Web server converstion keeps failing
I tried to convert a windows2003 ent. Server Web for a week now and it keeps failing. I managed Converter 2 other web servers w / same features. The machine sometimes fails to 1 - 2% other times it faulty 20-35%. I tried to use the Converter 3.0.3 and 4.0.0 Converter (both are standalone versions).
Here's the catch. I'm not allowed to stop IIS during the conversion. I don't know if it's important but guess he could.
The 1st web area converted to 6 hours approximately. It hosts the only site that is rarely used.
2nd box hosts 15 web sites - this conversion took about 100-120 hours (5 days)? but finished and I check the virtual machine and it seems to work (it will start and data is there)-have not yet been fully tested.
The 3rd area web hosting 80 sites + and will not convert. Once again, it is estimated to be about 5 days and fails to about 20-35%. I just tried to convert by using Converter 4 and again once it failed about 10 minutes in.
* Attached are 2 files - the zipped file is 4.0 conversion that doesn't have 10 minutes. -the .txt file is the conversion of 3.0.3 which failed to 22%.
I see in your converter agent log
NfcNetTcpRead: timeout of waiting for data
NfcFssrvrRecv: failed with code = 9
NfcFssrvr_DiskIo: have not received a response of e/s
DISKLIB-LIB: RWv failed ioId: #150 (290) (34).
4641 writing on the destination volume error
BackgroundWriter::ThreadFunc: write failure.
NFC errors related to the network and can come from a variety of network related components.
Here's more on what is the cause and what you need to do: http://kb.vmware.com/kb/1004615
Tags: VMware
Similar Questions
-
Web Server Configuration tool fails
I remove Coldfusion MX 6.1 "works" of Windows XP Professional and installed MX 7. Met an error when installing on the wall of fire problems possible preventing complete installation.
I went to the Web Server Configuration tool to configure IIS. When I clicked on the Add button, I get the following message:
Could not connect to JRun/ColdFusion servers on host localhost. Possible causes: server not - running performer and fire wall blocking JNDI - restriction in security.properties host.
I have disabled virus protection and Firewall window also well off the coast.
I've reconfigured the jrun.xml and ColdFusion runs on its own server, but I wanted it on IIS for some tests.
Thanks in advance.
Mike
> Yes is all three. I ran the two instructions that you gave me and this is the result.
Finally, we could be something. Follow the link bpurcell.org that I have given above and scroll down to the bottom. You will see a post about Windows XP SP2 and socks.
Apparently, there's a limit to how many socks open authorized on the operating systems such as Windows XP SP2 and Windows 2003 SP1. If we believe that, then your problem is caused by Windows XP. The default behavior of the wsconfig tool is to analyze all ports in the range of 2900-3000, exceeding of Windows XP SP socks limited.
A solution would be to run wsconfig with a limited number of ports scanned. Follow these steps and then on the command line:
C:\CFusionMX7\runtime\jre\bin\java.exe-DWSConfig.PortScanStartPort=2920-DWSConfig.PortScanCount=1-jar C:\CFusionMX7\runtime\lib\wsconfig.jar
-
Rapidwiz upgrade to R12.2 - Web Server pre-installation verification failed
Hello people.
I'm on the right track to improve my EBS 12.1.3 to R12.2. I did all the pre-reqs/patch before the upgrade according to the DOC: Oracle E-Business Suite Upgrade Guide version 12.0 and 12.1 to 12.2 E48839-02 Réf..
Finally, I run rapidwiz. However, after entering all the required values, when rapidwiz reached the status of control system, after doing several checks he stuck on 'Web server pre-installation check failed ".
System check the status showing window continues same message for 2 hours. For more information please see the screenshot below.
Please, let me know where rapidwiz creates log file so that I can investigate the reason to fail. Also, please try to fix this.
Thank you!
Ali
Checksums MD5 for R12.2 Quick Install Media (Doc ID 1505510.1) helped me to solve the mentioned problem.
Thank you
Ali Raza Memon
-
NEITHER Application Web server refuses to be activated
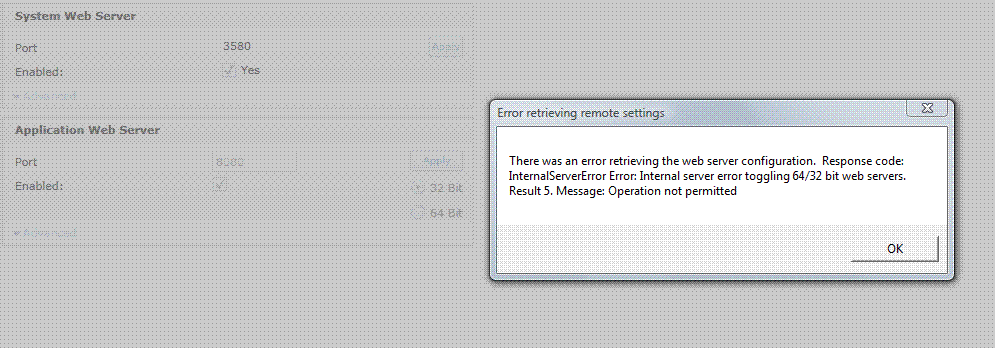
I am trying to deploy a web service in LabVIEW 2010 and it fails to deploy in saying that the Web of Application service OR work...
If I connect to http://localhost:3580, log in as Admin (empty password) and click on the page of web servers. I put the server to Application Web 8080 port, click on the check box turn on... then click apply - and the only thing that happens is that the browser displays the error on the page symbol in the status bar... There is not 'yes', showing next to the Enable checkbox for the web server of the system...
So - if I start again from zero and do the same thing, but also click the 32-bit option button before hitting the button apply - what is happening? Well, I get an error dialog box:
The service itself (32-bit, 64-bit is registered but not also started) runs according to the services control panel...
I'm stuck... If anyone knows what is missing here, is there something I am doing wrong, or something that must be done before activating the application service?
Uninstalling and reinstalling 32-bit LabVIEW 2010 on two different computers revealed that the problem appeared only on my Vista 64 bits - not the Windows 7 32-bit macine macine...
By looking at the services that are running on the machine with the problem that I could see that he was running the 32-bit version of the application Web server, had a 64-bit installed but disabled--but--only the latter has been fixed to depend on the Web Server service of NOR. This seemed a bit strange that the 32-bit version on the 32-bit computer was dependent on the Web server of OR...
So - I disabled the 32 bit Server Web Application service OR, turned on the 64-bit... and - I am now able to configure the Web application server to start.
Why so the 32 and 64-bit application Web services installed, with only 32 bit one running-, but not properly? This happens to everyone, but everyone arranges it by opting for the 64-bit version... or is there something that causes the installation get messed up?
-
I'm running Win 7 and I was trying to set up two accounts different wireless setting - home and hotspot, one for each type of internet connection used. Somehow, I screwed up the initial settings in the 'built-in Web server' and don't know how to access again to make the changes. My printer just keeps giving me 0.0.0.0. I'm unable to access the last URL I had for the Assembly of the House.
If more information is needed, please let me know as I am new to this forum. Thanks for any help you provide.
Live, love, laugh and calculateHello
Please see the document below to install the printer wireless.
-
cant access built-in web server on HP6940 due to the new router
New router has IP 192.168.2.1
Changed Deskjet 6940 IP 192.168.2.60 and it turned off... fails to 192.168.1.3 to the power upward and can not find network using IP or hostname
Hoe can I access the Web server integrated to change the IP address without having to reinstall everything... seem to have misplaced the installation CD
Thank you
Chris
Solved the problem of the IP address as follows:
Connected a spare laptop router.
