General Vpn
I have a few questions general VPN...
(1) when the hub has Transparent NAT - IPsec over UDP and IPsec over TCP enabled to support both, one who is a priority?
The UDP is by default on the client... None?
(2) if another administrator logs on the hub while I (an admin) already logged, what are the permissions should be I'm already on? Read/write or just read because an admin is already connected as two administrator accounts are allowed read/write.
Hello
(1) on UDP ISPEC is a priority.
(2) the second admin will have only read access.
Thank you
Sujit
Tags: Cisco Security
Similar Questions
-
Hello
I looked at some sites today on how to set up a vpn anyconnect for a basic 5506-x license.
So far, I have found this site
https://networklessons.com/security/Cisco-ASA-AnyConnect-remote-access-VPN/
Inside, they ask for contributions, and I do not give sites randomly my number of credit card debt for obvious reasons. I just want to know what they block that I can't see. If I know that he trusted I could rethink give them money but for now I don't trust them.
If you know a guide like this next to the Cisco white paper, answer him in return.
Hello
Anyconnect configuration is the same regardless of the license you have so that you can follow any documentation out there to set it up. I saw some videos on youtube on how to do it. ASDM has also an Anyconnect installation wizard it will take 2 minutes to do following the wizard I don't think that you must pay on a website for an example of configuration, cisco documentation is very detailed check it will explain the process of the ASDM Wizard:
http://www.Cisco.com/c/en/us/support/docs/security/AnyConnect-secure-mob...
Best regards, please rate.
-
General VPN router configuration
Hello experts,
I need to connect to a VPN with my router cisco a Cisco Asa version 7.2
I need advice to see if this configuration looks like just because I'm confused with the phases 1 & 2:
Phase 1 - required
Encryption PROTOCOL: IPSEC
VARIOUS - HELLMAN: GRUPO2
Encryption algorithm: 3DES
Hash: SHA
Lifetime: 86400 SECONDS
MODe: HAND
-I have configured:
key, testkey address 1.1.1.1 crypto ISAKMP xauth No.
crypto ISAKMP policy 21
BA 3des
preshared authentication
Group 2
* sha does not appear because I read that it is default
battery life does not appear
----------------------
Phase 2 - required
Encapsulation: ESP
Encryption: 3DES
Authentication: SHA
PFS: group2
Life expectancy: 8 hours
LIfetimeKB: 4608000
-I have configured:
Crypto ipsec transform-set esp-3des esp-sha-hmac test
17 3desmap of ipsec-isakmp crypto map
defined peer 1.1.1.1
Set transform-set test
PFS group2 Set
match the address acltest
My questions:
1. Transform-set phase is 2?
2. where can I configure the lifetime of 8 hours?
Thank you
the game of transformation is the phase 2 (and the isakmp policy is phase 1).
You can set the duration of life under the isakmp policy. I believe you can leave it as, and during the negotiation if the two peers differ on periods of life, she should choose the smallest value.
-
How to enable VPN on iphone 4?
Hello all, in fact I installed a vpn application on my iphone but after when I went to the
The iPhone settings, I found their vpn option in settings > general > vpn, so now I want to know who
How does the iphone vpn is - even as the applications available on the store for the iphone and how to configure
I have no idea what to do what should I fill in the vpn options available when we try
TO enable vpn on iphone?
VPN:
A virtual private network (VPN) extends a private network by a public network such as the Internet. It allows users to send and receive data on shared or public networks as if their computing devices were connected directly to the private network, and benefit the functionality, security and private network management policies. [1] A VPN is created by connecting virtual point to point through the use of dedicated connections, virtual, tunneling protocolsor encryptionof traffic.
Wikipedia
Better find you the developer's Web site and see what they can do with their application.
-
Hi I'm new Anyconnect VPN. These are fundamental questions. The first step to set up the vpn is download image. What is this image? I noticed that the configuration of the VPN does not contain some general vpn configuration steps such as crypto isakmp policy and crypto ipsec etc. Maybe the image contains all of this information? If so, how to get the image? Thank you
IPsec is not a kind of SSL. It's a total different encryption mechanism.
