DVTI
Hello
I don't understand why I can't connect to DVTI. I made the simplest configuration to connect VPN between ASIT and DVTI and it works no-someone ' could you please explain what this is?
I have the router (IP 1.1.1.1) R1 and R2 (IP 2.2.2.1) router
Configuration of R1:
crypto ISAKMP policy 10
BA aes 192
preshared authentication
Group 5
key encryption isakmp address 0.0.0.0 0.0.0.0
Crypto ipsec transform-set set2 ah-sha-hmac
Crypto ipsec profile vi
Set transform-set set2
interface Tunnel0
172.16.0.1 IP address 255.255.255.0
source of tunnel Serial0/0
tunnel destination 2.2.2.1
ipv4 ipsec tunnel mode
Profile of protection vi ipsec tunnel
interface Serial0/0
IP 1.1.1.1 255.255.255.252
IP route 0.0.0.0 0.0.0.0 Serial0/0 10
Configuration of R2:
crypto ISAKMP policy 10
BA aes 192
preshared authentication
Group 5
key encryption isakmp address 0.0.0.0 0.0.0.0
Crypto isakmp vi profile
default keychain
function identity address 0.0.0.0
virtual-model 2
Crypto ipsec transform-set set2 ah-sha-hmac
Crypto ipsec profile vi
Set transform-set set2
the vi isakmp profile value
interface Loopback0
172.16.0.2 IP address 255.255.255.0
interface Serial0/0
IP 2.2.2.1 255.255.255.252
tunnel type of interface virtual-Template2
IP unnumbered Loopback0
ipv4 ipsec tunnel mode
Profile of protection vi ipsec tunnel
IP route 0.0.0.0 0.0.0.0 Serial0/0 10
ASIT tunnel rises, virtaul-access Interface arrives also and as a result of configuration:
interface virtual-Access2
MTU 1514
IP unnumbered Loopback0
tunnel source 2.2.2.1
tunnel destination 1.1.1.1
ipv4 ipsec tunnel mode
Profile of protection vi ipsec tunnel
No ipsec tunnel protection initiate
end
R2 receives all R1 IPsec traffic, but there is no response from R2. The only point that I see it, is that R2 na not create a reverse route to R1.
THX
Dmytro,
Somrthing like this works for me:
DVTI:
Peering2_961 #sh run virtual int-model 1
Building configuration...
Current configuration: 158 bytes
!
type of interface virtual-Template1 tunnel
IP unnumbered Loopback0
source of tunnel Serial0/0
ipv4 ipsec tunnel mode
Tunnel PRO ipsec protection profile
end
Peering2_961 # run HS | s crypto
Crypto pki token removal timeout default 0
crypto ISAKMP policy 10
BA aes
preshared authentication
Group 2
address of cisco key crypto isakmp 0.0.0.0 0.0.0.0
ISAKMP crypto PRO profile
default keychain
function identity address 0.0.0.0
virtual-model 1
Crypto ipsec transform-set TRA aes - esp esp-sha-hmac
Crypto ipsec profile PRO
game of transformation-TRA
Set PRO isakmp-profile
Peering2_961 #sh passage int se0/0
Building configuration...
Current configuration: 178 bytes
!
interface Serial0/0
IP 172.16.0.2 255.255.255.252
IPv6 2001:DB8:BB:2 address / 126
transfer of bgp MPLS
MPLS protocol ldp label
MPLS ip
series 0 restart delay
end
Peering2_961 #sh run int l0
Building configuration...
Current configuration: 69 bytes
!
interface Loopback0
223.255.255.1 the IP 255.255.255.255
end
Peering2_961 # run HS | s r r
Peering2_961 # run HS | s r RIP
router RIP
version 2
network 11.0.0.0
network 223.255.255.0
No Auto-resume
ASIT:
Peering1_960 # run HS | s crypto
Crypto pki token removal timeout default 0
crypto ISAKMP policy 10
BA aes
preshared authentication
Group 2
address of cisco key crypto isakmp 0.0.0.0 0.0.0.0
Crypto ipsec transform-set TRA aes - esp esp-sha-hmac
Crypto ipsec profile PRO
game of transformation-TRA
Peering1_960 #sh run int tu0
Building configuration...
Current configuration: 167 bytes
!
interface Tunnel0
IP unnumbered Loopback0
source of tunnel Serial0/0
ipv4 ipsec tunnel mode
tunnel destination 172.16.0.2
Tunnel PRO ipsec protection profile
end
Routing on DVTI:
Peering2_961 #sh ip route
(... omitted...)
11.0.0.0/8 is variably divided into subnets, 3 subnets, 2 masks
R 11.0.0.0/24 [120/1] via 223.255.255.0, 00:00:12, Access2-virtual
C 11.1.1.0/24 is directly connected, Loopback100
L 11.1.1.1/32 is directly connected, Loopback100
172.16.0.0/16 is variably divided into subnets, 2 subnets, 2 masks
C 172.16.0.0/30 is directly connected, Serial0/0
The 172.16.0.2/32 is directly connected, Serial0/0
223.255.255.0/32 is divided into subnets, 2 subnets
R 223.255.255.0 [120/1] via 223.255.255.0, 00:00:12, Access2-virtual
C 223.255.255.1 is directly connected, Loopback0
Ping test:
Peering2_961 #sh crypto ipsec his | I have caps | ident
local ident (addr, mask, prot, port): (0.0.0.0/0.0.0.0/0/0)
Remote ident (addr, mask, prot, port): (0.0.0.0/0.0.0.0/0/0)
#pkts program: 41, #pkts encrypt: 41, #pkts digest: 41
#pkts decaps: 33, #pkts decrypt: 33, #pkts check: 33
Peering2_961 #ping 223.255.255.0 re 1000
Type to abort escape sequence.
