Split Tunnel problem.
Hello.
All started to play with split-mining.
So far so good.
I can access the server when the Tunnel of splitting is disabled, and my itinerary looks very good. But cannot access the internet.
I can not access the server when the Tunnel of splitting is enabled, my itinerary seems wrong. But can access the internet.
I think it's my access list the problem (also tried to overthrow).
split_test list extended access allowed host 4.4.4.4 ip 10.10.253.0 255.255.255.0
attributes of the strategy of group test_policy
Split-tunnel-policy tunnelspecified
value of Split-tunnel-network-list split_test
I read that I can't filter on the ports during the shared use of tunnelling, is this correct?
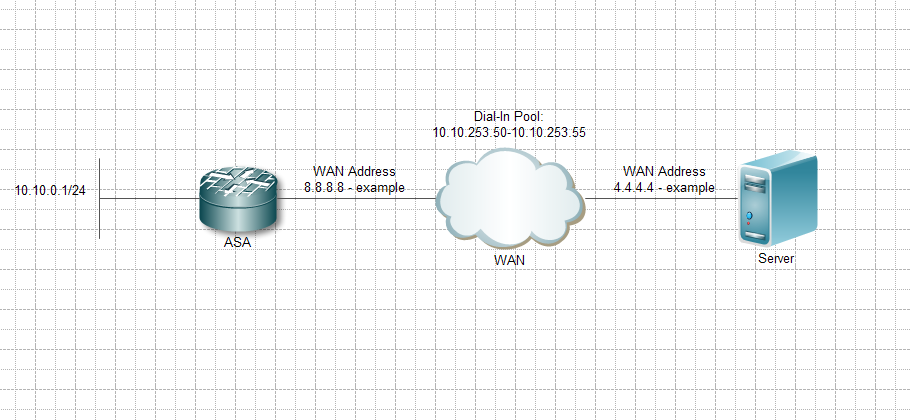
I have attached a quick drawing of the installation.
Best regards, Søren.
Hello
Then you can use the following version of above indicate changes in configurations
attributes of the strategy of group test_policy
No split-tunnel-network-list split_test value
No list of extended split_test access not allowed host 4.4.4.4 ip 10.10.253.0 255.255.255.0
host of access TUNNEL of SPLIT standard allowed 4.4.4.4 list
attributes of the strategy of group test_policy
no value of split-tunnel-network-list SPLIT-TUNNEL
The above configuration would be basically set up the VPN Client connection so that connections for ONLY the IP 4.4.4.4 the VPN connection will be provided by the user.
As I understand it, the traffic of users to the destination server would only be encrypted between the Client and the ASA. From there it would be just like any traffic between hosts on the external network. Except of course your ASA has a separate VPN L2L connection on the site where the Server 4.4.4.4.
Even if the above Split Tunnel ACL configuration is correct, you will still need to manage the NAT for VPN Client users. To determine the NAT configuration correct, I need to know the version of the software of your ASA and the current dynamic PAT rule for internal users, for example if the VPN users are supposed to use the same public IP address for their IP NAT address.
Also, you will at least have to add this configuration on the SAA
permit same-security-traffic intra-interface
This will allow connections to VPN users enter through the 'outside' of the interface and head to this same ' outside ' interface. It is not possible without the above configured command even if all other configurations were correct.
-Jouni
Post edited by: Jouni Forss (typos in the post)
Tags: Cisco Security
Similar Questions
-
AnyConnect SSL VPN Split tunneling problem
Hello
We have home users that VPN in on a regular basis, but when they VPN in they cannot print locally or to connect to local resources. Is there a way to activate the split for all remote users VPN tunneling? It is not possible to add all the remote subnets, especially since I don't know which subnets are used and it would be a question of management. I noticed that when I connect to the House a new route is added to my PC, who prefers the VPN link.
I noticed one of the options with the client Anyconnect is 'enable local LAN access (if configured) '. Can I use?
Thanks in advance.
Hello
According to my understanding, you need to connect to your local printers while you are connected to the ASA via SSL VPN.
You can do this by creating a policy of exclusion of tunnel split on SAA and the local lan access on the client option, or you can use the profile AnyConnect allowing local lan access.
Please find the link below: -.
I hope it helps.
Thank you
Shilpa
-
Access remote VPN, no split tunneling, internet access. Translation NAT problem
Hi all, I'm new to the forum. I have a Cisco ASA 5505 with confusing (to me) question NAT.
