rv220 allow traffic on a port magnified
Hello
This should be a simple. I am in my rv220, and the title of port forwarding, I created a rule. I also created a personalized service for the particular port I want to allow traffic. The problem is I want traffic to go to any computer on the local network. What ip address I put as a destination. I tried to put on a show, but it did not. 192.168.1.255. what I just put in the IP of the router LAN and it will do the rest?
Please notify.
Tony
Hi Tony,.
Packets transmitted by the WAN port are unicast. Broadcast packets are filtered and not allowed to the local network by default. No option in RV220 to rewrite a unicast packet to disseminate.
There is only IGMP multicast support on this router, but I guess you do not speak on this subject.
Normally with only firewall rule, you can allow traffic for a specific service to enter, WAN, LAN, but more NAT will be a problem.
You can share the service you're trying to broadcast in the local network?
Kind regards
Bismuth
Tags: Cisco Support
Similar Questions
-
A PIX-to-PIX VPN can allow traffic in only one direction?
Here is the configuration of the PIX 501 that accepts incoming VPN tunnels of the other PIX dynamic-ip. Everything works very well, allowing traffic to flow both ways after that the tunnel rises. But then I somehow limit or prevent the traffic that originates on the PIX (192.168.27.2) to go to other networks of PIX? In other words, if a tunnel exists (192.168.3.0 to 192.168.27.0), I only want to allow network traffic to access the network 27.0 3.0, and I want to anyone on the network 27.0 access network 3.0.
Thanks for any comments.
pixfirewall # sh conf
: Saved
: Written by enable_15 at 13:29:50.396 UTC Saturday, July 3, 2010
6.3 (4) version PIX
interface ethernet0 car
interface ethernet1 100full
ethernet0 nameif outside security0
nameif ethernet1 inside the security100
activate the encrypted password
encrypted passwd
pixfirewall hostname
.com domain name
fixup protocol dns-maximum length 4096
fixup protocol ftp 21
fixup protocol h323 h225 1720
fixup protocol h323 ras 1718-1719
fixup protocol http 80
fixup protocol they 389
fixup protocol rsh 514
fixup protocol rtsp 554
fixup protocol sip 5060
fixup protocol sip udp 5060
fixup protocol 2000 skinny
fixup protocol smtp 25
fixup protocol sqlnet 1521
fixup protocol tftp 69
names of
access-list 101 permit ip 192.168.27.0 255.255.255.0 10.10.10.0 255.255.255.0
access-list 102 permit ip 192.168.27.0 255.255.255.0 10.10.0.0 255.255.0.0
access-list 102 permit ip 192.168.27.0 255.255.255.0 192.168.3.0 255.255.255.0
access-list 102 permit ip 192.168.27.0 255.255.255.0 192.168.7.0 255.255.255.0
pager lines 24
ICMP deny everything outside
Outside 1500 MTU
Within 1500 MTU
IP address outside xxx.xxx.xxx.248 255.255.255.255
IP address inside 192.168.27.2 255.255.255.0
alarm action IP verification of information
alarm action attack IP audit
IP local pool ippool 10.10.10.1 - 10.10.10.254
PDM logging 100 information
history of PDM activate
ARP timeout 14400
NAT (inside) - 0 102 access list
Route outside 0.0.0.0 0.0.0.0 xxx.xxx.xxx.1 1
Timeout xlate 0:05:00
Timeout conn 01:00 half-closed 0:10:00 udp 0: CPP 02:00 0:10:00 01:00 h225
H323 timeout 0:05:00 mgcp 0: sip from 05:00 0:30:00 sip_media 0:02:00
Timeout, uauth 0:05:00 absolute
GANYMEDE + Protocol Ganymede + AAA-server
AAA-server GANYMEDE + 3 max-failed-attempts
AAA-server GANYMEDE + deadtime 10
RADIUS Protocol RADIUS AAA server
AAA-server RADIUS 3 max-failed-attempts
AAA-RADIUS deadtime 10 Server
AAA-server local LOCAL Protocol
No snmp server location
No snmp Server contact
SNMP-Server Community public
No trap to activate snmp Server
enable floodguard
Permitted connection ipsec sysopt
Crypto ipsec transform-set esp - esp-md5-hmac gvnset
Crypto-map dynamic dynmap 10 transform-set gvnset
gvnmap 10 card crypto ipsec-isakmp dynamic dynmap
gvnmap interface card crypto outside
ISAKMP allows outside
ISAKMP key * address 0.0.0.0 netmask 0.0.0.0
ISAKMP identity address
ISAKMP keepalive 60
ISAKMP nat-traversal 20
part of pre authentication ISAKMP policy 9
encryption of ISAKMP policy 9
ISAKMP policy 9 md5 hash
9 2 ISAKMP policy group
ISAKMP policy 9 life 86400
vpngroup address ippool pool gvnclient
vpngroup dns 192.168.27.1 Server gvnclient
vpngroup gvnclient wins server - 192.168.27.1
vpngroup gvnclient by default-domain '.com'
vpngroup split tunnel 101 gvnclient
vpngroup idle 1800 gvnclient-time
vpngroup password gvnclient *.
