How to implement password policies in BI 11 g?
Hi people,Can someone point me to a doc that shows how to set password policies in BI 11 g? I want to talk about things like the end of the password, the application of complex passwords etc., things like that. I understand that now in 11g, users need to be put in place through the Weblogic console, but I'm not in there, and I don't know where to go to from there.
Thank you very much
-Adam vonNieda
Hi Adam,.
Is that what you are looking for;
http://download.Oracle.com/docs/CD/E21764_01/apirefs.1111/e13952/TaskHelp/security/ConfigurePasswordValidationProviders.html
See you soon,.
Daan Bakboord
http://obibb.WordPress.com
Tags: Business Intelligence
Similar Questions
-
How to set the police custom in the BI Publisher
Hi all
I use BI publisher (5.6 Build 45) and MS word (2010) presentation of the data.
The generated pdf file must have Verdana as its police force. So I changed the font Verdana in rtf.
But when I generate pdf from this template, the police is automatically converted to Helvetica.
How can I generate pdf using Verdana as font?
Help, please.
Thank youHere's the documentation to implement external policies:
http://www.Oracle.com/technetwork/middleware/bi-Publisher/learnmore/demo-library-TOC-173301.html
Good luck!
Thank you
Pradeep -
How to implement backup-lamw script (ghettoVCBni.sh)?
Who can help me (to understand how) to implement the (page ghettoVCBni.sh) lamw backup script? Even after a lot of Googl'ing I don't know how to do this (.. newbie...). I'm currently under ESXi with 2 data warehouses the and would like to backup computer virtual from the first to the second. I guess I ran the script on the ESXi host computer but can not find a way to the place to go. I would really appreciate if someone will write a howto (small).
Thanks in advance, Edmond
1) you must enable access to the ESXi console.
Follow these instructions to do so: http://www.vm-help.com/esx/esx3i/ESXi_enable_SSH.php
2) option: if you mainly in Windows (if no, go to 3 ), open ghettoVCBni.sh in Notepad (it is asuming you have already downloaded the script of http://communities.vmware.com/docs/DOC-8760) and change:
VM_BACKUP_VOLUME = / vmfs/volumes/kevin-test-nfs-storage
in order to take into account any data store that you want to store your backups in. In your case, it would be the name of your second local data store. The data MUST have store a vmfs/volumes/above IT. Another option, you should look at is the previous backups how you want to keep for each virtual machine. This can be changed on the line:
VM_BACKUP_ROTATION_COUNT = 3
WARNING: DO NOT PRESS RETURN AFTER ALL AS notebook of LINES to the INTERIOR THAT IT CAN break INTO THE SCRIPT.
3) SCP the file ghettoVCBni.sh on the ESXi server. You can use WinSCP (user name is root, password is any password you gave ESXi) to do if you are running Windows, use something else, the *nix scp command. (for example from the source running: scp ghettoVCBni.sh [email protected]: )
4) SSH into the ESXi server using "putty" or something physically go (or use Digital KVM or other) to the ESXi console itself and log in as root.
5) make a file on the ESXi server that lists the virtual machines that you want to back up.
There are two simple ways to do so:
Has) create the file backup_vms inside the ESXi console
If you know how to use a * nix like vi text editing tool, then use it to create a text file that has all the display names for the virtual machines that you want to back up. Don't forget that there is a new line for the display name for each virtual machine.
If you don't know how to use a * nix text editing tools, the easiest (though tedious ) to do this inside the ESXi console is:
VM1 echo > backup_vms
VM2 echo > > backup_vms
VM3 echo > > backup_vms
To check your work, run: cat backup_vms
the output should look like:
~ # cat backup_vms
VM1
VM2
VM3
~ #
If it doesn't, run: rm backup_vms and start over (so note the tedious ). Someone chime if there is a way to do this without rm'ing or edit with vi.
B) create the backup_vms file it on a separate system and the SCP in the ESXi server. You must be careful, however, not use not Notepad because after each return, he will add in ^ M (where the warning at the top). It's bad. Again, you can check your work by using the cat backup_vms inside the ESXi console (after you scp it exceeds of course) to make sure there are not the weird characters.
