Another failure of the LDAP authentication
I'm trying to setup LDAP authentication for my ASA, as well as the AD Agent. Currently my authentication fails with the following debug output...
[- 2147483610] Starting a session
[- 2147483610] New Session request, the 0xcc854d8c, reqType = authentication context
[- 2147483610] Fiber has started
[- 2147483610] Create LDAP context with uri = ldap://10.11.1.15:389
[- 2147483610] Connect to the LDAP server:
status = success
supportedLDAPVersion [-2147483610]: value = 3
supportedLDAPVersion [-2147483610]: value = 2
[- 2147483610] Liaison as a Sargent\
[- 2147483610] Authentication Simple for Sargent\ to 10.11.1.15
[- 2147483610] LDAP search:
Base DN = [DC = City, DC = charlottesville, DC = org]
Filter = [sAMAccount = sargentm]
Range = [subtree]
[- 2147483610] The analysis of returned search results State failure
[- 2147483610] Fiber output Tx = 308 bytes Rx = 677 bytes, status =-1
[- 2147483610] End of the session
ERROR: Authentication rejected: not specified
I can however run successful AD etc., queries using the following commands.
show the identity of the user ad-users city.charlottesville.org filter sargentm
Ideas?
Replace the below listed command within the parameters of the server:
sAMAccount name-attribute LDAP
With
LDAP-naming-attribute sAMAccountName
Note: the sAMAccountName is configured correctly.
Jatin kone
-Does the rate of useful messages-
Tags: Cisco Security
Similar Questions
-
Hello
I guess the title says it all...
Trying to convert a Win7 machine to ESXi, vCenter 5.5 - work is never point I get an error in the submission.
Tried both with converter 5.5.3 and 6.0 without result.
There is no (known?) another connection to vCenter.
Bundle of newspaper is closed.
Any help / suggestions most welcome!
He must make sure that you have network connectivity to port 902 times Server Converter and the machine of the source to the destination ESX server (note it isn't the vCenter server). If your ESX Server is registered in vCenter hostname, but not with the IP address, then Server Converter machine and the source machine should be able to resolve the DNS name of the ESX Server.
-
Cisco ISE 1.1.2.145 Admin authentication via the LDAP protocol
I have configured the LDAP protocol and able to retrieve our LDAP directory structure. Now, I'm trying to point authentication "Admin Access" Source 'External identity', which is the new LDAP IS I created. But I couldn't find an option to authenticate locally if for some reason the LDAP configuration does not work. I learned that the ISE can automatically return to local auth as external sources Idenitity are inaccessible. How can I test the LDAP authentication with breaking them our Admin Access? I thought to open two parallel sessions, one with Super Admin account Local and one with the domain account. But I noticed that ISE communication is smart enough for the closing session/connection no matter what other sessions in different browsers so, basically, I can't open two parallel sessions the same machine to test. Suggestions? or am I missing something here?
Thanks in advance.
Hi Srinivas,
Even if you configure LDAP as a source of external identity of admin access, you can always internal relief without having locked. According to the ISE user guide:
During the operation, Cisco ISE is designed to "fall back" and try to perform the internal identity database authentication, if the communication with the external identity store has not been established, or if it fails. In addition, whenever an administrator for which you have configured external authentication launches a browser and initiates a logon session, the administrator must still the option authentication of demand through the local Cisco ISE database by choosing 'Internal' to the Selector drop-down storage of identity in the Connect dialog box.
http://www.Cisco.com/en/us/docs/security/ISE/1.1/user_guide/ise_man_identities.html#wp1351543
Please see the attached screenshot by my lab ISE:
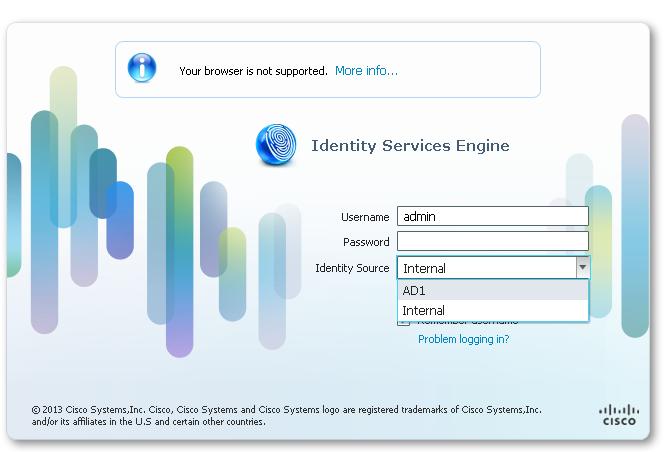
I configured the admin authentication against AD, but I still see both 'Internal' and 'AD' at the time of the connection.