Sending of 1000, 100-byte ICMP echoes to 223.255.255.0, time-out is 2 seconds:
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!.
Success rate is 99 percent (525/526), round-trip min/avg/max = 20/36/52 ms
Peering2_961 #sh crypto ipsec his | I have caps | ident
local ident (addr, mask, prot, port): (0.0.0.0/0.0.0.0/0/0)
Remote ident (addr, mask, prot, port): (0.0.0.0/0.0.0.0/0/0)
#pkts program: 569, #pkts encrypt: 569, #pkts digest: 569
#pkts decaps: 561, #pkts decrypt: 561, #pkts check: 561
Tags: Cisco Security
Similar Questions
-
Hello
in fact I situation as mentioned further and I am confused about design and implement what VPN topology, I choose DMVPN, GETVPN or DVTI
I have 4 branch and 1 main site, branches have 2 connectivity to HQ a via INTERNET one another through MPLS, so I want to have Fail-over on the links and also secure two-way tunnel
Best regards
John Mayer
GETVPN is not supposed to be used on the internet. If this isn't the solution.
With this small amount of sites I set up static VTI on MPLS and use DVTIs on the internet if the branches have dynamic IPs. If the branches also have the static IP, I re also these links with the stuffy VTI.
DMVPN could also be used in this scenario, but the protocol overhead is not necessary in this small scale scenario.
-
DMVPN, deny traffic to the satellite mission
Hello
Maybe it's a weird qeustion but im DMVPN test with several scenarios.
At the moment I have 1 Hub with 4 spoke, they all work properly. We test it because we have a lot of customers who do not have a fixed IP address to the outside, then an IP address changes each time, you have to configure VPN to our headquarters all over again. DMVPN appears as a perfect solution...
Now my goal is to configure the DMVPN of all customers (speaks) at our headquarters. But I don't want guests to have access to our local network and nor, I want to have access to the other satellite mission. The only one who has full access allowed to all LAN's headquarters (Hub).
What is the best way to achieve this? I started working with access lists or can I do it with EIGRP somehow? And make the ACL on the tunnels or the ethernet interfaces?
Or maybe DMVPN is not the best solution? All comments and advice ar worm appreciated!
Thanks already,
Bart
In this scenario, you use the better the VTI/DVTI tunnels. On the Hub, you can accept any peers with the DVTI-config VPN. The rays use traditional VTI-tunnels. The virtual model on the hub (which is used to build the-access-virtual interfaces by talk can be configured with a value by default-ACL (deny an ip) and CBAC firewall rule that inspects your outgoing traffic to allow packets back.) You can even use the zone based firewall, but this seems an exaggeration in this configuration.
Sent by Cisco Support technique iPad App
-
Pool of dhcp NAT VPN to the LAN on router 2911
I need nat the ips assigned by dhcp vpn to my LAN pool. My problem is that I do not know which interface to set my nat statement on since there is no interface that is in the same subnet as my dhcp pool. Any help would be appreciated.
For remote client ipsec, you must have DVTI according to configuration described here:
http://www.Cisco.com/en/us/docs/iOS/12_3t/12_3t14/feature/guide/gtIPSctm...
'use ip nat inside' on the virtual model and 'ip nat outside' on the inside of the interface.
HTH
Averroès.
-
Problem with IKEv2 routes w using PSK and RADIUS
Hello
I have a 7 881 + (15.2 (4) M2) connected to a 1001 ASR (03.07.01.S) via the Internet. The goal is to set up DVTI on the ASR, use FlexVPN on the CPE and inject crypto IKEv2 itineraries in the VRF on the EP for subnets protected on the SCE when using pre-shared key for authentication and RADIUS to return the attributes.
I can get the tunnel works fine, but I can't get the cryptographic routes.
My configs:
7 881 + CPE:
Crypto ikev2 keyring Keychain-CPE
peer ASR
address
pre-shared key abcd
!
Profile of crypto ikev2 IKEV2-PROFILE-CPE
match one address remote identity
255.255.255.255 identity local fqdn cpe.ipsec.net
sharing front of remote authentication
sharing of local meadow of authentication
Keyring key chain local-CPE
DPD 30 2 periodic
!
Crypto ipsec transform-set esp - TFS-AES256-SHA-HMAC-aes 256 esp-sha-hmac
tunnel mode
!
by default the crypto ipsec profile
game of transformation-TFS-AES256-SHA-HMAC
profile ikev2 IKEV2-PROFILE-CPE
!
