Installation of on IOS SSL certificates
Having a problem with an SSL certificate (DigiCert) on a Cisco 2811 running IOS 124 - 24.T4.
I can get the certificates, intermediate and certificates of server installed fine unsing the a trustpoint created. Web ssl site works very well for IE browsers, and other types of browsers get errors. When I do a verification of the SSL certificate it shows that the "the server does not send the certificate requires intermediary" (see attachment). I feel that I have followed is available as well. Any suggestion is appreciated.
It's the best information I could find to follow. They are specifically for Go-Daddy certs, but I think it would be the same process for all.
Thank you
BR
Hello
If you have several CA certificates, you must authenticate the trustpoint containing the CERT of identity using the immediate intermediate cert and then use other trustpoints to import the other CA certs one by one.
So, basically, we need to follow the following configuration to import the CA 3 certificate and the certificate of identity on the router:
1. Create root trustpoint >> >> Crypto ca trustpoint root >> Enrollment terminal >> >> chain-validation stop >> >> revocation-check none >> >> Crypto ca authenticate root >> (this will prompt to paste in the PEM/base64 of the Root CA certificate) >> Quit after you paste the Root CA certificate. >> >> >> 2. Create intermediate trustpoint for the primary intermediate certificate >> >> crypto ca trustpoint intermediate-primary >> enrollment terminal >> >> chain-validation continue root >> >> revocation-check none >> >> crypto ca authenticate intermediate-primary >> (this will prompt to paste in the PEM/base64 of the Primary Intermediate CA certificate) >> Quit after you paste the intermediate primary certificate. >> >> >> 3. Create intermediate trustpoint for the secondary intermediate certificate >> >> crypto ca trustpoint intermediate-secondary >> enrollment terminal >> keypair >> chain-validation continue intermediate-primary >> >> crypto ca authenticate intermediate-secondary >> (this will prompt to paste in the PEM/base64 of the Secondary Intermediate CA certificate) >> Quit after you paste the intermediate secondary certificate. >> >> 4. Import the IDentity certificate >> >> crypto ca import intermediate-secondary certificate >> (paste the ID certificate PEM/base64 here)
Tags: Cisco Security
Similar Questions
-
CA-signed SSL certificates on vCenter 5.1 installation (server or device)
I recently updated my 5.0 to 5.1 ESXi ESXi hosts and they all kept CA-signed SSL certificates that I installed previously. I did a new install of vCenter 5.1 server where the box even ran SSO, inventory, vCenter Server and Manager Update Services. After installing, everything worked perfectly except that none of the vCenter services used my CA-signed SSL certificate - only 5.1 ESXi hosts had these.
So, I followed the instructions in replacing default vCenter 5.1 and ESXi certificates PDF found at http://www.vmware.com/resources/techresources/10318. The document is terrible. For example, page 10 lists the locations by three default certificates SSL on Windows 2008. None of these paths are correct. The first a typo of extra space between "Program" and "Data" and the other two say "Program Files" when they should have been "ProgramData". This is just the beginning of the problems.
If you follow the instructions to the letter, you'll break vCenter. I got frustrated and thought I'd give the vCenter 5.1 device a shot. With regard to the Certificates SSL signed by CA, it was worse. The vCenter 5.1 device can even automatically generate a new SSL certificate if you change the host name (turn on generation auto-certificat, change of hostname and restart). It gives an error 653 during the boot process and keeps the original of the certificate. Even bother trying the steps on page 18 of the above-mentioned guide - you will get just the same mistake 653.
It seems to me that VMware did not all tests around the CA-signed SSL certificate on vCenter 5.1 installation. It's amazing to me that the installation of the SSL certificate is so tedious for ESXi and vCenter when vShield Manager 5.1 has a very simple process that works well (and is similar to the installation procedure for Certificate SSL on the DRAC, ASR, breeding various firewalls, etc.).
