Tunnel of Site2Site more
How can I create more site2site tunnel at different locations. I have only a config for a.
version 15.1
no service button
horodateurs service debug datetime msec
Log service timestamps datetime msec
encryption password service
!
XXX host name
!
boot-start-marker
boot-end-marker
!
!
logging buffered 51200 warnings
!
AAA new-model
!
!
AAA authentication login default local
AAA authentication login sdm_vpn_xauth_ml_1 local
AAA authorization exec default local
AAA authorization sdm_vpn_group_ml_1 LAN
!
!
!
!
!
AAA - the id of the joint session
!
clock timezone THIS 1 0
summer time clock THIS recurring last Sun Mar 02:00 last Sun Oct 03:00
dot11 syslog
IP source-route
!
!
!
!
!
IP cef
XXXXXX IP domain name
No ipv6 cef
!
Authenticated MultiLink bundle-name Panel
!
Crypto pki token removal timeout default 0
!
Crypto pki trustpoint TP-self-signed-xxxxxxxxxx
enrollment selfsigned
name of the object cn = IOS-Self-signed-certificate-xxxxxxxxxxx
revocation checking no
!
!
!
Archives
The config log
hidekeys
user name admin secret of privilege 15 5
!
redundancy
!
!
property intellectual ssh version 2
!
!
crypto ISAKMP policy 1
BA 3des
preshared authentication
Group 2
ISAKMP crypto ascom key address XXX.XXX.XXX.XXX
!
!
Crypto ipsec transform-set esp-SHA-ESP-3DES-3des esp-sha-hmac
!
map SDM_CMAP_1 1 ipsec-isakmp crypto
Tunnel GVB description
defined peer XXX.XXX.XXX.XXX
game of transformation-ESP-3DES-SHA
match address 100
!
!
!
!
!
interface FastEthernet0/0
Description * external *.
address IP XXX.XXX.XXX.XXX 255.255.255.240
NAT outside IP
IP virtual-reassembly in
automatic duplex
automatic speed
map SDM_CMAP_1 crypto
!
interface FastEthernet0/1
Description * internal *.
IP 192.168.51.250 255.255.255.0
IP nat inside
IP virtual-reassembly in
IP tcp adjust-mss 1452
automatic duplex
automatic speed
!
!
IP forward-Protocol ND
IP http server
local IP http authentication
IP http secure server
IP http timeout policy slowed down 60 life 86400 request 10000
!
!
IP nat inside source map route SDM_RMAP_1 interface FastEthernet0/0 overload
IP route 0.0.0.0 0.0.0.0 XXX.XXX.XXX.XXX
!
exploitation forest esm config
access-list 1 permit 192.168.51.0 0.0.0.255
access-list 1 permit 192.168.10.0 0.0.0.255
access-list 100 permit ip 192.168.51.0 0.0.0.255 10.94.0.0 0.0.255.255
access-list 100 permit ip 192.168.10.0 0.0.0.255 10.94.0.0 0.0.255.255
access-list 101 deny ip 192.168.51.0 0.0.0.255 10.94.0.0 0.0.255.255
access-list 101 deny ip 192.168.10.0 0.0.0.255 10.94.0.0 0.0.255.255
access-list 101 permit ip 192.168.51.0 0.0.0.255 any
not run cdp
!
!
!
!
allowed SDM_RMAP_1 1 route map
corresponds to the IP 101
!
!
!
!
control plan
!
!
!
Line con 0
line to 0
line vty 0 4
privilege level 15
transport input telnet ssh
!
max-task-time 5000 Planner
Scheduler allocate 20000 1000
end
Hello
You just created a new encryption card, but with a different number, for example:
crypto map SDM_CMAP_1 2 ipsec-isakmp description NEW Tunnel set peer YYY.YYY.YYY.YYY set transform-set ESP-3DES-SHA match address 101
Tags: Cisco Security
Similar Questions
-
I have a setup VPN gateway to gateway between two routers RV042 (do a few reps of low level with them), but I find that I need a little more speed. Will add another connection and set up the DualWAN help?
Any help would be appreciated.
Billy,
A few things you could try to accelerate things through the tunnel from gateway to gateway. The first thing you could try is to disable PFS (perfect forward secrecy) on both sides of the tunnel. The next thing you can do is just be dead peer detection and keep alive enabled on one side of the tunnel. If you have these options activate on both sides of the tunnel, it creates more over the head for the connection. What we are trying to do is to reduce the need for bandwidth for other things and the speed of the transmission of data through the tunnel.
Adding another connection and setting up dual WAN will not tunnel gateway in gateway more speed. The design of the dual Wan must give the network more speed when the sending and receiving of information from the internet. Load Balancing on the Internet. He sends out packets on one side or the other depending on how much support a side. Times dual wan will cause more problems for a tunnel.