Crypto ikev2 client flexvpn FLEX
Peer 1
Customer inside Loopback0
customer connect Tunnel0
!
interface Loopback0
IP 255.255.255.255
!
interface Tunnel0
the negotiated IP address
source of tunnel Dialer2
ipv4 ipsec tunnel mode
dynamic tunnel destination
tunnel protection ipsec default profile
PE OF THE ASR:
Authorization group to the network IPSEC-AUTHOR of AAA AAA-GROUP-IPSEC-RADIUS
!
Crypto ikev2 60 2 dpd periodicals
!
Profile of crypto ikev2 IKEV2-PROFILE-ASR
corresponds to fvrf FVRF
match identity fqdn remote domain ipsec.net
sharing front of remote authentication
sharing of local meadow of authentication
Keyring aaa IPSEC-AUTHOR
AAA authorization user psk IPSEC-AUTHOR list
virtual-model 1
!
Crypto ipsec transform-set esp - TFS-AES256-SHA-HMAC-aes 256 esp-sha-hmac
tunnel mode
!
by default the crypto ipsec profile
game of transformation-TFS-AES256-SHA-HMAC
the value of RADU ikev2-profile
answering machine only
!
type of interface virtual-Template1 tunnel
no ip address
source of tunnel GigabitEthernet0/0/3
ipv4 ipsec tunnel mode
tunnel vrf FVRF
tunnel protection ipsec default profile
Definition of RADIUS user name:
CPE. IPSec.net
Tunnel-Password = abcd,
Framed-IP-Address = 172.16.0.254,
Box-IP-Netmask = 255.255.255.254,
Cisco-avpair = "ip:interface - config = vrf forwarding test",
Cisco-avpair = "" ip:interface - config = address ip 172.16.0.255 255.255.255.254 ","
Cisco-avpair = 'ipsec:route - value = interface',
Cisco-avpair = "ipsec:route - value prefix =
32", Cisco-avpair = "ipsec:route - accept = any"
The tunnel interface is coming on the CPE, the virtual access interface is implemented on the ASR. I could use BGP to Exchange routing between EP and CPE information, but I want to use IKE.
I think the problem is because I don't know how to call a permission policy IKEv2 on PBS (in which I could set up a list of access for the
). But on the CPE, I have the following limitations: I want to use PSK for authentication, but no RADIUS server is available. So, the only other option for PSK authentication is a Keyring set locally, as there is no way to use a user name defined locally (local authentication) with a set of keys.
So how can I trigger an IKEv2 authorization under the profile of IKEv2 policy?
CPE (config-ikev2-profile) list of psk #aaa user authorization?
The WORD AAA list name
If I set a local aaa authorization list, then all authentication fails:
AAA authorization network default local
Profile of crypto ikev2 IKEV2-PROFILE-CPE
by default the AAA user psk authorization list
* 15:52:27.042 Dec 20 UTC: IKEV2-3-NEG_ABORT %: negotiation failed due to the ERROR: exchange Auth failed
And there is no way to trigger that the authorization policy if I do not set the command above, is not it? I tried to modify the authorization policy by default with access list, but it is not taken into account.
If I use a card with an access-list and IKEv2 encryption, I can get directions crypto on the ASR. But I want to use FlexVPN on the CPE.
Is there a way to do this?
Also the IOS configuration guides are not too useful
Thank you
Radu
. "09:12:42.299 Dec 21 UTC: IKEv2:IKEv2 local AAA asks author ' 87.84.214.31 '.
. "09:12:42.299 Dec 21 UTC: IKEv2:IKEv2 local AAA - political ' 87.84.214.31 ' does not exist.
. 09:12:42.299 Dec 21 UTC: authorization IKEv2:IKEv2 162 error
Not sure how resembles your config, but here it says that it cannot find
ikev2 crypto 87.84.214.31 permission policy
<...>
If it is configured?
-
Ezvpn client unable to route to the Internet via UC540
Hello
I have a UC540 configured as a server Ezvpn. I can connect to a Cisco VPN client and connect all private addresses, register the IP communicator etc. However when I try to connect to the web using a web browser it does not connect.
The client receives the server's DNS entries. I also tried to use the IP address instead of the DNS name and still able to connect on the Internet only. It is a complete tunnel split. I tried checking the box in the VPN client to make a tunnel of split and still unable to connect. Guests on the main site (directly connected to the UC540) can connect to the Internet fine, it's just through the Ezvpn, they can't. The subnet Ezvpn is included in the nat ACL.
Any advice would be appreciated.
Andy
Andy,
What is the legacy or the deployment DVTI?
If inherited, you can create a fake loopback (with 'ip nat inside') and punt ezvpn subnet to it with a road map.
If DVTI can you please make sure you have 'ip nat inside' on the interface?
Running config would help ;-)
Marcin
-
EZVPN 861 connects but sees no VPN network
Hi all
I've been hitting my head against the wall on a question and I'd love to help if possible. I am a recent CCENT and beginner on cisco VPN. I have set up my 851w running ios c850-advsecurityk9 - mz.124 - 15.T11.bin using the CCP without any problem. Then I started the installation program of the Cisco 861 running ios c860-universalk9 - mz.150 - 1.M3.bin the same way. I used the CCP to configure EZVPN server for client connections. Customers connect properly and work the first time. If I try to connect a second time then it will authenticate and connect but I get no access to the internal private network. Split tunnel seems to work very well I can access the internet, but I can't ping the internal router or access anything whatsoever on the VPN. If I do a reload of the router, it works the first time and then not the second time. Please, someone tell me that sounds familiar.
