LLDP and SNMP
I have a 81xxF of powerconnect, 7048 switch and 5548 switches bouquets and I would get topology
LLDP and SNMP
should the OID I use?
Eric,
Here's the OID assignments for all Dell Networking switches.
The OID industry:. 1.3.6.1.4.1
Manufacturer OID: Reference Dell = 674
LOB OID: Networks Dell = 10895
Example =. 1.3.6.1.4.1.674.10895.1000 is a PowerConnect 5212 switch
System for all products Dell Netwoking object IDS:
5212 - 10895.1000
5224 - 10895.4
6024/F 10895.3000
3324 - 10895.3002
3348 - 10895.3003
5324 - 10895.3004
3424 - 10895.3006
3448 - 10895.3007
3424 P - 10895.3008
3448 P - 10895.3009
6224-10895.3010
6248 10895.3011
6224P 10895.3012
6248P 10895.3013
10895.3014 6224F
M6220 = 10895.3015
3524 = 10895.3016
3548 = 10895.3017
3524 P = 10895.3018
3548 P = 10895.3019
5424 10895.3020
5448 10895.3021
M8024 = 10895.3022
8024 = 10895.3023
8024F = 10895.3024
M6348 = 10895.3025
2808 10895.3026
2816 10895.3027
2824 10895.3028
2848 10895.3029
5524 = 10895.3030
5548 = 10895.3031
5524 P = 10895.3032
5548 P = 10895.3033
7024 = 10895.3034
7048 = 10895.3035
7024 P = 10895.3036
7048 P = 10895.3037
7024F = 10895.3038
7048T = 10895.3039
7048T - RA = 10895.3040
M8024-k = 10895.3041
N4032 = 10895.3042
8132 = 10895.3042
N4032F = 10895.3044
8132F = 10895.3044
N4064 = 10895.3045
8164 = 10895.3045
N4064F = 10895.3046
8164F = 10895.3046
N2024 = 10895.3053
N2048 = 10895.3054
N2024P = 10895.3055
N2048P = 10895.3056
N3024 = 10895.3057
N3048 = 10895.3058
N3024P = 10895.3059
N3048P = 10895.3060
N3024F = 10895.3061
Dell Wireless devices:
Controller W-650 = 10895.5001
W-651 controller = 10895.5002
Controller W-3200 = 10895.5003
Controller W-3400 = 10895.5004
Controller W-3600 = 10895.5005
W-AP92 = 10895.5006 access point
W-AP93 = 10895.5007 access point
W-AP105 = 10895.5008 access point
W-AP124 = 10895.5009 access point
W-AP125 = 10895.5010 access point
W-RAP5 = 10895.5011 access point
W-RAP5WN = 10895.5012 access point
W-RAP2 = 10895.5013 access point
Controller W-620 = 10895.5014
Hope this helps,
B
Tags: Dell Switches
Similar Questions
-
I can't have a log and snmp in vpn
Hello
I can't have a log and snmp in vpn when I want to achieve the management interface, or remote access to asdm and ssh is strange ok.it for your help thank you.
Best regards
If you want to access the ASA via a VPN connection, you would not use (or should use) NAT. You only need to add command -access to the administration .
So let's say you want to use the IP address associated with the interface named inside of handle the ASA. Then you go inside management-access command
--
Please do not forget to rate and choose a good answer -
I'm looking to collect statistics on the use of the cpu interface and memory. How to configure snmp on CIDS network IPS products and or IPS?
Cisco IDS v4.1 does not support SNMP in any form.
IIRC, IPS v5.0 supports SNMP v2c (to send alerts as traps or accepting to provide statistics of sensor applications), although I don't personally know well set up this feature.
Details on the configuration of SNMP (whether to alert or the collection of statistics) on a sensor running v5.0 can be found here:
I hope this helps.