I did a lot of research on Google and found various articles on the installation of the SSL certificate, but most were based on GA pre - 5.1 products. If you have any installation of certificates SSL CA-signed success with vCenter Server or device 5.1 GA, let me know how you got around some of these issues. Please indicate if your vCenter Server or device will run on a 5.1 GA ESXi host as well. Please do not answer about vCenter 5.0 - I had no problem with SSL certificates (other than it was more painful to be).
Thanks in advance,
Nate
Finally I managed to install giving him to 127.0.0.1 instead of the period of INVESTIGATION, accessible from the outside of the vCenter server, it's very well in my case the vCenter and VUM server are on the same VM but its not exactly ideal for deployments of more large.
-
The 5.5 SSL certificate installation device Orchestrator
Need for additional documents and advice on installing the Orchestrator's SSL certificate. My approach resulted in a failure to download error. Method: keystore file downloaded using selection in Configuration Orchestrator interface. Removed the embedded free signed certificate and key private using commands in the key tool. Issues for a new original keystore certificate using the keytool command. Treaty of applicantst on a windows certification authority. Installed at root, intermediate, and new machine cert in original keystore, checked the chain and tried to install the key file using the GUI with a download error received.
See the following resources:
- http://mighty-virtualization.blogspot.de/2012/09/VCO-51-appliance-how-to-fix.html
- http://www.vcoteam.info/articles/learn-VCO/181-work-with-VCO-over-SSL.html
- http://KB.VMware.com/kb/2007032
Also, could you give more information about the error, you receive (for example, trace error stack in the log files)?
-
Pre complains about SSL certificate on the exchange server
Hello. I just got a pre and tries to set up to communicate with an exchnage server. Pre complains and will not set up the connection with this error message: «"SSL certificate error.» Is the date and time correct? ». The date and time are correct, but the server is running a self signed certificate. This causes no problems with iPhones that use a lot of people here.
How can I fix it? It is not all parameters for this problem.
I spent the weekend trying to test and understand what was going on. I found that if I nominated the e-mail server (name after HTTPS: / / in Setup) the same as the name of certificate displayed in the Certificate Manager (Launcher > Device Info > more info > Menu > Certificate Manager), the error should disappear. The problem for me was that the name of cert in cert Manager was different from address of mail server (in my case server. [domain .local] instead of mail. ([Domain_name] .com). The transformation it seems to use is:
(1) find the certificate...
(2) CN is HTTPS: / / in the installer?
(3) If no, use error 'Verify the certificate, date and time not correct' (or whatever it is) - If Yes, go to HTTPS: / /.
(4) Exchange requires safety pin? If no, proceed to synchronize - if so, use error "unsupported of security policies.
So I looked more closely CERT and it held several common names (CN) for the cert. It seems that ANY OTHER DEVICE can filter through the list of common names, and use the one that works. The Pre uses only (whether first or last, I don't know).
So, there are two options for the certificate problem (I guess the 3rd is that you can return the phone):
FIRST SOLUTION
=====================
(1) check the name of cert in cert Manager.
(2) if it is a name that can be resolved DNS (i.e. [mail]. [mywebsite]. [com]) then change this setting in your exchange installation program in the mail server field beside the HTTPS: / /.
This will only fix it if your COMPUTER administrator has with permissions on the used field. It is possible that an alias is used on other areas
SECOND SOLUTION (as I have done)
=================================
(1) ensure that your Certification Authority is installed. You can do it by clicking START > ADMINISTRATIVE TOOLS > CERTIFICATION AUTHORITY - OR - on a computer on your network using IE/Safari/Firefox and typing http://server/certsrv. If the page is found, then you are installed, if not, then you will need to have installed.
NOTE: SBS 2003 WILL AWARD A CERT TO THE IIS WITHOUT THE ROOT CA. THIS SEEMS TO BE THE PROBLEM WITH THE AUTO CERTS GENERATED I HAD
(2) If you have not installed it, go to this topic, it is well written to get step by step instructions how to install, create demand for cert, create the cert and install the cert (it took me about 30 min). http://www.MSExchange.org/tutorials/SSL_Enabling_OWA_2003.html
NOTE: IF YOU ALREADY HAVE A CERT ON IIS, YOU NEED TO REMOVE IT AS IT IS "DEFECTIVE" CERT BEFORE YOU CAN REQUEST A NEW CERTIFICATE. YOU MAY BE ABLE TO REINSTALL OVER THE NEW CERT, BUT I DON'T KNOW
(3) open https://mail.domain.com/exchange on your computer - display details of the cert and save the file on your desktop - if you are using a laptop, you can also install it on your laptop to use for use outside the Office (this is also a good back-up that you can use to get more later if needed again).
