Is your data with VMware NSX she safe?
Is your data with VMware NSX she safe?
An analogy often used in COMPUTER security is equivalent to a candy that has a hard shell, but a soft Center, data center. This means that, once the network firewall has been violated, an attacker has free rein in an environment traditionally networked. In addition to the speed and flexibility, VMware boasts the security features of NSX to businesses who want to keep virtual machines
Tags: VMware
Similar Questions
-
Laboratory: HOL-INF-06 - deploy and operate your cloud with VMware vCloud Suite
I started this laboratory - are there instructions/steps somewhere about how to accomplish the laboratory?
Thank you
You should see a tab 'MANUAL' of the extreme right to the top.
Click on the tab to expand it. Arrows to click through the manual there. You can also rearrange the manual window where you want to.
See you soon!
Bill
-
Back up my data with installation DVD
I want to transfer my data to an external with installation DVD drive because my Mac OS isn't bootable anymore because of the sierra of mac os. So I'll do a new install of snow leopard on my macbook late 2009. Does anyone know how to transfer my data in my external drive across the disc of the DVD Installer prior to installation of Snow Leopard sanitation? Somone told me to do it this way, but I don't know how.
I recommend strongly against from any attempt of recovery/reinstallation without a valid (and verified) backup on a different disk. As you are still able to boot the system with the installation DVD, you can
- use
Disk Utilityon the installation DVD to create a full backup of your internal drive to an external - copy
/Applicationsand/Usersto an external drive (which should focus on 'all' critical data)
Then comes to an attempt of resettlement.
You can restore your data after the installation of the operating system. First make a note of bookmark, password or registration required by your system.
Perform a full backup with time machine, then restart with your installation dvd, then reinstall the operating system
When Setup restarts, you can restore your data with the migration wizard.
When possible, you should do a clean install with 3rd party applications and drivers HW until the migration may or may not be compatible with the older operating system and removes the possibility of corruption of preference.
- use
-
Backup integration with VMware Data Recovery (VDR) tape - how to guide
Hi all
It's just something I've had a lot of people ask me about this.
Here is an article on using VDR tape backup. It's actually very simple, there is no rocket science here, but it might be useful to the have exposed again.
Backup integration with VMware Data Recovery (VDR) tape
Pete
FWIW, I used your great white paper today, Peter, with a lot of success in testing applications third VDR. Discovered VDR is actually much faster and easier to work, especially for the backup of NAS devices. Thx for the link!
-
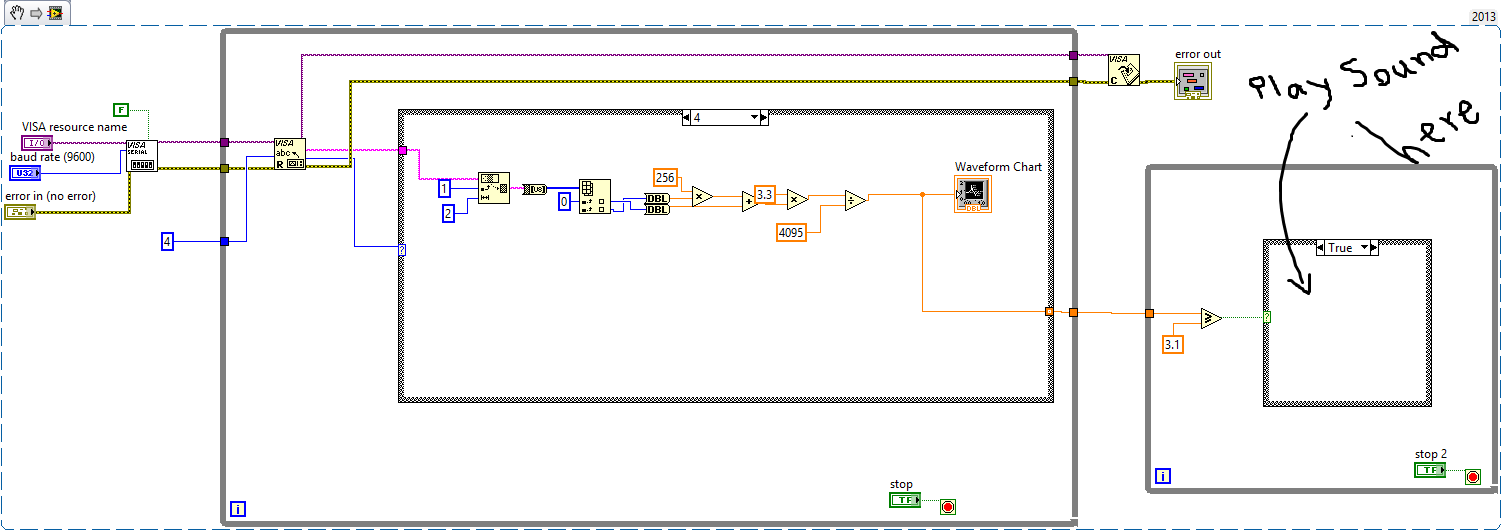
play sounds temporary and file of your choice when reading data with VISA functions?
