Cisco VTI and configuration of IPSec (IKE Phase2) ITS proposal.
Hello
I have a question about the functionality of the virtual Tunnel Interface (VTI) configuration option. I have a Cisco IOS router, ending individual customers with the tunnel interfaces. The question I have now is that how can I specify the traffic 'interesting' on the security association proposal ITS IPsec (IKE Phase2). The configuration of the router is made by cryptographic profiles like this:
!
crypto ISAKMP policy 10
BA 3des
preshared authentication
Group 2
!
Crypto isakmp ISAKMP_PHASE1_PARAMETERS profile
key ring PRESHARED_KEYS
function identity address 1.2.3.4 255.255.255.255
!
door-key crypto PRESHARED_KEYS
pre-shared key address 1.2.3.4 key xyz
!
Crypto ipsec transform-set esp-3des esp-sha-hmac VPN-TRANSFORMSET
!
Profile of crypto ipsec ISAKMP_PHASE2_TUNNEL
game of transformation-VPN-TRANSFORMSET
PFS group2 Set
ISAKMP_PHASE1_PARAMETERS Set isakmp-profile
!
Tunnel1 interface
IP 10.10.10.1 255.255.255.252
IP mtu 1450
source of tunnel Loopback1
tunnel destination 1.2.3.4
ipv4 ipsec tunnel mode
Tunnel ISAKMP_PHASE2_TUNNEL ipsec protection profile
!
Now when I look at the output of the command 'See the crypto ipsec his tu1 int' I get the following:
....
Interface: Tunnel1
Tag crypto map: x.x.x.x addr Tunnel1-head-0, local
protégé of the vrf: (none)
local ident (addr, mask, prot, port): (0.0.0.0/0.0.0.0/0/0)
Remote ident (addr, mask, prot, port): (0.0.0.0/0.0.0.0/0/0)
current_peer 1.2.3.4 port 500
LICENCE, flags is {origin_is_acl},
....
However, the peer on the other side do not accept the proposal, as it would like to have specific IP subnets on the IPSec security association proposal parameters. He would accept the policy if the identity local remote proxies, for example, would be 192.168.10.0/255.255.255.0/0/0 (local) and
192.168.200.0/255.255.255.0/0/0 (remotely).
Y at - it 'interesting' no IOS configuration for traffic configuration option on the profile of crypto? With the crypto map - basic configuration you can specify interesting traffic with an ACL under the crypto map configuration section.
I'm in IOS version 15.1 (4) M with Advanced IP Services have together.
Hello
ASIT will always want to negotiate a whole as traffic selectors.
What you MIGHT find is multi-SA DVTI configuration, in what remote end could say what proxy identity he would like to encrypt. (Supported from 15.2 M / T)
Unfortunately, the ceveat of this configuration is this remote end needs to open the negotiation.
M.
Tags: Cisco Security
Similar Questions
-
Right off the bat, the wizard tells me that I can't use a multicast address, when it is the only destination I am interested in security. Here is exactly what I want to do - no more, no less (although I can use the mode of transport instead of tunnel at some point):
#! / bin/bash
Echo 2 >/proc/sys/net/ipv4/conf/eth0/force_igmp_version
# NOTE: To avoid the possibility of breaking IGMPv2 snooping, src should ONLY be defined for SHIPPERS, NOT for RECEIVERS! Otherwise, joins will be compromised by the IPsec encryption and the switch will not detect them.
IP xfrm State flush; IP political xfrm hunting
State of xfrm IP add src 10.0.2.15 dst 239.192.1.1 proto esp spi 0x54c1859e tunnel mode reqid 0x67cea4aa auth-trunc hmac\ (sha256\) 128 0xc8a8bf5ce6330699c3500bd8d2637bc1fa26929bab747d5ff2a1c4dddc7ce7ff enc cbc\ (aes\) 0xfdce8eaf81e3da02fa67e07df975c0111ecfa906561e762e5f3e78dfe106498e # aead rfc4106\ (gcm\ (aes\) \) 0x123456789abcdef0baddeed0deadbeeffeedface900df00d0fedcba987654321 128 #Error: duplicate 'ALGO-TYPE': 'aead' is the second value.
