No.-xauth, mode-config-No.
What is the meaning of [No.-xauth, no.-config-mode]?
Disable the VPN software if executed [No.-xauth, no.-config-mode] connection?
Hello
No.-xauth is used authentication extended, which must have the user prompted for a user name and password before you connect
No-config-mode is used to disable the push of data to the user who connects via the VPN client as the ip address, the DNS server, the WINS server...
both of the above are required to exist when you connect using a VPN client software.
I hope that the above answers your questions.
Sincere greetings,
Shadi'
Tags: Cisco Security
Similar Questions
-
Cisco RV220W IPSec VPN problem Local configuration for any config mode
Dear all,
I need help, I am currently evaluating RV220W for VPN usage but I'm stuck with the config somehow, it seems that there is a problem with the Mode-Config?
What needs to be changed or where is my fault?
I have installed IPSec according to the RV220W Administrator's Guide. Client's Mac with Mac Cisco IPSec VPN, I also tried NCP Secure Client.
I have 3 other sites where the config on my Mac works fine, but the Cisco VPN router is not.
2013-03-07 01:55:49: [CiscoFirewall] [IKE] INFO: remote for found identifier "remote.com" configuration
2013-03-07 01:55:49: [CiscoFirewall] [IKE] INFO: application received for the negotiation of the new phase 1: x.x.x.x [500]<=>2.206.0.67 [53056]
2013-03-07 01:55:49: [CiscoFirewall] [IKE] INFO: early aggressive mode.
2013-03-07 01:55:49: [CiscoFirewall] [IKE] INFO: received unknown Vendor ID
2013-03-07 01:55:49: [CiscoFirewall] [IKE] INFO: received Vendor ID: RFC 3947
2013-03-07 01:55:49: [CiscoFirewall] [IKE] INFO: received unknown Vendor ID
2013-03-07 01:55:49: [CiscoFirewall] [IKE] INFO: received unknown Vendor ID
2013-03-07 01:55:49: [CiscoFirewall] [IKE] INFO: received unknown Vendor ID
2013-03-07 01:55:49: [CiscoFirewall] [IKE] INFO: received unknown Vendor ID
2013-03-07 01:55:49: [CiscoFirewall] [IKE] INFO: received unknown Vendor ID
2013-03-07 01:55:49: [CiscoFirewall] [IKE] INFO: received unknown Vendor ID
2013-03-07 01:55:49: [CiscoFirewall] [IKE] INFO: received unknown Vendor ID
2013-03-07 01:55:49: [CiscoFirewall] [IKE] INFO: received unknown Vendor ID
2013-03-07 01:55:49: [CiscoFirewall] [IKE] INFO: received Vendor ID: draft-ietf-ipsec-nat-t-ike-02
2013-03-07 01:55:49: [CiscoFirewall] [IKE] INFO: received Vendor ID: draft-ietf-ipsra-isakmp-xauth-06.txt
2013-03-07 01:55:49: [CiscoFirewall] [IKE] INFO: received Vendor ID: CISCO - UNITY
2013-03-07 01:55:49: [CiscoFirewall] [IKE] INFO: received Vendor ID: DPD
2013-03-07 01:55:49: [CiscoFirewall] [IKE] INFO: for 2.206.0.67 [53056], version selected NAT - T: RFC 39472013-03-07 01:55:50: [CiscoFirewall] [IKE] INFO: floating ports NAT - t with peer 2.206.0.67 [52149]
2013-03-07 01:55:50: [CiscoFirewall] [IKE] INFO: NAT - D payload is x.x.x.x [4500]
2013-03-07 01:55:50: [CiscoFirewall] [IKE] INFO: NAT - D payload does not match for 2.206.0.67 [52149]
2013-03-07 01:55:50: [CiscoFirewall] [IKE] INFO: NAT detected: Peer is behind a NAT device
2013-03-07 01:55:50: [CiscoFirewall] [IKE] INFO: request sending Xauth for 2.206.0.67 [52149]
2013-03-07 01:55:50: [CiscoFirewall] [IKE] INFO: ISAKMP Security Association established for x.x.x.x [4500] - 2.206.0.67 [52149] with spi: 1369a43b6dda8a7d:fd874108e09e207e
2013-03-07 01:55:50: [CiscoFirewall] [IKE] INFO: type of the attribute "ISAKMP_CFG_REPLY" from 2.206.0.67 [52149]
2013-03-07 01:55:50: [CiscoFirewall] [IKE] INFO: connection for the user "Testuser".
2013-03-07 01:55:50: [CiscoFirewall] [IKE] INFO: type of the attribute "ISAKMP_CFG_REQUEST" from 2.206.0.67 [52149]
2013-03-07 01:55:50: [CiscoFirewall] [IKE] ERROR: local configuration for 2.206.0.67 [52149] has no config mode
2013-03-07 01:55:50: [CiscoFirewall] [IKE] ERROR: local configuration for 2.206.0.67 [52149] has no config mode
2013-03-07 01:55:50: [CiscoFirewall] [IKE] ERROR: local configuration for 2.206.0.67 [52149] has no config mode
2013-03-07 01:55:50: [CiscoFirewall] [IKE] ERROR: local configuration for 2.206.0.67 [52149] has no config mode
2013-03-07 01:55:50: [CiscoFirewall] [IKE] WARNING: ignored attribute 5
2013-03-07 01:55:50: [CiscoFirewall] [IKE] ERROR: local configuration for 2.206.0.67 [52149] has no config mode
2013-03-07 01:55:50: [CiscoFirewall] [IKE] ERROR: local configuration for 2.206.0.67 [52149] has no config mode
2013-03-07 01:55:50: [CiscoFirewall] [IKE] ERROR: local configuration for 2.206.0.67 [52149] has no config mode
2013-03-07 01:55:50: [CiscoFirewall] [IKE] ERROR: local configuration for 2.206.0.67 [52149] has no config mode
2013-03-07 01:55:50: [CiscoFirewall] [IKE] WARNING: attribute ignored 28678
2013-03-07 01:55:50: [CiscoFirewall] [IKE] ERROR: local configuration for 2.206.0.67 [52149] has no config mode
2013-03-07 01:55:50: [CiscoFirewall] [IKE] ERROR: local configuration for 2.206.0.67 [52149] has no config mode
2013-03-07 01:55:50: [CiscoFirewall] [IKE] ERROR: local configuration for 2.206.0.67 [52149] has no config mode
2013-03-07 01:55:50: [CiscoFirewall] [IKE] ERROR: local configuration for 2.206.0.67 [52149] has no config mode
2013-03-07 01:55:50: [CiscoFirewall] [IKE] WARNING: attribute ignored 28683
2013-03-07 01:56:07: [CiscoFirewall] [IKE] INFO: purged-with proto_id = ISAKMP and spi = 1369a43b6dda8a7d:fd874108e09e207e ISAKMP Security Association.
