RADIUS answer ise
No idea why I get this even if the clients are authenticated?

Edon,
I often see this when I test, if I start to dot1x and then I disconnect the port, the peap session is still active in the database of the ISE and then expires after 120 seconds. Usually, if users roam again with all groups of mobility, if happen them to wander from one controller to another, you could wait this behavior if the customer happens to be associate with that time here.
Thank you
Tarik Admani
* Please note the useful messages *.
Tags: Cisco Security
Similar Questions
-
Authentication RADIUS with ISE - a wrong IP address
Hello
We use ISE for radius authentication. I have setup a new Cisco switch stack to one of our branches and set up the device network in ISE. Unfortunately, in trying to authenticate, ISE logs show a lack of "Impossible to locate device network or Client AAA" the reason for this failure is that the log shows that it comes from a bad IP address. The IP address of the switch is 10.xxx.aaa.241, but the logs show that it is 10.xxx.aaa.243. I removed and added the configs of RADIUS on ISE and the switch, but it is always so que.243. There is another switch battery location (same model, IOS etc), which works correctly.
The config of RADIUS on the switch:
AAA new-model
!
!
AAA authentication login default local
AAA authentication login Comm group local RADIUS
the AAA authentication enable default
RADIUS group AAA authorization exec default authenticated ifradius of the IP source-interface Vlanyy
10.xxx.yyy.zzz RADIUS server
10.xxx.yyy.zzz auth-port 1812 acct-port 1813 ipv4 address
abcdefg 7 keyThe journal of ISE:
Overview
5405 RAY lost event
Username
ID of the endpoint
Profile of endpoint
The authorization profileDetails of authentication
Source Timestamp 2014-07-30 08:48:51.923
Receipt 08:48:51.923 Timestamp 2014-07-30
Policy Server ise
5405 RAY lost event
11007 failure reason could not locate device network or Client AAA
Resolution check if the device network or AAA client is configured in: Administration > network resources > network devices
Root cause could not find the network device or the AAA Client while accessing NAS by IP during authentication.
Username
Type of user
ID of the endpoint
Profile of endpoint
IP address
Identity store
Membership group
ID of Session verification
Authentication method
Authentication Protocol
Type of service
Network device
Type of device
Location
10.xxx.AAA.243 address IP NAS
ID of Port NAS tty2
Virtual NAS Port Type
The authorization profile
Status of the posture
Security group
Response timeOther attributes
ConfigVersionId 107
Device port 1645
DestinationPort 1812
Radius protocol
NAS-Port 2
AcsSessionID ise1/186896437/1172639
IP address of the device 10.xxx.aaa.243
CiscoAVPairMeasures
Request for access received RADIUS 11001
11017 RADIUS creates a new session
11007 could locate no device network or Client AAA
5405As a test, I set up a device that uses the adresse.243. While ISE claims that it authenticates, it really doesn't. I have to use my local account to access the device.
Any advice on how to solve this problem would be appreciated. Please let me know if you need more information.
Beth
Remove your (RADIUS-server host 10.x.x.x... ect) tele-health and try this command and see if the problem goes away. The new section is the non-standard expression allows to see if that helps.
RADIUS-server host non-standard key of acct-port of the auth-port 1645 10.xxx.xxx.xxx 1646 *.
-
Impossible to use ad groups for authentication RADIUS on ISE 2.0
I tried following the guide on how to configure ISE 2.0 for peripheral administration GANYMEDE and when I get to the ensembles 'political device admin' the only thing that I can use identiity default user groups there. It won't let me choose an ad group. Even if I create a group of identity I'm unable to map a group of ads to it. Am I missing something here?
Make sure that you use the box of 3 (left to right) when your state of construction based on ad groups. The 2nd box only searches the internal identity store. Then you will need to click on the 3rd box > create new Condition > Select attribute > AD1 (or whatever you named your connection AD) > external groups
I hope this helps!
Thank you for evaluating useful messages!
-
ASA college level of RADIUS (Cisco ISE)
Dear,
I have treid to authenticate access management ASA of ISE and it works fine, when I tried to push private level 15 to him even in private 1.
I am using my version, Cisco-AV-pair attribute ASA 9.0
Thank you
Even if you press on cisco-av-pair attribute as shell: priv-lvl = 15 ASA, it won't allow you to land directly on the privileged exec mode. You supply enable password until you get # mode.
https://supportforums.Cisco.com/thread/2201512
Let me know if you have any other requirement.
