TCP/IP access to Siemens S7 RT (no OPC)
Hello
We try to develop a pilot customer (for PXI RT OS) using the TCP/IP protocol in order to read data from LabVIEW (later also return some) of a S7 API from Siemens. We do not want to use the approach of the OPC.
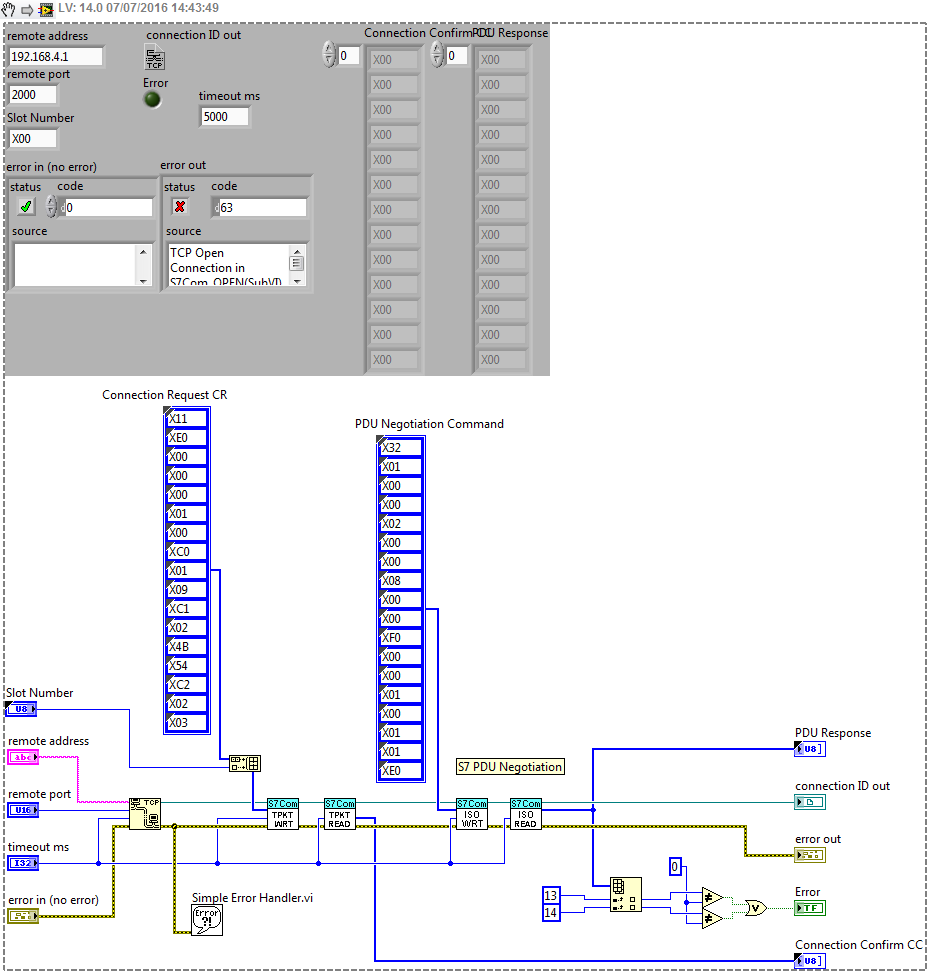
I try to use some code example from the https://decibel.ni.com/content/docs/DOC-5467#/ link. The problem is that I always get a "the network connection has been refused by the server", code 63. (see 1st picture below). So I can't test all features in RW since the simple "TCP connection open" order is already a failure. The IP address of the server, Siemens is 192.168.4.1, and the PC is set to 192.168.4.2 fixed. The port number for the S7 is set on 2000 and also enabled in Windows Firewall.
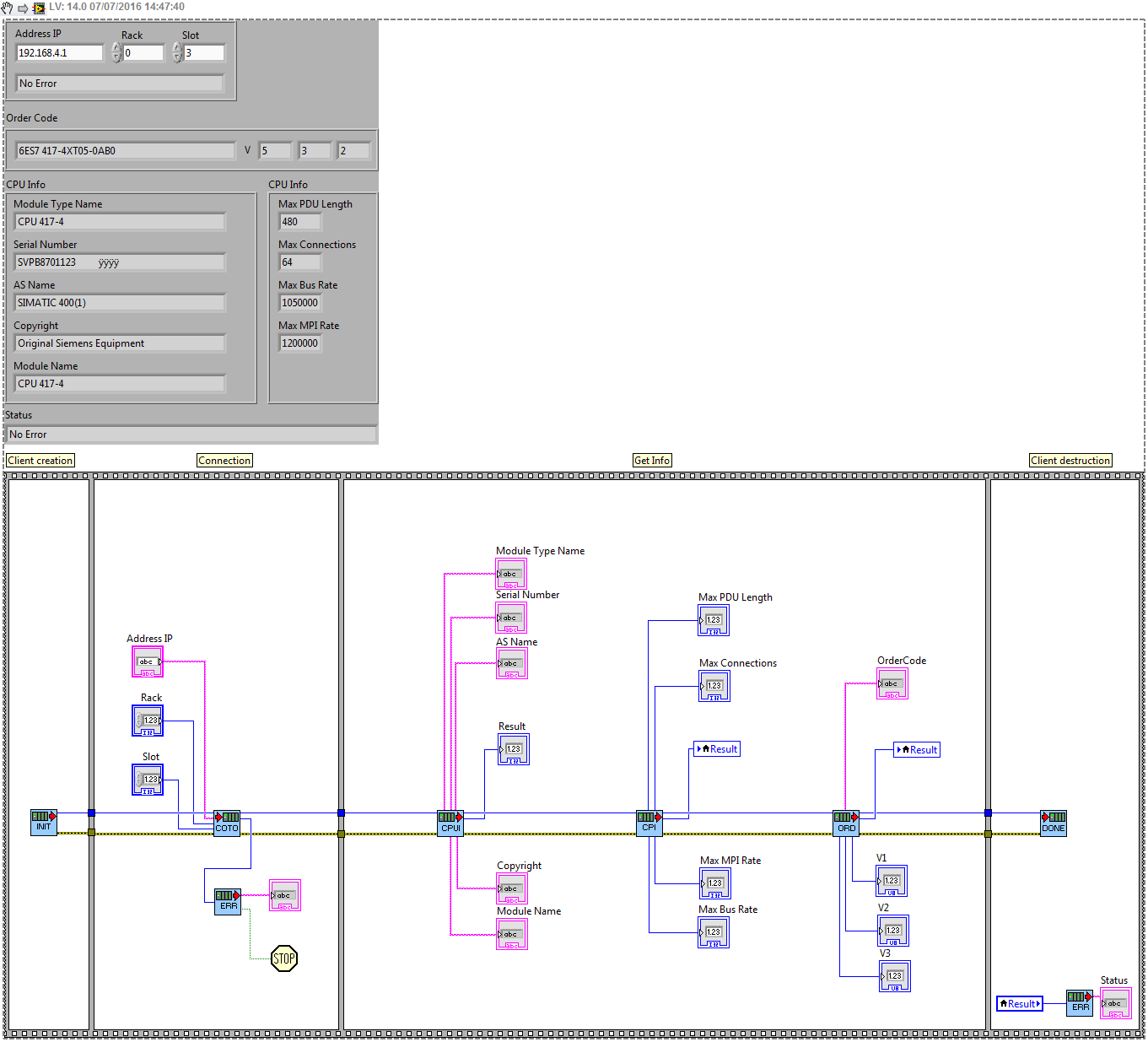
Counter-check, I have correctly connected to S7 with example LabVIEW here (see the second picture below):
The only problem with this LV driver set it uses a DLL and I need to use simple TCP/IP functions because I want to access the system from a real time OS S7, so go to the DLL approach...
How it can be that the sample code Snap7 works using TCP/IP, but failure of a login attempt very simple LabVIEW by the "TCP connection open"?
Maybe someone could give me a tip or an idea what else to try, or what I'm doing wrong...?
Thank you very much
Kind regards
snapshots:
Tags: NI Software
Similar Questions
-
Connecting a PLC Siemens S7-300 NI OPC Server
The project of memory Bachelor last year, I have two other are involved, I was instructed to implement a HMI/SCADA system to control the level and flow in several water storage tanks. This must be done locally via a "operator panel" and also remotely via Internet through a webbrowser. These storage tanks and control system is placed on a wheeled demonstration model, so it can be used in classrooms and auditoriums. Therefore, I have a Siemens PLC S7-300 and the latest edition of LabVIEW (ed. professional 2009) available to me. To create an HMI system, we will also acquire the DSC module OR that she would have everything we need (OR OCP is included?).
Since it is a project of the bachelor and the school is mainly to pay for everything, we are on a pretty strict budget. This means that we have not opted for a solution for the "operator panel" because this would be depends on the way in which the Group and the PLC interfaces. We would like to do for the sake of simplicity is to use commercial laptop computer with touchscreen ability thus having a solution 'all-in-one' low cost, both for the local input & control and ability to web publishing. Now, most of the computers today do not serial agrees, but rather USB ports.