Changed router IP to 192.168.1.1
Printer plugged into router
Could then access printer Web Server to 192.168.1.3
Changed printer IP for 192.168.2.6
Printer is now accessible on the network
-
asa5512 V8.6 nat web server cannot access
Hi all
asa5512 V8.6 nat web server cannot access.
my home pc can access www.cisco.com, but external client cannot access my web server inside...
all of my config, I do not know what is wrong.
Thank youe help.
ciscoasa #.
See the ciscoasa # running
ciscoasa # show running-config
: Saved
:
ASA 1.0000 Version 2
!
ciscoasa hostname
activate 2KFQnbNIdI.2KYOU encrypted password
2KFQnbNIdI.2KYOU encrypted passwd
names of
!
interface GigabitEthernet0/0
nameif outside
security-level 0
address IP XXX1 255.255.255.240
!
interface GigabitEthernet0/1
Shutdown
No nameif
no level of security
no ip address
!
interface GigabitEthernet0/2
Shutdown
No nameif
no level of security
no ip address
!
interface GigabitEthernet0/3
Description link to 3560 G0/1
Speed 1000
full duplex
nameif inside
security-level 100
192.168.1.13 IP address 255.255.255.0
!
interface GigabitEthernet0/4
Shutdown
No nameif
no level of security
no ip address
!
interface GigabitEthernet0/5
Shutdown
No nameif
no level of security
no ip address
!
interface Management0/0
nameif management
security-level 100
IP 192.168.100.1 address 255.255.255.0
!
!
time-range k3used
absolute starting 08:00 January 1, 2008
daily periodical 0:00 to 23:59
periodical daily 09:00-18:00
!
passive FTP mode
clock timezone BeiJing 8
network object obj - 192.168.1.0
subnet 192.168.1.0 255.255.255.0
network object obj - 192.168.200.0
192.168.200.0 subnet 255.255.255.0
network object obj - 192.168.1.2
host 192.168.1.2
network object obj - 192.168.1.2 - 01
host 192.168.1.2
network object obj - 192.168.1.19
Home 192.168.1.19
network object obj - 192.168.1.20
host 192.168.1.20
network object obj - 192.168.1.88
Home 192.168.1.88
network object obj - 192.168.1.1
host 192.168.1.1
network object obj - 192.168.1.2 - 02
host 192.168.1.2
network object obj - 192.168.1.6
host 192.168.1.6
object obj - X.X.X.3 network
Home X.X.X.3
object obj-tcp-source-eq-25 service
tcp source eq smtp service
obj-tcp-source-eq-110 service object
tcp source eq Microsoft pop3 service
object obj - X.X.X.10 network
Home X.X.X.10
obj-tcp-source-eq-8086 service object
tcp source eq 8086 service
obj-tcp-source-eq-80 service object
tcp source eq www service
network object obj - 192.168.1.1 - 01
host 192.168.1.1
obj-tcp-source-eq-3389 service object
source eq 3389 tcp service
obj-tcp-source-eq-9877 service object
tcp source eq 9877 service
obj-tcp-source-eq-21 service object
tcp source eq ftp service
object obj-tcp-source-eq-20 service
tcp source eq ftp service - data
network object obj - 192.168.2.88
Home 192.168.2.88
network object obj - 192.168.2.88 - 01
Home 192.168.2.88
network object obj - 192.168.2.88 - 02
Home 192.168.2.88
network object obj - 192.168.1.19 - 01
Home 192.168.1.19
network object obj - 192.168.2.2
host 192.168.2.2
network object obj - 192.168.2.2 - 01
host 192.168.2.2
network object obj - 192.168.2.2 - 02
host 192.168.2.2
network object obj - 192.168.3.2
host 192.168.3.2
network object obj - 192.168.3.2 - 01
host 192.168.3.2
network object obj - 192.168.3.2 - 02
host 192.168.3.2
object obj - X.X.X.9 network
Home X.X.X.9
obj-tcp-source-eq-8087 service object
tcp source eq 8087 service
network object obj - 192.168.1.200
host 192.168.1.200
network object obj - 192.168.1.200 - 01
host 192.168.1.200
network object obj - 192.168.1.30
host 192.168.1.30
network object obj - 192.168.1.30 - 01
host 192.168.1.30
network object obj - 192.168.1.1 - 02
host 192.168.1.1
object obj - X.X.X.6 network
Home X.X.X.6
obj-tcp-source-eq-8088 service object
tcp source eq 8088 service
network object obj - 192.168.3.5
Home 192.168.3.5
network object obj - 192.168.3.5 - 01
Home 192.168.3.5
network object obj - 192.168.3.5 - 02
Home 192.168.3.5
network object obj - 192.168.3.5 - 03
Home 192.168.3.5
network object obj - 192.168.3.5 - 04
Home 192.168.3.5
network object obj - 192.168.2.0
Subnet 192.168.2.0 255.255.255.0
network object obj - 192.168.3.0
subnet 192.168.3.0 255.255.255.0
network object obj - 192.168.4.0
subnet 192.168.4.0 255.255.255.0
network object obj - 192.168.5.0
192.168.5.0 subnet 255.255.255.0
network object obj - 192.168.6.0
192.168.6.0 subnet 255.255.255.0
network object obj - 192.168.7.0
192.168.7.0 subnet 255.255.255.0
network object obj - 192.168.8.0
192.168.8.0 subnet 255.255.255.0
vpn_list to access ip 192.168.1.0 scope list allow 255.255.255.0 192.168.200.0 255.255.255.0
vpn_list to access extended list ip 192.168.200.0 allow 255.255.255.0 192.168.1.0 255.255.255.0
access-list 101 extended deny ip any host 58.215.78.113
access-list 101 extended deny ip any host 61.139.126.81
access-list 101 extended deny ip any host 61.152.94.154
access-list 101 extended allow host ip 192.168.4.2 all
access-list 101 extended allow host ip 192.168.4.3 all
access-list 101 extended allow host ip 192.168.4.4 all
access-list 101 extended allow host ip 192.168.4.5 all
access-list 101 extended allow host ip 192.168.4.7 everything
access-list 101 extended permit ip host 192.168.4.8 all
access-list 101 extended permit ip host 192.168.4.9 all
access-list 101 extended permit ip host 192.168.4.10 all
access-list 101 extended allow host ip 192.168.4.11 all
access-list 101 extended allow host ip 192.168.4.12 all
access-list 101 extended allow host ip 192.168.4.13 all
access-list 101 extended allow host ip 192.168.4.14 all
access-list 101 extended allow host ip 192.168.4.15 all
access-list 101 extended allow host ip 192.168.4.16 all
access-list 101 extended allow host 192.168.4.18 ip everything
access-list 101 extended allow host ip 192.168.4.19 all
access-list 101 extended allow host ip 192.168.4.20 all
access-list 101 extended allow host ip 192.168.4.180 all
access-list 101 extended deny ip 192.168.4.0 255.255.255.0 any
access-list 101 extended allow host ip 192.168.2.176 all
access-list 101 extended allow icmp a whole
access-list 101 extended allow host ip 192.168.2.3 everything
access-list 101 extended allow host ip 192.168.2.164 all
access-list 101 extended allow host ip 192.168.2.171 all
access-list 101 extended allow host ip 192.168.2.142 all
access-list 101 extended allow host ip 192.168.2.180 all
access-list 101 extended allow host ip 192.168.2.149 all
access-list 101 extended allow host ip 192.168.2.201 all
access-list 101 extended allow host ip 192.168.2.170 all
access-list 101 extended allow host ip 192.168.2.168 all
access-list 101 extended allow host ip 192.168.2.103 everything
access-list 101 extended allow host ip 192.168.2.34 all