xfrm IP strategy add 10.0.2.15 src 239.192.1.1 dst dir output stat CBC 10.0.2.15 dst 239.192.1.1 proto reqid 0x67cea4aa tunnel mode esp
xfrm IP policy add 10.0.2.15 src 239.192.1.1 dst dir in src 10.0.2.15 stat dst 239.192.1.1 proto reqid 0x67cea4aa tunnel mode esp
xfrm IP strategy add 10.0.2.15 src dst 239.192.1.1 dir fwd stat 10.0.2.15 src dst 239.192.1.1 proto reqid 0x67cea4aa esp tunnel mode
A graphical interface which requires me to work in step by step mode (in particular to implement a relatively simple configuration of the shared key) with no idea of what irrelevant or confusing questions await us doing me no favor. And while this computer uses Windows 7, the eventual target can use something older or newer. I want to do is create the portable equivalent of a preferred scenario, no instructions to repeat the time-consuming and confusing. This approach exist? (I already checked cygwin and there seems to be no support for the ip packet, and even if there were, it seems not support sudo is.)
Hello
Thank you for visiting Microsoft Community and we provide a detailed description of the issue.
I suggest you to send your request in the TechNet forums to get the problem resolved.
Please visit the link below to send your query in the TechNet forums:
https://social.technet.Microsoft.com/forums/en-us/home?category=WindowsServer
Hope this information is useful. Please come back to write to us if you need more help, we will be happy to help you.
-
IPSec vpn cisco asa and acs 5.1
We have configured authentication ipsec vpn cisco asa acs 5.1:
Here is the config in cisco vpn 5580:
standard access list acltest allow 10.10.30.0 255.255.255.0
RADIUS protocol AAA-server Gserver
AAA-server host 10.1.8.10 Gserver (inside)
Cisco key
AAA-server host 10.1.8.11 Gserver (inside)
Cisco key
internal group gpTest strategy
gpTest group policy attributes
Protocol-tunnel-VPN IPSec
Split-tunnel-policy tunnelspecified
value of Split-tunnel-network-list acltest
type tunnel-group test remote access
tunnel-group test general attributes
address localpool pool
Group Policy - by default-gpTest
authentication-server-group LOCAL Gserver
authorization-server-group Gserver
accounting-server-group Gserver
IPSec-attributes of tunnel-group test
pre-shared-key cisco123
GBA, we config user group: VPN users. all VPN users in this group. ACS can visit his political profile: If the user in the 'VPN users' group, access ACS.
When we connect from a VPN Client to the server, all users connect to success. When you see the parser in ACS journal, each user success connect also get
error:
22040 wrong password or invalid shared secret
(pls see picture to attach it)
the system still works, but I don't know why, we get the error log.
Thanks for any help you can provide!
Duyen
Hello Duyen,
I think I've narrowed the issue. When remote access VPN using RADIUS authentication we must keep in mind that authentication and authorization are included on the same package.
Depending on your configuration, the ACS is defined as a server RADIUS (Gserver Protocol radius aaa server) and becomes the VPN Tunnel authenticated and 'authorized' on this server group:
authentication-server-group LOCAL Gserver
authorization-server-group Gserver
As noted above, the RADIUS of request/response includes authentication and authorization on the same package. This seems to be a problem of incorrect configuration that we should not set up the 'permission' in the Tunnel of the group.
Please remove the authorization under the Tunnel of Group:
No authorization-server-group Gserver
Please test the connection again and check the logs of the ACS. At this point there are only sucessful newspaper reported on the side of the ACS.
Is 'Permission-server-group' LDAP permission when authenticating to a LDAP server so to retrieve the attributes of permission on the server. RAY doesn't have the command as explained above.
I hope this helps.
Kind regards.
