTE-NET 255.255.255.0 255.255.255.0
I suppose that you run ASA v8.3 + that you referred to an older document. If you have a more recent software, the logic is the same but the NAT commands differ.
Sent by Cisco Support technique iPad App
-
Troubleshooting IPSec Site to Site VPN between ASA and 1841
Hi all
in the past I've implemented several VPN connections between the devices of the SAA. So I thought a site link between an ASA site and 1841 would be easier... But it seems I was mistaken.
I configured a VPN Site to Site, as it has been described in the Document ID: SDM 110198: IPsec Site to Site VPN between ASA/PIX and an example of IOS Router Configuration (I have not used SDM but CCP).
I have run the wizards on the ASA with ASDM and the current IOS version 15.1 1841, with CCP.
It seems to Phase 1 and 2 are coming although my ASA in ADSM reports (monitoring > VPN > VPN statistics > Sessions) a tunnel established with some of the Tx traffic but 0 Rx traffic),
On the ASA:
Output of the command: "sh crypto ipsec its peer 217.xx.yy.zz.
address of the peers: 217.86.154.120
Crypto map tag: VPN-OUTSIDE, seq num: 2, local addr: 62.aa.bb.ccaccess extensive list ip 192.168.37.0 outside_2_cryptomap_1 allow 255.255.255.0 172.20.2.0 255.255.255.0
local ident (addr, mask, prot, port): (LAN-A/255.255.255.0/0/0)
Remote ident (addr, mask, prot, port): (LAN-G/255.255.255.0/0/0)
current_peer: 217.xx.yy.zz#pkts program: 400, #pkts encrypt: 400, #pkts digest: 400
#pkts decaps: 0, #pkts decrypt: 0, #pkts check: 0
compressed #pkts: 0, unzipped #pkts: 0
#pkts uncompressed: 400, comp #pkts failed: 0, #pkts Dang failed: 0
success #frag before: 0, failures before #frag: 0, #fragments created: 0
Sent #PMTUs: 0, #PMTUs rcvd: 0, reassembly: 20th century / of frgs #decapsulated: 0
#send errors: 0, #recv errors: 0local crypto endpt. : 62.aa.bb.cc, remote Start crypto. : 217.xx.yy.zz
Path mtu 1500, fresh ipsec generals 58, media, mtu 1500
current outbound SPI: 39135054
current inbound SPI: B2E9E500SAS of the esp on arrival:
SPI: 0xB2E9E500 (3001672960)
transform: esp-3des esp-sha-hmac no compression
running parameters = {L2L, Tunnel, PFS 2 group}
slot: 0, id_conn: 100327424, crypto-map: VPN-OUTSIDE
calendar of his: service life remaining (KB/s) key: (4374000/1598)
Size IV: 8 bytes
support for replay detection: Y
Anti-replay bitmap:
0x00000000 0x00000001
outgoing esp sas:
SPI: 0 x 39135054 (957567060)
transform: esp-3des esp-sha-hmac no compression
running parameters = {L2L, Tunnel, PFS 2 group}
slot: 0, id_conn: 100327424, crypto-map: VPN-OUTSIDE
calendar of his: service life remaining (KB/s) key: (4373976/1598)
Size IV: 8 bytes
support for replay detection: Y
Anti-replay bitmap:
0x00000000 0x00000001Output of the command: "sh crypto isakmp his."
