Probes IPS from multicast traffic
The ASA/AIP-SSM modules pass multicast traffic when it is configured in online mode?
-Bob
Hi Bob,
The AIP - SSM acts as a L2 bridge when it is used in Inline mode, so it must pass very well multicast traffic.
I did some research, and unfortunately, there is a bug that would prevent do this according to me:
| CSCtb82257 Multicast sending to the AIP - SSM module affects Dimethylacetamide 0000.0000.0000 |
Since it is not fixed yet, I advise you to have multicast traffic circumvent the AIP - SSM and send unicast traffic to it.
Kind regards
Nicolas
Tags: Cisco Security
Similar Questions
-
How to restrict multicast traffic to specific ports on GS716Tv3?
I can not find specific instructions to limit traffic of multicast on the smart switch GS715Tv3.
I need to force all multicast traffic to travel on a specific set of interfaces, or at least stay within a given virtual LAN on the switch to which it is native. All the changes you want multicast servers and listeners will be on these interfaces in their separate vLAN.
We have several GS715Tv3 switches configured identically, but multicast traffic does not pass between the switches.
Topology:
Eight GS716Tv3 smart switches, each configured with three VLANS identical.
No traffic should pass between these VLANS on the switch or pass between the switches
In other words, even if all the 8 switches each have a vLAN named "IOSubsystem", I do not considered the same vLAN.
.
vLAN 4 is corresponding to the hosts of Linux to address major
vLAN 5 is for the audio subsystem
vLAN 6 is for the IO subsystem
VLAN each switch 4 has two active ports, a session to the external interface of the main Linux host and the other to a central switch of 9th GS716Tv3 where a system of software development is also linked.
VLAN each 5 switch connects to the components of the audio subsystems (not shown).
VLAN each switch 6 has two active ports, a going inward a lead Linux host interface and one for the IO subsystem.
-> [vLAN4 | g10]---> [Switch #9]-+.
-> [vLAN4 | g9]-> [Linux host #1: eth0] |
[Switch #1]-> [vLAN6: g1]-> [Linux host #1 | eth1] |
-> [vLAN6: g2]-> [e/s 1 subsystem] |
|
-> [vLAN4 | g10]---> [Switch #9]- +---> [software Dev host]
-> [vLAN4 | g9]-> [Linux host #2: eth0] |
[Switch #2]-> [vLAN6: g1]-> [Linux host #2 | eth1] |
-> [vLAN6: g2]-> [subsystem/o 2] |
... ~
|
-> [vLAN4 | g10]---> [Switch #9]-+.
-> [vLAN4 | g9]-> [Linux host #8: eth0]
[Switch #8]-> [vLAN6: g1]-> [Linux host #8 | eth1]
-> [vLAN6: g2]-> [i/o subsystem #8]We get multicast traffic unwanted between each of these systems, causing corruption of our stream. We limit the multicast traffic on vLAN6 of each switch to stay on the vLAN6 of this specific switch.
Thanks for any help.
To switch the management VLAN to 4.
Make sure you have 2-way switch, one in VLAN4 in a VLAN1.
4 and apply the value of the system you use to a static IP address to the switch and confirm the access to the web configuration and then change "management VLAN ID. then pass the system that you use on the port or any VLAN 4, then you should have access, otherwise, wait about 60-90sec and try again, because you might have PLEASE and it will block anything on the port for just under its set to "Enabled" 'Fast Link '.
Then under "IP Configuration" value switches other IP address in IP range of VLAN4.
For the love of Simplisicty, unmarked ports should never be in 1 VLAN simultaneously.
And instead of using the point and click, goto "Port PVID Configuration" and just create the VLAN it.
Member of the PVID and VLAN the same thing for a port, on what VLAN, it must be in the database
And to confirm, you have a cable from switch to each VLAN? You can cut down on cables and ports if you tag/trunk ports to the next switch. then all VLAN 3 just 1 cable between each pair of switches, saving you at least 4 ports on each switch.
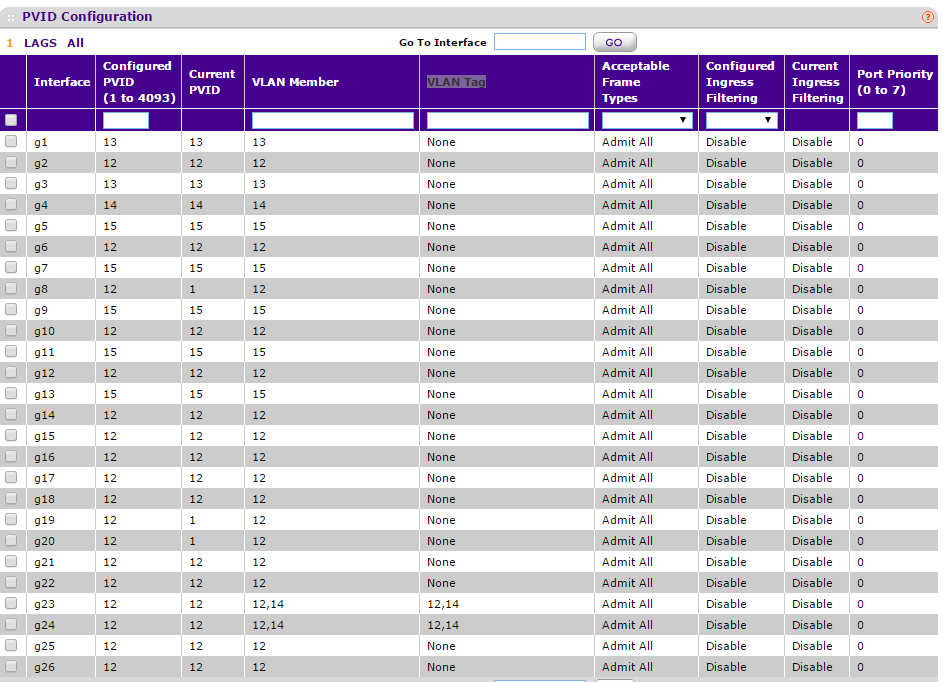
Just an example of my GS724T (ignore ports g8 and g-19-20, their current PVID is because of something else you do not, LACP and Span/Monitoring):
All ports are configured to a single VLAN, my 'LAN hand' is VLAN12, that the management VLAN is set for, g23-24 ports VLAN trunks, they are set on tagg VLAN12 and 14 when the traffic is out of these ports, then switch to the other side reads the consequence tagg and acts, that way I don't need 2 cables/port for each of them.
-
Multicast traffic stops flowing after a while when using IGMP snooping
Hi all
I have the following configuration:
:

Where host 1 is a multicast traffic source and host 2 is a customer of multicast traffic. IGMP snooping is configured on both switches.
Host 2 boots and sends an IGMP report, in order to join the multicast host group 1. Given that SW2 does not know where the mrouter from the group, adds port Eth1/1 to the Group of snooping and removes the package, the IGMP packet. Once host 1 starts, it sends an IGMP query (which is flooded by the port channel), and multicast traffic starts to flow to host 2.
When I ran 'show ip Mattia snooping groups' I've seen the same result on both switches: on the two switches of the groups the Eth1/1 and the channel port, but after a while, the switch connected to the host 2 deleted the channel of the port of the group.
After consultation with the switch logs and sniff traffic on one of the channel port on SW1 interfaces, I came to the conclusion that happens since SW1 ceases to send queries generated by host 1 and responding to them locally (some proxy or something). I also noticed that IGMP reports generated by host 2 stop arriving on SW1 (since SW2 do not know that there a connected mrouter more across the channel of the port).My questions are:
1. How does SW1 knows he should keep the channel port as part of the group, if it does not IGMP reports coming from SW2 more?
2. what happens if the host 2 is not interested in multicast traffic, but do not send and IGMP leave message (a behavior that is supported according to the Protocol, to my knowledge)? How SW1 knows he should cease to IGMP sent from host 1 query response?
Thanks in advance,
Omer.
Hello
The problem is because you have not mrouter port sw1. It is well documented by virtue
http://www.Cisco.com/c/en/us/support/docs/switches/Catalyst-6500-Series-...
There are 3 ways you can solve this problem.
1. enable Pim on Sw1.
Or
2. enable ip igmp snooping interrogator on Sw2
Or
3. create staitc mrouter port on sw2.
ip igmp snooping vlan 1 mrouter interface PoX
-
Why IPSec does not support multicast traffic?
If IPSec is a tunnel, why can't set you the multicast traffic in an ACL to protect?
IPSec is a standard, and there is nothing in the standard that allows for multicast or broadcast traffic to go through it.
Specifically, the IPSec RFC (ftp://ftp.isi.edu/in-notes/rfc2401.txt) says things like:
A security association is identified by a triple compound
a security parameter Index (SPI), Destination IP address, and a
identifier (AH or ESP) security protocol. In principle, the
Destination address may be a unicast, broadcast IP address
address or multicast group address. However, the IPsec Security Association Management
Currently, the mechanisms are defined only for unicast SAs.
and
The receiver-orientation of the Security Association implies that, in
the case of unicast traffic, the destination system will normally be
Select the SPI value. Making the destination select the SPI
value, there is no risk for manually configured security
Associations to conflict with automatically configured (e.g., via a)
The key management protocol security associations) or safety
Associations from several sources in conflict between them. For
multicast traffic, there are multiple destination systems by
Multicast group. If some system or person will need to coordinate
Among all the multicast groups to select an SPI or SPIs on behalf of each
multicast group and communicate the IPsec group information to
all legitimate members of this group of multicast through mechanisms
not defined here.
Several transmitters to a multicast group SHOULD use a single title
Association (and therefore Security Parameter Index) for all traffic to
This group when a symmetric key encryption or authentication
algorithm is used. In such circumstances, the receiver knows only
that the message is from a system with the key for this
Multicast group. In such circumstances, a receiver will be generally
not be able to authenticate which system sent the multicast traffic.
Specifications for other, more general multicast cases are postponed
for later IPsec documents.
Sorry to quote RFC from you, but we just follow the standard and the standard does not support this. You can bypass it by setting a GRE/IPSec connection, but what really is encapsulating the broadcast/multicast in a package of volition unicast first, then encrypt this unicast packet.
-
Can I use private as Source IPs from a remote network IP addresses while building the IPSec tunnel?
Can I use private as Source IPs from a remote network IP addresses while building the IPSec tunnel? If not why? If so, how?
Your explanation is much appreciated.
Hi Deepak,
In such a situation, you usually NAT traffic that goes to the internet, but exempt traffic that goes through the VPN, because it will be wrapped in packages with public IP (tunnel) addresses. You can use the same IP address on your interface in the face of internet for the NAT/PAT and source of IPSEC Tunnel.
-
inter esxi host ipv6 multicast traffic are not detected by the destination VM
Hello
Warning, I do not have in-depth knowledge of vmware, so please excuse the bad wording, misconception and ignorance in the post below.
The current topology is:
Each esxi 4.1 update 3 (DL380 G8) host is to connect both layer 2 switch.
on each host, the vswitch has two network cards configured as active/active, with the default NIC cluster approach (route based on the original virtual port code).
Everything else is default.
The switches are connected by a link to trunk (not bunk)
I have two Windows Server 2008 R2 VM in the same subnet and you have enabled ipv6 on them (by default)
When two virtual machines are on the same physical host, ping-6 destination_ipv6_address works (I just use the link local address)
When two virtual machines are on different hosts, ping fails with the "destination unreachable" message, which usually means the neighbor discovery process fails (similar to arp in ipv4 where source VM cannot get mac address of the destination virtual machine)
When two virtual machines are on the same physical host, the the packet capture shows that Neighbor Solicitation message is sent via an ipv6 multicast address
When they are not on the same physical hosts, packet capture on the VM shows that the destination virtual machine will ever get the destination ipv6 multicast packets.
I then connect two DL380 G8 in a similar way to the switches and install windows Server2008 R2 directly without virtualization on them and ping-6 works perfectly.
My questions are:
-I missed somewhere, a configuration to allow ipv6 multicast to work? Or even to remove any 'logic' and treat it simply as a show?
On network switches, you can do this by disabling IGMP who will then deal with multicast as broadcast packets.
Although I can't find a similar setting under esxi anywhere.
-J' saw an option "Enable ipv6" on esxi, but I guess it's only useful if the host itself to participate in ipv6 and therefore not applicable to my case?
The only similar question I found the research is on the link below, which suggest to hardcode the next table on virtual machines, which is not ideal.
I can confirm however, hard coding the table nearby on two virtual machines to work. This problem seems to be on how esxi vswitches manage ipv6 multicast traffic
Ideas, points of view are very appreciated
Ed
I don't know if this will really solve your problem, but it is worth trying to update the firmware of the NETWORK adapter and the driver.
Looks like it's a HP NC 331FLR NIC (gen8 DL by default NETWORK 4 ports with the BCM5719 chip card).
There is no binary updates that you can run from the 4.1, but you can update all the components of the firmware with the current Service Pack HP for Proliant image:
Or start the server in a live Linux of your choice and use the Linux binary update:
http://www.HP.com/swpublishing/MTX-ec0e18db6a8e4d978b57aa95d1
These will update the NIC 331FLR to the Boot Code version 1.37/NCSI 1.2.37.
Then update the tg3 driver in ESXi with this set to 3.129d.v40.1 offline:
You need the file bundle offline (BCM - tg3 - 3.129d.v40.1 - offline_bundle - 1033618.zip) in this package. You can import in the vCenter update manager for easier deployment or install it (probably) ESXi shell with esxupdate--bundle=/tmp/BCM-tg3-3.129d.v40.1-offline_bundle-1033618.zip
I'm a little rusty in the Department of ESXi 4.1 CLI however, you may need to use the vihostupdate utility or with PowerCLI Install-VMHostPatch remote:
-
E1000/E1000e receive multicast traffic all
Hello
I used E1000/E1000e as NIC in Linux and I found out that all multicast traffic network interface which meant vSwitch passed all multicast traffic to these interfaces.
I don't want the network interface to see all multicast traffic because it does not affect the performance of vSwitch. How can I do?
I knew also VMXNET 3 can meet my needs, but for some reason, I have to use E1000/E1000e.
Gabriel
I knew what wrong with this case. I use tcpdump to view multicast traffic that has been approved to be unreliable. Tcpdump changed the E1000/E1000e configuration, if she could see the multicast traffic.
Right now, I've changed my method. I looked statistics packages based on order esxtop. In QNX 6.5.0, I did the following steps:
1. start of QNX, let interface upward. I don't see any esxtop, THAT VM has received all the packages.
2. start tcpdump. I saw tcpdump captured packets multicasts. Also of esxtop, I see VM received packets.
3 collapsed tcpdump. Of esxtop, VM has not received all packages.
To conclude, QNX with E1000/E1000e support multicast packets. And tcpdump couldn't be used to see the multicast traffic.
-
Can IPS deployment limit political from the traffic speed or router?
Hello
I have a small question: can deploy IPS traffic rate limiting political to Cisco switch or router?
As we know, IPS sensor can throttle suspected trafficking instead of block, don't know if IPS can send policy lever swtich cisco gases or the router.
Thank you
-Alejin
You will find the following on what the PPE can do in terms of rate limiting (it also includes what signature and what routers, what must be configured and what not to set up, etc.):
http://www.Cisco.com/en/us/docs/security/IPS/7.0/Configuration/Guide/IDM/idm_blocking.html#wp2005501
The above is on IPS version 7.x.
Hope that helps.
-
ASA - NG IPS inspect encrypted traffic
Hello
We buy ASA 5525-X with IPS for us to network. We have a number of servers that provide services Web Applications.We have a big problem installing ASA it is we cannot use ASA inspect and IPS has because over 80% traffic through encrypted.Thank you to tell me how I can solve this problem.I know a solution to use Proxy HTTPS in ASA, but for some reason, this solution cannot be implemented.Thank you.If you want to protect you own Web servers against attacks from the internet. You cannot use the HTTPS-decryption of the ASA-CX as the internet - customers do not have your CX-certificate.
To resolve this problem, the typical is to place a proxy reversed in a DMZ and do the SSL/TLS-manipulation here. The reverse-proxy sends plain HTTP through the ASA and the IPS may inspect what and protect your servers.
-
SSP IPS can send traffic, so it acts only as an IDS, not as an IPS?
Hello
I could get the wrong end of the stick, I'm looking at the IPS Cisco portfolio, as the noise of the SSP IPS in 5585-X. I would like to than the IPS SSM to act passively, just monitor illicit traffic. Traffic would not be increased by X-5585, only to her.
I would like to the SSP, IPS to send a copy of the Treaty and then monitor it.
This would be possible using the SSP IPS?
Thank you very much
IDS/IPS module will only receive traffic only after its passage by the ASA. The IPS module security policy is adjustable for non-blocking actions, if you wish.
-Robert
-
Send from FW traffic via IPSec tunnel
Hello
I have a FW in site B that needs to authenticate VPN users that connect to the FW in site B to an RSA RADIUS server to site A. So, this means that the FW would send traffic RADUIS via its peer interface to site A. At least that is how the RADIUS server in site A see traffic. The RADIUS server will see it as coming from au pair from right side of site B's IP address?
The public (peer) IP of the interface does not part of interesting traffic, and I wonder if it might bite me in the a$ $.
Does this make any sense?
Thank you!
Perhaps add it but make an exclusion of Protocol in the interesting traffic.
That is to say excluding isakmp and esp traffic.
I'm not sure if it will work, but its worth a try
-
HP Pavilion 500-369: prob inherited from the bios!
I just install a new video card in my hp Pavilion 500-369 its r7 sapphire radeon 265 and a 600watts power when I turned on it beeps 6 times... and I tried all sorts of tricks to youtube... tried to change my bios in legacy mode but I can't find it... plss help
More recent versions of the UEFI suport Sapphire cards if it is stated in the specs on the website of the company. Perhaps you should consider returning and its replacement by a new PCIe card.
Here is the list of specifications to Sapphire in the link below. Notice that most of the R9 series supports UEFI. There is no map of R7 series made my Sapphire Tech who take care of UEFI.
The r7 Radeon 240 by Club3D, r7 Visiontek 250 FF, PowerColor R7 250 2 GB GDDR5 Eyefinity 4 LP Edition (UEFI) all supports UEFI.
-
Multicast over GRE tunnel traffic
Hi guys,.
I have a connection via ISP connection point to point BGP on a connection of 100 Mbps between the branch and the central office.
I set up in two cisco routers with ios security advance 2801 a tunnel WILL running the ospf Protocol so I can share the multicast traffic for streaming between the two sites, but I am only able to get 6 Mbps out of the tunnel between the sites. I have configured multicast PIM sparc-mode to transport video traffic above the tunnel.
Is there a limit on the GRE tunnel, could it be MTU, or perhaps other issues anyone can help me solve this question guys?
Hello
There is a lot of discussion about the limitations of bandwidth on the tunnel interface. But most of the discussions flow seems to be linked to the limitation of the software on the device.
Issues could be related to MTU. Have you enabled PMTUD on the tunnel interface? If this is not the case, turn it on, as it recommended on the tunnel interface.
HTH.
Evaluate the useful ticket.
Kind regards
Terence
-
Customer multicast via vpn traffic
Hi guys,.
Then. I have already created a vpn server on my router 878... while I can connect to this router and the network with ip - sec (cisco vpn client)...
Al works fine... but... when I also want to allow multicast on my vpn connection traffic. should I then a vpn free WILL? or what?
What is only necessary when you use a site to site vpn... ?
And how to activate it?
Thanksssss
There is no way we can send directly via remote access VPN tunnel multicast traffic.
-
Topic for sticky thread: Multicast
Hi all
I have just a question which is completely driving me crazy. I googled 50 + pages, I searched this whole forum, and after reading almost a hundred articles I can't find a 'factual' or 'Clear' answer to this question with the evidence:
On the NEW routers Linksys, such as the V1 WRT610N with latest firmware or the WRT310N V1.
"Security," there is the "Filter multicast" option
Should it be "Checked = Enabled" to BLOCK or ALLOW, through the network multicast traffic.
I ask, because apparently there was a lot of typo and the misconceptions, because the previous Linksys models such as the 2006 BEFSR41v4 router, was typoed: "Filter Multicast" was actually supposed to be "enable multicast Passthrough.
This still applies today, and with all other Linksys routers?
The reason is because it is grammatically incorrect and very misleading so it can be written as "Filter Multicast" because the word "Filter" means to remove this option by 'Vérification', you'd be 'Prevent' multicast traffic. That would make sense because all other options on the Security page, works this way.
However, from what I've seen, people have gotten mixed results and the conclusion is often to "Activate" "Filter multicast" to "Allow" traffic, but that makes no sense!
This is a VERY important subject, because it solved once and for all, put an end to tons of questions of others.
It comes
Xbox 360 games questions
Vista Media Extender
UPNP Gaming
PS3 network problems
Media sharing
Hello
IPTV
ITunes and many others.
Thank you all very much for any idea that you can provide, also if possible how can I test to make sure that it is indeed "allowing" multicast once understand us this?
Please help me answer this question once and for all...
When the option is enabled, "Filter Multicast" will filter multicast traffic, i.e. it does not.
When the option is disabled, the router will run the multicast daemon and it will deliver multicast traffic.
Most people see no difference, because they get all multicast traffic. I guess the most likely situation where you will see the multicast traffic is when you use your ISP's IPTV service. All general internet traffic will not be multicast and she will not even pass through your ISP network...
Maybe you are looking for
-
Recovery of a Satellite A100 (PSAA9) - deleted the partitions and XP Home no Pro
We have recently had trouble with our laptop and decided to restore the settings from the manufacturer with the recovery CD from Media. My son decided to do when he started the program, he chose the option to delete the partitions the crash Now, he h
-
Generation of a test without a module result
I have a fundamental question on the generation of a test result without calling a module in TestStand. For example, I have a pair of read of a product operations and digital to return the results of a pair of local variables. Now, I want to do a num
-
GetTableCellValue "the control is not of the type expected by the function.
I hope you can help me to find out why GetTableCellvalue is a failure.I don't get "the control is not of the type expected by the function.int calPanelId = LoadPanel (PARENT, "gui_main.uir", CAL_PANEL);Point p;p.x = 1;p.y = 1;Double val = - 1.0;State
-
Can someone please helpWhen playing a DVD on the computer, I get good Sound & picture on ajoining tv, I get a good quality image but no soundConcerningDarryl
-
HP Officejet 6000 e609a transport Jam
Hello. I use this printer-e609a via the local USB port on my 32-bit XP machine. Everything has been working great. The last time I went to print, was advising me of a paper jam. I have rempoved the paper tray and I checked carefully, and there is