I hope this helps.
Thank you
Aastha
-
How to choose the LDAP settings in the authentication scheme?
Hello
I'm not LDAP expert by any stretch of the imagination ("newbie" would probably be a much better description of my 'expert' level), so please help me understand in simple terms why I'm not going to put up the correct authentication scheme.
When you use Softerra LDAP Browser 2.6 from my PC (where Apex 3.2 is also running in an instance of Oracle 11 g), I can successfully connect to an LDAP service and see all of the directory by using the following parameters:
-Host: 10.34.70.236
-Port: 389
-User DN: cn = RIS, OU = RIS, or = Applications, OU = Services, o = BMGC
-Password is empty
When you configure the LDAP authentication scheme, I use the same settings:
-LDAP host: 10.34.70.236
-LDAP Port: 389
-String LDAP DN: cn = RIS, or = RIS, ou = Applications, OU = Services, o = BMGC
When you try to log in with my user name, I get error of authentication fr.
-How is it supposed to work?
-How is he (supposedly) find my user name in LDAP full?
-How the LDAP_USER parameter is used?
-Where can I learn more about this topic?
- And finally and above all, how can I make this work as any user in the LDAP service can connect but no one else do?
Thanks in advance,
GaborIn the LDAP DN string field, you would put % LDAP_USER % where you want your user name typed-in (from the logon page) to go, for example,.
CN = % LDAP_USER %, or = RIS, or = Applications, OU = Services, o = BMGC
This becomes the DN DBMS_LDAP argument. SIMPLE_BIND_S and the password for your login page is used as the argument of PASSWD SIMPLE_BIND_S.
How is it (supposedly) find my user name in LDAP full?
You must know the exact structure of the directory to find out where your username is present.
And finally and above all, how can I make this work as any user in the LDAP service can connect but no one else?
If the verification of user name and password succeeds on the LDAP directory, then authentication is successful and that the user will be connected. I don't know what is the other case.
Scott
-
We're running out of WinXP SP3. Apparently, we are unable to install/uninstall anything correctly. I think it may have something to do with "a basic installation damaged." I got this error when trying to manually install KB972581 (a security update for 2007 Microsoft Office System). This could have been caused by running the Windows Installer cleanup utility, I didn't have problems with Office 2007. We were informed at all by continuing to upgrade with another program issues.
We daily use Outlook 2007. Multiple users, so we can't delete it.
Same thing with KB970895 (update of security for SQL Server 2005 Service Pack 2) - another failure with the description of the error "Unable to install Windows Installer MSP file".
Basically, the automatic updates of Windows always fail. Comprehensive research of these forums, I found and ran the Microsoft FixIt! # 50202, without result.
How can I fix anything that makes things installation fails?
I had a similar problem - resolved two things actually. First make sure yu have the latest windows installer engine. Then download the package fails and run interactive mode. This will give you the 'real' error which causes the failure so that you can correct it.
In my case it was a dependency on another file system that was resolved by running sfc/scannow - it's maybe not the question you... once again, run the full installation package and also to enablehttp://support.microsoft.com/kb/223300 logging to track down issues...
-
ASA5510 ldap authentication: out of memory error
Hi all
I have a problem in the ldap authentication.
When I try the test of authentication I get this error: "Authenticatione rejected: out of memory error.
What it means? Is that a response from the server?
RADIUS authentication to the same server works very well.
The ASA version is 8.0 (4) and asdm version 6.2 (1).
same problem, version 8.2
-
Asa and Cisco ldap authentication
Hi all
I have a problem with LDAP authentication.
I have a cisco Asa5510 and windows Server 2008 R2
I create the LDAP authentication.
AAA-server LDAPGROUP protocol ldap
AAA-server host 10.0.1.30 LDAPGROUP (inside)
Server-port 389
LDAP-base-dn dc = systems, dc = local
LDAP-naming-attribute sAMAccountName
LDAP-login-password *.
LDAP-connection-dn CN = users, OU = users, DC = network, DC = local
microsoft server typebut when I test, I have an error (user account work directly to the server)
AAA-authentication server LDAPGROUP host 10.0.1.30 userid password test *.
INFO: Attempt to <10.0.1.30>IP address authentication test (timeout: 12 seconds)
ERROR: Authentication rejected: not specifiedHelp, please
concerning
Frédéric
You have the account with username 'user' in ' 'reseaux.local' and "Utilisateurs.reseau.local '?"