Unique external IP (outside interface) with several translations of NAT static object to allow the redirection of port of various internal devices. The configuration worked smoothly during the past years.
Recently, I configured a without the split tunneling VPN remote access and access to the internet and noticed yesterday that my port forwarding has stopped working.
I reviewed the new rules for the VPN NAT and found the culprit.
I've been reviewing the rules again and again, and all I can think about and interpret it, I don't know how this rule affects the port forwarding on the device or how to fix.
Here's the NAT rules, I have in place: ('inactive' rule is the culprit. Once I have turn on this rule, the port forwarding hits a wall)
NAT (inside, outside) static source any any static destination VPN_Subnet VPN_Subnet non-proxy-arp-search to itinerary
NAT (outside, outside) static source VPN_Subnet VPN_Subnet VPN_Subnet VPN_Subnet non-proxy-arp-search of route static destination
NAT (outside, outside) source VPN_Subnet dynamic interface inactive
!
network obj_any object
NAT dynamic interface (indoor, outdoor)
network of the XXX_HTTP object
NAT (inside, outside) interface static tcp www www service
Access-group outside_access_in in interface outside
Route outside 0.0.0.0 0.0.0.0 xxx.xxx.xxx.xxx 1Any help would be appreciated.
Try changing the nat rule to VPN_Subnet interface of nat (outside, outside) the after-service automatic dynamic source
With respect,
Safwan
-
I'm working on an installation of the laboratory program at home with my X-5506, and I got a split tunneling configuration problem. Every change I seem to give me internet access, gives me access to the local network or remove both. The current configuration, I took them both and I am a little puzzled. I have attached the configuration. Any guidance would be greatly appreciated!
Change:
split-tunnel-policy excludespecified
TO:split-tunnel-policy tunnelspecified
I notice you are using 192.168.0.0/24. Make sure that you do not work VPN'ing an address 192.168.0.0/24 as well (or a subnet that is also identical to your subnet that you are trying to access remotely) or it won't work. Overall, you should avoid using 10.0.0.0/24 and 192.168.0.0/24 in production networks because they are so frequently used in home networks. I also note that you have configured IKEv2. IKEv2 does not support split tunneling. SO be sure you use only the AnyConnect client in SSL mode. -
Hi guys,.
I just sent a SRP527W that I had lying around for a while.
Everything about the unit works as well as can be expected, however I have an obligation to perform split tunneling for VPN users.
Currently, the only way that receives the VPN client is a default route. I noticed that on site-to-site VPN and tunnels GRE, you can specify safe routes, but I can't find anything that relates to remote VPN users. This can be done on IOS without problem, but would be good for the RPS.
I'm under the latest firmware 1.01.26, so if I have not forgotten anything it would be probably for a future version?
See you soon.
Bryce
Hi Bryce,.
Nothing is overlooked, it is not possible to set up split tunneling for the VPN of the RPS server.
Kind regards
Andy
-
How to add an external IP address to a split tunnel?
Hello
I've set up VPN access on my ASA box as customers use a split tunnel so that only on our internal network traffic through the tunnel. Now, I need to add an external IP address to this tunnel. Is this possible, and if so, how can I achieve that? Just add the address to the list of tunnel network does not; If I do this, the client cannot connect to the external address at all.
Can anyone help?
Cheers, Georg.
Hello
Will need to see some configurations.
Usually incoming VPN traffic bypasses ACL interface. If you have the default setting, you will need to allow traffic to the pool/subnet VPN server. Unless of course the server already has a rule that allows traffic to a "some" source address.
Also a likely problem may be your NAT configuration.
The local IP address of the server the public IP address is included in the current NAT0 configurations for the VPN connection? If yes then which will probably cause problems for connections to its public IP address. Traffic could be abandoned due to a RPF NAT audit that basically checks the NAT that corresponds to the traffic in the opposite direction.
Therefore to confirm the above things, or share configurations, then we can do it.
To my knowledge by adding the address IP of the Split tunnel should naturally also be taken.
EDIT: The number of the station 6000
-Jouni
-
Disable Split Tunneling - SAs are not when I change crypto ACL
Hello!
When I change my ACL Crypto I receive an error message in phase I: "PROPOSAL_NOT_CHOSEN NOTIFIER' of IKE. I do this to disable the ST and get all the hollow tunnel traffic. Please see the config below:
crypto ISAKMP policy 10
md5 hash
preshared authentication
life 3600
ISAKMP crypto key cisco address x.x.x.x
!