IPsec uses pre-shared keys (almost always) and is so symmetric cryptography (the two peers have the same "secret"). Until there are 4-5 ears it was predominant VPN technology and is still widely used, particularly in site-to-site VPN connections.
SSL uses a PKI (PKI) with a private key ('secret') not shared between peers and therefore asymmetric. More new remote access VPN in recent years are based on SSL. SSL does not use lines of configuration of ipsec crypto or crypto isakmp but instead relies on certificates and trustpoints.
Complicating the landscape there is a new safer type of VPN IPsec is IKEv2. It is not widely adopted in my experience, but is increasingly used by organizations and agencies who need to comply to strict government standards.
-
VPN traffic via a secondary access provider
Hello world
I have been asked by a client to implement this topology:

where:
ISP 1 is used as primary internet connection.
2 ISP will be used to connect remote users by IPsec VPN.
Currently, I'm not looking for the Active/Backup feature, I need to know if I can use both ISP connections (as I've written before) an ISP for the Internet company and the other for the user remote access VPN.
I read some post where, said, it's possible, but I want to be sure.
Kind regards
Jose
ASA must add the static route in the routing table automatically when the VPN client is connected. So, in general, you don't need to do anything. But if not, you can just manually configure who will forward a VPN client IP packet to ISP2.
With respect to NAT, in general, VPN traffic must ignore the NAT. You can use "nat (inside_interface_name) 0-list of access ' with an ACL that define the vpn traffic to do so.
-
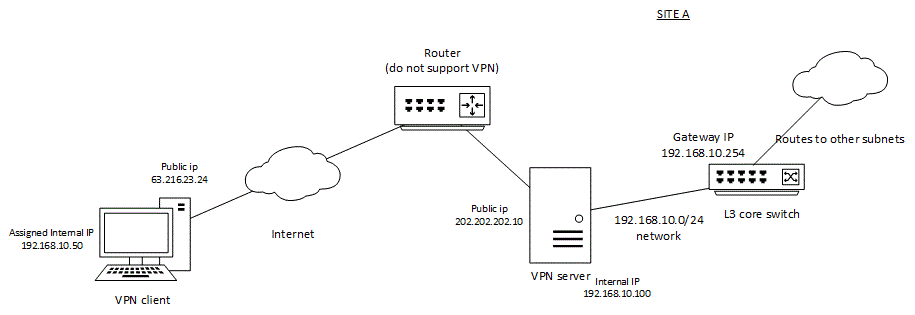
VPN on a general plan to understand for a beginner.
Hi all
This question is not really particularly related to any Cisco VPN / Firewall product.
But I really hope to seek clarification with regard to the general operation of a tunnel VPN gurus here...So here we go...
I understand that (the encryption side), VPN tunnels incorporates real source and destination of a packet network with the public internet address (for example the internal network) between the VPN client and the VPN server.
For example, the site has, I would have a private 192.168.10.0/24 network and I wish that connections of A site VPN clients part of the 192.168.10.0/24 network. The gateway for this network is a coreswitch L3 - 192.168.10.254 who will be roads and then to other resources/internal network.
As shown in my picture below, I have an internet router that does not support VPN, so I have to configure a different VPN behind her with a public IP address
My question is->
If there is a road to install in my VPN client with
192.168.4.0 255.255.255.0 192.168.10.254
Which means my package of 'internet' is always sent to the VPN server and the VPN server can "unpack" it and "transmit" to the IP Address of the gateway of the coreswitch - 192.168.10.254 L3?
e.g. embedded package from computer VPN client
[src] [dest] [load]
[192.168.10.50] [192.168.4.3] [icmp]
final package
[public CBC] [public dest] [software package]
[63.216.23.24] [202.202.202.10] [192.168.10.50] [192.168.4.3] [ICMP]
T1) what I wanted to say, that is, the final package is sent via the internet to the VPN (202.202.202.10) server, how does the VPN server, can continue to transfer the package to the L3 gateway then? Surely she needed a right sort of ability to transmission and routing?
In general how, the embedded package does get sent to the VPN server, then to the L3 switch-> to the desired destination 192.168.4.3?
- or - what I need to Setup/assign a separate subnet together VPN for the VPN client and the VPN server; and the gateway for VPN client for all other internal networks will be for the VPN server (and not the coreswitch L3), with the server VPN with roads to another network internal with the L3 coreswitch instead?