-
/ * Style definitions * / table. MsoNormalTable {mso-style-name : « Tabla normal » ; mso-tstyle-rowband-taille : 0 ; mso-tstyle-colband-taille : 0 ; mso-style-noshow:yes ; mso-style-priorité : 99 ; mso-style-qformat:yes ; mso-style-parent : » « ;" mso-rembourrage-alt : 0 à 5.4pt 0 à 5.4pt ; mso-para-margin : 0 ; mso-para-marge-bottom : .0001pt ; mso-pagination : widow-orphelin ; police-taille : 11.0pt ; famille de police : « Calibri », « sans-serif » ; mso-ascii-font-family : Calibri ; mso-ascii-theme-font : minor-latin ; mso-fareast-font-family : « Times New Roman » ; mso-fareast-theme-font : minor-fareast ; mso-hansi-font-family : Calibri ; mso-hansi-theme-font : minor-latin ; mso-bidi-font-family : « Times New Roman » ; mso-bidi-theme-font : minor-bidi ;}
/ * Style definitions * / table. MsoNormalTable {mso-style-name : « Tabla normal » ; mso-tstyle-rowband-taille : 0 ; mso-tstyle-colband-taille : 0 ; mso-style-noshow:yes ; mso-style-priorité : 99 ; mso-style-qformat:yes ; mso-style-parent : » « ;" mso-rembourrage-alt : 0 à 5.4pt 0 à 5.4pt ; mso-para-margin : 0 ; mso-para-marge-bottom : .0001pt ; mso-pagination : widow-orphelin ; police-taille : 11.0pt ; famille de police : « Calibri », « sans-serif » ; mso-ascii-font-family : Calibri ; mso-ascii-theme-font : minor-latin ; mso-fareast-font-family : « Times New Roman » ; mso-fareast-theme-font : minor-fareast ; mso-hansi-font-family : Calibri ; mso-hansi-theme-font : minor-latin ; mso-bidi-font-family : « Times New Roman » ; mso-bidi-theme-font : minor-bidi ;} Hi I need to estimate the time of installation and configuration of addresses IP of Cisco (Cisco IPS NM at 3800, 2811, 2821 and no. 2851).
In your experience, would you give this information?
Thanks for any help you can give on this subject.
You are welcome. If things are clear please mark it as answered.
-
Configure to integrate Cisco ASA and JOINT
Hello
We have Cisco ASA and JOINT, need assistance on the integration of the same thing; Please email me so that I'll share the details of the architecture.
Thank you best regards &,.
REDA
Hi reda,.
If I correctly your diagram, you do not want to send any traffic from the external switch to the JOINT with a SPAN port and all traffic from your DMZ interfaces with another.
Is this correct?
If so, can you tell me why you want to inspect the traffic before it goes through the firewall? As I said in my original answer, we generally advise putting IP addresses after the firewall.
Not to mention that in your case, I guess that some traffic will be inspected twice so you will need to assign a different virtual sensors to each JOINT internal interfaces to ensure that the same instance does not see the traffic of several times.
Kind regards
Nicolas
-
Hello
I wonder if it is possible to have a configuration in IPSEC tunnel, in which one side of the tunnel is configured with static VTI and the traditional second with crypto-map.
If so, how the configuration on the crypto-Map site should be configured.
Thank you in advance for an answer.
Concerning
Lukas
Lukasz,
This config is impractical for several reasons.
VTI dictates that a "any any" proxy set ID is negotiated. While this works well on a virtual interface, where routing can push traffic to a specific interface, it will make ALL traffic is encrypted on crypto maps side and expect all traffic is encrypted when it is recived (because crypto card is part of ECAS in the Lane exit).
A more practical approach in the world of Cisco is multi SA DVTI, where a DVTI can put end to any kind of insider tunnel (i.e. allow us DVTI to manage several SAs under a virtual interface) it works very well in some cases.
You can have DVTI on your end and allow the clients to use almost anything (from ASIT cryptographic maps).
I'll shoot you as an email at the same time, a bit stuck on something at the moment.M.
-
2 one-Site VPN Cisco 2801 and with crossing NAT
Hi guys,.
I would like to configure two Cisco 2801 using IPSEC/IKE. Both routers are connected to the internet through DSL lines. The DSL line have RFC1918 address side LAN where routers connected to the internet face. I can do NAT on DSL modems.
Cisco IOS 2801 routers allow to configure site-2-site VPN with NAT crossing?
Here is a model of physics/IP configuration:
LAN<->2801 Modem DSL<-Internet->DSL modem<-Priv ip-=""> 2801<-Priv ip-=""><-> LAN
Thank you
Gonçalo
Yes, you're good to go only if one or both of the sites has an IP address which is natted with private IP address statically. The implementation of IPSec on SRI NAT support in most crosses so that shouldn't be a concern
-
Cisco 2600 router as an IPSec client
Hello
Currently I use a Cisco VPN client software to connect to a remote server for IPSec on the workstations.