!
Crypto ipsec transform-set esp - the esp-hmac-md5 ENCRYPTION
!
crypto map ipsec-isakmp CLIENT 1
defined peer x.x.x.x
game of transformation-CRYPTO
match address 115
!
access-list 115 permit ip 10.10.10.0 0.0.0.255 10.10.11.0 0.0.0.255
access-list 115 deny ip any one
I changed the ACL 115 to so I can disable split tunneling, and it looks like this:
access-list 115 permit ip 10.10.10.0 0.0.0.255 any
access-list 115 deny ip any one
What is a failure? I have donthink the crypto ACL must be the same?
OK, you use a card dynamic encryption on your head just as I suggested, so that's fine. What you have done, which is causing your problem (and usually causes more problems than it's worth), is to assign an access list to the dynamic encryption card. It is not necessary, because with a dynamic encryption the router head card accept any model of traffic the remote router sends.
In your case since you changed the remote router to be 'all', it is no longer maps to the 115 ACL on the head and now is failing.
Way easier around it is simply to remove the 'match 115' address card dynamic encryption on the head. This will not affect any of your other tunnels and allow the remote router to establish a tunnel.
The exact commands you would use are as follows:
> crypto dynamic-map PERSONAL 10
> no address for correspondence 115
-
Internet access from the default remote gateway? NO SPLIT TUNNELING
I am facing a problem for a long time, I have an ASA5505 I went through a lot of config and research until I got the inside interface to be able to go to the internet; However my VPN clients are unable to go to the Internet. Now, here's the network config:
-J' have a router (which is a modem and a router and an AP) 3 in 1... This router is connected to the ISP with a coaxial cable. the Interior is 192.168.0.0/24 network.
-L'ASA is connected to rotate inside the network of its ' outside the interface.
-L' SAA within the 192.168.1.0/24 network is a configured static gateway already (which is the router)
outside the int > default gateway 192.168.0.1 (which is the internal IP address of the router). -Inside the ASA computers are able to connect to Web sites (but I can't do anything outside the network of CMD PING)!
-When a VPN cleint to connect using IPsec (without certificate) by using a Cisco VPN client software, the client can ping and do the remote desktop connection with computers on the same within the network (192.168.1.0/24) but can not pass the Internet even know that other computers on the network can go to the internet.
-One of the computers on the network (the inside network) is a DC server 2008 R2 which can go to the internet, as I mentioned above.
What I'm trying to do is have the VPN clients to be able to go to the internet with the help of which the ASA inside the NETWORK card as a default gateway (192.168.1.1), I already have the VPN configuration with the name of the group, preshared key, user name and password and without the split tunneling (which is what I want)
Thank you
Hello
The most common problem by getting ICMP to work through the ASA failed ACL or the ICMP Inspection rules.
Check your configurations of current ' policy-map ' on the SAA with the command
See the race policy-map
I assume you have the default configurations 'policy-map' on the SAA, that are attached to the global
Under ' policy-map ' configurations, you should see several 'inspect' commands. Pass under the correct configuration mode (where the current commands are found) and add the following
inspect the icmp
inspect the icmp error
Then retest the ICMP through firewall.
In regards to the VPN Internet traffic, we would need to know the level of Software ASA which you can check with the command 'show version'
You must first verify that you have this command
permit same-security-traffic intra-interface
This will allow the traffic to the VPN users access the interface ' outside ' of the ASA, get PATed and then leave again through the ' outside ' interface. Without the command above it will not work. Will never go the VPN Internet user traffic through the interface "inside" of your ASA.
Then, you will also need the dynamic configuration PAT for your VPN users, so they are translated at the same IP address that users of LAN behind the ASA. This format of configuration depends on the software level, that I mentioned above
On a SAA running 8.2 (or below) you would usually have this configuration
Global 1 interface (outside)
nat (inside) 1 0.0.0.0 0.0.0.0 (or the mentioned specifically LAN)
To activate the dynamic PAT for VPN users that you would add
NAT (outside) 1
On one ASA 8.3 running (and above) you can configure the dynamic PAT for users of VPN in the following way
network of the VPN-PAT object
subnet
dynamic NAT interface (outdoors, outdoor)
It should be. Of course, you could have a configuration that may replace it, but I doubt it.