Telnet 0.0.0.0 0.0.0.0 inside
Telnet timeout 30
SSH 0.0.0.0 0.0.0.0 outdoors
SSH timeout 30
management-access inside
Console timeout 0
Terminal width 80
Cryptochecksum:
pixfirewall #.Of course, without a doubt capable.
You can configure the inside interface access list to deny traffic from 192.168.27.0/24 to 192.168.3.0/24, and then allow anything else.
Example:
access list for the Interior-acl deny ip 192.168.27.0 255.255.255.0 192.168.3.0 255.255.255.0
the Interior-acl ip access list allow a whole
group-access Interior-acl in the interface inside
Hope that helps.
-
This allows traffic between two interfaces ethernet on a PIX
I have a PIX with interface inside, IP 10.198.16.1. It also has an interface called WTS, IP 10.12.60.1. I'm having difficulty to allow traffic from the 10.198.16.0 network to cross the PIX in 10.12.60.0. I'm trying specifically to allow access to a server with an IP address of 10.12.60.2.
I enclose my config. Any help would be greatly appreciated!
OK, so the inside interface has a security level of 100, WTS has a security level of 75, so traffic from inside to WTS is considered outbound traffic, which is allowed by default. All you need is a pair of nat/global (or static) between both interfaces so that the PIX knows how NAT traffic between two interfaces (remember, the PIX do NAT).
You have this in your config file:
NAT (inside) 1 10.0.0.0 255.0.0.0 0 0
who says all traffic inside, interface with the IP 10.x.x.x address will be NAT would have, but you must then a global for the interface WTS define what those IPS will be NAT would.
Adding:
Global (WTS) 1 interface
will be PAT all inside resolves the IP address of the interface WTS and allow traffic to flow between the interfaces. If you prefer the hosts inside the interface to appear as their own IP address on the WTS network, then you can use a static command and NAT addresses themselves, actually doing NAT, but not actually change addresses:
static (inside, WTS) 10.198.16.1 10.198.16.1 netmask 255.255.240.0
Hope that helps.
-
Catch 22 - Port Network Configurations: how to combine identifiers VLAN native with DHCP (but allow the virtual computer)
I came across a Catch 22. Maybe someone can restore the directly here. I found a "witch hunt" for sure.
It comes with the Ports of junction on the side of the switch of the ESX host network.
Context:
Ok. The Setup is a HP Blade C7000 enclosure. I try to configure ports for switching to the blades. ESX 3.5 U4 will be installed the BL460cs. Installation is preferred method: revive unattended. No problem with the syntax of Kick-Start,
I am here, it's the side network.
The problem:
I find a major complication in that the switch ports must be configured for both traffic Service Console and VMkernel, more Virtual Machine since only two NICs by blade. Not best practices, but we have only two switches Cisco 3020 inside. The two uplink physical NIC is paired in the same vSwitch. (No iSCSI does fortunately).
So the Catch 22 question is as follows:
If the id VLAN native set up on the switch port, DHCP works of course and the VMware boot loader is able to grasp a binary / packets on the network (FTP Site) and install OK. But after no installation, no communication with SC unless I set the VLAN id of the SC to '0 '. The value "4" 0 does not communication, but "40" is the VLAN native.
If id configuring VLAN native retired from the Switch port, DHCP will not work and host does not have IP address during the VMware boot process. This is as expected as traffic without label is not assigned an eligible
VLAN, so no comms.