Please let me know if it helps
Thank you
Q
-
Hi all
I have some problems with nat/sheep on a pix 515e.
the pix is connected to a tunnel of site2site on the external interface.
the problem is to ping the vpn tunnel to the hosts of the demilitarized zone.
I think it should with a static entry as follows:
static (outside, dmz) 10.43.26.0 10.43.26.0 netmask 255.255.254.0
but in the newspaper, I always get the message:
305005: no outside group translation not found for icmp src: 10.43.27.250 dmz:10.43.100.3 (type 8, code 0) dst
I also tried a nat rule 0 without success.
Then I attached a config performed:
access-list allowed sheep ip 10.0.0.0 255.0.0.0 10.0.0.0 255.0.0.0
access-list allowed sheep ip 10.0.0.0 255.0.0.0 192.168.0.0 255.255.0.0
access-list allowed sheep ip 10.0.0.0 255.0.0.0 200.1.58.0 255.255.255.0
access-list allowed sheep ip 10.0.0.0 255.0.0.0 172.16.0.0 255.255.0.0
IP outdoor 199.99.99.2 255.255.254.0
IP address inside the 10.43.8.12 255.255.240.0
10.43.100.2 dmz IP address 255.255.255.0
Global (outside) 1 199.99.99.11 netmask 255.255.255.255
Global (outside) 1 199.99.99.14 netmask 255.255.255.255
Global (dmz) 1 10.43.100.50 - 10.43.100.98 netmask 255.255.255.0
Global (dmz) 1 10.43.100.99 netmask 255.255.255.0
NAT (inside) 0 access-list sheep
NAT (inside) 1 10.43.0.44 255.255.255.255 0 0
NAT (inside) 1 10.43.8.0 255.255.255.0 0 0
NAT (inside) 1 10.43.9.0 255.255.255.0 0 0
static (inside, outside) 199.99.99.2 tcp telnet 10.43.8.52 telnet netmask 255.255.255.255 0 0
static (inside, dmz) 10.43.8.29 10.43.8.29 netmask 255.255.255.255 0 0
static (inside, dmz) 10.43.8.20 10.43.8.20 netmask 255.255.255.255 0 0
static (dmz, external) 199.99.99.6 10.43.100.6 netmask 255.255.255.255 0 0
public static 199.99.99.7 (Interior, exterior) 10.43.9.56 netmask 255.255.255.255 0 0
public static 199.99.99.5 (Interior, exterior) 10.43.8.53 netmask 255.255.255.255 0 0
static (dmz, external) 199.99.99.4 10.43.100.4 netmask 255.255.255.255 0 0
static (dmz, external) 199.99.99.3 10.43.100.3 netmask 255.255.255.255 0 0
static (outside, dmz) 10.43.26.0 10.43.26.0 netmask 255.255.254.0 0 0
Access-group acl_out in interface outside
acl_in access to the interface inside group
Access-group acl_dmz in dmz interface
any tips?
Thank you
Armin
Without seeing the rest of the config it is difficult to tell you exactly what's happening (IE ACL, sysopt connection ipsec permits etc.)
However, you will need to have a sheep for the DMZ traffic back through the VPN:
IP 10.43.100.0 allow Access-list sheep-dmz 255.255.255.0 10.43.27.0 255.255.255.0
NAT (dmz) access-list sheep-dmz
Also remove the 10.43.26.0 static (outside, dmz) 10.43.26.0 netmask 255.255.254.0 0 0. I see no reason for you to destination NAT.
HTH
-
Thin client SSL VPN (WebVPN) on SAA
I try to config Thin - Client SSL VPN (WebVPN) on the command-line use ASA and ASDM
http://www.Cisco.com/en/us/products/ps6120/products_configuration_example09186a008072462a.shtml
the link applies to ASDM 5.2 and ASA 7.2
I want to config with ASDM 6.3 and ASA 8.2.
I try the command line and I can not find command: port-forward
port-forward portforward 3044 10.2.2.2 telnet Telnet to R1
Do you know how to do with this command ?
I dont find much info about thin-client ssl vpn.
thanks
DuyenHi Alex,
It can be configured by going to Setup > remote access VPN > clientless SSL VPN access > political group and change your WebVPN users group strategy, as you can see:

If I can give you an opinion on it, I would recommend using smart-tunnel-port forwarding because it is getting out of date and you will be able to get the same results with chip-tunnels.
More information on smart-tunnels:
http://www.Cisco.com/en/us/docs/security/ASA/asa82/configuration/guide/WebVPN.html#wp1218044
Kind regards
Nicolas
-
LRT224 impossible to deal simultaneously with more than one VPN tunnel?
We have configured a client to gateway VPN tunnel group and six in the tunnels of single user gateway on a LRT224. Each unique connection works perfectly using Shrew soft client. But when we try to connect with a second tunnel, the first tunnel disconnects. It seems that the LRT224 cannot process more than one VPN tunnel at the same time? Is there any configuration, that we would have missed?
TLR log seem to indicate that the Shrew Soft customers use all 192.168.30.0 that their IP address instead of a random IP address in this range.