Thanks for any help.
It is probably hitting this bug
CSCth39861
 road IPP may not be added to the RT (DVTI configuration)
road IPP may not be added to the RT (DVTI configuration)makes duplication with the
CSCta53372
 static route RRI disappears from the Routing No./tap-tap interface on table
static route RRI disappears from the Routing No./tap-tap interface on table -
Lost comunication in VPn tunnel after session claire encryption
Hello!
EzVPN with DVIT.
Everything works (it has communication with remote local networks, I can ping) up to this I type:
Claire crypto his
After this command, the tunnel is restarted, the tunnel is UP, but the communication does not come back (I can't ping inside).
on, client and server, I have
invalid-spi-recovery crypto ISAKMP
ISAKMP crypto keepalive 10 periodicalsWhat is the code for the server EZVPN are you with DVTI? You can go on this bug.
Try to reload the zone and see if the tunnel back upwards once and issue the command erase again and see if the IPP disappears.
-
Hello
I was wondering if it was possible to use CRYPTOGRAPHY even for both: DMVPN and CLIENT IPsec?
To make it work, I have to use 1 crypto for the DMVPN and 1 crypto for IPsec, both systems operate on the same router, my router TALK can connect to my HUB router and my computer can connect to the router "HUB" via an IPsec tunnel.
Is their any way to make it easier, instead of doing configs in a single router for more or less the same work?
My stitching question may be stupid, sorry for that, I'm still learning, and I love it
Here below the full work DMVPN + IPsec:
Best regards
Didier
ROUTER1841 #sh run
Building configuration...
Current configuration: 9037 bytes
!
! Last configuration change to 21:51:39 gmt + 1 Monday February 7, 2011 by admin
! NVRAM config last updated at 21:53:07 gmt + 1 Monday February 7, 2011 by admin
!
version 12.4
horodateurs service debug datetime localtime
Log service timestamps datetime msec
encryption password service
!
hostname ROUTER1841
!
boot-start-marker
boot-end-marker
!
forest-meter operation of syslog messages
logging buffered 4096 notifications
enable password 7 05080F1C2243
!
AAA new-model
!
!
AAA authentication banner ^ C
THIS SYSTEM IS ONLY FOR THE USE OF AUTHORIZED FOR OFFICIAL USERS
^ C
AAA authentication login userauthen local
AAA authorization groupauthor LAN
!
!
AAA - the id of the joint session
clock time zone gmt + 1 1 schedule
clock daylight saving time gmt + 2 recurring last Sun Mar 02:00 last Sun Oct 03:00
dot11 syslog
no ip source route
!
!
No dhcp use connected vrf ip
DHCP excluded-address IP 192.168.10.1
DHCP excluded-address IP 192.168.20.1
DHCP excluded-address IP 192.168.30.1
DHCP excluded-address IP 192.168.100.1
IP dhcp excluded-address 192.168.1.250 192.168.1.254
!
IP dhcp pool vlan10
import all
network 192.168.10.0 255.255.255.0
default router 192.168.10.1
lease 5
!
IP dhcp pool vlan20
import all
network 192.168.20.0 255.255.255.0
router by default - 192.168.20.1
lease 5
!
IP dhcp pool vlan30
import all
network 192.168.30.0 255.255.255.0
default router 192.168.30.1
!
IP TEST dhcp pool
the host 192.168.100.20 255.255.255.0
0100.2241.353f.5e client identifier
!
internal IP dhcp pool
network 192.168.100.0 255.255.255.0
Server DNS 192.168.100.1
default router 192.168.100.1
!
IP dhcp pool vlan1
network 192.168.1.0 255.255.255.0
Server DNS 8.8.8.8
default router 192.168.1.1
lease 5
!
dhcp MAC IP pool
the host 192.168.10.50 255.255.255.0
0100.2312.1c0a.39 client identifier
!
IP PRINTER dhcp pool
the host 192.168.10.20 255.255.255.0
0100.242b.4d0c.5a client identifier
!
MLGW dhcp IP pool
the host 192.168.10.10 255.255.255.0
address material 0004.f301.58b3
!
pool of dhcp IP pc-vero
the host 192.168.10.68 255.255.255.0
0100.1d92.5982.24 client identifier
!
IP dhcp pool vlan245
import all
network 192.168.245.0 255.255.255.0
router by default - 192.168.245.1
!
dhcp VPN_ROUTER IP pool
0100.0f23.604d.a0 client identifier
!
dhcp QNAP_NAS IP pool
the host 192.168.10.100 255.255.255.0
0100.089b.ad17.8f client identifier
name of the client QNAP_NAS
!
!