(4) plug your pre in USB mode.
(5) slide the cert and unplug the USB cable
(6) go to cert Manager
7) tap on the icon of "Sun" at the bottom left
(8) press on the new file cert that you save in USB mode
(9) to confirm that the new cert appears with the name of the correct mail server
10) go to the e-mail program and configure the exchange account
The above will create a REAL root cert (not IIS domain root Cert) that the Pre can work with.
Really, I don't know that how/why Palm overlooked this possibility because they claimed so-called does not want to sell to companies who need strict security requirements. For me, it means a small / medium company that has limited IT supports (according to the needs, pay as you or green guy with limited knowledge). Then, why they test the GER in this environment, I'm not sure. I bet they were tested on their own network, which has all the correct methods, best practices for the management of cert. I guess it's like the developers that they have offended and almost lost their support until turned it over and said: 'sorry, we really want make you programs for our platform WebOS. ". We've just been paranoid for so long salivate us when the bell rings. "They just didn't beta test this well enough. The sad result of this is that Sprint will have to address all of the sheets because this certificate simple reading process was given only minimal recognition capabilities.
But having said that - I'm now completely in love with my pre!

I'm happy to try to help if you need it. I found a lot of the forum of solutions were not enough detailed, so do not hesitate to contact.
-
How to install the ssl certificate in windows server 2008?
Hello
Can someone give me the steps to install the SSL certificate on my application hosted on windows server 2008 R2?
Hello
Although technet.microsoft.com should be the best forum for the problems of server below is a guide on how to install an SSL certificate.
It will be useful.
To install your newly acquired in IIS 7 SSL certificate, first copy the file somewhere on the server and then follow these instructions:
- Click on the start menu, go to administrativetools and click on Manager of Services Internet (IIS).
- Click the server name in the links on the left column. Double-click server certificates.
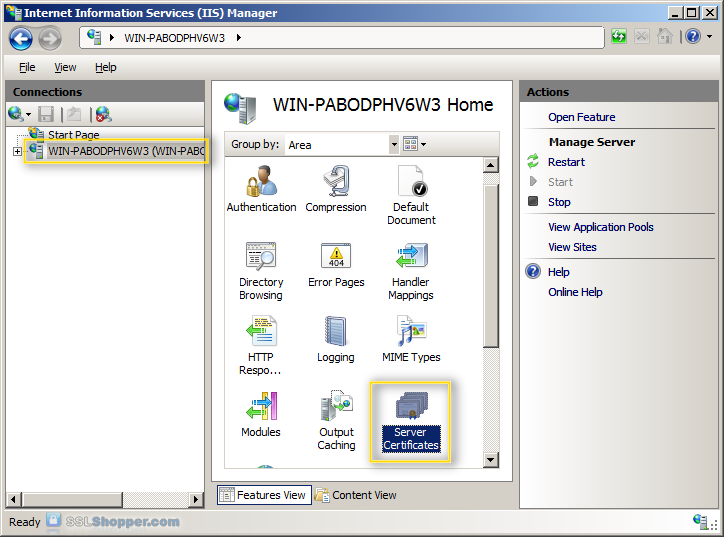
- In the Actions column to the right, click Complète Certificate Request...