Don't forget, the virtual machines inside the backup_vms of the file MUST be saved on the host of ESXi (i.e. existing in the inventory of the ESXi host in vi-client). In addition, it would be easier to have the ghettoVCBni.sh and backup_vms file to be in the same directory. For this document, this is assuming that you are in /. To make sure you're there, use pwd. To get there use: cd /
5) if you follow the optional step 2 then edit the ghettoVCBni.sh script using a text inside the ESXi console editor and change:
VM_BACKUP_VOLUME = / vmfs/volumes/kevin-test-nfs-storage
in order to take into account any data store that you want to store your backups in. In your case, it would be the name of your second local data store. The data MUST have store a vmfs/volumes/above IT. Another option, you should look at is the previous backups how you want to keep for each virtual machine.
This can be changed on the line:
VM_BACKUP_ROTATION_COUNT = 3
6) change permissions on script to allow execution: chmod + x ghettoVCBni.sh
7) run the script. In the case of this document: ghettoVCBni.sh backup_vms
8) sit and wait or go do something else.
These instructions also apply to the ESX ( under step 1 ). Oh yes, this script can be run on virtual machines (power) live and you don't need any additional trick to run it.
Nice day
Tuan
-
How can implement you not with Tim Capsule and AirPort their simulation on the iMac?
Hello
How can implement you not with Time Capsule and AirPort their simulation on the iMac?
I don't know what you're asking.
AirPort Extreme is a wireless router.
A Time Capsule airport is an AirPort Extreme with a built-in hard drive for data storage.
An iMac is a Mac computer.
An iMac is not a wireless router, so he is unable to perform the functions of a wireless router.
-
Even with AV software, how safe are passwords in T-bird, worried?
With the threat of the Zeus botnet and even with the AV software and vigilance for the phishing emails, how can secure passwords in TB you, if even a master password is effective only for a single session?
Surely, TB is not safe in itself against such an attack.
Comments please, Steve.Point 1. If they cannot follow, they have a problem.
Thunderbird 17 November 20, 2012
Thunderbird 24 September 17, 2013
Thunderbird 31 later in 2014I hope they can keep up with new versions of the virus, because Thunderbird is almost up to once a year.
Point 2. Thunderbird stores your e-mails on your hard disk in plain text format.
Point 3. Zeus is dead. http://www.USATODAY.com/story/news/nation/2014/06/02/global-cyber-fraud/9863977/
Point 4. Nothing will protect you against malware. Nothing less than your computing device to disconnect from the internet, all networks and all media. That's put the machine in a glass bubble. Anything that can be done is reduce the risk, not remove it. A few years ago new USB keys have been sold at retail by malware on them. How do you want to know, how would your anti virus program know, if it was the first appearance of such.
Point 5. Your data can be encrypted, there are a lot of account and there entire disk encryption products, but the data useless even to you in this State. So when you connect to your computer data is decrypted, so you can use it. Crypto locker or as happens and encrypts your data. When you disconnect from your operating system with renew your already inaccessible encrypted data encryption.
Point 6. «Please do not use the term good AV software.» Famous, yes but nothing anti virus programs we have are good. They rely on questionable heuristic engines lists value and the search for known viruses. Some of them have not been seen in the wild for 30 years and daily updates. In some cases more frequent to broadcast their new definitions to the infections.
Point 6. Thunderbird is written with security in mind. So, no support for remote images by default, no vbScript, javascript code and not Flash. All the HTML is analyzed and disinfected before reaching even to see. So the risk of read any mail is very very low. I'm sure that there is an unknown exploit here somewhere, but the 6 weekly releases of security and stability Gets the most serious closed in due course.
Point 7. Most anti programs anti-virus analyzes the flow of data, whether HTTP for the web, IMAP or POP for mail, so if your anti virus program does not only and requires some sort of program plugin, maybe you need the other.
Point 8. The biggest risk is the spare part, because they are sent as they were sent. However, to open an attachment, it must first be re-created as a file and saved in your temp folder and then executed in the same way that if you double click on a file on your desktop. If your antivirus can't find out and stop a problem either through the writing of the file, or it is later opening will be useless for this threat in any case. For what is does or does not email is irrelevant.
Point 9. I have the challenge of security on why companies e-mail Scanner even exist, the best I can get from them is "another line of defense." It's true, they are aware because their scanners residents should detect anything that arrives in the mail, the email stuff is just "another line of defense' very annoying which causes most of the problems of electronic mail. Regarding outgoing mail, that was really me. They certify your machine clean and then scan outgoing mail for, I have no idea what. Your machine is clean.
-
How we implemented personal signatures in Thunderbird?
How we implemented personal signatures in Thunderbird?