On the Web server under the title OPC Device Connectivity page, it is specifically indicated "Siemens HMI adapter for S7-300/400 via Serial with HMI adapter". I guess this means the following Siemens unit: https://support.automation.siemens.com/WW/llisapi.dll/csfetch/8774263/hmi_adapter_x.pdf?func=cslib.c... (6ES7 972-0CA1X-0XA0).
This means that the server of the OCP can only use a connecting series via the HMI adapter for S7-300 directly? Is it not possible to use a USB adapter series without driver with the HMI, or for example the Siemens CP5711 MPI adapter USB adapter? If it is not possible to use a USB based solution, we would have to use an old desktop PC with a Compote series or an additional PCI card and it's something that we would like to avoid.
Any help on this would be much appreciated.
-DanJack, NUC Norway
Through 3rd party providers that I discovered that pilots of NI OPC for Siemens S7-300 Server supports ONLY in legacy communication RS232, no USB connectivity support any. You can only use the MPI for adapter RS232 or HMI for RS232 adapter.
-DanJack, NUC Norway
-
enable outbound access to TCP ports
would figure out how to open the outbound for TCP ports access and allow outgoing TCP access to certain ports? I know where to add a port. Put the name of am I let pass like Second Life?
Hello Angela12,
What operating system is installed on your computer?
This can be useful for you:
http://Windows.Microsoft.com/en-us/Windows7/open-a-port-in-Windows-Firewall
Kind regards
Savan - Microsoft technical support.
-
How to access a server based on the TCP/IP protocol port?
Hi all
Is it possible to access a server through a specific port via TCP/IP?
We have a step of database server in our network that supports the TCP/IP access. My boss asks if it is possible to get some simple data via blackberry?
The thing is that blackberry device is not in the network, how can we put a bb device in our intranet? Via enterprise server?
Alternatively, if we can put the server on the internet, can the blackberry device access via TCP/IP?
Thank you
Jerry
If you use wifi BB can access local servers. using direct tcp: nope.
You can use a bes express (which is free) If you're afraid of costs, still takes time to install/configure etc of course, otherwise you can only use your product if your BB is in the local WiFi network.
-
How my VISA control can communicate with an instrument via TCP/IP?
