AnyConnect local auth
I configured webvpn/AnyConnect on an ASA. This firewall has also IPSec for remote access configured (and work). When I try and connect to the webvpn, I get the following error.
Unauthorized user to access AnyConnect Client, please contact your administrator
I think I have good sound because users of IPSec use RADIUS to authenticate and webvpn is also. I want webvpn to use only the local database at the moment. Someone knows how to put webvpn for local auth?
WEBVPN as uses a group of tunnel for this validation of the user, if it is not expressly defined it will use namely 'DefaultWEBVPNGroup' by default in this section, you must enter DefaultWEBVPNGroup General-attributes tunnel-group mode and enable the LOCAL server as shown below:
attributes global-tunnel-group DefaultWEBVPNGroup
LOCAL authentication-server-group
NOTE: If this webvpn already uses the RADIUS to validate users, you must create another group of tunnel where you set LOCAL authentication and ensure that this group of WEBVPN Tunnel is chosen by the user. This can be done with the group alias or group url on the ASA.
Tags: Cisco Security
Similar Questions
-
Cisco ASA 8.4 Active Failover / standby with anyconnect local CA
Hi Friend´s
I hope you do well! I ve got a question, hope you can help me. I ve got an ASA 5550 with version 8.4 (6), it s focusing anyconnect VPN remote access who authenticate through certificate locally generated in ASA. We´ve got an another 5550 with the same hardware and same version, and we focus on the configuration of the failover. I ve heard of network other than it s engineers may not failover configuration when the ASA doing this local. Then I ve read full failover for version 8.4 operating guide (6) and I didn t find any restrictions on the local failover and CA working together. I m tests over the next weekend, but I would like to know from your experience, if I'm having problems on VPN connections or failover configuration.
Please, do not hesitate to ask as much as necessary information. All comment and documentation will be appreciated.
Best regards!
It's the n: documentatio
Does not support Active/Active or Active/Standby failover
And on top of that, ASDM shows that "Local CA cannot be configured when failover is activated".
-
Configuration of AAA to include local auth for Console connections
Recently, during a maintenance window, that my AAA configurations are not configured to use local authentication if the AAA server is unavailable. Could use a little help in making sure I have the correct configuration. Here is what I set up today:
AAA new-model
AAA authentication login default group Ganymede +.
the AAA authentication enable default group Ganymede +.
AAA authorization auth-proxy by default group Ganymede +.
orders accounting AAA 15 by default start-stop Ganymede group.RADIUS-server host x.x.x.x
RADIUS-server timeout 120
RADIUS-server application made
radius-server keyGood... If you want you will need configure a fallback option when you sign in aaa and enable authentication lines. Throw a 'local' keyword on the end of those, and that you will get what you are looking for.
I'm a little worried that the "console aaa authentication" is not appear in your configuration. It makes me think that he will not survive until the next refill.
Are you running the latest revision of your version of IOS?
-
authentication local auth-proxy
Hello
Auth-proxy authentication works with the usernames of local aaa on a Cisco router or RADIUS / Ganymede + mandatory server for this task?
I m trying to limit the access of web on a branch office router without using a proxy server that is centralized on the main office.
Thanks for your help.
Hello
You will need a RADIUS/ACS server for this feature. See:
"Cisco IOS Firewall authentication proxy feature allows network administrators to apply specific security policies on a per-user basis. Previously, user identity and related authorized access were associated with an IP address of the user, or a single security policy should be applied to a group of users together or subnet. Now, users can be identified and authorized on the basis of their policy of each user. Adaptation of the access privileges on an individual basis is possible, as opposed to the application of a general policy between several users.
With the authentication proxy feature, users can connect to the network or access the Internet via HTTP, and their specific access profiles are automatically retrieved, of a CiscoSecure ACS, or other RADIUS or GANYMEDE authentication server +. User profiles are active only when there is active traffic from authenticated users. »
HTH,
Bobby
* Please note the useful messages.
-
AAA Ganymede + with backup local auth
Hello
I try to get my switches/routers/etc to aaa allows you to restrict access to the configuration of the devices on my network. I have the aaa authentication to GBA v3.3 now, but for some reason any my local user no longer works. I would like to have the possibility of a connection to access local, just in case my ACS becomes unavailable.
My config on a 2950 is...
version 12.1
Service nagle
no service button
tcp KeepAlive-component snap-in service
a tcp-KeepAlive-quick service
horodateurs service debug uptime
Log service timestamps uptime
encryption password service
!
AAA new-model
connection authentication AAA SMOC-access group Ganymede + local select none
AAA authorization exec SMOC-access group Ganymede + local
AAA SMOC-access authorization network group Ganymede + local
AAA accounting exec SMOC-access arrhythmic group Ganymede +.
AAA accounting network SMOC-access group arrhythmic Ganymede +.
Select the secret xxx
activate the password xxx
!
username admin privilege 15 secret xxx
RADIUS-server host 172.20.2.25 key xxx
RADIUS-server key xxx
radius-server administration
line vty 0 4
exec-timeout 15 0
password xxx
exec SMOC-access permission
exec accounting SMOC-access
Synchronous recording
SMOC-access connection authentication
length 48
line vty 5 15
password xxx
!
The only time wherever the local user will work is when your RADIUS server is not available. You can test by putting in the wrong key of Ganymede and establishing a new seeiosn. Be sure to keep the original session open just in case :-)
HTH and rate please.
-
Cisco Anyconnect with auth double factor
Is it possible to configure an ASA with Anyconnect to require both a user name and a certificate in order to connect?
Yes. Cisco is a configuration example posted here.
-
WLC Flex connect local authentication does not work
Hi guys,.
I'll give you a brief description of our current flexconnect configuration. We have APs configured mode flexconnect in the remote office and in local mode in the local office. Wireless LANs are the same in both locations and we have detected a problem in one specific SSID. It is a voice SSID and configured in 802.1 x mode that authenticates to a RADIUS server in the remote desktop.
We detected only when the WAN line gets collapsed the IP phones unplugged wireless SSID and when the WAN line become free, reconnected.
We have seen that we can configure Flexconnect local auth mode to avoid this problem, but it of esn can't work properly. We have set up APs in remote site with an IP address static and configured as NAS in the RADIUS server, but we did not see any which authenticayion in th RADIUS server package when change us the SSID to «FlexConnect auth» local
Can you give me an idea to help solve this problem?
Thanks in advance.
Joel
I suppose that clients connected by access points Flexconnect have problems where the WAN connection is down (?)
It depends on your current configuration and security policy what are the feasible options in this scenario. If there is an available RADIUS server - who can still authenticate your users while the WAN line is down, you can configure your access points to access this server directly. You must use a FlexConnect for this group and configure the external server on the general tab, in the menu "AAA". You already made the point of access-static IP addresses and add them as clients on the RADIUS server, then it should work.
Another option is that in the event of failure, access points to will authenticate the client based on a local data base and/or certificate. Also, this requires a FlexConnect group and the option 'Enable local authentication AP'. For example: If you are using PEAP and a specific user for VoWLAN account you can download the server and the certificates of CA to the WLC and add the credentials of this account to build the same configuration with the external server. Downside of this is the lack of central logging that may not match your security policy.
Remember that the access point itself can't remember the relationship between the access point and FlexConnect group, in both scenarios, you need to configure all controllers manually with these MAC to the Group mappings. This behavior is different in comparison with the "groups of AP" what access point you remember during the passage of the controllers.
The "FlexConnect local authentication" option on the SSID itself forces always use local authentication that has been configured on the FlexConnect group even if the connection with the WLC is available. I don't think that it is feasible to use it in your scenario.
Please rate helpful messages... :-)
-
local web authentication fails
Hello experts!
I have problems performing clients to authenticate locally on a controller 2106 with ios v.4.1.171.0.
do I need a radius server must be able to get local auth.
also the auth login page does not automatically appear when I open a browser and type www.cisco.com or any other url.
I have to type in vip 1.1.1.1 to be able to set up the connection on the page.
This is how it is supposed to be for this particular code.
Thanks for any input... really appreciate it.
It seems that you have a configuration problem on the wlc. If you can access the web before enabling webauth then you should have no problem getting web page... unless you have a proxy? If you enter 1.1.1.1 and get the webauth page, then it looks that dns does not work or perhaps your home page is a secure https page. Try google.com or something like that.
-
Local VCS-E - Authentication for H323 failure
Hello
We have allowed Local DB authentication in our E - VCS and could not succeed to authenticate endpoints H323 behind the firewall. SIP devices register without problems.
Source on VCS - Local AUTH
VCS said "Request received from source not authenticated".
Under settings are pushed to the endpoint.
For example) EX60 performing TC4. X
H323 profile H323Alias ID: [email protected] / * /
H323 Profile H323Alias E164: 654321
Profile PortAllocation h323: Dynamics
H323 Profile CallSetup Mode: Gatekeeper
H.323 Gatekeeper profile address: XX. YY. ZZ. AA
H.323 profile Gatekeeper discovery: manual
H323 profile authentication LoginName: user name
H323 profile password: password
H323 profile Authentication Mode: on
Here's the application endpoint. anID VCS sends back a rejection stating the refusal of security.
I would like to make a capture of work scenario, where I see the credentials going to VCS in the registration request.
For example) C40 TC4 running. X
and VCS confirms the request.
So, I want to know which prevents the end point to be authenticated.
One last thing to be noticed in the screenshot above is...
For the scenario to work the RAS has the full discovery of the true value. Whereas it is false for the other.
Could it be a problem of capability not shared sets properly.
Best regards / / Rio
Hi Rio,
a couple of things you can try:
S ' ensure that the endpoint has a configured NTP server
-On the verge of ending, try changing the configuration mode of appeal to 'Live' and then save again "Gatekeeper" and save again.
It should be I hope that endpoint are starting to send the RRQ with cryptographic tokens.
You could try restarting endpoint.
-Andreas
-
Cisco ISE 1.1.2.145 Admin authentication via the LDAP protocol
I have configured the LDAP protocol and able to retrieve our LDAP directory structure. Now, I'm trying to point authentication "Admin Access" Source 'External identity', which is the new LDAP IS I created. But I couldn't find an option to authenticate locally if for some reason the LDAP configuration does not work. I learned that the ISE can automatically return to local auth as external sources Idenitity are inaccessible. How can I test the LDAP authentication with breaking them our Admin Access? I thought to open two parallel sessions, one with Super Admin account Local and one with the domain account. But I noticed that ISE communication is smart enough for the closing session/connection no matter what other sessions in different browsers so, basically, I can't open two parallel sessions the same machine to test. Suggestions? or am I missing something here?
Thanks in advance.
Hi Srinivas,
Even if you configure LDAP as a source of external identity of admin access, you can always internal relief without having locked. According to the ISE user guide:
During the operation, Cisco ISE is designed to "fall back" and try to perform the internal identity database authentication, if the communication with the external identity store has not been established, or if it fails. In addition, whenever an administrator for which you have configured external authentication launches a browser and initiates a logon session, the administrator must still the option authentication of demand through the local Cisco ISE database by choosing 'Internal' to the Selector drop-down storage of identity in the Connect dialog box.
http://www.Cisco.com/en/us/docs/security/ISE/1.1/user_guide/ise_man_identities.html#wp1351543
Please see the attached screenshot by my lab ISE:
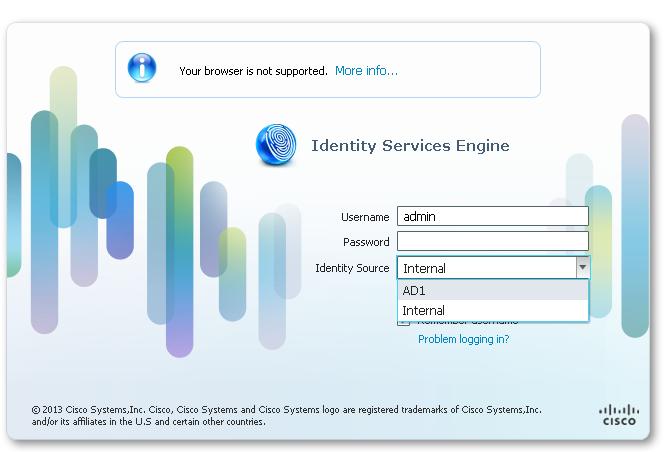
I configured the admin authentication against AD, but I still see both 'Internal' and 'AD' at the time of the connection.
I hope this helps.
Thank you
Aastha
-
[ACS 5.4] Retrieve the MAC address (to be used in the policy)
Hello
I want to authenticate clients WLC and compare their MAC address with LDAP attributes.
We have stored MAC address for each user on our LDAP server.
I have to get MAC address stored by FAC in policy rules to compare with the LDAP value.
The only attribute containing the MAC address I found is 'Calling-Station-ID' in the dictionary "RADIUS-IETF."
I don't know if this attribute will always be the MAC address...
Is it possible to recover a "MAC address" attribute?
Thanks for your help,
Patrick
If you are using 802.1 x or mac filtering, the username of the device is used as the mac address, or calling-station-id, the time that you will see only the mac address is when you make web local auth with external authentication to the ACS. Also for users of vpn, you see this and also in terms of auth-proxy.
For WLC and dot1x mac address is always used for the calling-station-id.
I hope this helps.
Tarik Admani
* Please note the useful messages *. -
AAA/RADIUS of debugging for a special mac only address
I have a question - is there a way I can debug aaa, RADIUS, communication eap on a switch to a particular mac (endpoint) only address?
Thank you.
EAP authentication
In order to troubleshoot the interaction between the WLC and the authentication server (RADIUS external or internal to the EAP server), use the command debug AAA all turn on, which shows the required details. This command must be used after the client to debug
command and can be combined with other commands to debug as needed (for example, transfer). (Cisco Controller) >debug client 00:00:00:00:00:00 (Cisco Controller) >debug aaa all enable (Cisco Controller) >show debug MAC address ................................ 00:00:00:00:00:00 Debug Flags Enabled: aaa detail enabled. aaa events enabled. aaa packet enabled. aaa packet enabled. aaa ldap enabled. aaa local-auth db enabled. aaa local-auth eap framework errors enabled. aaa local-auth eap framework events enabled. aaa local-auth eap framework packets enabled. aaa local-auth eap framework state machine enabled. aaa local-auth eap method errors enabled. aaa local-auth eap method events enabled. aaa local-auth eap method packets enabled. aaa local-auth eap method state machine enabled. aaa local-auth shim enabled. aaa tacacs enabled. dhcp packet enabled. dot11 mobile enabled. dot11 state enabled dot1x events enabled dot1x states enabled. mobility handoff enabled. pem events enabled. pem state enabled.
-
Permission denied on 3560 after than IOS upgrade
Hi all
I just upgraded a CAT3560-48TS IOS 12.2 (37) SE1 (ipservicesk9) at 12.2 (46) SE (ipservicesk9). Everything seems fine until I tried logging with my account GANYMEDE: I get an authorization failure. Connect with a local priv15 account works fine. After removing the following statements:
AAA authorization exec default local auth-server group
0 default auth-server group AAA authorization commands no
orders of 1 AAA authorization auth-server group default no
orders of 15 AAA authorization auth-server group default no
everything works fine again.
Also, I have improved other 3560 switches to 12.2 (46) SE with a picture of ipbase. These switches work fine with exactly the same IOS AAA configuration. Any thoughts on this one?
See you soon,.
Vincent
Run these commands,
no single-radius-server host connection
radius-server host
Kind regards
Prem
Please rate if this can help!
-
Profile C40 with VCS Starter Pack Expressway system
Hello guys,.
Customer not want options like Firewall and the Conference (MCU 5300) crossing.
