Machines to restrict to a single VLAN
Hi all
I'm trying to figure out if there is a way to stop a single machine to eventually act as a bridge between the VLANS. Assuming that there are two local area networks VIRTUAL (operations 10 and 20 being secure), how we can ensure that a machine cannot be added with two NICs, VLAN10 connection and the other to VLAN20. Of course, being a VLAN secure, we would limit what MAC addresses can connect to a port VLAN20.
Any ideas? Is this just a risk that a client must accept when using VIRTUAL LANs for security rather than separate switches?
Has nothing to do with VLAN as such because the same still applies if you used physical separate switches IE. SW1 for vlan 10 and sw2 for vlan 20, then you on a PC with a NIC 2 for each switch.
If a user can add another NETWORK card and has the ability to connect its NIC 2 two VLAN / different switches in your network, then you have some very serious problems of physical security.
I guess what I'm trying to say is that Yes, you can use port-security etc... but the kind of problem you are exhibitor is much better addressed at the level of physical procedures.
Jon
Tags: Cisco Security
Similar Questions
-
How to assign a range of interfaces to a single VLAN?
How can I assign ports or multiple interfaces to a single VLAN. I use multilayer switches.
Hello
example of
interface series g1/0/1 - 18
switchport access vlan 10
-
Machine access restrictions in ACS 3.3
Can someone tell me how to implement on a device ACS 3.3 Machine access restrictions?
Machine must be a member of the domain / company before access to the wireless local area network is permitted...
DRM
Remco
The configuration you have the GBA:
-Authentication verified machine
-MAR activated, i.e. you checked, 'group authentication successful without authentication card machine' to a group, generally «»
Configuration of the client/supplicant:
-Client configured to send authentication of the computer information.
You take a computer that is part of the AD and was introduced on the network. This is the first time.
Start the computer to the top (for the first time).
Computer is configured to send credentials to the Machine, so he sends to the switch, sends switch ACS, ACS verifies whether or not the machine is a valid machine.
If this is the case, put in cache 'Calling-Station-Id' for the interval configured in this section.
(End user still cannot do anything yet, because MAR is still in process)
Computer has completed the guest of GINA.
End user presses Ctrl + Alt + Delete.
Type username/password (first time).
Computer transmits the credentials of the user to switch, then switch to ACS, ACS gets it checked against AD.
If the user is a valid user, the user is mapped to an ACS group, according to the mapping and is in.
IF the user authentication fails, even if the computer authentication succeeded.
Now, it was one of the scenarios, other is,
Your machine is NOT part of the AD, so eventually Machine authentication will fail. Suppose that the user trying to connect in network has a name of user and password valid, but the computer using the the it is not a part of the AD.
Then, you will get an error during the machine on "supplicant" as authentication.
You cannot connect blah blah area...
But you will be allowed to provide your name of user and password combination.
Generally MAR is implemented to restrict this access, i.e. users trying to connect into the corporate network using non-active society, who are the majority of the infected by the virus at the time.
It is the point where this option comes into play,
"Group card for user authentication successful without authentication machine."
So even if the authenticated user successfully, but from the machine that is not part of the AD, the user will be mapped to the group according to the above option.
What 'Calling-Station-Id' caching.
Even if the authentication was successful. ACS will check if the Calling-Station-Id is cached for the machine from where comes the good name of username/password? If this isn't the case, you use a wrong machine to connect to the network.
HTH
Kind regards
Prem
-
Standalone WAP several SSID to a single VLAN
I have an AIR-AP1142N-A-K9, I use for my home wireless. I am trying to use the 5 GHz and 2.4 GHz radio, so I can have the SSID and SSID [5 GHz] announced. It seems that I am unable to set multiple SSID to use a single VLAN. I searched a doc or config with this subject guide, but I came up empty. The config at the end that I'm looking creates four SSID. A guest and SSID private radio with the SSID of comments on one VLAN and the private SSID [encrypted] on another VIRTUAL local network. Any help is greatly appreciated.