IP cef
no ip bootp Server
IP domain name dri
host IP SW12 192.168.1.252
host IP SW24 192.168.1.251
IP host tftp 192.168.10.50
host IP of Router_A 192.168.10.5
host IP of Router_B 10.0.1.1
IP ddns update DynDNS method
HTTP
Add http://dri66: [email protected] / * *//nic/update?system=dyndns&hostname=mlgw.dyndns.info&myip=[email protected] / * //nic/update?system=dyndns&hostname=mlgw.dyndns.info&myip=
maximum interval 1 0 0 0
minimum interval 1 0 0 0
!
NTP 66.27.60.10 Server
!
Authenticated MultiLink bundle-name Panel
!
!
Flow-Sampler-map mysampler1
Random mode one - out of 100
!
Crypto pki trustpoint TP-self-signed-2996752687
enrollment selfsigned
name of the object cn = IOS - Self - signed - certificate - 2996752687
revocation checking no
rsakeypair TP-self-signed-2996752687
!
!
VTP version 2
username Admin privilege 15 secret 5 $1$ gAFQ$ 2ecAHSYEU9g7b6WYuTY9G.
username cisco password 7 02050D 480809
Archives
The config log
hidekeys
!
!
crypto ISAKMP policy 3
BA 3des
preshared authentication
Group 2
!
crypto ISAKMP policy 10
md5 hash
preshared authentication
ISAKMP crypto cisco123 key address 0.0.0.0 0.0.0.0
!
ISAKMP crypto client configuration group 3000client
key cisco123
DNS 8.8.8.8
dri.eu field
pool VPNpool
ACL 150
!
!
Crypto ipsec transform-set strong esp-3des esp-md5-hmac
Crypto ipsec transform-set esp-3des esp-sha-hmac RIGHT
!
Profile cisco ipsec crypto
define security-association life seconds 120
transformation-strong game
!
!
Crypto-map dynamic dynmap 10
Set transform-set RIGHT
!
!
map clientmap client to authenticate crypto list userauthen
card crypto clientmap isakmp authorization list groupauthor
client configuration address map clientmap crypto answer
10 ipsec-isakmp crypto map clientmap Dynamics dynmap
!
!
!
property intellectual ssh time 60
property intellectual ssh authentication-2 retries
IP port ssh 8096 Rotary 1
property intellectual ssh version 2
!
!
!
interface Loopback0
IP 192.66.66.66 255.255.255.0
!
interface Tunnel0
172.16.0.1 IP address 255.255.255.0
no ip redirection
IP mtu 1440
no ip next-hop-self eigrp 90
property intellectual PNDH authentication cisco123
dynamic multicast of IP PNDH map
PNDH network IP-1 id
No eigrp split horizon ip 90
source of tunnel FastEthernet0/0
multipoint gre tunnel mode
0 button on tunnel
Cisco ipsec protection tunnel profile
!
interface FastEthernet0/0
DMZ description
IP ddns update hostname mlgw.dyndns.info
IP ddns update DynDNS
DHCP IP address
no ip unreachable
no ip proxy-arp
NAT outside IP
IP virtual-reassembly
automatic duplex
automatic speed
clientmap card crypto
!
interface FastEthernet0/0,241
Description VLAN 241
encapsulation dot1Q 241
DHCP IP address
IP access-group dri-acl-in in
NAT outside IP
IP virtual-reassembly
No cdp enable
!
interface FastEthernet0/0.245
encapsulation dot1Q 245
DHCP IP address
IP access-group dri-acl-in in
NAT outside IP
IP virtual-reassembly
No cdp enable
!
interface FastEthernet0/1
Description INTERNAL ETH - LAN$
IP 192.168.100.1 address 255.255.255.0
no ip proxy-arp
IP nat inside
IP virtual-reassembly
Shutdown
automatic duplex
automatic speed
!
interface FastEthernet0/0/0
switchport access vlan 10
spanning tree portfast
!
interface FastEthernet0/0/1
switchport access vlan 245
spanning tree portfast
!
interface FastEthernet0/0/2
switchport access vlan 30
spanning tree portfast
!
interface FastEthernet0/0/3
switchport mode trunk
!
interface Vlan1
IP address 192.168.1.250 255.255.255.0
IP nat inside
IP virtual-reassembly
!
interface Vlan10
IP 192.168.10.1 255.255.255.0
IP nat inside
IP virtual-reassembly
!
interface Vlan20
address 192.168.20.1 255.255.255.0
IP nat inside
IP virtual-reassembly
!
Vlan30 interface
192.168.30.1 IP address 255.255.255.0
IP nat inside
IP virtual-reassembly
!
interface Vlan245
IP 192.168.245.1 255.255.255.0
IP nat inside
IP virtual-reassembly
!
Router eigrp 90
network 172.16.0.0
network 192.168.10.0
No Auto-resume
!
IP pool local VPNpool 172.16.1.1 172.16.1.100
IP forward-Protocol ND
no ip address of the http server
local IP http authentication
IP http secure server
!
IP flow-cache timeout idle 130
IP flow-cache timeout active 20
cache IP flow-aggregation prefix
cache timeout idle 400
active cache expiration time 25
!
