Validation of the design of the DMZ
Here is a summary of my current client environment30 total of physical machines. I have a data center with 3 different VLANa DMZ public face to face a company intranet and DMZ. Security is important in this environment, and we should not go through certification and accreditation audits. I'm afraid that the security officer will push a physical separation for each network, as by running different ESX clusters for each. It will be very costly and inefficient, especially since both DMZ networks have 3-4 VMs each. I wouldn't run 4 VMs on a pair of DL380 G6s simply because they are in a different trust zone!
I propose to create a vSwitch distributed with 4 NIC team, with each vlan segmented using tagging vlan and combining the three sites on the same physical host. We can also consider having the VLAN MGMT and VMotion on these same 4 natachasery. I already read this document and he described in detail how this could be done.
http://www.VMware.com/files/PDF/dmz_virtualization_vmware_infra_wp.PDF
I think we're going to need to use a product like vShield zones, or a 3rd party firewall virtual (such as Altor) to transmit our audits and satisfy the security people. We can get the physical network interface cards on the hosts so that will provide the best separation. I guess in a perspective of network traffic, it might be a good practice at least put the console service and VMotion on separate natachasery.
Where should we go with VLAN here, or advise you to use natachasery on the separate virtual switches for the separation? Finally, my question boils down to this - is my solid design and are there any additional recommendations to the execution of the three zones of different trust in a single cluster?
Thanks in advance!
Hello
IS always implies that you use VLAN within your physical network to DMZ and other areas of trust... So continue to use VLANs within the virtual world. You can't really treat the vNetwork 'less' safe as the pNetwork because it is actually NOT. It's safer, "back of the box" from a perspective of layer 2 as the vNetwork is not sensitive to the many attacks of layer 2 while pNetwork 'out of the box' is sensitive.
If you use VLAN in the physical world and 'trust' as your pSwitches stay or are configured correctly.
So use VLAN in the vNetwork as well. VST works fine in this case.
However, if your DMZ is PHYSICALLY separated from your other pNetworks then maintaining this separation to help IS the DMZ pSwitch. I wouldn't take the DMZ pSwitch plugged into the pSwitch directly upstream of the ESX host and then use IS/VST. This is not correct.
In both cases when you combine demilitarized and DMZ not trust areas on the same cluster, you need to increase your vigilance to ensure that things do not move to where they do not belong.
Even within the same group, I tend to keep my DMZ VMs on their own host or hosts to ensure their care does not impact on the rest of the environment or at least start like that and let DRS figure the rest. I also LUN separate VMs DMZ outweigh the problems of disk IO.
However, if you need to be compliant, your auditors MAY require a physical separation at the moment as a PCI PCI has yet to turn off any other type of orientation. This decision is left to the listener actually. That probably means that you WILL Have to physically separate. Talk to your accounts, they are there to help.
Best regards
Edward L. Haletky VMware communities user moderator, VMware vExpert 2009
Now available: url = http://www.astroarch.com/wiki/index.php/VMware_Virtual_Infrastructure_Security'VMware vSphere (TM) and Virtual Infrastructure Security' [/ URL]
Also available url = http://www.astroarch.com/wiki/index.php/VMWare_ESX_Server_in_the_Enterprise"VMWare ESX Server in the enterprise" [url]
Blogs: url = http://www.virtualizationpractice.comvirtualization practice [/ URL] | URL = http://www.astroarch.com/blog Blue Gears [url] | URL = http://itknowledgeexchange.techtarget.com/virtualization-pro/ TechTarget [url] | URL = http://www.networkworld.com/community/haletky Global network [url]
Podcast: url = http://www.astroarch.com/wiki/index.php/Virtualization_Security_Round_Table_Podcastvirtualization security Table round Podcast [url] | Twitter: url = http://www.twitter.com/TexiwillTexiwll [/ URL]
Tags: VMware
Similar Questions
-
WIN 64: The application is valid but was designed for a different system (32-bit).