Try to set each Shrew Soft client with a specific IP address in the 192.168.30.1 - 50 rank instead of ' use virtual adapter and address randomly.
-
VPN - question of General design for a ut of a router tunnel more
Hello
We have a router that has VPN connections with different partners of our company. VPN remote access were used on computers that are connecting to the different partners of our company.
There has been problems of this kind, that is to say put on both a watchdog and a customer vpn cisco router led to blue-screens on the PC.
The current idea is to put different tunnels from site to site on the router (default gateway of PC clients that connect to the partners). My question is... How our PC to get DHCP addresses on networks of visitors, once the tunnels are up? I guess I'm alittle confused about the address for the PC on our side how will work.
Thanks for your help.
Divide the pool of ip from the internal network, you're going to visit. for example the document below will be exaplain the same configuration in user mode.
-
Another tunnel to the PIX firewall Site2Site
I have PIX 506 Firewall and configured site2site VPN with router on the other side and also remote VPN on PIX and both work well. I want to add an another VPN on PIX site2site with another site router can someone guide me in this regard how accompalish it. I have attached the configuration file.
Mohammed,
Please see the attachment; I changed the configuration and added a 2nd peer IPSec of course you will need to change the remote router accordingly too!
Hope this helps and pls rate post if it isn't.
Jay
-
Another problem with the configuration of Cisco VPN Client access VPN Site2site
We have a Cisco ASA 5505 at our CORP. branch I configured the VPN Site2Site to our COLO with a Juniper SRX220h, to another site works well, but when users access the home Cisco VPN client, they cannot ping or SSH through the Site2Site. JTACS contacted and they said it is not on their end, so I tried to contact Cisco TAC, no support. So here I am today, after for the 3 days (including Friday of last week) of searching the Internet for more than 6 hours per day and try different examples of other users. NO LUCK. The VPN client shows the route secure 10.1.0.0
Sorry to post this, but I'm frustrated and boss breathing down my neck to complete it.
CORP netowrk 192.168.1.0
IP VPN 192.168.12.0 pool
Colo 10.1.0.0 internal ip address
Also, here's an example of my config ASA
: Saved
:
ASA Version 8.2 (1)
!
hostname lwchsasa
names of
name 10.1.0.1 colo
!
interface Vlan1
nameif inside
security-level 100
IP 192.168.1.1 255.255.255.0
!
interface Vlan2
backup interface Vlan12
nameif outside_pri
security-level 0
IP 64.20.30.170 255.255.255.248
!
interface Vlan12
nameif backup
security-level 0
IP 173.165.159.241 255.255.255.248
!
interface Ethernet0/0
switchport access vlan 2
!
interface Ethernet0/1
switchport access vlan 12
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
!
interface Ethernet0/7
!
passive FTP mode
permit same-security-traffic inter-interface
permit same-security-traffic intra-interface
object-group network NY
object-network 192.168.100.0 255.255.255.0
BSRO-3387 tcp service object-group
port-object eq 3387
BSRO-3388 tcp service object-group
port-object eq 3388
BSRO-3389 tcp service object-group
EQ port 3389 object
object-group service tcp OpenAtrium
port-object eq 8100
object-group service Proxy tcp
port-object eq 982
VOIP10K - 20K udp service object-group
10000 20000 object-port Beach
the clientvpn object-group network
object-network 192.168.12.0 255.255.255.0
APEX-SSL tcp service object-group
Description of Apex Dashboard Service
port-object eq 8586
object-group network CHS-Colo
object-network 10.1.0.0 255.255.255.0
the DM_INLINE_NETWORK_1 object-group network
object-network 192.168.1.0 255.255.255.0
host of the object-Network 64.20.30.170
object-group service DM_INLINE_SERVICE_1
the purpose of the ip service
ICMP service object
service-object icmp traceroute
the purpose of the service tcp - udp eq www
the tcp eq ftp service object
the purpose of the tcp eq ftp service - data
the eq sqlnet tcp service object
EQ-ssh tcp service object
the purpose of the service udp eq www
the eq tftp udp service object
object-group service DM_INLINE_SERVICE_2
the purpose of the ip service
ICMP service object
EQ-ssh tcp service object
inside_nat0_outbound to access ip 192.168.1.0 scope list allow 255.255.255.0 clientvpn object-group
inside_nat0_outbound to access ip 192.168.1.0 scope list allow 255.255.255.0 object-group NY
inside_nat0_outbound to access ip 192.168.1.0 scope list allow 255.255.255.0 object-group CHS-Colo
inside_nat0_outbound list of allowed ip extended access any 192.168.12.0 255.255.255.0
outside_pri_1_cryptomap to access ip 192.168.1.0 scope list allow 255.255.255.0 object-group NY
outside_pri_access_in list extended access permit tcp any interface outside_pri eq www
outside_pri_access_in list extended access permit tcp any outside_pri eq https interface
outside_pri_access_in list extended access permit tcp any interface outside_pri eq 8100
outside_pri_access_in list extended access permit tcp any outside_pri eq idle ssh interface
outside_pri_access_in list extended access permit icmp any any echo response
outside_pri_access_in list extended access permit icmp any any source-quench
outside_pri_access_in list extended access allow all unreachable icmp
outside_pri_access_in list extended access permit icmp any one time exceed
outside_pri_access_in list extended access permit tcp any 64.20.30.168 255.255.255.248 eq 8586
levelwingVPN_splitTunnelAcl list standard access allowed 192.168.1.0 255.255.255.0
levelwingVPN_splitTunnelAcl list standard access allowed 10.1.0.0 255.255.255.0
outside_pri_cryptomap to access ip 192.168.1.0 scope list allow 255.255.255.0 object-group CHS-Colo
backup_nat0_outbound list extended access allowed object-group DM_INLINE_NETWORK_1 192.168.12.0 ip 255.255.255.0
outside_pri_cryptomap_1 list extended access allow DM_INLINE_SERVICE_2 of object-group 192.168.1.0 255.255.255.0 10.1.0.0 255.255.255.0
outside_19_cryptomap to access extended list ip 192.168.12.0 allow 255.255.255.0 10.1.0.0 255.255.255.0
inside_nat0_outbound_1 to access ip 192.168.1.0 scope list allow 255.255.255.0 object-group CHS-Colo
VPN-Corp-Colo extended access list permits object-group DM_INLINE_SERVICE_1 192.168.12.0 255.255.255.0 10.1.0.0 255.255.255.0
Note to OUTSIDE-NAT0 NAT0 customer VPN remote site access-list
OUTSIDE-NAT0 192.168.12.0 ip extended access list allow 255.255.255.0 10.1.0.0 255.255.255.0
L2LVPN to access extended list ip 192.168.12.0 allow 255.255.255.0 10.1.0.0 255.255.255.0
pager lines 24
Enable logging
debug logging in buffered memory
exploitation forest asdm warnings
record of the rate-limit unlimited level 4
destination of exports flow inside 192.168.1.1 2055
timeout-rate flow-export model 1
Within 1500 MTU
outside_pri MTU 1500
backup of MTU 1500
local pool LVCHSVPN 192.168.12.100 - 192.168.12.254 255.255.255.0 IP mask
no failover
ICMP unreachable rate-limit 100 burst-size 5
ICMP allow any inside
ICMP allow any outside_pri
don't allow no asdm history
ARP timeout 14400
NAT-control
interface of global (outside_pri) 1
Global 1 interface (backup)
NAT (inside) 0-list of access inside_nat0_outbound
NAT (inside) 0 inside_nat0_outbound_1 list of outdoor access
NAT (inside) 1 0.0.0.0 0.0.0.0
NAT (outside_pri) 0-list of access OUTSIDE-NAT0
backup_nat0_outbound (backup) NAT 0 access list
static TCP (inside outside_pri) interface https 192.168.1.45 https netmask 255.255.255.255 dns
static TCP (inside outside_pri) interface 192.168.1.45 www www netmask 255.255.255.255 dns
static TCP (inside outside_pri) interface 8586 192.168.1.45 8586 netmask 255.255.255.255 dns
static (inside, inside) tcp interface 8100 192.168.1.45 8100 netmask 255.255.255.255 dns
Access-group outside_pri_access_in in the outside_pri interface
Route 0.0.0.0 outside_pri 0.0.0.0 64.20.30.169 1 track 1
Backup route 0.0.0.0 0.0.0.0 173.165.159.246 254
Timeout xlate 03:00
Conn Timeout 0:00:00 half-closed 0:30:00 udp icmp from 01:00 0:00:02
Sunrpc timeout 0:10:00 h323 0:05:00 h225 mgcp from 01:00 0:05:00 mgcp-pat 0:05:00
Sip timeout 0:30:00 sip_media 0:02:00 prompt Protocol sip-0: 03:00 sip - disconnect 0:02:00
Timeout sip-provisional-media 0:02:00 01:00 uauth uauth absolute inactivity from 01:00
timeout tcp-proxy-reassembly 0:01:00
dynamic-access-policy-registration DfltAccessPolicy
AAA authentication enable LOCAL console
AAA authentication http LOCAL console
the ssh LOCAL console AAA authentication
http server enable 981
http 192.168.1.0 255.255.255.0 inside
http 0.0.0.0 0.0.0.0 outside_pri
http 0.0.0.0 0.0.0.0 backup
SNMP server group Authentication_Only v3 auth
SNMP-server host inside 192.168.1.47 survey community lwmedia version 2 c
No snmp server location
No snmp Server contact
Server enable SNMP traps snmp authentication linkup, linkdown cold start
Sysopt connection tcpmss 1200
monitor SLA 123
type echo protocol ipIcmpEcho 216.59.44.220 interface outside_pri
Annex ALS life monitor 123 to always start-time now
Crypto ipsec transform-set ESP-AES-256-SHA 256 - aes - esp esp-sha-hmac
Crypto ipsec transform-set ESP-DES-SHA esp - esp-sha-hmac
Crypto ipsec transform-set ESP-DES-MD5 esp - esp-md5-hmac
Crypto ipsec transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
Crypto ipsec transform-set ESP-3DES-MD5-esp-3des esp-md5-hmac
Crypto ipsec transform-set ESP-AES-128-SHA aes - esp esp-sha-hmac
Crypto ipsec transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
Crypto ipsec transform-set ESP-AES-128-MD5-esp - aes esp-md5-hmac
Crypto ipsec transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
Crypto ipsec transform-set esp-3des-sha1 esp-3des esp-sha-hmac
Crypto ipsec transform-set esp-SHA-ESP-3DES-3des esp-sha-hmac
life crypto ipsec security association seconds 28800
Crypto ipsec kilobytes of life - safety 4608000 association
Crypto ipsec df - bit clear-df outside_pri
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 pfs Group1 set
Crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 value transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA MD5-ESP-3DES ESP-DES-SHA ESP-DES-MD5
card crypto outside_pri_map 1 match address outside_pri_1_cryptomap
card crypto outside_pri_map 1 set pfs
peer set card crypto outside_pri_map 1 50.75.217.246
card crypto outside_pri_map 1 set of transformation-ESP-AES-256-MD5
card crypto outside_pri_map 2 match address outside_pri_cryptomap
peer set card crypto outside_pri_map 2 216.59.44.220
card crypto outside_pri_map 2 the value transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA MD5-ESP-3DES ESP-DES-SHA ESP-DES-MD5
86400 seconds, duration of life card crypto outside_pri_map 2 set security-association
card crypto outside_pri_map 3 match address outside_pri_cryptomap_1
peer set card crypto outside_pri_map 3 216.59.44.220
outside_pri_map crypto map 3 the value transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA MD5-ESP-3DES ESP-DES-SHA ESP-DES-MD5
outside_pri_map card crypto 65535-isakmp dynamic ipsec SYSTEM_DEFAULT_CRYPTO_MAP
card crypto outside_pri_map interface outside_pri
crypto isakmp identity address
ISAKMP crypto enable outside_pri
crypto ISAKMP policy 5
preshared authentication
3des encryption
sha hash
Group 2
life 86400
crypto ISAKMP policy 10
preshared authentication
the Encryption
sha hash
Group 2
life 86400
crypto ISAKMP policy 30
preshared authentication
aes-256 encryption
md5 hash
Group 2
life 86400
crypto ISAKMP policy 50
preshared authentication
aes encryption
md5 hash
Group 2
life 86400
!
track 1 rtr 123 accessibility
Telnet timeout 5
SSH 192.168.1.0 255.255.255.0 inside
SSH timeout 5
Console timeout 0
management-access inside
dhcpd auto_config outside_pri
!
dhcpd address 192.168.1.51 - 192.168.1.245 inside
dhcpd dns 8.8.8.8 8.8.4.4 interface inside
rental contract interface 86400 dhcpd inside
dhcpd field LM inside interface
dhcpd allow inside
!
a basic threat threat detection
statistical threat detection port
Statistical threat detection Protocol
Statistics-list of access threat detection
a statistical threat detection host number rate 2
no statistical threat detection tcp-interception
WebVPN
port 980
allow inside
Select outside_pri
enable SVC
attributes of Group Policy DfltGrpPolicy
VPN-idle-timeout no
Protocol-tunnel-VPN IPSec l2tp ipsec svc webvpn
internal GroupPolicy2 group strategy
attributes of Group Policy GroupPolicy2
Protocol-tunnel-VPN IPSec svc
internal levelwingVPN group policy
attributes of the strategy of group levelwingVPN
Protocol-tunnel-VPN IPSec svc webvpn
Split-tunnel-policy tunnelspecified
value of Split-tunnel-network-list levelwingVPN_splitTunnelAcl
username password encrypted Z74.JN3DGMNlP0H2 privilege 0 aard
aard attribute username
VPN-group-policy levelwingVPN
type of remote access service
rcossentino 4UpCXRA6T2ysRRdE encrypted password username
username rcossentino attributes
VPN-group-policy levelwingVPN
type of remote access service
bcherok evwBWqKKwrlABAUp encrypted password username
username bcherok attributes
VPN-group-policy levelwingVPN
type of remote access service
rscott nIOnWcZCACUWjgaP encrypted password privilege 0 username
rscott username attributes
VPN-group-policy levelwingVPN
sryan 47u/nJvfm6kprQDs password encrypted username
sryan username attributes
VPN-group-policy levelwingVPN
type of nas-prompt service
username, password cbruch a8R5NwL5Cz/LFzRm encrypted privilege 0
username cbruch attributes
VPN-group-policy levelwingVPN
type of remote access service
apellegrino yy2aM21dV/11h7fR password encrypted username
username apellegrino attributes
VPN-group-policy levelwingVPN
type of remote access service
username rtuttle encrypted password privilege 0 79ROD7fRw5C4.l5
username rtuttle attributes
VPN-group-policy levelwingVPN
username privilege 15 encrypted password vJFHerTwBy8dRiyW levelwingadmin
username password nbrothers Amjc/rm5PYhoysB5 encrypted privilege 0
username nbrothers attributes
VPN-group-policy levelwingVPN
clong z.yb0Oc09oP3/mXV encrypted password username
clong attributes username
VPN-group-policy levelwingVPN
type of remote access service
username, password finance 9TxE6jWN/Di4eZ8w encrypted privilege 0
username attributes finance
VPN-group-policy levelwingVPN
Protocol-tunnel-VPN IPSec l2tp ipsec svc webvpn
type of remote access service
IPSec-attributes tunnel-group DefaultL2LGroup
Disable ISAKMP keepalive
tunnel-group 50.75.217.246 type ipsec-l2l
IPSec-attributes tunnel-group 50.75.217.246
pre-shared-key *.
Disable ISAKMP keepalive
type tunnel-group levelwingVPN remote access
tunnel-group levelwingVPN General-attributes
address LVCHSVPN pool
Group Policy - by default-levelwingVPN
levelwingVPN group of tunnel ipsec-attributes
pre-shared-key *.
tunnel-group 216.59.44.221 type ipsec-l2l
IPSec-attributes tunnel-group 216.59.44.221
pre-shared-key *.
tunnel-group 216.59.44.220 type ipsec-l2l
IPSec-attributes tunnel-group 216.59.44.220
pre-shared-key *.
Disable ISAKMP keepalive
!
!
!
Policy-map global_policy
!
context of prompt hostname
Cryptochecksum:ed7f4451c98151b759d24a7d4387935b
: end
Hello
It seems to me that you've covered most of the things.
You however not "said" Configuring VPN L2L that traffic between the pool of VPN and network camp should be in tunnel
outside_pri_cryptomap to access extended list ip 192.168.12.0 allow 255.255.255.0 object-group CHS-Colo
Although naturally the remote end must also the corresponding configurations for users of VPN clients be able to pass traffic to the site of the camp.
-Jouni
-
November 25, 2016, I plugged iPhone 6 s more in my MacBook Pro OS X 10.7.5 and did not have a new folder 'privacy' has been created.
I thought I had a virus.
I deleted everything I couldn't recognize and run check disk permissions repaired several times.
I created a firewall to prevent the virus connects to protect themselves, and I created a master password to prevent the virus to tunnel through everything trying to solve this problem.
Because the permissions log kept referring to Safari, iTunes, and privacy as "ALC found, but should not...» ", I searched and found the records of the private life.
Permissions every time identified another folder in "intimacy", I would delete it.
Journal system kept recording 'questionable' property, but I am the only user and administrator only this computer never had.
Thought an upgrade to Yosemite might solve the problem, but now my computer will only allow me to sign with my username and password but doesn't recognize me as a user/administrator.
Without any authorization, I cannot install a work-around and plugged my phone in case it would be to recreate the problem and I hope I can regain control of back in.
The phone requires an update to iTunes, but I know now that the download of an update will not fix the permissions, it gives just another protocol of permission, that I can't answer an installation.
Everything works fine except that I have to use data instead of wifi to connect.
Any hope of help here?
[Sorry to add this note: Please do not respond if your overall response is to criticize me for doing things by ignorance.] [I already know that.]
Thank you.
Brenda Miller
Back up your data to external storage at least once and preferably twice, preferably disassemble and disconnect one of the backup copies to avoid chances of overwriting your data, then wipe the boot disk and reinstall OS X from a current copy of 10.7.5 then migrate your data from your backup. Treat this as a new-to-you Mac.
-
Could not load the driver for Teredo Tunneling Pseudo-Interface
Hello
Does anyone know how to fix this problem (Vista) Business
Product
Teredo Tunneling Pseudo-InterfaceProblem
Could not load driver softwareDescription
Windows was able to successfully install device driver software, but the driver has encountered a problem when he tried to run. The problem code is 10.Signature of the problem
Problem event name: PnPDeviceProblemCode
Architecture: x 86
Hardware ID: * TUNMP
Configure the class GUID: {4d36e972-e325-11ce-bfc1-08002be10318}
The PnP problem code: 0000000-a
Driver name: tunmp.sys
Driver version: 6.0.6000.16386
Driver date: 02/11/2006
OS version: 6.0.6000.2.0.0.256.6
Locale ID: 2057Additional information about the problem
Bucket ID: 12121968Concerning
DaveHi Dave
Can you please give us more information on your laptop and what is happening exactly?
-
SSL Tunneling Application outgoing failure
Outgoing SSL Tunneling Application error Hello dear colleagues,
I have UTM5 with the latest firmware. The unit works fine now with 3 VLANS / subnets, routing inter - VLAN, SSL VPN configuration, etc. I have an interesting question, but probably one of these questions to someone else experienced and solved (I hope).Medical practice I have set this up for actually needs of outgoing VPN tunnel/SSL. I encouraged the VPN on UTM protocols so the initial remote OUTGOING connection goes off flawlessly and allows users to authenticate. My question is when we try to show the remote Citrix server/published apps page. I get an error "request the Tunneling SSL - Failed to connect to server" . I know that the issue must be understood with the ProSecure UTM because I've temporarily removed the UTM equation and put in a D-Link DIR - 655 and Citrix published apps portal page launches very well. I am able to launch a published application and function normally. I pass on the D-Link with the Prosecure and I get the same question.
I really don't understand what prevents to launch published applications page.
I'd be more than happy to provide more information that I need to solve this problem.
Not that it is important, but all endpoint devices are XPSP3/IE8. Yet once, shouldn't matter that customers can bring to the top of the published page no problem when the D-Link is used.
Thank you
MEDADIT, I've really hemmed and best enemy cela and managed to get a solution in place. Curious, if you have an idea on the terminal services question license I have known which I'll explain a little.
So, I have disabled HTTPS scanning as you said and it helped the citrix portal page to come; However, the user received an error of connection application failure when they launched an app on the page. The error said that there are not enough licenses available Terminal Server. I am as there is no way in hell that all licenses are in use.
So I completely disconnected from the remote network via SSL - VPN and not connected from my home network this site remote to see if I would have the same result and no problems to launch the applications of the portal page... basically no problem license Terminal Server services. I tried connecting from the prosecure and received the same error message.
I wanted to keep HTTPS enabled analysis despite connect it secure by nature implemented with 443, so I spotted around based on your advice and added 4 remote domains to exclusions scan tab (my eyes completely spent during this 1st 10 x (very annoying). I tested the outgoing connection and it helped me successfully citrix portal page, but applications would not launch successfully. I received once again the same error of license to the Terminal Server services, but we expected it because it didn't start with the scanning to disabled .
so I connected to the remote network and thought that I would allow my client to its remote desktop RDP access. I have configured RDP on his computer to Office XP and the connected failed. I thought at this stage that he had something to do with trying to RDP through the Microsoft UAG gateway used by the remote site. Rather than trying to work through sets of rules with the specialist support network out there, we decided to allow my client to run an IP network connector dry which was all ready helped the UAG. This enabled him successfully to RDP to his remote desktop and run any distance needed applications on the remote network.
So, it's not what I really wanted to do. I really want to start individual applications of the closed Citrix portal page, but why this issue licenses arose himself the Terminal Server services is a mystery to me. The specialist in support of the remote side has been also blocked down there. He informed me that he has other clients that connect out through boxes of CISCO ASA and they have any problems launches applications of the portal page. If they scan you 80/443 traffic is not relevant because I disabled it completely on the UTM and it did not help.
So any thoughts on that would be great and I once again thank you for your expertise.
-
Through tunnels of automatic indexation to write data files?
Hello
I use neither-controller to control a servo and position and torque data collection. I want to write data to the TDMS files.
Recently, I learned about the design of producer/consumer model and I thought it would be a good approach to ensure that writing the files didn't slow down my timed loop of data collection.
However, I also realized that my program seems to work well if I wire the data that I collect the tunnels of automatic indexation. Can I use a structure that executes only after the entire collection of data is made to write the charts that I built to TDMS files.
Is there a reason that would make the last method against? Can the tunnels of idexing auto slow my loop enough to concern him? I collect only about 5,000 points of data for each channel.
See you soon,.
Kenny
In my opinion, the main consideration is timing. If you use consumers/producers, you essentially make writing while the data collection process is "pending" the next item to collect. It should be the case that the consumption will be faster than production, so at any time, 99% of the data are already written, Yes (perhish forbid!) if the program crashes, you already have most of the data on the disk. fo
Alternatively, you can use the tunnels and send an array of 5000 points (from the tunnel exit) for the writing process. This requires it to be rather than parallel series - no writing occurs until all the 5000 points are generated, and the writing process, instead of is almost as soon as it starts, takes 5000 times longer (more or less).
The series is 'simpler', especially for a beginner. The producer/consumer, if you understand the design model, would be my preference.
BS
-
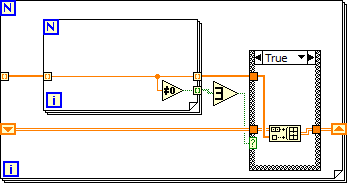
alternative to the option conditional tunnel (for LV 2011)
Hello
I created a VI in 2013 LV that uses a conditional tunnel in a loop for.