Alex Arndt
-
SFE2000 and SNMP Configuration Switch SGE20x0
Hello
I'm looking for the OID of the memory, but I can't find them. I found the mib to SGE20x0, who also works for the SFE2000 here switcch
http://software.cisco.com/download/release.html?mdfid=282414067&softwareid=283415684&release=3.0.0&relind=AVAILABLE&rellifecycle=&reltype=latest , but there is no OID pick-up for memory. Is no OID for memory available?
Concerning
Jürgen
Hi Jürgen, the information contained in the link is the information documented and supported.
If the OID / name of the object is not listed you want is essentially not supported.
If you haven't already done so, you can try to walk to the database and analyze the results to see if there is anything close to what you want.
-Tom
Please mark replied messages useful -
Get started with OpenManage / IT Assistant and SNMP.
Hello
I have 8 Dell poweredge servers.
They have all the power supplies redundent and raid 1.
If there is a problem, it appears in the LCD display on the side front of the server.
However... I'm about to send off to a data center and is no longer able to see the facades of my servers.
How to make the machines simply send me an email when they feel the need to display a message on the LCD screen. So I can remotely see what is happening.
I reflected on this and tried Assistant and Assistant to the server but it gets ridiculously complicated when all I want is the error sent to me.
These are critical machines and so far it seems IT Deputy can do software updates and a lot of things on the remote machines that I don't want. This is related to a security risk or will simply another thing to fool you that will have the machine with her!
My question is how the machine to send me his problems.
The main, I want to know is failure of HDD, redundent power failure, maxing out CPU and drives low on space.
Any help on this would be really welcome. The closest I got settled assistant server on a machine that seems to be able to generate alerts, but strangely, there doesn't seem to be able to send them by email, but oddly, he can do a popup will appear on the screen, if someone is logged.
Many thanks in advance,
Simon
-
Configure the file snmp.xml on 5.5 ESXi via PowerShell and PowerCLI
Hello:
I wonder if there is a way to configure the file snmp.xml on the ESXi host (/ etc/vmware/snmp.xml) using the script? I have root password and you want to be able to day/edit this file remotely...
Thank you very much!
To use the Set-VMHostSnmp cmdlet you must be directly connected to the ESXi host. The following example will connect to an ESXi host named ESX01 and SNMP sets active and a community example of community read-only (example 1 of using Set-VMHostSnmp):
SE connect-VIServer ESX01
$vmhostSNMP = get-VMHostSNMP
Game-VMHostSNMP $vmhostSNMP - active: $true - ReadOnlyCommunity example 'Community '.
-
ISE MAC movement move and host of Cisco
Hello
I read that SNMPTraps should not be sent to ISE using probe RADIUS, because it will trigger only a SNMPQuery duplicate. If so, how do you support a use case by which a device can withdraw the authorization of a switch port and successfully allow on a different port. It is one of the following exclusion of others?
1 authentication allowed mac-passage
2. analysis of IP device
3. change notification-mac address table, notification of mac address table mac-move, trap snmp-server (global configuration) and snmp trap mac-notification (configuration interface)
I understand that for a device behind a non-cisco IP, CDP or LLDP logoff phone or Proxy EAPOL will inform the switch.
Thank you
move to the Mac permits is the solution.
