Setting up VPN - RV042 v3 issues
Hi guys,.
I just bought a version of Cisco/Linksys RV042 3 and having difficulty getting my Macbook Pro running IPSecuritas to establish a VPN tunnel.
I get a message "Error - IKE - no message should be encrypted" in the journal of connection IPSecuritas. It will keep retrying which results in the same error. Finally, it gives just straight up.
I'm sure that I have the settings on the router and configured in the same way Macbook of VPN end.
Here is a screenshot of the RV042 configuration page. Any input would be greatly appreciated, thanks:

Hello.
These products are processed by the Cisco Small Business Support Community.
* If my post answered your question, please mark it as "acceptable Solution".
Thank you!
Tags: Linksys Routers
Similar Questions
-
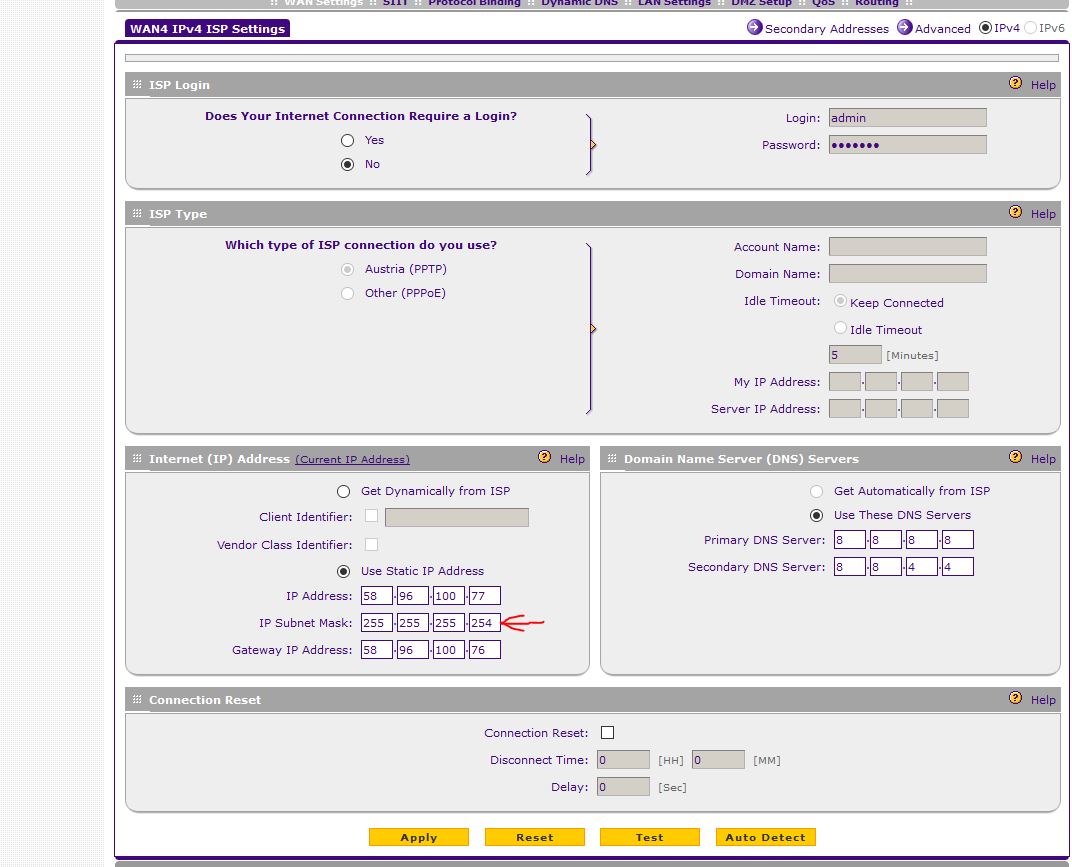
I can't add/subnet mask 31 255.255.255.254 ISP WAN > static IP setting in VPN Firewall SRX5308
Hello
I can't add/subnet mask 31 255.255.255.254 ISP WAN > static IP setting in VPN Firewall SRX5308. When I try to apply it, I get the popup error message like "invalid IP subnet mask. Please enter 0/128/192/224/240/248/252 for octet 4 ". I try to add provider NTU fiber optic internet service in one of the 4 WAN settings. The vendor gave me a 31 block IP and the subnet as 255.255.255.254 mask. It is a limitation in this firewall? I have to ask the provider to give me a 30 block the IP instead? With 30 block IP subnet mask will be 255.255.255.252 who is authorized by this firewall setting. I tried this on another (SnapGear SG560) firewall and it works without any problem. See the screenshots below. Can someone please?