-
How to store passwords on my macbook pro so that they are secure
How to store passwords on my Macbook Pro so that they are secure? I like to keep my huge list of passwords in a document on my computer but worry they will not be secure. I have a Macbook Pro with the retina display OSX 10.9.5
Thank you
Martha
The Finder, choose utilities go to menu and use disk utility to create an encrypted drive or image if you wish, turn on FileVault.
(136891)
-
How to implement point filters fixed for FPGA
Hello!
I am applying the bandpass filter Butterworth for FPGA.
I managed to develop filters of fixed point that suits my needs, but I don't know how to implement on a table in a project after the FPGA code generation. I tried to understand it in the examples, but I was not very successful.
My time to finish what runs, any help would be really appreciated...
Any suggestions?... some examples?
Thanks in advance
I've already done that and solved the problem.
In any case thank you and have a nice day
Ljubica
-
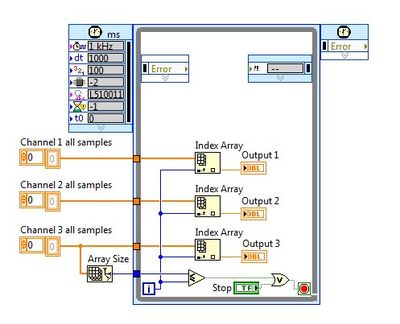
How to implement the reading of data from a matte file on a cRIO?
Hi all!
I'm still not sure, it is plausible, but I'll ask rather before you begin complicating. So far, I found no useful information on reading in the data to a device of RT from a file (type of a simulation test - data is simulated).
I have the MatLab plugin that allows the storage of data read a MAT file, which has a number of columns that represent the different signals and lines representing the samples at a time (depending on the time of the sample - sample every time has its own line of signal data).
I have no idea how to implement this at cRIO.
The idea is:
I have some algorithms running on the controller of RIO in a timed loop. As the entries of these algorithms I need to access each of the values of columns in the row, which is the time of the sample (sort of a time series - without written actual times).
I am fairly new to RT and LV development, so any help would be appreciated.
Thank you
Luka
Dear Luka!
I think the reading of all the samples in a single channel is exactly what you need here, because reading the files may take some time and is not deterministic, so it is best to read all the data in memory (or if this is not feasible due to problems of size, fairly large pieces may be sufficient). The table read can be provided and then in the loop simulating outings, something like this:
I used here separate channels so it's more graphic, but you can build all the channels in a 2D array and array index corresponding to the samples fom 1 who. You can also use for loops with indexing as tunnels are setup and then you won't need the index functions and the number of iterations is also set automatically, but you have to take care of synchronization settings.
Best regards:
Andrew Valko
National Instruments
-
How to implement the wafer map using LabVIEW?
Hello LabVIEW Masters!
I have a project which includes control and searching for information on a PROBER. One of the difficulties I have now is how to implement a WAFER card using LabVIEW. According to the requirements of my client, the element of pads varies between 6 k and 23 k. I guess that do everything (a = a ctl/indicator led) will be a hell of a task, especially on how to effectively manipulate each elements. Does anyone have a better idea on the way whose that?
Please, I seriously need your help...

Thank you and best regards,
Dennis DG
Hi Dennis,
This wafer GerdW post card appears to me as a sort of histogram (for example http://www.ni.com/white-paper/4158/en#toc3);
Altenbach post well this example that shows how to use a plot of intensity to create a 2d histogram:
http://forums.NI.com/T5/LabVIEW/overlay-plots-as-intensity-graph/m-p/211222#M119248
Learn how it works and try to adapt it to your specific task.
Alex
-
How to implement Canopen on FPGA to run the engine using NOR-9881?
Dear,
Your support will be highly appreciated,
There is only one available for NOR-9881 example.
Please note that the following materials were properly connected:
cRIO-9024, cRIO-9113, OR-9881 and motor Nanotec (SMCI36 against L2818L0604-T5X5), the following
sites Web shows the engine Nanotec in details:
http://us.Nanotec.com/products/660-L28-linear-actuators-with-trapezoid-spindle/
http://us.Nanotec.com/products/1041-SMCI36-stepper-motor-and-BLDC-motor-position ing-control /
The main problem is how to configure the inputs and outputs, where, in most examples, the entry and exit have been automatically
configured.
the following three examples and I wonder how to start:1 - example Nanotec: dependent VISA controls for data transfer
http://us.Nanotec.com/support/application-notes/LabVIEW-example/
2 - reference example CANopen for series C OR - 9853 Module CAN:
the NOR-9853 has default Can0 which was used in the codehttp://zone.NI.com/DevZone/CDA/EPD/p/ID/6093
3 - from finder labView example: search for 9881 then choose
NOR - CANopen_cRIO.lvproj, which depended on SDO orders for transfer orders
The attached picture shows that NEITHER-9881 can be seen, after compilation and
loading the bitfile FPGA.