I have an application written in Toolbook 4.0 (WIN 95 to 1996). It works fine in XP 32-bit. When I try to run in XP 64, I get the error message "the application is valid but was designed for a different system" is at - it an emulator or a way to make a 64-bit computer to run 32-bit code? I know that this application is old but it works fine in XP 32 and I can't replace it witout totally re - develop from scratch.
There are several options depending on your operating system.
For XP/Vista: You can use Microsoft Virtual PC 2007 and run Windows XP x 32 inside your x 64 system.
http://www.Microsoft.com/downloads/details.aspx?FamilyId=04d26402-3199-48A3-afa2-2dc0b40a73b6&displaylang=en
For Windows 7 (Pro and Ultimate only): you can use Windows Virtual PC, which comes with a copy of Windows XP on the inside to run legacy applications.
http://www.Microsoft.com/Windows/Virtual-PC/default.aspx
-
Validity of the trial ADOBE Design & Web Premium CS6
I am a user of ADOBE Design & Web Premium CS6. until yesterday, the validity of the software is 3200 days, but this morning when I tried to open it, it says that the test limit has expired. is it wise for me to uninstall it and reinstall and use the same serial number?
I contacted the support for help and they checked my serial number... but it seems that it is still valid and there is no problem. might be a technical problem? can someone tell me what to do?
No, you can use the serial number again on the same computer while reinstalling the program.
Kind regards
Mohit
-
What is a good way to determine the validity of the GPS with BPS?
Hello
I use bps for a native application on the Playbook. There are a lot of functions to call to get information about the events of geolocation, which is great. But I'm looking to distill information into something that could tell me if yes or no position (lon, lat at least) is designed to use in my application... it is to tell whether or not I am a "GPS coordinates". You can check the validity of all to a large number of parameters (altitude, heading, speed, etc.) ... but nothing that tells you if lon and lat are valid.
Does anyone have advice as to how I can a true/false 'gpsIsValid' extracts the available data?
REF;
If you get a reading at all, it should be "valid" in the sense that it came from calculated data based on the satellites used.
What you need to do is to decide 'how' it is valid, that's up to you: https://developer.blackberry.com/native/reference/playbook/com.qnx.doc.bps.lib_ref/com.qnx.doc.bps.l...
-
I run a server from Vsphere to only serve clients located in the demilitarized zone using the local drive.
I need to connect to our Vcenter server in our local business network.
What network configuration preferred for this for maximum security of the host and our local business network?
I was thinking about a pair of network adapters on a virtual switch just for the guests in the DMZ and for the rest of the virtual switch on our local corporate network.
Our networking group thinks have the host in the demilitarized zone and control access through the firewall would be better.
Or maybe a hybrid approach using a second firewall.
Any help on this would be appreciated. I read the Vmware in the doc of the DMZ, but I'd like to hear from someone with experience...
Thank you
Hello
Moved to the security forum.
I run a server from Vsphere to only serve clients located in the demilitarized zone using the local drive.
First of all, you must realize that there are at least 2 areas of trust of network at work here. The network of the VM for DMZ VMs and Device Management/Service Console for virtualization management.
I need to connect to our Vcenter server in our local business network.
Well the vCenter Server really should be a firewall from the rest of your corporate LAN within a network of virtualization management.
What network configuration preferred for this for maximum security of the host and our local business network?
2 natachasery for SC/Management Appliance, 2 natachasery for VM networks.
I would also use NO Local storage as Local storage can be damaged if the host has problems. That means bye-bye VMs. local storage is not a very good idea to a worry of availability or a concern for performance. ISCSI or FC are protocols very quickly compared to the local storage.
I was thinking about a pair of network adapters on a virtual switch just for the guests in the DMZ and for the rest of the virtual switch on our local corporate network.
2 for virtual machines. 2 for management NOT on the local network of the company directly.
Our networking group thinks have the host in the demilitarized zone and control access through the firewall would be better.
Or maybe a hybrid approach using a second firewall.
They don't understand virtualization if they offer it.