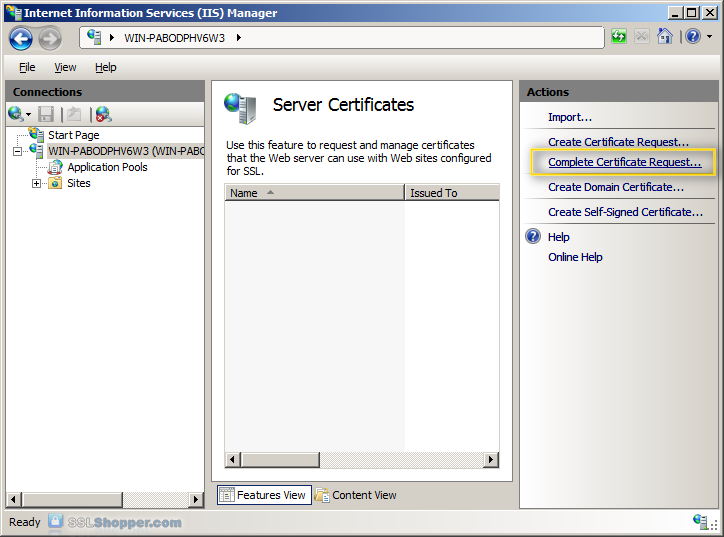
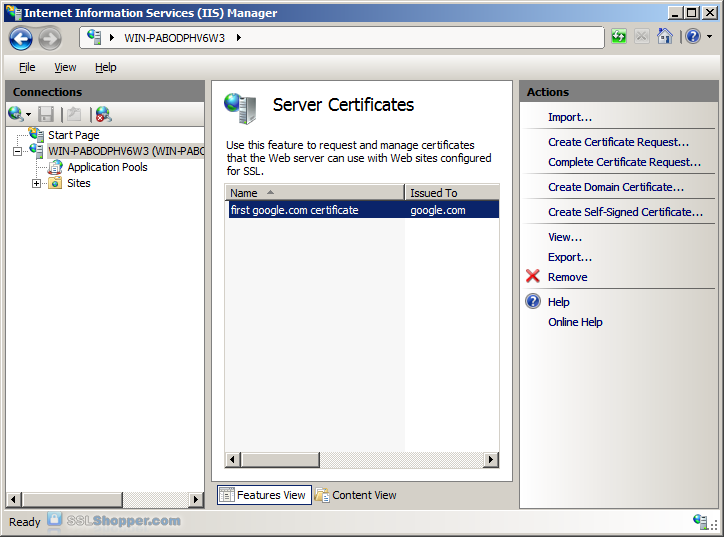
- Click on the button with the three points, and then select the server certificate that you received from the certificate authority. If the certificate does not have a .cer file extension, select this option to display all types. Enter a friendly name that you can keep track of certificate on this server. Click OK.

- If successful, you will see your newly installed in the list certificate. If you receive an error indicating that the request or the private key is not found, make sure that you use the correct certificate and you install it on the same server that you generated the CSR on. If you are sure these two things, you just create a new certificate and reissue or replace the certificate. If you have problems with this, contact your certification authority.
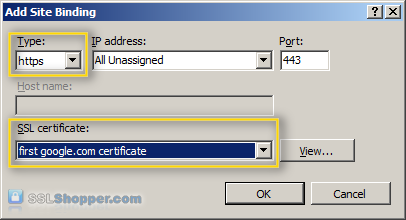
Bind the certificate to a Web site
- In the column of links on the left, expand the sites folder, and click the Web site that you want to bind the certificate to click links... in the right column.

- Click the Add... button.

- Change the Type to https , and then select the SSL certificate that you just installed. Click OK.
- You will now see the listed link for port 443. Click close.
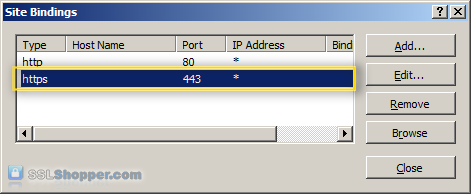
Install all the intermediate certificates
Most of the SSL providers issue certificates of server out of an intermediate certificate so you will need to install the intermediate certificate on the server as well or your visitors will receive a certificate error not approved. You can install each intermediate certificate (sometimes there are more than one) by following these instructions:
- Download the intermediate certificate in a folder on the server.