VISA controls are my GPIB instrument when I select "Refresh", but none of the instruments TCPIP. I know that the TCPIP instruments are connected because I can their ping.
If you are looking for how to build the resourcename, we find more here
TCPIP SOCKET TCPIP [Council]: host address:  ort:
ort: OCKET
OCKETfor example
TCPIP0::1.2.3.4::999:  OCKET
OCKETRAW TCP/IP access to the port at the specified IP address 999. TCPIP::dev.company. com::InStr A TCP/IP using VXI - 11 device located at the specified address. This example uses the default value for the inst0 LAN device name. -
Configuration of the ACL to restrict access via SSH/Telnet
You want to shoot a SSH/Telnet access to ISP address/IP of my switch interface. Since the Dells have no strict vty/con interface to apply an ACL I guess I just have to match on an interface instead. Using the ACL below. Problem is that applying it kills telnet/ssh sessions completely and does them in. Replaced the iPs in the wrong example with IPs. Confirm that my public IP address is 112.94.236.58. You will see a 112.94.236.56/29 with a permit instruction.
TEST from the list of access permitted tcp 111.126.50.0 255.255.255.0 111.126.50.16 255.255.255.0 eq 22
TEST from the list of access permitted tcp 111.126.50.0 255.255.255.0 111.126.50.16 255.255.255.0 eq telnet
TEST tcp allowed access list 112.94.236.56 255.255.255.248 111.126.50.16 255.255.255.0 eq 22
TEST the access permitted tcp 112.94.236.56 list 255.255.255.248 111.126.50.16 255.255.255.0 eq telnet
TEST from the list of access permitted tcp 112.94.254.0 255.255.255.128 111.126.50.16 255.255.255.0 eq 22
TEST from the list of access permitted tcp 112.94.254.0 255.255.255.128 111.126.50.16 255.255.255.0 eq telnet
TEST the access permitted tcp 112.94.248.176 list 255.255.255.248 111.126.50.16 255.255.255.0 eq 22
TEST the access permitted tcp 112.94.248.176 list 255.255.255.248 111.126.50.16 255.255.255.0 eq telnet
access list tcp TEST refuse any 111.126.50.16 255.255.255.0 eq 22
access list tcp TEST refuse any 111.126.50.16 255.255.255.0 eq telnet
TEST the ip access list allow a whole
111.126.50.16 is the switch
Maybe I should use a destination host in the ACL instead? (edit, nope, tried with a subnet of 255 s all, same problem)
The ACL is created using the command access-list config mode. On the interface it won't let me use ip access-class.
Figured it out. Kept, see references to "MACL", think why I needed a MAC access control list.
Nope.
Dell world, this means access control list management.
-
Enabling access to outside SMTP server
I've seen a Cisco Pix 501 and use it to access the Internet. It is configured to use PPPoE and is linked to an ADSL line. It works very well, however I'm trying to configure it to allow access to my internal mail server. I read this previous post:
https://supportforums.Cisco.com/thread/72060
I followed all the instructions, but it still does not work. What I am doing wrong?
Here is my configuration:
6.3 (4) version PIX
interface ethernet0 10baset
interface ethernet1 100full
ethernet0 nameif outside security0
nameif ethernet1 inside the security100
activate the password * encrypted
passwd * encrypted
somehost hostname
domain abcd.ef
clock timezone EDT 0
clock to summer time EDT recurring 2 Sun Mar 2:00 1 Sun Nov 02:00
fixup protocol dns-maximum length 1500
fixup protocol ftp 21
fixup protocol h323 h225 1720
fixup protocol h323 ras 1718-1719
fixup protocol http 80
no correction protocol rsh 514
fixup protocol rtsp 554
fixup protocol sip 5060
fixup protocol sip udp 5060
fixup protocol 2000 skinny
fixup protocol smtp 25
fixup protocol tftp 69
names of
name 10.1.1.19 mailserver
out2in tcp allowed access list any interface outside eq smtp
pager lines 24
debug logging in buffered memory
Outside 1500 MTU
Within 1500 MTU
IP address outside pppoe setroute
IP address inside 10.1.1.2 255.255.255.0
alarm action IP verification of information
alarm action attack IP audit
history of PDM activate
NAT (inside) 1 0.0.0.0 0.0.0.0 0 0
public static tcp (indoor, outdoor) interface smtp server e-mail smtp netmask 255.255.255.255 0 0
Access-group out2in in interface outside
Timeout xlate 03:00
Timeout conn 01:00 half-closed 0:10:00 udp 0: CPP 02:00 0:10:00 01:00 h225
H323 timeout 0:05:00 mgcp 0: sip from 05:00 0:30:00 sip_media 0:02:00
Timeout, uauth 0:05:00 absolute
GANYMEDE + Protocol Ganymede + AAA-server
AAA-server GANYMEDE + 3 max-failed-attempts
AAA-server GANYMEDE + deadtime 10
RADIUS Protocol RADIUS AAA server
AAA-server RADIUS 3 max-failed-attempts
AAA-RADIUS deadtime 10 Server
AAA-server local LOCAL Protocol
No snmp server location
No snmp Server contact
SNMP-Server Community public
No trap to activate snmp Server
enable floodguard
Telnet 10.1.1.17 255.255.255.255 inside
Telnet timeout 5
SSH 10.1.1.17 255.255.255.255 inside
SSH timeout 5
management-access inside
Console timeout 0
VPDN group PRMM request dialout pppoe
VPDN group PRMM localname [email protected] / * /
VPDN group PRMM ppp authentication pap
VPDN username [email protected] / * / password * local store
dhcpd dns 10.1.1.18 10.1.1.8
dhcpd outside auto_config
password to user auser name * encrypted privilege 2
Terminal width 80
Cryptochecksum: *.