The real question is: how the DMZ is currently implemented? Is that the DMZ is currently implemented by using the switch physical separation or VLAN. If its VLAN, then where are they currently placing their TRUST? With themselves the most likely. If they use VLANs within the physical network you can use VLANs within the virtual network. If they don't think that this is the case, then they really need to know a little more about the coverage to the VLAN in the vNetwork regarding the attacks of layer 2 compared to the pNetwork (which is all about confidence and not authority). If they use the physical separation, then you continue to use the physical separation.
The first step is to migrate your vCenter and appliances of consoles/service management ESX/ESXi to a network firewall virtualization management separately. You also place a bunch of Machines to jump within this network so that Admins use RDP to access machines jump where they perform the vSphere Client and other virtualization management tools which should never be executed from within your network of business directly.
Once it is your management network is protected which solves the 3/4S of the current batch of attacks. Then you come to add the new cluster host in the network and let the virtual machines to live directly in the demilitarized zone.
Personally, I use the physical separation of the separate pSwitches and vSwitches jut for loads of the DMZ, but I do not have a host ESX JUST for the demilitarized zone. I have and it works too.
Any help on this would be appreciated. I read the Vmware in the doc of the DMZ, but I'd like to hear from someone with experience...
I would be very interested to see their reasoning behind their suggestions and how the current DMZ is designed and works. This is the real question. Once you know this, you can make the appropriate vNetwork suggestions.
Best regards
Edward L. Haletky VMware communities user moderator, VMware vExpert 2009, 2010Now available: url = http://www.astroarch.com/wiki/index.php/VMware_Virtual_Infrastructure_Security'VMware vSphere (TM) and Virtual Infrastructure Security' [/ URL]
Also available url = http://www.astroarch.com/wiki/index.php/VMWare_ESX_Server_in_the_Enterprise"VMWare ESX Server in the enterprise" [url]
Blogs: url = http://www.virtualizationpractice.comvirtualization practice [/ URL] | URL = http://www.astroarch.com/blog Blue Gears [url] | URL = http://itknowledgeexchange.techtarget.com/virtualization-pro/ TechTarget [url] | URL = http://www.networkworld.com/community/haletky Global network [url]
Podcast: url = http://www.astroarch.com/wiki/index.php/Virtualization_Security_Round_Table_Podcastvirtualization security Table round Podcast [url] | Twitter: url = http://www.twitter.com/TexiwillTexiwll [/ URL]
-
"The document is not valid. The index.xml file is missing.
I suddenly can't open one of my docs of numbers. I get a msg "'name of the doc' document is not valid. The index.xml file is missing. I literally had the open document this morning without problem, closed, tried to reopen and now I get this msg... all in the same session of the computer. It began not after an update or anything like that, right in the middle of a session of the computer. You seem to affect all the docs of numbers. I can't open an any of them now. I am running OS X El Capitan Version 10.11 and numbers 09, Version 2.1.
Hi jg,.
The case usual this message, it is that the document has been opened in numbers version 3.xx, which converts it into a new file version that uses the file index.xml internal requested by Numbers ' 09.
You have 3 numbers installed on your machine? This file has already been opened in this application?
The file was saved to iCloud or opened by the iOS version numbers or numbers for iCloud?
Recommended 'cure' is to open the file using the 3 numbers, then save as... or export to format Numbers ' 09. As a result, remember numbers to quit smoking (v3) - menu numbers > numbers to quit smoking; by clicking on the red light closed the file, but doesn't end numbers. So avoid open numbers files by double-clicking on the file itself.
Instead, start Numbers ' 09 (v2.3) and open the file in the application.
Kind regards
Barry
-
On a single Web site my usercode and password entries are considered not valid. The same words and password work fine in IE and Google.
I found that my Norton Toolbar had been disabled so I enabled it. When I tried the site it worked. Go figure.
-
I currently have www.google.com set as my homepage, but Firefox says that the url is not valid for the default home page.
The problem is now solved with the current version of Firefox 10.0. Thanks for the help ccbrunt and SafeBrowser.
-
I even got this message when I tried to post my question! It is said that Firefox can not verify a connection with mozilla, or any website, I am visiting, because the security certificate is not valid. It gives even the dates to which the certificate will be valid, and the date indicates that it is valid. So frustrating! I "replace" Firefox every time.