~ BR
Jatin kone* Does the rate of useful messages *.
-
ISE device administration authentication Radius possible?
Hello
does anyone know if the edge RADIUS authentication and authorization administration is possible with the actual release of ISE? I know that GANYMEDE will be available in future releases.
Concerning
Joerg
Yes it is possible according to the "Ask the experts" forum
--------------------------
https://supportforums.Cisco.com/thread/2172532
"If you use RADIUS for the administration of the system, ISE can be used using authorization policy elements that return Cisco av-pairs." But personally, I think that ACS is currently superior to ISE for this task. »
--------------------------
In any case, I'm about to test "device admin" and "network access" at the same time in the same switch with Radius and ISE.
Please rate if this can help
-
ISE IOS CLI authentication Quandry
Im trying to push the limits of the ISE, as Ganymede + is not yet supported. The goal is to authenticate the switches and routers using RADIUS against ISE. I think I'm on the right track, since I can connect against ISE. However, when I login to activate the journal of ISE permissions shows lack of status of RADIUS, with an attempt failed to use $enabl15$.
I have my unit added to ISE. An authorization profile has been created for each privilege level, I use strategy games and have the correct authz and the autht policies. Some examples of my configuration of ISE and configuration of the router. I hope that helps to solve my problem, or it can help the next troll successfully their own configuration.
Profile of AUTH: When you choose priv-lvl = 15 after hitting save, web auth is automatically selected.

Strategy game:
the router configuration
RADIUS AAA server group Rad_AUTH1
name of the server Rad_Auth
!
local authentication AAA CONSOLE connection
AAA authentication login Rad_Auth group local Rad_AUTH1 no
Group AAA authentication enable default Rad_AUTH1 allow none
default AAA authorization exec no
Group AAA authorization exec Rad_Auth if authenticated Rad_AUTH1
start-stop radius group AAA accounting exec by default
!Server RADIUS Rad_Auth
ipv4 x.x.x.x address auth-1645 acct-port of 1646
timeout 3
touch 7 052F302B3B7E491B41line vty 0 4
session-timeout 30
exec-timeout 30 0
exec authorization Rad_Auth
authentication of the connection Rad_Auth
entry ssh transportGlad that you got your own problem solved! Also, thank you for taking the time to come back and post the solution here! (+ 5 from me).
Given that the problem is resolved you must mark the thread as "answered" :)
-
ISE node failure & pre authorization ACL
Hi all
I would like to know who, in what should be the best practice for the following configuration.
(1) access for devices/end users network if both nodes ISE become inaccessible? How we can ensure that full network access should be granted if the two ISE nodes become unavailable.
(2) what is the best practice for setting up pre authorization ACL if IP phones are also in the network?
Here is the configuration of the port and the pre authorization ACL which I use in my network,
Interface Fa0/1
switchport access vlan 30
switchport mode access
switchport voice vlan 40
IP access-group ISE-ACL-DEFAULT in
authentication event failure action allow vlan 30
action of death event authentication server allow vlan 30
living action of the server reset the authentication event
multi-domain of host-mode authentication
open authentication
authentication order dot1x mab
authentication priority dot1x mab
Auto control of the port of authentication
periodic authentication
Server to authenticate again authentication timer
protect the violation of authentication
MAB
dot1x EAP authenticator
dot1x tx-period 5
*****************************************
IP access-list extended by DEFAULT ACL - ISE
Note DHCP
allow udp any eq bootpc any eq bootps
Note DNS and domain controllers
IP enable any host 172.22.35.11
IP enable any host 172.22.35.12
Notice Ping
allow icmp a whole
Note PXE / TFTP
allow udp any any eq tftp
Note all refuse
deny ip any any newspaper
Thank you best regards &,.
Guelma
Hello
On question 1, since you use 'authentication mode host multi-domain' then "action dead event server authentication allows vlan X" is the way to go.
But if you use "authentication host-mode multi-auth" then you should use "action death event authentication server reset vlan X"
On question 2, it is not mandatory to use pre permission ACL. My current deployment have IP phones, since I use the profiling and CDP RADIUS then ISE can detect and allow the IP phones, even if the switch blocks all packets. "Why I didn't need pre-authorization ACL.
Please rate if this can help.