- Double-click the certificate to open the certificate information.
- At the bottom of the general tab, click the install Certificate button to start the Certificate Import Wizard. Click Next.
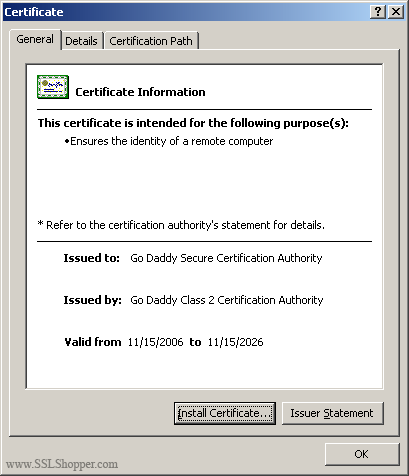
- Select place all certificates in the following store , and then click Browse.

- Select the Show physical stores checkbox, then expand the Intermediate certificate authorities folder, select the below folder on the Local computer . Click OK. Click Next, and then click Finish to complete the installation of the intermediate certificate.
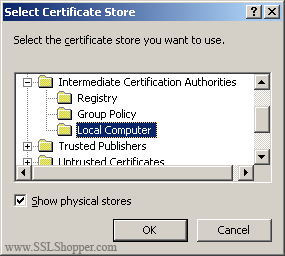
You may need to restart IIS so that it starts the new certificate to give. You can verify that the certificate is installed correctly by visiting the site in your web browser using https rather than http.
Links
- Move or copy an SSL certificate on a Windows Server to another Windows Server
- How to disable SSL 2.0 in IIS 7
- How to configure the SSL in IIS 7.0
- Video tutorials to install an SSL certificate in IIS 7 to NetoMeter
Kind regards
Joel
-
I'm trying to configure an SSL VPN on a 2811. I believe I have the part SSL VPN, but I can't tell because I get stuck on the certificate server, ca trustpoint configuration and the identity of trustpoint.
Does anyone know of a guide that walks you through the cert CA, Cert ca trustpoint and identitiy trustpoint iOS SSL VPN server? For some reason, I'm having a problem to enter the configuration of the certificate.
Thanks for the help
Triton.
Follow these steps:
> Add the host SSLVPN.securemeinc.com file to the user (client)
> When you open the SSL VPN page on the user's browser. Right click... Select "Properties..." 'See Ceriticate' and then save/open the certificate on the computer companies.
> Make sure the time is synchronized between the VPN server and client
Concerning
Farrukh
-
Windows 2000 SSL certificate export
Hi all
I am trying to export the certificate SSL in Windows 2000 server that is running Cisco ACS 3.3. This SSL certificate is issued by a third-party CA. This certificate is issued by CA bound our server host name. Thus, this certificate can be reused on another server with a different host name.
I followed under the installation program to export the certificate since 2000 planter
[1] start > run > Type "mmc" and press ENTER.
[2], click on Console > Add/Remove Snap-in...
[3], click Add > certificate > add > computer account > next > Local computer > finish > close > Ok
[4] expand Certificates > expand Trusted Root Certificate Authority and select certificates
[5] select the certificate CA ACS, right click > all tasks > export > next > select ' encoded in Base 64 X.509 (.) REB)' > next > Browse
Choose the storage location and give it a name.
Press next > finish
We should get a message "export was successful."
After the export of the certificate in the CERTIFICATION AUTHORITY folder ROOT of TRUST based on the name of the seller. I could see that the certifcates are self-signed certificate. This certificate is not valid certificate approved in the sound emitted by the CA.
My Question is: If this certifcate issued by 3 third party trust will be located in a different folder outside the ROOT of TRUST certificate folder. If the folder in which this certifcate trust will be so now.
I'm checking the certificates of
published by:
issued to:
SE signed certifcate times issued to and issued by is even
SETTING SNAP SHOT of certifcate MMC window.
Hello
ACSCertStore is a record of the certificate created in the MMC - folder of the server certificate.
I hope this helps.
Kind regards
Anisha.