-
Hello
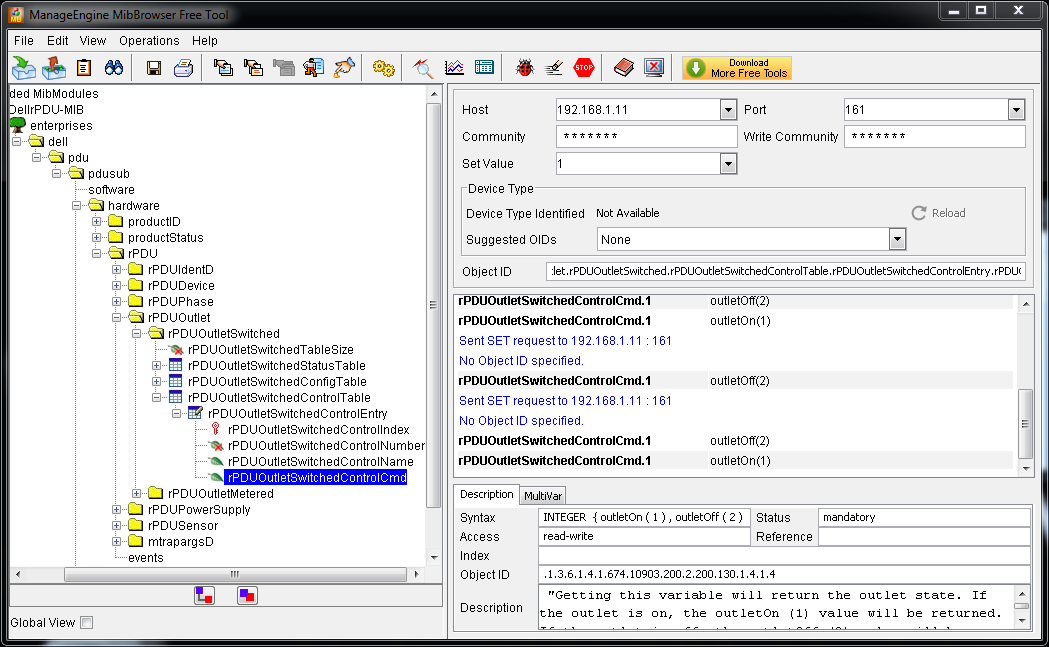
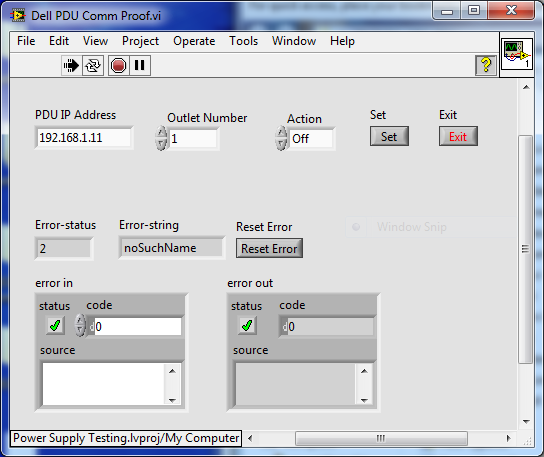
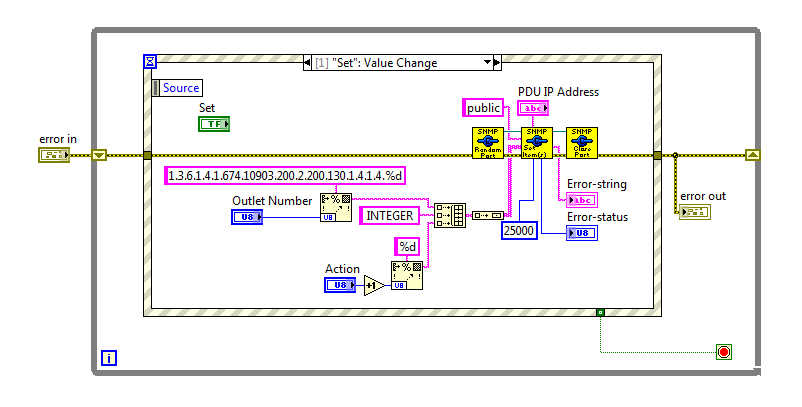
I'm all new to SNMP, although I have used LabVIEW a few times in recent years. Office supplies for the moment, I am developing an application to test the power. We use a G756N Dell PDU for each switching power. I tried a couple of approaches to control and SNMP is the most promising so far. During my research I came across free ManageEngine MibBrowser and I could find the last MIB to download the firmware from Dell here. I was able to communicate with the UDA and points of sale under and out so far, but I really need to integrate control of the PDU in the application of LabVIEW to automate tests. I'm pinned Mark Yedinak and his APC PDU SNMP communication library, only the most recent of which I found examples in this thread.