The Port of the Switch configuration:
interface GigabitEthernet0/16
SERVERNAME description
switchport trunk encapsulation dot1q
switchport trunk vlan native 40
switchport trunk allowed vlan 40-254
switchport mode trunk
switchport nonegotiate
Speed 1000
No cdp enable
spanning tree portfast trunk
end
Summary
OK, let's summarize where things are and if possible please attach responses to their digital identity.
(1) is there a way to delete the VLAN tagging altogether side ESX host? Not only the id '0 '. The problem is with clearly with the VLAN native defined as "40". If "40" IDs specified on the Group of ports for the Service Console, no joy, no comms. If the id of '0' value, capable of ping gateway and communicate on the network.
(2) what is the problem with the definition of VLAN native as "40" when the config for the switch port is set as VLAN native "40"? Or if it was a problem? Both parameters clearly do not work together.
(3) a switch receiving a unmarked frame it will assign to the VLAN Trunk native. Ok. Trunking bases and why I need a VLAN specified on the port for DHCP native work. But it seems that since the id VLAN is set manually even as VLAN native, closed communications and no traffic as possible.
(4) executives made tag 802. 1 q VLAN native? I think that it is not and this could well be the problem. Since the id VLAN "40" is not labeled, but try to score the side host vSwitch port group.
Please let me know your thoughts, community and how in general, we are approaching 2 NIC ESX configurations.
When trunking multiple VLANs, you either have a default VLAN is nothing is tagged, or you don't. That's what the vlan native to you, it defines which VLAN would be used if no tag is visible on the packets traversing the network. For servers, if you are marking, then everything has to tag, if you're not marking at the server level, then the port must be either an access port or a VLAN native or default must be set. I also don't keep your service console the same network as your vm. Keep this isolated for the security of the network. If you isolate this VLAN, you can separate and use a single IP address for installation and one for post construction.
Or, you can provide an IP address during the build.
-KjB
VMware vExpert
-
Allow traffic from port 80 to 1 single ip address
I block port 80 for all PCs, but it looks like I'll have to open up to a single address for our hosted service proxy filtered correctly display the block page. (They have improved their systems and I don't understand why it must be open, sort of defeated the purpose in my opinion). Does anyone know how to do this on a WRT54G?
You can't do it with the firmware and the Linksys WRT54G.
You can Flash 3rd party firmware like dd - wrt or tomato on your WRT54G (if compatible) and use it. If it is not possible via the web interface of dd-wrt/tomato, you still have the option to connect in Linux on the WRT, and set up a manual filter using iptables.
If you want a device that officially supports this, I think you have to look at the Cisco Small Business devices or better. I think that the consumer of Linksys routers do not support this feature.
-
How to restrict multicast traffic to specific ports on GS716Tv3?
I can not find specific instructions to limit traffic of multicast on the smart switch GS715Tv3.
I need to force all multicast traffic to travel on a specific set of interfaces, or at least stay within a given virtual LAN on the switch to which it is native. All the changes you want multicast servers and listeners will be on these interfaces in their separate vLAN.
We have several GS715Tv3 switches configured identically, but multicast traffic does not pass between the switches.
Topology:
Eight GS716Tv3 smart switches, each configured with three VLANS identical.
No traffic should pass between these VLANS on the switch or pass between the switches
In other words, even if all the 8 switches each have a vLAN named "IOSubsystem", I do not considered the same vLAN.
.
vLAN 4 is corresponding to the hosts of Linux to address major
vLAN 5 is for the audio subsystem
vLAN 6 is for the IO subsystem
VLAN each switch 4 has two active ports, a session to the external interface of the main Linux host and the other to a central switch of 9th GS716Tv3 where a system of software development is also linked.
VLAN each 5 switch connects to the components of the audio subsystems (not shown).
VLAN each switch 6 has two active ports, a going inward a lead Linux host interface and one for the IO subsystem.
-> [vLAN4 | g10]---> [Switch #9]-+.
-> [vLAN4 | g9]-> [Linux host #1: eth0] |
[Switch #1]-> [vLAN6: g1]-> [Linux host #1 | eth1] |
-> [vLAN6: g2]-> [e/s 1 subsystem] |
|
-> [vLAN4 | g10]---> [Switch #9]- +---> [software Dev host]
-> [vLAN4 | g9]-> [Linux host #2: eth0] |
[Switch #2]-> [vLAN6: g1]-> [Linux host #2 | eth1] |
-> [vLAN6: g2]-> [subsystem/o 2] |
... ~
|
-> [vLAN4 | g10]---> [Switch #9]-+.