HIS active: 4
Generate a new key SA: 0 (a tunnel report Active 1 and 1 to generate a new key during the generate a new key)
Total SA IKE: 4IKE Peer: 217.xx.yy.zz
Type: L2L role: initiator
Generate a new key: no State: MM_ACTIVEOn the 1841
1841 crypto isakmp #sh its
IPv4 Crypto ISAKMP Security Association
DST CBC conn-State id
217.86.154.120 62.153.156.163 QM_IDLE 1002 ACTIVE1841 crypto ipsec #sh its
Interface: Dialer1
Tag crypto map: SDM_CMAP_1, local addr 217.86.154.120protégé of the vrf: (none)
local ident (addr, mask, prot, port): (172.20.2.0/255.255.255.0/0/0)
Remote ident (addr, mask, prot, port): (192.168.37.0/255.255.255.0/0/0)
current_peer 62.153.156.163 port 500
LICENCE, flags is {origin_is_acl},
#pkts program: encrypt 0, #pkts: 0, #pkts digest: 0
#pkts decaps: 585, #pkts decrypt: 585, #pkts check: 585
compressed #pkts: 0, unzipped #pkts: 0
#pkts uncompressed: 0, #pkts compr. has failed: 0
#pkts not unpacked: 0, #pkts decompress failed: 0
Errors #send 0, #recv 0 errorslocal crypto endpt. : 217.86.154.120, remote Start crypto. : 62.153.156.163
Path mtu 1452, ip mtu 1452, ip mtu BID Dialer1
current outbound SPI: 0xB2E9E500 (3001672960)
PFS (Y/N): Y, Diffie-Hellman group: group2SAS of the esp on arrival:
SPI: 0 x 39135054 (957567060)
transform: esp-3des esp-sha-hmac.
running parameters = {Tunnel}
Conn ID: 2003, flow_id: FPGA:3, sibling_flags 80000046, card crypto: SDM_CMAP_1
calendar of his: service life remaining (k/s) key: (4505068/1306)
Size IV: 8 bytes
support for replay detection: Y
Status: ACTIVEthe arrival ah sas:
SAS of the CFP on arrival:
outgoing esp sas:
SPI: 0xB2E9E500 (3001672960)
transform: esp-3des esp-sha-hmac.
running parameters = {Tunnel}
Conn ID: 2004, flow_id: FPGA:4, sibling_flags 80000046, card crypto: SDM_CMAP_1
calendar of his: service life remaining (k/s) key: (4505118/1306)
Size IV: 8 bytes
support for replay detection: Y
Status: ACTIVEoutgoing ah sas:
outgoing CFP sas:
Interface: virtual Network1
Tag crypto map: SDM_CMAP_1, local addr 217.86.154.120protégé of the vrf: (none)
local ident (addr, mask, prot, port): (172.20.2.0/255.255.255.0/0/0)
Remote ident (addr, mask, prot, port): (192.168.37.0/255.255.255.0/0/0)
current_peer 62.153.156.163 port 500
LICENCE, flags is {origin_is_acl},
#pkts program: encrypt 0, #pkts: 0, #pkts digest: 0
#pkts decaps: 585, #pkts decrypt: 585, #pkts check: 585
compressed #pkts: 0, unzipped #pkts: 0
#pkts uncompressed: 0, #pkts compr. has failed: 0
#pkts not unpacked: 0, #pkts decompress failed: 0
Errors #send 0, #recv 0 errorslocal crypto endpt. : 217.86.154.120, remote Start crypto. : 62.153.156.163
Path mtu 1452, ip mtu 1452, ip mtu BID Dialer1
current outbound SPI: 0xB2E9E500 (3001672960)
PFS (Y/N): Y, Diffie-Hellman group: group2SAS of the esp on arrival:
SPI: 0 x 39135054 (957567060)
transform: esp-3des esp-sha-hmac.
running parameters = {Tunnel}
Conn ID: 2003, flow_id: FPGA:3, sibling_flags 80000046, card crypto: SDM_CMAP_1
calendar of his: service life remaining (k/s) key: (4505068/1306)
Size IV: 8 bytes
support for replay detection: Y
Status: ACTIVEthe arrival ah sas:
SAS of the CFP on arrival:
outgoing esp sas:
SPI: 0xB2E9E500 (3001672960)
transform: esp-3des esp-sha-hmac.
running parameters = {Tunnel}
Conn ID: 2004, flow_id: FPGA:4, sibling_flags 80000046, card crypto: SDM_CMAP_1
calendar of his: service life remaining (k/s) key: (4505118/1306)
Size IV: 8 bytes
support for replay detection: Y
Status: ACTIVEoutgoing ah sas:
outgoing CFP sas:
It seems that the routing on the 1841 is working properly as I can tear down the tunnel and relaunch in scathing a host on the network of 1841, but not vice versa.