Kind regards
NoobYes.Participation in this forum is a voluntary activity and often work day will be pre-empting of quick answers.
There is 'something like' a table in a session. In fact, a set of security IPsec Associations (SAs) as the VPN device uses to keep track of the remote clients connected.
It represents for the networks being the that these customers are on the device itself (even if they are actually remote) then that traffic from VPN clients and the local subnets will never see the VPN itself as a device in the path (for example, via the output of traceroute)
-
Web VPN/SSL - general Split Tunnel capable?
When I look through some examples of configuration for IOS Web VPN - it seems you attract to the filling of a web page of web sites that users can go to. I would be rather thin client act as client light 4.x CVPN - divided for example tunnel with access to a resource internal resource. Is this possible with Cisco VPN Web? Also - with is WebVPN any ability of the NAC?
I'm not sure IOS SSL vpn, but on the asa webvpn, there is a complete client ssl option. With this, you can either create a tunnel, or all split tunnel and the only defined networks. I hope that answers your question.
-
VPN inside a PIX (General Questions)
Hello
I'm trying to implement a scenario of communication between a customer inside a pix that talks to a server on the outside. The customer must have an ipsec inside connection. I have the following config and a few questions I´d be very happy to get an answer for...
Backup on the interface outside the security0 Server
Client safety within 100 interface
The client IP address is 200.200.212.194
backup server address is 200.200.202.201
I want to implement a VPN client connection to the inside interface, and therfore have implemented the following configuration.
external IP 200.200.202.200 255.255.255.0
IP address inside 200.200.212.193 255.255.255.192
access-list 100 permit host 200.200.202.201 ip 10.3.3.0 255.255.255.0
IP local pool privada 10.3.3.1 - 10.3.3.254
Crypto ipsec transform-set esp-3des esp-sha-hmac RIGHT
Crypto-map dynamic dynmap 10 transform-set RIGHT
map mymap 10-isakmp ipsec crypto dynamic dynmap
client configuration address map mymap crypto initiate
client configuration address map mymap crypto answer
mymap map crypto inside interface
ISAKMP allows inside
ISAKMP key * address 0.0.0.0 netmask 0.0.0.0
ISAKMP identity address
part of pre authentication ISAKMP policy 10
ISAKMP policy 10 3des encryption
ISAKMP policy 10 sha hash
10 2 ISAKMP policy group
ISAKMP life duration strategy 10 86400
vpngroup address private pool PRIVADAGROUP
PRIVADAGROUP vpngroup password *.
vpngroup split tunnel 100 PRIVADAGROUP
I have a few questions about this configuration maybe some kind soul able to respond.
1. the VPN clients receive an address (10.3.3.1) for example through the IKE negotiation. When I ping my server from the client with the active VPN tunnel I assume the real package that passes through the wire has 10.3.3.1 a source address and a destination of 200.200.212.193 (endpoint the VPN and inside interface). Within IPSEC, the package is my real ip with a source 200.200.212.194 address (address of the real client) and a destination address of 200.200.202.201 (address of the backup server that I am trying to ping). If all this makes sense and is correct could you confirm the following point.
2 when the PIX deencrypts the package and removes the IPSEC header I find myself with my IP packet of origin with a source 200.200.212.194 address (address of the real client) and a destination address of 200.200.202.201 (address of the backup server that I am trying to ping). I don't know if I need then the following configuration to allow the package to be transferred to the backup without NAT server:
access-list allowed sheep host ip 200.200.212.194 255.255.255.0 200.200.202.0 255.255.255.0
NAT (inside) 0 access-list sheep
I was previously using the following configuration and it seemed to work but the more I think the less sense it seems to do as I´d wait for the SENATE to run on the dencypted package. I must be missing something or confused, or both.
IP 10.3.3.0 allow Access-list sheep 255.255.255.0 200.200.202.0 255.255.255.0
NAT (inside) 0 access-list sheep
3. as a last and probably least I m pretty sure I don't have to line "isakmp key * address 0.0.0.0 netmask 0.0.0.0" when connecting with a VPN client software only. Somone can confirm that for me.
I'm actually trying to get this to work remotely with someone else doing the actual work and we don't speak the same language.