: end
Here are the lines of interest:
name 10.1.1.19 mailserver
out2in tcp allowed access list any interface outside eq smtp
public static tcp (indoor, outdoor) interface smtp server e-mail smtp netmask 255.255.255.255 0 0
Access-group out2in in interface outside
What I am doing wrong?
TIA
Daniel,
How do you test the access to this server?
For example, what happens if you Telnet from outside your public IP address on port 25? If you can telnet to port 25, then the PIX config is fine and you should start looking at the server config.
Now if this does not work what do I you see if you're doing a "show xlate | Inc. 10.1.1.19.
In addition, you can try to activate a capture and see if the packets are making it through the PIX:
access-list 199 permit tcp any host 10.1.1.19 eq 25
access-list 199 permit tcp host 10.1.1.19 eq 25 all
capture the interface access-list 199 emailserver inside the length of the package-1300
Then try again to establish the connection and check what capture:
See capture emailserver
Try it and tell us how it goes.
Raga
-
RA-tunnel upward, but can not access to remote resources
The VPN client connects successfully to the PIX, but it does not appear that all traffic through the tunnel. There is a tunnel from site to site, which works very well, it's just the stuff of RA that doesn't. He had worked at some point and then stopped. This is a sanitized config:
:
6.3 (3) version PIX
interface ethernet0 car
interface ethernet1 100full
ethernet0 nameif outside security0
nameif ethernet1 inside the security100
activate the password *.
passwd *.
name of host depot-pix
domain.local domain name
fixup protocol dns-length maximum 512
fixup protocol ftp 21
fixup protocol h323 h225 1720
fixup protocol h323 ras 1718-1719
fixup protocol http 80
fixup protocol rsh 514
fixup protocol rtsp 554
fixup protocol sip 5060
fixup protocol sip udp 5060
fixup protocol 2000 skinny
No fixup not protocol smtp 25
fixup protocol sqlnet 1521
fixup protocol tftp 69
names of
name 2.2.2.2 cottage-pix
Server1 name 192.168.0.3
name 192.168.0.4 Server2
vpn ip 192.168.0.0 access list permit 255.255.255.0 192.168.10.0 255.255.255.0
vpn access list allow icmp a whole
vpn ip 192.168.0.0 access list permit 192.168.30.0 255.255.255.0 255.255.255.0 sign
access list permit ip 192.168.0.0 split tunnel 255.255.255.0 192.168.30.0 255.255.255.0
access-list acl_out permit icmp any one
acl_out tcp allowed access list any interface outside eq https
acl_out tcp allowed access list any interface outside eq 9333
pager lines 24
opening of session
monitor debug logging
debug logging in buffered memory
ICMP allow any inaccessible outside
Outside 1500 MTU
Within 1500 MTU
IP 1.2.3.4 address outside 255.255.255.248
IP address inside 192.168.0.1 255.255.255.0
alarm action IP verification of information
alarm action attack IP audit
IP local pool vpnPool 192.168.30.10 - 192.168.30.20
PDM logging 100 information
history of PDM activate
ARP timeout 14400
Global 1 interface (outside)
NAT (inside) 0-list of access vpn
NAT (inside) 1 0.0.0.0 0.0.0.0 0 0
public static tcp (indoor, outdoor) interface smtp server1 smtp netmask 255.255.255.255 0 0
public static tcp (indoor, outdoor) interface 5989 192.168.0.2 5989 netmask 255.255.255.255 0 0
public static tcp (indoor, outdoor) interface https server1 https netmask 255.255.255.255 0 0
public static tcp (indoor, outdoor) interface 9333 server2 9333 netmask 255.255.255.255 0 0
Access-group acl_out in interface outside
Route outside 0.0.0.0 0.0.0.0 1.2.3.5 1
Timeout xlate 0:05:00
Timeout conn 01:00 half-closed 0:10:00 udp 0: CPP 02:00 0:10:00 01:00 h225
H323 timeout 0:05:00 mgcp 0: sip from 05:00 0:30:00 sip_media 0:02:00
Timeout, uauth 0:05:00 absolute
GANYMEDE + Protocol Ganymede + AAA-server
RADIUS Protocol RADIUS AAA server
AAA-server local LOCAL Protocol
RADIUS protocol AAA-server raAuth
raAuth AAA-server (host server1 secretkey timeout 5 inside)
RADIUS protocol local AAA server
Enable http server
http 192.168.0.0 255.255.255.0 inside
No snmp server location
No snmp Server contact
SNMP-Server Community public
No trap to activate snmp Server
enable floodguard
Permitted connection ipsec sysopt
Crypto ipsec transform-set strong esp-3des esp-sha-hmac
Crypto-map Dynamics 20 set transformation-strong dynMap
map OutsideMap 10 ipsec-isakmp crypto
card crypto OutsideMap 10 is the vpn address
card crypto OutsideMap 10 set counterpart cottage-pix
map OutsideMap 10 game of transformation-strong crypto
map OutsideMap 20-isakmp ipsec crypto dynamic dynMap
card crypto client OutsideMap of authentication raAuth
OutsideMap interface card crypto outside
ISAKMP allows outside
ISAKMP key * address cottage-pix netmask 255.255.255.255
ISAKMP nat-traversal 20
part of pre authentication ISAKMP policy 9
ISAKMP policy 9 3des encryption
ISAKMP policy 9 sha hash
9 1 ISAKMP policy group
ISAKMP policy 9 life 86400
part of pre authentication ISAKMP policy 20
ISAKMP policy 20 3des encryption
ISAKMP policy 20 chopping sha
20 2 ISAKMP policy group
ISAKMP duration strategy of life 20 86400
vpngroup address vpnPool pool remoteAccess
vpngroup dns-server server1 remoteAccess
vpngroup remoteAccess wins-server server1
vpngroup remoteAccess by default-field domain.local
vpngroup split-tunnel remoteAccess split tunnel
vpngroup idle time 1800 remoteAccess
remoteAccess vpngroup password *.
management-access inside
Console timeout 0
dhcpd outside auto_config
Terminal width 80
Cryptochecksum:9f8a7e0796962279858931db84e4e14a
: endHello
Want to send traffic destined to remote clients, through the tunnel from Site to Site.