P.S.: Please mark this message as answered if you feel that your query is resolved. Note the useful messages.
-
Cisco ASA 5505 and comodo SSL certificate
Hey all,.
I'm having a problem with setting up the piece of Certificate SSL of Cisco AnyConnect VPN. I bought the certificate and installed it via the ASDM under Configuration > VPN remote access > Certificate Management > identity certificates. I also placed the piece of 2 CA under the CA certificates. I have http redirect to https and under my browser, it is green.
Once the AnyConnect client installs and automatically connect I get no error or anything. The minute I disconnect and try to reconnect again, I get the "VPN Server untrusted certificates! ' which is not true because the connection information to be https://vpn.mydomain.com and the SSL certificate is configured as vpn.mydomain.com.
On that note, it lists the IP address instead of the vpn.mydomain.com as the unreliable piece of this. Now of course I don't have the IP as part of the SSL-cert, just the web address. On the side of the web, I have a record A Setup to go from vpn.mydomain.com to the IP address of the Cisco ASA.
What I'm missing here? I can post config if anyone needs.
(My Version of the Software ASA is 9.0 (2) and ASDM Version 7.1 (2))
Yes that's correct. technically, it will take you to EKU as keys to authenticate server who was a little forced in version 3.1. But eventually, he was taken away. If you get no error using the browser and ot only comes with the anyconnect client. Most likely, you do not have to configured values. I can confirm that if you can share the fqdn with me also, you can try the upgrade and check it out.
Thank you
Bad Boy
-
MSE 8510: default SSL certificate expired
Hello community,
the SSL certificate self-signed of our MSE8510 that has been Setup automatically during installation has expired. Is there a way to create a new directly on the box or do I need to do external and transfer?
Someone has a short guide on how to do it?
Thank you
Renz
Check:
Its always a good idea to browse the first cisco documentation site! :-)
You will find also some information when you use google, such as:
http://blog.codesalot.com/2010/11/25/creating-certificates-fo-Codian-MCU/
Please remember useful frequency responses (using the stars below) and mark answers useful or correct .
-
Replacement of the SSL certificate in vCenter Server Heartbeat with a new certificate
Realized the SSL certificates on my vsphere vCenter Server 5.5 environment change, but now I'm looking to deploy vmware vCenter Server HeartBeat service, but I have the following doubts.
1. it is necessary to perform the exchange of currently used SSL certificate in my environment. ()http://kb.vmware.com/selfservice/microsites/search.do?language=en_US & cmd = displayKC & externalId = 2013041( )
KB article talking about amendment of the certificate of a vCenter Server Heartbeat deployed... If the vCSHB are not deployed and yet, you don't need to worry... just go ahead with the installation and the new vCenter server certificate will be recognized by vCSHB.
-
Error update vcenter SSL certificate?
Hello people,
I've recently upgraded to vcenter 5.1 U1a successfully.
I'm following VMware articles and a popular blog to prepare and run the certificate VMware 1.0 automation tool.
http://www.derekseaman.com/2012/09/VMware-vCenter-51-installation-part-2.html
http://www.derekseaman.com/2013/04/using-VMware-vCenter-certificate.html
Everything was pretty smooth up until I have to replace the the vcenter Server SSL certificate. Option 2 vcenter update ssl. See the attached photo.
After the error, my vcenter service will not start.
I tried to reset the password of database using vpxd.exe - p, but vcenter still does not start.
I also checked that the correct service ID is matched between vpxd.cfg and LS_ServiceID.prop.
Stuck at this point. I have since went instant return, but try to see if anyone has any suggestions?
Could this be type a bad password?
Thank you!
You mentioned the KB as well?
Concerning
Girish
-
Can't connect to SSL certificate re VMware Update Manager - utility
In the context of http://KB.VMware.com/selfservice/microsites/search.do?cmd=displayKC & docType = kc & docTypeID = DT_KB_1_1 & externalId = 2037581 , I'm at step 7 where I enter the credentials for the VMwareUpdateManagerUtility.exe. It just hangs and ends by mistake. I copied the new certificate SSL files above. I have 2 errors different no matter what I try.