If so, can you check if they are two other AD domain? The bug pointed out that ASA do not support authentication via LDAP refererals multi-domain.
You might consider to using an account administrator AD in "reseaus.local" for ASA to connect to AD.
-
Hello
I am able to get the LDAP authentication works for the VPN, but when I go to test a user that is not defined in the VPN group in the ad, they are still able to authenticate and access to the VPN. I'm at a loss for what is the real problem, because everything seems to be set correctly.
I joined newspapers in debugging ldap for a user that works properly and that a user that does not work properly. I think that they should be able to authenticate to a group JOB_ADMINS_VPN and if they are not in this group then they should be denied rights of VPN connection.
LDAP attribute-map JOB_ADMIN_MAP
name of the memberOf Group Policy map
map-value memberOf CN = JOB_ADMINS_VPN, OU = VPN, DC = test, dc = net JOB_ADMINS
AAA-server JOB_ADMINS protocol ldap
AAA-server JOB_ADMINS (Prod) 10.5.1.11
LDAP-base-dn DC = test, DC = net
OR LDAP-group-base dn = VPN, DC = test, DC = net
LDAP-scope subtree
LDAP-naming-attribute sAMAccountName
LDAP-login-password *.
LDAP-connection-dn CN = saVPNLDAP, CN = Users, DC = test, DC = net
microsoft server type
LDAP-attribute-map JOB_ADMIN_MAP
I don't know miss me something small, but I don't know what I'm missing. Any contributions to this number will be grately apperciated.
Thank you!
Please review the below listed config and see what hand you lack of other "sh run" of the SAA.
Configuration to limit access to a particular group of windows on AD
internal group noaccess strategy
attributes of the strategy group noaccess
VPN - connections 1
address pools no
LDAP LDAP of attribute-map-MAP
name of the memberOf IETF-Radius-class card
map-value memberOf
AAA-Server LDAP-AD ldap Protocol
AAA-Server LDAP-AD
Server-port 389
LDAP-base-dn
LDAP-scope subtree
LDAP-naming-attribute sAMAccountName
LDAP-connection-dn
LDAP-login-password
microsoft server type
LDAP-attribute-map LDAP-map
Group Policy internal
attributes of group policy
VPN - connections 3
Protocol-tunnel-VPN IPSec l2tp ipsec...
value of address pools
.....
.....
type of tunnel-group-remote access
global-tunnel-group attributes
Group-AD-LDAP authentication server
NoAccess by default-group-policy
!
!
attributes of the strategy group noaccess
VPN - concurrent connections 0
Jatin kone
-Does the rate of useful messages-
-
Save and reuse the ldap session
Hello!
I have an app with the LDAP authentication scheme custom - I wrote custom authentication and it works very well.
After authentication, on a button click I have need to do a few other requests to my Active Directory (dbms_ldap.search_s). AD do not accept anonymous requests, so I need new initialization of ldap_session and then do simple_bind_s - but apex does not save the password to the user after authorization!
My question is: can I save the ldap_session value returned by dbms_ldap.init in my authentication and use it later?
I tried to put the function of authentication in the package, and then save ldap_session value in a public variable to the package, but I found that this package initialized twice: authentication, and once again, when I try to use this value. And I get nothing in the second.
Sorry for my English.
Thank you, nail.NoGot wrote:
My question is: can I save the ldap_session value returned by dbms_ldap.init in my authentication and use it later?
I tried to put the function of authentication in the package, and then save ldap_session value in a public variable to the package, but I found that this package initialized twice: authentication, and once again, when I try to use this value. And I get nothing in the second.Why not try these other options variable public instead of package:
1. use an application using: SAMPLE_APP_ITEM or & SAMPLE_APP_ITEM.
2 use a custom table to store the value from the id of the session of the Summit and recover when you want to reuseVikram
-
OBIEE 101341 & password for ldap authentication
Hello
We strive to implement LDAP authentication for our users to obiee using ADSI option. The users passwords are encrypted to the LDAP server. Support for OBIEE LDAP authentication mechanism - only clears passwords to verify the credentials of the user?
We tried once in the past to set the LDAP authentication, when we were on 782 Analytics Siebel and Oracle said encrypted passwords don't are not supported for LDAP authentication in this version od Siebel Analytics 782. Now that we have upgraded to OBIEE 101341, we want to try again and see. Any body let me know if the OBIEE LDAP authentication mechanism supports passwords encrypted in the clear.