access-list 101 extended allow host ip 192.168.2.174 all
access-list 101 extended allow host ip 192.168.2.199 all
access-list 101 extended allow host ip 192.168.2.253 everything
access-list 101 extended allow host ip 192.168.2.236 all
access-list 101 extended allow host ip 192.168.2.214 all
access-list 101 extended allow host ip 192.168.2.110 everything
access-list 101 extended allow host ip 192.168.2.127 all
access-list 101 extended allow host ip 192.168.2.178 all
access-list 101 extended allow host ip 192.168.2.21 all
access-list 101 extended allow host ip 192.168.2.24 all
access-list 101 extended allow host ip 192.168.2.251 all
access-list 101 extended allow host ip 192.168.2.33 all
access-list 101 extended allow host ip 192.168.2.120 all
access-list 101 extended allow host ip 192.168.2.85 all
access-list 101 extended allow host ip 192.168.2.137 all
access-list 101 extended allow host ip 192.168.2.113 all
access-list 101 extended allow ip 192.168.2.20 host everything
access-list 101 extended allow host ip 192.168.2.101 everything
access-list 101 extended allow host ip 192.168.2.106 all
access-list 101 extended allow host ip 192.168.2.140 all
access-list 101 extended allow host ip 192.168.2.215 all
access-list 101 extended allow host ip 192.168.2.107 all
access-list 101 extended allow host ip 192.168.2.234 all
access-list 101 extended allow host ip 192.168.2.15 all
access-list 101 extended allow host ip 192.168.2.55 all
access-list 101 extended allow host ip 192.168.2.41 all
access-list 101 extended permit ip host 192.168.2.13 all
access-list 101 extended allow host ip 192.168.2.133 everything
access-list 101 extended allow host ip 192.168.2.73 all
access-list 101 extended allow host ip 192.168.2.172 all
access-list 101 extended allow host ip 192.168.2.175 all
access-list 101 extended allow host ip 192.168.2.88 all
access-list 101 extended allow host ip 192.168.2.188 all
access-list 101 extended allow host ip 192.168.2.136 all
access-list 101 extended allow host ip 192.168.2.74 all
access-list 101 extended allow host ip 192.168.2.12 everything
access-list 101 extended allow host ip 192.168.2.100 everything
access-list 101 extended allow host ip of 192.168.2.102 everything
access-list 101 extended allow host ip 192.168.2.152 all
access-list 101 extended allow ip 192.168.2.4 host everything
access-list 101 extended allow host ip 192.168.2.5 everything
access-list 101 extended allow host ip 192.168.2.6 everything
access-list 101 extended allow host ip 192.168.2.14 all
access-list 101 extended allow host ip 192.168.2.19 all
access-list 101 extended permit ip host 192.168.2.16 all
access-list 101 extended allow host ip 192.168.2.17 all
access-list 101 extended allow host ip 192.168.2.18 all
access-list 101 extended allow host ip 192.168.2.22 all
access-list 101 extended allow host ip 192.168.2.23 all
access-list 101 extended allow host ip 192.168.2.115 all
access-list 101 extended allow host ip 192.168.2.116 all
access-list 101 extended allow host ip 192.168.2.117 all
access-list 101 extended allow host ip 192.168.2.118 all
access-list 101 extended allow host ip 192.168.2.119 all
access-list 101 extended allow host ip 192.168.2.150 all
access-list 101 extended allow host ip 192.168.2.128 all
access-list 101 extended deny ip 192.168.2.0 255.255.255.0 any
access-list 101 extended allow ip 192.168.3.2 host everything
access-list 101 extended allow host ip 192.168.3.3 everything
access-list 101 extended permit ip host 192.168.3.4 everything
access-list 101 extended allow host ip 192.168.3.5 all
access-list 101 extended allow host ip 192.168.3.6 all
access-list 101 extended allow host ip 192.168.3.7 all
access-list 101 extended allow host ip 192.168.3.8 all
access-list 101 extended allow host ip 192.168.3.9 all
access-list 101 extended allow host ip 192.168.3.10 everything
access-list 101 extended allow host ip 192.168.3.11 all
access-list 101 extended allow host ip 192.168.3.12 all
access-list 101 extended allow host ip 192.168.3.13 all
access-list 101 extended allow host ip 192.168.3.14 all
access-list 101 extended allow host ip 192.168.3.15 everything
access-list 101 extended allow host ip 192.168.3.16 all
access-list 101 extended allow host ip 192.168.3.17 everything
access-list 101 extended allow host ip 192.168.3.18 all
access-list 101 extended allow host ip 192.168.3.19 all
access-list 101 extended allow host ip 192.168.3.20 everything
access-list 101 extended permit ip host 192.168.3.21 all
access-list 101 extended allow host ip 192.168.3.22 all
access-list 101 extended allow host ip 192.168.3.23 all
access-list 101 extended allow host ip 192.168.3.24 everything
access-list 101 extended allow host ip 192.168.3.25 all
access-list 101 extended allow host ip 192.168.3.26 all
access-list 101 extended allow host ip 192.168.3.27 all
access-list 101 extended allow host ip 192.168.3.28 all
access-list 101 extended allow host ip 192.168.3.29 all
access-list 101 extended allow host ip 192.168.3.30 all
access-list 101 extended allow host ip 192.168.3.31 all
access-list 101 extended allow host ip 192.168.3.32 all
access-list 101 extended allow host ip 192.168.3.33 all
access-list 101 extended allow host ip 192.168.3.34 all
access-list 101 extended allow host ip 192.168.3.35 all
access-list 101 extended allow host ip 192.168.3.36 all
access-list 101 extended allow host ip 192.168.3.37 all
access-list 101 extended allow host ip 192.168.3.38 all
access-list 101 extended allow host ip 192.168.3.39 all
access-list 101 extended allow host ip 192.168.3.40 all
access-list 101 extended allow host ip 192.168.3.41 all
access-list 101 extended allow host ip 192.168.3.42 all
access-list 101 extended allow host ip 192.168.3.43 all
access-list 101 extended allow host ip 192.168.3.86 all
access-list 101 extended allow host ip 192.168.3.88 all
access-list 101 extended allow host ip 192.168.3.89 all
access-list 101 extended allow host ip 192.168.3.56 all
access-list 101 extended allow host ip 192.168.3.55 all
access-list 101 extended allow host ip 192.168.3.96 all
access-list 101 extended allow host ip 192.168.3.97 all
access-list 101 extended allow host ip 192.168.3.98 all
access-list 101 extended allow host ip 192.168.3.116 all
access-list 101 extended allow host ip 192.168.3.111 all
access-list 101 extended allow host ip 192.168.3.175 all
access-list 101 extended allow host ip 192.168.3.176 all
access-list 101 extended allow host ip 192.168.3.201 all
access-list 101 extended allow host ip 192.168.3.202 all
access-list 101 extended allow host ip 192.168.3.203 all
access-list 101 extended allow host ip 192.168.3.204 all
access-list 101 extended allow host ip 192.168.3.205 all
access-list 101 extended allow host ip 192.168.3.206 all