I tried to do a VI to test communication in LabVIEW using the OID I received from MibBrowser, but it returns an error code 2, noSuchName. The PDU is configured to use SNMP v1 and the public and private communities write access +. I tried with and without the main point, but without success. I'm using LabVIEW 2013 64-bit. Could someone please review the information below and see what I could do wrong, or that the direction to take to solve the problems there?
Thank you
Simon
MIB object IDS:
. iso.org.dod.internet.private.enterprises.dell.pdu.pdusub.hardware.rPDU.rPDUOutlet.rPDUOutletSwitched.rPDUOutletSwitchedControlTable.rPDUOutletSwitchedControlEntry.rPDUOutletSwitchedControlCmd
. 1.3.6.1.4.1.674.10903.200.2.200.130.1.4.1.4.1: {1 or 2}
I added le.1 at the end of the index to the first exit, and 1 variable is instantaneous, while the 2 is instant off
Photo
VI:
Front panel:
Wiring:
Link to examples of SNMP Communications and APC_PDU.zip:
http://forums.NI.com/T5/LabVIEW/APC-ups-with-desktop/m-p/2431528/highlight/true#M749059
For some reason, I can't the real VI set. The MIB is too in the archive. Its in my selection here:
https://DL.dropboxusercontent.com/u/10871313/power%20Supply%20Testing.zip
Thanks again
-
OME 2.0.1 and Brocade M5424 fc switches
Hello
I have problem with OME discovery/inventory abd Brocade M5424. 4 M5424 brocades are defined as 2 M1000e chassis access gateways, problem is this discovery/inventory OME found as a fibre channel switch with 4 ip addresses.
Inventory and discovery works well with all the other components of these 2 chassis, only fc switches I have this problem.
M5424 have unique host names, single ip addr. and snmp is defined. OME same troubleshooting tool gives me the correct result when the connection on these switches CF test.
Anyone with the same problem? Mode gateway may be the source of this problem?
Thanks for any help
Martin
-
5548, 7048 - PowerConnect backup SNMP configuration
Hello
I Powerconnect 5548 and 7480 switches and I would like to know if it is possible to backup with TFTP and SNMP commands configuration files, like I do with my cisco switches?
Thank you.
You should be able to use rlcopy which is OID.1.3.6.1.4.1.89.87
Location of the source Rlcopy.1.3.6.1.4.1.89.87.2.1.3
Rlcopy the ip address of destination.1.3.6.1.4.1.89.87.2.1.9
Updates of the firmware also contain the mib files, so you can find the OID http://www.dell.com/support/home/us/en/04/Drivers/DriversDetails?driverId=JRCF6&fileId=3365034200&osCode=NAA&productCode=powerconnect-5524&languageCode=EN&categoryId=NI
-
OnPlus discovery and Nexus 5548
Hello
I just installed an OnPlus agent for a customer who has a Nexus with a 3 layer daugthter card 5548 as their central switch, but the agent is not discovered any device beyond the vlan in which he is sitting. Does anyone have any experience with the OnPlus ageent and Nexus switches. It is obviously not a Cisco device supported but I configured IDs connection and snmp access to the switch on the portal, but still nothing is discovered. Any advice greatly appreciated.
Concerning
Ian
Hi Ian,
To discover the multi - VLAN, connect the On100 to an 802. 1 q trunk port. This will allow the On100 discover other VLANs. It is currently connected to an access port which is to limit the broadcast traffic of the other VLAN.
Although the device is not currently supported, he discovered and enable basic support we provide for all detected devices.
Thank you
The OnPlus team
-
Hello
We have two WAP561 devices and they delivered with firmware 1.0.3.4. In this firmware release notes, there is open opposition with reference number CSCty22825, declaring that telnet and ssh is disabled in the interface chart and SNMP. In the notes of the other releases, as 1.1.0.4, this caveat is no longer present. We have improved our 1.1.0.4 devices, over telnet and ssh section is still not present in the GUI.