concerning
Ridwan
/ 31 would be used in specific scenarios where you * really * need to keep the address space and on links only point to point. To be honest I've never met anyone, or any ISP that uses it. It works on point to point, because, well, there no need to broadcast address because there are only two devices on the link (one on each side of the cable)... IP address ranges would be;. 0-. 1,.2-. 3, etc.
Most (if not all) Netgear devices will prevent you from setting 31, but you will probably be able to use without problem in all 30 cases, according to the setup of the ISP I do not think that it would cause you problems really. But if you can, I would certainly ask a 30 instead.
-
new to InDesign 6 months I do a newspaper page layout every two weeks. This time, when I opened my model, set up for the next issue, when I typed "W" to display the grid, I have something I never saw elsewhere. ". The background was filled with a new grid of tiles rather than the void behind the newspaper that I'm used to seeing. I don't know what happened, but it seems that Adobe has tinkered once more with the program. The last time this happened, I lost the icon "cover the columns" at the top; now, it's a case of two steps to put the head-lines across more than one column. NOT useful.
There is probably a command or a term, I don't know that this right but my main question is why, when I did this dozens of times before, doing something different will come this time. (I know, without replica.)
I'd also appreciate comments that someone out there could offer re why now when I tap on InDesign, is there a slight pause before that something happens to the screen. What is my new Mac, or something to do with the program that I can fix it?
Thanks, Sacie
It looks like the grid of the document, which can be disabled in the view menu.
-
How to set the VPN connection in Windows 7 64 bit?
Hello
How can I set up a Vpn connection in Windows 7 x 64 bit.
Thank you.
Hello
Go to the network control panel and Internet-network sharing Center.
http://www.windows7hacker.com/index.php/2009/08/how-to-set-up-a-VPN-connection-in-Windows-7/
Note that you need to know the login and the password to access the Internet :)
-
Wireless and VPN RV042 router WRT54G
Respected member, please help if you can! I have an ADSL with dynamic connected with the wrt54g router, I recently bought RV042 and want to connect the wire coming from wireless with ports. so, basically, I want to use RV042VPN for help after the router, is there a way I can use vpn behind with port using RV042 router wireless
I can't be able to connect to the vpn as he seeks is not an ip or WAN/LAN.
It may be possible if you're lucky. But I highly recommend not to connect the RV042 after the WRT. A VPN server must always have a public IP address. Running a VPN server behind a router NAT (such as WRT) makes it extremely difficult and often it won't work at all. Connect the RV042 directly to your modem, configure it to your internet connection. In this way the RV042 has the public IP and VPN should become much easier. Then implement the WRT as simple access point in your network by changing the address LAN IP of 192.168.1.1 to 192.168.1.2, disable the DHCP server, and connect a LAN port of the WRT on a LAN on the RV042 port.
-
I have the router RV042 at the regional office in Smart Backup link with 2 ISP mode. Is it possible to switch the VPN Tunnel automatically to secondary, when WAN router turned on at WAN side?
Thanks for the cooperation
VPN backup feature you requested is currently supported by RV082, not RV042.
-
Recently, I have set up a 1721 running IOS c1700-k9o3sy7 - mz.122 - 15.T5.bin
This router terminated a VPN with another router, a 1721 with the exact same version of IOS. This router has initially been connected via a WAN link on eth0 wireless. We moved their on a t1 as the main interface with the wireless as a backup. Then we had to
-Configure a loopback - its ip address device would end the vpn
-make the source of the vpn packages come from the loop
-Configure static routes w / higher administrative distance
Do all this we tested VPN - they worked. Unplugged at t1 connection and traffic moves on the wireless. We checked the vpn clients could connect. Everything worked ok...
Except when you move large files between hosts behind fa0 via the vpn to the guests at the bottom. To prove the vpn worked and routing was in place, we could telnet from a host behind fa0 via the vpn to a remote host and you connect... Then, we would try an ftp files more. We could connect to the ftp server BUT once a file transfer started things would hang.
