AnyConnect 3.1.04072 allows remote users
I find no establishment of VPN Windows with "Allow remote users" in the profile editor. Is it discouraged?
Pavlo,
Could be a limitation of the profile editor you are using (stand-alone or ASDM?)
The value exists in VPN XML reference:
and his retirement to my knowledge.
M.
Tags: Cisco Security
Similar Questions
-
remote users access site ipsec tunnel
How to configure the ACL and the road to allow remote users access to site ipsec as local users?
Current scenario is
1. distance users (192.168.2.0/24) ipsec <->Cisco 870 (192.168.0.0/24)
(2 cisco 870(192.168.0.0/24) ipsec tunnel <->cisco 1811 (10.0.0.0/24)
Now remote users can access the 192.168.0.0 network, no problem, but how they can access 10.0.0.0 network?
I guess I can do like this:
1. in cisco 870, site to site ip 192.168.0.0 tunnel allow 0.0.0.255 10.0.0.0 0.0.0.255
(add) permit ip 192.168.2.0 0.0.0.255 10.0.0.0 0.0.0.255
2. in the site-to-site vpn cisco 1811
(add) permit ip 10.0.0.0 0.0.0.255 192.168.2.0 0.0.0.255
3. in settings vpn split cisco870 add the 10.0.0.0/24 network
Is this fair?
Thank you.
You must configure the interesting traffic that an ACL contains the source is remote destination as local LAN and LAN.
-
ASA5505 with 10 users. Need to connect 25 remote users with AnyConnect Client
Hello to everyone.
I ASA5505 with license 10 users. I need to connect 25 remote users via SSL VPN (in my case cisco Anyconnect client). So I have to buy the license more security (ASA5505-SEC-PL =) for more then 10 simultaneous VPN connections on Cisco ASA 5505. Fix?
And the main question. What I need to order the user getting up-to-date (for example ASA5505-SW-10-50 =, or ASA5505-SW-10-UL =) license for my device Cisco ASA5505 in order to have 25 connections of concurrent remote users without restriction for each remote user?
You need the license SecPlus for increased remote access users. But you don't need an extra user license if you still only up to 10 internal systems.
-
AnyConnect using IKEV2 that allows access to the provider
Hello world
We have configured Anyconnect using IKEv2 for our internal users and it works fine.
Recently I received the request of our management to allow our service provider to our network, but they do need full access to our internal network.
This provider also uses the IKEv2 anyconnect to access their own internal network.
What I've done is asked our IT guy provider to update their profile with info below xml
XYZ.com
XYZ.com where xyz.com is our ASA VPN hostname.
Need to know what I have to config anyconnect new profile and political group to make it work, or can I only create new group policy for this provider?
Concerning
Mahesh
Yes, it's a common use case Mahesh.
Whenever you install remote access VPN, one of the things you have to decide is to tunnel all traffic, traffic tunnel to specified networks, or to exclude the tunneling for some networks.
It is usually a case of "split tunnel" (these two types) or "no split tunnel" (or "tunnelall"). Since you want to tunnel all traffic, then follow a Setup for "tunnelall." It should look like:
attributes of the strategy of group vendorgroup
Ikev2 VPN-tunnel-Protocol
Split-tunnel-policy tunnelallIt is a good recent example in the next document in TAC.
-
Vulnerabilities in Microsoft Windows could allow Remote Code execution
My Question is: are you F * % ING KIDDING ME?
Original title: Ko 3039066 security to PREVENT a REMOTE EXECUTION of CODE after 5years vulnerability update FAILING to INSTALL / UNINSTALLED by windows update!
Hi C.D.Miller,
What operating system is installed on your computer?
This update fixes vulnerabilities in Microsoft Windows. The vulnerability could allow remote code execution if an attacker successfully convince a user to navigate to a specially designed website, specially designed to open or access a working directory that contains a specially designed DLL file.
Follow the workaround solutions mentioned in the article below and check if that helps.
Microsoft Security Bulletin MS15-020
I hope this helps.
-
To find the details of connection of the remote user to my computer
I want to know who is connected to my office using the Remote Desktop feature in Windows XP / Vista / windows &. is there a system where Windows saves the remote user connection logs
Hi Roger,
Remote Desktop connection is a technology that allows you to sit at a computer (sometimes called the client computer) and connect to a remote computer (called the host computer) in a different location.
If someone wants to connect to your computer, you need to enable remote desktop on the computer.
For more information, see the links.
Connect to another computer using Remote Desktop connection
Remote Desktop connection: frequently asked questions
If you suspect an infection of malicious software on your computer, see the link.