Please, please advice me:
1. how to start?
2. how to create variables of entry for NI9881?
3. how to implement CANopen mode FPGA? where there is no CANopen palette.Thanks in advance and
Hello!
From my understanding, the 9881 can be treated from the FPGA, but only from the application of the RT. I think that the point 3 of your post examples of the use of the module fine.
Kind regards
Georg
-
How do I password protect the document HTML library or individual files which are: IE: pictures etc?
How do I password protect the document HTML library or individual files which are: IE: pictures etc?
In Windows there is no password protection.
-
How to eiminate password screen to start windows xp professional
How eiminate screen password to start windows xp professional?
Thank you
Terry
Try this link:
"How to turn on automatic logon in Windows XP"
<>http://support.Microsoft.com/kb/315231 >HTH,
JW -
How to implement interfaces or inheritance in LabVIEW?
Hi all
I try to implement oriented OBJECT in my LabVIEW code and require heritage or just an interface (such as might be required in java). I have a good knowledge of OOP is just how do me in LabVIEW, I'm curious.
I'll try to stick with my own example for now, so that someone is able to tell me exactly how to implement this.
in any case, I have two different DMM and each come with their own GPIB commands to get the measures and set the measurement configurations. This seems to be a perfect example to learn how to use inheritance. I figured out how to make a class for each DMM but was curious as to how I might be able to create a parent class for each of them because they both require the same fields in their configuration (AC/DC, Measurment Type, rank, address VISA). I think that I could create a parent class with these fields, then the methods of use of these fields and have then child classes inherit fields and override the methods of the parent class so that depending on what the user selected DMM, it would be able to use the correct class to issue the right GPIB commands.
If anyone can point me to a good example or explain how this could be implemented in labview that would be super. I'm also browsing the forums LVOOP to LavaG trying to figure this out, thanks!
Brent
Brent,
LabVIEW help contains a lot of detailed information on the use of classes. I recommend reading through it, before we begin with OOP in LabVIEW. In the content of the Help window tab, search for "Fundamentals > LabVIEW Object - Oriented Programming > How - to's» There is an article entitled 'change the legacy of a LabVIEW class' that should be what you're looking for.
Chris M
-
How to enable password protection in windows xp after disableing it
How to enable password protection in windows xp after disableing it I disabled it and now I don't have to reverse the trend.
Hello
· What password are you referring, passwords, or any other application?
If you're referring to passwords, then follow the steps mentioned below.
a. Click Start, and click Control Panel.
b. click on user account and click on your username.
c. click password to create and then create a new password.
How to create and configure user accounts in Windows XP
http://support.Microsoft.com/kb/279783
Thanks and regards.
Thahaseena M
Microsoft Answers Support Engineer.
Visit ourMicrosoft answers feedback Forum and let us know what you think.
Maybe you are looking for
-
loop nested using iteration of the outer loop as counter
Hello world. I have a moment where I perform calculations at each iteration of the loop and display on the front panel. Then, in a loop iteration randomly (referred to here as I = 9 to test) it fires an event where that performs calculations on x n
-
Slimline S5 1554 Joshua-H61 Mthrbrd SSD - HP
Morning - I have a HP Slimline Pavilion S5-1554, product HP #: H3L78AAR #ABA The system supplied with Windows v8.0 and has been updated for Windows ver 8.1 I think that HP Support App identifies the unit as a "model H3L78AA". As with the purchase, th
-
For pete even when bbm will grow and have the fashion landscape? We prefer portrait mode and surely, it is not difficult to be included. I think I speak for a lot of people and so it would be nice for bb to listen! Landscape that more please!
-
Photosmart C8180 All-in-one: not able to print colors light magenta and magenta
I bought photosmart c8180 about 3 years as a spare printer. I set up and printed a few pages. A printer was perfectly fine. Last week, I decided to use this printer. When I tried to print, color photos are released totally foires. I used the tools-
-
Is it possible to update my Version of Lightroom5 to the Version6 if my program came bundled with a Canon or Leica camera?