Hello
Pls check this doc...
https://supportforums.Cisco.com/docs/doc-16087
If you still don't get work, please paste the config.
Thank you!
Concerning
Victor V"Help others using the system of rating and marking answers questions as * answered."
-
Add Virtual Machine Port Group vSwitch (network and Vlan ID tag) by Script
Hello
I want to add a port group of VM for about 200 guests vSwitch. This can be done manually, but if anyone can help me to do it with the help of Powercli. We have guests organized on the basis of clusters.
Virtual machine port group.
Tag network:-XYZ
VLAN ID: XYZ
Thank you
Pranab
You could do something like that
$clusterName = "cluster" $pgName = "test2" $vlanId = "1111" $vSwName = "vSwitch1" Get-Cluster -Name $clusterName | Get-VMHost | Get-VirtualSwitch -Name $vSwName | New-VirtualPortGroup -Name $pgName -VLanId $vlanId
It will add the portgroup to the vSwitch on all hosts in the cluster
____________
Blog: LucD notes
Twitter: lucd22
-
MAR machine access restrictions
Hello
I'm like to identify peripheral societies against BYOD. So, I'm using "WasMachineAuthenticated" State, this is my config:
ISE 1.3 Patch 3
Windows 7 with Machine and user auth supplicant. With the help of the PEAP Protocol.
I have Machine Auth and auth User policy.
In the external identity Sources, MAR is enabled with 192 hours aging time.
Lately, I read this topic, and I came across several comments on some reserves. What are these warnings?
Everyone has implementied successfully this feature? BTW, for me the chaining of EAP is not an option.
Thank you!
Tony
Hi Tony -.
Yes, MAR comes with many limitations and traps and therefore, I highly recommend that avoid you it. I posted this issue in previous discussions. Take a look at the following links and let me know if you have any other questions:
https://supportforums.Cisco.com/discussion/12209441/Cisco-ISE-machine-failed-machine-authentication
If the EAP chaining is not an option, then you have other options:
1. you can use the profiling and using the class identifier DHCP to distinguish Corp. machines vs non-corporate
2. you can use the evaluation of posture and the NAC agent looking for some hidden file or registry that have only machines (both the file and registry can be pushed via GPO)
3. you can also perform authentication to be 'Only Machine' this will prevent non-domaine joined machines to authenticate
I hope this helps!
Thank you for evaluating useful messages!
-
Specific machine accounts: restrict customers?
Hello!
If I have specific accounts for a computer lab machine, is there a way to prevent the aid of the other login clients?
ESXi 5.0, vCenter 5.0, 5.1 view.
Thank you!
You can use the Kiosk mode to link a customer to a vDesktop.
If they are zero-clients, then you can hardcode the username/password in the config of zero-customers.
Linjo
-
Tagged management VLAN and the virtual machines on the same VLAN
I'm faced with a problem related to our Brocade switches newly acquired and get the private VLAN to work on trunk connections to our ESX servers. Every time I try something different, he creates a new problem.
In our configuration, our management of VLAN is not tag and we have a VLAN for this management network that is placed on our switches VLAN no marked native. We also have virtual machines hosted on those same ESX servers that are on the same VLAN and everything works fine. However, when I change the ESX management to carry a label on this VLAN and change the switchports accordingly (IE no untagged VLAN native), management work, but hosted on the ESX Server machines that are on the same VLAN can get no network connectivity.
Is it possible to have a management network labeled and also the host of virtual machines on the same VLAN or is it totally impossible? I'm not very familiar with networking behind ESX, so I apologize if this is a dumb question with an obvious answer.
Thank you
Mark J.
Is it possible to have a management network labeled and also the host of virtual machines on the same VLAN or is it totally impossible?