Hello.
I read the function of reading data with VISA and then I use as multiple functions to display data on the graph. everything is OK.
now, I want to play a sound specified (like a song in my desired folder 3s) signal which cross above the specified value range. then after the desired time, it will wait still new cross above the specified value and this repetition of the procedure until I stop the program.
Data MCU is from and it does not stop when his game system and what system of incoming data for this part (his play) will ignore them pending that outdated.
I use this for reading data and part VI mentioned which belongs to her is empty and I don't know what I have to do?
altougth I use an another while loop for his apartment because I want to save time CPU.
Thank you.
I recommend you do the data type of the notifier a cluster that contains a path and a numeric (double). The path indicates the reader what file to play. Digital is the duration.
Now in a way a bit complicated, but really good stop your second loop. Do not use a second notification. Instead, send the normal notification but not use a path for the path in the cluster. Your second loop can write a check for the path of a not and stops when that is received.
-
How to know if your computer is up-to-date with updates?
Hello
How could I know if my computer is up to date with windows updates?
I would accept a computer on a virtual private network computers that want to connect have their updated windows update.
How could I check that? a key value in the registry? access to a database?Thanks a lot for your help
Hi tofke22,
Thank you for using answers Forum.
You can check if your computer if up-to-date by checking the Windows Update control panel section and see if updates are available.
However, if you want to know if a person who connects to you via the VPN is in common with their updates, the only method that I know would ask them. There is not a way to check the status of update a PC without having access to the office.
I hope this helps.
Chris
Microsoft Answers Support Engineer
Visit our Microsoft answers feedback Forum and let us know what you think. -
Im having a problem with your security software. Your data bass must be bad, now I can't have spent my address question. Ive answered all questions to the best of my knowledge and software has always said that my answers are incorrect
Hello Bernard,.
You sign a document that has authentication based on knowledge, applied in it? If so, and if you can't go to questions, then you will need to contact the sender of the document because they can remove it and return you the document. You can respond directly to the e-mail received esign and happens directly from the sender.
Kind regards
-Usman
-
Anyone run a Terminal servers virtual with VMware ESXi 3.5 If Yes please share your experiences?
Hello guys,.
We are runnig Terminal Server with Windows Server 2003 Ent in a cluster environment (TS 7), we plan to go with VMware ESXi 3.5 to virtualize the TS. Does anyone have any kind of experiences that can help make a decision?
Thank you.
Keep an eye on the side esxtop ESX and see your % RDY meters in this output. Don't forget, as underlined chamon, with high vSMP values do not match always the best performance. Typical scenarios citrix/ts use 1-2 vCPU for more effective results. If you bump up to a larger number of users, you also want to watch the overcommitt on your processors and vCPUs in the box. Many users a lot of switching and use heavy context on the processors for the management of the OS and the user. 1-2 vCPU seems to be the sweet spot. What kind of applications are underway within the environment?
-KjB
VMware vExpert
-
Safe on Etherchanel / 802.3ad, it works with vmware esx?
Trunk etherchanel in cisco switch configuration, it works with vmware esx?