-> [vLAN4 | g9]-> [Linux host #8: eth0]
[Switch #8]-> [vLAN6: g1]-> [Linux host #8 | eth1]
-> [vLAN6: g2]-> [i/o subsystem #8]We get multicast traffic unwanted between each of these systems, causing corruption of our stream. We limit the multicast traffic on vLAN6 of each switch to stay on the vLAN6 of this specific switch.
Thanks for any help.
To switch the management VLAN to 4.
Make sure you have 2-way switch, one in VLAN4 in a VLAN1.
4 and apply the value of the system you use to a static IP address to the switch and confirm the access to the web configuration and then change "management VLAN ID. then pass the system that you use on the port or any VLAN 4, then you should have access, otherwise, wait about 60-90sec and try again, because you might have PLEASE and it will block anything on the port for just under its set to "Enabled" 'Fast Link '.
Then under "IP Configuration" value switches other IP address in IP range of VLAN4.
For the love of Simplisicty, unmarked ports should never be in 1 VLAN simultaneously.
And instead of using the point and click, goto "Port PVID Configuration" and just create the VLAN it.
Member of the PVID and VLAN the same thing for a port, on what VLAN, it must be in the database
And to confirm, you have a cable from switch to each VLAN? You can cut down on cables and ports if you tag/trunk ports to the next switch. then all VLAN 3 just 1 cable between each pair of switches, saving you at least 4 ports on each switch.
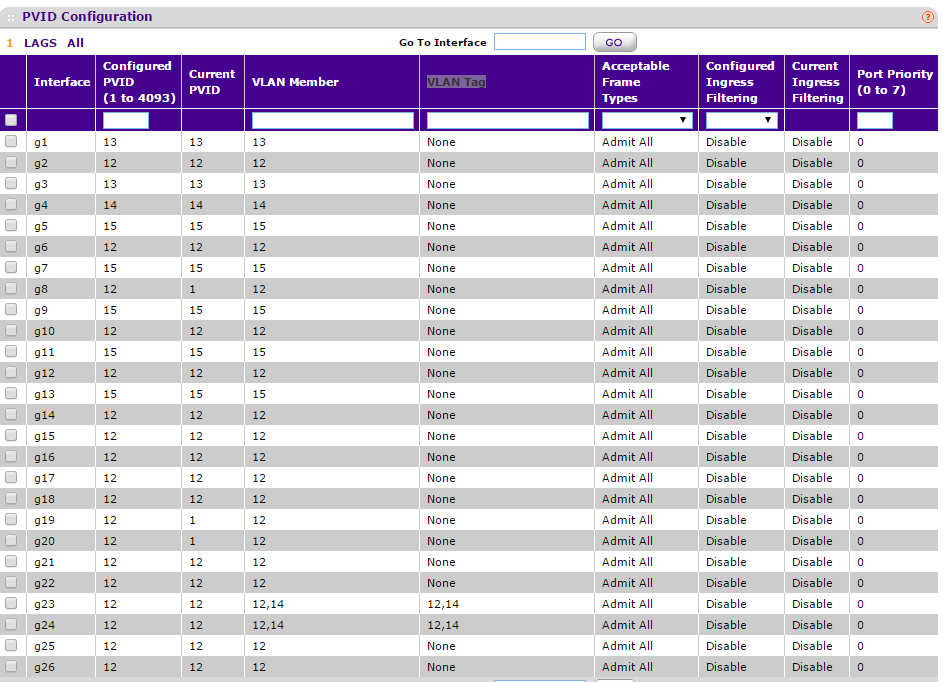
Just an example of my GS724T (ignore ports g8 and g-19-20, their current PVID is because of something else you do not, LACP and Span/Monitoring):
All ports are configured to a single VLAN, my 'LAN hand' is VLAN12, that the management VLAN is set for, g23-24 ports VLAN trunks, they are set on tagg VLAN12 and 14 when the traffic is out of these ports, then switch to the other side reads the consequence tagg and acts, that way I don't need 2 cables/port for each of them.