Is there a way to enable ssh on these devices? In the administration guide, there should be a section called 'Telnet and SSH', but it is not present in the GUI. We also checked with the emulators with different firmwares. Still no telnet and ssh, section.
Your help is very appreciated.
Thank you
Hello
These options were available in a very old firmware (the first version) which is no longer present on the cisco.com site and unfortunately I do not have. For security reasons, these options have been removed the new firmwares available.
I hope that the information provided was useful.
If you have any other questions do not hesitate to contact me.
Best regards
-
Hello
We run 3xWLC controller with 800 AP using ISE 1.2 for authentication wireless 802. 1 x. I was looking in the config of the ISE and notice of 400 edge cheating only 2x2960s are configured with 802. 1 x (ISE RADIUS config) and SNMP and only 2 of the port is 2 ap tie with swtich remaining ports.and the 3XWLC in network devices.
I do not understand how an access point is to do this work (802.1 x) because it is location on different site and people are connecting to various different locations. ISE almost run/do 11 876 profiled ends.
version 12.2
!
boot-start-marker
boot-end-marker
!
enable secret 5 $1$ fokm$ lesIWAaceFFs.SpNdJi7t.
!
Test-RADIUS username password 7 07233544471A1C5445415F
AAA new-model
Group AAA dot1x default authentication RADIUS
Group AAA authorization network default RADIUS
Group AAA authorization auth-proxy default RADIUS
start-stop radius group AAA accounting dot1x default
start-stop radius group AAA accounting system by default
!
!
!
!
AAA server RADIUS Dynamics-author
Client 10.178.5.152 server-key 7 151E1F040D392E
Client 10.178.5.153 server-key 7 060A1B29455D0C
!
AAA - the id of the joint session
switch 1 supply ws-c2960s-48 i/s-l
cooldown critical authentication 1000
!
!
IP dhcp snooping vlan 29,320,401
no ip dhcp snooping option information
IP dhcp snooping
no ip domain-lookup
analysis of IP device
!
logging of the EMP
!
Crypto pki trustpoint TP-self-signed-364377856
enrollment selfsigned
name of the object cn = IOS - Self - signed - certificate - 364377856
revocation checking no
rsakeypair TP-self-signed-364377856
!
!
TP-self-signed-364377856 crypto pki certificate chain
certificate self-signed 01
30820247 308201B 0 A0030201 02020101 300 D 0609 2A 864886 F70D0101 04050030
2 060355 04031325 494F532D 53656 C 66 2 AND 536967 6E65642D 43657274 30312E30
69666963 33363433 37373835 36301E17 393330 33303130 30303331 0D 6174652D
305A170D 2E302C06 1325494F 03550403 32303031 30313030 30303030 5A 303031
532D 5365 6C662D53 69676E65 642D 4365 72746966 69636174 652 3336 34333737
06092A 86 4886F70D 01010105 38353630 819F300D 00308189 02818100 0003818D
B09F8205 9DD44616 858B1F49 A27F94E4 9E9C3504 F56E18EB 6D1A1309 15C20A3D
31FCE168 5A8C610B 7F77E7FC D9AD3856 E4BABDD1 DFB28F54 6C24229D 97756ED4
975E2222 939CF878 48D7F894 618279CF 2F9C4AD5 4008AFBB 19733DDB 92BDF73E
B43E0071 C7DC51C6 B9A43C6A FF035C63 B53E26E2 C0522D40 3F850F0B 734DADED
02030100 01A 37130 03551 D 13 6F300F06 0101FF04 05300301 01FF301C 0603551D
11041530 13821150 5F494D2B 545F5374 61636B5F 322D312E 301F0603 551D 2304
18301680 1456F3D9 23759254 57BA0966 7C6C3A71 FFF07CE0 A2301D06 03551D0E
04160414 56F3D923 75925457 BA09667C 6C3A71FF F07CE0A2 2A 864886 300 D 0609
F70D0101 5B1CA52E B38AC231 E45F3AF6 12764661 04050003 81810062 819657B 5
F08D258E EAA2762F F90FBB7F F6E3AA8C 3EE98DB0 842E82E2 F88E60E0 80C1CF27
DE9D9AC7 04649AEA 51C49BD7 7BCE9C5A 67093FB5 09495971 926542 4 5A7C7022
8D9A8C2B 794D99B2 3B92B936 526216E0 79 D 80425 12B 33847 30F9A3F6 9CAC4D3C
7C96AA15 CC4CC1C0 5FAD3B
quit smoking
control-dot1x system-auth
dot1x critical eapol
!