I want to set up the IPSec client on Cisco 2600 router that connects to the remote server IPSec so that workstations can access subnet VPN without using VPN software.
Can someone guide me on how to configure the IPSec client on the router?
Thank you
Hi Adam,.
Sorry for my late reply, I'm a little sick.
I have checked the logs and did small repro. For me, it seems that the server does not support NEM:
It is disabled with NEM VPN server:
Nov 30 00:13:56 [IKEv1 DEBUG]: Group = gsa3mle3, name of user = cisco, IP = 10.10.10.2, MODE_CFG: request received for the DHCP for DDNS hostname is: R1!
Nov 30 00:13:56 [IKEv1]: Group = gsa3mle3 username = cisco, IP = 10.10.10.2, material Connection Client rejected! Network Extension mode is not allowed for this group!
The customer:
* 1 Mar 00:45:56.387: ISAKMP: (1007): lot of 10.10.10.13 sending my_port 500 peer_port 500 (I) CONF_ADDR
* 00:45:56.439 Mar 1: ISAKMP (0:1007): received 10.10.10.13 packet dport 500 sport Global 500 (I) CONF_ADDR
* 1 Mar 00:45:56.439: DGVPN:crypt_iv after decrypt, its: 650BE464
7BCF116E8E4DFF6C
* 00:45:56.443 Mar 1:
* 00:45:56.443 Mar 1: ISAKMP: content of the packet of information (flags, 1, len 92):
* 00:45:56.447 Mar 1: HASH payload
* 00:45:56.447 Mar 1: delete payload
* 00:45:56.459 Mar 1: ISAKMP: content of the packet of information (flags, 1, len 80):
* 00:45:56.459 Mar 1: HASH payload
* 00:45:56.459 Mar 1: delete payload
* 1 Mar 00:45:56.459: DGVPN: crypt_iv after encrypting, its: 650BE464
Change it to client mode and try it.
Kind regards
Michal
-
Router Cisco SSL VPN Configuration
Hello support.
A question concerning this scenario.
One of our clients has currently SSLVPN enabled for remote users and I was wondering if there is anyway to configure a remote Cisco router to connect via IPSEC at this endpoint SSLVPN? the idea is simply to set up the tunnel without requiring changes on my end of customers.
Thanks in advance.
Ivan Chacon
Hello
IPSEC and SSLVPN are 2 different configurations, there is no way to have a router configured for IPSec and connect to another without changing this end as well. You can run IPSec and SSLVPN on the same router, however.
There are a lot of IOS Lan to Lan configuration guides, or if you want the router to act as a client, are looking to make EZVPN.
HTH
-Jason
-
Cisco Unity Express Configuration 8.6
We have a Router (3945) CME with CUE 8.6 8.6 (ISM-SRE-300-K9 Module). I have a few concerns about the installation and configuration of CUE.
- Cisco ships CUE 8.6 Application preinstalled on ISM-SRE-300-K9 Module?
- What is the initial state of CUE in ISM-SRE-300-K9 Module when he left?
- To restore CUE setting factory and download/install CUE from scratch?
- OR can I directly give the IP interface addresses and go directly to the CUE - GUI?
- As I ordered three languages (Arab Saudi, British and English North American) these language packs are available with in the Module when it was shipped? or do I have to download and install?
ISM-SRE-300-K9 Module (ISM) internal services with Services ready engine CON-SAU-ISRE300 SW UPGR + SUPP APP internal Services Module (ISM) with SRE SCUE-ISM-8, 6 - K9 Cisco Unity Express version 8.6 CUE-LANG-ARA Cisco Unity Express - Saudi Arabic CUE-LANG-EN Cisco Unity Express - British English CUE-LANG-ENU Cisco Unity Express - North American English FL-CUE-MBX-5 Unity Express license - 5 mailboxes - CUCM and CUCME FL-CUE-IVR-2 Unity License Express - Session 2 IVR FL-CUE-PORT-2 Unity License Express - 2 ports FL-CUE-NR-PORT-2 Unity Express license 2 - no hostable re - Port I have recently installed one of these modules and my experience has been that unit has not come with any software installed. I had to download and install the software/language packs of cisco.com.