The recommendation is to use a different ACL for nat0 and crypto ACL.
Federico.
-
VPN connects but no remote LAN access
Hello
I'll put up on a PIX 501 VPN remote access.
When I try to connect via VPN software, I am able to connect but I am unable to access LAN resources.
I have pasted below part of which seems relevant to my setup. I'm stuck on this issue, could someone help me? Thanks in advance.
ethernet0 nameif outside security0
nameif ethernet1 inside the security100
test.local domain name
name 10.0.2.0 inside
name 10.0.2.13 MSExchange-en
2.2.2.2 the MSExchange-out nameoutside_access_in tcp allowed access list all gt 1023 host 2.2.2.2 eq smtp
outside_access_in list access permit tcp any host 2.2.2.2 eq https
outside_access_in list access permit tcp any host 2.2.2.2 eq www
inside_outbound_nat0_acl 10.0.2.0 ip access list allow 255.255.255.0 192.168.235.0 255.255.255.192
access-list 101 permit icmp any one3.3.3.3 exterior IP address 255.255.255.0
IP address inside 10.0.2.254 255.255.255.0
IP local pool vpn_pool 192.168.235.1 - 192.168.235.15
IP local pool vpn_pool_2 192.168.235.16 - 192.168.235.401 3.3.3.4 (outside) global
NAT (inside) 0-list of access inside_outbound_nat0_acl
NAT (inside) 1 0.0.0.0 0.0.0.0 0 0
static (inside, outside) 2.2.2.2 10.0.2.13 netmask 255.255.255.255 1000 1000
Access-group outside_access_in in interface outside
Route outside 0.0.0.0 0.0.0.0 3.3.3.1 1RADIUS Protocol RADIUS AAA server
AAA-server RADIUS (inside) host 10.0.2.3 * timeout 10
AAA-server local LOCAL ProtocolPermitted connection ipsec sysopt
Crypto ipsec transform-set ESP-3DES-MD5-esp-3des esp-md5-hmac
Crypto-map dynamic dynmap 10 game of transformation-ESP-3DES-MD5
map outside_map 90-isakmp ipsec crypto dynamic dynmap
card crypto outside_map the LOCAL RADIUS client authentication
outside_map interface card crypto outside
ISAKMP allows outside
part of pre authentication ISAKMP policy 20
ISAKMP policy 20 3des encryption
ISAKMP policy 20 md5 hash
20 2 ISAKMP policy group
ISAKMP duration strategy of life 20 86400
vpngroup signal address vpn_pool pool
vpngroup dns-server 10.0.2.3 signal
vpngroup default-field test.local signal
vpngroup idle time 1800 signal
vpngroup max-time 14400 signal
signal vpngroup password *.
vpngroup TF vpn_pool_2 address pool
vpngroup dns-server 10.0.2.3 TF
TF vpngroup default-domain test.local
vpngroup TF 1800 idle time
vpngroup max-time 14400 TF
TF vpngroup password *.Kind regards
Joana
Very similar to the question of the configuration of the switch. You should check if there is no specific roads on the switch outside the default gateway. The switch should route the subnet pool ip to the firewall (10.0.2.254).
-
Network for access to the external interface inside
Hey,.
I have an ASA5520 7.2 (1) I have a few probs with - which is something I struggle with that.
I'm trying to hit a website of a host on the inside network that is actually hosted internally, but decides the static NAT would focus on the external interface of the firewall.
Now I can see the TCP built, translation occurring at a port on the external interface, this port high dialogue to one of the static electricity would be addresses on the external interface, then that's all. There are no more entries in my journal in regards to the connection and I get not syn on the internal web server is so the connection is not back in.
IP address outside 222.x.x.9 255.255.255.248
IP address inside 192.168.87.1 255.255.255.0
Static NAT to Web servers: -.
public static 222.x.x.10 (Interior, exterior) 192.168.87.5
access lists access... :-
list of allowed inbound tcp extended access any host 192.168.87.5 eq http
Access-group interface incoming outside in
Everything works fine when creating a global internet address - just not when address from inside and dynamic PAT is performed to the original address.
Here's a capture session by using the following access to capture list inside and outside interfaces simultaneously
permit for line of web access-list 1 scope ip host 222.222.222.10 all
web access-list extended 2 line ip allow any host 222.222.222.10
on the INSIDE interface (nothing is connected to the outside) (ip addresses have been replaced by nonsense) - but address 222 is would take into account the interface static and the other is on the internal network.
316: 19:14:02.900206 192.168.87.10.2275 > 222.222.222.10.80: S 2029971541:2029971541 (0) win 64512
317: 19:14:05.973185 192.168.87.10.2275 > 222.222.222.10.80: S 2029971541:2029971541 (0) win 64512
192.168.87.10 is my client is trying to connect
Someone of any witch hunt, which is stop this function work?
All networks are directly attached and there is no route summary ancestral anywhere.
I hope you guys can help!
Concerning
Paul.
To my knowledge the ASA supports only hairpining on a VPN tunnel. The security apparatus does not allow traffic that is sent to an interface to go back in the direction of what she received.
-
ACL IP and TCP ACL... What is the difference?
Hello
I have a few questions on the ACL.