Error 1: "cannot run vciInstallUtility."Error 2: "error: unknown vCenter Server error."For "vCenter Server IP address or name", I tried < FQDN vcenter >: 80, < vCenter IP >: 80, < vCenter fake DNS in the hosts file >: 80 and they all hang on for a few minutes and then give one of the errors. VUM is installed on a separate computer vCenter virtual. I did a complete reinstall of VUM. I use vCenter and VUM 5.1.0 installation media - rates from 880471 since that's our motto. I checked that port 80 is correct using this query on VCDB, SELECT VALUE FROM VPX_PARAMETER WHERE NAME = "WebService.Ports.http";. Any suggestions?I gave up, uninstalled VUM server, re-installed on the vCenter server administrator, used 127.0.0.1 and VUM finally got with valid SSL certificates. As part our design, we didn't have the same server as vCenter VUM but I found myself with no other choice.
-
Cannot save vSphere Web Client after the replacement of the SSL certificate
Hi all
I have followed the Articles of Derek Seaman on the replacement of all the certificates in vSphere 5.1 and have since turned to the VMware KB Articles. I replaced the certificates for the SSO, the inventory Service and vCenter Server with no problems (other than having to use OpenSSL-Win64 for vCenter certificate that I could not get the x 86 version certificate of work, makes no sense, but I'll take the small victory).
If you follow the guide of vmware to replace the web service certificate, http://kb.vmware.com/selfservice/microsites/search.do?cmd=displayKC & docType = kc & docTypeID = DT_KB_1_1 & externalId = 2035010, I get to step 12, enter the VMware vSphere Client Web back to vCenter Single Sign On and the following error:
##########################
D:\Program Files\VMware\Infrastructure\vSphereWebClient\SsoRegTool > regTool.cmd registerService - cert "C:\ProgramData\VMware\vSphere Web Client\ssl" - ls - url ( https://(Server URL): 7444/lookupservice/sdk - username admin@system-domain - password (password) - dir 'D:\Program Files\VMware\Infrastructure\vSphereWebClient\SsoRegTool\sso_conf' - ip "*." ' * ' - serviceId-file 'D:\Program Files\VMware\Infrastructure\vSphereWebClient\serviceId'
No file properties not found
Initialization of provider of record...
SSL certificates for https://vsphere.au.ray.com:7444/lookupservice/sdk
SSL certificates for https://vsphere.au.ray.com:7444 / sso-adminserver/sdk
Unhandled exception trying to escape: null
Return code is: OperationFailed
100##########################
VMware technical support suggested I uninstall all components, delete all databases and try again. I have done this and have exactly the same result.
Has anyone seen elsewhere or managed to solve?
Chris
So, I managed to solve this problem. Not sure that this applies to everyone, but my problem was caused by registering using among other names of the subject in the SSL certificate for the SSO rather than the common name of the certificate.
For example, the server name is server1.company.com. It is the common name of the certificate. But one of SAN of the certificate has been "vSphere.company.com". If I used this other name in one of the component records that they would fail. I found that I have to use the common name. Even if the alternative names of job access to via your browser web, there is no certificate warning, if the registration of components using these names, it would fail.
It seems crazy that you can use any of the San... then why allow us to make?
Initially, I tried to replace the authentication certificate ONLY when the town was called vsphere.company.com, rather than the hostname of the server, and which is installed. However, try to install the Web Client would fail. When you come to the step where you have to accept the certificate of SSO, the installation fails because the common name of the certificate does not have the host name of the SSO server. It seems insane to me... why the host name of the server running the SSO should still come in when all calls are over HTTPS is simply absurd!
I confirmed this with VMware Technical Support and they checked my conclusions.