access-list 101 extended allow host ip 192.168.3.207 all
access-list 101 extended allow host ip 192.168.3.208 all
access-list 101 extended allow host ip 192.168.3.209 all
access-list 101 extended allow host ip 192.168.3.210 all
access-list 101 extended allow host ip 192.168.3.213 all
access-list 101 extended allow host ip 192.168.3.214 all
access-list 101 extended allow host ip 192.168.3.215 all
access-list 101 extended allow host ip 192.168.3.101 all
access-list 101 extended allow host ip 192.168.3.102 all
access-list 101 extended allow host ip 192.168.3.103 all
access-list 101 extended allow host ip 192.168.3.106 all
access-list 101 extended allow host ip 192.168.3.107 all
access-list 101 extended allow host ip 192.168.3.152 all
access-list 101 extended allow host ip 192.168.3.151 all
access-list 101 extended allow host ip 192.168.3.153 all
access-list 101 extended allow host ip 192.168.3.195 all
access-list 101 extended allow host ip 192.168.3.45 all
access-list 101 extended allow host ip 192.168.3.46 all
access-list 101 extended allow host ip 192.168.3.199 all
access-list 101 extended allow host ip 192.168.3.157 all
access-list 101 extended refuse 192.168.3.0 ip 255.255.255.0 any
access-list 101 extended allow tcp a whole
access list 101 scope ip allow a whole
vpnclient_splitTunnelAcl list standard access allowed 192.168.1.0 255.255.255.0
2 extended access-list permit ip 192.168.2.0 255.255.255.0 any
3 extended access-list allow ip 192.168.3.0 255.255.255.0 any
4 extended access-list allow ip 192.168.4.0 255.255.255.0 any
access-list extended 500 k permit ip host XXX1 everything
access-list extended 500 k allow icmp host XXX1 everything
access-list 102 extended allow host ip 192.168.1.6 everything
access-list extended 100 permit tcp any host 192.168.1.1 eq www
access-list extended 100 permit tcp any host 192.168.1.1 eq 8080
access-list extended 100 permit tcp any host X.X.X.4
access-list extended 100 permit ip any host X.X.X.4
access-list extended 100 permit icmp any host X.X.X.4
access-list extended 100 permit tcp any host 192.168.1.6 eq smtp
access-list extended 100 permit tcp any host 192.168.1.6 eq pop3
access-list extended 100 permit tcp any host 192.168.1.6 eq www
access-list extended 100 permit tcp any host 192.168.1.6
access-list 100 scope ip allow any host 192.168.1.6
access-list extended 100 permit icmp any host 192.168.1.6
access-list extended 100 permit tcp any host 192.168.1.19 eq 3389
access-list extended 100 permit tcp any host 192.168.1.20 eq 3389
access-list extended 100 permit tcp any host 192.168.1.88 eq 3389
access-list extended 100 permit tcp any host X.X.X.12
access-list extended 100 permit ip any host X.X.X.12
access-list extended 100 permit icmp any host X.X.X.12
access-list extended 100 permit tcp any host 192.168.1.6 eq 8086
access-list extended 100 permit tcp any host 192.168.1.1 eq 3389
access-list extended 100 permit tcp any host 192.168.1.6 eq 3389
access-list extended 100 permit tcp any host 192.168.1.6 eq ftp
access-list extended 100 permit tcp any host 192.168.1.6 eq ftp - data
access-list extended 100 permit tcp any host 192.168.2.88 eq 3389
access-list extended 100 permit tcp any host 192.168.2.88 eq 12172
access-list extended 100 permit tcp any host 192.168.2.2 eq 3389
access-list extended 100 permit tcp any host 192.168.2.2 eq 9116
access-list extended 100 permit tcp any host 192.168.3.2 eq 25243
access-list extended 100 permit tcp any host 192.168.3.2 eq 3389
access-list extended 100 permit tcp any host 192.168.1.200 eq www
access-list extended 100 permit tcp any host 192.168.1.200 eq 12001
access-list extended 100 permit tcp any host 192.168.1.30 eq 3389
access-list extended 100 permit tcp any host 192.168.3.5 eq 4160
access-list extended 100 permit tcp any host 192.168.3.5 eq 11111
access-list extended 100 permit tcp any host 192.168.3.5 eq 3389
access-list extended 100 permit tcp any host X.X.X.10
access-list extended 100 permit udp any host 192.168.2.88 eq 12172
access-list extended 100 permit udp any host 192.168.2.2 eq 9116
access-list extended 100 permit udp any host 192.168.3.2 eq 25243
access-list extended 100 permit udp any host 192.168.3.5 eq 4170
access-list extended 100 permit udp any host 192.168.3.5 eq 11111
access-list extended 100 permit ip any host X.X.X.10
access-list extended 100 permit tcp any host 192.168.1.6 eq 8087
access-list extended 100 permit tcp any host X.X.X.9
access-list extended 100 permit ip any host X.X.X.9
access-list extended 100 permit tcp any host 192.168.1.30 eq www
access-list extended 100 permit tcp any host X.X.X.5
access-list extended 100 permit ip any host X.X.X.5
access-list extended 100 permit icmp a whole
access-list extended 100 permit tcp any host 192.168.1.6 eq 8088
access-list extended 100 permit ip any host X.X.X.6
access-list extended 100 permit tcp any host X.X.X.6
access list extended 100 permit tcp host 61.186.169.129 host 192.168.1.2 eq 5872 times-range k3used
access list extended 100 permit tcp host 61.186.169.129 host 192.168.1.2 eq 8088 times-range k3used
access list extended 100 permit tcp host 61.186.169.129 host 192.168.1.2 eq 3389 times-range k3used
allowed extended access list 100 tcp host 61.186.169.129 host 192.168.1.19 eq www time-range k3used
access-list extended 100 permit tcp host 61.186.169.129 X.X.X.2 time-range k3used
access list extended 100 permit tcp host 61.186.169.130 host 192.168.1.2 eq 5872 times-range k3used
access list extended 100 permit tcp host 61.186.169.130 host 192.168.1.2 eq 8088 times-range k3used
access list extended 100 permit tcp host 61.186.169.130 host 192.168.1.2 eq 3389 times-range k3used
allowed extended access list 100 tcp host 61.186.169.130 host 192.168.1.19 eq www time-range k3used
access-list extended 100 permit tcp host 61.186.169.130 X.X.X.2 time-range k3used
access list extended 100 permit tcp host 61.186.169.131 host 192.168.1.2 eq 5872 times-range k3used
access list extended 100 permit tcp host 61.186.169.131 host 192.168.1.2 eq 8088 times-range k3used
access list extended 100 permit tcp host 61.186.169.131 host 192.168.1.2 eq 3389 times-range k3used
allowed extended access list 100 tcp host 61.186.169.131 host 192.168.1.19 eq www time-range k3used
access-list extended 100 permit tcp host 61.186.169.131 X.X.X.2 time-range k3used
access list extended 100 permit tcp host 61.186.169.132 host 192.168.1.2 eq 5872 times-range k3used
access list extended 100 permit tcp host 61.186.169.132 host 192.168.1.2 eq 8088 times-range k3used
access list extended 100 permit tcp host 61.186.169.132 host 192.168.1.2 eq 3389 times-range k3used
allowed extended access list 100 tcp host 61.186.169.132 host 192.168.1.19 eq www time-range k3used