Any help to store my confused brain would be appreciated.
1. No, it's the other way around. The real package that passes through the wire has the address IP of the PC (200.200.212.194) as a source. Within the IPSec packet is allocated 10.3.3.1 as source IP address. When the PIX decrypts the packet, the outer header is removed, and the package has a source of 10.3.3.1 as it is sent to your server on the outside. The external server will respond to 10.3.3.1 so it must be routed to the PIX for her to work.
Think of this as the normal instance with the PC to the outside through the Internet. A package from of and sent to 10.3.3.1 would never do to the original PC. The encrypted IPSec packet always contains the VPN endpoints real IP source and destination addresses. The decrypted original deck contains allocated as source IP and the actual destination as destination (usually also a private address) computer.
2. This should make more sense now that you know the answer to 1.
3. you don't need that if you have a "vpngroup password xxxx" command. This command «isakmp key...» "If there is no specific vpngroup key, or someone connects with a different groupname.
-
VPN - question of General design for a ut of a router tunnel more
Hello
We have a router that has VPN connections with different partners of our company. VPN remote access were used on computers that are connecting to the different partners of our company.
There has been problems of this kind, that is to say put on both a watchdog and a customer vpn cisco router led to blue-screens on the PC.
The current idea is to put different tunnels from site to site on the router (default gateway of PC clients that connect to the partners). My question is... How our PC to get DHCP addresses on networks of visitors, once the tunnels are up? I guess I'm alittle confused about the address for the PC on our side how will work.
Thanks for your help.
Divide the pool of ip from the internal network, you're going to visit. for example the document below will be exaplain the same configuration in user mode.
-
Tips to add a VPN router to my current network configuration
Dear all
My apologies if the answer to this question already exists, however, I searched in many situations and none seem to match what I'm after.
I currently have an ISP modem/router in Bridge mode connected to a TC of Apple which is my wireless router, I have 2 Express airport connected to this acting as the extensors of the range. I have a VPN service through the MyPrivate network I activate on the desired device when required and everything works fine.
What I want to do now is to be able to use my AppleTV and burning Amazon via the VPN as well so you need to add a VPN router in the configuration. I want to finish with 2 wireless networks running together for these devices who need VPN and those who are not. I don't want to lose the opportunity to extend the network to express it however airport.
If someone could explain to me if this is possible and if so how do I set up the network.
Thanks in advance
Mark
Basically you would need a device that supports VPN-passthrough and VLANS for your goals of networking. MyPrivate network, seems to be a VPN SSL, which is a user-server configuration. In other words, you install a client VPN on your Mac and you connect to the VPN network MyPrivate server to establish a VPN tunnel.
Networking two or more "separated", should be using a router that supports VLAN services. Each segment of VIRTUAL local area network, in essence, would be a separate, she either wired or wireless network or a combination of both. This would probably be the 'easiest' part for the installation program.
Now how combining the two would be the question, and I don't know what would be the best way, or even if it is possible.
A few thoughts:
- Use a router that supports VLANS. Create at least two VIRTUAL LAN segments. One for Apple TV & Burns, one for Internet access in general. Connect the device to VPN client host on the first segment, and configure for Internet sharing.
- Download a dedicated VPN network application that supports hosting of third-party VPN clients, like yours. You would still need a router that supports VLAN to provided separate network segments.
- Hire a consultant network. Let them know what you the goals of networking and ask them to offer potential solutions.
-
VPN using hotspot with ios 10 does not
I often work off site and use my iPhone AT & T s 6 to attach my work Windows 10 Pro (processor ASUS T300CHI) Tablet. Although many places I work have Wifi, most only allow VPN I need to connect to my work server. After updating ios 10 (I'm on 10.0.1), I did have problems engaging, but VPN doesn't work anymore.
VPN integrated Windows 10 Pro on my Tablet has an automatic configuration that appears to detect the type of configuration (IKEv2/IPSec/PPTP/L2TP, etc.) and you just put in user name and password. According to my dept IT, the VPN connection in the office not only supports PPTP (I understand has been disabled with ios 10) but also supports IKEv2 and L2TP/IPSec. Nevertheless, I always left configuration VPN on Windows 10 in auto. I tried selecting the connection type, but it did not work either. Generally I get the error "failure of VPN tunnels.