But as this is a small script (there around 2 profile C40 + 2 SX20 10 video Jabber), I found that it will be interesting using VCS Starter Pack Expressway. He's no more than 50 records or 25 route calls as shown in the data sheet 'support '.
I took a look at the topis here and also some documents and say that C40/SX20 are not supported for the supply, but since the SIP/h.323 support, calls should work perfectly.
No doubt: that the client will lose in terms of features or benefits without the support of this commissioning endpoints?
It would be a pain in the neck to enter the SX20 or C40 to VCS Starterpack expressway?
http://www.Cisco.com/en/us/prod/collateral/ps7060/ps11305/ps11315/ps11337/data_sheet_c78-697075.html
Thank you!
Alan
Olá Alan, respenderei em inglês para fica na don't base dados, mas design sao best respondidas send any video Business forum.
About your 3 points, depends on:
(1) even if you deploy the TMS, endpoint will try to get the directory using HTTP/HTTPS connection. If the endpoints are outside / internet, it may be refused by security reasons.
(2) you can always configure auth on the StarterPack VCS to auth against the local database. At the endpoints configured manually, you can enter the identification information.
(3) you can configure the bandwidth on VC (subareas or pipes) configuration control or limit directly to each endpoint
The SX/MX/EX/C series can register the StarPack using a direct connection (h.323/SIP) or behind the FW/NAT using H.460.18/19 or assent. They can local Auth VCS DB. Be aware that the VCS S is usually installed in an external DMZ or directly with a public IP address. In this case, if you have 2 x SX to the internal network and the VCS at the DMZ (with NAT in the middle), all media will be hollow VCS, even if the two SX are on the same subnet.
PS: Be careful where to include the VCS. If you use NAT on the VCS, basic network license need double.
It will be useful.
Concerning
Elter
-
Currently our ASA is configured to use LDAP for authentication of VPN clients. I have read several books that show how to set the ASA to LDAP, RADIUS and LOCAL authentication. I want to make use of LDAP and LOCAL authentication. So that if a client connects, it would check for local authentication before check LDAP. Has anyone successful cela and could share an example config?
Thank you!
Looks like double authentication is not what you are looking for. Based on the above condition, you will be better of setting up a tunnel for your closed user group that uses local authentication exclusively. You can then present the user with a drop-down menu on the auth portal where they choose their desired tunnel group. You can also configure the group URL to direct users to the correct tunnel group. For example, you might have https://vpn.vpn.com/employee and https://vpn.vpn.com/vendor where it used TG uses LDAP and the TG seller will use local auth.
Maybe you are looking for
-
iPhone more replaced 6 speaker stopped working after update to iOS 9.3.4.
iPhone more replaced 6 speaker stopped working after update to iOS 9.3.4. New speaker of iFixit. After replacement speaker works perfectly. With FaceTime, the call, music, etc. And IPhone running on iOS 9.3.3. But after the update to IOS 9.3.4 speake
-
Hearing sound stops when it is used with the iPhone
Using sound Linx 2 hearing aids. They are matched correctly with the iPhone (worm 9.3.3). When receiving or phone call, right aid will report the outage battery and closed. Resound app shows the phone id psired AIDS both all-around and IPHONE. Good h
-
Point of mystery of material; an HP product. that I can't find a support.
Hello I have a video card that I can't find except in passing mentions, with further references obscure motherboard chipsets. Some web sites seem to contradict what type of map this thing really is, and I have no way to say for sure at this point. Fr
-
PSC 1610 all-in-one printer: PSC 1610 will not print
HP PSC 1610 all-in-one No including photographic paper feed and the following messages are received: paper jam or paper. This is not correct. Jam has recently replaced; all paper rolls have been cleaned up with water. Any advice would be appreciated.
-
Share the invocation and the pound sign
Hello Qml I am sharing a message that contains a pound sign "£", but this charcacter is corrupted: {Of invocationID: sharequery: {InvokeQuery}mimetype: "text/plain".ID: idQueryinvokeActionId: "bb.action.SHARE".}onArmed: {}If (idQuery.data! = "") {}Tr