-
ISE Posture Windows enter password to view the desktop very slow
Hello, had a problem of slowness that I don't know how to solve problems. ISE 2.0 patch3, AnyConnect 4.3.02
My setup is Anyconnect which is already on the computer windows laptop 10, EAP with TLS chaining for authentication of the host and PEAP for user auth. ISE Posture checks for windows AV defs and AV windows install. AnyConnect has 'start before logon' installed and * just work *. Boots of the user, auths from the machine before the connection of the user, user logs in and ISE Posture check runs and passes. The user gets the green checkmark on the line.
With a little problem. At the time wherever the user types the password and hit enter, the grip of the Welcome screen for about 45 to 60 seconds, a few rare occasions longer, my high water line is 1 minute 12 seconds. Meanwhile machine auth and auth user spend with the unknown state of compliance in the live of the radius of ISE log. Then welcome screen disappears and the bureau paints (finally), at this time, the machine cannot access anything on the network, 5 seconds later the Anyconnect client starts. 1 second later the bumps network connection, and the analysis of the Posture of ISE in the Anyconnect client starts. Analysis of the Posture of the ISE takes about 7-10 seconds to complete. After that everything is good and the user can access the network.
If control of Posture of ISE is deleted, the whole process takes 10-15 seconds password entry the user to be able to use the laptop and access the internet.
Does anyone have an idea whence this 'start delay '? Feels like a timeout of some sort. It happened on this latest version of the Anyconnect and 3 previous ones as well. I concentrate on my test machine windows 10 laptop, but the same thing happened on 4 other test systems which are a mixture of windows 7, 8.1 and 10. The 10 win test system is a lenovo x 1 carbon with an SSD and is normally fairly quick.
All the tips are greatly appreciated.
e-
Do you have the port in a vlan to auth machine and then change once the machine and the user connects? Also, you will probably need to open any acl you apply while the posture is 'unknown '. It is usually due to some AD access that is blocked.
-
The ID attribute of the station call needs for Anyconnect VPN client MAC address
Hi all
We test tring Anyconnect VPN users to connect using the certificate. ASA East of validation / authentication user based on cert and approval it requires Radius server (ISE). Currently ASA sends the Ip address of the VPN client in «calling station ID» We want ASA to send the Anyconnect VPN client MAC address to the radius server in RADIUS attribute «calling station ID» Is it possible to do this. Get around them?
Parag salvation,
The calling Station ID always contains the IP if Anyconnect VPN.
L3 is originally unlike wireless which has L2 Assoc.
Currently no work around.
Respect of
Ed
-
Cisco ISE: External RADIUS server
Hello
I send RADIUS of NHP NHP, another. I have already defined "External RADIUS servers".
So, how can I use this external RADIUS server to process my application?
Looking at the user guide, but did not find information on this parameter (for the rule after rule not simple)
Cela if anyone use this, please suggest me.
Thank you
Mathias
Please specify which version you are using. There were improvements to the functionality of the proxy in ISE 1.1.1
This can be used as follows:
-Define "External RADIUS server"
-Set the "Sequence of RADIUS server. This allows you to define a sequence of proxies that will send queries to until you get an answer
-In the authentication policy when the rules instead of the allowed protocols can select a "RADIUS server Sequence.
-
Salvation of the Forumers
I am looking for some answer about ISE profiling.
I could use ISE to test 802.1 x wireless connection to Active Directory external identity store.
Sort of ISE, after enable profiling on deployment nodes configuration, as long as the device with appropriate authentication and enter the network will then showed all MAC addresses found on the identity management > identity > endpoints
My question is:
01 can authentication 802. 1 x i made without using the identity outside stores? So far I have only test on the use of Active Directory, but not with the ISE identities > users.
02 if, in an environment that doesn't use not external identity stores for authentication, how I got to know the MAC address belongs to WHO?
Thank you
WPA - PSK ends on the drive, there is no RADIUS because the key must match on the client and the controller. It is not a Yes or a no to this question because the design of WPA - PSK is not utiilize a back-end service.
-
ISE Sponsor authentication via RADIUS
My client demand change us the way the sponsor users are authenticated and authorized to access portal Sponsor of ISE.
Their similar to the request of the ISE AD via a RADIUS server first. They said "avoid sending credentials of the AD to ISE directly. Under this condition,.
My research and limited knowledge give to assume I have to define a RADIUS Proxy
I think I can define an external RADIUS server, but I wonder if this creation, it would be available as a Source of identity for "portal Sponsor sequence.
If this is not the case, how can I add this? After that, what conditions or attributes should I look for to use in the 'strategy of group sponsor' in order to filter the name of user and password and allow access to employees and deny access to everyone?