-
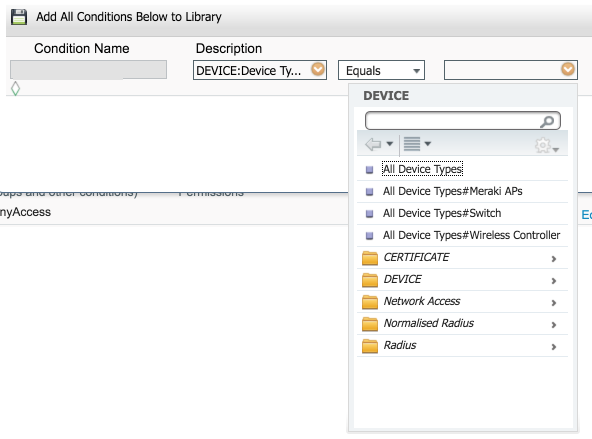
I am very new to Cisco ISE and Meraki. I try to get the Radius configuration for wireless authentication. When I do a test of the Meraki to ISE, it passes.
When I try to connect from my laptop, I look at the logs of the Radius and it passes; However, it does not connect me to good policy. I keep hitting the default policy. I have my Meraki police above the default policy in the strategy defined in article. I have attached what looks like my strategy game.
Devices does not really matter. Here is what I see when I create a device group (where you add the access point to this group), and then create the condition:
And here is where I create the condition of strategy game and you should be able to select the Meraki access points:
This will give you the condition similar to what I posted above. This is perhaps why you aren't hit that is not matching the condition for this game.
-
Cisco ACS GANYMEDE + AAA can be activated for telnet to Cisco 600 and 700 routers?
Unfortunately you can not configure radius AAA or Ganymede in routers series 600 or 700.
-
HSRP between Cisco 4321 and Cisco 887VA
Hi all
I am looking to install the following and I was wondering if anyone could answer a few questions I have.
Installation program:
- A subsidiary, our ISP gives us 20/100 leased line and ADSL circuit use for failover.
- We plan to connect the line leased to a Cisco 4321 or a G2 Cisco 2921/2951
- We intend to connect the ADSL circuit to the Cisco 887VA G2
- We will have a pair of HA of the ASA firewall 5506 x connected routers (be it via a dedicated L2 switch or a VLAN on a switch L3).
- The LAN is sitting behind the firewall.
We want to run BGP on both routers (the one that connects to the leased line and ADSL line) and configure them as a pair of HSRP/VRRP, while if the leased line LAN users cannot always access internet and you connect to the main office through a VPN S2S which ends on the firewall. BGP will be used to announce our public subnet to the ISP
Questions
- Can a 4321 and a 887VA form an HSRP/VRRP pair as they are running IOS XE and IOS?
- How much RAM and Flash is recommended on each router for BGP?
Thanks in advance for your time.
Ranil
Hello
Can a 4321 and a 887VA form an HSRP/VRRP pair as they are running IOS XE and IOS?
This isn't a problem, it will work between two routers
How much RAM and Flash is recommended on each router for BGP?
Flash is only an isuse to the size of an image, both routers should have enough speace in support of the default image size
800 s cannot support full BGP table they can not handle cpu or ram and 4321 same with 8 GB of ram can fight a bit with full table, you plan on reducing what is learned inform your ISP regarding prefixes? route map and prefix filtering?
the leased line is 100 to download 20 upward, 4321 media and aggregate of 50 - 100mps may need to get the 100mpbs for her performance / request
http://www.Cisco.com/c/dam/en/us/products/collateral/routers/4000-series...
-
Help setting up a laboratory at home using Cisco kit and a blank Superhub

Hello world
I just started my CCENT class and so I try to create a laboratory that is separate from my LAN House, initially using a blank Superhub and a Cisco 1841 router. Please keep in mind that I am a beginner, so it may not make sense or be completely illogical...
The superhub for those who don't know, is a renamed netgear, limit VMDG480. It's basically a cable modem and router wireless combined.
The normal daily LAN side of the network was the default installation to receive an IP address via DHCP from the superhub in range 192.168.0.1/24.
At first, I thought I could put things in preparation for my lab installation, by configuring the LAN subnet using 192.168.0.0 and superhub of/16 mask rank for my 'everyday' network and 192.168.1.0 rank for my "laboratory at home." (Good or bad?...)