-
Various involved Ports:
Local: 257 remotely: 513
Local: 513 remotely: 6146
I also saw port 259 and a few others...
The firewall settings work for various other users, but seem to don't like is not something in my configuration.As a member of a domain running Windows XP Pro SP3
When it blocks the traffic, they are always directed to a remote IP address of a domain within my local network controller. I uninstalled a lot of applications, and made sure I have no services for unix/linux installed. For a bit, I thought he may have something for security certificates because my computer and user accounts are configured with our local CA... I doubt, however, that is related...I also know that my domain name is not the configuration as tight as we would like to see because we had to reduce some of the security settings for old Windows 98 and AS / 400 systems. So I remember an old key "reg" which might not help:
Location: HKLM\System\CurrentControlSet\Services\lanmanworkstation
\Parameters
Key: enablesecuritysignature
Initial value: 0
New value: 1
This changed seemed to help but then after another it reboot started appearing again...Amaranth Hello,
Thank you for visiting the website of Microsoft Windows Vista Community. The question you have posted is related to the area and would be better suited to the TechNet Forums community. Please visit the link below to find a community that will provide the support you want.
http://social.technet.Microsoft.com/forums/en-us/categories/
Keith
Microsoft Answers Support Engineer
Visit our Microsoft answers feedback Forum and let us know what you think -
Allowing a blocked by port-security device
Lets say that I have set up on ports on a switch port as this security:
Secure the security Port MaxSecureAddr CurrentAddr SecurityViolation Action
(County) (County) (County)
---------------------------------------------------------------------------
Et0/2 1 1 0 stop
---------------------------------------------------------------------------And also that I have to use sticky to allow all connected devices.
Now let's say that an admin unplug the computer that is plugged into the port and taken in another. Port of the switch as planned closures. Now the admin name and asked that the currently connected computer to be granted access. What is the proper way to allow access to that computer?
I ran it again on this specific interface and did one not closed, but it's still stop. I have to completely disable and re-enable the security of ports on this interface to allow the new device?
Hello
In the command line, write:
Switch(conf-IF) #shutdown
and
interface Dynamics-security of the ports of the switch #clear XX/XX
and
dynamic interface of the switch #clear XX/XX mac address table
and
Switch(conf-IF) #no shutdown
In the 2 interfaces - interfaces of old and new.
Thank you.
-
Tunnel VPN L2L with NATTing will not allow traffic which will be initiated by spoke to the hub.
Traffic from internal hosts will NAT address works ok, but what speaks tests it traffic never connects.
get the 10.1.12.232 NAT host would be 172.27.63.133 and past through the VPN tunnel to 10.24.4.65 without problem. However when 10.24.4.65 tries to ping or connect to 172.27.63.133 traffic does not make inside host 10.1.12.232
ASA-1 #.
!
network object obj - 172.27.73.0
172.27.73.0 subnet 255.255.255.0
network object obj - 172.27.63.0
172.27.63.0 subnet 255.255.255.0
network object obj - 10.1.0.0
10.1.0.0 subnet 255.255.0.0
network object obj - 10.24.4.64
subnet 10.24.4.64 255.255.255.224
network object obj - 172.27.73.0 - 172.27.73.255
range 172.27.73.0 172.27.73.255
the object of the 10.0.0.0 network
subnet 10.0.0.0 255.0.0.0
network object obj - 24.173.237.212
Home 24.173.237.212
network object obj - 10.1.12.232
Home 10.1.12.232
network object obj - 172.27.63.133
Home 172.27.63.133
the DM_INLINE_NETWORK_9 object-group network
object-network 10.0.0.0 255.255.255.0
object-network 10.0.11.0 255.255.255.0
object-network 10.0.100.0 255.255.255.0
object-network 10.0.101.0 255.255.255.0
object-network 10.0.102.0 255.255.255.0
object-network 10.0.103.0 255.255.255.0
the DM_INLINE_NETWORK_16 object-group network
object-network 10.1.11.0 255.255.255.0
object-network 10.1.12.0 255.255.255.0
object-network 10.1.13.0 255.255.255.0
object-network 10.1.3.0 255.255.255.0
!
outside_1_cryptomap list extended access permitted ip object-group DM_INLINE_NETWORK_16-group of objects DM_INLINE_NETWORK_9
access extensive list ip 172.27.73.0 outside_8_cryptomap allow 255.255.255.0 10.24.4.64 255.255.255.224
access extensive list ip 172.27.63.0 outside_8_cryptomap allow 255.255.255.0 10.24.4.64 255.255.255.224
!
list of allowed outside access extended ip 10.24.4.64 255.255.255.224 172.27.63.0 255.255.255.0
list of allowed outside access extended ip 10.24.4.64 255.255.255.224 10.1.0.0 255.255.0.0
list of allowed outside access extended ip 172.27.63.0 255.255.255.0 10.1.0.0 255.255.0.0
!