pvst spanning-tree mode
spanning tree extend id-system
No vlan spanning tree 294-312,314-319,321-335,337-345,400,480,484-493,499,950
!
!
!
errdisable recovery cause Uni-directional
errdisable recovery cause bpduguard
errdisable recovery cause of security breach
errdisable recovery cause channel-misconfig (STP)
errdisable recovery cause pagp-flap
errdisable recovery cause dtp-flap
errdisable recovery cause link-flap
errdisable recovery cause FPS-config-incompatibility
errdisable recovery cause gbic-invalid
errdisable recovery cause psecure-violation
errdisable cause of port-mode-failure recovery
errdisable recovery cause dhcp-rate-limit
errdisable recovery cause pppoe-AI-rate-limit
errdisable recovery cause mac-limit
errdisable recovery cause vmps
errdisable recovery cause storm-control
errdisable recovery cause inline-power
errdisable recovery cause arp-inspection
errdisable recovery cause loopback
errdisable recovery cause small-frame
errdisable recovery cause psp
!
internal allocation policy of VLAN ascendant
!
!
interface GigabitEthernet1/0/10
switchport access vlan 320
switchport mode access
IP access-group ACL-LEAVE in
authentication event fail following action method
action of death server to authenticate the event permit
living action of the server reset the authentication event
multi-domain of host-mode authentication
open authentication
authentication order dot1x mab
authentication priority dot1x mab
Auto control of the port of authentication
periodic authentication
authentication violation replace
MAB
dot1x EAP authenticator
dot1x tx-time 10
spanning tree portfast
spanning tree enable bpduguardinterface GigabitEthernet1/0/16
switchport access vlan 320
switchport mode access
IP access-group ACL-LEAVE in
authentication event fail following action method
action of death server to authenticate the event permit
living action of the server reset the authentication event
multi-domain of host-mode authentication
open authentication
authentication order dot1x mab
authentication priority dot1x mab
Auto control of the port of authentication
periodic authentication
authentication violation replace
MAB
dot1x EAP authenticator
dot1x tx-time 10
spanning tree portfast
spanning tree enable bpduguard
interface GigabitEthernet1/0/24
switchport access vlan 320
switchport mode access
IP access-group ACL-LEAVE in
authentication event fail following action method
action of death server to authenticate the event permit
living action of the server reset the authentication event
multi-domain of host-mode authentication
open authentication
authentication order dot1x mab
authentication priority dot1x mab
Auto control of the port of authentication
periodic authentication
authentication violation replace
MAB
dot1x EAP authenticator
dot1x tx-time 10
spanning tree portfast
spanning tree enable bpduguard
!
interface GigabitEthernet1/0/33
switchport access vlan 320
switchport mode access
IP access-group ACL-LEAVE in
authentication event fail following action method
action of death server to authenticate the event permit
living action of the server reset the authentication event
multi-domain of host-mode authentication
open authentication
authentication order dot1x mab
authentication priority dot1x mab
Auto control of the port of authentication
periodic authentication
authentication violation replace
MAB
dot1x EAP authenticator
dot1x tx-time 10
spanning tree portfast
spanning tree enable bpduguard
interface GigabitEthernet1/0/34
switchport access vlan 320
switchport mode access
IP access-group ACL-LEAVE in
authentication event fail following action method
action of death server to authenticate the event permit
living action of the server reset the authentication event
multi-domain of host-mode authentication
open authentication
authentication order dot1x mab
authentication priority dot1x mab
Auto control of the port of authentication
periodic authentication
authentication violation replace
MAB
dot1x EAP authenticator
dot1x tx-time 10
spanning tree portfast
spanning tree enable bpduguard
!