2013-03-07 01:56:08: [CiscoFirewall] [IKE] INFO: ISAKMP Security Association deleted for x.x.x.x [4500] - 2.206.0.67 [52149] with spi: 1369a43b6dda8a7d:fd874108e09e207e
Hi Mike, the built-in client for MAC does not work with the RV220W. The reason is, the MAC IPSec client is the same as the Cisco VPN 5.x client.
The reason that this is important is that the 5.x client work that on certain small business products include the SRP500 and SA500 series.
I would recommend that you search by using a client VPN as Greenbow or IPSecuritas.
-Tom
Please mark replied messages useful -
Impossible to activate the dark mode in Firefox 39.0 with subject: config.
After you have installed the 39.0 beta of Firefox, I was impossible to activate the dark by topic mode: config.
That's what I changed:
Browser.devedition.Theme.Enabled: true
devtools. Theme: black
lightweightThemes.selectedThemeID: [email protected]I use "Fox, but better" plugin and I have to disable it without success.
guigs2 said
Hi CiRiX,
I understand that you are using a dark theme and have changed the settings in topic: config, that could change how the button toggle works in the themes section for about: addons...It is possible to reinstall the extension, or try these troubleshooting steps:
I managed to fix it by clicking Activate and then deactivate it on another theme.
Thanks for your help!
-
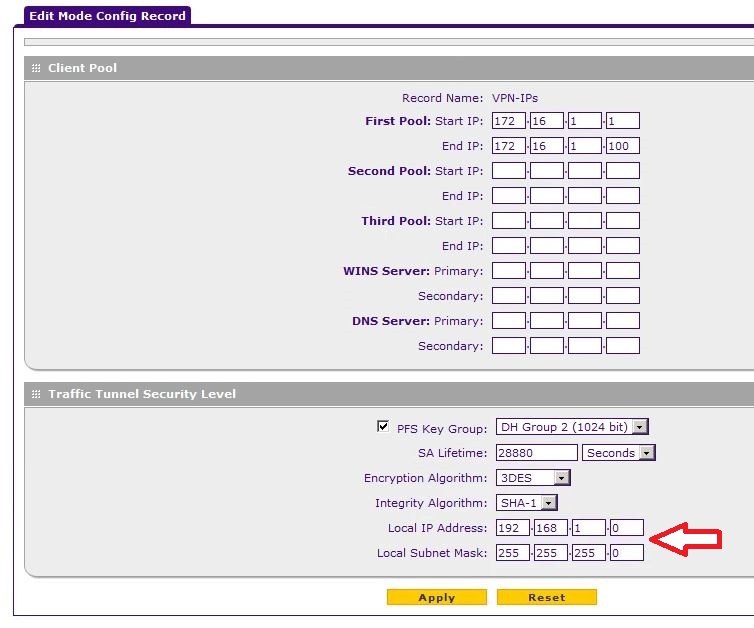
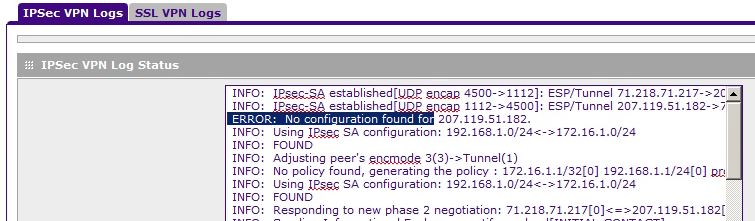
SRX5308 IPsec Config Mode - [IKE] ERROR: no configuration is found for...
I have a real simple setup for Client-to-gateway VPN installation. Base tunnels seem to work fine, but when I try to install
a policy of Mode Config I get an error in the connection and cannot ping resources on the local VPN network.
The local IP address at the end of check-in Mode Config is 192.168.1.0. The manual says to leave the field empty and it will default to the address of the gateway, which is 192.168.1.1. If I leave the field blank this wrong address gets automatically enrolled and if I try to manually enter the right one I get an error saying it's an invaild address?
Then when I connect, I get the following error:
I think that is the question. How to work around this problem or do it properly? The manual is not any help and I googled my old brian dead.
Thanks for any idea that you can give me!
CC
Thanks for the reply okadis and thanks for the link to this site, it is very useful!
I was able to find a solution. Turns out that the works of very good firewall configuration. All I had to do was use the remote configuration of the CLIENT as the LAN address 192.168.1.0, and then everything worked.