Hope this helps
-Jouni
-
I have a pix 501 configured as easy VPN client and CAN connect to my VPN from Cisco 3005 concentrator without problem in a test environment.
Basic config - looks like this:
vpngroup vpnclient * password *.
vpnclient username * password *.
vpnclient Server aaa.bbb.ccc.ddd
vpnclient-mode client mode
vpnclient enable
Regarding the connectivity, it is sufficient - the 3005 is located at our main office and we have no access to the network behind the PIX (which will be eventually on a wired network with DHCP enabled).
How can I add tunneling split in such a configuration? (end users need all their traffic coming back here before going to the world). I made a few unsuccessful attempts at adding an ACL and in the binder to the nat, but nothing helped.
Any suggestions are appreciated.
Thank you in advance.
Split tunnelling, as with software clients, is configured on the hub of head. This information is then passed to the PIX EzVPN client during the negotiation process.
Set up a network on the 3005 list, then configure split tunneling for this group on the 3005 and use the list that you just created. You will need to should not do something on the PIX itself.
-
Split tunneling cannot access remote host
Hi guys,.
Having this problem by which I am able to connect the Anyconnect client but unable to ping / access of remote servers. See below for the config of the SAA;
Any ideas would be a great help, thank you!
ASA Version 9.1 (1)
!
ASA host name
enable the encrypted password xxxxxxx
xxxxxxxxxxxxx encrypted passwd
names of
mask of local pool AnyPool 10.0.0.1 - 10.0.0.10 IP 255.255.255.0
!
interface GigabitEthernet0/0
nameif outside
security-level 0
IP address 203.106.x.x 255.255.255.224
!
interface GigabitEthernet0/1
nameif inside
security-level 99
IP 172.19.88.254 255.255.255.0
!
interface Management0/0
management only
nameif management
security-level 100
IP 192.168.1.1 255.255.255.0
!
passive FTP mode
clock timezone 8 MYT
the SVR object network
Home 172.19.88.11
e-mail server in description
network of the NETWORK_OBJ_172.19.88.0_24 object
172.19.88.0 subnet 255.255.255.0
network of the VPN-POOL object
10.0.0.0 subnet 255.255.255.0
object-group Protocol TCPUDP
object-protocol udp
object-tcp protocol
object-group service DM_INLINE_SERVICE_0
ICMP service object
area of service-purpose tcp - udp destination eq
the destination hostname eq tcp service object
the purpose of the tcp destination eq https service
the purpose of the tcp destination eq imap4 service
the purpose of the tcp destination eq nntp service
the purpose of the tcp destination eq pop3 service
the purpose of the tcp destination eq smtp service
the purpose of the tcp destination eq telnet service
Outside_access_in list extended access allowed object-group DM_INLINE_SERVICE_0 any object SVR
Outside_access_in list extended access allow TCPUDP of object-group a
Outside_access_in access-list extended ip any any idle state to allow
Internal_access_in list extended access allow TCPUDP of object-group a
Internal_access_in access-list extended ip any any idle state to allow
SPLIT_TUNNEL list standard access allowed 10.0.0.0 255.255.255.0
pager lines 24
Enable logging
timestamp of the record
exploitation forest-size of the buffer 16384
buffered logging critical
asdm of logging of information
Debugging trace record
exploitation forest flash-bufferwrap
record level of the rate-limit 1000 1 2
management of MTU 1500
MTU 1500 internal
Outside 1500 MTU
no failover
ICMP unreachable rate-limit 1 burst-size 1
ASDM image disk0: / asdm - 711.bin
don't allow no asdm history
ARP timeout 14400
no permit-nonconnected arp
!
the SVR object network
203.106.x.x static NAT (indoor, outdoor)
!