Yes, it is possible... why it doesn't work for you I don't know, but try the following:
1. set up the Group of ports of VMS to use VLAN;
2 configure the interface of management VMkernel port group use VLAN;
3 configure the physical switch port to allow to this VLAN and put the default VLAN natively for these interfaces.
-
VLANS, assigning to VMware view pool
We have a large network with division into departments. Each Department corresponds to a single vlan with individual restrictions.
During the user of transport of the physical machine to the virtual machine, I need to save all these restrictions.
As I know the only way to assign the VLAN necessary for vm is to make main image separate VLAN correct.
Will there be another opportunity to assign VLAN necessary to the pool without a separate master image for each Department?
VMware View 4.6
You can assign the VLAN on a per master so a level of snapshot and multiple snapshots pointing to different VLAN. You can also read this article by André using powershell. http://myvirtualcloud.NET/?p=1838&utm_source=FeedBurner&utm_medium=feed&utm_campaign=feed%3A+Myvirtualcloudnet+%28myvirtualcloud.NET%29
-
Hi all
I understand that this vlan system allows the traffic flow for the vlan was VSM is not accessible, and vlan system should NOT be normal machine virtual traffic vlan. In my deployment of a normal vSphere environment with N1kv, I'll put these VLANS as system vlan: ESXi Mgmt N1kv mgmt, control & package, VMotion, storage over IP.
I put the VLANs as system vlan on the uplink port profiles and indivdual port profiles for each VIRTUAL local area network. Correct me if that's wrong.
What should be system vlan, or what those who shouldn't be system vlan? VMotion vlan? What are the disadvantages to specify all the VLANS as system vlan? Is it not better because even if VSM fell for a reason, MEC will still send traffic for all virtual machines?
Thank you
Ming
Ming,
Your understanding of the system VLAN is not totally accurate. All them VLAN will be forwarding the case where your VSM is not accessible. Each MEC module will continue to pass system and non-vlan traffic if the VSM is offline. EACH MEC will keep its current programming, but will not accept any changes until the VSM is back online. System VLAN behaves differently that they will always be in a State of transfer. VLAN systems will transmit the traffic even before that a MEC is programmed by VSM. That is why some system profiles demand them - IE. Control/package etc. These VLANs must be transferred in ORDER for the MEC to talk to the VSM.
As for your list of "what should be system VLAN"-remove VMotion. There is no reason that your VMotion network should be defined as a system of VIRTUAL LAN. All the others are correct.
Also remember that you can ONLY define a VLAN on the port profile an uplink. So if you use an uplink for 'system' type traffic and the other for traffic of type "Data VM", you would have just any single VLAN 'authorized' on an uplink - not both. Allowing them the time will cause problems. The only case, you have to keep in mind is that for a "system vlan" to apply, it must be defined on the Port of vEthernet profile and a profile of Uplink Port.
E.g.
Let's say my Service Console uses VLAN 10 and my VMs also use the VLAN 10 for their data traffic. (Bad design, but just to illustrate a point).
VLAN in "two places" seen set the system would you allow to treat ONLY the traffic of your "Service Console" as a traffic system and always apply security programming for your traffic "VLAN Data. After a reboot, you Console of Service traffic would be routed immediately, but your VM data would not be until the MEC had pulled the programming of the VSM.
profile port vethernet dvs_ServiceConsole type
VMware-port group
switchport mode access
switchport access vlan 10
no downtime
System vlan 10<== defined="" as="" system="">
enabled stateprofile port vethernet dvs_VM_Data_VLAN10 type
VMware-port group
switchport mode accessswitchport access vlan 10<== no="" system="">
no downtime
enabled stateprofile system uplink ethernet port type
VMware-port group
switchport mode trunk
switchport trunk allowed vlan 10, 3001-3002
Active Channel-Group auto mode
no downtime
System vlan 10, 3001-3002<== system="" vlan="" 10="">
enabled stateHope this clears your understanding.