We opened a Cisco tac case and it turned out that the addition of
IP tcp adjust-mss 1300
the interface fa0 fixed all - file transfer worked.
My question why would be reduced aid package size? The vpn add some packages generals cauing more large packages to remove?
A clue was here, BUT it's PPPoE - no VPN...
I'm looking to explain why this reduced MTU size worked. I would of never figured this out on my own...
Here's the running-config, we used. Don't forget that everything worked (switching between WAN, vpn, NAT connectivity link) except the transfer of files and when large amounts of data was pushed over the line as MS-sharing files/printers, emails with attachments (a few hundred k). The only change is a line at the fa0 interface.
version 12.2
horodateurs service debug uptime
Log service timestamps uptime
encryption password service
!
hostname HPARFD
!
queue logging limit 100
logging buffered debugging 8192
enable secret 5
enable password 7
!
abc username password
clock timezone CST - 6
clock to summer time recurring CDT
AAA new-model
!
!
AAA authentication login userauthen local
AAA authorization groupauthor LAN
AAA - the id of the joint session
IP subnet zero
!
!
no ip domain search
IP domain name blahblah.net
IP-name server
IP-name server
!
audit of IP notify Journal
Max-events of po verification IP 100
property intellectual ssh time 60
!
!
!
!
crypto ISAKMP policy 1
md5 hash
preshared authentication
!
crypto ISAKMP policy 2
md5 hash
preshared authentication
!
crypto ISAKMP policy 3
BA 3des
preshared authentication
Group 2
!
crypto ISAKMP policy 10
md5 hash
preshared authentication
test3030 key crypto isakmp address
No.-xauth ISAKMP crypto key address 0.0.0.0 test3131 0.0.0.0
crypto ISAKMP client configuration address pool local ourpool
!
ISAKMP crypto client configuration group whatever
key
pool ourpool
ACL 101
!
!
Crypto ipsec transform-set esp - esp-md5-hmac rptset
Crypto ipsec transform-set esp - esp-md5-hmac trans2
Crypto ipsec transform-set esp-3des esp-md5-hmac v35clientset
!
Crypto-map dynamic dynmap 10
Set transform-set v35clientset
Crypto-map dynamic dynmap 20
Set transform-set trans2
!
!
card crypto rtp-address Loopback0
crypto isakmp authorization list groupauthor rtp map
client configuration address card crypto rtp initiate
client configuration address card crypto rtp answer
RTP 1 ipsec-isakmp crypto map
defined by peers
Set transform-set rptset
match address 115
map rtp 50-isakmp ipsec crypto dynamic dynmap
!
!
!
!
interface Loopback0
Description loopback address is NOT dependent on any physical interface
IP 255.255.255.255
no ip proxy-arp
NAT outside IP
No cutting of the ip horizon
!
interface Ethernet0
secondary description - wireless WAN link
255.255.255.252 IP address no ip proxy-arp
NAT outside IP
No cutting of the ip horizon
Half duplex
crypto rtp map
!
interface FastEthernet0
Description connected to EthernetLAN
IP
255.255.255.0 no ip proxy-arp
IP tcp adjust-mss 1300
^ ^ ^ Tac added cisco work around
IP nat inside
automatic speed
!
interface Serial0
first link description WAN - t1
255.255.255.252 IP address no ip proxy-arp
NAT outside IP
random detection
crypto rtp map
!
router RIP
version 2
passive-interface Loopback0
passive-interface Serial0
passive-interface Ethernet0
network
No Auto-resume
!
IP local pool ourpool
IP nat inside source overload map route sheep interface Loopback0
IP classless
IP route 0.0.0.0 0.0.0.0 Serial0
IP route 0.0.0.0 0.0.0.0 Ethernet0
IP route
255.255.255.0 Serial0 IP route
255.255.255.0 Ethernet0 200 IP route
255.255.255.0 Serial0 IP route
255.255.255.0 Ethernet0 200 IP route
255.255.255.0 Serial0 IP route
255.255.255.0 Ethernet0 200 no ip address of the http server
no ip http secure server
!
!