NAT (inside, all) source static obj - 172.27.73.0 obj - 172.27.73.0 destination static obj - 10.24.4.64 obj - 10.24.4.64 no-proxy-arp-search to itinerary
NAT (inside, all) source static obj - 172.27.63.0 obj - 172.27.63.0 destination static obj - 10.24.4.64 obj - 10.24.4.64 no-proxy-arp-search to itinerary
NAT (inside, outside) source dynamic obj - 10.66.0.0 obj - 172.27.73.0 - 172.27.73.255 destination static obj - 10.24.4.64 obj - 10.24.4.64
NAT (inside, outside) source dynamic obj - 10.70.0.0 obj - 172.27.73.0 - 172.27.73.255 destination static obj - 10.24.4.64 obj - 10.24.4.64
NAT (inside, outside) source dynamic obj - 10.96.228.0 obj - 172.27.73.0 - 172.27.73.255 destination static obj - 10.24.4.64 obj - 10.24.4.64
NAT (inside, outside) source dynamic obj - 10.96.229.0 obj - 172.27.73.0 - 172.27.73.255 destination static obj - 10.24.4.64 obj - 10.24.4.64
NAT (inside, outside) source dynamic obj - 192.168.5.0 obj - 172.27.73.0 - 172.27.73.255 destination static obj - 10.24.4.64 obj - 10.24.4.64
NAT (inside, outside) source dynamic obj - 10.75.0.0 obj - 172.27.73.0 - 172.27.73.255 destination static obj - 10.24.4.64 obj - 10.24.4.64
NAT (inside, outside) source dynamic obj - 10.11.0.0 obj - 172.27.73.0 - 172.27.73.255 destination static obj - 10.24.4.64 obj - 10.24.4.64
NAT (inside, outside) source static obj - 10.1.3.37 obj - 10.71.0.37 destination static obj - 50.84.209.140 obj - 50.84.209.140
NAT (inside, outside) source static obj - 10.1.3.38 obj - 10.71.0.38 destination static obj - 50.84.209.140 obj - 50.84.209.140
NAT (inside, outside) source static obj - 10.1.12.232 obj - 172.27.63.133 destination static obj - 10.24.4.64 obj - 10.24.4.64
NAT (inside, outside) source dynamic obj - 10.1.0.0 obj - 172.27.73.0 - 172.27.73.255 destination static obj - 10.24.4.64 obj - 10.24.4.64
!
NAT (exterior, Interior) source static obj - 10.24.4.64 obj - 10.24.4.64 destination static obj - 172.27.63.133 obj - 10.1.12.232
NAT (outside, outside) source static obj - 10.24.4.64 obj - 10.24.4.64 destination static obj - 172.27.63.133 obj - 10.1.12.232the object of the 10.0.0.0 network
NAT (inside, outside) dynamic obj - 24.173.237.212
!
NAT (VendorDMZ, outside) the after-service automatic source dynamic obj - 192.168.13.0 obj - 24.173.237.212
outside access-group in external interface
Route outside 0.0.0.0 0.0.0.0 24.173.237.209 1
Route inside 10.1.0.0 255.255.0.0 10.1.10.1 1
Route inside 10.2.1.0 255.255.255.248 10.1.10.1 1
!
Crypto ipsec transform-set ikev1 SHA-ESP-3DES esp-3des esp-sha-hmac
Crypto ipsec transform-set ikev1 ESP-AES-256-SHA esp-aes-256 esp-sha-hmac
Crypto ipsec transform-set ikev1 ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
Crypto ipsec transform-set ikev1 ESP-3DES-SHA-DH2-esp-3des esp-sha-hmac
Crypto ipsec pmtu aging infinite - the security association
!
card crypto GEMed 8 corresponds to the address outside_8_cryptomap
card crypto GEMed 8 set peer 64.245.57.4
card crypto GEMed 8 set ikev1 transform-set ESP-AES-256-SHA ESP-AES-256-MD5
GEMed outside crypto map interface
!
