IPSec Client through ASA5540 error
Hello world
We have an ASA 5540 successfully using SSL VPN Client Tunnels without problems and have sought to build the ability for IPSec Clients can connect as well. I have authentication works, still cannot complete the implementation of the tunnel for the client. The customer receives an error of "secure VPn connection terminated by Peer, 433 reason: (reason unspecified peer).
In the log on the client, I see the following when connecting:
(this is after a connection successful, divided tunnel configurations, then this set to appear in the journal)
377 09:29:08.071 28/02/13 Sev = Info/4 IKE / 0 x 63000014
RECEIVING< isakmp="" oak="" info="" *(hash,="" notify:status_resp_lifetime)="" from="">
378 09:29:08.071 28/02/13 Sev = Info/5 IKE / 0 x 63000045 Answering MACHINE-LIFE notify has value of 86400 seconds 379 09:29:08.071 28/02/13 Sev = Info/5 IKE / 0 x 63000047 This SA was already alive for 4 seconds, affecting seconds expired 86396 now 380 09:29:08.071 28/02/13 Sev = Info/5 IKE/0x6300002F Received packet of ISAKMP: peer =
381 09:29:08.071 28/02/13 Sev = Info/4 IKE / 0 x 63000014 RECEIVING< isakmp="" oak="" info="" *(hash,="" del)="" from="">
382 09:29:08.071 28/02/13 Sev = Info/5 IKE/0x6300003C Received a payload to REMOVE SA IKE with cookie: I_Cookie = 5E1213254915B44F R_Cookie = D80631768AD86493 383 09:29:08.071 28/02/13 Sev = Info/4 IKE / 0 x 63000013 SEND to > ISAKMP OAK INFO *(HASH, DEL) to
384 09:29:08.071 28/02/13 Sev = Info/4 IKE / 0 x 63000049 IPsec security association negotiation made scrapped, MsgID = 8A3649A8 385 09:29:08.071 28/02/13 Sev = Info/4 IKE / 0 x 63000017 Marking of IKE SA delete (I_Cookie = 5E1213254915B44F R_Cookie = D80631768AD86493) reason = PEER_DELETE-IKE_DELETE_UNSPECIFIED 386 09:29:08.414 28/02/13 Sev = Info/4 IPSEC / 0 x 63700014 Remove all keys etc.etc.etc... through the closure of the tunnel and removal So, I turned on debugging everything I can think of the ASA, and the only thing I can find that might be relevant is the following: ENTER SESS_Mgmt_CalculateLicenseLimit< 08b053e4="">< 086ab182="">< 0869fb4f=""><> Session idle time calculation: 0x1FD000, direction: receive Tunnel: 0x1FD002: timestamp: 6731252, now: 6731290, slowed down: 38, using this tunnel for idle IDLE = 38 ENTER SESS_Mgmt_UpdateSessStartTime< 08b056fe="">< 084dc614="">< 084e2379="">< 084a73b3="">< 0931c3ff="">< 084a64fb="">< 084b6467=""><> SESS_Mgmt_UpdateSessStartTime: session not found 0 ENTER SESS_Mgmt_CheckLicenseLimitReached< 08b09a7e="">< 084ac8b0="">< 0931c3ff="">< 084a64fb="">< 084b6467="">< 084b6f73=""><> ENTER SESS_Mgmt_CalculateLicenseLimit< 08b099cb="">< 084ac8b0="">< 0931c3ff="">< 084a64fb="">< 084b6467="">< 084b6f73=""><> ENTER SESS_Mgmt_CreateSession< 08b0a09a="">< 084ac541="">< 0931c3ff="">< 084a64fb="">< 084b6467="">< 084b6f73=""><> ENTER SESS_Mgmt_CheckLicenseLimitReached< 08b09a7e="">< 08b09fd2="">< 084ac541="">< 0931c3ff="">< 084a64fb="">< 084b6467="">< 084b6f73=""><> ENTER SESS_Mgmt_CalculateLicenseLimit< 08b099cb="">< 08b09fd2="">< 084ac541="">< 0931c3ff="">< 084a64fb="">< 084b6467="">< 084b6f73=""><> ENTER SESS_Util_CreateSession< 08b0343e="">< 08b0a007="">< 084ac541="">< 0931c3ff="">< 084a64fb="">< 084b6467="">< 084b6f73=""><> ENTER SESS_Mgmt_GetLoginCount< 08b18d71="">< 0806e65e="">< 08072627="">< 08077013="">< 0931c3ff="">< 080749ca="">< 08074ae8=""><> ENTER SESS_Mgmt_AddEntry< 08b088be="">< 08509b43="">< 084a9097="">< 0931c3ff="">< 084a64fb="">< 084b6467="">< 084b6f73=""><> VPN-SESSION_DB in SESS_Mgmt_AddEntry p->... Protocol = 1 EncrAlg = 2 HashAlg = 2 ignoreAcct = 0 CompAlg = 0 SSOType = 0 pfsGroup = 0 IkeNegMode = 2 EncapMode = 0 AuthenModeIKE = 1 AuthenModeSSL = 0 AuthenModePPP = 0 AuthenModeX = 3 AuthorModeX = 1 DiffHelmanGrp = 2 * TunnelGroupName = IPSECVPNClients server_group_Id = 0 RekeyTime = 2147483 RekeyKBytes = 0 pGetCounters = 0 x 0 pClearCounters = 0 x 0 pGetfSessData = 0 x 0 Temps_inactivite = 0
ConnectTime = 0
pKill = 0 x 8506020
* manage = 0 x 200000
publicIpAddr =
LocAddrType = 0 LocProxyAddr1 = 0.0.0.0 LocProxyAddr2 = 0.0.0.0 LocProxyProtocol = 0 x 0 LocProxyPort = 0 x 0 RemAddrType = 0 RemProxyAddr1 = 0.0.0.0 RemProxyAddr2 = 0.0.0.0 RemProxyProtocol = 0 x 0 RemProxyPort = 0 x 0 assignedIpAddr =
assignedIpv6Addr =: hubInterface = 1.0.0.0 WINSServer-> server_type = 0 WINSServer-> server_count = 0 WINSServer-> server_addr_array [0] = 0x0 DNSServer-> server_type = 0 DNSServer-> server_count = 0 DNSServer-> server_addr_array [0] = 0x0 * Username =
* ClientOSVendor = WinNT * ClientOSVersion = 5.0.07.0440 * ClientVendor = * ClientVersion = InstId = 2097152 TcpSrcPort = 0 TcpDstPort = 0 UdpSrcPort = 13583 UdpDstPort = 500 filterId = 0 * aclId = ipv6filterId = 0 * ipv6aclId = vcaSession = 0 sessIndex = 0 x 200000 ENTER SESS_Util_CreateTunnel< 08b036e0="">< 08b08a33="">< 08509b43="">< 084a9097="">< 0931c3ff="">< 084a64fb="">< 084b6467="">< 084b6f73=""><> ENTER SESS_Mgmt_AddSessionToTunnelGroup< 08b1781e="">< 08b092f4="">< 08509b43="">< 084a9097="">< 0931c3ff="">< 084a64fb="">< 084b6467=""><> ENTER SESS_Util_FindTunnelGroup< 08b16fce="">< 08b17751="">< 08b092f4="">< 08509b43="">< 084a9097="">< 0931c3ff="">< 084a64fb=""><> SESS_Mgmt_AddSessionToTunnelGroup: Name of user =
ENTER SESS_Util_AddUser< 08b1922d="">< 08b1779c="">< 08b092f4="">< 08509b43="">< 084a9097="">< 0931c3ff="">< 084a64fb="">< 084b6467=""><> ENTER SESS_Util_AddUser< 08b1922d="">< 08b0930f="">< 08509b43="">< 084a9097="">< 0931c3ff="">< 084a64fb="">< 084b6467="">< 084b6f73=""><> ENTER SESS_MIB_AddUser< 08b198ad="">< 08b094f7="">< 08509b43="">< 084a9097="">< 0931c3ff="">< 084a64fb="">< 084b6467="">< 084b6f73=""><> ENTER SESS_Mgmt_CheckActiveSessionTrapThreshold< 08b09697="">< 08509b43="">< 084a9097="">< 0931c3ff="">< 084a64fb="">< 084b6467=""><> SESS_Mgmt_StartAcct: Failed to start for the account SESS_Mgmt_AddEntry: Created the Tunnel: 00200001, Protocol: 1 VPN-SESSION_DB in SESS_Mgmt_UpdateEntry p->... Protocol = 1 EncrAlg = 2 HashAlg = 2 ignoreAcct = 0 CompAlg = 0 SSOType = 0 pfsGroup = 0 IkeNegMode = 2 EncapMode = 0 AuthenModeIKE = 1 AuthenModeSSL = 0 AuthenModePPP = 0 AuthenModeX = 3 AuthorModeX = 1 DiffHelmanGrp = 2 * TunnelGroupName = IPSECVPNClients server_group_Id = 0 RekeyTime = 2147483 RekeyKBytes = 0 pGetCounters = 0 x 0 pClearCounters = 0 x 0 pGetfSessData = 0 x 0 Temps_inactivite = 0 ConnectTime = 0 pKill = 0 x 8506020 * manage = 0 x 200000 publicIpAddr =
LocAddrType = 0 LocProxyAddr1 = 0.0.0.0 LocProxyAddr2 = 0.0.0.0 LocProxyProtocol = 0 x 0 LocProxyPort = 0 x 0 RemAddrType = 0 RemProxyAddr1 = 0.0.0.0 RemProxyAddr2 = 0.0.0.0 RemProxyProtocol = 0 x 0 RemProxyPort = 0 x 0 assignedIpAddr =
assignedIpv6Addr =: hubInterface = 1.0.0.0
WINSServer-> server_type = 0
WINSServer-> server_count = 0
WINSServer-> server_addr_array [0] = 0x0
DNSServer-> server_type = 0
DNSServer-> server_count = 0
DNSServer-> server_addr_array [0] = 0x0
* Username =
* ClientOSVendor = WinNT * ClientOSVersion = 5.0.07.0440 * ClientVendor = * ClientVersion = InstId = 2097152 TcpSrcPort = 0 TcpDstPort = 0 UdpSrcPort = 13583 UdpDstPort = 500 filterId = 0 * aclId = ipv6filterId = 0 * ipv6aclId = vcaSession = 0 sessIndex = 0 x 200000 Released SESS_Mgmt_UpdateEntry: Return Code = 0 VPN-SESSION_DB in SESS_Mgmt_UpdateEntry p->... Protocol = 1 EncrAlg = 2 HashAlg = 2 ignoreAcct = 0 CompAlg = 0 SSOType = 0 pfsGroup = 0 IkeNegMode = 2 EncapMode = 0 AuthenModeIKE = 1 AuthenModeSSL = 0 AuthenModePPP = 0 AuthenModeX = 3 AuthorModeX = 1 DiffHelmanGrp = 2 * TunnelGroupName = IPSECVPNClients server_group_Id = 0 RekeyTime = 86400 RekeyKBytes = 0 pGetCounters = 0 x 0 pClearCounters = 0 x 0 pGetfSessData = 0 x 0 Temps_inactivite = 0
ConnectTime = 0
pKill = 0 x 8506020
* manage = 0 x 200000
publicIpAddr =
LocAddrType = 0 LocProxyAddr1 = 0.0.0.0 LocProxyAddr2 = 0.0.0.0 LocProxyProtocol = 0 x 0 LocProxyPort = 0 x 0 RemAddrType = 0 RemProxyAddr1 = 0.0.0.0 RemProxyAddr2 = 0.0.0.0 RemProxyProtocol = 0 x 0 RemProxyPort = 0 x 0 assignedIpAddr =
assignedIpv6Addr =: hubInterface = 1.0.0.0 WINSServer-> server_type = 0 WINSServer-> server_count = 0 WINSServer-> server_addr_array [0] = 0x0 DNSServer-> server_type = 0 DNSServer-> server_count = 0 DNSServer-> server_addr_array [0] = 0x0 * Username =
* ClientOSVendor = WinNT * ClientOSVersion = 5.0.07.0440 * ClientVendor = * ClientVersion = InstId = 2097152 TcpSrcPort = 0 TcpDstPort = 0 UdpSrcPort = 13583 UdpDstPort = 500 filterId = 0 * aclId = ipv6filterId = 0 * ipv6aclId = vcaSession = 0 sessIndex = 0 x 200000 Released SESS_Mgmt_UpdateEntry: Return Code = 0 ENTER SESS_Mgmt_DeleteEntryFileLineFunc< 08b05ece="">< 084cfa02="">< 084d1d93="">< 084b6c3e="">< 084b6f73=""><> SESS_Mgmt_DeleteEntryFileLineFunc: index = 200001, reason = 0 SESS_Mgmt_DeleteEntryFileLineFunc: Index: 0 x 00200001, reason: unknown (0-0 online) @ isadb.c:[email protected]/ * / _set_cond_dead ENTER SESS_Mgmt_DeleteEntryInt< 08b0b473="">< 084cfa02="">< 084d1d93="">< 084b6c3e="">< 084b6f73=""><> SESS_Mgmt_DeleteEntryInt: index = 0 x 00200001, reason = 0 ENTER SESS_Mgmt_DeleteTunnel< 08b0b2b5="">< 08b0b4f9="">< 084cfa02="">< 084d1d93="">< 084b6c3e="">< 084b6f73=""><> SESS_Mgmt_DeleteTunnel: ID: 0 x 00200001, reason: unknown, kill: Yes, Active SESS_Mgmt_DeleteEntryInt: session ending after deleted tunnel
ENTER SESS_Mgmt_FreeSessionFileLineFunc< 08b08043="">< 084d28c8="">< 084b6c3e="">< 084b6f73=""><>
SESS_Mgmt_FreeSessionFileLineFunc: Index: 0 x ACTIVE 00200000 @ isadb.c:[email protected]/ * / _delete_entry
ENTER SESS_Mgmt_RemoveSessionFromTunnelGroup< 08b17a3e="">< 08b07bbe="">< 084d28c8="">< 084b6c3e="">< 084b6f73=""><>
ENTER SESS_Util_FindTunnelGroup< 08b16fce="">< 08b179b2="">< 08b07bbe="">< 084d28c8="">< 084b6c3e="">< 084b6f73=""><>
ENTER SESS_Util_DeleteUser< 08b1906d="">< 08b179f5="">< 08b07bbe="">< 084d28c8="">< 084b6c3e="">< 084b6f73=""><>
ENTER SESS_Util_DeleteUser< 08b1906d="">< 08b07bd0="">< 084d28c8="">< 084b6c3e="">< 084b6f73=""><>
ENTER SESS_MIB_DeleteUser< 08b196dd="">< 08b07fb0="">< 084d28c8="">< 084b6c3e="">< 084b6f73=""><>
I see the message where it stops and where is says "Account start failure" but I can't understand what it's showing... anyone have suggestions on what to look for?
You need only 1 debug for that.
Debug crypto isakmp 254
After the release of this when you try to connect, as well as the output sanitized of:
See the establishment of performance-crypto
SH run tunnel-group
SH run Group Policy
SH run ip local pool
and we can have a better idea of where the bat hurt.
Tags: Cisco Security
Similar Questions
-
Windows 7 32 b ipsec client error 789 RV220W
Hello
I'm trying to connect to RV220W with the windows client 7 but I do not see: error 789. I compare new pre shared key, but it doesn't change anything
Is everyone to connect to RV220W with the IPsec client?
Thank you
GF, this isn't a vpn ipsec and he is not so sure. Support only integrated window will be PPTP regarding the connection to the router.
If you are looking for IPsec, you must use quickvpn (free Cisco software) or a 3rd party software greenbow, shrewsoft, ipsecuritas, etc..
-Tom
Please evaluate the useful messages -
Is there a 64-bit version of the Cisco's IPSEC client on the roadmap?
I know that there is the AnyConnect client, but that would mean buying more licenses for SSL when we have a lot of IPSEC.
I understand that there will be no support for it. The only option is to go to AnyConnect.
-
double authentication with Cisco's VPN IPSEC client
Cisco VPN client (the legacy IPSEC client) does support dual authentication with RSA token AND ActiveDirectory credentials?
I know that AnyConnect supports it and the commandsecondary- authentication -Server- group' is only for ssl connections, but must be confirmed.
Kind regards
Mohammad
Hi Mohammad,.
What is double authentication support for Cisco VPN Client?
A. No. Double authentication only is not supported on the Cisco VPN Client.
You can find more information on the customer Cisco VPN here.
As you said the only client that supports dual authentication is the Cisco AnyConnect secure mobility Client.
Please note and mark it as correct this Post!
Let me know if there are still questions about it!
David Castro,
-
Cisco ASA5520 facing ISP with private IP address. How to get the IPSec VPN through the internet?
/ * Style definitions * / table. MsoNormalTable {mso-style-name : « Table Normal » ; mso-tstyle-rowband-taille : 0 ; mso-tstyle-colband-taille : 0 ; mso-style-noshow:yes ; mso-style-priorité : 99 ; mso-style-qformat:yes ; mso-style-parent : » « ;" mso-rembourrage-alt : 0 à 5.4pt 0 à 5.4pt ; mso-para-marge-top : 0 ; mso-para-marge-droit : 0 ; mso-para-marge-bas : 10.0pt ; mso-para-marge-left : 0 ; ligne-hauteur : 115 % ; mso-pagination : widow-orphelin ; police-taille : 11.0pt ; famille de police : « Calibri », « sans-serif » ; mso-ascii-font-family : Calibri ; mso-ascii-theme-font : minor-latin ; mso-fareast-font-family : « Times New Roman » ; mso-fareast-theme-font : minor-fareast ; mso-hansi-font-family : Calibri ; mso-hansi-theme-font : minor-latin ;}
Hello guys,.
I have Cisco ASA5520 facing the ISP with private IP address. We don't have a router and how to get the IPSec VPN through the internet?
The question statement not the interface pointing to ISP isn't IP address private and inside as well.
Firewall configuration:
Firewall outside interface Gi0 10.0.1.2 > ISP 10.0.1.1 with security-level 0
Firewall inside the interface Ethernet0 192.168.1.1 > LAN switch 192.168.1.2 with security-level 100
I have public IP block 199.9.9.1/28
How can I use the public IP address to create the IPSec VPN tunnel between two sites across the internet?
can I assign a public IP address on the Gig1 inside the interface with the security level of 100 and how to apply inside to carry on this interface?
If I configure > firewall inside of the item in gi1 interface ip address 199.9.9.1/28 with security-level 100. How to make a safe lane VPN through this interface on the internet?
I'm used to the public IP address allocation to the interface outside of the firewall and private inside the interface IP address.
Please help with configuration examples and advise.
Thank you
Eric
Unfortunately, you can only complete the VPN connection on the interface the VPN connection source, in your case the external interface.
3 options:
(1) connect a router in front of the ASA and assign your public ip address to the ASA outside interface.
OR /.
(2) If your ISP can perform static translation of 1 to 1, then you can always finish the VPN on the external interface and ask your provider what is the static ip address assigned to your ASA out of the IP (10.0.1.2) - this will launch the VPN of bidirectionally
OR /.
(3) If your ISP performs PAT (dynamic NAT), then you can only start the tunnel VPN on the side of the ASA and the other end of the tunnel must be configured to allow VPN LAN-to-LAN dynamics.
-
IOS VPN L2L + C2L (cisco IPSEC client)
Hello
need to configure a C2L (client to the LAN) vpn on a cisco router where there is already an ipsec vpn.
!!! already configured on the ROUTER
!
crypto ISAKMP policy 1
md5 hash
preshared authentication
address of cisco key crypto isakmp 0.0.0.0 0.0.0.0
!
!
Crypto ipsec transform-set esp - esp-md5-hmac Tunnel
!
crypto dynamic-map 10 Road-Tunnel
game of transformation-Tunnel
match address 115
!
!
!
!
Crypto map 10 ipsec-isakmp Crypto-Tunnel Dynamic Channel-Tunnel
!
point-to-point interface ATM0/1/0.1
card crypto Crypto-Tunnel
!
access-list 115 permit ip 10.0.0.0 0.0.0.255 192.168.168.0 0.0.0.255
access-list 115 permit ip 10.0.0.0 0.0.0.255 10.2.0.0 0.0.0.255
access-list 115 deny ip 10.0.0.0 0.0.0.255 any
!
!!! new configuration for cisco ipsec client
!
no address Cisco key crypto isakmp 0.0.0.0 0.0.0.0
address of cisco key crypto isakmp 0.0.0.0 0.0.0.0 no.-xauth
!
AAA new-model
!
AAA authentication login AutClient local
AAA authorization groupauthor LAN
!
!
username 0 pippo pippo
!
crypto ISAKMP policy 10
BA 3des
preshared authentication
Group 2
!
ISAKMP crypto client configuration group vpnclient
key 0-pippo
DNS 10.10.10.10
WINS 10.10.10.20
domain cisco.com
pool ippoolvpnclient
Save-password
ACL 188
!
!
card crypto Crypto-Tunnel client authentication list AutClient
card crypto Crypto-Tunnel isakmp authorization list groupauthor
card crypto Crypto-Tunnel client configuration address respond
card crypto Crypto-ipsec-isakmp dynamic dynmap Tunnel 20
!
Crypto ipsec transform-set esp-3des esp-md5-hmac RIGHT
!
Crypto-map dynamic dynmap 10
match address 188
Set transform-set RIGHT
!
!
!
!
IP local pool ippoolvpnclient 10.99.0.1 10.99.0.30
!
access-list 188 note #.
access-list 188 note # split tunneling VPN C2L
access-list 188 allow ip 10.99.0.0 0.0.0.31 10.0.0.0 0.0.0.255
!
can you tell me if the new configuration is OK?
Thank you all
NOT the ACL should be the opposite. Sound from the point of view of the router.
access-list 188 allow ip 10.2.0.0 0.0.0.255 10.5.0.0 0.0.0.31
Concerning
Farrukh
-
IPsec client for s2s NAT problem
Hello
We have a remote site (Paris) with a 5512 with some s2s and RA light customer vpn (anyconnect IPsec) tunnels. AnyConnect has no problem, but the ipsec client can not pass traffic on the LAN. The subnet behind the fw is 10.176.0.0/16 and the RA 10.172.28.0/24 customer pool. However, we have a s2s than nat 10.0.0.0/8 tunnel and it appears that customers vpn IPSEC RA being bound traffic matches this rule and prevents connectivity to local resources via vpn ipsec client.
......
hits = 485017, user_data = 0x7fffa5d1aa10, cs_id = 0 x 0, use_real_addr, flags = 0 x 0 = 0 protocol
IP/ID=10.176.0.0 SRC, mask is 255.255.0.0, port = 0
IP/ID=10.0.0.0 DST, mask is 255.0.0.0, port = 0, dscp = 0 x 0
input_ifc = inside, outside = output_ifc
...
Manual NAT policies (Section 1)
1 (outdoor) static source Paris_Network Paris_Network static destination Remote2_LAN_Networks Remote2_LAN_Networks non-proxy-arp-search to itinerary (inside)
translate_hits = 58987, untranslate_hits = 807600
2 (inside) (outside) static source Paris_Network Paris_Network static destination DM_INLINE_NETWORK_2 DM_INLINE_NETWORK_2-route search
translate_hits = 465384, untranslate_hits = 405850
3 (inside) (outside) static source Paris_Network Paris_Network static destination Remote1_Networks Remote1_Networks-route search
translate_hits = 3102307, untranslate_hits = 3380754
4 (outside) (inside) static source Paris_RA_VPN Paris_RA_VPN static destination Paris_Network Paris_Network-route search
translate_hits = 0, untranslate_hits = 3
This method works on other sites with almost identical configuration, but for some reason, it doesn't work here. I can't specify different subnets for the s2s tunnel because there is too much of. Can someone help me and tell me why I can't get this to work?
Hello
So you're saying that the AnyConnect is working but not IPsec? What is the the AnyConnect VPN? It is outside the 10.0.0.0/8 network?
You should be able to substitute the NAT VPN L2L configuration by simply configuring a separate NAT for the local network for VPN pool traffic at the top of your NAT configurations
For example
being PARIS-LAN network
10.176.0.0 subnet 255.255.0.0
object netwok PARIS-VPN-POOL
10.172.28.0 subnet 255.255.255.0
NAT (inside, outside) 1 static source PARIS PARIS - LAN LAN destination PARIS-VPN-POOL PARIS-VPN-POOL static
This should ensure that the first rule on the SAA is the NAT rule that matches the VPN Client for LAN traffic. Other aircraft in the L2L VPN should still hit the original NAT rule to the VPN L2L
If this does not work then we must look closer, the configuration.
Hope this helps
Remember to mark a reply as the answer if it answered your question.
Feel free to ask more if necessary
-Jouni
-
Cisco 2600 router as an IPSec client
Hello
Currently I use a Cisco VPN client software to connect to a remote server for IPSec on the workstations.
I want to set up the IPSec client on Cisco 2600 router that connects to the remote server IPSec so that workstations can access subnet VPN without using VPN software.
Can someone guide me on how to configure the IPSec client on the router?
Thank you
Hi Adam,.
Sorry for my late reply, I'm a little sick.
I have checked the logs and did small repro. For me, it seems that the server does not support NEM:
It is disabled with NEM VPN server:
Nov 30 00:13:56 [IKEv1 DEBUG]: Group = gsa3mle3, name of user = cisco, IP = 10.10.10.2, MODE_CFG: request received for the DHCP for DDNS hostname is: R1!
Nov 30 00:13:56 [IKEv1]: Group = gsa3mle3 username = cisco, IP = 10.10.10.2, material Connection Client rejected! Network Extension mode is not allowed for this group!
The customer:
* 1 Mar 00:45:56.387: ISAKMP: (1007): lot of 10.10.10.13 sending my_port 500 peer_port 500 (I) CONF_ADDR
* 00:45:56.439 Mar 1: ISAKMP (0:1007): received 10.10.10.13 packet dport 500 sport Global 500 (I) CONF_ADDR
* 1 Mar 00:45:56.439: DGVPN:crypt_iv after decrypt, its: 650BE464
7BCF116E8E4DFF6C
* 00:45:56.443 Mar 1:
* 00:45:56.443 Mar 1: ISAKMP: content of the packet of information (flags, 1, len 92):
* 00:45:56.447 Mar 1: HASH payload
* 00:45:56.447 Mar 1: delete payload
* 00:45:56.459 Mar 1: ISAKMP: content of the packet of information (flags, 1, len 80):
* 00:45:56.459 Mar 1: HASH payload
* 00:45:56.459 Mar 1: delete payload
* 1 Mar 00:45:56.459: DGVPN: crypt_iv after encrypting, its: 650BE464
Change it to client mode and try it.
Kind regards
Michal
-
Misconfigured remote VPN server by using IPSEC client
I'm trying to figure out what I did wrong in my setup. The environment is:
ASA 5505 running 8.2 with 6.2 ASDM.
Version of the VPN Client 5.0.05.0290
I installed VPN ipsec clients both anyconnect and connected successfully to the remote access VPN server. However, the client doesn't show any returned package. Thinking that I have badly configured, I have reset to the default value of the factory and began again. Now I only have the configured ipsec vpn and I have exactly the same symptoms. I followed the instructions to configure the ipsec vpn in Document 68795 and double-checked my setup and I don't know what I did wrong. Because I can connect to the internet from inside network and I can connect to the VPN from outside of the network (and the ASDM Watch monitor an active connection with nothing sent to the client) I believe this is a road or an access rule preventing communication but I can't quite figure out where (and I tried the static routes to the ISP and a wide variety of access rules before rinsing to start) above).
a basic threat threat detection
Statistics-list of access threat detection
no statistical threat detection tcp-interception
WebVPN
internal group vogon strategy
attributes of vogon group policy
Protocol-tunnel-VPN IPSec
Split-tunnel-policy tunnelspecified
value of Split-tunnel-network-list vogon_splitTunnelAcl
username password privilege encrypted 0987654321 zaphod 15
username password encrypted AaBbCcDdEeFf privilege 0 arthur
username arthur attributes
VPN-group-policy vogon
tunnel-group vogon type remote access
tunnel-group vogon General attributes
address pool VPN_Pool
strategy-group-by default vogon
tunnel-group vogon ipsec-attributes
pre-shared-key *.
!
class-map inspection_default
match default-inspection-traffic
!
!
type of policy-card inspect dns preset_dns_map
parameters
message-length maximum 512
Policy-map global_policy
class inspection_default
inspect the preset_dns_map dns
inspect the ftp
inspect h323 h225
inspect the h323 ras
inspect the rsh
inspect the rtsp
inspect esmtp
inspect sqlnet
inspect the skinny
inspect sunrpc
inspect xdmcp
inspect the sip
inspect the netbios
inspect the tftp
!
global service-policy global_policy
context of prompt hostname
Cryptochecksum:xxxxxxxxxxxxxxxxxxxxxxLooks like a typo for the Pool of IP subnet mask.
You currently have:
mask 10.92.66.10 - 10.92.66.24 255.255.0.0 IP local pool VPN_Pool
It should be:
mask 10.92.66.10 - 10.92.66.24 255.255.255.0 IP local pool VPN_Pool
Please kindly change the foregoing and test, if it still does not work, please please add the following:
management-access inside
Policy-map global_policy
class inspection_defaultinspect the icmp
Then try to VPN in and see if you can ping 10.92.65.1 and let us know if this ping works.
Please also share the output of: "cry ipsec to show his" after the trial, if it does not work.
-
vCenter Web client: a server error has occurred. [500] SSO error: null
Hello all, I have problem with vCenter 6.0
I installed vCenter 6.0 with service of external platform controller.
I saw when I worked in the Web client alert (warning), something like "vAPI health alarm.
Now, I can not connect to the Web client with the error 'a server error has occurred. .
[500] SSO error: null
" Check the logs from the Server Web Client vSphere for details."
And I can't connect to vCenter with vsphere client.
In the logfile "vsphere_client_virgo.txt" I have seen the error:
[2015 04-08 T 14: 28:38.505 - 07:00] [WARNING] http-bio-9443-exec-1
70000146 100005 200003 org.springframework.flex.core.DefaultExceptionLogger
The following exception occurred during treatment with the BlazeDS MessageBroker in demand and will be serialized to the client: flex.messaging.MessageException: com.vmware.vsphere.client.error.ApplicationException: unable to connect to the services of vSphere. Connection for vSphere Web Client and try again.
at flex.messaging.services.remoting.adapters.JavaAdapter.invoke(JavaAdapter.java:444)
at com.vmware.vise.messaging.remoting.JavaAdapterEx.invoke(JavaAdapterEx.java:50)
at flex.messaging.services.RemotingService.serviceMessage(RemotingService.java:183)
at flex.messaging.MessageBroker.routeMessageToService(MessageBroker.java:1400)
at flex.messaging.endpoints.AbstractEndpoint.serviceMessage(AbstractEndpoint.java:1011)
to flex.messaging.endpoints.AbstractEndpoint$ $FastClassByCGLIB$ $1a3ef066.invoke (< generated >)
at net.sf.cglib.proxy.MethodProxy.invoke(MethodProxy.java:149)
to org.springframework.aop.framework.Cglib2AopProxy$ CglibMethodInvocation.invokeJoinpoint (Cglib2AopProxy.java:689)
at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:150)
at org.springframework.flex.core.MessageInterceptionAdvice.invoke(MessageInterceptionAdvice.java:66)
at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:172)
at org.springframework.aop.framework.adapter.ThrowsAdviceInterceptor.invoke(ThrowsAdviceInterceptor.java:124)
at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:172)
to org.springframework.aop.framework.Cglib2AopProxy$ FixedChainStaticTargetInterceptor.intercept (Cglib2AopProxy.java:573)
to com.vmware.vise.messaging.endpoints.AMFEndpoint$ $EnhancerByCGLIB$ $75e2a5d4.serviceMessage (< generated >)
at flex.messaging.endpoints.amf.MessageBrokerFilter.invoke(MessageBrokerFilter.java:103)
at flex.messaging.endpoints.amf.LegacyFilter.invoke(LegacyFilter.java:158)
at flex.messaging.endpoints.amf.SessionFilter.invoke(SessionFilter.java:44)
at flex.messaging.endpoints.amf.BatchProcessFilter.invoke(BatchProcessFilter.java:67)
at flex.messaging.endpoints.amf.SerializationFilter.invoke(SerializationFilter.java:166)
at flex.messaging.endpoints.BaseHTTPEndpoint.service(BaseHTTPEndpoint.java:291)
to com.vmware.vise.messaging.endpoints.AMFEndpoint$ $EnhancerByCGLIB$ $75e2a5d4.service (< generated >)
at org.springframework.flex.servlet.MessageBrokerHandlerAdapter.handle(MessageBrokerHandlerAdapter.java:109)
at org.springframework.web.servlet.DispatcherServlet.doDispatch(DispatcherServlet.java:923)
at org.springframework.web.servlet.DispatcherServlet.doService(DispatcherServlet.java:852)
at org.springframework.web.servlet.FrameworkServlet.processRequest(FrameworkServlet.java:882)
at org.springframework.web.servlet.FrameworkServlet.doPost(FrameworkServlet.java:789)
at javax.servlet.http.HttpServlet.service(HttpServlet.java:755)
at javax.servlet.http.HttpServlet.service(HttpServlet.java:848)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:303)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:208)
at org.apache.tomcat.websocket.server.WsFilter.doFilter(WsFilter.java:52)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:241)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:208)
at com.vmware.vise.security.SessionManagementFilter.doFilterInternal(SessionManagementFilter.java:82)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:76)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:241)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:208)
at com.vmware.vsphere.client.logging.MDCLogFilter.doFilterInternal(MDCLogFilter.java:41)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:76)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:241)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:208)
at org.apache.catalina.core.StandardWrapperValve.invoke(StandardWrapperValve.java:220)
at org.apache.catalina.core.StandardContextValve.invoke(StandardContextValve.java:122)
at org.apache.catalina.authenticator.AuthenticatorBase.invoke(AuthenticatorBase.java:501)
at org.apache.catalina.core.StandardHostValve.invoke(StandardHostValve.java:170)
at org.apache.catalina.valves.ErrorReportValve.invoke(ErrorReportValve.java:98)
at org.eclipse.virgo.web.tomcat.support.ApplicationNameTrackingValve.invoke(ApplicationNameTrackingValve.java:33)
at org.apache.catalina.valves.AccessLogValve.invoke(AccessLogValve.java:950)
at org.apache.catalina.core.StandardEngineValve.invoke(StandardEngineValve.java:116)
at org.apache.catalina.connector.CoyoteAdapter.service(CoyoteAdapter.java:408)
at org.apache.coyote.http11.AbstractHttp11Processor.process(AbstractHttp11Processor.java:1040)
to org.apache.coyote.AbstractProtocol$ AbstractConnectionHandler.process (AbstractProtocol.java:607)
to org.apache.tomcat.util.net.JIoEndpoint$ SocketProcessor.run (JIoEndpoint.java:315)
at java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1145)
to java.util.concurrent.ThreadPoolExecutor$ Worker.run (ThreadPoolExecutor.java:615)
at java.lang.Thread.run(Thread.java:745)
Caused by: com.vmware.vsphere.client.error.ApplicationException: unable to connect to the services of vSphere. Connection for vSphere Web Client and try again.
at com.vmware.vsphere.client.error.ErrorReportUtil.getService(ErrorReportUtil.java:126)
at com.vmware.vsphere.client.error.ErrorReportPage.toErrorStack(ErrorReportPage.java:168)
at com.vmware.vsphere.client.error.impl.ErrorReportServiceImpl.getErrorStack(ErrorReportServiceImpl.java:48)
at sun.reflect.NativeMethodAccessorImpl.invoke0 (Native Method)
at sun.reflect.NativeMethodAccessorImpl.invoke(NativeMethodAccessorImpl.java:57)
at sun.reflect.DelegatingMethodAccessorImpl.invoke(DelegatingMethodAccessorImpl.java:43)
at java.lang.reflect.Method.invoke(Method.java:606)
at org.springframework.aop.support.AopUtils.invokeJoinpointUsingReflection(AopUtils.java:319)
at org.eclipse.gemini.blueprint.service.importer.support.internal.aop.ServiceInvoker.doInvoke(ServiceInvoker.java:56)
at org.eclipse.gemini.blueprint.service.importer.support.internal.aop.ServiceInvoker.invoke(ServiceInvoker.java:60)
at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:172)
at org.springframework.aop.support.DelegatingIntroductionInterceptor.doProceed(DelegatingIntroductionInterceptor.java:131)
at org.springframework.aop.support.DelegatingIntroductionInterceptor.invoke(DelegatingIntroductionInterceptor.java:119)
at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:172)
at org.eclipse.gemini.blueprint.service.importer.support.LocalBundleContextAdvice.invoke(LocalBundleContextAdvice.java:57)
at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:172)
at org.springframework.aop.support.DelegatingIntroductionInterceptor.doProceed(DelegatingIntroductionInterceptor.java:131)
at org.springframework.aop.support.DelegatingIntroductionInterceptor.invoke(DelegatingIntroductionInterceptor.java:119)
at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:172)
at org.springframework.aop.framework.JdkDynamicAopProxy.invoke(JdkDynamicAopProxy.java:202)
to com.sun.proxy. $Proxy232.getErrorStack (unknown Source)
at sun.reflect.NativeMethodAccessorImpl.invoke0 (Native Method)
at sun.reflect.NativeMethodAccessorImpl.invoke(NativeMethodAccessorImpl.java:57)
at sun.reflect.DelegatingMethodAccessorImpl.invoke(DelegatingMethodAccessorImpl.java:43)
at java.lang.reflect.Method.invoke(Method.java:606)
at flex.messaging.services.remoting.adapters.JavaAdapter.invoke(JavaAdapter.java:418)
... 56 omitted common images
I tried to restart the vcenter services and received the error
Then I tried to start vcenter sevice
Once I rebooted two virtual machines (vCenter and PSC) it works short time (about 2-3 days).
Who knows how to solve this problem?
Hi KissTobor,
I solved my problem, but it was different in my case.
In vsphere web clients log I found massaes something like this "psc.test.local don't answer."
I try ping psc.test.local, result was compensate, DNS name has not solved. As a result, I found that I can't ping my domen controller. Problem was in my network, routing did not work well.
Thanks for trying to help me.
-
ORA-12518: TNS:listener could not hand off client connection (DBD ERROR: OCIServerAttach)
Hi again,
I'm on my business management console and the database Instance and the headset shows the green arrow, but the connection of the Agent of the Forum shows a red arrow down and the error:
Status: failed
Details: ORA-12518: TNS:listener could not hand off client connection (DBD ERROR: OCIServerAttach)
My OraClrAgnt service is up and running (using winxp pro, oracle 11 g 2), I'm on my pc at home, all my ports are open (name of my machine's "abigail" and it's dmzhost)
Any suggestions to solve this error?
My Tnsnames ora file:
ABIGAIL =
(DESCRIPTION =
(ADDRESS_LIST =
(ADDRESS = (PROTOCOL = TCP) (HOST = ABIGAIL)(PORT = 1521))
)
(CONNECT_DATA =
(SERVICE_NAME = orcl.0.0.10)
)
)
LISTENER_ORCL =
(DESCRIPTION =
(ADDRESS_LIST =
(ADDRESS = (PROTOCOL = TCP) (HOST = ABIGAIL)(PORT = 1521))
)
(CONNECT_DATA =
(SID = ORCL)
)
)
RMAN =
(DESCRIPTION =
(ADDRESS = (PROTOCOL = TCP) (HOST = ABIGAIL)(PORT = 1521))
(CONNECT_DATA =
(SERVER = DEDICATED)
(SERVICE_NAME = rman.abigail)
)
)
My listener.ora
SID_LIST_LISTENER =
(SID_LIST =
(SID_DESC =
(SID_NAME = CLRExtProc)
(ORACLE_HOME = E:\app\abigail\product\11.2.0\dbhome_1)
(= Extproc PROGRAM)
(ENVS = "EXTPROC_DLLS=ONLY:E:\app\abigail\product\11.2.0\dbhome_1\bin\oraclr11.dll")
)
)
LISTENER =
(DESCRIPTION_LIST =
(DESCRIPTION =
(ADDRESS = (PROTOCOL = CIP)(KEY = EXTPROC1521))
(ADDRESS = (PROTOCOL = TCP) (HOST = ABIGAIL)(PORT = 1521))
)
)
ADR_BASE_LISTENER = E:\app\abigail
My SQLNET. ORA
SQLNET. AUTHENTICATION_SERVICES = (NTS)
NAMES. DIRECTORY_PATH = (EZCONNECT, TNSNAMES, LOCALHOST)
NAMES. TRACE_LEVEL = ADMIN
My alert file
< time msg = "2013-10 - T 10, 20: 47:02.687 - 04:00 ' org_id = 'oracle' id_comp = 'tnslsnr'"
type = 'UNKNOWN' level = '16' = host_id "ABIGAIL."
host_addr =': 1' >
< txt > 10 October 2013 20:47:01 * (CONNECT_DATA = (CID = (PROGRAM =)(HOST=__jdbc__) (USER = SYSTEM)) (SERVICE_NAME = orcl.0.0.10)) * (ADDRESS = (PROTOCOL = tcp (PORT = 38289))(HOST=127.0.0.1)) * establish * orcl.0.0.10 * 12518
< / txt >
< / msg >
< time msg = "2013-10 - T 10, 20: 47:02.687 - 04:00 ' org_id = 'oracle' id_comp = 'tnslsnr'"
type = 'UNKNOWN' level = '16' = host_id "ABIGAIL."
host_addr =': 1' >
< txt > TNS-12518: TNS:listener could not hand off client connection
AMT-12560: TNS:protocol adapter error
< / txt >
< / msg >
My listener status and services
LSNRCTL > status
Connection to (DESCRIPTION = (ADDRESS = (PROTOCOL = IPC) (KEY = EXTPROC1521)))
STATUS of the LISTENER
------------------------
Alias LISTENER
Version TNSLSNR for 32-bit Windows: Version 11.2.0.1.0 - Prod
ction
Start date October 10, 2013 22:47:58
Uptime 0 days 0 h 2 min 1 sec
Draw level off
Security ON: OS Local Authentication
SNMP OFF
Listener parameter File E:\app\abigail\product\11.2.0\dbhome_1\network\admin\l
istener.ora
E:\app\abigail\diag\tnslsnr\ABIGAIL\listener\ale log listener
rt\log. XML
Summary of endpoints listening...
(DESCRIPTION=(ADDRESS=(PROTOCOL=ipc)(PIPENAME=\\.\pipe\EXTPROC1521ipc)))
(DESCRIPTION = (ADDRESS = (PROTOCOL = tcp)(HOST=ABIGAIL) (PORT = 1521)))
Summary of services...
Service 'CLRExtProc' has 1 instance (s).
Instance of 'CLRExtProc', status UNKNOWN, has 1 operation for this service...
Service 'orcl.0.0.10' has 1 instance (s).
Instance "orcl", State LOAN, has 8 managers of this service...
The command completed successfully
LSNRCTL > services
Connection to (DESCRIPTION = (ADDRESS = (PROTOCOL = IPC) (KEY = EXTPROC1521)))
Summary of services...
Service 'CLRExtProc' has 1 instance (s).
Instance of 'CLRExtProc', status UNKNOWN, has 1 operation for this service...
Managers:
"DEDICATED" set up: 0 denied: 0
LOCAL SERVER
Service 'orcl.0.0.10' has 1 instance (s).
Instance "orcl", State LOAN, has 8 managers of this service...
Managers:
"D006" put in place: 0 denied: current: 0 0 max: 800 status: loan
DISPATCHER < machine: ABIGAIL, pid: 1312 >
(ADDRESS = (PROTOCOL =)(HOST=ABIGAIL) (PORT = 1060) CST)
"D005" put in place: 0 denied: 12 current: 0 max: 800 status: ready
DISPATCHER < machine: ABIGAIL, pid: 1288 >
(ADDRESS = (PROTOCOL =)(HOST=ABIGAIL) (PORT = 1061) CST)
"D004" put in place: 0 denied: 1 current: 1 max: 16383 State: loan
DISPATCHER < machine: ABIGAIL, pid: 1260 >
(ADDRESS = (PROTOCOL = tcp)(HOST=ABIGAIL) (PORT = 1063))
"D003" put in place: 0 denied: 1 current: 1 max: 16383 State: loan
DISPATCHER < machine: ABIGAIL, pid: 1140 >
(ADDRESS = (PROTOCOL = tcp (PORT = 1062))(HOST=ABIGAIL))
"D002" put in place: 0 denied: 1 current: 1 max: 16383 State: loan
DISPATCHER < machine: ABIGAIL, pid: 140 >
(ADDRESS = (PROTOCOL = tcp (PORT = 1059))(HOST=ABIGAIL))
"D001" put in place: 0 denied: 1 current: 1 max: 16383 State: loan
DISPATCHER < machine: ABIGAIL, pid: 1072 >
(ADDRESS = (PROTOCOL = tcp (PORT = 1057))(HOST=ABIGAIL))
"D000" put in place: 0 denied: 1 current: 1 max: 16383 State: loan
DISPATCHER < machine: ABIGAIL, pid: 748 >
(ADDRESS = (PROTOCOL = tcp (PORT = 1058))(HOST=ABIGAIL))
"DEDICATED" set up: 0 denied: 0 status: ready
LOCAL SERVER
The command completed successfully
I added this on my listener.ora
DIRECT_HANDOFF_TTC_LISTENER = OFF
Now it works!
Moral of the story, google is your friend lol. Thanks for replying tho!
-
installation of FF breaks Microsoft Application Virtualization Client with XULRunner error!
We have a document management major (Java-based) program to work. It works through virtualization: "C:\Program Files (x 86) \Microsoft Application Virtualization Client\sfttray.exe" / launch "Cosa 18.0.0.4752.
When I try to run the program once I installed FF I get a XULRunner error: error: platform version ' 18.0 ' is not compatible with minVersion > = 19.0.2 maxVersion < = 19.0.2.» After that, the program does any launch. When I uninstall FF, it works again. I installed as standard IE browser.
I tried to install XULRunner 19.0.2. But being a noob, rather, it does not appear to be installed as a program. And it shouldn't be part of FF offshore already? I have the latest version of FF! Operating system is Win7 64 b.
What should do? I think it's weird that client virtualization is suddenly pointing to the installation of FF.
I solved the problem! On a co-workers computer, I noticed the firefox.exe process. She has not installed ff. Apparently, the document management program is actually a full-screen, the package based on a browser, using FF.
When I installed FF 19.0.2 it conflicted with virtualization, running version 18. I lowered my install FF at 18.0. The document management program now embarks on a new tab, no errors.
-
Cisco's VPN IPSec client for LAN connectivity
I've looked through further discussions and were not able to find a clear answer on this, so I apologize if this is a duplicate question.
I have the client setup Cisco VPN on an ASA 5505 with tunneling split. I can connect to the VPN very well. I can access the internet fine. I can't get the LAN, however. I try to do a ping, telnet, rdp, etc devices on the side LAN of the firewall without a bit of luck. I have torn down and configure the VPN several times via the CLI and I even used various configurations by using the wizard, all this without a bit of luck. Any help would be appreciated.
ASA Version 8.2 (2)
!
hostname spp-provo-001-fwl-001
domain servpro.local
activate the F7n9M1BQr1HPy/zu encrypted password
F7n9M1BQr1HPy/zu encrypted passwd
no names
name 10.0.0.11 Exch-Srv
name 10.0.0.12 DRAC
name 10.0.0.10 DVR
!
interface Vlan1
nameif inside
security-level 100
the IP 10.0.0.1 255.255.255.0
!
interface Vlan2
nameif outside
security-level 0
ServPro PPPoE client vpdn group
IP address pppoe setroute
!
interface Vlan12
nameif Guest_Wireless
security-level 90
IP 10.10.0.1 address 255.255.255.0
!
interface Ethernet0/0
switchport access vlan 2
!
interface Ethernet0/1
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
!
interface Ethernet0/7
switchport access vlan 12
!
exec banner * only authorized access *.
exec banner * this system is the property of ServPro. Unplug IMMEDIATELY that you are not an authorized user. *
connection of the banner * only authorized access *.
connection of the banner * this system is the property of ServPro. Unplug IMMEDIATELY that you are not an authorized user. *
banner asdm * only authorized access *.
banner asdm * this system is the property of ServPro. Unplug IMMEDIATELY that you are not an authorized user. *
boot system Disk0: / asa822 - k8.bin
passive FTP mode
clock timezone STD - 7
clock to summer time recurring MDT
DNS lookup field inside
DNS server-group DefaultDNS
10.0.0.11 server name
Name-Server 8.8.8.8
domain servpro.local
DRACServices tcp service object-group
EQ port 5900 object
EQ object of the https port
EQ object Port 5901
object-group service Exch-SrvServices tcp
EQ port 587 object
port-object eq 993
port-object eq www
EQ object of the https port
port-object eq imap4
EQ Port pop3 object
EQ smtp port object
SBS1Services tcp service object-group
EQ port 3389 object
port-object eq www
EQ object of the https port
EQ smtp port object
outside_access_in list extended access permit tcp any host *. *. *. * object-group SrvServices Exch
outside_access_in list permits all icmp access *. *. *. * 255.255.255.248
capture a whole list of access allowed icmp
Servpro_splitTunnelAcl list standard access allowed 10.0.0.0 255.255.255.0
inside_nat0_outbound to access ip 10.0.0.0 scope list allow 255.255.255.0 172.16.10.0 255.255.255.240
inside_nat0_outbound list of allowed ip extended access any 172.16.10.0 255.255.255.240
guest_wireless_in list extended access permitted tcp a whole
guest_wireless_in of access allowed any ip an extended list
NO_NAT to access ip 10.0.0.0 scope list allow 255.255.255.0 10.10.0.0 255.255.255.0
pager lines 24
Enable logging
asdm of logging of information
Within 1500 MTU
Outside 1500 MTU
MTU 1500 Guest_Wireless
mask 172.16.10.1 - 172.16.10.14 255.255.255.240 IP local pool ServProDHCPVPN
no failover
ICMP unreachable rate-limit 1 burst-size 1
ASDM image disk0: / asdm - 625.bin
don't allow no asdm history
ARP timeout 14400
NAT-control
Global 1 interface (outside)
NAT (inside) 0-list of access inside_nat0_outbound
NAT (inside) 1 0.0.0.0 0.0.0.0
NAT (Guest_Wireless) 1 0.0.0.0 0.0.0.0
static (inside, outside) *. *. *. * 10.0.0.11 netmask 255.255.255.255
Access-group outside_access_in in interface outside
Access-group guest_wireless_in in the Guest_Wireless interface
Route outside 0.0.0.0 0.0.0.0 *. *. *. * 2 track 2
Timeout xlate 03:00
Timeout conn 01:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
Sunrpc timeout 0:10:00 h323 0:05:00 h225 mgcp from 01:00 0:05:00 mgcp-pat 0:05:00
Sip timeout 0:30:00 sip_media 0:02:00 prompt Protocol sip-0: 03:00 sip - disconnect 0:02:00
Timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
dynamic-access-policy-registration DfltAccessPolicy
AAA-server Exch-Srv Protocol nt
AAA-server Exch-Srv (inside) host 10.0.0.11
Timeout 5
auth-NT-PDC SRV EXCH
the ssh LOCAL console AAA authentication
AAA authentication LOCAL telnet console
AAA authentication http LOCAL console
LOCAL AAA authentication serial console
Enable http server
http server idle-timeout 10
http 10.0.0.0 255.255.255.0 inside
http 0.0.0.0 0.0.0.0 outdoors
redirect http outside 80
redirect http inside 80
No snmp server location
No snmp Server contact
Server enable SNMP traps snmp authentication linkup, linkdown cold start
monitor SLA 124
type echo protocol ipIcmpEcho 4.2.2.2 outside interface
NUM-package of 3
frequency 10
Annex monitor SLA 124 life never start-time now
Crypto ipsec transform-set ESP-AES-128-SHA aes - esp esp-sha-hmac
Crypto ipsec transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
Crypto ipsec transform-set ESP-DES-MD5 esp - esp-md5-hmac
Crypto ipsec transform-set ESP-AES-256-SHA 256 - aes - esp esp-sha-hmac
Crypto ipsec transform-set ESP-AES-128-MD5-esp - aes esp-md5-hmac
Crypto ipsec transform-set ESP-DES-SHA esp - esp-sha-hmac
Crypto ipsec transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
Crypto ipsec transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
Crypto ipsec transform-set ESP-3DES-MD5-esp-3des esp-md5-hmac
Crypto ipsec transform-set esp-SHA-ESP-3DES-3des esp-sha-hmac
life crypto ipsec security association seconds 28800
Crypto ipsec kilobytes of life - safety 4608000 association
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 pfs Group1 set
Crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 value transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA MD5-ESP-3DES ESP-DES-SHA ESP-DES-MD5
outside_map card crypto 65535-isakmp dynamic ipsec SYSTEM_DEFAULT_CRYPTO_MAP
outside_map interface card crypto outside
Crypto ca trustpoint ASDM_TrustPoint0
registration auto
name of the object CN = cisco.spprovo.com
ServPro key pair
Configure CRL
string encryption ca ASDM_TrustPoint0 certificates
certificate f642be4b
308202fc 308201e4 a0030201 020204f6 42be4b30 0d06092a 864886f7 0d 010105
311a 3018 05003040 06035504 03131163 6973636f 2e737070 726f766f 2e636f6d
31223020 06092 has 86 01090216 13636973 636f2e73 726f2e6c 65727670 4886f70d
6f63616c 31303034 30383230 35363232 30303430 35323035 5a170d32 301e170d
3632325a 3040311a 30180603 55040313 and 11636973 636f2e73 7070726f 766f2e63
6f6d3122 30200609 2a 864886 f70d0109 02161363 6973636f 2e736572 7670726f
2e6c6f63 616c 3082 0122300d 06092 has 86 01010105 00038201 0f003082 4886f70d
010a 0282 010100 has 5 b4646cde f981f048 efa54c8a 4ba4f51c 25471e01 459ea905
313ef490 72b4d853 4e95ab7d a8c1350e 5728dca6 a98c439e 2c12d219 06ee7209
9f2584d1 b2abf71c 31c0890f 3098533b 6bc3ad4b 3bcd8986 e70ca78e 07a749d6
ee4e0892 4fcb79b6 724f7012 9f42fc2f b80c17ed adb5d36b 67590061 453d9ae6
16583d 36 5a22b7c2 737fd705 94656f3f 578fb67f 79bd2a59 17522be3 d2386e22
2c62352f cda317b0 be805a04 76f19989 34031cbd a5fc62a7 1d9f52f3 00cf60b6
bbbdc4f0 fb651b82 b3e22a0a 718ff0b4 e213f4ac cdeb413b 9c4a47c3 9134d7a9
e8dcf2c5 c1cd4075 61d75e3a 475a17f1 2f955741 9ed2a8d6 c381eba3 247134e1
b5c33fac 7ae03d02 03010001 300 d 0609 2a 864886 05050003 82010100 f70d0101
156 5fde62c5 b4cbb0f4 0c61fab7 fae04399 27457ab7 9790c 3fac914d 70595db9
e69d3f19 3476dc51 32c885de b5904030 05624fe0 e8983e0a ab5527f3 8c5dd64a
1e1a6082 b6091657 8704c 539 a3c6be47 da2a871f 4fafe668 70db2c2b 573d47b2
7f3df02f c9d53a92 bcf5f518 9953e14c f957a6ca 279f9e9f ddbd2561 6e0503c2
ba59a165 055d697f dd028d00 5cc288c4 83ced827 9c82ef3e 7e67f2d2 6de573e3
42a0b6bf ef8d06ed cb9805f2 c38011d3 5263bc3f 5b68df7a bef36c40 8c5e33f3
26b02c27 63a9848c 8461738f cd19ae95 f059ee34 afe4bdbc 8d8d2335 751b 0621
65464b2c 4649779d 3ba01b69 8977 has 790 73815f8b 3c483f93 a5ca9685 04b6e18a
quit smoking
crypto ISAKMP allow outside
crypto ISAKMP policy 10
preshared authentication
3des encryption
sha hash
Group 2
life 86400
No encryption isakmp nat-traversal
!
Track 2 rtr 124 accessibility
Telnet 10.0.0.0 255.255.255.0 inside
Telnet timeout 10
SSH 10.0.0.0 255.255.255.0 inside
SSH 0.0.0.0 0.0.0.0 outdoors
SSH timeout 10
SSH version 2
Console timeout 10
VPDN group ServPro request dialout pppoe
VPDN group ServPro localname *
VPDN group ServPro ppp authentication pap
password username * VPDN * local store
dhcpd outside auto_config
!
dhcpd address 10.10.0.100 - 10.10.0.227 Guest_Wireless
dhcpd dns 8.8.8.8 4.2.2.2 interface Guest_Wireless
enable Guest_Wireless dhcpd
!
a basic threat threat detection
threat detection statistics
a statistical threat detection tcp-interception rate-interval 30 burst-400-rate average rate 200
NTP server 38.117.195.101 source outdoors
NTP server 72.18.205.157 prefer external source
SSL-trust outside ASDM_TrustPoint0 point
WebVPN
allow outside
SVC disk0:/anyconnect-win-2.3.0254-k9.pkg 1 image
enable SVC
tunnel-group-list activate
attributes of Group Policy DfltGrpPolicy
Protocol-tunnel-VPN IPSec l2tp ipsec svc webvpn
Servpro internal group policy
Group Policy attributes Servpro
Server DNS 10.0.0.11 value
Protocol-tunnel-VPN IPSec svc webvpn
Split-tunnel-policy tunnelspecified
value of Split-tunnel-network-list Servpro_splitTunnelAcl
SERVPRO.local value by default-field
servpro encrypted NtdaWcySmet6H6T0 privilege 15 password username
servpro username attributes
type of service admin
username, encrypted bHGJDrPmHaAZY/78 Integratechs password
tunnel-group Servpro type remote access
attributes global-tunnel-group Servpro
address pool ServProDHCPVPN
authentication-server-group LOCAL Exch-Srv
strategy-group-by default Servpro
tunnel-group Servpro webvpn-attributes
enable ServPro group-alias
IPSec-attributes tunnel-group Servpro
pre-shared key *.
!
class-map inspection_default
match default-inspection-traffic
!
!
type of policy-card inspect dns preset_dns_map
parameters
message-length maximum 512
Policy-map global_policy
class inspection_default
inspect the preset_dns_map dns
inspect the ftp
inspect h323 h225
inspect the h323 ras
inspect the rsh
inspect the rtsp
inspect esmtp
inspect sqlnet
inspect the skinny
inspect sunrpc
inspect xdmcp
inspect the sip
inspect the netbios
inspect the tftp
Review the ip options
inspect the icmp
!
global service-policy global_policy
context of prompt hostname
call-home
Profile of CiscoTAC-1
no active account
http https://tools.cisco.com/its/service/oddce/services/DDCEService destination address
email address of destination [email protected] / * /
destination-mode http transport
Subscribe to alert-group diagnosis
Subscribe to alert-group environment
Subscribe to alert-group monthly periodic inventory
monthly periodicals to subscribe to alert-group configuration
daily periodic subscribe to alert-group telemetry
Cryptochecksum:52bca254012b1b05cca7dfaa30d1c42a
: end
Most likely you are behind a router PAT when you are connected to the VPN, so please allow the following:
Crypto isakmp nat-traversal 30
-
SRX5308 IPsec Config Mode - [IKE] ERROR: no configuration is found for...
I have a real simple setup for Client-to-gateway VPN installation. Base tunnels seem to work fine, but when I try to install
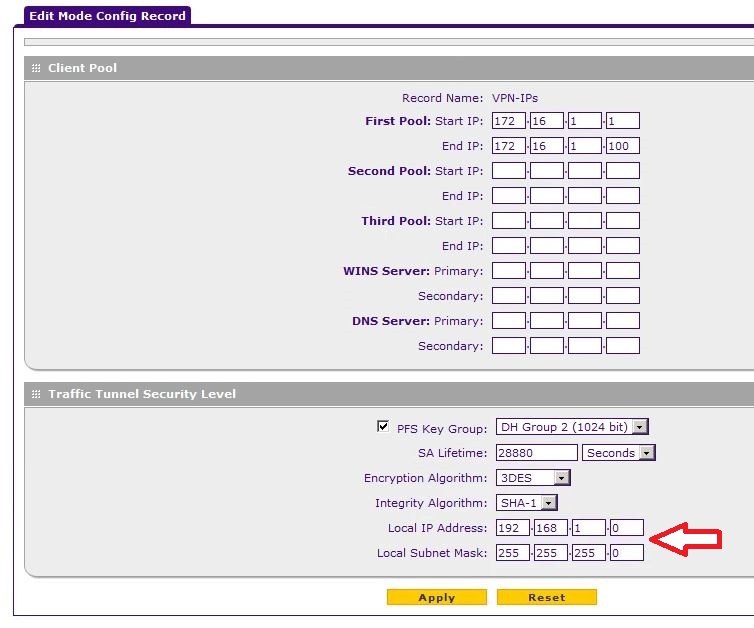
a policy of Mode Config I get an error in the connection and cannot ping resources on the local VPN network.
The local IP address at the end of check-in Mode Config is 192.168.1.0. The manual says to leave the field empty and it will default to the address of the gateway, which is 192.168.1.1. If I leave the field blank this wrong address gets automatically enrolled and if I try to manually enter the right one I get an error saying it's an invaild address?
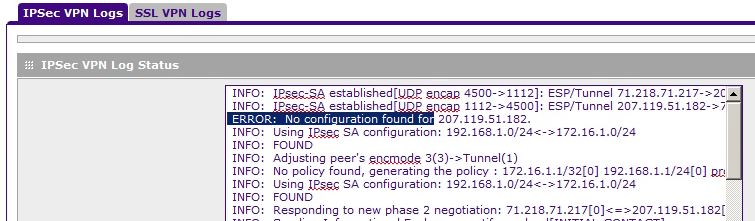
Then when I connect, I get the following error:
I think that is the question. How to work around this problem or do it properly? The manual is not any help and I googled my old brian dead.
Thanks for any idea that you can give me!
CC
Thanks for the reply okadis and thanks for the link to this site, it is very useful!
I was able to find a solution. Turns out that the works of very good firewall configuration. All I had to do was use the remote configuration of the CLIENT as the LAN address 192.168.1.0, and then everything worked.
Now, for me, it's 2 "bugs" in the SRX5308 of Mode Config record:
1 192.168.1.0 is not the address of the Local network subnet, it is 192.168.1.1; The manual says if left blank by default subnet LAN, which it isn't, it's default 192.168.1.0
2. it won't let you enter ANY ip address here. It must be left blank.
Maybe I'm missing something here, but it works perfectly after using what is there in the end customer.
Should have been simple. Well...
CC
-
Cisco HX system connection vSphere Client Web show error internal
I've been recently install HX system version 1.7.3 finishing
and connect on vSphere Web Client display error - internal
Could not load the module on /vshpere-client/pluginui/locales/StorvisorUi-zh_TW.swf resources
Version of vCenter is 6.0U2
Is - this mean no Chinese tranditional support?
Have you you successfully to redeploy your 1.7.3 cluster HX?
There is little cleanup that needed to be done in vCenter to erase the old information before re - deploy - such as remove the plugin the vCenter MOB and removal of the old cluster cluster HX
Maybe you are looking for
-
Need new keyboard for Satellite A500
I have a PC laptop toshiba Satellite A500-025 and I had a bit of water splashed on keyboard and some keys are no longer works. I was going to replace the keyboard. Mine was purchased in the Canada and has a bilingual English/french keyboard. I was wo
-
Aspire V5 - 552G crashes, what's next?
Hi, I was wondering if you could guide me in what I should do next. Recently, I decided to buy this laptop in August for College. http://www.Newegg.com/product/product.aspx?item=N82E16834314119 At first when I arrived it was very good and really work
-
I've never owned an HP so I am a little confused. Whenever I try to install the drivers from AMD, it never lists the display driver as one of the options to install. HP Pavilion HPE series Model no. H8-1214 AMD HD 7450 Windows 7 x 64
-
This error in executing the PowerCLI code belowEnvironment5.5 bUsing PowerCLI 5.5Do not use a custom certificate(1) tried to use passwords in clear text in the script (not my favorite)(2) tried to retype the password in the customization specificatio
-
I have Dreamweaver 2014.1.1 build 6982My computer is an iMac running Yosemite 10.10.3Whenever a file is opened, I get the following error message:"The following translators were not loaded due to errors: ASP.htm: has configuration information that is