Kind regards
Robert
-
I'm running an ISE 1.1.1 patch 2 and authetntication machine Windows XP using PEAP authentication with authentication computer and user.
The issue is that when a machine is powered on fine machine authentication processes and the user authentication is successful. The problem is that, after that the machine is connected to the left and left unattended for may hours I am bounced in a guest VLAN - ISE newspapers say that they can validate is no longer the machine has been authenticated via AD. If the user reboots the computer, he is well again.
Are there timers in AD or the machine that are hot flushes the status of RADIUS: WasMachineAuthenticated? Can someone tell me if there is a recommended configuration when the machine authentication is maintained throughout a work day or night?
Hello rcianci.
You experience this problem because of your authorization rule "WasMachineAuthenticated." This process (aka MAR - Machine access restrictions) occurs only when a computer is restarted or powered. Once the expiration of the timer to MAR the machine authentication fails until it is restarted again.
Here are two ways you can try to tackle this problem:
1. I used MAR in the past and:
a. set the timer for 168 hours (1 week)
b. educated users that they must restart their machines per week
It worked 'OK' but it's still irritating to the end users. It can also cause problems if you do that for cable and because the MAC address will change and ISE/ACS will not see the new authenticated as mac address, which requires the user to perform another reboot
2. a better way to be rid of MAR all together. If you want to keep things simple, you can just use PEAP machine based authentication using the credentials of the machine. It's not always ideal, but if your ad is correctly locked where only certain users can join computer to a domain then you should be good to go. However, if you want to continue to use the machine + user you will need to look at something a little more complex such as EAP-chaining.
I hope that this help... Let me know if you have any other questions
Thanks for the note!
-
Port - group VLAN ID Questions
Hi guys
Can I change change the running virtual machine port group?
in the case where the virtual machine was in a group of Port named test - VLAN ID 100 and I need to change the Port Group deployment VLAN ID 105 which now means my VM will not have access to traffic on vlan 100? It's automatically or I need to change my IP or something?
and this comes from the frequently asked questions
Q: a configurable virtual machine on several VLANs?
A: you can set up a single VLAN ID for each virtual network adapter on a virtual machine. However, since you can config -.
ERUS up to four virtual cards per virtual machine, you can configure a virtual machine that spans four different VLAN.
I think I'll need to set up several virtual LANs for some virtual machines. What do mean by "set up a virtual machine that spans four different VLAN".
Thank you guys
Yes, you can certainly change the portgroup. But, remember, your new VLAN is configured properly in order to maintain the networking of virtual machine after the change.
Max on max. position 2-3 drops of ping may occur depending on your use of the network and ESX utlization of resource for the change task.
Simply go to the settings-> virtual adapter - > select new vlan-> OK
If you want your traffic to be moved to a different VLAN dynamically, it must be done at the level of the physical switch. Think of the vswitch as a "dummy" switch layer 2, it will follow policies of networking of the physical switch only, sound rather a passage only. Everything depends on the new port (nic) configured to take the new vlan correctly or not.
NUTZ
VCP 3.5
(Preparation for VCP 4)
-
I'm pretty new to VSphere, go to the install/configure in November class but had a consultant come do a show dog & Pony and he said we could do VLAN tagging to allow all our VLAN's communicate via a single distributed switch connected to a physical switch port 1. I can't get to work - can I get some advice on what I'm wrong? Attached screenshot - any help is appreciated
Yes - 8 trade and assign each of them a single VLAN and then give them your virtual machines the portgroup appropriate.
-
"the machine virtual source is not recognized" using VMWare Converter stand-alone 4.01
All,
Shadow protect IT edition allows us to create backups of image files from our servers. We need the ability to convert files Shadow protect (SPF) in VMWare Server 2.x. files about half of our servers do not convert. We get a message that says: "the machine virtual source is not recognized. What gives? I know image backups are fine because I tested.
Any help would be appreciated.
Thank you.
vmnoob
We support only a few specific versions of ShadowProtect.
> StorageCraft ShadowProtect 2.0, 2.5, 3.0, 3.1 and 3.2
There may be additional restrictions when you attempt to use these types of files, such as the following from the Manual:
1. dynamic disks are not supported.
2. all the images in the backup of a machine must be in a single folder, without other images placed there.
3. for incremental images, so 16 incremental backups are supported.
4. images of systems with logical drives are not supported if the logical drive is also a system or an active volume
5. for volume-based cloning, all volumes on the disk until the active devices and the system must be saved.
5.1 for example, if a drive has four partitions, 1 to 4, with the partition as the active volume 2 and partition 3 as long as the system volume, the backup must include 1 to 3 partitions. (ShadowProtect only).
Kind regards
EvilOne
VMware vExpert 2009
NOTE: If your question or problem has been resolved, please mark this thread as answered and awarded points accordingly.
-
How to restrict multicast traffic to specific ports on GS716Tv3?
I can not find specific instructions to limit traffic of multicast on the smart switch GS715Tv3.
I need to force all multicast traffic to travel on a specific set of interfaces, or at least stay within a given virtual LAN on the switch to which it is native. All the changes you want multicast servers and listeners will be on these interfaces in their separate vLAN.
We have several GS715Tv3 switches configured identically, but multicast traffic does not pass between the switches.
Topology:
Eight GS716Tv3 smart switches, each configured with three VLANS identical.
No traffic should pass between these VLANS on the switch or pass between the switches
In other words, even if all the 8 switches each have a vLAN named "IOSubsystem", I do not considered the same vLAN.
.
vLAN 4 is corresponding to the hosts of Linux to address major
vLAN 5 is for the audio subsystem
vLAN 6 is for the IO subsystem
VLAN each switch 4 has two active ports, a session to the external interface of the main Linux host and the other to a central switch of 9th GS716Tv3 where a system of software development is also linked.
VLAN each 5 switch connects to the components of the audio subsystems (not shown).
VLAN each switch 6 has two active ports, a going inward a lead Linux host interface and one for the IO subsystem.
-> [vLAN4 | g10]---> [Switch #9]-+.
-> [vLAN4 | g9]-> [Linux host #1: eth0] |
[Switch #1]-> [vLAN6: g1]-> [Linux host #1 | eth1] |
-> [vLAN6: g2]-> [e/s 1 subsystem] |
|
-> [vLAN4 | g10]---> [Switch #9]- +---> [software Dev host]
-> [vLAN4 | g9]-> [Linux host #2: eth0] |
[Switch #2]-> [vLAN6: g1]-> [Linux host #2 | eth1] |
-> [vLAN6: g2]-> [subsystem/o 2] |
... ~
|
-> [vLAN4 | g10]---> [Switch #9]-+.
-> [vLAN4 | g9]-> [Linux host #8: eth0]
[Switch #8]-> [vLAN6: g1]-> [Linux host #8 | eth1]
-> [vLAN6: g2]-> [i/o subsystem #8]We get multicast traffic unwanted between each of these systems, causing corruption of our stream. We limit the multicast traffic on vLAN6 of each switch to stay on the vLAN6 of this specific switch.
Thanks for any help.
To switch the management VLAN to 4.
Make sure you have 2-way switch, one in VLAN4 in a VLAN1.
4 and apply the value of the system you use to a static IP address to the switch and confirm the access to the web configuration and then change "management VLAN ID. then pass the system that you use on the port or any VLAN 4, then you should have access, otherwise, wait about 60-90sec and try again, because you might have PLEASE and it will block anything on the port for just under its set to "Enabled" 'Fast Link '.
Then under "IP Configuration" value switches other IP address in IP range of VLAN4.
For the love of Simplisicty, unmarked ports should never be in 1 VLAN simultaneously.
And instead of using the point and click, goto "Port PVID Configuration" and just create the VLAN it.