!
overload of IP nat inside source list 170 interface FastEthernet0/0
overload of IP nat inside source list interface FastEthernet0/0.245 NAT1
IP nat inside source static tcp 192.168.10.10 80 interface FastEthernet0/0 8095
!
access-list 150 permit ip 192.168.10.0 0.0.0.255 172.16.1.0 0.0.0.255
access-list 170 refuse ip 192.168.10.0 0.0.0.255 172.16.0.0 0.0.0.255
access-list 170 refuse ip 192.168.10.0 0.0.0.255 172.16.1.0 0.0.0.255
access-list 170 permit ip 192.168.10.0 0.0.0.255 any
access-list 180 deny ip 192.168.10.0 0.0.0.255 172.16.1.0 0.0.0.255
access-list 180 permit ip 192.168.10.0 0.0.0.255 any
not run cdp
!
!
!
route NAT allowed 10 map
corresponds to the IP 180
!
!
!
control plan
!
exec banner ^ C
WELCOME YOU ARE NOW LOGED IN
^ C
connection of the banner ^ C
WARNING!
IF YOU ARE NOT:
Didier Ribbens
Please leave NOW!
YOUR IP and MAC address will be LOGGED.
^ C
!
Line con 0
Speed 115200
line to 0
line vty 0 4
access-class 5
privilege level 15
Rotary 1
transport input telnet ssh
line vty 5 15
access-class 5
Rotary 1
!
Scheduler allocate 20000 1000
end
Didier,
Some time ago, I wrote a bit on VT, you should be able to find information about the server ezvpn DVTI it.
The configuartion you have right now is the way to strives for ezvpn, with the new way DMVPN (protection of tunnel).
If it is true for the most part, it is best to go on the learning curve Moose and go everythign new configuration.
With EZVPN you can always assign IP from the pool by group ezvpn or external authorization ;-)
Anyway let me know if you face any problems.
Marcin
-
Easy VPN with the Tunnel Interface virtual IPSec dynamic
Hi all
I configured easy vpn remote on a cisco 1841 and dynamic server easy vpn with virtual tunnel interface on the server (cisco 7200, 12.4.15T14)
It works with easy vpn remote to the client mode and mode network-extesión, but it doesn't seem to work when I configure mode plus network on the client of the cpe, or when I try to have TWO inside the ez crypto interfaces. On the customer's site, I see two associations of security, but on the server PE site only security SA!
Without virtual dynamic tunnel interface, dynamic map configuration is ok... This is a limitation of the virtual tunnnel dynamic interface?
Federica
If one side is DVTI and the other uses a dynamic map, it does support only 1 SA. If the two end uses DVTI or the two end uses dynamic card then it supports several SAs.
Here is the note of documentation for your reference:
Note: Multiple inside interfaces are supported only when the Cisco Easy VPN server and the Cisco Easy VPN client have the same type of Easy VPN configuration. In other words, both must use a Legacy Easy VPN configuration, or both must use a DVTI configuration.
Here's the URL:
Hope that answers your question.
-
Hello
I wonder if it is possible to have a configuration in IPSEC tunnel, in which one side of the tunnel is configured with static VTI and the traditional second with crypto-map.
If so, how the configuration on the crypto-Map site should be configured.
Thank you in advance for an answer.
Concerning
Lukas
Lukasz,
This config is impractical for several reasons.
VTI dictates that a "any any" proxy set ID is negotiated. While this works well on a virtual interface, where routing can push traffic to a specific interface, it will make ALL traffic is encrypted on crypto maps side and expect all traffic is encrypted when it is recived (because crypto card is part of ECAS in the Lane exit).
A more practical approach in the world of Cisco is multi SA DVTI, where a DVTI can put end to any kind of insider tunnel (i.e. allow us DVTI to manage several SAs under a virtual interface) it works very well in some cases.
You can have DVTI on your end and allow the clients to use almost anything (from ASIT cryptographic maps).
I'll shoot you as an email at the same time, a bit stuck on something at the moment.M.
-
Hello
I had two 1841 and a router cisco 881. I keep one of this router to HO and remaining at the branch. I have a static internet IP to HO but dynamic IP at the branch.
I want to configure a VPN to connect to HO branch through router. The branch connects via an IP private use of the internet. What VPN is the safer and better for it.
Kind regards
Mero
This is a typical scenario for dynamic virtual Tunnel Interfaces (DVTI):
http://www.Cisco.com/en/us/partner/docs/iOS/12_3t/12_3t14/feature/guide/gtIPSctm.html#wp1027258
--
Don't stop once you have upgraded your network! Improve the world by lending money to low-income workers:
http://www.Kiva.org/invitedBy/karsteni -
Cisco VTI and configuration of IPSec (IKE Phase2) ITS proposal.
Hello
I have a question about the functionality of the virtual Tunnel Interface (VTI) configuration option. I have a Cisco IOS router, ending individual customers with the tunnel interfaces. The question I have now is that how can I specify the traffic 'interesting' on the security association proposal ITS IPsec (IKE Phase2). The configuration of the router is made by cryptographic profiles like this:
!
crypto ISAKMP policy 10
BA 3des
preshared authentication
Group 2
!
Crypto isakmp ISAKMP_PHASE1_PARAMETERS profile
key ring PRESHARED_KEYS
function identity address 1.2.3.4 255.255.255.255
!
door-key crypto PRESHARED_KEYS
pre-shared key address 1.2.3.4 key xyz
!