Any thoughts would be appreciated
MattyBH,
Please keep us informed if you were able to solve this problem. I also have the same problem since the update iOS10. I think it has to do with Apple, removing the IOS10 PPTP protocol... I was able to confirm the conclusion of downgrading to previous IOS 9.3 and my VPN works very well, unfortunately my users with iPHONE7 cannot sink their IOS and now can not access VPN through hotspots iOS10
-
VPN connection error - pppd limited
Hi I think I have a problem with OX, the captain and the networks, I sail perfectly with the team but since update stops running the VPN, I tried the possibility to go to recovery mode to 'disable csrutil' then ' sudo chmod u + s / usr / sbin / pppd "but it does not work when you use Netextender or FortiClient." I have another Mac with Lion and works properly the only difference I notice in the file 'pppd' Captain makes me 'limited, compressed' and only 'compressed' Lion I put a photo and a newspaper of netextender:
15/09/2016 10:15:59.271 [603 General info] NetExtender 8.1.788 for Mac OS X initialized
15/09/2016 path of the bundle app NetExtender 10:15:59.299 [General info 603] = /Applications/NetExtender.app
15/09/2016 createLogPanel() 10:16:01.045 [gui info 603]
15/09/2016 10:16:01.730 [config info 603] loading saved profiles...
15/09/2016 10:16:16.507 [connect info 603] user: "prueba".
15/09/2016 10:16:16.507 [connect info 603] domain: "abcd.hos."
15/09/2016 10:16:16.509 [connect info 603] Server: 'vpn.abcd.es:444 '.
15/09/2016 10:16:16.581 [603 general notice] connection to vpn.abcd.es:444...
15/09/2016 10:16:16.820 [General error 603] ERROR: SSL_connect: Undefined error: 0 (0)
15/09/2016 10:16:16.821 [General notice 603] retry...
15/09/2016 10:16:16.822 [General error 603] ERROR: SSL_connect: Undefined error: 0 (0)
15/09/2016 10:16:16.823 [General error 603] authentication failed: connection failed. See the log for more details.
15/09/2016 10:16:16.823 [General error 603] NetExtender connection failed.
15/09/2016 10:16:16.823 [General notice 603] SSL VPN disconnect...
15/09/2016 10:16:17.058 [General error 603] ERROR: SSL_connect: Undefined error: 0 (0)
15/09/2016 10:16:17.058 [General notice 603] retry...
15/09/2016 10:16:17.060 [General error 603] ERROR: SSL_connect: Undefined error: 0 (0)
15/09/2016 10:16:17.061 [General error 603] disconnect command failed
15/09/2016 10:16:17.063 [General notice 603] SSL VPN connection is completed.
15/09/2016 10:16:17.063 [config info 603] loading saved profiles...
15/09/2016 10:16:17.065 [gui info 603] connection failed. See the log for more details.
I think that the problem is a network file or because I put the wrong password and I cannot detect this error. as I said the VPN working properly with another MAC using the same network.
Help...
You shouldn't be messing with the security features of the operating system.
Problems may have to do with the network, or client software that you use.
I start by making sure all the software are updated and then create a new entry, vpn, double control system that everything has been entered correctly.
FWIW, I use the built-in features of VPN on El Capitan to connect to my University regularly and without problem.
I'm not familiar with "Fortinet", and I suspect that you may need to be updated, or simply use the built-in VPN.
-
iOS 9.3 VPN On Demand ignores RequiredDNSServers
We have an application which works well on iOS 9.2, it uses the "RequiredDNSServers" of VPN service on demand. But when you take 9.3 (9.3 all versions, including 9.3.2 beta 4), VPN on demand just ignore "RequiredDNSServers".
"RequiredDNSServers" is an array of IP addresses that are used to resolve the specified areas. When DNS servers are unavailable, a VPN connection is established in response. However, the VPN connection should never start.
Submit a bug to apple iOS SDK team and got the answer that ' there is nothing can help Developer Technical Support, you need to connect General supported VPN that is supported by AppleCare. As I use the same mobile configuration on iOS 9.2 and 9.3 iOS but get totally opposite results. So I think there must be something wrong with iOS 9.3. Could someone help?