Thank youBI Server uses passwords in clear text in the LDAP authentication. Make sure that your LDAP servers are set up to allow this. No support for encrypted password. Hope this helps
-
AnyConnect user using the user certificate authentication and LDAP authentication
Hello
I'm trying to implement the Anyconnect VPN for my office. Now, I want the user to authenticate the user certificate based (which is install user local system are we) CN value and LDAP authentication. A help how to achieve this requirement. We install Certificate ROOT and INTERMEDIATE Godaddy and even already installed ASA. Also, we have the user certificate installed on each system user to authenticate the user.
Any help please.
Hi subhasisdutta,
This link will certainly help you with the configuration:
http://www.Cisco.com/c/en/us/support/docs/security/AnyConnect-secure-mob...
Hope this info helps!
Note If you help!
-JP-
-
Hello
I use Windows 7 (32-bit) with SP1.
Quite often (at least three times a day) I am to be locked of my PC and cannot connect to 30 mts each time. I've analyzed carefully and there is absolutely nothing wrong with my ID on the front of Windows AD or group etc. policy.
I am getting event ID 40690 in my observer of events and here are the details...
WARNING on 09/06/2011 09:07:54 lsasrv 40960 any
Log name: System
Source: lsasrv with
Date: 09/06/2011 09:07:54
Event ID: 40960
Task category: no
Level: WARNING
Keywords:
User: SYSTEM
Computer: workstation.companyname.com
Description:
The security system detected an authentication for the HTTP/http-proxy server error - nom_societe.com. The code of failure of the authentication protocol Kerberos was "the user account has been automatically locked because too many attempts to invalid login or password change attempts have been requested.
(0xc0000234).
I searched all possible sites and cannot find an appropriate solution.
As it is causing a lot of inconvenience would appreciate a miracle solution as soon as POSSIBLE.
See you soon,.
bcshekar
Hi bcshekar,
The question you have posted is related to the area and would be better suited to the net Tech community. Please visit the link below to find a community that will provide the support you want.
http://social.technet.Microsoft.com/forums/en-us/w7itprosecurity/threads -
Clientless VPN SSL - policy of another LDAP authentication group
Hi all
I am currently working with Clientless SSL VPN. I have a problem with the creation of access to the different or blocking of users.
I created tunnel/connection-profile (WEB-VPN-TEST-Profil2) and create group WEB-VPN-TEST2. I joined with the LDAP server. I also create a map LDAP attribute to provide only specific users to access. I havn't create an address pool
What I'm trying to do is give access to the 'IL DBA' team and stop access to all the others in my organization. But to the login page when I give my password, I am able to connected even if I'm in the team "IT Network". Here's what I've done, (think I work for abcxyz.com)
=======================================================
AAA-server BL_AD protocol ldap
AAA-server BL_AD (inside) host 172.16.1.1
OR base LDAP-dn = abcxyz, DC = abcxyz, DC = com
LDAP-naming-attribute sAMAccountName
LDAP-login-password *.
LDAP-connection-dn [email protected] / * /
microsoft server type
LDAP-attribute-map CL-SSL-ATT-map
=======================================================
LDAP attribute-map CL-SSL-ATT-map
name of the memberOf IETF-Radius-class card
map-value memberOf 'CN = IT s/n, OU = abcxyz, DC = abcxyz, DC = com' WEB-VPN-TEST2
========================================================
WebVPN
allow inside
tunnel-group-list activate
internal-password enable
========================================================
internal strategy group WEB-VPN-TEST2
Group WEB-VPN-TEST2 policy attributes
VPN-tunnel-Protocol webvpn
group-lock value WEB-VPN-TEST-Profil2
WebVPN
value of the URL-list WEB-VPN-TEST-BOOKMARK
value of personalization WEB-VPN-TEST2
========================================================
remote access of tunnel-group WEB-VPN-TEST-Profil2 type
attributes global-tunnel-group WEB-VPN-TEST-Profil2
authentication-server-group abcxyz_AD
Group Policy - by default-WEB-VPN-TEST2
tunnel-group WEB-VPN-TEST-Profil2 webvpn-attributes
enable WEB-VPN-TEST-Profil2 group-alias
=========================================================
Please let me know if there is a question or let me know why I am still able to access the same if I did my attribure to match only with "IT"DBA ".
Thanks in advance.
BR.
Adnan
Hello Adnan,
That's what you do:
internal group WITHOUT ACCESS strategy
attributes of non-group policy
VPN - concurrent connections 0
attributes global-tunnel-group WEB-VPN-TEST-Profil2
Group Policy - by default-NO-ACCESS
Group WEB-VPN-TEST2 policy attributes
VPN - connections 3
Kind regards
-
Change the role of the user once authenticated LDAP authentication
Hi forum,
I do know that if it is possible, I have not found a solution so far
I have a simple web application with LDAP authentication. We would like to use LDAP for authentication and store the information of user roles in the database. After authentication, LDAP assigns the role of "guest" to the user and the home page (the only page available for this role) is displayed.