interface GigabitEthernet1/0/44
switchport access vlan 320
switchport mode access
IP access-group ACL-LEAVE in
authentication event fail following action method
action of death server to authenticate the event permit
living action of the server reset the authentication event
multi-domain of host-mode authentication
open authentication
authentication order dot1x mab
authentication priority dot1x mab
Auto control of the port of authentication
periodic authentication
authentication violation replace
MAB
dot1x EAP authenticator
dot1x tx-time 10
spanning tree portfast
spanning tree enable bpduguard!
interface GigabitEthernet1/0/46
switchport access vlan 320
switchport mode access
IP access-group ACL-LEAVE in
authentication event fail following action method
action of death server to authenticate the event permit
living action of the server reset the authentication event
multi-domain of host-mode authentication
open authentication
authentication order dot1x mab
authentication priority dot1x mab
Auto control of the port of authentication
periodic authentication
authentication violation replace
MAB
dot1x EAP authenticator
dot1x tx-time 10
spanning tree portfast
spanning tree enable bpduguardinterface GigabitEthernet1/0/48
switchport access vlan 320
switchport mode access
IP access-group ACL-LEAVE in
authentication event fail following action method
action of death server to authenticate the event permit
living action of the server reset the authentication event
multi-domain of host-mode authentication
open authentication
authentication order dot1x mab
authentication priority dot1x mab
Auto control of the port of authentication
periodic authentication
authentication violation replace
MAB
dot1x EAP authenticator
dot1x tx-time 10
spanning tree portfast
spanning tree enable bpduguard
!
interface GigabitEthernet1/0/49
Description link GH
switchport trunk allowed vlan 1,2,320,350,351,401
switchport mode trunk
MLS qos trust dscp
IP dhcp snooping trust
!interface GigabitEthernet1/0/52
Description link CORE1
switchport trunk allowed vlan 1,2,29,277,278,314,320,401
switchport mode trunk
MLS qos trust dscp
IP dhcp snooping trust
!
!
interface Vlan320
IP 10.178.61.5 255.255.255.128
no ip-cache cef route
no ip route cache
!
default IP gateway - 10.178.61.1
IP http server
IP http secure server
IP http secure-active-session-modules no
active session modules IP http no
!
!
Access IP extended ACL-AGENT-REDIRECT list
deny udp any any domain eq bootps
permit tcp any any eq www
permit any any eq 443 tcp
IP extended ACL-ALLOW access list
allow an ip
IP access-list extended by DEFAULT ACL
allow udp any eq bootpc any eq bootps
allow udp any any eq field
allow icmp a whole
allow any host 10.178.5.152 eq 8443 tcp
permit tcp any host 10.178.5.152 eq 8905
allow any host 10.178.5.152 eq 8905 udp
permit tcp any host 10.178.5.152 eq 8906
allow any host 10.178.5.152 eq 8906 udp
allow any host 10.178.5.152 eq 8909 tcp
allow any host 10.178.5.152 eq 8909 udp
allow any host 10.178.5.153 eq 8443 tcp
permit tcp any host 10.178.5.153 eq 8905
allow any host 10.178.5.153 eq 8905 udp
permit tcp any host 10.178.5.153 eq 8906
allow any host 10.178.5.153 eq 8906 udp
allow any host 10.178.5.153 eq 8909 tcp
allow any host 10.178.5.153 eq 8909 udp
refuse an entire ip
Access IP extended ACL-WEBAUTH-REDIRECT list
deny ip any host 10.178.5.152
deny ip any host 10.178.5.153
permit tcp any any eq www
permit any any eq 443 tcpradius of the IP source-interface Vlan320
exploitation forest esm config
logging trap alerts
logging Source ip id
connection interface-source Vlan320
record 192.168.6.31
host 10.178.5.150 record transport udp port 20514
host 10.178.5.151 record transport udp port 20514
access-list 10 permit 10.178.5.117
access-list 10 permit 10.178.61.100
Server SNMP engineID local 800000090300000A8AF5F181
SNMP - server RO W143L355 community
w143l355 RW SNMP-server community
SNMP-Server RO community lthpublic
SNMP-Server RO community lthise
Server SNMP trap-source Vlan320
Server SNMP informed source-interface Vlan320
Server enable SNMP traps snmp authentication linkdown, linkup cold start
SNMP-Server enable traps cluster
config SNMP-server enable traps
entity of traps activate SNMP Server
Server enable SNMP traps ipsla
Server enable SNMP traps syslog
Server enable SNMP traps vtp
SNMP Server enable traps mac-notification change move threshold
Server SNMP enable traps belonging to a vlan
SNMP-server host 10.178.5.152 version 2 c lthise mac-notification
SNMP-server host 10.178.5.153 version 2 c lthise mac-notification
!