I'd appreciate advice that you can give me to offer the best recommendation to the client.
Kind regards.
Daniel Escalante.
Hi sliman,.
Unfortunately, this document is not relevant to what Daniel is trying to achieve. There need to be able to refer to a RADIUS server as part of the Sponsor authentication process, that is not possible today. The only possibilities are that I have indicated in my original answer.
Richard
-
Hello!!
We are working on a mapping between a promoter Cisco ISE group and a user group in Active Directory, but the customer wants the mapping through a RADIUS SERVER, to avoid the ISE by querying directly activate Directory.
I know it is possible to use a RADIUS SERVER as source of external identity for ISE... but, is possible to use this RADIUS SERVER for this sponsor group manages?
Thank you and best regards!
Hi Rodrigo,
The answer is no. There is no way to integrate the portal Sponsor config with a RADIUS server. Your DB for authentication Portal Sponsor options;
AD
LDAP
User internal ISE DBSent by Cisco Support technique iPhone App
-
Cisco ISE with GANYMEDE + and RADIUS both?
Hello
I'm wired opening of authentication on a network using Cisco ISE. I studied the conditions for this. I know that I need to enable the RADIUS on the Cisco switches on the network. The switches in the network are already programmed to GANYMEDE +. Anyone know if they can both operate on the same network at the same time?
Bob
I suppose that Ganymede is configured (with ACS 4.x or 5.x) for the peripheral administration via telnet/ssh, and now you need the RADIUS (radius) to authenticate 802. 1 x. Yes they can both work on the same network at the same time.
~ BR
Jatin kone* Does the rate of useful messages *.
-
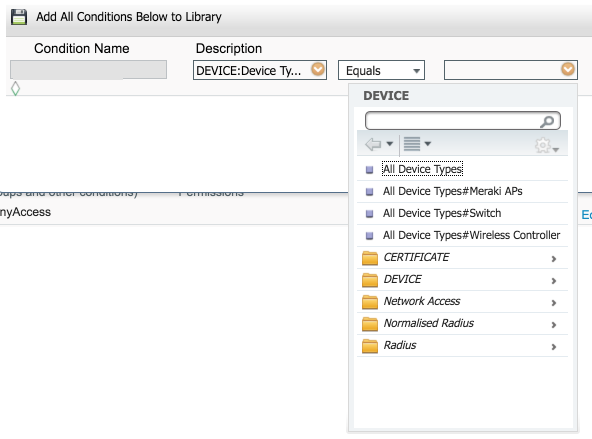
I am very new to Cisco ISE and Meraki. I try to get the Radius configuration for wireless authentication. When I do a test of the Meraki to ISE, it passes.
When I try to connect from my laptop, I look at the logs of the Radius and it passes; However, it does not connect me to good policy. I keep hitting the default policy. I have my Meraki police above the default policy in the strategy defined in article. I have attached what looks like my strategy game.
Devices does not really matter. Here is what I see when I create a device group (where you add the access point to this group), and then create the condition:
And here is where I create the condition of strategy game and you should be able to select the Meraki access points:
This will give you the condition similar to what I posted above. This is perhaps why you aren't hit that is not matching the condition for this game.
Maybe you are looking for
-
I forgot my master password. I used the address provided to reset. He takes me to the page that tells me that all passwords will be forgotten and gives the possibility to RESET or CANCEL. I try choosing RESET and nothing happens. What am I doing here
-
Better graphics for HP Pavilion Elite HPE-570f card
I have the Pavilion Elite HPE-570f (BV542AA) Windows 7 ultimate with 16 GB of ram upgraded and an upgrade HARD drive with 7200 RPM. The P/S is a 460w and ATI Radeon HD 6770 with only 1Gig vram. I would like to upgrade the video card up without comper
-
Windows media player will not install due to incompatibility of the language.
I have windows XP sp3 and when I tried to update my Windows Media Player (WMP), I first installed the wrong language. So I downloaded the English version which indicated to me, due to a mismatch of language, uninstall current WMP to procceed. so I us
-
I can't connect to the Internet via a modem USB Bandluxe!
Hello, everyone. I have Win 7 Home premium. And my problem with usb (BandLuxe) modem connection.The problem is when I try to connect to the internet using the BandLuxe software, it should take for a while thenI get the message that failed and has NO:
-
Hallo, the forum is full of questions similar to mine and everything seems complete without useful answers some time early last year. I would like to give a try today to see if I get a solution. Have Windows 7 Enterprise 64 bit and installed XP mode