How to stimulate your defence of malware and protect your PC
Note: The data files that are infected must be cleaned only by removing the file completely, which means that there is a risk of data loss.
Event Viewer is a snap Microsoft Management Console (MMC) that allows you to browse and manage event logs. It is an indispensable tool for the operation of systems for monitoring and resolution of problems when they arise.
For more information, see the link.
http://TechNet.Microsoft.com/en-us/library/cc766042 (WS.10) .aspx
Please update us with the results and we will be happy to help you.
-
Add an account, leaving the remote user to choose the password
I need to let some (lan) users remote access to a folder. I discovered that, if her sweat and the password are the same of the remote account, vista doesn't do not ask credential and allow the user easily. I like it, but the remote user does not want to share with me their password for the pc, so I'm thinking how to add them elsewhere.
Sorry, but I would say to the remote user it does not work like that. You must be able to add name of account/password your on your computer. Maybe you must host this file on a type of DropBox site instead of on your local computer. MS - MVP - Elephant Boy computers - don't panic!
-
NAC Appliance with ASA (for remote user VPN)
I have a pair of firewall 5520 cisco which is used as a VPN gateway (for remote user VPN) and perimeter firewall Internet (to provide outbound internet connectivity).
We allow the NAC to remote VPN users. I have it will be deployed with active 3 layer inband.
The problem with this design is that how to ensure that outgoing internet traffic does not pass through the CASE?
I heard about couple of optioins:
-ACB (for send only IP subnet to VPN users remote to go through CASE)
-Version 8.x characteristic of ASA (Restrcit access to VLAN under Group Policy).
I intend to do with ASA firewall where I can set a new subinterface on the SAA (with a new tag VLAN) and under the group policy for remote user VPN, I select the option to "restrict access to the new VLAN.
My question is: is - it still works (even if the firewall have a route to the internal network by using the 'inside' interface and NOT the new interface of the NAC). If this does not work, please let me know what are the other options for this type of deployment.
Thanks in advance.
Hello
It should work. Please see the attached PDF for more clarity on this topic: https://supportforums.cisco.com/docs/DOC-9102
HTH,
Faisal
-
remote VPN and vpn site to site vpn remote users unable to access the local network
As per below config remote vpn and vpn site to site vpn remote users unable to access the local network please suggest me a required config
The local 192.168.215.4 not able ping server IP this server connectivity remote vpn works fine but not able to ping to the local network vpn users.
ASA Version 8.2 (2)
!
host name
domain kunchevrolet
activate r8xwsBuKsSP7kABz encrypted password
r8xwsBuKsSP7kABz encrypted passwd
names of
!
interface Ethernet0/0
nameif outside
security-level 0
PPPoE client vpdn group dataone
IP address pppoe
!
interface Ethernet0/1
nameif inside
security-level 50
IP 192.168.215.2 255.255.255.0
!
interface Ethernet0/2
nameif Internet
security-level 0
IP address dhcp setroute
!
interface Ethernet0/3
Shutdown
No nameif
no level of security
no ip address
!
interface Management0/0
Shutdown
No nameif
no level of security
no ip address
management only
!
passive FTP mode
clock timezone IST 5 30
DNS server-group DefaultDNS
domain kunchevrolet
permit same-security-traffic intra-interface
object-group network GM-DC-VPN-Gateway
object-group, net-LAN
access extensive list ip 192.168.215.0 sptnl allow 255.255.255.0 192.168.2.0 255.255.255.0
192.168.215.0 IP Access-list extended sheep 255.255.255.0 allow 192.168.2.0 255.255.255.0
tunnel of splitting allowed access list standard 192.168.215.0 255.255.255.0
pager lines 24
Enable logging
asdm of logging of information
Outside 1500 MTU
Within 1500 MTU
MTU 1500 Internet
IP local pool VPN_Users 192.168.2.1 - 192.168.2.250 mask 255.255.255.0
ICMP unreachable rate-limit 1 burst-size 1
enable ASDM history
ARP timeout 14400
NAT-control
Global 1 interface (outside)
NAT (inside) 1 0.0.0.0 0.0.0.0
Route outside 0.0.0.0 0.0.0.0 59.90.214.1 1
Timeout xlate 03:00
Timeout conn 01:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
Sunrpc timeout 0:10:00 h323 0:05:00 h225 mgcp from 01:00 0:05:00 mgcp-pat 0:05:00