source of auto after the cessation of NAT (inside, outside) dynamic interface
Internal_access_in in interface internal access-group
Access-group Outside_access_in in interface outside
Route outside 0.0.0.0 0.0.0.0 203.106.23.97 1
Timeout xlate 03:00
Pat-xlate timeout 0:00:30
Timeout conn 01:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
Sunrpc timeout 0:10:00 h323 0:05:00 h225 mgcp from 01:00 0:05:00 mgcp-pat 0:05:00
Sip timeout 0:30:00 sip_media 0:02:00 prompt Protocol sip-0: 03:00 sip - disconnect 0:02:00
Timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
Floating conn timeout 0:00:00
dynamic-access-policy-registration DfltAccessPolicy
identity of the user by default-domain LOCAL
the ssh LOCAL console AAA authentication
LOCAL AAA authorization command
Enable http server
http 192.168.1.0 255.255.255.0 management
http authentication certificate management
No snmp server location
No snmp Server contact
Server enable SNMP traps snmp authentication linkup, linkdown warmstart of cold start
No vpn sysopt connection permit
Crypto ipsec ikev2 ipsec-proposal OF
encryption protocol esp
Esp integrity sha - 1, md5 Protocol
Crypto ipsec ikev2 proposal ipsec 3DES
Esp 3des encryption protocol
Esp integrity sha - 1, md5 Protocol
Crypto ipsec ikev2 ipsec-proposal AES
Esp aes encryption protocol
Esp integrity sha - 1, md5 Protocol
Crypto ipsec ikev2 ipsec-proposal AES192
Protocol esp encryption aes-192
Esp integrity sha - 1, md5 Protocol
Crypto ipsec ikev2 AES256 ipsec-proposal
Protocol esp encryption aes-256
Esp integrity sha - 1, md5 Protocol
Crypto ipsec pmtu aging infinite - the security association
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 define ikev2 AES256 AES192 AES 3DES ipsec-proposal OF
card crypto Outside_map 65535-isakmp dynamic ipsec SYSTEM_DEFAULT_CRYPTO_MAP
Outside_map interface card crypto outside
Crypto ca trustpoint ASDM_TrustPoint0
Terminal registration
name of the object CN = ASA
Configure CRL
Crypto ca trustpoint Anyconnect_TrustPoint
registration auto
name of the object CN = ASA
anyconnect_rsa key pair
Configure CRL
Crypto ca trustpoint _SmartCallHome_ServerCA
Configure CRL
trustpool crypto ca policy
string encryption ca Anyconnect_TrustPoint certificates
IKEv2 crypto policy 1
aes-256 encryption
integrity sha
Group 2 of 5
FRP sha
second life 86400
IKEv2 crypto policy 10
aes-192 encryption
integrity sha
Group 2 of 5
FRP sha
second life 86400
IKEv2 crypto policy 20
aes encryption
integrity sha
Group 2 of 5
FRP sha
second life 86400
IKEv2 crypto policy 30
3des encryption
integrity sha
Group 2 of 5
FRP sha
second life 86400
IKEv2 crypto policy 40
the Encryption
integrity sha
Group 2 of 5
FRP sha
second life 86400
Crypto ikev2 activate out of service the customer port 443
Crypto ikev2 access remote trustpoint Anyconnect_TrustPoint
Telnet timeout 3
SSH 172.19.88.0 255.255.255.0 internal
SSH 0.0.0.0 0.0.0.0 outdoors
SSH timeout 15
Console timeout 0
management of 192.168.1.100 - 192.168.1.200 addresses dhcpd
enable dhcpd management
!
a basic threat threat detection
Statistics-list of access threat detection
no statistical threat detection tcp-interception
NTP server 119.110.97.148 prefer external source
SSL-trust outside Anyconnect_TrustPoint point
WebVPN
allow outside
AnyConnect image disk0:/anyconnect-win-2.5.2014-k9.pkg 1
AnyConnect image disk0:/anyconnect-macosx-i386-2.5.2014-k9.pkg 2
AnyConnect image disk0:/anyconnect-linux-2.5.2014-k9.pkg 3
AnyConnect profiles AnyConnect_client_profile disk0: / AnyConnect_client_profile.xml
AnyConnect enable
attributes of Group Policy DfltGrpPolicy
VPN-tunnel-Protocol ikev1, ikev2 ssl clientless ssl ipsec l2tp client
Split-tunnel-policy tunnelspecified
value of Split-tunnel-network-list SPLIT_TUNNEL
Group Policy 'GroupPolicy AnyConnect' internal
Group Policy attributes "GroupPolicy AnyConnect"
value of server WINS 172.19.88.11
value of server DNS 172.19.88.11
SSL VPN-tunnel-Protocol ikev2 client ssl clientless
WebVPN
AnyConnect value AnyConnect_client_profile type user profiles
attributes global-tunnel-group DefaultWEBVPNGroup
address pool AnyPool
tunnel-group "AnyConnect" type remote access
attributes global-tunnel-group "AnyConnect".
address pool AnyPool
strategy-group-by default "GroupPolicy AnyConnect"
tunnel-group "AnyConnect" webvpn-attributes
Group-alias "AnyConnect" activate
!
class-map inspection_default
match default-inspection-traffic
!