access-list extended 100 permit tcp host 61.186.169.132 X.X.X.2 time-range k3used
access list extended 100 permit tcp host 61.186.169.133 host 192.168.1.2 eq 5872 times-range k3used
access list extended 100 permit tcp host 61.186.169.133 host 192.168.1.2 eq 8088 times-range k3used
access list extended 100 permit tcp host 61.186.169.133 host 192.168.1.2 eq 3389 times-range k3used
allowed extended access list 100 tcp host 61.186.169.133 host 192.168.1.19 eq www time-range k3used
access-list extended 100 permit tcp host 61.186.169.133 X.X.X.2 time-range k3used
access-list extended 100 permit ip host 61.186.169.129 X.X.X.2 time-range k3used
access-list extended 100 permit ip host 61.186.169.130 X.X.X.2 time-range k3used
access-list extended 100 permit ip host 61.186.169.131 X.X.X.2 time-range k3used
access-list extended 100 permit ip host 61.186.169.132 X.X.X.2 time-range k3used
access-list extended 100 permit ip host 61.186.169.133 X.X.X.2 time-range k3used
access-list extended 100 permit icmp host 61.186.169.129 X.X.X.2 time-range k3used
access-list extended 100 permit icmp host 61.186.169.130 X.X.X.2 time-range k3used
access-list extended 100 permit icmp host 61.186.169.131 X.X.X.2 time-range k3used
access-list extended 100 permit icmp host 61.186.169.132 X.X.X.2 time-range k3used
access-list extended 100 permit icmp host 61.186.169.133 X.X.X.2 time-range k3used
access list extended 100 permit tcp host 183.64.106.194 host 192.168.1.2 eq 5872 times-range k3used
access list extended 100 permit tcp host 183.64.106.194 host 192.168.1.2 eq 8088 times-range k3used
access list extended 100 permit tcp host 183.64.106.194 host 192.168.1.2 eq 3389 times-range k3used
allowed extended access list 100 tcp host 183.64.106.194 host 192.168.1.19 eq www time-range k3used
access-list extended 100 permit tcp host 183.64.106.194 X.X.X.2 time-range k3used
access-list extended 100 permit ip host 183.64.106.194 X.X.X.2 time-range k3used
access-list extended 100 permit icmp host 183.64.106.194 X.X.X.2 time-range k3used
access list extended 100 permit tcp host 183.64.106.195 host 192.168.1.2 eq 5872 times-range k3used
access list extended 100 permit tcp host 183.64.106.195 host 192.168.1.2 eq 8088 times-range k3used
access list extended 100 permit tcp host 183.64.106.195 host 192.168.1.2 eq 3389 times-range k3used
allowed extended access list 100 tcp host 183.64.106.195 host 192.168.1.19 eq www time-range k3used
access-list extended 100 permit tcp host 183.64.106.195 X.X.X.2 time-range k3used
access-list extended 100 permit ip host 183.64.106.195 X.X.X.2 time-range k3used
access-list extended 100 permit icmp host 183.64.106.195 X.X.X.2 time-range k3used
access list extended 100 permit tcp host 14.107.162.32 host 192.168.1.2 eq 5872 times-range k3used
access list extended 100 permit tcp host 14.107.162.32 host 192.168.1.2 eq 8088 times-range k3used
access list extended 100 permit tcp host 14.107.162.32 host 192.168.1.2 eq 3389 times-range k3used
allowed extended access list 100 tcp host 14.107.162.32 host 192.168.1.19 eq www time-range k3used
access-list extended 100 permit tcp host 14.107.162.32 X.X.X.2 time-range k3used
access-list extended 100 permit ip host 14.107.162.32 X.X.X.2 time-range k3used
access-list extended 100 permit icmp host 14.107.162.32 X.X.X.2 time-range k3used
access list extended 100 permit tcp host 14.107.247.121 host 192.168.1.2 eq 5872 times-range k3used
access list extended 100 permit tcp host 14.107.247.121 host 192.168.1.2 eq 8088 times-range k3used
access list extended 100 permit tcp host 14.107.247.121 host 192.168.1.2 eq 3389 times-range k3used
allowed extended access list 100 tcp host 14.107.247.121 host 192.168.1.19 eq www time-range k3used
access-list extended 100 permit tcp host 14.107.247.121 X.X.X.2 time-range k3used
access-list extended 100 permit ip host 14.107.247.121 X.X.X.2 time-range k3used
access-list extended 100 permit icmp host 14.107.247.121 X.X.X.2 time-range k3used
access list extended 100 permit tcp host 61.128.208.106 host 192.168.1.2 eq 5872 times-range k3used
access list extended 100 permit tcp host 61.128.208.106 host 192.168.1.2 eq 8088 times-range k3used
access list extended 100 permit tcp host 61.128.208.106 host 192.168.1.2 eq 3389 times-range k3used
allowed extended access list 100 tcp host 61.128.208.106 host 192.168.1.19 eq www time-range k3used
access-list extended 100 permit tcp host 61.128.208.106 X.X.X.2 time-range k3used
access-list extended 100 permit ip host 61.128.208.106 X.X.X.2 time-range k3used
access-list extended 100 permit icmp host 61.128.208.106 X.X.X.2 time-range k3used
access-list 100 extended tcp refuse any host 192.168.1.2 eq 5872
access-list 100 extended tcp refuse any host 192.168.1.2 eq 8088
access-list 100 extended tcp refuse any host 192.168.1.2 eq 3389
access-list 100 extended tcp refuse any host 192.168.1.19 eq www
access-list 100 extended tcp refuse any host X.X.X.2
access-list extended 100 deny ip any host X.X.X.2
access-list extended 100 refuse icmp any host X.X.X.2
pager lines 24
Outside 1500 MTU
Within 1500 MTU
management of MTU 1500
IP local pool 192.168.200.1 - 192.168.200.20 mask 255.255.255.0 vpn_pool
ICMP unreachable rate-limit 1 burst-size 1
don't allow no asdm history
ARP timeout 14400
NAT (inside, all) source static obj - obj - 192.168.1.0 destination 192.168.1.0 static obj - 192.168.200.0 obj - 192.168.200.0 non-proxy-arp
NAT (inside, all) source static obj - 192.168.200.0 obj - 192.168.200.0 destination static obj - 192.168.1.0 obj - 192.168.1.0 non-proxy-arp
NAT (inside, outside) source static obj - 192.168.1.6 obj - X.X.X.3 service obj-tcp-source-eq-25 obj-tcp-source-eq-25
NAT (inside, outside) source static obj - 192.168.1.6 obj - X.X.X.3 service obj-tcp-source-eq-110 obj-tcp-source-eq-110
NAT (inside, outside) source static obj - 192.168.1.6 obj - X.X.X.10 service obj-tcp-source-eq-8086 obj-tcp-source-eq-80
NAT (inside, outside) source static obj - 192.168.1.6 obj - X.X.X.10 service obj-tcp-source-eq-3389 obj-tcp-source-eq-9877
NAT (inside, outside) source static obj - 192.168.1.6 obj - X.X.X.10 service obj-tcp-source-eq-21 obj-tcp-source-eq-21
NAT (inside, outside) source static obj - 192.168.1.6 obj - X.X.X.10 service obj-tcp-source-eq-20 obj-tcp-source-eq-20
NAT (inside, outside) source static obj - 192.168.1.6 obj - X.X.X.9 service obj-tcp-source-eq-8087 obj-tcp-source-eq-80
NAT (inside, outside) source static obj - 192.168.1.6 obj - X.X.X.6 service obj-tcp-source-eq-8088 obj-tcp-source-eq-80
NAT (inside, outside) source static obj - 192.168.1.6 obj - X.X.X.3 service obj-tcp-source-eq-80 obj-tcp-source-eq-80
NAT (inside, outside) source dynamic obj - 192.168.1.6 obj - X.X.X.3
!