1. for PIX ACL, let's say I want to host a Web server in the network internally (just to simplify my question), and I do not PAT, but only a static NAT
public static 202.188.100.1 (Interior, exterior) 10.1.1.1 netmask 255.255.255.0
acl_out tcp allowed access list all 10.1.1.1 eq 80
Access-group acl_out in interface outside
Done the above equivalent to
public static 202.188.100.1 (Interior, exterior) 10.1.1.1 netmask 255.255.255.0
ip access list acl_out permit any 10.1.1.1
Access-group acl_out in interface outside
2. for IOS ACL, is it possible to block A (10.1.1.0/24) network access to network B (10.1.2.0/24) but to allow access from network B to network A? How can I do?
Thank you.
Hello
1. first of all your ACL is a little bad, you need to enable connections to the public of your devices address and not the private sector when allowing traffic from the outside.
The answer to your first question is no, if you don't mind the tcp 80 port in your access list then you allow just that, if you allow ip in your access list then you allow all IP protocols based including all TCP ports, UDP and ICMP ports all.
2. you can do this using either the keyword in your access list or reflexive access lists.
Network B to an ACL
---
IP 10.1.2.0 allow 0.0.0.255 10.1.1.0 0.0.0.255
Network from A to B ACL
---
ip licensing 10.1.1.0 0.0.0.255 10.1.2.0 all created 0.0.0.255
Means that any traffic can pass from network B to network A, however only established connections (packets with the ACK bit value) are admitted from B to A.
The other method is reflexive-list using access which are with State of access lists. When the traffic moves from one network to the other a dynamic access list is created, traffic is only allowed to enter the network source if a dynamic entry is present in the table with the same source and destination IP information. An access list works in a direct, so from A to B, if you wanted to allow B to talk to A you need to configure specific static access list entries.
HTH
PJD
-
IPSec VPN pix 501 no LAN access
I'm trying to set up an IPSec VPN in a basic small business scenario. I am able to connect to my pix 501 via IPSec VPN and browse the internet, but I am unable to ping or you connect to all devices in the Remote LAN. Here is my config:
: Saved
:
6.3 (3) version PIX
interface ethernet0 car
interface ethernet1 100full
nameif ethernet0 WAN security0
nameif ethernet1 LAN security99
enable encrypted password xxxxxxxxxxxxx
xxxxxxxxxxxxxxxxx encrypted passwd
host name snowball
domain xxxxxxxxxxxx.local
clock timezone PST - 8
fixup protocol dns-length maximum 512
fixup protocol ftp 21
fixup protocol h323 h225 1720
fixup protocol h323 ras 1718-1719
fixup protocol http 80
fixup protocol pptp 1723
fixup protocol rsh 514
fixup protocol rtsp 554
fixup protocol sip 5060
fixup protocol sip udp 5060
fixup protocol 2000 skinny
No fixup not protocol smtp 25
fixup protocol sqlnet 1521
fixup protocol tftp 69
names of
acl_in list of access permit udp any any eq field
acl_in list of access permit udp any eq field all
acl_in list access permit tcp any any eq field
acl_in tcp allowed access list any domain eq everything
acl_in list access permit icmp any any echo response
access-list acl_in allow icmp all once exceed
acl_in list all permitted access all unreachable icmp
acl_in list access permit tcp any any eq ssh
acl_in list access permit tcp any any eq www
acl_in tcp allowed access list everything all https eq
acl_in list access permit tcp any host 192.168.5.30 eq 81
acl_in list access permit tcp any host 192.168.5.30 eq 8081
acl_in list access permit tcp any host 192.168.5.22 eq 8081
acl_in list access permit icmp any any echo
access-list acl_in permit tcp host 76.248.x.x a
access-list acl_in permit tcp host 76.248.x.x a
allow udp host 76.248.x.x one Access-list acl_in
access-list acl_out permit icmp any one
ip access list acl_out permit a whole
acl_out list access permit icmp any any echo response
acl_out list access permit icmp any any source-quench
allowed any access list acl_out all unreachable icmp
access-list acl_out permit icmp any once exceed
acl_out list access permit icmp any any echo
Allow Access-list no. - nat icmp a whole
access-list no. - nat ip 192.168.5.0 allow 255.255.255.0 172.16.0.0 255.255.0.0
access-list no. - nat ip 172.16.0.0 allow 255.255.0.0 any
access-list no. - nat permit icmp any any echo response
access-list no. - nat permit icmp any any source-quench
access-list no. - nat icmp permitted all all inaccessible
access-list no. - nat allow icmp all once exceed
access-list no. - nat permit icmp any any echo
pager lines 24
MTU 1500 WAN
MTU 1500 LAN
IP address WAN 65.74.x.x 255.255.255.240
address 192.168.5.1 LAN IP 255.255.255.0
alarm action IP verification of information
alarm action attack IP audit
IP local pool pptppool 172.16.0.2 - 172.16.0.13
PDM logging 100 information
history of PDM activate
ARP timeout 14400
Global (WAN) 1 interface
NAT (LAN) - access list 0 no - nat
NAT (LAN) 1 0.0.0.0 0.0.0.0 0 0
static (LAN, WAN) 65.x.x.37 192.168.5.10 netmask 255.255.255.255 0 0
static (LAN, WAN) 65.x.x.36 192.168.5.20 netmask 255.255.255.255 0 0
static (LAN, WAN) 65.x.x.38 192.168.5.30 netmask 255.255.255.255 0 0
static (LAN, WAN) 65.x.x.39 192.168.5.40 netmask 255.255.255.255 0 0
static (LAN, WAN) 65.x.x.42 192.168.5.22 netmask 255.255.255.255 0 0
static (LAN, WAN) 65.x.x.43 192.168.5.45 netmask 255.255.255.255 0 0
static (LAN, WAN) 65.x.x.44 192.168.5.41 netmask 255.255.255.255 0 0