-
I am going through the vSphere Upgrade Guide impatient of my upgrade to vSphere 4.0 vSphere 4.1. My current VirtualCenter server is Windows 2003 32-bit, and looking at the documentation I will move to a 64-bit server. It's fine, I can create a new 64-bit of Windows 2008 Server and follow the documentation for moving to a new server. First of all in the document, he identified the default device of the SSL certificates as «installation location\VMware\VMware VirtualCenter\SSL.» I assumed that the 'location', mentioned in the Program Files folder, but found no such a file to this location. Later the documentation tells me to save my SSL certificates located in the «%ALLUSERSPROFILE%\Application Data\VMware\VMware\VirtualCenter.» I see a * .key, * .crt and *.pfx sub-folder SSL at this place. I guess these are the good files to back up?
Yes.
-
See 4.5 Security server problems since installing SSL certificate
I'm having some very strange problems with my view view connection Server 4.5 (front and back) running. I hope someone could shed some light on the problem, because I have tried everything I know to do this job properly.
Before installing a certificate self-signed server of external connection again, I was running the default VMware certificate. Everything worked very well in this configuration. I installed a new self-signed certificate and now I'm having intermittent problems, the connection to the server:
1. in the connection from a windows machine I CAN reach the site URL/HTTP to download the client from the view. Once I run the client to view I got the following error: failed connection to connect to the server view. Network error.
2. I tried to connect via the IP address of the server, ensure that the external URL is correct (everything worked fine before the installation of the SSL certificate).
3. completely removed security server and reinstalled, restart the services etc. Still not connect on some machines. Connecting from a Wyse compatible iPad still works, never a problem.
4. If I connect the VPN of the company on the machine that does not work, then launches the Client to view and connect everything works as it should. When I disconnect the VPN and try to connect again, I can connect very well! So I need to connect to the VPN to connect to browse... its really weird. I checked DNS etc and everything is identical with the default certificate. I did so that machines that have problems approve the certificate and I also followed the Cisco ASA firewall logs, I do not see happneing anything different between periods of work and does not.
Someone at - he never lived something along these lines or can think of anything I can try?
Thank you!
I came across this same thing. The conflict is between the customer to view and your new self-signed SSL certificate. More precisely the thing causing the problem is the version of the wininet.dll file provided with IE8. The wininet.dll file provided with IE8 causes some kind of conflict with the customer view 4.5 (if using other SSL certificate that the server generated one) and will not allow the client to view 4.5 software to connect to your server security. I reported this to VMware (2 weeks ago) so that they should be aware of the problem.
If you remove your new SSL certificate and return to the one created by the display server then everything works perfectly again. If you are using a machine with IE6 or IE7 XP remove IE8, it also works very well. I tried taking the file wininet.dll from XP SP3 IE6 machine and restore this file after installing IE8 and everything seemed to work ok, but probably not the best solution.
Bottom line is until VMware resolves the conflict with their client to view, you may not use any SSL certificate (other than that of the server is) If you are going to connect to windows machines running IE8 or newer.
Maybe you are looking for
-
How to make ffx actually load the content of all the tabs from last session
As of recently, when I restart ffx, all tabs from last session are open, but not charged. I want that they all load immediately, rather than load it only when I concentrate on each tab. Is this possible? Thank you -)
-
Printer disappeared after installing Windows SP3
I have no printer listed now. I tried to go thru administrative "Printer Spooler" in the system - nothing has worked. I get an error "1068", which I can't find something on. Help!
-
Satellite C50D-B-120 - unknown device ACPI\VEN_SMB & DEV_0001 Windows 10
I had to reinstall a new copy of Windows 10 and I can not find a Windows driver for my C50D-B-120 (ACPI\VEN_SMB & DEV_0001). I found one for a previous version of windows, but it does not load. Len
-
Dell Latitude D630 - lack of wireless network connection
I have a laptop Dell Latitude D630 and we re-installed a new version of Windows XP on top an old XP version. When the installation is complete, I went into network connections and all I have is the connection to the LAN. There is no wireless networ
-
Which groups of security/permissions are necessary for access to the API?
I have a user account API that belongs to the user "API" and "Everyone" security group.I get the following error during the processing of the API calls:[{"type": "PermissionError", "missingPermission": "read", "objectId": 130, "objectType": "Eloqua.A