network object obj - 192.168.1.0
NAT dynamic interface (indoor, outdoor)
network object obj - 192.168.200.0
NAT dynamic interface (indoor, outdoor)
network object obj - 192.168.1.2
NAT (inside, outside) Static X.X.X.2 5872 5872 tcp service
network object obj - 192.168.1.2 - 01
NAT (inside, outside) Static X.X.X.2 8088 8088 tcp service
network object obj - 192.168.1.19
NAT (inside, outside) Static X.X.X.12 tcp 3389 8001 service
network object obj - 192.168.1.20
NAT (inside, outside) Static X.X.X.12 tcp 3389 8002 service
network object obj - 192.168.1.88
NAT (inside, outside) Static X.X.X.12 tcp 3389 12345 service
network object obj - 192.168.1.1
NAT (inside, outside) Static X.X.X.4 tcp www www service
network object obj - 192.168.1.2 - 02
NAT (inside, outside) Static X.X.X.2 service tcp 3389 8005
network object obj - 192.168.1.1 - 01
NAT (inside, outside) Static X.X.X.10 tcp 3389 9876 service
network object obj - 192.168.2.88
NAT (inside, outside) Static X.X.X.10 tcp 3389 3129 service
network object obj - 192.168.2.88 - 01
NAT (inside, outside) Static X.X.X.10 12172 12172 tcp service
network object obj - 192.168.2.88 - 02
NAT (inside, outside) Static X.X.X.10 service udp 12172 12172
network object obj - 192.168.1.19 - 01
NAT (inside, outside) Static X.X.X.2 service tcp www 8056
network object obj - 192.168.2.2
NAT (inside, outside) Static X.X.X.10 3389 3128 tcp service
network object obj - 192.168.2.2 - 01
NAT (inside, outside) Static X.X.X.10 9116 9116 tcp service
network object obj - 192.168.2.2 - 02
NAT (inside, outside) Static X.X.X.10 service udp 9116 9116
network object obj - 192.168.3.2
NAT (inside, outside) Static X.X.X.10 25243 25243 tcp service
network object obj - 192.168.3.2 - 01
NAT (inside, outside) Static X.X.X.10 service udp 25243 25243
network object obj - 192.168.3.2 - 02
NAT (inside, outside) Static X.X.X.10 tcp 3389 3130 service
network object obj - 192.168.1.200
NAT (inside, outside) Static X.X.X.10 service tcp www 1114
network object obj - 192.168.1.200 - 01
NAT (inside, outside) Static X.X.X.10 12001 12001 tcp service
network object obj - 192.168.1.30
NAT (inside, outside) Static X.X.X.5 tcp www www service
network object obj - 192.168.1.30 - 01
NAT (inside, outside) Static X.X.X.10 tcp 3389 9878 service
network object obj - 192.168.1.1 - 02
NAT (inside, outside) Static X.X.X.4 8080 8080 tcp service
network object obj - 192.168.3.5
NAT (inside, outside) Static X.X.X.10 4160 4160 tcp service
network object obj - 192.168.3.5 - 01
NAT (inside, outside) Static X.X.X.10 service udp 4170 4170
network object obj - 192.168.3.5 - 02
NAT (inside, outside) Static X.X.X.10 11111 11111 tcp service
network object obj - 192.168.3.5 - 03
NAT (inside, outside) Static X.X.X.10 tcp 3389 3127 service
network object obj - 192.168.3.5 - 04
NAT (inside, outside) Static X.X.X.10 11111 11111 udp service
network object obj - 192.168.2.0
NAT dynamic interface (indoor, outdoor)
network object obj - 192.168.3.0
NAT dynamic interface (indoor, outdoor)
network object obj - 192.168.4.0
NAT dynamic interface (indoor, outdoor)
network object obj - 192.168.5.0
NAT dynamic interface (indoor, outdoor)
network object obj - 192.168.6.0
NAT dynamic interface (indoor, outdoor)
network object obj - 192.168.7.0
NAT dynamic interface (indoor, outdoor)
network object obj - 192.168.8.0
NAT dynamic interface (indoor, outdoor)
Access-group 100 in external interface
Access-group 101 in the interface inside
Route outside 0.0.0.0 0.0.0.0 X.X.X.14 1
Route inside 192.168.2.0 255.255.255.0 192.168.1.12 1
Route inside 192.168.3.0 255.255.255.0 192.168.1.12 1
Route inside 192.168.4.0 255.255.255.0 192.168.1.12 1
Route inside 192.168.5.0 255.255.255.0 192.168.1.12 1
Route inside 192.168.6.0 255.255.255.0 192.168.1.12 1
Timeout xlate 03:00
Timeout conn 01:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
Sunrpc timeout 0:10:00 h323 0:05:00 h225 mgcp from 01:00 0:05:00 mgcp-pat 0:05:00
Sip timeout 0:30:00 sip_media 0:02:00 prompt Protocol sip-0: 03:00 sip - disconnect 0:02:00
Timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
Floating conn timeout 0:00:00
dynamic-access-policy-registration DfltAccessPolicy
identity of the user by default-domain LOCAL
Enable http server
No snmp server location
No snmp Server contact
Server enable SNMP traps snmp authentication linkup, linkdown warmstart of cold start
Crypto ipsec transform-set esp - esp-md5-hmac ikev1 vpn_set
Crypto-map dynamic vpn_map 10 set transform-set vpn_set ikev1
Crypto-map dynamic vpn_map 10 the value reverse-road
vpnmap 10 card crypto ipsec-isakmp dynamic vpn_map
vpnmap interface card crypto outside
Crypto ikev1 allow outside
IKEv1 crypto policy 1
preshared authentication
the Encryption
md5 hash
Group 2
life 86400
IKEv1 crypto policy 65535
preshared authentication
3des encryption
sha hash
Group 2
life 86400
Telnet 0.0.0.0 0.0.0.0 inside
Telnet 192.168.1.0 255.255.255.0 inside
Telnet timeout 5
SSH 0.0.0.0 0.0.0.0 outdoors
SSH timeout 30
SSH version 1
Console timeout 0
a basic threat threat detection
Statistics-list of access threat detection
no statistical threat detection tcp-interception
Server NTP 192.43.244.18
internal group vpnclient strategy
vpnclient group policy attributes
value of server DNS 61.128.128.68
Ikev1 VPN-tunnel-Protocol
Split-tunnel-policy tunnelspecified
value of Split-tunnel-network-list vpnclient_splitTunnelAcl
cisco 3USUcOPFUiMCO4Jk encrypted password username
type tunnel-group vpn_group remote access
tunnel-group vpn_group General-attributes
address vpn_pool pool
Group Policy - by default-vpnclient
vpn_group group of tunnel ipsec-attributes
IKEv1 pre-shared-key *.
!
class-map 500 k
matches the access list 500 k
class-map inspection_default
match default-inspection-traffic
class-map 2
matches the access list 2
PAM-class 3
matches the access list 3
class-map 4
corresponds to the list of access-4
!
!
type of policy-card inspect dns preset_dns_map
parameters
maximum message length automatic of customer
message-length maximum 512
Policy-map global_policy
class inspection_default
inspect the preset_dns_map dns
inspect the ftp
inspect h323 h225
inspect the h323 ras
Review the ip options
inspect the netbios
inspect the rsh
inspect the rtsp
inspect the skinny
inspect esmtp
inspect sqlnet
inspect sunrpc
inspect the tftp
inspect the sip
inspect xdmcp
Policy-map 500 k
500 k class
Policy-map 2
class 2
class 3
class 4
!
global service-policy global_policy
context of prompt hostname
remote anonymous reporting call invites 2
call-home
Profile of CiscoTAC-1
no active account
http https://tools.cisco.com/its/service/oddce/services/DDCEService destination address
email address of destination [email protected] / * /
destination-mode http transport
Subscribe to alert-group diagnosis
Subscribe to alert-group environment
Subscribe to alert-Group 13 monthly periodic inventory
Subscribe to alert-group configuration periodic monthly 13
daily periodic subscribe to alert-group telemetry
Cryptochecksum:ecead54d7c85807eb47c7cdaf7d7e82a
: end
ciscoasa# $
ciscoasa #.
ciscoasa #.
Hello
You have changed the source IP address of the order I suggested?
There is no reason to use the 192.168.1.1 IP address as the source of this command "packet - trace" that the source will NEVER be this IP address, because it is a private IP not routable on the public Internet.
Then you can try with the order I suggested.
entry Packet-trace out tcp 1.1.1.1 12345 61.186.236.4 80
I guess that the above command / test failed because you were using the real server IP address as the IP source for the test.
-Jouni
-
DMZ web server-> inside the database server
Suppose that a network topology looks like this:
A PIX with 3 interfaces:
interface (private public static IP 10.10.10.1) interface (public static IP of 69.110.38.35) interface (static IP private address of the 30.30.30.1) --------------------------------------------
The internal network has a {server} with the IP address of 10.10.10.2.