And I'm not the only person who has experienced this problem. Another thread here: https://forums.developer.apple.com/thread/42624
Here's a snippet of our mobile configuration.
Expected result:
When loading from google.com, it must first check for result DNS 8.8.8.8.
Actual result:
It will not ask for result DNS 8.8.8.8 and immediately start VPN connection.
- < key > OnDemandEnabled < / key >
- < integer > 1 < / integer >
- < key > OnDemandRules < / key >
- < table >
- < dict >
- < key > Action < / key >
- < string > EvaluateConnection < / string >
- < key > InterfaceTypeMatch < / key >
- < string > Wifi < / string >
- < key > ActionParameters < / key >
- < table >
- < dict >
- Areas of < key > < / key >
- < table >
- < string > < /string > www.google.com
- < / array >
- < key > RequiredDNSServers < / key >
- < table >
- < string > 8.8.8.8 < / string >
- < / array >
- < key > DomainAction < / key >
- < string > ConnectIfNeeded < / string >
- < / dict >
- < / array >
- < / dict >
- < / array >
Please do not post the same question multiple times. It can be confusing and unnecessarily tedious for everyone. When anyone can reply to your message, they will.
See you soon,.
GB
-
iPhone 6s won't connect to VPN on work wifi but goes on other wifi networks
Hello
I have been connected to my wifi to work for a while and had to use a VPN to use things such as whats'app and access to sites like Facebook. It worked well until what recently just VPN logs not when I am connected to this wifi network. I know that the password etc and I get the symbol wifi at the top of my phone but never impossible to access Web sites (which was normal, but the VPN it fixed), but now I can not connect the VPN even more.
The VPN application I use is Betternet but I've also tried a few others, none works. However, they all work when I connect to my own wifi network.
iPhone 6 s - last version of iOS from today (28 Apr 16) cannot find the exact version on my phone
Pleaseeeeee help me connect to my VPN when I'm on my work wifi
VPN can be difficult, maybe to consult Betternet. Also see this article for suggestions.
iOS: setting up VPN - Apple Support
FWIW here are some general recommendations for Wi - Fi problems, maybe one of them will help you.
(1) perform a forced reboot: hold the Home and Sleep/Wake buttons simultaneously for about 15-20 seconds, until the Apple logo appears. Leave the device to reboot.
(2) resetting the network settings: settings > general > reset > reset network settings. Join the network again.
(3) reboot router/Modem: unplug power for 2 minutes and reconnect. Update the Firmware on the router (support Web site of the manufacturer for a new FW check). Also try different bands (2.4 GHz and 5 GHz) and different bandwidths (recommended for 2.4 to 20 MHz bandwidth).
(4) change of Google DNS: settings > Wi - Fi > click the network, delete all the numbers under DNS and enter 8.8.8.8 or otherwise 8.8.4.4
(5) disable the prioritization of device on the router if this feature is available.
(6) determine if other wireless network devices work well (other iOS devices, Mac, PC).
(7) try the device on another network, i.e., neighbors, the public coffee house, etc.
(8) to restore the device (ask for more details if you wish).
https://support.Apple.com/en-us/HT201252
(9) go to the Apple Store for the evaluation of the material.
Maybe you are looking for
-
How can I access my iCloud drive to external sources?
Dear community, I would like to share a few videos and fotos on my iCloud drive with friends. This should only be for a short time, for example 1 month! How can I do this, or what I have to configure a DropBox account?
-
Pavilion 15-P216tu: could not find drivers for HPP Pavilion 15-P216TU
Hello Unfortunately, this is my first time with HP note book that. I'm really a fan of Dell & Apple... their site is very useful. Comes to drivers... I can't find any driver this laptop on your generous HP website. He said simply that "we never could
-
System off: 69539635 What is the password of the bios? Thank you
-
Hello! You could tell me please what is the maximum memory size for the laptop and what type of faster memory modules can be installed?I tried to find this information in the world, but without result. I want to replace the two memory modules to get
-
original title: Setup error. I want to install a program, but when I run the setup I have this error displays "an error (-5006: 0x8000ffff) occurred while runnig the Setup program." Please make sure you have finished any previous Setup and closed oth