!
type of policy-card inspect dns preset_dns_map
parameters
maximum message length automatic of customer
message-length maximum 512
Policy-map global_policy
class inspection_default
inspect the preset_dns_map dns
inspect the ftp
inspect h323 h225
inspect the h323 ras
inspect the rsh
inspect the rtsp
inspect esmtp
inspect sqlnet
inspect the skinny
inspect sunrpc
inspect xdmcp
inspect the sip
inspect the netbios
inspect the tftp
Review the ip options
Hi Max,.
Please send me the output of 'see the anyconnect vpn-sessiondb' once connected with VPN.
And try to add the following configuration and see if that helps:
NAT (inside, outside) 1 static source NETWORK_OBJ_172.19.88.0_24 NETWORK_OBJ_172.19.88.0_24 static destination VPN-VPN-POOL no-proxy-arp-route search
And one more qusetion do you use split tunnel? If yes then you must make the following changes, because your split tunnel is incorrect, in the split tunnel, you have configured the address pool of vpn. Please make the following change:
no access list SPLIT_TUNNEL standards not allowed 10.0.0.0 255.255.255.0
Standard access list SPLIT_TUNNEL allow 172.19.88.0 255.255.255.0
Group Policy attributes "GroupPolicy AnyConnect"
Split-tunnel-policy tunnelspecified
value of Split-tunnel-network-list SPLIT_TUNNEL
Let me know if this can help, or if you have any questions, more about it.
Thank you
Jeet Kumar
-
Help: Customer Cisco VPN & Split Tunnel but not Internet
Hi Forum.
We are faced with this problem: after having successfully open a VPN connection with the Cisco VPN Client to a router Cisco, the rest of the world are not properly available more.
This is what has been verified / so far attempted to identify the problem on a Windows Vista computer:
-Router: Split Tunneling is allowed according to sysop
-On the VPN-Client: "allow Local Lan access" is checked
-On the Client (statistics): only STI VPN-rout configured listed unter "guarantee routes." "Local Lan routes" is empty.
-Calling 'http://www.google.com' in IE fails
-Call ' 74.125.232.116' (IE IP) IE works / ping the IP works.
-nslookup properly lists the current DNS server
-nslookup www.google.com resolves correctly the name of intellectual property
It seems that it is not that the connection with the rest of the Internet is deleted, but DNS resolution fails somehow, even though all signs point to the appropriate DNS server is in force and although the command line can resolve the name.
does anyone have a tip how to debug this correctly?
No worries Pat...
Sent by Cisco Support technique iPhone App
-Please evaluate solutions
-
Split tunnel setup on asa 8.4 with 6.4 AMPS
We have established and work, with the exception of tunneling split anyconnect.
the 6.4 AMPS I went to: remote VPN access > (Client) network access > Group Policy > GroupPolicy_anyconnect_vpn > edit > advanced > split tunneling > then unchecked "inherit" on list of network and selected an ACL called "TUNNEL of SPLIT.