Member of the PVID and VLAN the same thing for a port, on what VLAN, it must be in the database
And to confirm, you have a cable from switch to each VLAN? You can cut down on cables and ports if you tag/trunk ports to the next switch. then all VLAN 3 just 1 cable between each pair of switches, saving you at least 4 ports on each switch.
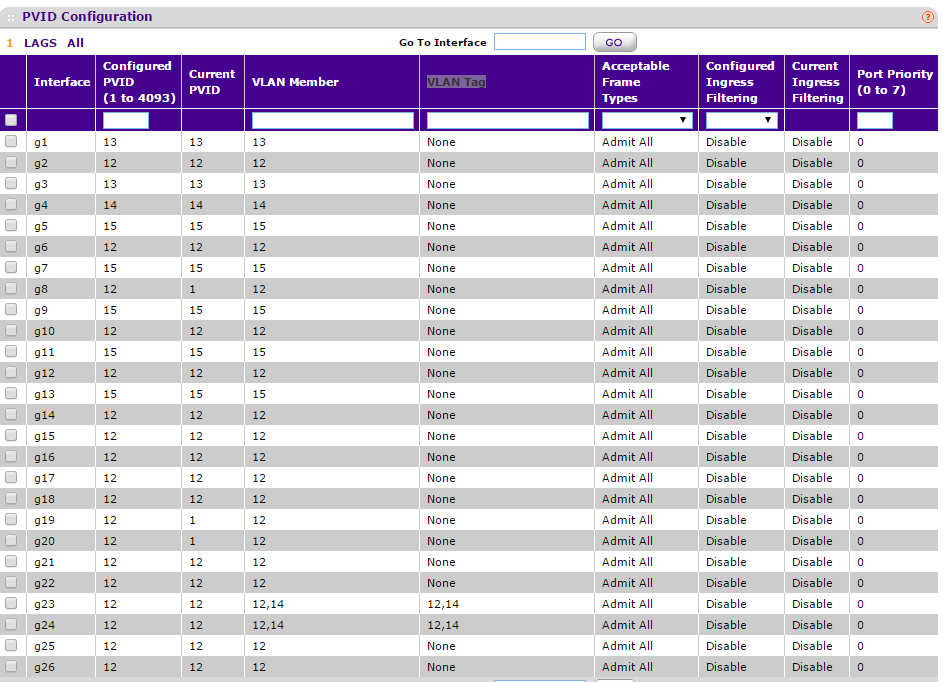
Just an example of my GS724T (ignore ports g8 and g-19-20, their current PVID is because of something else you do not, LACP and Span/Monitoring):
All ports are configured to a single VLAN, my 'LAN hand' is VLAN12, that the management VLAN is set for, g23-24 ports VLAN trunks, they are set on tagg VLAN12 and 14 when the traffic is out of these ports, then switch to the other side reads the consequence tagg and acts, that way I don't need 2 cables/port for each of them.
Maybe you are looking for
-
The page not to pin dusappear in the icon, just of the ot
-
Impossible to Document with HP Officejet 6310 all-in-One scanner
Dear all, I have a HP 6310 of all-in-one desktop. My scanner was working fine until I changed my PC running on Windows & Pro. I tried various solutions proposed by the community and the last test has been with HP Print & Scan Doctor 4.3. Follow the i
-
How to save or write notes (like memo) lenovo k3 notes.
-
No Windows Vista Boot Manager. Tried everything.
Yesterday, my computer was working fine. Now, I can't boot my computer without going through a "BootMGR is missing". I was looking at the previous post in this regard and could not make it work later. I have only the available recovery disc, so maybe
-
Problem to shrink my local C drive and create new partitions on this subject.
I am shrinking my local disk C (current boot volume) and create new partitions on this subject. But I get a warning message that if I do, I won't be able to boot from any excepet volume the current boot Volume. In case if I need to recovery my laptop