: end
ASA-1 #.Hello
First of all, I would like to remove these two lines because they do nothing productive
nat (outside,inside) source static obj-10.24.4.64 obj-10.24.4.64 destination static obj-172.27.63.133 obj-10.1.12.232nat (outside,outside) source static obj-10.24.4.64 obj-10.24.4.64 destination static obj-172.27.63.133 obj-10.1.12.232
Then, I was running packet - trace to see what NAT rule actually hit you.packet-tracer input inside 10.1.12.232 12345 10.24.4.65 12345
-
More than 100MB of traffic on a port FIN_WAIT_2 - process long gone
I have 100's of megabytes of traffic while a loooooooong (10-20 minutes), after that the process has spent on the port that once belonged to this process and is now in FIN_WAIT_2. I know that some will say 'impossible', but here is the proof: I used to be a network guy, doing same programming (Linux) kernel of the TCP (firewall) code so I know at least a little bit what I talk even if it was some time ago. In my view, I must say that, as all previous because these reports and discussions that I could find where met with disbelief.
I run Wireshark, so I can SEE the traffic, and it's all about the port that "netstat - year ' lists as"FIN_WAIT_2.
Reminder: This is twitch.tv and flow of video on demand (not live). I use the latest Flash and Firefox. Even when I do some (list of processes) that Firefox and the Flash plugin went network traffic continues to max my connection 16Mbit.
Connections (which are TCP-> HTTP) are data centers "Level 3 Communications' (a company), which is where the shaking hosts them (I checked that, and besides, as I said, I can see the traffic with Wireshark).
How can I stop this unnecessary traffic? How is it possible anyway? Yes, I know it is not lack of Windows, but I have no access to the servers of video at the request of jerk or the code of their flash video player. I * could * add manually a firewall block for the port, but I'm not even sure which would prevent the server continue to send packets, only that I can't - and this "denial of service attack" on my connection Internet would always be there.
I found this, and there is a sentence that gives me pause:
http://msdn.Microsoft.com/en-us/library/Windows/hardware/ff550023%28V=vs.85%29.aspx
"If an acceptable TCP segment arrives on the connection, before the expiration of the timer FIN_WAIT_2, unloading target restarts the FIN_WAIT_2 timer."
Given that these packages coming form the server (lots of them!) it seems that perhaps happens, which does not expire the FIN_WAIT_2 timer?
EDIT:
Maybe is not specific twitch.tv, as I watched my system more closely I noticed that it may be a general problem with playback of the video stream through Flash (on Firefox?).
EDIT 2:
This problem may be more widespread, here's a similar report for videos on Chrome (they don't say no HTML5 or Flash videos?): https://productforums.google.com/forum/#! Chrome/EupZB8aHVPM/section
EDIT 3:
More of the same show (if you read the details): http://forum.bitdefender.com/lofiversion/index.php/t46323-100.html
Hello
The question you posted would be better suited to Windows 7 IT pro community.
http://social.technet.Microsoft.com/forums/en-us/w7itpronetworking/threads -
Cryptographic cards are allowed on the Ethernet ports
I want to set up encryption between E0 on RouterA and E0 on RouterB. Is this possible?
RouterA and RouterB are related through the ports series (T1) or dial-up connections (ISDN, POTS) and are never on the same ethernet connection.
Intermediate links between RouterA and RouterB change regularly and frequently in my portable environment.
When I apply a cryptographic card to an ethernet port, it seems to crash the router, part of the traffic goes thru, but I lose telnet.
I use 2520 s and 4500's
Any ideas?
Thank you
Mark Matthias CCNA, CNA, CNE, MCP
The card encryption should be applied to the port outgoing (port facing the other peer router). You apply the encryption card to T1 and ISDN/POTS interfaces and define your ACL crypto to encrypt traffic between subnets ethernet.
-
Allowing traffic SMTP on some IP address ranges
I have to configure my 506th PIX to allow only traffic to certain IP's SMTP goes to my mail server. However, I don't know about the right way to accomplish this task. If I put in the lists of access for each beach and anything else associated with SMTP that accomplish the task?