Configuration of the Cisco switch like that (I don't have a switch, can not test it):
src-dst-ip port-channel load-balance
the interface vlan 4094
no ip address
Interface Port - Channel 1
switchport
switchport mode trunk
switchport trunk encapsulation dot1q
switchport trunk allowed all the VLANs
switchport trunk vlan 4094 native
no ip address
interface GigabitEthernet1/1
switchport
switchport mode trunk
switchport trunk encapsulation dot1q
switchport trunk allowed all the VLANs
switchport trunk vlan 4094 native
no ip address
Chanel-Group 1 mode on
interface GigabitEthernet1/2
switchport
switchport mode trunk
switchport trunk encapsulation dot1q
switchport trunk allowed all the VLANs
switchport trunk vlan 4094 native
no ip address
Chanel-Group 1 mode on
endWhat you have should work OK, because it is not too different from the example of work from my lab:
ocs4948-1 #sh int item in gi1/2nd round
Building configuration...
Current configuration: 536 bytes
!
interface GigabitEthernet1/2
switchport trunk encapsulation dot1q
switchport trunk allowed vlan 2.10
switchport mode trunk
MTU 9198
channel-group 64 mode on
spanning tree portfast
spanning tree enable bpduguard
endocs4948-1 #sh run int item in gi1/6
Building configuration...
Current configuration: 536 bytes
!
interface GigabitEthernet1/6
switchport trunk encapsulation dot1q
switchport trunk allowed vlan 2.10
switchport mode trunk
MTU 9198
channel-group 64 mode on
spanning tree portfast
spanning tree enable bpduguard
endocs4948-1 #sh run int in64
Building configuration...
Current configuration: 291 bytes
!
Interface Port-channel64
Description esx402 LACP link
switchport
switchport trunk encapsulation dot1q
switchport trunk allowed vlan 2.10
switchport mode trunk
MTU 9198
load-interval 30
Storm-control broadcasts 5.00
spanning tree portfast
spanning tree enable bpduguard
endocs4948-1 #sh int trunk
VLAN Mode Encapsulation native port State
In64 on 802. 1 q trunking 1Port VLAN allowed on trunk
In64 2.10Port VLAN authorized and active in the field of management
In64 2.10VLAN port extending on transmission State and no tree pruned
In64 2.10The only thing to look at will be the VLANs that you got set up on the vSwitch. You have defined VLAN native example, the VLAN untagged on the switch to be 4094, any traffic sent on the aura tags trunk VLAN, which will be removed by the vSwitch.
In my setup, I have established groups of ports using VLANS and VLAN 2 10. Traffic to the virtual machines on these VLANs are .1Q marked by the physical switch, which is then stripped by the vSwitch.
Take a look at the section "VLAN in VMware Infrastructure" on page 7 the concepts of virtual networking André already mentioned, but also the other interesting reading material is http://www.vmware.com/pdf/esx3_vlan_wp.pdf.
Finally, for the side of the switch of things, look at the examples on Scott Lowe's blog at http://blog.scottlowe.org/2006/12/04/esx-server-nic-teaming-and-vlan-trunking/.
Concerning
-
Even with AV software, how safe are passwords in T-bird, worried?
With the threat of the Zeus botnet and even with the AV software and vigilance for the phishing emails, how can secure passwords in TB you, if even a master password is effective only for a single session?
Surely, TB is not safe in itself against such an attack.
Comments please, Steve.Point 1. If they cannot follow, they have a problem.
Thunderbird 17 November 20, 2012
Thunderbird 24 September 17, 2013
Thunderbird 31 later in 2014I hope they can keep up with new versions of the virus, because Thunderbird is almost up to once a year.
Point 2. Thunderbird stores your e-mails on your hard disk in plain text format.
Point 3. Zeus is dead. http://www.USATODAY.com/story/news/nation/2014/06/02/global-cyber-fraud/9863977/
Point 4. Nothing will protect you against malware. Nothing less than your computing device to disconnect from the internet, all networks and all media. That's put the machine in a glass bubble. Anything that can be done is reduce the risk, not remove it. A few years ago new USB keys have been sold at retail by malware on them. How do you want to know, how would your anti virus program know, if it was the first appearance of such.