RADIUS attribute 6 sur-pour-login-auth server
Server RADIUS attribute 8 include-in-access-req
RADIUS attribute 25-application access server include
dead-criteria 5 tent 3 times RADIUS server
test the server RADIUS host 10.178.5.152 auth-port 1812 acct-port 1813 username test-RADIUS 7 key 03084F030F1C24
test the server RADIUS host 10.178.5.153 auth-port 1812 acct-port 1813 username test-RADIUS 7 key 141B060305172F
RADIUS vsa server send accounting
RADIUS vsa server send authenticationany help would be really appreciated.
I'm not sure that completely understand the question; But if LSE is only political wireless, then none of the wired switches need any configuration of ISE.
Access points tunnel all wireless traffic to the WLC on CAPWAP (unless you use FlexConnect). This is the configuration 802. 1 x on the WLC that implements policies defined in ISE.
Switches wired never need to act as an access network (n) device and so do not need to be defined in ISE unless or until you want to apply policies of ISE for wired devices...
-
Hi all
All those being implemented / activated the module SNMP on DMS?
"The only issue that I face today, is that if I get syslong, snmp for the DMP inaccessible, I can't receive email notification.
Won't do anything with notifications by e-mail on 5.2? »
Please explain further...
Only alerts for DMP are DMP outages, reboots, conflict of IP and records. Describe what you
mean inaccessible?
The E-mail, Syslog, and SNMP all seem to work my setup 5.2 for the alerts listed above.
Thank you
T.
-
Cisco first below 3.0 and integration of NAM - 3
Hello
I have a problem with the service integration first and NAM-2 module below.
I added NAM - 3 on the first with HTTP and SNMP, but NAM-3 Protocol does not show as Data Source, I also add first Infra to NAM - 3,.
Anyone know the cause of this problem?
Thank you very much
Hello
Have you made sure your first server Infrastructure running license type insurance?
NAM/monitoring NetFlow depend on this course of activation.
Luis
Maybe you are looking for
-
Satellite 5200 903 - how to enter the BIOS Setup
Hello, ive got a S5200-903 Satellite and I have to reinstall my Windows XP. But I am not able to get into the Bios, please tell me how.
-
Satellite 3000-100: 2nd battery does not charge.
Hi, I have just a PA3099U-1BRS bought 2nd battery internal bay for Satellite 3000-100, but he remains at 0% and will not load. I read the areas of support of the site and it says I need at least v1.90 BIOS and I 2.40 (otherwise it could have been the
-
Photos.app didn't rename my converted iPhoto library. Is this ok?
Hi, I upgraded to El Capitan and Photos.app ran for the first time. He converted all 660 GB of our iPhoto/Aperture on its new format library and created the "Library.photoslibrary Photos" bundle in the images folder. However, I noticed she did not r
-
Error code: 646 (cannot install KB228621)
Please can you owed me well KB errors to fix this please
-
I changed my account from administrator to a limited account user, as I had 2 accounts of users, two administrator accounts. Now I can't login as administrator. I can't find the administrator and any other accounts show that when I try to switch user