The DMZ has a {web server} with the IP address of 30.30.30.2.
I will welcome external guests (outside) access to the web server (30.30.30.2) via port 80.
This web server access turn the database server (10.10.10.2).
Assume that all other commands are issued. Then, I'll create an access list that allows server WWW DMZ to communicate with inside the database server.
access-list dmz-to-inside permit tcp host 30.30.30.2 host 10.10.10.2 eq 1521
Should I publish the following, too:
(1) access-list dmz permit tcp host 30.30.30.2 no matter what 80 eq
(2) access-group in interface dmz dmz
(3) static (inside the dmz) 10.10.10.0 10.10.10.0 netmask 255.255.255.0
xlate clear 4)
If so, what each of them do?
Thank you for helping.
Scott
1. Yes, the static statement "10.10.10.0 static (inside, dmz) 10.10.10.0 netmask 255.255.255.0" will disable NAT. Although it is not necessary to disable nat, however, it saves money and simple to manage. the reason for this is the traffic between the dmz and inside is private, there is therefore not necessary to apply the public ip address.
2 pix receives the package intended to 30.30.30.2 10.10.10.2. PIX examines the static statement and based on the static above statement, pix will not nat package (i.e. pix will leave the soruce address be) and send it to 30.30.30.2 via the interface of the demilitarized zone.
for example
original package - source 10.10.10.2, destination 30.30.30.2
After pix - source 10.10.10.2, destination 30.30.30.2
3. the "Clear xlate" command must be issued whenever the nat/global or static has been added/deleted/modified. This command is to force the pix to clear the existing ip translation.
for example, before you add the command "static 1.1.1.1 (indoor, outdoor) 192.168.1.100 netmask 255.255.255.255", the pix may already have an ip 192.168.1.100 translation (it might come from the nat/global). now, after you apply the static command, the pix will keep the existing translation for a certain period time. 'clear xlate' is needed to erase the old translation and so to activate the new static statement.
-
External HTTP > internal to the web server
Hello
I have a router ADSL with a public IP assigned, preforming NAT. This leads to a 506th PIX which leads to a Web server. The entire interior of the ADSL is on private IP addresses.
I want to allow external users access to the Web server on port 80.
I inwardly and outwardly put up ICMP connectivity (for testing only) and it works correctly.
I created a virtual server on the ADSL router that forwards port 80 traffic to the external interface of the web server. It has worked successfully for half an hour and then something in the config changed PIX and it no longer works. Here is my config PIX
SH conf
: Saved
: Written by xxxxx at 08:41:10.001 NZST Thursday, October 13, 2005
6.3 (4) version PIX
interface ethernet0 car
Auto interface ethernet1
ethernet0 nameif outside security0
nameif ethernet1 inside the security100
enable the encrypted password xxxxxxxx
xxxxxxxxx encrypted passwd
hostname PIX
domain ciscopix.com
clock timezone GMT
fixup protocol dns-length maximum 512
fixup protocol ftp 21
fixup protocol h323 h225 1720
fixup protocol h323 ras 1718-1719
fixup protocol http 80
icmp protocol error correction
fixup protocol rsh 514
fixup protocol rtsp 554
fixup protocol sip 5060
fixup protocol sip udp 5060
fixup protocol 2000 skinny
fixup protocol smtp 25
fixup protocol sqlnet 1521
fixup protocol tftp 69
no names
name 192.168.5.3 PixExt
name PixInt 192.168.6.1
name 192.168.5.1 ADSLInt
name 192.168.6.2 WebExt
acl1 list access permit icmp any any echo response
access-list acl1 allow icmp all once exceed
access-list icmp permitted acl1 everything all inaccessible
acl1 list access permit tcp any host 192.168.6.2 eq www
pager lines 22
opening of session
timestamp of the record
Record being buffered memory errors
logging trap notifications
ICMP allow all outside
ICMP allow any inside
Outside 1500 MTU
Within 1500 MTU
external IP 192.168.5.3 255.255.255.0
IP address inside 192.168.6.1 255.255.255.0
alarm action IP verification of information
alarm action attack IP audit
location of PDM 192.168.6.2 255.255.255.255 inside
PDM logging 100 information
history of PDM activate
ARP timeout 14400
NAT (inside) 0 192.168.6.0 255.255.255.0 0 0
Access-group acl1 in external interface
Route outside 0.0.0.0 0.0.0.0 192.168.5.1 1
Timeout xlate 0:05:00
Timeout conn 01:00 half-closed 0:10:00 udp 0: CPP 02:00 0:10:00 01:00 h225
H323 timeout 0:05:00 mgcp 0: sip from 05:00 0:30:00 sip_media 0:02:00
Timeout, uauth 0:05:00 absolute
GANYMEDE + Protocol Ganymede + AAA-server
AAA-server GANYMEDE + 3 max-failed-attempts
AAA-server GANYMEDE + deadtime 10
RADIUS Protocol RADIUS AAA server
AAA-server RADIUS 3 max-failed-attempts
AAA-RADIUS deadtime 10 Server
AAA-server local LOCAL Protocol
Enable http server
http 192.168.1.0 255.255.255.0 inside
http 192.168.6.2 255.255.255.255 inside
No snmp server location
No snmp Server contact
SNMP-Server Community public
No trap to activate snmp Server
enable floodguard
Telnet timeout 5
SSH timeout 5
Console timeout 0
dhcpd lease 3600
dhcpd ping_timeout 750
xxxxx xxxxxxx privilege 15 encrypted password username
Terminal width 80
Cryptochecksum:xxxx
DMZInside (config) # route sh
outside 0.0.0.0 0.0.0.0 192.168.5.1 1 ANOTHER static
outside 192.168.5.0 255.255.255.0 192.168.5.3 1 static CONNECTION
inside 192.168.6.0 255.255.255.0 192.168.6.1 1 static CONNECTION
DMZInside (config) #.
No idea where I have gone wrong?
Thank you.
you are missing this statement
public static 192.168.6.2 (Interior, exterior) 192.168.6.2
Thank you
Nadeem
-
How can I publish 9 Captivate to a web server?
I placed the project in my disk space (according to the recommendations of this discussion), but when research address in a browser, it says the file is not found. Y at - it a special procedure to send Captivate projects to a web server?
Robert
As Lilybri said, you must download the entire folder to keep all of the hierarchy.
The image below shows a project I published locally. The folder on the left, ShapeSVGtest is what you download for all the files inside it remain exactly as will appear it when published.
-
Unable to connect to port 80 on the web server on host Ubuntu guest
I have a very strange problem. I've been running a VM of 14.04 Ubuntu on my MBP under VMware Fusion for some time. I have re-installed Yosemite during the weekend for a clean installation trying to solve some of the problems I had. I now have my Ubuntu VM up and running. All right, except that I can't hit the web server on the virtual machine.
I can access the virtual machine in a variety of different ways!
- Ping: I can ping
- SSH: I can ssh in
- psql: I can connect to the database remotely via port 5432
- NFS: can I get the files of the virtual machine files on my hard drive
- Tomcat: I can access my web application directly through Tomcat on port 8080
When I do a scan of port of the virtual machine, I get this:
Port scan started...
Host port scan: 10.39.186.13
Open TCP Port: 22 ssh
Open TCP Port: 111 sunrpc
Open TCP Port: 389 ldap
Open TCP Port: 2049 nfsd
Open TCP Port: 5001 commplex-link
Open TCP Port: 5432 postgresql
Open TCP Port: 8000 irdmi
Open TCP Port: 8080 http-alt
Open TCP Port: 8104
Open TCP Port: 37805
Open TCP Port: 41301
Open TCP Port: 42060
Open TCP Port: 55224
Open TCP Port: 60974
Port scan has completed...