Point 5. Your data can be encrypted, there are a lot of account and there entire disk encryption products, but the data useless even to you in this State. So when you connect to your computer data is decrypted, so you can use it. Crypto locker or as happens and encrypts your data. When you disconnect from your operating system with renew your already inaccessible encrypted data encryption.
Point 6. «Please do not use the term good AV software.» Famous, yes but nothing anti virus programs we have are good. They rely on questionable heuristic engines lists value and the search for known viruses. Some of them have not been seen in the wild for 30 years and daily updates. In some cases more frequent to broadcast their new definitions to the infections.
Point 6. Thunderbird is written with security in mind. So, no support for remote images by default, no vbScript, javascript code and not Flash. All the HTML is analyzed and disinfected before reaching even to see. So the risk of read any mail is very very low. I'm sure that there is an unknown exploit here somewhere, but the 6 weekly releases of security and stability Gets the most serious closed in due course.
Point 7. Most anti programs anti-virus analyzes the flow of data, whether HTTP for the web, IMAP or POP for mail, so if your anti virus program does not only and requires some sort of program plugin, maybe you need the other.
Point 8. The biggest risk is the spare part, because they are sent as they were sent. However, to open an attachment, it must first be re-created as a file and saved in your temp folder and then executed in the same way that if you double click on a file on your desktop. If your antivirus can't find out and stop a problem either through the writing of the file, or it is later opening will be useless for this threat in any case. For what is does or does not email is irrelevant.
Point 9. I have the challenge of security on why companies e-mail Scanner even exist, the best I can get from them is "another line of defense." It's true, they are aware because their scanners residents should detect anything that arrives in the mail, the email stuff is just "another line of defense' very annoying which causes most of the problems of electronic mail. Regarding outgoing mail, that was really me. They certify your machine clean and then scan outgoing mail for, I have no idea what. Your machine is clean.
-
I am at a loss. I've set up a root certification authority to sign all servers in my workspace of Horizon, SAML is in the Green and after a lot of reading when troubleshooting also synchronized on all my ESXi hosts and guests.
Basically, what I did is the following:
Set up the connection to the Server VMware View Horizon 5.2 - created different pools and can connect via the customer different platform. (a few times to eliminate any possible configuration errors along the way)
Configuration of VMware View Horizon Workspace 1.0 (a few times now) with self-signed and CA signed certs. My workspace appears fine, the synchronization of files, apps work, and view pools appear. When I try to launch your desktop from inside the Horizon workspace I get this error:
The page you are looking for is not available. You may need to contact your administrator with this error: 404 Page not found.
Now I think that I followed it down to something to do with SAML connection - which, to my understanding, archery chips between workspace and view. On the login server, I see it in the Windows event log:
BROKER_USER_AUTHFAILED_SAML_ACCESS_REQUIRED
SAML access required but not tempted by customer
Attributes:
Source = com. VMware.VDI.Broker.filters.SamlAuthFilter
Time = MON may 20 16:06:41 MDT 2013
Gravity = AUDIT_FAIL
Node = ViewConnection.access360.ca
Module = broker
Recognized = true
Something is not crossing to allow me to access my office view since the workspace of Horizon. If I remove the requirement of SAML on the login server see, when I try to connect to a desktop computer from the view connection server I get a promotion for and can I get my IDs & field and have full access with reviews, as well as blast HTML - just cannot get there with Horizon Workspace. There must be something that I am missing with SAML...
As I said, I'm at a loss here on what does not work between the Horizon workspace and the connection of SAML for display to connect to the server. There is no server security, server transfer, and firewalls is all off, so I don't think it's a network problem. Simple as possible. The Windows Journal event displays the login displays server error is: access required but not attempted by client SAML. I have all my servers synchronized after a few seconds - so I don't think that documented the TIME Horizon workspace synchronization time sensitivity is responsible here. I am Pack overnight, but will do exactly the same thing with a client of tomorrow - hopefully without the same result!
Any ideas?
A
So I re-deployed the VAPP (again!) very attentive as I went. As usual, the initial database installation failed because I entered my domain FULL of the gateway name, so it does not match. After useful messages already there for this (Workspace install fails with error creating the user admin) I used the wizardssl.hzn of connfigurator - going to recreate a rootca to the environment based on my FULL domain instead of the bridge - going and then let it grow all for the other vApps. I then connected to each and pulled down my private rootca and ran c_rehash, etc. (another useful message!- adding MS signed Certs to Horizon Workspace & laquo;) Carlos & #039; Corner) I actually use my background to UNIX and openssl to be my own private CA and sign all of my certificates. I created the SAN cert and added to the SSL configuration on the Configurator - going and connector - going. Oddly enough, both of these server do not appear to be accepting SAN cert that includes their ENTIRE domain, but that's for another day... My Horizon Workspace FQDN does show as being approved by installed RootCA private (which does not have other DNS names for the service - going, the Configurator - goes, the data - will and the connector - will, but as I have already said--a battle for another day) so it's a good thing. I joined my workspace to my domain name - well! Activated would be pools seen in the Configurator - goes - sync - good. CRT for the my display login server has accepted and implemented the SAML trust. Still good. Sync in my opinion users group who already had a couple of linked clone pools allowed to do. Good. Connected to the FQDN of my workspace and clicked on computers - seen my 3 pools. Clicked on one and after a few seconds, launched in a new window of the explosion. Success! I disconnected and connected on a different machine, and something that I saw before, but doesn't have a lot of attention to was the connector - will put 'use windows authentication', I couldn't understand why every time I sailed on my Horizon workspace a no vmware window opens asking access my FQDN:443 with a user and pass. It is this setting - duh. I'm not sure yet that gives me, so it's off for now.
Thanks for all the input: it's good to know that there are others with some of the same questions. It's still v1.0, it is related to some of these pitfalls. It is capricious with derived from same time less than 10 seconds seems to have a negative impact. Had to ensure my ESXi servers were strong (never worried a lot in the past with MS AD being quite tolerant with small derivatives) I tired my vApps affecting a NTP, but they seemed like being left to the default of synchronization to the ESXi host. See how than pans. CERT is somewhat capricious depending on your deployment. Of course the connector - will and the Configurator - must be signed by a CA that they are internal, but always be nice to then have signed internal...
Now, I'm on ThinApps for desktops as well as the web interface integration.
I bumped my head against the wall with my first configuration of Citrix XA and XD (before having VDI in a box!) and it was the best way to learn.
I don't know that I grave along that I finished my PoC, but I'm very happy with today's results. I still plan on the comparison of my logs successful with the logs I have pulled my former deployment TIME and see what it was that it was broken. I think it was that wanted me a PTR record to my domain FULL DNS MS. name I think I just had the direct search for the original bridge - will and FULL, but only a setback for the gateway domain - name. Would explain why I was never able to connect to the gateway to access your desktop. Oops.
A
-
Internet deal with VMware and SAN?
I am designing my first VI3.5 environment in the face of internet and I was wondering if there are problems with sharing a single SAN network between a data center VMware internal and an external datacenter, VMware.
At this stage of design I'm not concerned with the network, just a storage security.
________________________________
Jason D. Langdon
Hello
I am designing my first VI3.5 environment in the face of internet and I was wondering if there are problems with sharing a single SAN network between a data center VMware internal and an external datacenter, VMware.
Use different LUN for internal vs external
Do not use the iSCSI initiators in DMZ VMs
Do not use NPIV in DMZ VMs
Set your virtual computer security settings.
At this stage of design I'm not concerned with the network, just a storage security.
There usually no problem as long as your security policy supports these actions, because everything goes through ESX (with the advice above isolation). Your concern is to make sure that your San is separated from any hostile VM. IE if the CF is to be default. If it's iSCSI then separate your networks/VMs VM iSCSI networks. I would not use VLAN for that, but that's just me.
Best regards, Edward L. Haletky VMware communities user moderator, VMware vExpert 2009
"Now available on Rough Cuts: url = http://www.astroarch.com/wiki/index.php/VMware_Virtual_Infrastructure_Security' VMware vSphere (TM) and Virtual Infrastructure Security: ESX security and virtual environment ' [url]
Also available url = http://www.astroarch.com/wiki/index.php/VMWare_ESX_Server_in_the_Enterprise"VMWare ESX Server in the enterprise" [url]
[url =http://www.astroarch.com/wiki/index.php/Blog_Roll] SearchVMware Pro [url] | URL = http://www.astroarch.com/blog Blue Gears [url] | URL = http://www.astroarch.com/wiki/index.php/Top_Virtualization_Security_Links Top security virtualization [url] links | URL = http://www.astroarch.com/wiki/index.php/Virtualization_Security_Round_Table_Podcast Virtualization Security Table round Podcast [url] -
is not cold p2v windows 2000 for ESX 3.5.4 with vmware converter 4.0.2U3
Hello
I met a problem today, with the cold p2v windows 2000 sp4 server
stop process to 2% saying unknown error occurred
Here is the log of error-content (agent):
NfcNetTcpRead: the time-out waiting for data
NfcFssrvrRecv: failed with code = 9
NfcFssrvr_DiskIo: have not received response from e/s
DISKLIB-LIB: RWv failed ioId: #69 (5666) (34).
DiskLib_Write has no sector 40960 HA - nfc: / / [Local_Storage_
1_elcvmw02] vlzwwc02 / [email protected]:902! 52 98 d dd 00 99 72 6 b4-66 82 23 be cc 20 31 f1 with error invalid NDB error code.
NfcNetTcpWrite: bwritten:-err 1: 10053
NfcFssrvr_Close: failed to send a close message
NfcNetTcpWrite: bwritten:-err 1: 10053
NfcNet_Send: asked to 264, only 8 bytes sent
BlockLevelCloning::task: Image Processing task a ISP
LED with MethodFault::Exception: sysimage.fault.DiskLibConnectionFault
BTW: I tried several ESXs target and I also tried a migration cold with vmware converter 3.0.x
No idea what is the problem?
Thanks for your help guys
Best practices for using and troubleshooting VMware Converter
* If you found this information useful, please consider awarding points for
"Correct" or "useful."
-
it is possible to recovery data after restore and software update ( ios 7.1.2 ) ? with same apple id or not ?
It is possible if you have backed up your data. Follow this article restore your iPhone, iPad or iPod touch backup - Apple Support
-
How can I restore my data with the recovery firefox key?
So, my laptop was recently reimagee. I was able to get a recovery key Firefox before everything has been removed. When I downloaded Firefox on the recreated machine, asked me to connect. After several resets the password, I have been in. None of my data came down from the cloud "firefox". It does give me an option to enter the recovery key. Is it possible to recover all my stuff?
Firefox sync was never to be a backup service, you should always have a printed copy of your data.
You can do it, although there is no guarantee that it will work.
- Download firefox ftp://ftp.mozilla.org/pub/firefox/releases/28.0/win32/en-US/28.
- Do not stay on 28, it's not safe, but we will use it to retrieve your old data sync
- Use your recovery key to connect to your sync account, see if you can download your data. If it works, please do the next step
- Upgrade to Firefox 30 Update Firefox to the latest version
- Update to the new Sync synchronize your bookmarks from Firefox, history, passwords, etc.
Maybe you are looking for
-
I have windows 7 pro office. Downloaded the latest version of Firefox which was working fine then got on Firefox AOL malware browser hijacker, so I must have inadvertently downloaded some software when it was included. I got rid of that and deleted t
-
XZero script forms do not load in FireFox
Hello, if you are familiar with the XZeroscript, it is a community class based php script similar to Craigslist. I tried to make changes to the code, but for a reason, the following fields are not loaded in FireFox but all other browsers the fields l
-
My backspace does not work, when I try to go back he wound work, let me know what I need to do.
-
Hello My lifecam studio worked pretty well, but I kept getting a message saying something about the requirements is not enoughbut it was the path in front of the requirements. but I was going to upgrade my CPU when even if I upgraded from AMD Phenom
-
How do I have a packard bell istart 2380 factory reset?
My computer is incredibly slow and I just want this thing factory reset, I tried looking for countless hours to find how do and found nothing, please for the love of all that is pure can someone please tell me how to do?