Now, for me, it's 2 "bugs" in the SRX5308 of Mode Config record:
1 192.168.1.0 is not the address of the Local network subnet, it is 192.168.1.1; The manual says if left blank by default subnet LAN, which it isn't, it's default 192.168.1.0
2. it won't let you enter ANY ip address here. It must be left blank.
Maybe I'm missing something here, but it works perfectly after using what is there in the end customer.
Should have been simple. Well...
CC
-
Hello
I have VPN 3005 with 4.7.2 OS (a last to this day). I am trying to turn off the Mode aggressive treatment (stick to the main Mode only) for VPN clients to remove. Please note that remote VPN clients and NOT the LAN-to-LAN connections.
So far I don't see how this can be done.
TAC engineer is not to come up with more good responses.
In any case has an idea?
Thank you!
David
I don't think you can do the Remoting on VPN
the hub works with the main mode, unless
you decide to use the certificate instead of
pre-shared key:
"The Cisco VPN client uses main mode and aggressive mode pre-shared keys are used when the public key (PKI) infrastructure is used in Phase 1 of the tunnel negotiations. After wearing the Internet Security Association and Key Management Protocol (ISAKMP Security Association) Association Security upward for secure communications, Cisco VPN 3000 Concentrator prompts the user to specify the credentials of the user. In this phase, also known under the name X-Auth or extended authentication, the VPN 3000 Concentrator valid user on the database of authentication configured. If authentication success, the Cisco Concentrator sends a message of successful customer authentication. After X-Auth, the Cisco VPN client application configuration settings such as the assigned IP address, the domain name system (DNS) server IP address and the IP address of the Server Windows Internet Naming Service (WINS). During this phase, called mode-config, the VPN 3000 Concentrator sends the settings configured at the client. The final step for a VPN tunnel successful is negotiating the parameters of Phase 2.
-
Problems to connect via the Cisco VPN client IPSec of for RV180W small business router
Hello
I tried to configure my router Cisco of RV180W as a customer VPN IPSec, but have encountered a problem that I hope someone can help me with. "" I managed to do the work of configuration so that the Cisco's VPN IPSec client authenticates successfully with the XAUTH user, I put on the router, but during the negotiation, the client ends with the following, which appears several times on the router error message: ' Mar 20 Oct 19:41:53 2015 (GMT + 0000): [r1] [IKE] ERROR: local configuration for
> [34360] has no config mode. I've read around the internet and a number of people seem to say that the Cisco VPN Client is not compatible with the router, but the same thing happens to my iPhone VPN client.
Is it possible that this can be implemented? Below, I have attached the full configuration files and the log files. Thank you much in advance.
Router log file (I changed the IP
addresses > respectively as well as references to MAC addresses) Mar 20 Oct 20:03:10 2015 (GMT + 0000): [r1] [IKE] INFO: floating ports NAT - T with counterpart
> [44074]
Mar 20 Oct 20:03:10 2015 (GMT + 0000): [r1] [IKE] WARNING: notification to ignore INITIAL-CONTACT> [44074] because it is admitted only after the phase 1.
Mar 20 Oct 20:03:10 2015 (GMT + 0000): [r1] [IKE] INFO: NAT - D payload does not match for> [4500]
Mar 20 Oct 20:03:10 2015 (GMT + 0000): [r1] [IKE] INFO: NAT - D payload does not match for> [44074]
Mar 20 Oct 20:03:10 2015 (GMT + 0000): [r1] [IKE] INFO: received unknown Vendor ID
Mar 20 Oct 20:03:10 2015 (GMT + 0000): [r1] [IKE] INFO: received Vendor ID: CISCO-UNITY
Mar 20 Oct 20:03:10 2015 (GMT + 0000): [r1] [IKE] INFO: NAT detected: is located behind a device. NAT and alsoPeer is behind a NAT device
Mar 20 Oct 20:03:10 2015 (GMT + 0000): [r1] [IKE] INFO: request sending Xauth for> [44074]
Mar 20 Oct 20:03:10 2015 (GMT + 0000): [r1] [IKE] INFO: ISAKMP Security Association established for> [4500] - > [44074] with spi = >.
Mar 20 Oct 20:03:15 2015 (GMT + 0000): [r1] [IKE] INFO: receives the type of the attribute 'ISAKMP_CFG_REPLY' of> [44074]
Mar 20 Oct 20:03:15 2015 (GMT + 0000): [r1] [IKE] INFO: login successful for the user "myusername".