Trounleshoot VPN of the 1841 report shows a message like "the following sources are forwarded through the interface card crypto. (172.20.2.0 1) go to "Configure-> routing" and correct the routing table.
I have not found an error on the 1841 config so if one of the guys reading this thread has an idea I appreciate highly suspicion!
It's the running of the 1841 configuration
!
version 15.1
horodateurs service debug datetime msec
Log service timestamps datetime msec
encryption password service
!
host name 1841
!
boot-start-marker
start the system flash c1841-adventerprisek9 - mz.151 - 1.T.bin
boot-end-marker
!
logging buffered 51200 notifications
!
AAA new-model
!
!
AAA authentication login default local
!
AAA - the id of the joint session
!
iomem 20 memory size
clock timezone PCTime 1
PCTime of summer time clock day March 30, 2003 02:00 October 26, 2003 03:00
dot11 syslog
IP source-route
!
No dhcp use connected vrf ip
!
IP cef
no ip bootp Server
IP domain name test
name of the IP-server 194.25.2.129
name of the IP-server 194.25.2.130
name of the IP-server 194.25.2.131
name of the IP-server 194.25.2.132
name of the IP-server 194.25.2.133
No ipv6 cef
!
Authenticated MultiLink bundle-name Panel
!
!
object-group network phone
VoIP phone description
Home 172.20.2.50
Home 172.20.2.51
!
redundancy
!
!
controller LAN 0/0/0
atm mode
Annex symmetrical shdsl DSL-mode B
!
!
crypto ISAKMP policy 1
BA 3des
preshared authentication
Group 2
isakmp encryption key * address 62.aa.bb.cc
!
!
Crypto ipsec transform-set esp-SHA-ESP-3DES-3des esp-sha-hmac
!
map SDM_CMAP_1 1 ipsec-isakmp crypto
Description Tunnel to62.aa.bb.cc
the value of 62.aa.bb.cc peer
game of transformation-ESP-3DES-SHA
PFS group2 Set
match address 100
!
!
!
interface FastEthernet0/0
DMZ description $ FW_OUTSIDE$
10.10.10.254 IP address 255.255.255.0
IP nat inside
IP virtual-reassembly
automatic duplex
automatic speed
!
interface FastEthernet0/1
Description $ETH - LAN$ $FW_INSIDE$
IP 172.20.2.254 255.255.255.0
IP access-group 100 to
IP nat inside
IP virtual-reassembly
IP tcp adjust-mss 1412
automatic duplex
automatic speed
!
ATM0/0/0 interface
no ip address
No atm ilmi-keepalive
!
point-to-point interface ATM0/0/0.1
PVC 1/32
PPPoE-client dial-pool-number 1
!
!
interface Dialer1
Description $FW_OUTSIDE$
the negotiated IP address
IP mtu 1452
NAT outside IP
IP virtual-reassembly
encapsulation ppp
Dialer pool 1
Dialer-Group 2
PPP authentication chap callin pap
PPP chap hostname xxxxxxx
PPP chap password 7 xxxxxxx8
PPP pap sent-name of user password xxxxxxx xxxxxxx 7
map SDM_CMAP_1 crypto
!
IP forward-Protocol ND
IP http server
local IP http authentication
IP http secure server
!
!
The dns server IP
IP nat inside source static tcp 10.10.10.1 808 interface Dialer1 80
IP nat inside source static tcp 10.10.10.1 25 25 Dialer1 interface
IP nat inside source overload map route SDM_RMAP_1 interface Dialer1
IP nat inside source overload map route SDM_RMAP_2 interface Dialer1
IP route 0.0.0.0 0.0.0.0 Dialer1 permanent
!
logging trap notifications
Note category of access list 1 = 2 CCP_ACL
access-list 1 permit 172.20.2.0 0.0.0.255
Note access-list category 2 CCP_ACL = 2
access-list 2 allow 10.10.10.0 0.0.0.255
Note access-list 100 category CCP_ACL = 4
Note access-list 100 IPSec rule
access-list 100 permit ip 172.20.2.0 0.0.0.255 192.168.37.0 0.0.0.255
Note CCP_ACL the access list 101 = 2 category
Note access-list 101 IPSec rule
access-list 101 deny ip 172.20.2.0 0.0.0.255 192.168.37.0 0.0.0.255
access-list 101 permit ip 172.20.2.0 0.0.0.255 any
Note access-list 102 CCP_ACL category = 2
Note access-list 102 IPSec rule
access-list 102 deny ip 172.20.2.0 0.0.0.255 192.168.37.0 0.0.0.255
access-list 102 permit ip 10.10.10.0 0.0.0.255 any
!!
allowed SDM_RMAP_1 1 route map
corresponds to the IP 101
!
allowed SDM_RMAP_2 1 route map
corresponds to the IP 102
!
!
control plan
!
!
Line con 0
line to 0
line vty 0 4
length 0
transport input telnet ssh
!
Scheduler allocate 20000 1000
NTP-Calendar Update
NTP 172.20.2.250 Server prefer
endAs I mentioned previously: suspicion is much appreciated!
Best regards
Joerg
Joerg,
ASA receives not all VPN packages because IOS does not send anything.
Try to send packets to the 1841 LAN to LAN of the ASA and see is the "sh cry ips its" on the 1841 increments the encrypted packets (there not)
The problem seems so on the side of the router.
I think that is a routing problem, but you only have one default gateway (no other channels on the router).
The ACL 100 is set to encrypt the traffic between the two subnets.
It seems that the ACL 101 is also bypassing NAT for VPN traffic.
Follow these steps:
Try running traffic of LAN router inside IP (source of ping 192.168.37.x 172.20.2.254) and see if the packages are not through the translation and obtaining encrypted.
I would also like to delete 100 ACL from the inside interface on the router because it is used for the VPN. You can create an another ACL to apply to the interface.
Federico.
-
ISE and WLC for sanitation of the posture
Please can someone clarify a few things regarding the ISE and posture wireless.
(1) is the ACL-POSTURE-REDIRECT used for conversion, or is it just an ACL to redirect some of the posture of the kickoff checking traffic?
(2) can / a dACL/wACL list must be specified as a sanitation ACL?
(3) the WLC ACL should be written in long format (manually specify source and dest ports/doesny direction any job?)
(4) does anyone have working example ACL for redirect (CPC) posture and sanitation (dACL)?
(5) any other advice or pointers would be as useful as any docs I have found so far, what he TrustSec2, CiscoLive or anything else, do not seem to help me understand sanitation and WLC posture
Thank you
Nick
Yes,
This means that strategy available to your customer does not have a rule that will correspond to an entrepreneur who joined the network. Can you post a screenshot of the provisioning of customer policy?
Thank you
Tarik Admani
* Please note the useful messages *.
Maybe you are looking for
-
How to capture (record) streaming video online with his partner is on El Capitan?
Someone can advise or recommend including many different programs available that I must use to capture (record) streaming video online with it's associated audio on El Capitan? I tried MacX DVD Converter Pro, but believe it or not, it does not recor
-
My ipad is not syncing with my mini ipad contacts - how can I do?
How can I synchronize my contacts in my ipad to contacts in my mini ipad?
-
Out of memory system on environment 2011 27 "imacz
Yesterday began to receive messages from memory system on a regular basis. I haven't added any new application for almost a year and have not been broadcast nothing more than safari (with only 1 or 2 windows open), mail, adobe pro, calendar, contacts
-
I am running 64-bit Windows Vista Edition Home Premium with Service Pack 1 on my HP Pavilion dv7t-1000. I don't know why I had not noticed it before, but I checked my update history and found that my computer has been a failure to download Windows u
-
How to contact Microsoft? to order a copy of windows XP to reinstall my operating system damaged?
I have an old Compaq laptop that was purchased new with Windows XP Home Edition installed on it. Over the years, he became so slow that I can't do more. Is it possible to contact Microsoft and get a replacement OS cd in order to format the hard dri