static (LAN, WAN) 65.x.x.45 192.168.5.42 netmask 255.255.255.255 0 0
static (LAN, WAN) 65.x.x.46 192.168.5.44 netmask 255.255.255.255 0 0
static (LAN, WAN) 65.x.x.41 192.168.5.21 netmask 255.255.255.255 0 0
acl_in access to the WAN interface group
access to the LAN interface group acl_out
Route WAN 0.0.0.0 0.0.0.0 65.x.x.34 1
Timeout xlate 0:05:00
Timeout conn 01:00 half-closed 0:10:00 udp 0: CPP 02:00 0:10:00 01:00 h225
H323 timeout 0:05:00 mgcp 0: sip from 05:00 0:30:00 sip_media 0:02:00
Timeout, uauth 0:05:00 absolute
GANYMEDE + Protocol Ganymede + AAA-server
RADIUS Protocol RADIUS AAA server
AAA-server local LOCAL Protocol
NTP server 72.14.188.195 source WAN
survey of 76.248.x.x WAN host SNMP Server
location of Server SNMP Sacramento
SNMP Server contact [email protected] / * /
SNMP-Server Community xxxxxxxxxxxxx
SNMP-Server enable traps
enable floodguard
the string 1 WAN fragment
Permitted connection ipsec sysopt
Sysopt connection permit-pptp
Crypto ipsec transform-set esp - esp-md5-hmac RIGHT
Crypto-map dynamic dynmap 10 transform-set RIGHT
map mymap 10-isakmp ipsec crypto dynamic dynmap
client configuration address map mymap crypto initiate
client configuration address map mymap crypto answer
card crypto mymap WAN interface
ISAKMP enable WAN
ISAKMP nat-traversal 20
part of pre authentication ISAKMP policy 10
encryption of ISAKMP policy 10
ISAKMP policy 10 md5 hash
10 2 ISAKMP policy group
ISAKMP life duration strategy 10 86400
vpngroup myvpn address pptppool pool
vpngroup myvpn Server dns 192.168.5.44
vpngroup myvpn by default-field xxxxxxxxx.local
vpngroup split myvpn No. - nat tunnel
vpngroup idle 1800 myvpn-time
vpngroup myvpn password *.
Telnet 192.168.5.0 255.255.255.0 LAN
Telnet timeout 5
SSH 192.168.5.0 255.255.255.0 LAN
SSH timeout 30
Console timeout 0
VPDN group pptpusers accept dialin pptp
VPDN group ppp authentication pap pptpusers
VPDN group ppp authentication chap pptpusers
VPDN group ppp mschap authentication pptpusers
VPDN group ppp encryption mppe 128 pptpusers
VPDN group pptpusers client configuration address local pptppool
VPDN group pptpusers customer 192.168.5.44 dns configuration
VPDN group pptpusers pptp echo 60
VPDN group customer pptpusers of local authentication
VPDN username password xxx *.
VPDN username password xxx *.
VPDN enable WAN
dhcpd address 192.168.5.200 - 192.168.5.220 LAN
dhcpd 192.168.5.44 dns 8.8.8.8
dhcpd lease 3600
dhcpd ping_timeout 750
dhcpd enable LAN
username privilege 0 encrypted password xxxxxxxxxx xxxxxxxxxxx
username privilege 0 encrypted password xxxxxxxxxx xxxxxxxxxxx
Terminal width 80
Cryptochecksum:xxxxxxxxxxxxxxxxxx
: end
I'm sure it has something to do with NAT or an access list, but I can't understand it at all. I know it's a basic question, but I would really appreaciate help!Thank you very muchTrevor"No. - nat' ACL doesn't seem correct, please make sure you want to remove the following text:
do not allow any No. - nat icmp access list a whole
No No. - nat ip 172.16.0.0 access list allow 255.255.0.0 any
No No. - nat access list permit icmp any any echo response
No No. - nat access list permit icmp any any source-quench
No No. - nat access list permit all all unreachable icmp
No No. - nat access list do not allow icmp all once exceed
No No. - nat access list only allowed icmp no echo
You must have 1 line as follows:
access-list no. - nat ip 192.168.5.0 allow 255.255.255.0 172.16.0.0 255.255.0.0
Please 'clear xlate' after the changes described above.
In addition, if you have a personal firewall enabled on the host you are trying to connect from the Client VPN, please turn it off and try again. Personal firewall of Windows normally blocks the traffic of different subnets.
Hope that helps.
-
Using VI Server to check whether another executable LabVIEW is running
Hello to you all, helpful people.
I need to have a single executable check LabVIEW if an different LabVIEW executable is running. The simplest way to do seems to be to ask Windows if the name of the executable runs. A good thread is here.
However, this requires the use of a tool (task list) that does not exist on all Windows operating systems I need support (all flavors of XP, Vista and 7). In addition, even if I found an equivalent for each OS, I need to make sure that they continue to work and update my program whenever a new OS was released.
A much better solution would seem to be to use Server VI in LabVIEW, so it is cross-platform. However, despite reading over my printed manuals, by reading lots of subjects in the electronic manual, scanning through the forums and make some limited looking for a manual on the Web site of NOR, I still can't understand the basics of the implementation of a communication server VI between two executables. It's very frustrating, because I'm sure it's a simple task, but I can't find the right instructions.
A lot of instructions to configure a server VI say to go to tools-> Options-> VI Server: Configuration and enable the TCP/IP option. Which seems exaggerated, if I only need communication on a local computer, but ok. However, in other places told me that this sets the default settings for the instance of the main application (another subject I am still unclear on), so how does it apply to my existing LabVIEW project? My current project is an executable, and I thought I would create a new build for the second executable specification. Executable has all my existing code, while B executable would have just a reference VI available server ping, in order for an executable say if it is running.