Crypto ipsec transform-set esp-3des esp-sha-hmac VPN-TRANSFORMSET
!
Profile of crypto ipsec ISAKMP_PHASE2_TUNNEL
game of transformation-VPN-TRANSFORMSET
PFS group2 Set
ISAKMP_PHASE1_PARAMETERS Set isakmp-profile
!
Tunnel1 interface
IP 10.10.10.1 255.255.255.252
IP mtu 1450
source of tunnel Loopback1
tunnel destination 1.2.3.4
ipv4 ipsec tunnel mode
Tunnel ISAKMP_PHASE2_TUNNEL ipsec protection profile
!
Now when I look at the output of the command 'See the crypto ipsec his tu1 int' I get the following:
....
Interface: Tunnel1
Tag crypto map: x.x.x.x addr Tunnel1-head-0, local
protégé of the vrf: (none)
local ident (addr, mask, prot, port): (0.0.0.0/0.0.0.0/0/0)
Remote ident (addr, mask, prot, port): (0.0.0.0/0.0.0.0/0/0)
current_peer 1.2.3.4 port 500
LICENCE, flags is {origin_is_acl},
....
However, the peer on the other side do not accept the proposal, as it would like to have specific IP subnets on the IPSec security association proposal parameters. He would accept the policy if the identity local remote proxies, for example, would be 192.168.10.0/255.255.255.0/0/0 (local) and
192.168.200.0/255.255.255.0/0/0 (remotely).
Y at - it 'interesting' no IOS configuration for traffic configuration option on the profile of crypto? With the crypto map - basic configuration you can specify interesting traffic with an ACL under the crypto map configuration section.
I'm in IOS version 15.1 (4) M with Advanced IP Services have together.
Hello
ASIT will always want to negotiate a whole as traffic selectors.
What you MIGHT find is multi-SA DVTI configuration, in what remote end could say what proxy identity he would like to encrypt. (Supported from 15.2 M / T)
Unfortunately, the ceveat of this configuration is this remote end needs to open the negotiation.
M.
-
I'm standing, a site with an L2L connection, but needs to vpn client host connections as well. I know that you can do with old good crypto cards, but it is not the preferred method these days with the virtual Tunnel Interfaces? Trying to figure out the best method to deal with. Links and guidance appreciated.
Hi Robert,.
To be honest, today the best recommendation is to run AnyConnect instead of the legacy IPsec client.
In the case where you would need to run the IPsec client, it doesn't really matter if you use a virtual interface or not, given that from the point of view of the VPN client functionalilty is the same.
I would recommend simple card crypto for a simple connection to a router not to treat many types of VPN as DMVPN, VTI, DVTI connections, etc.
However, if you want to get more familiar with DVTI, then I suggest this link:
Cisco Easy VPN with IPSec configuration dynamic Tunnel Virtual Interface (DVTI)
Remember that the configuration of a box of equipment or software is pretty much the same thing on the VPN server.
With a card encryption:
So as you can see the configuration of the client is the same on the server:
crypto isakmp client configuration group vpngroup key cisco123 dns 10.10.10.10 wins 10.10.10.20 domain cisco.com pool ippool acl 101
What really changes is to use if a card encryption or a VTI.
It will be useful.
Portu.
Please note all useful posts
Post edited by: Javier Portuguez
-
Recovery site - redundant VPN peers
Hello all, thank you in advance for your expertise.
We put in place a recovery site disaster that will host the redundant copies of our servers and critical data in Kansas City. When disaster strikes, our headquarters site would be totally gone.
We currently have 7 locations that communicate to our HQ via VPN tunnels (whether on a circuit of the Internet or on a circuit of Cox Communications Ethernet WAN). Branch sites each can an ISR of Cisco 2821 router. At Headquarters and on the DR site, we use a Cisco ASA 5510 to terminate VPN tunnels and do everything that our column spinal routing. Routing on the ASA and branch routers is all static, using a routing protocol would be a nice update in the future... any ideas? We use IPSEC VPN lan lan tunnels 2, no GRE/VPN is used because it is not terminated by the ASA.
What is the best way to configure my routers for branch to automatically or manually failover to connect to one ASA different site of DR?
In addition, if my seat is still in place, but either my Internet or Cox headquarters ethernet circuit breaks down. How can I re - route all traffic in a loop to the seat on the right remains a circuit?
Is there a better way to do what I want to accomplish? BGP is not an option at this point due to its complexity.