The date / time set correctly in Windows Vista?
-
Tecra M10 - 120 - my European warranty is not valid in the United States
Hello
I have a Toshiba - Tecra M10 - 12o laptop.
This unit that I bought in Abu Dhabi, United Arab Emirates UNITED with 2 years international warranty extension.
The warranty is still on, and now I am settled in the USA.Now, I'm having a problem with the LCD and want to have it repaired. I went to two suppliers of services authorized for Toshiba in New York, but after reviewing my system, they said that they are not allowed to fix it because it's a European model laptop.
For the same problem, I had the LCD screen, replaced in Abu Dhabi, United Arab Emirates UNITED Toshiba distributor/service provider. But good as now I am in New York, USA and not able to get the correction of a problem here.
Please kindly advice how to get this problem fixed so that in the United States for a laptop of model Europen.
Thanks in advance.
Kind regards
PrasadHello
As far as I know and after the guarantee page ÉMAÉ Toshiba, Toshiba computers laptops, Netbooks and Smartbooks are covered by at least 1 year EMEA standard warranty, valid from the date of purchase.
This warranty is applicable only in the EMEA region (Europe, Middle East and Africa)You can find more details here on this Toshiba European page:
http://EU.computers.Toshiba-Europe.com/innovation/services/standard-warranty/Here you can find the PDF EMEA warranty info.
http://goo.GL/wN1mSSo if you're outside the region of EMAE and if you don t have bought additional warranty extensions, you will have to pay for the service :(
-
Configuration of the DMZ for MS access
I set up a DMZ for a Web server. I'll probably put an RODC in there later, but for now I want to open ports to the domain controller.
I'm a bit new to DMZ and I'm a bit confused.
I put in place services for different ports and then configure the rules of lan/dmz coming out of the demilitarized zone to the domain controller, but I get no connection.
I have the DMZ a 10.0.0.1 / 255.255.240.0
The value 10.0.0.5 Web server / 255.255.255.240.0
Gateway is 10.0.0.1DNS server on the primary domain controller 192.168.10.1
I opened the ports following services:
Kerberos 88 (TCP, UDP)
Time 123 (UDP)
135 Kerberos authentication (TCP)
LDAP 389
LDAP 445
MS DS 3268 (TCP)
1025-4999 RPC Ports (TCP)In the rules of the DMZ Lan, for those leaving, should I simply specify the machine side of DMZ DMZ users or do I need to specify the side Lan Lan users too?
Then I need to duplicate these ports in the Incoming, correct?
Any help in pointing to the relevant documentation would be great.
No, you should not need to configure static routes, unless you have something weird going. You can check the network path by adding rules incoming/outgoing ICMP LAN DMZ (ICMP-TYPE-8, to be precise) and ping back and forth between the DC and the Web server (ensuring any intermediate software firewall is disabled). If you can test in both directions, then you know with certainty that none of the static routes are needed.
-
Hello
I'm trying to control communication of the parallel port. But never a success.
I ran the sample VI: parallelportconnection.vi I got an error on Probe1. The error information are given below.
1073807246 error occurred at the VISA write to ParallelPortCommunication.vi
Possible reasons:
VISA: (Hex 0xBFFF0072) the resource is valid, but the VISA cannot currently access.
Please give me help.
Hello
To answer your question, please see the following articles:
Error 37 when using screw series compatibility or error-1073807246 VISAS screws
-
Hi all!
Yesterday, I worked all day in a VI and today, unfortunately, I'm frustrated when I tried to open it. Received the following error message:
LABVIEW: Unable to load dynamic library due to lack of external symbols or dependencies, or a format file not valid. The "ENG633 v1.vi" file could not be loaded.
This message repeats when I try else open a Subvi.
Step by step:
1. I created a copy of the LabVIEW VI example: "FuzzyEx Tanks with control of PI." I kept the copy in the same original directory.
2 - I have edited the copy, created Subvi etc.
3 - once I finished my course of programming I closed all the cut (ctrl-x) files and copied (ctrl v) into the other folder.
4. then I tried to open the next day and... bug! I just couldn't do

What can I do to open/recover the VI?