the ACL is pasted below the CLI, it is all of our internal networks, everything is static routed and on the same vlan
SG-ASA-1 # sho - TUNNEL of SPLITTING access list
list of access TUNNEL of SPLITTING; 10 items; hash name: 0x25b1daf1
Access-list 1 permit line SPLIT TUNNEL extended ip 192.168.100.0 255.255.255.0 192.168.22.96 255.255.255.224 (hitcnt = 0) 0xe3a9484b
permit for SPLIT-TUNNEL list lengthened 2 ip 192.168.105.0 access line 255.255.255.0 192.168.22.96 255.255.255.224 (hitcnt = 0) 0x377afd96
allowed for access list 3 SPLIT-TUNNEL line scope ip 192.168.110.0 255.255.255.0 192.168.22.96 255.255.255.224 (hitcnt = 0) 0x0b4d6f9c
line 4 extended to the TUNNEL of SPLIT-ip access list 192.168.120.0 allow 255.255.255.0 192.168.22.96 255.255.255.224 (hitcnt = 0) 0x7a6cc93f
allowed for access list 5 SPLIT-TUNNEL line scope ip 192.168.130.0 255.255.255.0 192.168.22.96 255.255.255.224 (hitcnt = 0) 0xe228bdad
allowed for access list 6 SPLIT-TUNNEL line scope ip 192.168.140.0 255.255.255.0 192.168.22.96 255.255.255.224 (hitcnt = 0) 0x317f80c8
allowed for access list 7 SPLIT-TUNNEL line scope ip 192.168.150.0 255.255.255.0 192.168.22.96 255.255.255.224 (hitcnt = 0) 0xe4c276b0
allowed for access list 8 SPLIT-TUNNEL line scope ip 192.168.160.0 255.255.255.0 192.168.22.96 255.255.255.224 (hitcnt = 0) 0x0c2dd3ab
allowed for access list 9 SPLIT-TUNNEL line scope ip 192.168.170.0 255.255.255.0 192.168.22.96 255.255.255.224 (hitcnt = 0) 0x00a4d4e3
permit for line TUNNEL of SPLITTING access-list 10 scope ip 192.168.180.0 255.255.255.0 192.168.22.96 255.255.255.224 (hitcnt = 0) 0xfb381008
SG-ASA-1 #.After this setting in the Group of ASSISTANT Deputy Ministers policy, we tested in vain yesterday morning. They can connect and ping all those inside network but not the internet. The journal of the asa showed what follows when a vpn client tried to ping Yao
6 August 14, 2012 07:51:04 64.60.xxx.xxx 4397 206.169.203.226 1433 routing cannot locate the next hop for TCP to inside:64.60.xxx.xxx/4397 to outside:206.169.203.226/1433
We can ping the inside no network problems after you connect to the VPN from outside.
64.60.xxx.xxx is our public IP address that is on the external interface, which is the IP address we use to vpn.ourdomain.com
Thanks in advance for any help
Hello
You can try to use the standard access list in the same menu.
List of strategies for the tunnel CLCK spit > click on manage, select the standard acl tab and only add 192.168.0.0 255.255.0.0 (for testing purposes)
Then test if it works to connect to Internet
The filtering you want, highest in your message you can do it with a security acl.
If it works, you can add more specific standard ACL split tunneling list, as
Add 192.168.100.0
etcetc
-
access list of split tunneling
Hello
I have some problems on ASA 5520 split tunneling configuration.
Here's the scenario:
Number of remote users connects ipsec with ASA 5520 (in central) using ubuntu vpnc-client.
Split tunneling is used, in order to allow remote users to surf the Internet using their ISP.
The goal is to remove the possibility for ssh/telnet servers within the local enterprise network for remote users.
Here is a part of the config:
internal REMOTE_gp group strategy
attributes of Group Policy REMOTE_gp
VPN-idle-timeout no
Protocol-tunnel-VPN IPSec
Group-lock no
Split-tunnel-policy tunnelspecified
value of Split-tunnel-network-list REMOTE_splittunnel-group type REMOTE access remotely
tunnel-group REMOTE General attributes
authentication-server-group RADIUSGR
Group Policy - by default-REMOTE_gp
REMOTE tunnel-group ipsec-attributes
pre-shared-key *.
ISAKMP keepalive retry threshold 15 10
RADIUS protocol AAA-server RADIUSGR
AAA-server RADIUSGR (INSIDE_LAN) 192.168.0.244
REMOTE_split list extended access deny tcp 192.168.0.0 255.255.255.0 ssh telnet rank everything
permit access ip 192.168.0.0 scope list REMOTE_split 255.255.255.0 192.168.100.0 255.255.255.0
ip subnet ##192.168.100.0/24 - where from Radius Server to allocate ip addresses to remote users.
INSIDE_LAN_in list extended access deny tcp 192.168.0.0 255.255.255.0 eq ssh 192.168.100.0 255.255.255.0
INSIDE_LAN_in list extended access deny tcp 192.168.0.0 255.255.255.0 eq telnet 192.168.100.0 255.255.255.0
permit access ip 192.168.0.0 scope list INSIDE_LAN_in 255.255.255.0 any
It has nat enabled on the interface, but there is a special instruction in nat0 ACL for 192.168.100.0 subnet
permit access ip 192.168.0.0 scope list INSIDE_LAN_nat0_outbound 255.255.255.0 192.168.100.0 255.255.255.0
The problem is that the remote users can easily ssh and telnet servers in network INSIDE_LAN. Everything I put in INSIDE_LAN_in ACL, remote users still have full access to this network. Restrictions in the REMOTE_split ACL do not work either.