Any help would be great!
Thank you
Michael: Laro
One thing that can help is to use "group objects. With group objects, you combine services networks and protocols (ftp, smtp, etc...). If you have a handful of IP addresses or subnets that you want to allow access to your SMTP e-mail server, you could do this is similar to the following. Remember, by default, NO traffic can come from the internet, through your external interface and in your private network. So, if you say that give permissions to following addresses, then only they and no one else. Here is an example of group objects.
SMTP server address: 172.17.1.1
Addresses you want to allow SMTP: 32.18.7.0/24, 204.215.18.0/24 and 113.113.45.1 and 118.55.34.20.
pixfirewall (config) # network object-group MAIL
pixfirewall(config-Network) network-object # 32.18.7.0 255.255.255.0
pixfirewall(config-Network) network-object # 204.215.18.0 255.255.255.0
pixfirewall(config-Network) # host network-object 113.113.45.1
pixfirewall(config-Network) # host network-object 118.55.34.20
Now create your access list:
pixfirewall (config) #-access list ENTRY-IN permit tcp object-group MAIL host 172.17.1.1 eq smtp
pixfirewall (config) #-access group ENTRY-IN in interface outside
This will allow the network and the ip addresses that you defined in the netgroup called 'MAIL' access to your mail server. I hope this helps.
-
VPN traffic through incoming port
On my ASA 5510 I want for the VPN clients can connect on the outer harbour and have their internet traffic directed back on that same port, with the internal traffic inside port. Is this possible? If so, how does do this?
Will be transmitted traffic VPN based on the routing table after out of the tunnel.
If you do not want to let Internet traffic to turn on the external interface, you must add
-permit same-security-traffic intra-interface
-make the Association NAT change such as
Global interface 4 (external)
NAT (outside) 4
-
Update my SPI allow traffic 5520 interruption?
I need to update my IPS licenses and did not know if that would cause an interruption of traffic or require a restart of the IPS? Thank you, Tony
Yes, you can apply or update a license on a sensor running without interupting traffic. Signature updates and Service Packs DO interrupt traffic if your FPS is online.
-
allow traffic through remote client
Hi friends,
I'll explain my setup.
I have an asa in datacenter with the static ip address, then site Office also having static ip, these two sites are connected via VPN and I configured the remote client to the data center.
workers of remote client needs to access the network of site office. It's my setup.
the problem I faced is that remote workers they cannot access the site office network.but if I try to ping the ip vpn site office pool and then if I try
the remote client, I can able to access the siteoffice of the remote client.
Please provide me with the solutions experts
I understand that you have the following topology:
(1) Lan-to-Lan VPN between data center and site office
(2) VPN Client that connects to the data center and here also join the site Office.
There are a few things that need to be configured for the VPN Client to access the site office:
On the ASA Data Center:
-command "permit same-security-traffic intra-interface"
-Tunnel of Split ACL must include the site LAN Office
-Crypto ACL for LAN-to-LAN VPN must include the following:
permit ip access list
On the ASA site Office:
-Crypto ACL for LAN-to-LAN VPN must include the following:
permit ip access list
-NAT exemption must include:
permit ip access list
Hope that helps.
Maybe you are looking for
-
Satellite L650-1N8 - ODD open habit
Hello again ^^ Open used the DVD player. Any idea?Thought that the eject mechanism are without work... Thank you regardingJan
-
I added on a new printer and lost my audio. What should I do?
I added on a new printer and lost my audio. What should I do?
-
Could not find the SRS audio device error
Since I installed Windows7 on my laptop, I got the error "Unable to find compatible SRS audio device" on start up. I checked the "Device Manager" and all audio devices seem to work normally. I have re-installed Windows7 and I still have the same prob
-
do C20 to call outside 8.6 CUCM
Hi Experts, I have in my project C20 telepresence and 8.6 CUCM, I want to be able to call remotely, and I want to know what I have to do to 8.6 CUCM and voice gateway if needed. Some people told me I should do NAT, but I don't want to do NAT. I want
-
Is there a way to query users for specific api access on app download?
For example, we need access to net_rim_bbapi_phone in a part of our application. Currently, the application prompts the user for access... unless the user has enough foresight to check "Set application permissions" before downloading and then comes