I am using 32-bit LabVIEW 2016 in a Windows 10
I tried opening them and got the same error you did, so I them opened with a hex editor to see if there was something in the file, and there is literally nothing other than the value of 0x00 for the entire file.
-
Installation of the SCOM Agent on servers in the DMZ
Dear,
can you please help me with the exact steps to install SCOM Agent to the DMZ (no trusted domain) server to monitor anyone and is it possible to test it before in any Windows 7 PC. ?
Thanks in advance
This issue is beyond the scope of this site (for consumers) and to be sure, you get the best (and fastest) reply, we have to ask either on Technet (for IT Pro) or MSDN (for developers)
If you give us a link to the new thread we can point to some resources it -
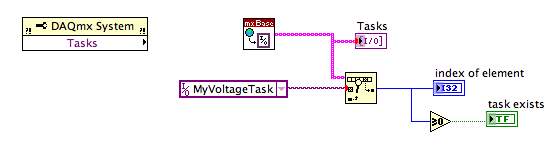
Verification of task names valid in the basis of NOR-DAQ
Hello
I have a question about the configuration of the tasks in the version of Base of NOR-DAQmx (I need basic because the application will need to be able to run on both Windows and Mac computers). The material is a box USB-6009, ordered through LabView. When you create a task inside LabView, is it possible to tell if the name you choose is already in use or not? Similarly, is it possible to get a list of and if all tasks are running?
The context is that I have a subroutine that made a brief burst of acquistion of analog input and then passes the result to the caller. I would like also to the subroutine to run standalone for different testing purposes. Normally, I would have the subroutine create and configure a task, the measure and then close the task. The problem is that the process of create/set up/start takes about 200-250 milliseconds (the measure itself is about 20 ms) that is long enough that I don't want to go through it whenever the subroutine is called from the top (I need to call this routine and do some other stuff a few times per second). So what I would is have the name of the task as a control on the subroutine, test that the value is a valid and if not valid only the initialization/etc. in the context of the subroutine, but if the subroutine has been passed a valid task from the top to skip a step all the time.
Looking through all of Base of NOR-DAQ functions, it doesn't seem to be something that allows me to do this kind of check with the exception of brute force to try to create a task and trapping so all errors that might be generated.
Suggestions (or ways) welcome.
Kelsey,
It seems that the property node is a component DAQmx, not a component DAQmx Base . I can't find any DAQmx Base property nodes.
dmsilev,
Try to replace the property node of the tasks with the DAQmx Base get tasks.vi. It is not in the DAQmx Base palette. It's a Subvi DAQmx Base create Task.vi. Caution: when you use a Subvi, which isn't on the pallets, know that they are generally not documented well and are subject to change in future versions of LV
If you weren't aware, DAQmx Base is written in LV and almost all the diagrams are not p [rotege so you can look inside and see how things are doing.
Lynn
Maybe you are looking for
-
I use Windows 7 with a Firefox browser. new flash player update Adobe... now, it blocks my computer!
I use Windows 7 and firefox browser. I was invited to update flash player to the new verion 17. (blah blah). 169. I downloaded the update. installed without a problem but come to find out now, everytime I try to go youtube my videos play but they are
-
my email has been hacked last night... I changed my password but now I can't send emails! says I have a limited quantity, I can send. What should I do?
-
I tried to connect my XP and VISTA via TeamViewer VPN friend. The Vista, it is possible to access the XP shared partitions but the XP, it is only possible to see letters of shared partitions, not records, however, it is possible to have full access t
-
Message: HP OfficeJet pro 8500 A910 is low on toner/ink
I get this message on my 8500, although all the cartridges are at an adequate level. I didn't know that the 8500 had a separate toner cartridge. T it? Where is he? Is there a name/number for her so I can ask for the right thing at the store? Thank yo
-
Windows 7 backup error "the system cannot find the file specified. (0 x 80070002) »
* Note that I never could solve this problem. In the long run, I ended up reinstalling the operating system (for different reasons), but the issue remained pending. Thanks to those who have tried to help. (January 30, 2011) Suddenly, I seem to have a