In this home page, the user must select a profile (the same user can have multiple profiles) in a list retrieved from the database. The profile of each user has an associated role. After selection, we want to change the role of the user "guest" to the role associated with the selected profile.
I don't think that implementation of a custom plug-in fits my needs because the role assignment requires the participation of the user.
Any suggestions?
Thanks in advance,
Tatiana.Hello
Well, the problem is that you need to change the subject of the user authenticated, who's a JAAS thing to do. The only way this can work is indeed use a custom LoginModule and then access the user object to add a security principal that represents the role you want to add.
Frank
-
Access to the LDAP VPN ASA group
Hello, I have configured the access remote vpn on asa with ldap authentication. But I can't limit access vpn with specific ldap group.
Here is my config:
AAA-server AZPBTDC01 (DC_Internal) host 192.168.10.250
LDAP-base-dn dc = company, dc = com
LDAP-scope subtree
LDAP-naming-attribute sAMAccountName
LDAP-login-password *.
LDAP-connection-dn cn = Netuser, OU = Services users, or is ASM HQ, dc is company, dc = com
microsoft server type
LDAP-attribute-map AZPBTDC01LDAP attribute-map AZPBTDC01
name of the memberOf Group Policy map
map-value memberOf "CN = VPN_Admin, OU = ASM group, OU = ASM HQ, DC = company, DC = com" RA_ADMIN_GPinternal group NOACCESS strategy
NOACCESS group policy attributes
VPN - concurrent connections 0
client ssl-VPN-tunnel-Protocol ikev1
address pools nointernal RA_ADMIN_GP group policy
RA_ADMIN_GP group policy attributes
value of server DNS 192.168.10.251
VPN - connections 3
Ikev1 VPN-tunnel-Protocol
Split-tunnel-policy tunnelspecified
value of Split-tunnel-network-list IPSEC_RA_ACL_ADMINattributes global-tunnel-group DefaultRAGroup
NOACCESS by default-group-policytype tunnel-group IPSEC_RA_ADMIN remote access
attributes global-tunnel-group IPSEC_RA_ADMIN
authentication-server-group LOCAL AZPBTDC01
authorization-server-group AZPBTDC01
Group Policy - by default-RA_ADMIN_GPThe problem is all the domen users can connect to the vpn. ASA does not ranking filter in a group, no VPN_Admin group users can connect, but the man should not be able to connect.
If it is possible to make this approach work, I wouldn't do it this way. Use rather DAP (Dynamic Access Policy).
The instructions for this are here:
Search for "Active Directory group" to jump directly to the corresponding section. Note that you may need two policies DAP. One to match users living in VPN_Admin and another default policy to deny access to everyone.
Note for the default "opt-out" policy, that I often make it pop up a message to the end user, saying that they do not have VPN access and contact xxx if they want to fix it.
Maybe you are looking for
-
Cannot get rid of the Yahoo Search bar. Have tried everything. Nothing works. I hate it.
I have no idea how Yahoo has arrived on my Firefox browser, but I hate it. I deleted everything I can think of Yahoo related, but without success. Help, please.
-
JUST DOWNLOADED 9.0, NOW THE POLICE IS SO SMALL THAT I CAN'T READ
I TRIED TO CHANGE THE FONT SIZE, BUT IT JUMPS BACK AND MESS UP THE REST OF THE COMPUTER. IT DOESN'T SEEM TO BE A PROBLEM IN GMAIL
-
Default values for FaceTime for Lync for calls
Hi guys I'm having a nightmare here with Lync and FaceTime. Whenever I put FaceTime as my "default for calls" it changes again in Lync whenever I get close and reopen the app Lync did the same when I change the phone FaceTime app, it returns just to
-
Subvi output displayed dynamically on XY graph
Hi, I'm trying to implement a VI to apply a voltage signal ramp up to a door of transistor and measure the current resulting from the source to the drain. It is necessary that the data is graphically in real time as it is acquired. I managed to do it
-
After the update of DVD driver from Dell, my PC does not recognize the drive at all the
Hi, I've updated my DVD burner on the Dell Web site (he said it was important), but since then, my computer does not recognize my dvd player at all. I click on "drivers" and the system finds it online. A halfway through the installation, I get an err