You must configure vpn-filter rather to block telnet and ssh access as follows:
Remote filter access list deny tcp 192.168.100.0 255.255.255.0 192.168.0.0 255.255.255.0 eq 22
Remote filter access list deny tcp 192.168.100.0 255.255.255.0 192.168.0.0 255.255.255.0 eq 23
distance-filter 192.168.100.0 ip access list allow 255.255.255.0 192.168.0.0 255.255.255.0
attributes of Group Policy REMOTE_gp
VPN-value filter-remote control
Split tunnel acl has the following statement and it should be extended to standard ACLs instead of:
REMOTE_split list of permitted access 192.168.0.0 255.255.255.0
Hope that helps.
-
The viewer or split display problem: I am getting small white boxes (similar to those seen in the browser) superimposed on my photos. Any ideas how to fix? There must be a display problem in the software.
Have you of the 'show Talking Points' enabled in the view menu? Then you can see small white boxes superimposed on the image in the Viewer.
You can enable or disable on / off power with ⌥F talking points.
-
Access restricted without the split tunneling
I'm disabled with Split tunneling VPN concentrator. Split tunneling has been disabled to carry the internet traffic of vpn clients via our internal web filtering server. But I must restrict access to my internal servers. How can I do that. I tried with filters/Rules but his does not work, and depending on the traffic of documents filter applies only to the traffic unencrypted.
Thank you
Avil
If you use a VPN3000 while you can apply a filter to the users configured in group. This filter can restrict access to the servers as a list of specific protocols and access. This filter certainly applies to ENCRYPTED traffic, do not know what you are referring to your last sentence.
You must first define the rules to define the traffic you want to restrict address., see here for more details:
http://www.Cisco.com/univercd/CC/TD/doc/product/VPN/vpn3000/4_1/config/polmgt.htm#1321359
Define a filter, then add the rules you just set it to him:
http://www.Cisco.com/univercd/CC/TD/doc/product/VPN/vpn3000/4_1/config/polmgt.htm#1007037
Thne go under the group that these users are configured with, and then apply the filter to it.
A couple of sample filter are the following:
Allow access to 10.1.1.2 and block everything else:
To block access to everything, but 10.10.1.2, create a rule that is Inbound/Forward, Source of Anything, Destination of 10.1.1.2/0.0.0.0. Create another rule, it can be left at the default value which is incoming, drop, no matter what Source Dest what whatsoever. Create a filter with the default action of the front and add two new your rules, ensuring that rule that allows access to the host 10.1.12 is above the default rule which will pass everything else.
Block access to 10.1.1.2, and leave all the rest:
To allow access to everything except 10.10.1.2, create a rule that said, drop, no matter what Source and Destination of 10.10.1.2/0.0.0.0. Add a filter that has a default action is to send, add the rule to the filter.
Notes:
-You can allow or block access to subnets simply by changing your address/mask to something like combination: 10.1.1.0/0.0.0.255
Maybe you are looking for
-
Satellite L670 - the system HARD drive recovery does not start
Hello together, I have a problem with my laptop. I installed Windows 7 Ultimate 64 bit, that the laptop came with Win7 Home Premium 32 bit.Now I want to restore the original Windows Home Premium. On the laptop is a second partition with a folder name
-
Pavilion 500-451nl: controller Ethernet and PCI Simple Communications Center missing
I bought a new HP Pavilion 500 - 451nl that came with 10 Windows installed. I did not like the new OS so I refomated the hard drive and installed Windows 7 64-bit. Now, Miss me the drivers for the following items: -Ethernet Controller: PCI\VEN_10EC
-
is it possible to run applications files created in labview windows on laptops with mac x
-
Hello I am currently working on a project involving a Eurotherm 3508 instrument. I control this instrument using the driver et3500 (http://sine.ni.com/apps/utf8/niid_web_display.download_page?p_id_guid=FA24DAC594CD4665E0340003BA7CCD...), but I have a
-
Emails from Outlook Express error: unable to poll for new messages on your HTTP server.
When you set up Outlook Express and send/receive I get the following message: unable to poll for new messages on your HTTP server. Account: 'Hotmail', server: 'http://services.msn.com/svcs/hotmail/httpmail.asp', Protocol: HTTPMail, server response:
