Disater recovery site main VPN, OSPF
I am trying to find a solution for our site recovery. We have 13 websites with VPN tunnles back to the main site with OSPF and GRE tunnels for routing. I need to make a site separate from the main site mirror (ip addresses, VIRTUAL LANs, etc.). How can I switch the VPN sites on the site automatically using the GRE and OSPF network disaster recovery using the same model of IP address?
The stateless failover is used when primary network edge platform fails, IPsec sessions can failover and reconnect to the edge network backup platform, thereby reducing downtime of connection.
Tags: Cisco Security
Similar Questions
-
Recovery site - redundant VPN peers
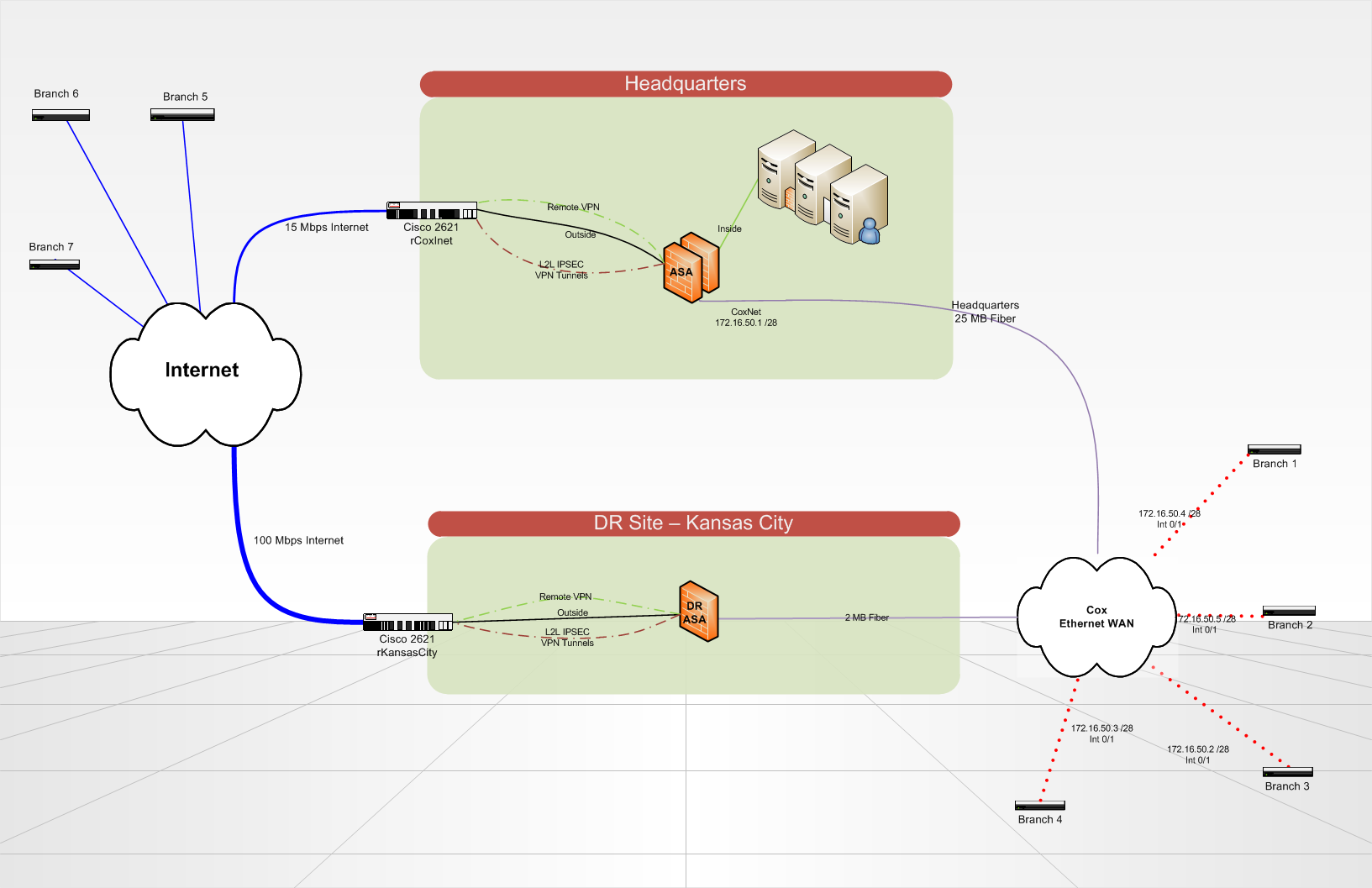
Hello all, thank you in advance for your expertise.
We put in place a recovery site disaster that will host the redundant copies of our servers and critical data in Kansas City. When disaster strikes, our headquarters site would be totally gone.
We currently have 7 locations that communicate to our HQ via VPN tunnels (whether on a circuit of the Internet or on a circuit of Cox Communications Ethernet WAN). Branch sites each can an ISR of Cisco 2821 router. At Headquarters and on the DR site, we use a Cisco ASA 5510 to terminate VPN tunnels and do everything that our column spinal routing. Routing on the ASA and branch routers is all static, using a routing protocol would be a nice update in the future... any ideas? We use IPSEC VPN lan lan tunnels 2, no GRE/VPN is used because it is not terminated by the ASA.
What is the best way to configure my routers for branch to automatically or manually failover to connect to one ASA different site of DR?
In addition, if my seat is still in place, but either my Internet or Cox headquarters ethernet circuit breaks down. How can I re - route all traffic in a loop to the seat on the right remains a circuit?
Is there a better way to do what I want to accomplish? BGP is not an option at this point due to its complexity.
Lucas,
To circumvent the two point separately.
The best way to provide active / standby time of reundancy is preferred peer in cryptographic cards (on the ISR routers).
You can choose to establish VPN to HQ and only if HQ is not aid you to DR, when HQ is you will EVENTUALLY return to it.
The answer to share of your questions may also be the preferred option by peers (and several counterparts in a crypto map entry).
This being said, you can try to send OSPF traffic to IPsec tunnel (and using the neighbor command to avoid the manipulation of mcast in pure IPsec).
Docs:
HTH,
Marcin
P. S.
If you want my personal opion, chaning ASAs in HQ and DR sites and put you in routers could make DMVPN or DVTI-ASIT scenario which gives you a lot more features ;-)
-
Hi, I currently have a site to site vpn upward and running and it works fine. I try to put the other two online and just cannot make them work. I used the same configuration of one operation but I cannot get the next tunnel. I saw several errors when debugging isakmp and ipsec and they are at the end of my configs. Anyone have any ideas? Thank you
Main site - a vpn clients connecting too it and pt to pt vpn to 3 endpoints
Cisco PIX Firewall Version 6.3 (3)
* Main Site Config *.
client_vpn 10.10.0.0 ip access list allow 255.255.0.0 192.168.0.0 255.255.255.0
VPN_to_Site2 10.10.0.0 ip access list allow 255.255.0.0 192.168.0.0 255.255.255.0
NAT (inside) 0-list of access client_vpn
Permitted connection ipsec sysopt
Crypto ipsec transform-set esp-3des esp-md5-hmac fws_encry_set
outside_map 60 ipsec-isakmp crypto map
address for correspondence card crypto outside_map 60 VPN_to_Site2
crypto outside_map 60 peer 64.X.X.19 card game
card crypto outside_map 60 transform-set fws_encry_set
outside_map interface card crypto outside
ISAKMP allows outside
ISAKMP key * address 64.X.X.19 netmask 255.255.255.255 No.-xauth-no-config-mode
ISAKMP identity address
ISAKMP nat-traversal 20
part of pre authentication ISAKMP policy 10
ISAKMP policy 10 3des encryption
ISAKMP policy 10 md5 hash
10 2 ISAKMP policy group
ISAKMP life duration strategy 10 86400
Site 2 config
* only because the pt to pt does not work I have it set up to allow vpn clients to cross to connect to the main site.
Cisco PIX Firewall Version 6.3 (5) *.
permit access ip 192.168.0.0 list VPN_to_Main 255.255.255.0 10.10.0.0 255.255.0.0
NAT (inside) 0-list of access VPN_to_Main
Permitted connection ipsec sysopt
Crypto ipsec transform-set esp-3des esp-md5-hmac fws_encry_set
outside_map 10 ipsec-isakmp crypto map
outside_map card crypto 10 corresponds to the address VPN_to_Main
crypto outside_map 10 peer 207.X.X.13 card game
card crypto outside_map 10 transform-set fws_encry_set
outside_map interface card crypto outside
ISAKMP allows outside
ISAKMP key * address 207.X.X.13 netmask 255.255.255.255 No.-xauth-no-config-mode
ISAKMP identity address
ISAKMP nat-traversal 20
part of pre authentication ISAKMP policy 10
ISAKMP policy 10 3des encryption
ISAKMP policy 10 md5 hash
10 2 ISAKMP policy group
ISAKMP life duration strategy 10 86400
Errors
PIX (config) # IPSEC (sa_initiate): ACL = deny; No its created
authenticator is HMAC-MD5IPSEC (validate_proposal): invalid local address
I have a link that works very well. I have copied the config from there, changed the ip info and it does not work. The only differences in the configs are no sysopt route dnat and it's on Version 6.2 (2)
IPSec (sa_initiate): ACL = deny; No its created
I think that you have configured a VPN tunnel without removing the cryptographic card of the external interface. The message above is the error we get in such situation.
I suggest the following solution:
-remove the external interface (the two pix) cryptographic card
-Cree claire isa his and trendy clear ipsec his (the two pix)
-Reapply the card encryption on external interfaces.
If this doesn't solve the problem, restart the equipment.
Kind regards
Ajit
-
RAC replication environment in a disaster recovery Site
Hi all, in my environment I must reproduce the main site on a recovery site disaster. I use the network at high speed between the two sites and the data on file systems shared on two of SEM (one on the primary) and one on the site of the disaster related synchronously.
My environment's RAC ORACLE 11 g 2, with AIX 6.1 and clusters of twins between the primary recovery and disaster sites.
Recovery site servers have IP addresses and different IP names and names of main site.
I mean, I installed my first ORACLE RAC, but I don't know how to install ORACLE RAC in the Dr site after a disaster.
I have a few questions:
(1) how should install ORACLE RAC in the recovering site, based on SAN storage that is constantly in overrided by replication of the primary storage to the storage of physical recovery? of course, the recovering site, ORACLE RAC is usually kept off-line, but I don't know how to organize the alignment between the two (primary and recovery) ORACLE environments and how to make the process of taking control.
Please, can you tell me?
Thank you
MarcoHi Marco,.
I think you should be able to start.Have you implemented this or being implemented?
I don't know about the behavior of replication SAN disk OCR/vote. But we use it for the database unique instance and it works fine.
I also suggest you open SR with oracle support on this subject.
Concerning
Rajesh -
Using Hotmail, how to change the recovery of main mobile phone account is linked to a mobile phone that is no longer in use.
I can't remove it, I can't change it or do anything else without the system you want to send a text message for that phone for conformation. can you change the setting to send an email to the place or the main number of conformation ahange.
Steve
Hello
The question you have posted is related to hotmail; This is why it would be better suited in the Windows Live community. Please visit the link below to find a community that will provide the best support.
-
How to get the ID of externsión SRM in an environment shared recovery sites
I am setting up a new site and I want to get this protected site and point to the existing shared recovery site.
I have no idea what is the ID extension SRM used the previous seller
Is anyway to extract the extension of MRS. ID?
Connect to the SRM at-> Solutions and Applications, go to the Sites-> Summary tab and you will see the ID of SRM as in this picture:
-
Protection and recovery Site ESX versions
All,
Not sure if this has been asked before, but is there a compatibility issue if my protected site is running vCenter 4.1, ESXi 4.1, 4.1.1 SRM and my recovery site is running vCenter 4.1, ESX 4.0 Update1 and SRM 4.1.1? Basically it is based, and I will have issues if my ESX version is higher on the protected site.
Thank you!
Hello
Although it is important to keep all versions ESX and vCenter the same, the difference in ESX versions directly will not affect SRM or the recovering site as long as controllers (vCenter) are the same at all levels. Most of that depends on SRM is databases.
-rp
-
Question of shared recovery Site
Here's my scenario. I need to test VMware View and SRM. I plan to use scripts provided by EMC to help with view and SRM because the view was not really made to be able to test in a DR scenario.
I have two vCenters in a production data center. One is used for my normal "servers" and is vCenter 4.1 x 64. The other vCenter is used for VMware View host computers, I have this vCenter (called "VDI") because I use View Composer and it is not compatible with x 64 servers.
On the site of DR, I have a vCenter. It is currently running vCenter 4.0. Now, I know that I can have a shared with MRS recovery site, but virtual machines can also be shared?
For example, should I perform a test of SRM which includes a production vCenter my "Server" domain controller and also include the view virtual machines that are part of the other 'VDI' vCenter in my production?
Thank you!
First of all, what version of MRS. you plan to use? You mentioned the two vCenter 4.1 and 4.0. SRM 4.1 is not compatible with vCenter 4.0 and SRM 4.0.x is not compatible with vCenter 4.1 (SRM versions must be the same at all sites).
Regarding your question, I have not implemented recovery shared functionality, but as far as I know, even in this configuration you can still pair site independently, i.e. protected satellite site SRM and SRM instance of its corresponding recoverysite instance. So I don't think that the associations for the Protection of several sites will be available to include in the unique recovery plan.
Please correct me if I'm wrong.
Michael
-
We can point out 2 sites main site recovery
Hello
I've already matched 2 vCenter servers and it works very well with all the rehearsals. We can point to a different primary site (3rd vCenter) the former site of recovery even?
Basically, I have only 1 site recovery with 2 main sites. How to handle this scenario?
Kind regards
Isabelle
Good luck Shivaji.
Please mark my okay if you are satisfied with the answer.
-
Another scenario of test - isolate the recovery Site
Question for the gurus out there:
Installation: We have a simple configuration with a single restore site protected and unique. The configuration of the network is stretched VLAN. All the tests to bubble networks works as advertised, and we are very pleased with the solution so far. In addition to virtual infrastructure, there is a certain physical systems that make up the environment, and the goal is to make a complete failure on the test of the site in the coming weeks.
Test case: the proposed solution is to drop the link between sites protected-recovery and turn the entire failover datacenter in a bubble (only accessible through VPN links). Once the test is completed, we would have back then all the changes on the recovering site, so that it protects once more the main site.
Question: Would it be possible to rotate part SRM to the test in 'Test' mode only - that she set up the whole environment attached to the VLAN direct (who are now isolated from production by dropping the link of the site) and once finished, reset the recovery by the normal site (i.e. "Test recovery finished, press on continue clean...") ») ? I don't see why it wouldn't work, unless for some reason, the test procedure requires communication between the sites that the effective recovery process does not.
Thanks for any comments.
Hello
Recovery test requires no connection to the protected site as far as I know.
About the networking part of your question, when you change a recovery plan, on the network management screen you have an option to configure the test networks. These networks is used during the trial instead of bubble networks (default).
SRM will be cleaning the virtual environment, but how do you cleaning physical servers?
For how long you plan to run on the recovering site? You have sufficient capacity for snapshots on your storage array?
Michael.
-
Hey all, I was instructed to set up a tunnel vpn site-to-site between 2 offices. I think I have everything configured correctly for the most part, but when I generate a valuable traffic, tunnel does. Can you tell me to look at the debug output below what could be the problem? Aaa.aaa.aaa.aaa my IP address and the IP address of my counterpart is bbb.bbb.bbb.bbb
ROUTER #.
* 27 Feb 14:41:30.677: IPSEC (sa_request):,.
(Eng. msg key.) Local OUTGOING = aaa.aaa.aaa.aaa:500, distance = bbb.bbb.bbb.bbb:500,
local_proxy = 172.18.230.0/255.255.255.0/0/0 (type = 4),
remote_proxy = 192.168.230.0/255.255.255.0/0/0 (type = 4),
Protocol = ESP, transform = esp - aes esp-sha-hmac (Tunnel),
lifedur = Ko 86400 s and 4608000,
SPI = 0 x 0 (0), id_conn = 0, keysize = 128, flags = 0 x 0
* 14:41:30.677 Feb 27: ISAKMP: 500 local port, remote port 500
* 14:41:30.677 Feb 27: ISAKMP: set new node 0 to QM_IDLE
* 14:41:30.677 Feb 27: ISAKMP: (0): insert his with his 4BA8CE24 = success
* 14:41:30.677 Feb 27: ISAKMP: (0): cannot start aggressive mode, try the main mode.
* 14:41:30.677 Feb 27: ISAKMP: (0): pair found pre-shared key matching bbb.bbb.bbb.bbb
* 27 Feb 14:41:30.677: ISAKMP: (0): built of NAT - T of the seller-rfc3947 ID
* 27 Feb 14:41:30.677: ISAKMP: (0): built the seller-07 ID NAT - t
* 27 Feb 14:41:30.677: ISAKMP: (0): built of NAT - T of the seller-03 ID
* 27 Feb 14:41:30.677: ISAKMP: (0): built the seller-02 ID NAT - t
* 14:41:30.677 Feb 27: ISAKMP: (0): entry = IKE_MESG_FROM_IPSEC, IKE_SA_REQ_MM
* 14:41:30.677 Feb 27: ISAKMP: (0): former State = new State IKE_READY = IKE_I_MM1
* 27 Feb 14:41:30.677: ISAKMP: (0): Beginner Main Mode Exchange
* 27 Feb 14:41:30.677: ISAKMP: (0): package bbb.bbb.bbb.bbb my_port 500 peer_port 500 (I) sending MM_NO_STATE
* 14:41:30.677 Feb 27: ISAKMP: (0): sending a packet IPv4 IKE.
* 14:41:30.713 Feb 27: ISAKMP (0): packet received dport 500 sport Global 500 (I) MM_NO_STATE bbb.bbb.bbb.bbb
* 14:41:30.713 Feb 27: ISAKMP: (0): entry = IKE_MESG_FROM_PEER, IKE_MM_EXCH
* 14:41:30.713 Feb 27: ISAKMP: (0): former State = new State IKE_I_MM1 = IKE_I_MM2
* 27 Feb 14:41:30.713: ISAKMP: (0): treatment ITS payload. Message ID = 0
* 27 Feb 14:41:30.713: ISAKMP: (0): load useful vendor id of treatment
* 27 Feb 14:41:30.713: ISAKMP: (0): provider ID seems the unit/DPD but major incompatibility of 123
* 27 Feb 14:41:30.713: ISAKMP: (0): provider ID is NAT - T v2
* 27 Feb 14:41:30.713: ISAKMP: (0): load useful vendor id of treatment
* 27 Feb 14:41:30.713: ISAKMP: (0): IKE frag vendor processing id payload
* 14:41:30.717 Feb 27: ISAKMP: (0): IKE Fragmentation support not enabled
* 14:41:30.717 Feb 27: ISAKMP: (0): pair found pre-shared key matching bbb.bbb.bbb.bbb
* 27 Feb 14:41:30.717: ISAKMP: (0): pre-shared key local found
* 27 Feb 14:41:30.717: ISAKMP: (0): pre-shared xauth authentication
* 14:41:30.717 Feb 27: ISAKMP: (0): audit ISAKMP transform 3 against the policy of priority 10
* 14:41:30.717 Feb 27: ISAKMP: 3DES-CBC encryption
* 14:41:30.717 Feb 27: ISAKMP: SHA hash
* 14:41:30.717 Feb 27: ISAKMP: group by default 2
* 14:41:30.717 Feb 27: ISAKMP: pre-shared key auth
* 14:41:30.717 Feb 27: ISAKMP: type of life in seconds
* 14:41:30.717 Feb 27: ISAKMP: life (IPV) 0 x 0 0 x 1 0 x 51 0x80
* 14:41:30.717 Feb 27: ISAKMP: (0): offered hash algorithm does not match policy.
* 14:41:30.717 Feb 27: ISAKMP: (0): atts are not acceptable. Next payload is 0
* 14:41:30.717 Feb 27: ISAKMP: (0): audit ISAKMP transform 3 against the policy of priority 15
* 14:41:30.717 Feb 27: ISAKMP: 3DES-CBC encryption
* 14:41:30.717 Feb 27: ISAKMP: SHA hash
* 14:41:30.717 Feb 27: ISAKMP: group by default 2
* 14:41:30.717 Feb 27: ISAKMP: pre-shared key auth
* 14:41:30.717 Feb 27: ISAKMP: type of life in seconds
* 14:41:30.717 Feb 27: ISAKMP: life (IPV) 0 x 0 0 x 1 0 x 51 0x80
* 14:41:30.717 Feb 27: ISAKMP: (0): free encryption algorithm does not match policy.
* 14:41:30.717 Feb 27: ISAKMP: (0): atts are not acceptable. Next payload is 0
* 14:41:30.717 Feb 27: ISAKMP: (0): audit ISAKMP transform 3 against priority policy 20
* 14:41:30.717 Feb 27: ISAKMP: 3DES-CBC encryption
* 14:41:30.717 Feb 27: ISAKMP: SHA hash
* 14:41:30.717 Feb 27: ISAKMP: group by default 2
* 14:41:30.717 Feb 27: ISAKMP: pre-shared key auth
* 14:41:30.717 Feb 27: ISAKMP: type of life in seconds
* 14:41:30.717 Feb 27: ISAKMP: life (IPV) 0 x 0 0 x 1 0 x 51 0x80
* 14:41:30.717 Feb 27: ISAKMP: (0): atts are acceptable. Next payload is 0
* 14:41:30.717 Feb 27: ISAKMP: (0): Acceptable atts: real life: 0
* 14:41:30.717 Feb 27: ISAKMP: (0): Acceptable atts:life: 0
* 14:41:30.717 Feb 27: ISAKMP: (0): fill atts in his vpi_length:4
* 14:41:30.717 Feb 27: ISAKMP: (0): fill atts in his life_in_seconds:86400
* 14:41:30.717 Feb 27: ISAKMP: (0): return real life: 86400
* 14:41:30.717 Feb 27: ISAKMP: (0): timer life Started: 86400.
* 27 Feb 14:41:30.717: ISAKMP: (0): load useful vendor id of treatment
* 27 Feb 14:41:30.717: ISAKMP: (0): provider ID seems the unit/DPD but major incompatibility of 123
* 27 Feb 14:41:30.717: ISAKMP: (0): provider ID is NAT - T v2
* 27 Feb 14:41:30.717: ISAKMP: (0): load useful vendor id of treatment
* 27 Feb 14:41:30.717: ISAKMP: (0): IKE frag vendor processing id payload
* 14:41:30.717 Feb 27: ISAKMP: (0): IKE Fragmentation support not enabled
* 14:41:30.717 Feb 27: ISAKMP: (0): entry = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
* 14:41:30.717 Feb 27: ISAKMP: (0): former State = new State IKE_I_MM2 = IKE_I_MM2
* 27 Feb 14:41:30.717: ISAKMP: (0): package bbb.bbb.bbb.bbb my_port 500 peer_port 500 (I) sending MM_SA_SETUP
* 14:41:30.717 Feb 27: ISAKMP: (0): sending a packet IPv4 IKE.
* 14:41:30.721 Feb 27: ISAKMP: (0): entry = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
* 14:41:30.721 Feb 27: ISAKMP: (0): former State = new State IKE_I_MM2 = IKE_I_MM3
* 14:41:30.753 Feb 27: ISAKMP (0): packet received dport 500 sport Global 500 (I) MM_SA_SETUP bbb.bbb.bbb.bbb
* 14:41:30.753 Feb 27: ISAKMP: (0): entry = IKE_MESG_FROM_PEER, IKE_MM_EXCH
* 14:41:30.753 Feb 27: ISAKMP: (0): former State = new State IKE_I_MM3 = IKE_I_MM4
* 27 Feb 14:41:30.757: ISAKMP: (0): processing KE payload. Message ID = 0
* 27 Feb 14:41:30.789: ISAKMP: (0): processing NONCE payload. Message ID = 0
* 14:41:30.789 Feb 27: ISAKMP: (0): pair found pre-shared key matching bbb.bbb.bbb.bbb
* 27 Feb 14:41:30.789: ISAKMP: (1640): load useful vendor id of treatment
* 27 Feb 14:41:30.789: ISAKMP: (1640): provider ID is the unit
* 27 Feb 14:41:30.789: ISAKMP: (1640): load useful vendor id of treatment
* 27 Feb 14:41:30.789: ISAKMP: (1640): provider ID seems the unit/DPD but major incompatibility of 193
* 27 Feb 14:41:30.789: ISAKMP: (1640): provider ID is XAUTH
* 27 Feb 14:41:30.789: ISAKMP: (1640): load useful vendor id of treatment
* 27 Feb 14:41:30.789: ISAKMP: (1640): addressing another box of IOS!
* 27 Feb 14:41:30.789: ISAKMP: (1640): load useful vendor id of treatment
* 14:41:30.789 Feb 27: ISAKMP: (1640): vendor ID seems the unit/DPD but hash mismatch
* 14:41:30.789 Feb 27: ISAKMP: receives the payload type 20
* 14:41:30.789 Feb 27: ISAKMP (1640): sound not hash no match - this node outside NAT
* 14:41:30.789 Feb 27: ISAKMP: receives the payload type 20
* 14:41:30.789 Feb 27: ISAKMP (1640): No. NAT found for oneself or peer
* 14:41:30.789 Feb 27: ISAKMP: (1640): entry = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
* 14:41:30.789 Feb 27: ISAKMP: (1640): former State = new State IKE_I_MM4 = IKE_I_MM4
* 14:41:30.789 Feb 27: ISAKMP: (1640): send initial contact
* 14:41:30.789 Feb 27: ISAKMP: (1640): ITS been pre-shared key, using id ID_IPV4_ADDR type authentication
* 14:41:30.789 Feb 27: ISAKMP (1640): payload ID
next payload: 8
type: 1
address: aaa.aaa.aaa.aaa
Protocol: 17
Port: 500
Length: 12
* 14:41:30.789 Feb 27: ISAKMP: (1640): the total payload length: 12
* 27 Feb 14:41:30.789: ISAKMP: (1640): package bbb.bbb.bbb.bbb my_port 500 peer_port 500 (I) sending MM_KEY_EXCH
* 14:41:30.789 Feb 27: ISAKMP: (1640): an IPv4 IKE packet is sent.
* 14:41:30.793 Feb 27: ISAKMP: (1640): entry = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
* 14:41:30.793 Feb 27: ISAKMP: (1640): former State = new State IKE_I_MM4 = IKE_I_MM5
* 14:41:30.825 Feb 27: ISAKMP (1640): packet received dport 500 sport Global 500 (I) MM_KEY_EXCH bbb.bbb.bbb.bbb
* 14:41:30.825 27 Feb: % CRYPTO-6-IKMP_NOT_ENCRYPTED: IKE bbb.bbb.bbb.bbb package was not encrypted and it should have been.
* 14:41:30.825 Feb 27: ISAKMP (1640): increment the count of errors on his, try 1 of 5: reset_retransmission
* 27 Feb 14:41:31.825: ISAKMP: (1640): transmit phase 1 MM_KEY_EXCH...
* 14:41:31.825 Feb 27: ISAKMP (1640): increment the count of errors on his, try 2 of 5: retransmit the phase 1
* 27 Feb 14:41:31.825: ISAKMP: (1640): transmit phase 1 MM_KEY_EXCH
* 27 Feb 14:41:31.825: ISAKMP: (1640): package bbb.bbb.bbb.bbb my_port 500 peer_port 500 (I) sending MM_KEY_EXCH
* 14:41:31.825 Feb 27: ISAKMP: (1640): an IPv4 IKE packet is sent.
* 14:41:31.857 Feb 27: ISAKMP (1640): packet received dport 500 sport Global 500 (I) MM_KEY_EXCH bbb.bbb.bbb.bbb
* 14:41:31.857 27 Feb: % CRYPTO-6-IKMP_NOT_ENCRYPTED: IKE bbb.bbb.bbb.bbb package was not encrypted and it should have been.
* 14:41:31.857 Feb 27: ISAKMP (1640): increment the count of errors on his, try 3 of 5: reset_retransmission
* 27 Feb 14:41:32.857: ISAKMP: (1640): transmit phase 1 MM_KEY_EXCH...
* 14:41:32.857 Feb 27: ISAKMP (1640): increment the count of errors on his, try 4 out 5: retransmit the phase 1
* 27 Feb 14:41:32.857: ISAKMP: (1640): transmit phase 1 MM_KEY_EXCH
* 27 Feb 14:41:32.857: ISAKMP: (1640): package bbb.bbb.bbb.bbb my_port 500 peer_port 500 (I) sending MM_KEY_EXCH
* 14:41:32.857 Feb 27: ISAKMP: (1640): an IPv4 IKE packet is sent.
* 14:41:32.889 Feb 27: ISAKMP (1640): packet received dport 500 sport Global 500 (I) MM_KEY_EXCH bbb.bbb.bbb.bbb
* 27 Feb 14:41:32.889: ISAKMP: (1640): package of phase 1 is a duplicate of a previous package.
* 27 Feb 14:41:32.889: ISAKMP: (1640): retransmission jumped to the stage 1 (time elapsed since the last transmission of 32)
ROUTER #u all
Off crypto conditional debugging.
All possible debugging has been disabled
* 14:42:00.821 27 Feb: % CRYPTO-6-IKMP_NOT_ENCRYPTED: IKE bbb.bbb.bbb.bbb package was not encrypted and it should have been.
* 14:42:01.853 27 Feb: % CRYPTO-6-IKMP_NOT_ENCRYPTED: IKE bbb.bbb.bbb.bbb package was not encrypted and it should have been.
Thank you all
Does that help?
-
Tunnel from site to Site - Customer VPN to access the site on the other.
Hello
How to make this work?
I want to enable the VPN connection clientens in the Cisco ASA for access network the 10.50.50.0.
Network information:
I have a Site of a VPN IPSec Site the Zywall 5 and USG 100 makes (148.148.0.0 and 10.50.50.0). Works great both ways.
I have the Cisco ASA for VPN clients, clients Gets a 24-address 10.210.210.0/ip and his fine work to access the 148.148.0.0/16 network.
The 148.148.0.235 is the main firewall/router for the 148.148.0.0 network.
I created a static route in the 148.148.0.235, saying that for access to the 10.210.210.0 goto 148.148.0.168 network.
I created a static route in the 148.148.0.168, saying that for access to the 10.50.50.0 network goto 148.148.0.235(I pouvez ping 10.50.50.1 de la boîte de Cisco)
I created a site for a second on the Zywall 5 and USG 100 which tunnelle the 10.50.50.0 and 10.210.210.0.In the splittunneling of Cisco ASA, I have authorized access to the 148.148.0.0/16 network and the network 10.50.50.0/24.

When I open the VPN client and connects to the network and try to network ping the 10.50.50.0 I get the following error:
(Here I am trying to ping 10.50.50.1)
5 sep 11 2011 12:36:09 305013 10.50.50.1 NAT rules asymmetrical matching for flows forward and backward; Connection for icmp src, dst outside: 10.210.210.34 inside: 10.50.50.1 (type 8, code 0) rejected due to the failure of reverse path of NAT
I try to make different NAT rules, but it does not change a thing.
Help me, what to do, to make it work?
Thank you.
Simon
Hello
Add this:
NAT (inside, outside) static source Vejle Vejle destination static obj - 10.210.210.0 obj - 10.210.210.0
and let me know if it works
HTH
Mohammad.
-
Access to the DMZ to remote sites via VPN S2S
We have an ASA 5520 and two remote site ASA 5505 that connect to each other through tunnels VPN S2S. They are doing tunneling split, while local traffic passes over the tunnel. We are local LAN (10.0.0.0/16) and our network to the DMZ (10.3.0.0/24) on the main site. The DMZ hosts our external sharepoint, but we access it internally
The problem is site A (10.1.0.0/24) and B (10.2.0.0/24) have no idea of it, and when you try to go to the site, it fails. You can access it via the external site address, but that's the only way. Normally the external address is blocked when you're an intern.
That I'm stuck on is even when we had all sent traffic from Site A to our Senior Center, would find it yet. I do a separate vpn purely tunnel that traffic to DMZ?
Yes. So if you do this in ASDM under Edit Site profile connection Site, it will look like this.
Local network: 10.0.0/16, 10.3.0.0/24
Distance: 10.1.0.0/24
-
Many Web sites (mainly non-google websites) will not open.
Many websites (mainly non-google Sites) does not open on Safari, Chrome , or firefox.
I tried resetting all my browsers, removing all extensions and even run anti-Malware / anti virus controls on my system.They open not just. Web sites are opening perfectly on other devices on the same network.
System details:
MacBook Air 13 inch 2015
OS X El Capitan 10.11
Safari Version 9.0
Thank you
You may have installed one or more variants of the malware "VSearch' ad-injection. Please back up all data, and then take the steps below to disable it.
Do not use any type of product, "anti-virus" or "anti-malware" on a Mac. It is never necessary for her, and relying on it for protection makes you more vulnerable to attacks, not less.
Malware is constantly evolving to work around defenses against it. This procedure works now, I know. It will not work in the future. Anyone finding this comment a couple of days or more after it was published should look for a more recent discussion, or start a new one.
Step 1
VSearch malware tries to hide by varying names of the files it installs. It regenerates itself also if you try to remove it when it is run. To remove it, you must first start in safe mode temporarily disable the malware.
Note: If FileVault is enabled in OS X 10.9 or an earlier version, or if a firmware password is defined, or if the boot volume is a software RAID, you can not do this. Ask for other instructions.
Step 2
When running in safe mode, load the web page and then triple - click on the line below to select. Copy the text to the Clipboard by pressing Control-C key combination:
/Library/LaunchDaemons
In the Finder, select
Go ▹ go to the folder...
from the menu bar and paste it into the box that opens by pressing command + V. You won't see what you pasted a newline being included. Press return.
A folder named "LaunchDaemons" can open. If this is the case, press the combination of keys command-2 to select the display of the list, if it is not already selected.
There should be a column in the update Finder window. Click this title two times to sort the content by date with the most recent at the top. Please don't skip this step. Files that belong to an instance of VSearch will have the same date of change for a few minutes, then they will be grouped together when you sort the folder this way, which makes them easy to identify.
Step 3
In the LaunchDaemons folder, there may be one or more files with the name of this form:
com Apple.something.plist
When something is a random string, without the letters, different in each case.
Note that the name consists of four words separated by dots. Typical examples are:
com Apple.builins.plist
com Apple.cereng.plist
com Apple.nysgar.plist
There may be one or more elements with a full name of this form:
com.something.plist
Yet once something is a random string, without meaning - not necessarily the same as that which appears in one of the other file names.
These names consist of three words separated by dots. Typical examples are:
com.semifasciaUpd.plist
com.ubuiling.plist
Drag all items in the basket. You may be prompted for administrator login password.
Restart the computer and empty the trash.
Examples of legitimate files located in the same folder:
com.apple.FinalCutServer.fcsvr_ldsd.plist
com Apple.Installer.osmessagetracing.plist
com Apple.Qmaster.qmasterd.plist
com Apple.aelwriter.plist
com Apple.SERVERD.plist
The first three are clearly not VSearch files because the names match either of the above models. The last two are not easy to distinguish by the name alone, but the modification date will be earlier than the date at which VSearch has been installed, perhaps several years. None of these legitimate files will be present in most installations of Mac OS X.
Do not delete the folder 'LaunchDaemons' or anything else inside, unless you know you have another type of unwanted software and more VSearch. The file is a normal part of Mac OS X. The "demon" refers to a program that starts automatically. This is not inherently bad, but the mechanism is sometimes exploited by hackers for malicious software.
If you are not sure whether a file is part of the malware, order the contents of the folder by date modified I wrote in step 2, no name. Malicious files will be grouped together. There could be more than one such group, if you attacked more than once. A file dated far in the past is not part of the malware. A folder in date dated Middle an obviously malicious cluster is almost certainly too malicious.
If the files come back after you remove the, they are replaced by others with similar names, then either you didn't start in safe mode or you do not have all the. Return to step 1 and try again.
Step 4
Reset the home page in each of your browsers, if it has been modified. In Safari, first load the desired home page, then select
▹ Safari preferences... ▹ General
and click on
Set on the current Page
If you use Firefox or Chrome web browser, remove the extensions or add-ons that you don't know that you need. When in doubt, remove all of them.
The malware is now permanently inactivated, as long as you reinstall it never. A few small files will be left behind, but they have no effect, and trying to find all them is more trouble that it's worth.
Step 5
The malware lets the web proxy discovery in the network settings. If you know that the setting was already enabled for a legitimate reason, you can skip this step. Otherwise, you must disable the setting.
Open the network pane in system preferences. If there is a padlock icon in the lower left corner of the window, click it and authenticate to unlock the settings. Click the Advanced button, and then select Proxies in the sheet that drops down. Uncheck that Auto Discovery Proxy if it is checked. Click OK, then apply, then close the window.
Step 6
This step is optional. Open the users and groups in the system preferences and click on the lock icon to unlock the settings. In the list of users, there may be one or more with random names that have been added by the malware. You can remove these users. If you are unsure if a user is legitimate or not, do not delete it.
-
ISA500 site by site ipsec VPN with Cisco IGR
Hello
I tried a VPN site by site work with Openswan and Cisco 2821 router configuration an Ipsec tunnel to site by site with Cisco 2821 and ISA550.
But without success.
my config for openswan, just FYI, maybe not importand for this problem
installation of config
protostack = netkey
nat_traversal = yes
virtual_private=%v4:10.0.0.0/8,%v4:192.168.0.0/16,%v4:172.16.0.0/12,%4:!$RIGHT_SUBNET
nhelpers = 0
Conn rz1
IKEv2 = no
type = tunnel
left = % all
leftsubnet=192.168.5.0/24
right =.
rightsourceip = 192.168.1.2
rightsubnet=192.168.1.0/24
Keylife 28800 = s
ikelifetime 28800 = s
keyingtries = 3
AUTH = esp
ESP = aes128-sha1
KeyExchange = ike
authby secret =
start = auto
IKE = aes128-sha1; modp1536
dpdaction = redΘmarrer
dpddelay = 30
dpdtimeout = 60
PFS = No.
aggrmode = no
Config Cisco 2821 for dynamic dialin:
crypto ISAKMP policy 1
BA aes
sha hash
preshared authentication
Group 5
lifetime 28800
!
card crypto CMAP_1 1-isakmp dynamic ipsec DYNMAP_1
!
access-list 102 permit ip 192.168.1.0 0.0.0.255 192.168.5.0 0.0.0.255
!
Crypto ipsec transform-set ESP-AES-SHA1 esp - aes esp-sha-hmac
crypto dynamic-map DYNMAP_1 1
game of transformation-ESP-AES-SHA1
match address 102
!
ISAKMP crypto key
address 0.0.0.0 0.0.0.0 ISAKMP crypto keepalive 30 periodicals
!
life crypto ipsec security association seconds 28800
!
interface GigabitEthernet0/0.4002
card crypto CMAP_1
!
I tried ISA550 a config with the same constelations, but without suggesting.
Anyone has the same problem?
And had anyone has a tip for me, or has someone expirense with a site-by-site with ISA550 and Cisco 2821 ipsec tunnel?
I can successfully establish a tunnel between openswan linux server and the isa550.
Patrick,
as you can see on newspapers, the software behind ISA is also OpenSWAN
I have a facility with a 892 SRI running which should be the same as your 29erxx.
Use your IOS Config dynmap, penny, you are on the average nomad. If you don't have any RW customer you shoul go on IOS "No.-xauth" after the isakmp encryption key.
Here is my setup, with roardwarrior AND 2, site 2 site.
session of crypto consignment
logging crypto ezvpn
!
crypto ISAKMP policy 1
BA 3des
preshared authentication
Group 2
lifetime 28800
!
crypto ISAKMP policy 2
BA 3des
md5 hash
preshared authentication
Group 2
lifetime 28800
!
crypto ISAKMP policy 3
BA 3des
preshared authentication
Group 2
!
crypto ISAKMP policy 4
BA 3des
md5 hash
preshared authentication
Group 2
!
crypto ISAKMP policy 5
BA 3des
preshared authentication
Group 2
life 7200
ISAKMP crypto address XXXX XXXXX No.-xauth key
XXXX XXXX No.-xauth address isakmp encryption key
!
ISAKMP crypto client configuration group by default
key XXXX
DNS XXXX
default pool
ACL easyvpn_client_routes
PFS
!
!
Crypto ipsec transform-set esp-3des esp-sha-hmac FEAT
!
dynamic-map crypto VPN 20
game of transformation-FEAT
market arriere-route
!
!
card crypto client VPN authentication list by default
card crypto VPN isakmp authorization list by default
crypto map VPN client configuration address respond
10 VPN ipsec-isakmp crypto map
Description of VPN - 1
defined peer XXX
game of transformation-FEAT
match the address internal_networks_ipsec
11 VPN ipsec-isakmp crypto map
VPN-2 description
defined peer XXX
game of transformation-FEAT
PFS group2 Set
match the address internal_networks_ipsec2
card crypto 20-isakmp dynamic VPN ipsec VPN
!
!
Michael
Please note all useful posts
Maybe you are looking for
-
What apps work best with the pencil
What apps work best with the pencil. Particularly interested in commenting, highlighting and rating photos and graphics.
-
It is more of a thing of aesthetics than anything else, but I'm looking for an analog/digital the 'empty string constant. I'll save this data in a file with the 'write to spreadsheet.vi"the array of strings on top will be recorded first as a header f
-
Cannot set up eprint. My printer was working with eprint very well until I got a new router. Since I can't not to use or setup eprint. It is connected to the home network wireless and it works fine for printing documents. I have reset the factory for
-
When I click on NEW to write an e-mail, a Microsoft sign come on screen saying "Web site wants to open content using theis program called Silverlight - Setup - exe, the Puplisher is Microsoft Corporation. Then the whole [page freezes. Won't happen u
-
Try to test the model of animation with Adobe Flash CS5 in Windows XP stops
I'm currently testing a model animation in Adobe Flash CS %, Windows displays an error message and stop the animation of initalising and then Windows States to close the program to check its compatibility. Nothing so haapens. I ran the compatibility