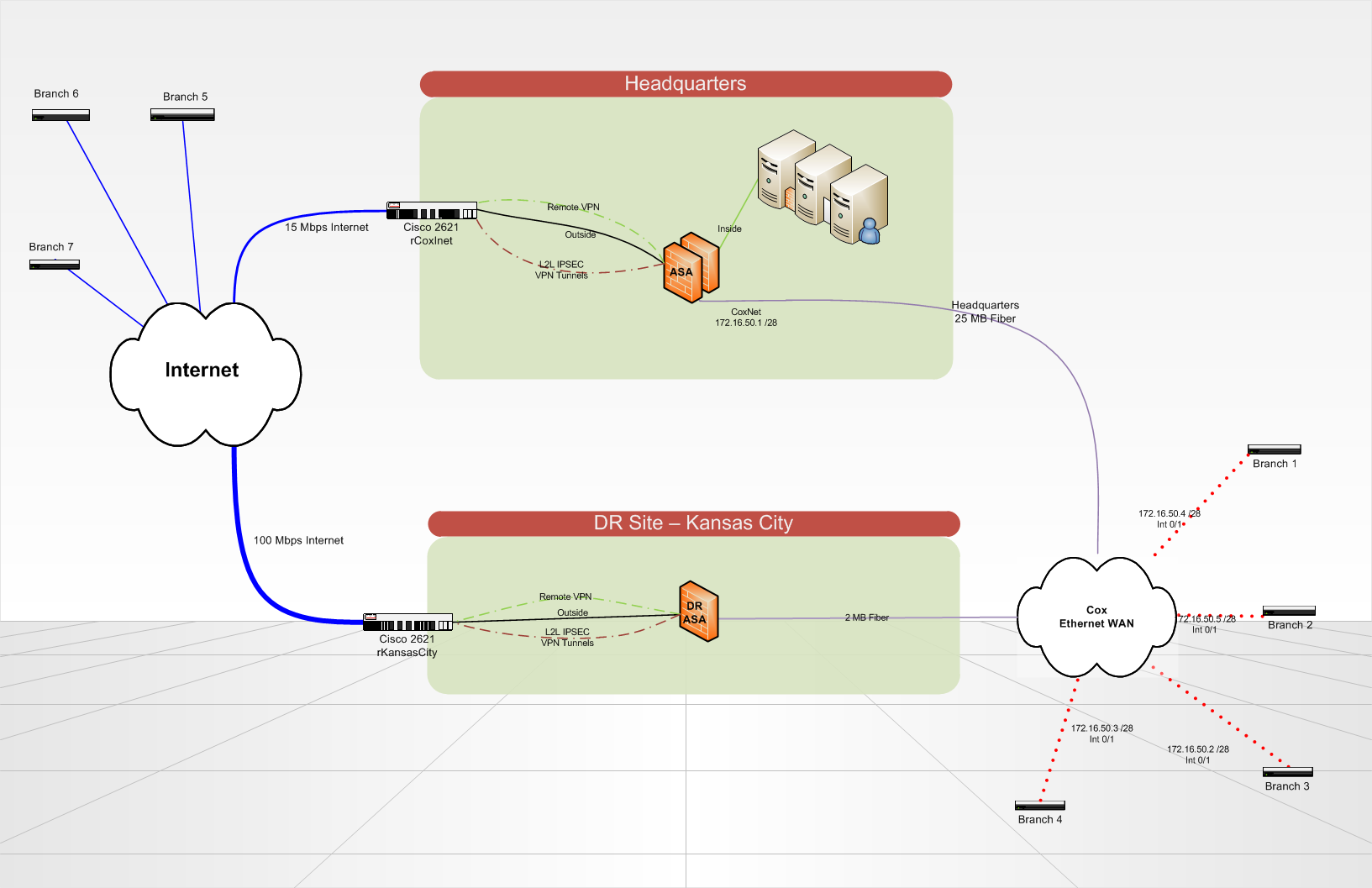
Lucas,
To circumvent the two point separately.
The best way to provide active / standby time of reundancy is preferred peer in cryptographic cards (on the ISR routers).
You can choose to establish VPN to HQ and only if HQ is not aid you to DR, when HQ is you will EVENTUALLY return to it.
The answer to share of your questions may also be the preferred option by peers (and several counterparts in a crypto map entry).
This being said, you can try to send OSPF traffic to IPsec tunnel (and using the neighbor command to avoid the manipulation of mcast in pure IPsec).
Docs:
HTH,
Marcin
P. S.
If you want my personal opion, chaning ASAs in HQ and DR sites and put you in routers could make DMVPN or DVTI-ASIT scenario which gives you a lot more features ;-)
Maybe you are looking for
-
Woke up to find that my Firefox has been automatically updated to Ver 6 +.The usual questions have emerged, with a few plugins not working do not. The annoying thing is Adobe flash player.I downloaded the latest version of the Flash player and instal
-
Mavericks 10.9.5 is compatible with Office for Mac 2016?
If I run Mavericks 10.9.5, it works with Office for Mac 2011, Office for Mac 2013 and Office for Mac 2016? Or what I need to upgrade to one of these versions of Office? A Microsoft 360 subscription is required to run Office for Mac 2016 or one of its
-
Problem connecting wirelessly with Windows XP
I broke out an old computer and was about 6 years old, updates to do. now that those who are in fact, can't the Wi - Fi to connect to save my life. I messed around online looking for a solution and have yet to find one. It seems that my problem has t
-
laptop stuck on the spinning circle during the upgrade to windows 8.1
Hello. I have a HP pavilion g6 and today I tried to update windows 8 to 8.1, and he spent the screen where it says put in place 1%... 2 %... Etc... Thereafter it restarted when he hit 100% and now its deadlock on the rotation circle thing. The only t
-
Back to height of GroupItem selected
I'm trying to get the selected GroupItem, and simply return the height of this selection. I am able to get all the GroupItems under an activeLayer, but failed to get the specific GroupItem was selected.