Sip timeout 0:30:00 sip_media 0:02:00 prompt Protocol sip-0: 03:00 sip - disconnect 0:02:00
Timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
dynamic-access-policy-registration DfltAccessPolicy
the ssh LOCAL console AAA authentication
AAA authentication LOCAL telnet console
AAA authentication http LOCAL console
AAA authentication enable LOCAL console
LOCAL AAA authentication serial console
Enable http server
x.x.x.x 255.255.255.252 out http
http 192.168.215.0 255.255.255.252 inside
http 192.168.215.0 255.255.255.0 inside
No snmp server location
No snmp Server contact
Server enable SNMP traps snmp authentication linkup, linkdown cold start
Crypto ipsec transform-set esp-3des esp-sha-hmac RIGHT
life crypto ipsec security association seconds 28800
Crypto ipsec kilobytes of life - safety 4608000 association
Crypto-map dynamic dynmap 65500 transform-set RIGHT
card crypto 10 VPN ipsec-isakmp dynamic dynmap
card crypto VPN outside interface
card crypto 10 ASA-01 set peer 221.135.138.130
card crypto 10 ASA - 01 the transform-set RIGHT value
crypto ISAKMP allow outside
crypto ISAKMP policy 10
preshared authentication
3des encryption
sha hash
Group 2
life 86400
crypto ISAKMP policy 65535
preshared authentication
the Encryption
sha hash
Group 2
lifetime 28800
Telnet 192.168.215.0 255.255.255.0 inside
Telnet timeout 5
SSH 0.0.0.0 0.0.0.0 outdoors
SSH timeout 5
Console timeout 0
management-access inside
VPDN group dataone request dialout pppoe
VPDN group dataone localname bb4027654187_scdrid
VPDN group dataone ppp authentication chap
VPDN username bb4027654187_scdrid password * local store
interface for identifying DHCP-client Internet customer
dhcpd dns 218.248.255.141 218.248.245.1
!
dhcpd address 192.168.215.11 - 192.168.215.254 inside
dhcpd allow inside
!
a basic threat threat detection
Statistics-list of access threat detection
no statistical threat detection tcp-interception
Des-sha1 encryption SSL
WebVPN
allow outside
tunnel-group-list activate
internal kun group policy
kun group policy attributes
VPN - connections 8
Protocol-tunnel-VPN IPSec
Split-tunnel-policy tunnelspecified
Split-tunnel-network-list value split tunnel
kunchevrolet value by default-field
test P4ttSyrm33SV8TYp encrypted password username
username kunauto password bSHrKTGl8PUbvus / encrypted privilege 15
username kunauto attributes
Strategy Group-VPN-kun
Protocol-tunnel-VPN IPSec
tunnel-group vpngroup type remote access
tunnel-group vpngroup General attributes
address pool VPN_Users
Group Policy - by default-kun
tunnel-group vpngroup webvpn-attributes
the vpngroup group alias activation
vpngroup group tunnel ipsec-attributes
pre-shared key *.
type tunnel-group test remote access
tunnel-group x.x.x.x type ipsec-l2l
tunnel-group ipsec-attributes x.x.x.x
pre-shared key *.
!
class-map inspection_default
match default-inspection-traffic
!
!
type of policy-card inspect dns preset_dns_map
parameters
maximum message length automatic of customer
message-length maximum 512
Policy-map global_policy
class inspection_default
inspect the preset_dns_map dns
inspect the ftp
inspect h323 h225
inspect the h323 ras
Review the ip options
inspect the netbios
inspect the rsh
inspect the rtsp
inspect the skinny
inspect esmtp
inspect sqlnet
inspect sunrpc
inspect the tftp
inspect the sip
inspect xdmcp
inspect the icmp
!
global service-policy global_policy
context of prompt hostname
call-home
Profile of CiscoTAC-1
no active account
http https://tools.cisco.com/its/service/oddce/services/DDCEService destination address
email address of destination [email protected] / * /
destination-mode http transport
Subscribe to alert-group diagnosis
Subscribe to alert-group environment
Subscribe to alert-group monthly periodic inventory
monthly periodicals to subscribe to alert-group configuration
daily periodic subscribe to alert-group telemetry
Cryptochecksum:0d2497e1280e41ab3875e77c6b184cf8
: end
kunauto #.Hello
Looking at the configuration, there is an access list this nat exemption: -.
192.168.215.0 IP Access-list extended sheep 255.255.255.0 allow 192.168.2.0 255.255.255.0
But it is not applied in the States of nat.
Send the following command to the nat exemption to apply: -.
NAT (inside) 0 access-list sheep
Kind regards
Dinesh Moudgil
P.S. Please mark this message as 'Responded' If you find this information useful so that it brings goodness to other users of the community
-
DB link without remote user password
Hi gurus,
I am creating a db_link from one database to others for a specific user. But I won't have the password for the remote user.
I tried by method of hash values that allowed me to create the db link but while accessing data, I ORA-00600: [see Err Kzdlk_zt2] and according to the values of the hash for the 456320.1 id method will not work.
Is there any other method to create a db_link without knowing the name of user and password remote.
Help, please.
We had the same problem g 11, that Oracle accounts created in the past and no one remembers the password. Not only that, but these applications that connect to the database also have the encrypted passwords.
We also had to create links to the database between databases, and of course 'IDENTIFIED BY VALUES' has failed.
Therefore, the solution was to create new accounts on the db target to be exclusively used for db links and provide these accounts with the necessary privileges to access the data.
I recommend using KeePass Password Safe to build your repositories of passwords and avoid this problem in the future.
Good luck!
-
(1) under address book, used for the book of MAC OS X, as well as the collected addresses and a third list, I can't remember.
Now it lists only MAC OS address book."(2) if I click on"Always allow remote content"it won't let me click on 'OK', I think that it says in the top left corner" adds: "but gives me an empty list.
Thank you!
If I'm more mac savy you we're in trouble. The last Mac I used has a black and white screen and used the floppy 3 1/2 "
See Troubleshooting in the Thunderbird Help menu, and then click the display folder of your profile (Thunderbird knows where he is, even if I'm not) the History.mab file is your collected addresses.
-
Application of the remote user
Hi guys,.
Do I have a chance to connect to the phone/ipad as a remote user/desktop? I need to connect an iPad to my family member and change the setting.
Thank you
I'm not aware of any way to do it on the iPad. There is an app that can interact with iOS itself, and as much as I know, there is none who can do right now.
~ Lyssa
-
Reconnect a remote user to the Volume Manager
I have a remote user who was gertting a license from my Volume Manager.
At the end of last week (when there was some network problems) it has been disconnected from the server, and now it seemed to reconnect.
It is now day 14 countdown (expiring Dec. 7), so he is anxious to get this resolved soon.
I tried to disconnect and reconnect the Volume Manager, but that did not help.
Clues?
TIA
Richard
James
We solved the problem by running 'vlmclient' on the remote machine, and this re-establsihed contact for the user.
I have to admit that after disconnection due to network problems, software to reconnect automatically to the VLM-, I would have expected but perhaps, it cannot differentiate between a manual disconnection and this situation.
Thanks a lot for your help.
Richard
-
Difficulty the front Dimension of the array, but allow the user to change the size of the array
Hello
I know there are a few other posts on table and scroll bars but mine is a little different. I want to have the physical size of the fixed table control and allow the user to change the size of the array as required and a scroll bar if the number of elements exceeds the specified physical dimension. I wouldn't mind if, at the end of the scroll bar, the user sees an uninitialized element.
Thank you very much
Hello
The problem I have with the property Num Row node is it seems to replace the scroll bar. Whenever I try to change the line number, the table automatically resizes its physical size on the front and the scroll bar has no effect.
However, I solved the problem by taking row completely digital. I just said if the table size is > to a constant value (i.e. 3), add a scroll bar and my front panel dashboard to be a size larger than what the value of this constant is size. Once I begin to add values in sequential order and I get to the fourth value, the scroll bar is added and the scroll bar has a feature where it adds an element of null for you, so if I fill this null element I just increased the size of the table and another null element appears underneath.
Thanks for the help
-
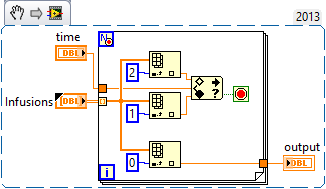
I want to allow the user to specify a curve like this:

Such as some under - VI shows the A2 value when a variable of time is between R1, A1 when the time variable is between A2 and A3 when time is in the range A3.
My design looks like this:
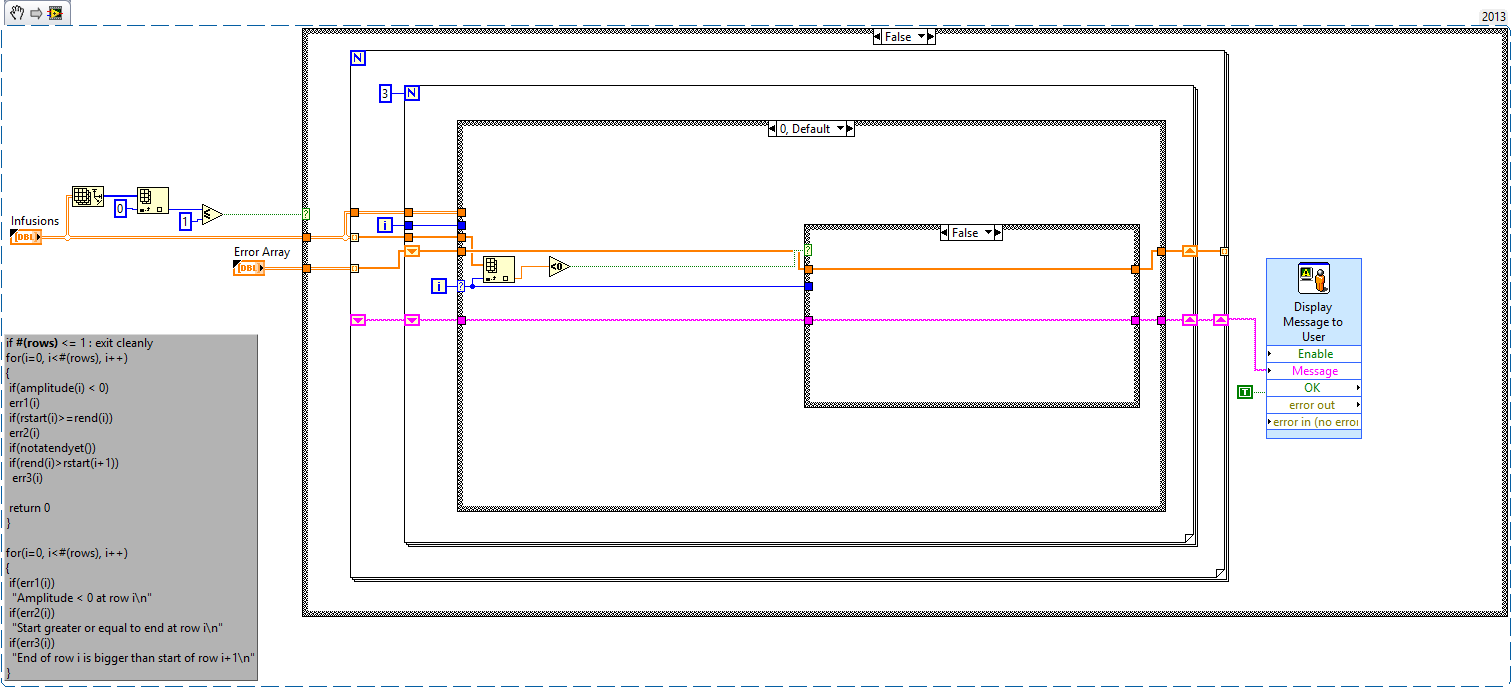
With the error checking that looks like this:
My question is, is the approach of the table according to optimal? Otherwise, how could combat this?
I think I can summarize the conversation on this point as a response to the original question (what is the best way...) -to start writing code, to think about what you want to accomplish and write it down (otherwise known as 'Write the first Documentation'). One of the points of a good User Interface is that it is not allow users to "stupid mistakes" - it leads the user "by hand", limiting the entries to the "legal values" and demanding that the entries be made logically.
If you were going to have a list of Infusions to enter, it is therefore logical to decide or not to enter into time intervals (which are always > 0) or order the times (which, logically) are still growing. You can (and should) decide that you (or you may have a control that allows the user decide, but maybe it's too flexible) and then apply your "rules".
Let's say you've decided on "Intervals" (which seems to me to be more User Friendly). After the user has entered the intervals (and you've provided a nice plot of perfusion vs. time), pouvez allow you the user to an interval of 'split', 'Delete' an interval, or "Edit the Infusion" interval, or you can decide to have a choice more simple "accept or start again" - If you have only a few intervals, the last would be the simplest (and therefore best) design choice.
Spend more time thinking before coding usually pays Big dividends!
(Speaking of sad experience) Bob Schor
Maybe you are looking for
-
How to import my address book from Outlook?
I have Windows 7 and Outlook on the same hard drive in Linux
-
P1C61EA #ABZ: problem Audio (driver?)
Hi, yesterday I updated to W10 anniversary. After that, my PC has a lot of audio problems, include the bass too metallic. So after reading in this forum I've updated the driver (sp74867), but doesn't my audio control (F6 key on the keyboard) and the
-
Upgrade SSD in Satellite L50 - has
IM intend to put an SSD in my L50 - A - 1 7 but I don't know if my laptop supports SATAIII. IM also not to use my ODD will be a work of caddy hard drive to put my hard drive in there to store data?
-
I'd like to import my photos in the computer to another I have pad 2. Thanks for your help.
-
Hi all... I have a few quick questions for everyone. I recently bought my laptop as well as the Microsoft Bluetooth Notebook 5000 mouse. I tried to get the laptop to see the mouse, but I keep coming up empty. I guess my questions are, first, that