So I built executable B, and I joined his VI for your reference. Deciding that the VI settings programmatically server configuration will be more comprehensible, I put options that seemed logical: a unique TCP Port number listen to Active = True, TCP/IP access list = IP Address of my computer and the executable = B.vi VI access list.
In my test executable A.i, which I use to this get up and running before changing my main code, I use Open Application references with the IP of my computer, the unique port number and a short timeout. I hooked up to a property App node to determine if I get the correct connection. All I really need is to check the name of the Application and I'm good. However, I keep getting 'LabVIEW.exe.
If anyone call tell me that I forget in this simple configuration, I would be very grateful. Some basics on something else I'm missing about how works the server VI, how the tools-> Options from the settings relate to all, etc., would be a big bonus. Eventually I'll need a way to specify no IP address of the computer (or a way to interrogate LabVIEW), so I can broadcast these two executables on any random PC.
Thank you in advance for your help!
-Joe
P.S. in the preview window that all of my text has run together; I hope sincerely that is not happy when he published, in particular given its length. If so, I apologize!
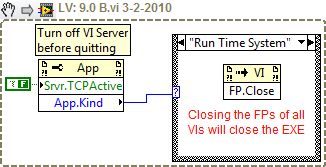
The application ini file should contain the following line:
Server.TCP.Enabled = True
Not to mention that this is a better way to see if your inside an executable file:
Tone
-
connection problems on BB 9500 Storm
Hi, I got a new device right now-9500 Storm. I wrote a simple application that only connects to the server, like this:
_sc = (SecureConnection) Connector.open ("ssl://address
 tro;") deviceside = true");
tro;") deviceside = true");and I can not connect, all the times I had:
Unable to connect net.rim.device.api.io.ConnectionClosedException: closed connection
I put in appropriate under Advanced-> TCP options access point. The browser works. And the server is too late, cause using the same code that I can connect using different devices (8300/8800/8700...).
I do not know the storm unit and I don't know if there is anything else that I need to activate the connections in my applications?
I will be grateful for any suggestion,
Kind regards
Browsers on a BlackBerry could connect on a different course (not direct TCP). You can try the httpdemo and/or socketdemo provided with the BlackBerry JDE? Don't you see the same results with these applications?
-
problem with pix506 and routing
Hi all
I need to make a simple configuration with pix506 with software version 6.3. I need to use it for a class of ip on the external interface for clients that are connected within routing interface. The class outside ip is 10.0.0.x 255.255.255.0; While the Interior is class ip 10.98.98.x 255.255.255.0. I need that inside clients can ping devices of class Pix 506. 10.0.0.x for this? I tried with many examples, but the journey seems does not work. Please check the above example and the diagram attached. Thank you all.
ethernet0 nameif outside security0
nameif ethernet1 inside the security100
interface ethernet0 100basetx
interface ethernet1 100basetx
external IP 10.0.0.35 255.255.255.0
IP address inside 10.98.98.254 255.255.255.0
pixfirewall hostname
ARP timeout 14400
no failover
names of
pager lines 24
debug logging in buffered memory
NAT (inside) 0 10.0.0.35 255.255.255.0
Route outside 0.0.0.0 0.0.0.0 10.0.0.20
access-list acl_out permit icmp any one
Access-group acl_out in interface outside
Timeout xlate 03:00
Timeout conn 01:00 half-closed 0:10:00
UDP 0: CPP 02:00 0:10:00 h323 0:05:00
SIP 0:30:00 sip_media 0:02:00
Timeout, uauth 0:05:00 absolute
No snmp server location
No snmp Server contact
SNMP-Server Community public
Outside 1500 MTU
MTU 1500 ethernet0 nameif inside outside security0
It comes to cisco.
Here are examples:
http://www.Cisco.com/en/us/products/HW/vpndevc/ps2030/prod_configuration_examples_list.html
You must understand the access list. If you do not set the traffic, the traffic is blocked. Look at the following example:
access-list acl_in allow icmp a whole
acl_in list access permit tcp any any eq 80
acl_in tcp allowed access list everything any 20 21 Beach
This example activates the icmp Protocol, application port 80 for Web and the port in the range 20-21 for Active FTP access. All other traffic would be blocked to a refusal. And traffic is actually inside, because you linked this list of access inside the interface interface.
opening of session
host of logging inside x.x.x.x
logging trap debug
Kind regards.
Maik
Maybe you are looking for
-
I just downloaded the latest update to itunes and now my Explorer displays more than 4.5 lines. I tried hovering over the lines as I've done it before and no double arrow to resize vertically. The double horizontal arrows show, but no arrow double ve
-
No sound on my computer device... How do you get her back?
my sound system has disappeared... it says there is no device audio stored on your computer... How can I get my it works again? its an xp (spk 3) (Dow!) but I know that the speakers should play when he saw is turned on... .but just will not play anyt
-
Want 5660 - how to change the date and time
During installation, I thought that I had chosen the date and time. Not happened. After that installation is completed how to make these changes?
-
IllegalStateExecption when you press FolderListener screen
Trying to push a new screen when an e-mail arrives. the application is configured to run at startup. Looks workfine, but the application itself has a FolderListener, which expects an upcoming email, then tries to push a screen. The problem seems to b
-
881w - lost in the wireless configuration. -need help
Hello I'm new with this kind of wifi router. I am quite lost in the configuration, I try to read the documentation, etc... but still he lost. Currently, if I have a notebook wired to 192.168.0.10 I ping my gateway 192.168.0.1 With wifi, I have an IP