Unfortunately, I'm unable to do so because the superhub only allows the last byte in the mask to be changed, so I changed the mask and it now reads 255.255.255.128, with the idea that I can always have 2 separate networks.
In the photo above you can see devices on the right side are all directly related to the superhub and continue to work as usual.
On the left side is where I've implemented a Cisco 1841 router and a laptop computer to test.
The details of each device are;
Blank Superhub
LAN:192.168.0.1
The DHCP scope: 192.168.0.2 - 192.168.0.126Cisco 1841
Fast Ethernet 0/1: 192.168.0.126
255.255.255.128Fast Ethernet 0/0: 192.168.0.129
255.255.255.128PC2 (mobile wired connected to FE 0/0)
IP: 192.168.0.200
255.255.255.128
Default gateway: 192.168.0.126 (the address IP of Cisco 1841)Someone would be kind enough to look at this and tell me where I'm wrong please?
I thought about pulling the superhub completely, but I am bound to her by my ISP :(
Hello
It of a little early in your studies for this :) but implementation of your knees it should work:
1841 router:
int fa0/0 (interface connected to the hub)
IP 192.168.0.126 255.255.255.0
NAT outside IP
No tapint fa0/1.2
encapsulaton dot1q 2
IP 172.16.0.1 255.255.0.0
IP nat inside
No tapint fa0/1 (interface connected to)
No tapNAT configuration:
access-list 1 permit 172.16.0.0 0.0.255.255
IP nat inside source list 1 interface fa0/0 overloadAdd a default route:
IP route 0.0.0.0 0.0.0.0 192.168.0.1 (so your router knows where to forward DNS queries to 8.8.8.8)Connect your 3560 to the second port on the router and configure a trunk on the switch port and add vlan 2:
int fa0/0 (connected to the 1841 router)
switch to trunk encapsulation dot1q
mode trunk switchVLAN 2
name Home_LabConnect your PC to the second switchport and add vlan2:
int fa0/1
access mode switch
access switch vlan 2
No tapFinally, give your PC an address in the subnet of vlan 2:
IP: 172.16.0.2
Mask: 255.255.0.0
Gateway: 172.16.0.1
DNS: 8.8.8.8You should be able to ping the address of the router on the subnet in 172.16.x.x 192.x.x.x. I don't have a Virgin hub to test this, but it worked well with two 1841 routers.
-
AnyConnect configuration using IPSec
I have configured our ASA 8.4 (7) running for the client AnyConnect (using IPSec). It prompted me to create an identity certificate when you run the VPN Wizard, I did. We use AAA to authenticate, so I not create a CA. It must in any case for AnyConnect? When I try to connect from a client AnyConnect prédéployée, I get an error: "untrusted certificates VPN server. If I ignore and choose Connect in any case, the connection fails. What Miss me?
Thank you
In addition to VPN IPsec IKEv2, there is a bit of customer service that runs when you first connect. which is used to check the version of the package AnyConnect and distribute changes in the customer profile (and some more obscure things). 'S done it via SSL and that these uses of certificate of the ASA to validate the server. If your client does not trust the certificate, you will get the error.
You can disable the service the customer by changing the default command:
Crypto ikev2 activate out of service the customer port 443
Just read
Crypto ikev2 allow outside
The best way is to enable and configure the ASA with an appropriate certificate of trust.
Maybe you are looking for
-
Qosmio F50 - bright/Fucntion keys do not work after update BIOS buttons
OK... I read a similar post and has FACT EXACTLY what IT SAID TO DO... He solved half of the problem or less... after the update to the new bios that I'd like speed or make my Qosmio energy gave me problem from the first day I installed it... The rea
-
WhatsApp is not compatible with iOS 6.1.6
Hello Today I bought an iPod Touch 4th generation (iOS 6.1.6) a friend. I'll install some applications of my "Purchased" in my iTunes account section. When I get Whatsapp and move a little box pops up saying: it is not supported with this iPhone. I g
-
2012 Foundation Server license compliance
The server has not completed the compliance audit of the licenses. If the server is joined to a domain, make sure that the server can connect to a domain controller. If the license compliant check cannot be performed, the server will automatically st
-
Original title: print a Document How can I install a printer in the menu printing. What to do when he says: a spooler problem.
-
I would like to delete a software that is said about a network resource where I can find the "Windows Cleanup" to remove it?