Unfortunately the PC I did the VI for running LV 2011, where the conditional tunnel option is not yet implemented.
so so, I build a work around:
with this workaround it takes much longer until the loop ends over the solution of the condtional tunnel.
an idea to work around the problem better/more fast?
I strongly suggest you to install the add-on OpenG your LabVIEW and the use of the Tunnel VI of conditional automatic indexing they provide in their palette. This has been implemented before LabVIEW added functionality and he worked many years.
It works essentially incrementing through indices real values in an array of Booleans and out the corresponding indices in the input array.
Edit: What you're doing are almost exactly what the code gets converted to when you register for the previous version as Aputman said. The only drawback to this is that you cannot use the parallelism because of the shift register. If you try to process a lot of data, run the loop with all the clues to get out (with parallelism) and post-process the array using the add-on OpenG.
-
TEREDO TUNNELING PSEUDO-INTERFACE DEVICE DOES NOT WORK CORRECTLY - ACCORDING TO AVG PC TUNE UP
My laptop is a HP G7030EA - MS Windows Vista Home Basic 32-bit SP2 Intel Pentium Dual CPU T2330 @ 1.60 GHz, 1.0 GB RAM, Mobile Intel 965 Express Chipset Family, bought new in February 2008. I have not changed any hardware, software, etc. I do not use it for games, only for things such as e-mails and visit websites
Until last month when my desktop computer broke, I used the laptop only occasionally as a backup of the computer. It never quite worked and seems to be unable to handle several tasks at once, often taking minutes for Google to load. When I get impatient and click the mouse too much I heard a horrible noise and the screen mouse cursor freeze for a minute or two.
As the laptop has become my main computer at the moment, I downloaded AVG PC Tune Up to see if it would improve it performance has not helped. I was surprised to see how much memory the AVG2013 anti virus program uses, but wonder if the speed of connection and freezing problems I experience result (AVG Tune Up conclusions on) the Teredo Tunneling pseudo-interface unit does not properly.
I follow AVG on screen re boards: looking for a software driver update but none was found, and I got the message "the best driver for your device software is already installed. Windows has determined that the driver software for your device is up-to-date, Tun Miniport, Microsoft Map.
This left me confused. If there is a problem with this device, no solution seems to exist.
Any help that will allow my laptop to function normally is welcome.
I understand that you want to know if the teredo adapter can cause performance problems.
The teredo adapter should not cause performance problems. It is really just used to allow devices work IPv4 with IPv6 Internet service provider. If the ISP was using IPv6 and your system did not have the adapter teredo, so it wouldn't work properly with the service provider. For now, IPv6 is a significant minority that the world continues to work on IPv4 as not all networks, Internet service providers, and businesses are not entirely passed to IPv6.
This thread on the Microsoft forums goes into a little more detail about the adapter teredo including how to disable it so that you only see it in Device Manager. Unless you are using IPv6, this shouldn't really be a problem.
If you start in safe mode, the performance problem persists? Turn on the computer and press F8 once per second for the Mode option, safe mode with networking. This will help you to further isolate the performance problem.
Furthermore, does this happen that the adapter is connected or not?
-
The calculator program working if the second number is more than 1 digit.
I was setting up a calculator on labview, which works except for when I entered that a second number of the calculator does not have the correct value if the second number is more than 1 digit. I think it's down to the use of shift registers and result of the operation is forgotten when a key is pressed. I joined the program, if someone could confirm that this is the problem / suggest potential ways around this problem that would be a great help
RavensFan wrote:
Use default if Unwired. Several of your tunnels are defined in this way, including the orange wire (double-precision) where you store your first operand.
If you run an event where a wire is not connected through the tunnel will display by default (empty for string, double zero) and the shift register will then forget what he was originally in it.
I think you meant not to use the default value if Unwired? I think you have to tell him to use linked entry Tunnel--> Create and wire Unwired cases instead?
Maybe you are looking for
-
Hello Last month, I got a strange problem with my Firefox browser in certain situations. The question is only apparent when executing some 3D games (most often when I run Diablo III). Each time these games is loaded my Firefox browser works incredibl
-
Failure of installing free config - Satellite P300-1EJ
Hello By updating the Config free on my Satellite P300, I got the following error message: Database: transformation: cannot update row that does not exist. Table. Feature. Help, please.
-
All necessary recovery for Satellite 2450 CD
Had to restore my laptop to factory settings, but find that the registry has been damaged. is it possible to have a new game and how much it costs.Your reallyE.R.Tubb PS. e-mail [email protected]
-
Display does not work on Satellite P500-1DZ
Hello P500-1dz screen went black. No sign of anything whatsoever on the screen so haven't tried a new screen. Still no display.Equip new inverter. Still no display. Replaced the Ribbon to the back of the monitor cable.Still nothing. Hooked on the VGA
-
Microsoft XML Core Services 4.0 Service Pack 2 (KB973688)
Cannot install someone can help? Kiko of Microsoft XML Core Services 4.0 Service Pack 2 (KB973688)