Port 80 is not even there. The virtual machine itself, I can access the site via port 80:
wget xnat@xnatdev:~$ http://xnatdev.wurstworks.com
-2015-06-22 11:20:50- http://xnatdev.wurstworks.com/
Resolution xnatdev.wurstworks.com (xnatdev.wurstworks.com)... 127.0.0.1
Connection to xnatdev.wurstworks.com (xnatdev.wurstworks.com) | 127.0.0.1 |: 80... connected.
Query HTTP sent, awaiting response... 302 Found
Location: http://xnatdev.wurstworks.com/app/template/login.VM;JSESSIONID=18A2C3A7C7AB6A63F39F7AC49E54FCD4 [next]
-2015-06-22 11:20:50- http://xnatdev.wurstworks.com/app/template/login.VM;JSESSIONID=18A2C3A7C7AB6A63F39F7AC49E54FCD4
Reuse an existing connection to xnatdev.wurstworks.com:80.
Query HTTP sent, awaiting response... 200 OK
Length: unspecified [text/html]
Record on: 'index.html '.
[ <=> ] 12,818 --.-K/s in 0.001s
2015-06-22 11:20:50 (11.2 MB/s) - 'index.html' saved [12818]
But the host OS, I get this:
wget rherrick@Aerys:~$ http://xnatdev.wurstworks.com
-2015-06-22 11:21:50- http://xnatdev.wurstworks.com/
Resolving xnatdev.wurstworks.com... 10.39.186.13
Connection to xnatdev.wurstworks.com | 10.39.186.13 |: 80... has failed: connection refused.
I tried switching between NAT and open networking (I know that I had to work with NAT before, but I'm willing to try anything at this point).
I'm on OS X 10.10.3 and the most recent, and VMware Fusion 7.1.2. Any ideas on how to get this working would be greatly appreciated!
OK, got it market. The issue was the listen directive in configuring nginx for connecting Tomcat. I'd put it domain name FULL and port 80 on the server, but something I did is the determination of the FULL domain to 127.0.0.1 instead of the IP DHCP-published name. If this does not work because the incoming request has been the full domain name of host configured in my/etc/hosts, OS, then nginx not pair together configuring nginx for the domain since listening has been screwed up.
-
Where to configure clustering: on the web server or a load balancer?
Hi all
a few installation questions. I read on clusters and where to set up the pool. My main goal is to reach stickness session, session failover. but I'll ask them later when I clarify below.
If my installation is
-> Cluster WebLogic Web server, I need to install the cluster weblogic web server plugin.
If my installation is
Balancer load-> cluster WebLogic, I need to configure the LB, cos the LB must meet certain criteria.
My planned Setup is
Webserver-> LB-> cluster WebLogic. the weblogic balancing is done at LB. I'll have to set up the LB to balance to the cluster.
I think I'm NOT configure the weblogic on the correct Web server plugin?
Configuring the web server is obviously a proxy directly through the lb.
So my next qn: the configuration to the LB is to balance the weblogic cluster OR a list of all the backend .jsf page server? Assuming that my application launch page is a jsf page. Enjoy your advisor.
(a) you have little sticky on LB. On the Web server, Weblogic Plugin will take care of permanent sessions.
(b) Yes, you need to add to your weblogic.xml in the application. There will be no conflict. However, your heap memory usage will increase as you could store session information on two servers.
"Circumstances and considerations should I need a LoadBalancer in front of my weblogic cluster? --
The main reason you would use a load balancer is to keep the VIP for your application. He would charge the balance between the weservers. Also usually SSL is stopped at the level of load balancer. It helps you reach cross clutser replication etc... You can read this document... Failover and replication in a Cluster
-
The latest changes to the "Upload to Host FTP" function made it useless - no point using a program such as Muse if I can't easily and automatically upload work to the Web server. I use BlueHost webhosting with a main area and I have several domains with this account (such as subdomains or folders on this server) - with older versions of Muse when downloading pages it simply opened a warning window to tell me (what I already know) the Web site I am downloading does not point to the main domain BUT now Muse is trying to create a new folder separated into the root directory of the main domain. completely ignoring the directory path that I am giving him - useless! Why do these crazy changes to the program - and so often - it is very frustrating as amateur ware!
Hello Stephen,
There are some problems with the download of ftp through Muse, who knows the team of engineers and those will be corrected in a future version of Muse. At this point, the work around would be to export the html code of Muse and then download via some third party client like filezilla ftp.
I would recommend that you keep an eye on our page of release notes to get updates more about it - Release notes | Adobe Muse CC
- Abhishek Maurya
-
vSphere 5 and local IIS Web server
Hi all
Sorry for my English, I'm Italian and I'm new to this community, but I have a problem with my vsphere 5.
I created a host with vsphere 5, inside of this host, I have 1 Small Business Server 2011 Microsoft VM and 2 virtual machines Windows 7 Professional.
Infrastructure is:
1 Fritzbox router attached to an hp proliant server.
Inside of the server I have 5 and within esx esx vmware, I have 3 virtual machines
Now, I have installed a local Web server in 1 virtual machine with Windows 7 Professional and IIS 7
I have a static IP and I have configured the router to forward traffic from the static ip address to my internal LAN to a specific IP (the ip of my local web server)
I open in my router port 80 for web traffic and open port 80 also in my firewall windows 7, but when I try to join my vm from the outside, the local web server virtual machine does not work. Is there any configuration, I need firewall configuration ESX?
Thanks a lot for the replies
Valentina Bombelli
To the internet:
Telnet
80 using a Windows command prompt. It seems that you do not specify a port 80, as it is said "... port 23, failed connection. / Rubeck
-
Can I use Centos on the merger as a web server "permanent"?
Hello
so I plan on using Centos 5 as a web server permanent through VMware Fusion.
The goal is to be able to save all small pieces (MySQL database, web files, configurations...) of a Web server from a single blow.
My worries...
Should I open a session to launch VMware Fusion?
Can I disconnect and keep VMware Fusion running?
Thanks in advance for your help.
Although VMware Fusion is not through its UI to provide functioning as a VM as a Service but yes you can do what you ask.
Take a look on: [t-292873]
Use the information in "Starting a Virtual Machine without user login" to start the Virtual Machine and the method suspends in the section "Shutdown / Suspend Virtual Machine on Mac OS X Reboot/Shutdown.
Maybe you are looking for
-
Airport express works do not with modem tp-link
10.11.3 OS iMAC Cable modem comcast just replaced w / tp-link modem is now no wi - fi. Comcast told me maybe my Airport express are too old (4 years). Rebooted everything several times - while I get the green light on express - still no wi - fi.
-
KB2183461 install not on Windows XP
Update KB2183461 titled 'Cumulative Update for Internet Explorer 8 for Windows XP security systems' will not install on Windows XP Home Edition, Service Pack 3. Strange, when I try to install it using Windows Update, it says, the installation was suc
-
original title: the cursor speed Hello!... How can I speed up my cursor?... it seems to me that a few times I have to slow down when I type to wait for the cursor to catch what I'm typing... Thanks in advance!
-
Vista 64-bit for Windows 7 32 bit. What will happen to my laptop?
I have VISTA 64 bit OS and I want to reformat my laptop to Windows 7 but I have Windows 7 32 bit. What will happen to my laptop if I install Windows 7 32 bit? I'm afraid that my laptop will be slow or something because I install 32 bit. Please help m
-
E4200 Intel 5300 on Lenovo T400 does not connect to N 2.4 ghz or 5 GHz
I searched the problem as well I can I to not eval, I can't have the Intel 5300 on a Lenovo T400 to connect to N or Radio I tried every combination possible parameter on the E4200 and on the 5300 That was a lot of combinations I can't get a G-connect