Mar 20 Oct 20:03:15 2015 (GMT + 0000): [r1] [IKE] INFO: myusername XAuthUser connected from the IP>
Mar 20 Oct 20:03:15 2015 (GMT + 0000): [r1] [IKE] INFO: sending of information Exchange: Notify payload [10381]
Mar 20 Oct 20:03:15 2015 (GMT + 0000): [r1] [IKE] INFO: receives the type of the attribute 'ISAKMP_CFG_REQUEST' of> [44074]
Mar 20 Oct 20:03:15 2015 (GMT + 0000): [r1] [IKE] ERROR: local configuration for> [44074] has no config mode
Mar 20 Oct 20:03:15 2015 (GMT + 0000): [r1] [IKE] ERROR: local configuration for> [44074] has no config mode
Mar 20 Oct 20:03:15 2015 (GMT + 0000): [r1] [IKE] ERROR: local configuration for> [44074] has no config mode
Mar 20 Oct 20:03:15 2015 (GMT + 0000): [r1] [IKE] ERROR: local configuration for> [44074] has no config mode
Mar 20 Oct 20:03:15 2015 (GMT + 0000): [r1] [IKE] WARNING: ignored attribute 5
Mar 20 Oct 20:03:15 2015 (GMT + 0000): [r1] [IKE] ERROR: local configuration for> [44074] has no config mode
Mar 20 Oct 20:03:15 2015 (GMT + 0000): [r1] [IKE] ERROR: local configuration for> [44074] has no config mode
Mar 20 Oct 20:03:15 2015 (GMT + 0000): [r1] [IKE] ERROR: local configuration for> [44074] has no config mode
Mar 20 Oct 20:03:15 2015 (GMT + 0000): [r1] [IKE] ERROR: local configuration for> [44074] has no config mode
Mar 20 Oct 20:03:15 2015 (GMT + 0000): [r1] [IKE] ERROR: local configuration for> [44074] has no config mode
Mar 20 Oct 20:03:15 2015 (GMT + 0000): [r1] [IKE] ERROR: local configuration for> [44074] has no config mode
Mar 20 Oct 20:03:15 2015 (GMT + 0000): [r1] [IKE] WARNING: attribute ignored 28683
Mar 20 Oct 20:03:15 2015 (GMT + 0000): [r1] [IKE] ERROR: local configuration for> [44074] has no mode config
Mar 20 Oct 20:03:15 2015 (GMT + 0000): [r1] [IKE] WARNING: attribute ignored 28684
Mar 20 Oct 20:03:15 2015 (GMT + 0000): [r1] [IKE] ERROR: local configuration for> [44074] has no config mode
Mar 20 Oct 20:03:15 2015 (GMT + 0000): [r1] [IKE] ERROR: local configuration for> [44074] has no mode config
Mar 20 Oct 20:03:15 2015 (GMT + 0000): [r1] [IKE] ERROR: remove the invalid payload with doi:0.
Mar 20 Oct 20:03:15 2015 (GMT + 0000): [r1] [IKE] INFO: purged-Association of ISAKMP security with proto_id = ISAKMP and spi =>.
Mar 20 Oct 20:03:15 2015 (GMT + 0000): [r1] [IKE] INFO: myusername XAuthUser Logged Out of the IP>
Mar 20 Oct 20:03:16 2015 (GMT + 0000): [r1] [IKE] INFO: ISAKMP Security Association deleted for> [4500] - > [44074] with spi = > The router configuration
IKE policy
VPN strategy
Client configuration
Hôte : < router="" ip=""> >
Authentication group name: remote.com
Password authentication of the Group: mysecretpassword
Transport: Enable Transparent Tunneling; IPSec over UDP (NAT/PAT)
Username: myusername
Password: mypassword
Please contact Cisco.
Correct, the RV180 is not compatible with the Cisco VPN Client. The Iphone uses the Cisco VPN Client.
You can use the PPTP on the RV180 server to connect a PPTP Client.
In addition, it RV180 will allow an IPsec connection to third-party customers 3. Greenbow and Shrew Soft are 2 commonly used clients.
-
This is perhaps a silly question, but I am at a loss to see what the problem is.
I have a 515 on my site and am trying to install a few small 501 office across the country.
Each office can connect and establish a tunnel when I configure use EZ and I a setting up split-tunnel to pass to the Internet or to me every time.
If for some reason, I have to restart my PIX or my T1 goes down, they lose the tunnel (of course), but they lose also any Internet connection they have. The only way to get them reconnected to the world must go and uncheck the box "use the EZVPN."
At the end of the day, I don't want to then lose all connectivity when / if I get off.
What I forget?
Thanks in advance.
Robert Crooks
Network systems administrator
Ivaco Rolling Mills
try to add no.-xauth-no-config-mode to your statement of isakmp key.
ISAKMP key YOURPASSWORD address 192.168.1.2 subnet 255.255.255.255 mask no.-xauth-config-mode no.
or try to run with this documentation
-
IPSec between an IOS device and a PIX
Hello
I'm not able to successfully establish an IPSec tunnel between an IOS (2600 router) box running 12.3 (9) and PIX501 pixos 6.2 running. I see the following error on 2600.
* 06:09:50.416 Mar 10: ISAKMP (0:1): retransmission phase 1 MM_SA_SETUP...
* 06:09:50.416 Mar 10: ISAKMP (0:1): will increment the error counter on his: broadcast
Phase 1
And on PIX501 following error message:
ISAKMP (0): ITS been pre-shared key, using id ID_IPV4_ADDR type authentication
to return to the State is IKMP_NO_ERROR
crypto_isakmp_process_block: CBC 9.8.1.2, dest 9.2.1.2
Exchange OAK_MM
ISAKMP (0): processing KE payload. Message ID = 0
ISAKMP (0): processing NONCE payload. Message ID = 0
ISAKMP (0): load useful treatment vendor id
ISAKMP (0): load useful treatment vendor id
ISAKMP (0): Peer Remote supports dead peer detection
ISAKMP (0): load useful treatment vendor id
ISAKMP (0): addressing another box of IOS!
ISAKMP (0): load useful treatment vendor id
ISAKMP (0): provider v6 code received xauth
to return to the State is IKMP_ERR_RETRANS
crypto_isakmp_process_block: CBC 9.8.1.2, dest 9.2.1.2
Exchange OAK_MM
I am able to ping the external interface of a box form another. Any idea what I might be missing?
Thanks in advance,
Krishna
The commands that I configured on 2600 as follows:
crypto ISAKMP policy 1
md5 hash
preshared authentication
Group 2
life 1200
cisco key crypto isakmp 9.2.1.2 address
ISAKMP crypto keepalive 50 10
!
life 1800 seconds crypto ipsec security association
!
Crypto ipsec transform-set esp - esp-sha-hmac krishnas
!
!
Krishnas 1 ipsec-isakmp crypto map
defined peer 9.2.1.2
game of transformation-krishnas
match address krishnas
!
!
!
!
interface FastEthernet0/0
IP 192.168.243.1 255.255.255.0
automatic speed
full-duplex
!
interface FastEthernet0/1
Description outside the interface to the cloud
bandwidth 10000
IP 9.8.1.2 255.255.0.0
automatic speed
Half duplex
card crypto krishnas
!
!
krishnas extended IP access list
IP 192.168.243.0 allow 0.0.0.255 192.168.244.0 0.0.0.255
The commands that I configured on PIX501:
IP 192.168.244.0 allow Access-list krishnas 255.255.255.0 192.168.243.0 255.255.255.0
Permitted connection ipsec sysopt
Crypto ipsec transform-set esp - esp-sha-hmac krishnas
Krishnas 1 ipsec-isakmp crypto map
card crypto krishnas 1 corresponds to the krishnas address
krishnas 1 peer set 9.8.1.2 crypto card
card crypto krishnas 1 the transform-set krishnas value
krishnas outside crypto map interface
ISAKMP allows outside
ISAKMP key cisco address 9.8.1.2 netmask 255.255.255.255 No.-xauth No.-config-mode
isakmp identity = address
ISAKMP keepalive 50 10
part of pre authentication ISAKMP policy 1
of ISAKMP policy 1 encryption
ISAKMP policy 1 md5 hash
Group of ISAKMP policy 1 2
ISAKMP policy 1 life 1200
Hello Krishna
If possible and feasible to try and downgrade the IOS 12.3 (9) to a low-level code as 12.3.6. But, make sure that the image is a single k9 and supports VPN. Also upgrade the pix to 6.3.3.
Assuming that the keys are the same, your configs find ok. Him debugs it seems its not able to pass from the phase 1 properly
could contribute to modify the code.
Concerning
Wakif
-
Two tunnels from site to site and vpnclient access
I have 2 remote sites, 1 with a static ip address and 1 with a dynamic ip address, they connect to a central site that has a PIX 501. I could get 2 ipsec tunnels works well for awhile, but my client wants to just now the possibility of having workers use the vpnclient to connect to the PIX as well. The problem I have is after you have added the config of vpngroup my site with the dynamic ip address can no longer connect. I had to use the ip address they have now and install an aditional counterpart in the card crypto, but if this ip address change I have to come in and change the config.
Here's the relevant info in the config:
IPSec ip 192.168.100.0 access list allow 255.255.255.0 192.168.150.0 255.255.255.0
IP 192.168.100.0 allow Access-list sheep 255.255.255.0 192.168.150.0 255.255.255.0
IP 192.168.100.0 allow Access-list sheep 255.255.255.0 192.168.125.0 255.255.255.0
IP 192.168.100.0 allow Access-list sheep 255.255.255.0 192.168.101.0 255.255.255.0
ipsec2 192.168.100.0 ip access list allow 255.255.255.0 192.168.125.0 255.255.255.0
Permitted connection ipsec sysopt
Crypto ipsec transform-set esp - esp-md5-hmac oadcset
Crypto-map dynamic oadcdynmap 30 transform-set oadcset
oadcmap 21 ipsec-isakmp crypto map
oadcmap 21 match address ipsec crypto map
oadcmap 21 crypto map set peer
card crypto oadcmap 21 transform-set oadcset
oadcmap 22 ipsec-isakmp crypto map
card crypto oadcmap 22 correspondence address ipsec2
crypto oadcmap 22 card set peer
card crypto oadcmap 22 transform-set oadcset
map oadcmap 25-isakmp ipsec crypto dynamic oadcdynmap
oadcmap interface card crypto outside
ISAKMP allows outside
ISAKMP key * address
netmask 255.255.255.255 No.-xauth-no-config-mode ISAKMP key * address
netmask 255.255.255.255 No.-xauth-no-config-mode ISAKMP identity address
part of pre authentication ISAKMP policy 21
encryption of ISAKMP policy 21
ISAKMP strategy 21 md5 hash
21 2 ISAKMP policy group
ISAKMP strategy life 21 28800
vpngroup address oadcclient pool oadcgroup
vpngroup dns 192.168.100.3 Server oadcgroup
vpngroup oadcgroup by default-field clientdomain.com
vpngroup idle 1800 oadcgroup-time
vpngroup password oadcgroup *.
Any help is appreciated,
Ken
Permitted connection ipsec sysopt
Crypto ipsec transform-set esp - esp-md5-hmac oadcset
Crypto-map dynamic oadcdynmap1 30 set transform-set oadcset
Dynamic crypto map match 30 oadcdynmap1 address ipsec2
Crypto-map dynamic oadcdynmap 30 transform-set oadcset
oadcmap 21 ipsec-isakmp crypto map
oadcmap 21 match address ipsec crypto map
oadcmap 21 crypto map set peer
card crypto oadcmap 21 transform-set oadcset
oadcmap 22 card crypto ipsec-isakmp dynamic oadcdynmap1
map oadcmap 25-isakmp ipsec crypto dynamic oadcdynmap
Try this and see if it helps. I have something similar on a router do not know if the PIX supports. Worth a try if
-
I have a site2site between PIX506 and 877 router VPN. Site A has PIX506 and Site B router a in 877. I configured site2site VPN and it worked fine. I also configured remote VPN on PIX 506 so that the remote user can access A site. But when I configure remote VPN on PIX506 site2site VPN works and both sides can ping each other. But site B users cannot access any resource network or application of the SiteA while site A can access resources of site B. After removing remote VPN site configuration B can access the resources of the Site I joined the configuration of the two sites. Someone help me please site2site and remote VPN work at the same time.
Please forgive me for not reading every line.
an add-on quick about the pix configuration:
change "isakmp key * address 213.181.169.8 netmask 255.255.255.255" at "isakmp key * address 213.181.169.8 netmask 255.255.255.255 No.-xauth No. config-mode.
-
L2l VPN not to come, or is it?
I was banging my head against a wall, trying to understand it, and I am puzzled. I tried to set up a VPN LAN to LAN between our network (Pix515e) and AT & T (router IOS). AT & T has provided the following configuration information.
Peers of ATT address is 209.183.xxx.yyy
IKE Phase I parameters:
3DES
SHA1 or md5
pre-shared key
DH group 2
Parameters IPSec phase II:
3DES
SHA
Preshared key: *.
ATT ACL or list of Local or remote network:
IP 192.168.80.0 allow 0.0.0.255 192.168.3.0 0.0.0.15
Here's my config, which must correspond to their. You can also see my hit counters go up for sheep traffic and interesting.
**********************************************************************************************************************************
IPSEC configuration
**********************************************************************************************************************************
ATTIPSecACL 192.168.3.0 ip access list allow 255.255.255.240 192.168.80.0 255.255.255.0
Crypto ipsec transform-set esp-3des esp-sha-hmac att
SSVPN 9 ipsec-isakmp crypto map
card crypto SSVPN 9 corresponds to the address ATTIPSecACL
card crypto SSVPN 9 set peer 209.183.xxx.yyy
card crypto SSVPN 9 the transform-set att value
ISAKMP key * address 209.183.xxx.yyy netmask 255.255.255.255 No.-xauth-no-config-mode
part of pre authentication ISAKMP policy 7
ISAKMP strategy 7 3des encryption
ISAKMP strategy 7 md5 hash
7 2 ISAKMP policy group
ISAKMP strategy 7 life 28800
part of pre authentication ISAKMP policy 9
ISAKMP policy 9 3des encryption
ISAKMP policy 9 sha hash
9 2 ISAKMP policy group
ISAKMP policy 9 life 28800
permit for line ATTIPSecACL access-list 1 ip 192.168.3.0 255.255.255.240 192.168.80.0 255.255.255.0 (hitcnt = 161)
allowed to Access-list sheep line 16 ip 192.168.3.0 255.255.255.240 192.168.80.0 255.255.255.0 (hitcnt = 5312)
**********************************************************************************************************************************
Due to limitations of size, I'll post the debugging in a second post.
Well Yes, you would have been able to determine this by the message of notify returned from the peer:
ISAKMP (0): processing NOTIFY payload 14 Protocol 3
14 message notification is a message of "NO_PROPOSAL_CHOSEN" which indicates a failure Phase 2 SA submitted
-
Hi, I currently have a site to site vpn upward and running and it works fine. I try to put the other two online and just cannot make them work. I used the same configuration of one operation but I cannot get the next tunnel. I saw several errors when debugging isakmp and ipsec and they are at the end of my configs. Anyone have any ideas? Thank you
Main site - a vpn clients connecting too it and pt to pt vpn to 3 endpoints
Cisco PIX Firewall Version 6.3 (3)
* Main Site Config *.
client_vpn 10.10.0.0 ip access list allow 255.255.0.0 192.168.0.0 255.255.255.0
VPN_to_Site2 10.10.0.0 ip access list allow 255.255.0.0 192.168.0.0 255.255.255.0
NAT (inside) 0-list of access client_vpn
Permitted connection ipsec sysopt
Crypto ipsec transform-set esp-3des esp-md5-hmac fws_encry_set
outside_map 60 ipsec-isakmp crypto map
address for correspondence card crypto outside_map 60 VPN_to_Site2
crypto outside_map 60 peer 64.X.X.19 card game
card crypto outside_map 60 transform-set fws_encry_set
outside_map interface card crypto outside
ISAKMP allows outside
ISAKMP key * address 64.X.X.19 netmask 255.255.255.255 No.-xauth-no-config-mode
ISAKMP identity address
ISAKMP nat-traversal 20
part of pre authentication ISAKMP policy 10
ISAKMP policy 10 3des encryption
ISAKMP policy 10 md5 hash
10 2 ISAKMP policy group
ISAKMP life duration strategy 10 86400
Site 2 config
* only because the pt to pt does not work I have it set up to allow vpn clients to cross to connect to the main site.
Cisco PIX Firewall Version 6.3 (5) *.
permit access ip 192.168.0.0 list VPN_to_Main 255.255.255.0 10.10.0.0 255.255.0.0
NAT (inside) 0-list of access VPN_to_Main
Permitted connection ipsec sysopt
Crypto ipsec transform-set esp-3des esp-md5-hmac fws_encry_set
outside_map 10 ipsec-isakmp crypto map
outside_map card crypto 10 corresponds to the address VPN_to_Main
crypto outside_map 10 peer 207.X.X.13 card game
card crypto outside_map 10 transform-set fws_encry_set
outside_map interface card crypto outside
ISAKMP allows outside
ISAKMP key * address 207.X.X.13 netmask 255.255.255.255 No.-xauth-no-config-mode
ISAKMP identity address
ISAKMP nat-traversal 20
part of pre authentication ISAKMP policy 10
ISAKMP policy 10 3des encryption
ISAKMP policy 10 md5 hash
10 2 ISAKMP policy group
ISAKMP life duration strategy 10 86400
Errors
PIX (config) # IPSEC (sa_initiate): ACL = deny; No its created
authenticator is HMAC-MD5IPSEC (validate_proposal): invalid local address
I have a link that works very well. I have copied the config from there, changed the ip info and it does not work. The only differences in the configs are no sysopt route dnat and it's on Version 6.2 (2)
IPSec (sa_initiate): ACL = deny; No its created
I think that you have configured a VPN tunnel without removing the cryptographic card of the external interface. The message above is the error we get in such situation.
I suggest the following solution:
-remove the external interface (the two pix) cryptographic card
-Cree claire isa his and trendy clear ipsec his (the two pix)
-Reapply the card encryption on external interfaces.
If this doesn't solve the problem, restart the equipment.
Kind regards
Ajit
-
I need help setting up a Cisco PIX 506th Version 6.3 (5)
I use the PDM to configure the device, because I don't know enough of CLI. I want to just the simplest of configurations.
Here is what is happening, I set up then I hang the Interface 1 to my laptop and use DHCP to get an ip address, but I can't get out to the internet like that. Thanks PDM tools, I can ping outside the IPS very well.
6.3 (5) PIX version
interface ethernet0 car
Auto interface ethernet1
ethernet0 nameif outside security0
nameif ethernet1 inside the security100
activate the encrypted password of DkreNA9TaOYv27T8
c4EBnG8v5uKhu.PA encrypted passwd
hostname EWMS-PIX-630
domain ciscopix.com
fixup protocol dns-length maximum 512
fixup protocol ftp 21
fixup protocol h323 h225 1720
fixup protocol h323 ras 1718-1719
fixup protocol http 80
fixup protocol rsh 514
fixup protocol rtsp 554
fixup protocol sip 5060
fixup protocol sip udp 5060
fixup protocol 2000 skinny
fixup protocol smtp 25
fixup protocol sqlnet 1521
fixup protocol tftp 69
names of
object-group service udp test
port-object eq isakmp
inside_access_in ip access list allow a whole
access-list inside_access_in allow a tcp
access-list inside_access_in allow icmp a whole
Allow Access-list inside_access_in esp a whole
inside_access_in tcp allowed access list all eq www everything
inside_outbound_nat0_acl list of permitted access interface ip inside 10.10.10.96 255.255.255.240
inside_outbound_nat0_acl ip access list allow any 10.10.10.192 255.255.255.224
pager lines 24
timestamp of the record
recording of debug trap
host of logging inside the 10.10.10.13
Outside 1500 MTU
Within 1500 MTU
IP outdoor 75.146.94.109 255.255.255.248
IP address inside 10.10.10.250 255.255.255.0
alarm action IP verification of information
alarm action attack IP audit
location of PDM 10.10.10.1 255.255.255.255 inside
location of PDM 10.10.10.13 255.255.255.255 inside
location of PDM 10.10.10.253 255.255.255.255 inside
location of PDM 75.146.94.105 255.255.255.255 inside
location of PDM 75.146.94.106 255.255.255.255 inside
location of PDM 10.10.10.96 255.255.255.240 outside
location of PDM 10.10.10.192 255.255.255.224 outside
PDM logging 100 information
history of PDM activate
ARP timeout 14400
NAT (inside) 0-list of access inside_outbound_nat0_acl
NAT (inside) 0 0.0.0.0 0.0.0.0 0 0
inside_access_in access to the interface inside group
Route outside 0.0.0.0 0.0.0.0 75.146.94.110 1
Timeout xlate 0:05:00
Timeout conn 01:00 half-closed 0:10:00 udp 0: CPP 02:00 0:10:00 01:00 h225
H323 timeout 0:05:00 mgcp 0: sip from 05:00 0:30:00 sip_media 0:02:00
Sip timeout - disconnect 0:02:00 prompt Protocol sip-0: 03:00
Timeout, uauth 0:05:00 absolute
GANYMEDE + Protocol Ganymede + AAA-server
AAA-server GANYMEDE + 3 max-failed-attempts
AAA-server GANYMEDE + deadtime 10
RADIUS Protocol RADIUS AAA server
AAA-server RADIUS 3 max-failed-attempts
AAA-RADIUS deadtime 10 Server
AAA-RADIUS (inside) host 10.10.10.1 server timeout 10
AAA-server local LOCAL Protocol
Enable http server
http 10.10.10.0 255.255.255.0 inside
No snmp server location
No snmp Server contact
SNMP-Server Community public
No trap to activate snmp Server
enable floodguard
Permitted connection ipsec sysopt
Crypto ipsec transform-set ESP-DES-MD5 esp - esp-md5-hmac
ISAKMP allows outside
ISAKMP peer ip 206.196.18.227 No.-xauth No.-config-mode
ISAKMP nat-traversal 20
ISAKMP policy 20 authentication rsa - sig
encryption of ISAKMP policy 20
ISAKMP policy 20 md5 hash
20 1 ISAKMP policy group
ISAKMP duration strategy of life 20 86400
part of pre authentication ISAKMP policy 40
encryption of ISAKMP policy 40
ISAKMP policy 40 md5 hash
40 2 ISAKMP policy group
ISAKMP duration strategy of life 40 86400
ISAKMP policy 60 authentication rsa - sig
encryption of ISAKMP policy 60
ISAKMP policy 60 md5 hash
60 2 ISAKMP policy group
ISAKMP strategy life 60 86400
Telnet 10.10.10.0 255.255.255.0 inside
Telnet timeout 5
SSH timeout 5
Console timeout 0
dhcpd address 10.10.10.2 - 10.10.10.5 inside
dhcpd dns 68.87.72.130
dhcpd lease 3600
dhcpd ping_timeout 750
dhcpd allow inside
btork encrypted Ww3clvi.ynWeGweE privilege 15 password username
vpnclient Server 10.10.10.1
vpnclient-mode client mode
vpnclient GroupA vpngroup password *.
vpnclient username btork password *.
Terminal width 80
Cryptochecksum:5ef06e69c17b6128e1778e988d1b9f5d
: end
[OK]any HEP would be appreciated.
Brian
Brian
NAT is your problem, IE.
NAT (inside) 0-list of access inside_outbound_nat0_acl
NAT (inside) 0 0.0.0.0 0.0.0.0 0 0presumanly first NAT is fot your good VPN that acl looks a little funny, what exactly are you doing with that?
The second NAT is the real problem but for outgoing internet access - the NAT statement, you said not NAT one of your addresses 10.10.10.x which is a problem as 10.x.x.x address is not routable on the Internet.
You must change this setting IE. -
(1) remove the second NAT statement IE. "no nat (inside) 0 0.0.0.0 0.0.0.0.
(2) add a new statement of NAT - ' nat (inside) 1 0.0.0.0 0.0.0.0.
(3) add a corresponding statement global - global (outside) 1 interface.
This will be PAT all your 10.10.10.x to external IP addresses.
Apologies, but these are some CLI commands that I don't use PDM.
Jon
-
PIX from site to site VPN at the Juniper
Hello world
have a problem with the vpn site to site configuration beetween cisco pix and juniper firewall.
When I entered the command "show isakmp crypto its" Cisco Pix console displays the following status:
State
OAK_CONF_ADDR
But I don't know what it means that State
or what is the problem?.
l think my setup is corret.
I also have VPN clients configured on the network, and they run correctly.
can someone help me! Plase...
Thanks a lot. = D
If phase 1 is completed successfully, you will see QM_IDLE in "isakmp crypto to show his". Therefore, this suggests a problem of phase 1 - orders «isakmp...» ».
Check the policy, check the pre-shared key.
"CONF_ADDR" gives to think that one end looking for mode config (address IP etc) with the other.
See line «isakmp key...» « a »... No.-xauth No.-config-mode"at the end.
-
Cannot generate interesting traffic
Why doesn't the following config generate no matter what interesting traffic when I ping 192.168.100.161 10.40.10.117?
I have a crypto debugging on and it doesn't seem to be any attempt to bring up the tunnel. I checked that it is hitting the correct access list and it is NATing correctly, but there is no attempt to bring up the tunnel. I would like an overview of this issue.
Thank you.
-pk
(I cut the pieces that I felt were significant to the problem.)
---------------------------------------
name Phil 192.168.100.161
the AddressesAllowed object-group network
Description here are the addresses that are allowed through the Firewall VPN.
network-object 10.40.10.118 255.255.255.255
network-object 10.40.110.71 255.255.255.255
network-object 10.48.10.37 255.255.255.255
network-object 10.48.10.38 255.255.255.255
network-object 192.168.41.31 255.255.255.255
network-object 192.168.41.32 255.255.255.255
network-object 10.46.0.15 255.255.255.255
network-object 10.46.0.19 255.255.255.255
network-object 10.40.10.117 255.255.255.255
network-object 10.46.0.1 255.255.255.255
polnat161 list of allowed access host ip Phil object-group AddressesAllowed
NAT (inside) 0-list of access inside_outbound_nat0_acl
NAT (inside) 1 0.0.0.0 0.0.0.0 0 0
public static 10.44.3.161 (inside, outside) access-list polnat161 0 0
Permitted connection ipsec sysopt
Crypto ipsec transform-set esp-SHA-ESP-3DES-3des esp-sha-hmac
outside_map 40 ipsec-isakmp crypto map
card crypto outside_map 40 correspondence address polnat161
peer set card crypto outside_map 40 21.54.52.112
outside_map crypto 40 card value transform-set ESP-3DES-SHA
life safety association set card crypto outside_map 40 seconds 21600 4608000 kilobytes
outside_map interface card crypto outside
ISAKMP allows outside
ISAKMP key * address 21.54.52.112 netmask 255.255.255.255 No.-xauth No. config-mode
ISAKMP identity address
part of pre authentication ISAKMP policy 40
ISAKMP policy 40 3des encryption
ISAKMP policy 40 sha hash
40 2 ISAKMP policy group
ISAKMP living 40 3600 duration strategy
Hi Philippe
Was your previous and current config is OK except one thing. You translate Philip to 10.44.3.161 when the internal IP address tries to reach one of the networks listed in AddressesAllowed it's very good.
But you say your crypto to establish a tunnel when Philip tries to climb AddressesAllowed. But Philip is translated! So it isn't the IP address that comes from traffic. It's 10.44.3.161. If you need to make the following change
int_traffic_40 permit IP host 10.44.3.161 list object-group AddressesAllowed
No crypto outside_map 40 correspondence card for polnat161
card crypto outside_map 40 correspondence address int_traffic_40
Concerning
Maybe you are looking for
-
I have a serial number of the IPad F6QQT07KFK15. I had a bad load anything on my IPad so I restarted and now it says IPad could not be activated because the activation server is not reachable. Try to connect to I tunes to activate, but how can I conn
-
Tecra S2 - resolution for external monitor on NVIDIA GeForce Go 6600
Hello! I'm new here... I have a Tecra S2 with Windows XP SP2 and a NVIDIA GeForce Go 6600 graphics card. Internal (laptop screen) resolution is 1024 x 768. His job very well. But I work with an external VGA monitor with function "DualView". It is a S
-
import music from cd to itunes
I have a 2014 Macbook Pro, which does not have a CD slot. I have a CD with the music on it I want to put it in iTunes and then on my iPhone. Is this possible? I had it on my iTunes using my Macbook Pro 2009 account which has the slot, but this com
-
"Appoint.exe Failed to load dll lanucher.
I use a Dell inspiron 1420 with Visa Windows Home Basic Edition. I started getting the "Appoint.exe Failed to load dll lanucher" message at startup. I can then no longer uses the roller up and down function on my touchpad. Please help me with this.
-
HP psc 2115 all in one color not printing on Mac
Hello I have a MacBook Pro, OSX 10.9.4. It prints very well on my HP psc 2115 all-in-one in black and white, but not color. I tried to find an update for the driver here, but nothing helps. Is it just that the printer is not compatible with my operat