!
remote_access extended IP access list
permit tcp any any eq 22
permit tcp
0.0.0.255 any eq telnet TCP refuse any any eq telnet
allow an ip
!
access-list 1 permit
0.0.0.255 access-list 100 permit ip 192.168.0.0
0.0.0.255 host access-list 100 permit ip 192.168.0.0
0.0.0.255 host access-list 100 permit ip 192.168.0.0
0.0.0.255 host access-list 101 permit ip
0.0.0.255 10.2.1.0 0.0.0.255 access-list 101 permit ip 192.168.0.0 0.0.255.255 10.2.1.0 0.0.0.255
access-list 199 permit tcp a whole Workbench
access-list 199 permit udp any one
access-list 199 permit esp a whole
access-list 199 permit ip 192.168.0.0 0.0.0.255
0.0.0.255 !
sheep allowed 10 route map
corresponds to the IP 110
!
Enable SNMP-Server intercepts ATS
RADIUS server authorization allowed missing Type of service
alias exec sv show version
alias exec sr show running-config
alias exec ss show startup-config
alias con exec conf t
top alias show proc exec
alias exec br show ip brief inter
!
Line con 0
exec-timeout 0 0
password 7
line to 0
line vty 0 4
exec-timeout 0 0
password 7
Synchronous recording
transport input telnet ssh rlogin udptn stream
!
NTP-period clock 17180059
NTP server
end
You can check the following site for more explanation:
http://www.Cisco.com/en/us/Tech/tk827/tk369/technologies_tech_note09186a0080093f1f.shtml
HTH...
-
How to set up VPN on the router via ASA5505 2811
Hello everyone
I apologize for the possible triviality of my question. The current configuration of our society considers appropriate for the edge, two ASA5505 below that are installed two routers configured with the CCME 2811 Express. When the two AS5505 is configured a VPN connection for the transmission of data in our network traffic. Given the presence of several public addresses available on our two sites, I was wondering if you could (and if so, how) to set up a VPN between two routers 2811, except that when existing data traffic, dedicated exclusively to the voice traffic. It give me a document that teach me how can I solve my problem?
Thank you very much
Damiano,
If you want an IPsec VPN for only separate voice and termination traffic on routers, there are several possibilities. Especially if you have a spare IP addresses:
IPsec VPN endpoints on the routers.
GRE over IPsec routers ending (gives you that soften what and where can be routed, in particular, identify voice traffic)
Termination of free WILL on the routers and unloading IPsec to ASAs. (Benefit of the foregoing + ASAs making encryption).
There is no problem to close the tunnels through the ASA, the only warning is that even in the case of static NAT you should probably use NAT-Traversal.
Marcin
-
IPSEC VPN tunnel on issue of Zonebased Firewall
Help, please!
I'm trying to configure a router lab ISR1921 to build the VPN tunnel with vmware vshield edge. The configuration of the 1921 is pasted below. There is not a lot of adjustment on the side of vshield really and I'm sure both sides are adapting to phase 1 & 2.
The question I have: the tunnel can be built correctly and I also see from show crypto ipsec release encap and decap counters. However the devices on each side can communicate. That said, I can ping from 1921 to the IP of the internal interface of the vshield with IP source specified. But just no communication part and other...
I did debugs and only "error" messages are:
01:58:03.193 20 February: ISAKMP: (1001): error suppression node 1656104565 FALSE reason 'informational (in) State d1.
...
01:58:03.193 20 February: ISAKMP: (1001): purge the node-1657220080
I hope that I did a stupid thing to configure error, but I spent too much time on it. It is supposed to be a really simple installation... Please help!
!
version 15.4
horodateurs service debug datetime msec
Log service timestamps datetime msec
no password encryption service
!
Lab-1900 host name
!
boot-start-marker
boot system flash: c1900-universalk9-mz. Spa. 154 - 1.T1.bin
boot system flash: c1900-universalk9-mz. Spa. 151 - 4.M7.bin
boot system flash: c1900-universalk9-mz. Spa. 150 - 1.M4.bin
boot-end-marker
!
AAA new-model
!
AAA authentication login default local
authorization AAA console
AAA authorization exec default local
!
AAA - the id of the joint session
clock timezone AST - 4 0
clock to summer time recurring ADT 3 Sun Mar 2 Sun Nov 02:00 02:00
!
DHCP excluded-address IP 192.168.100.1 192.168.100.40
!
dhcp DHCPPOOL IP pool
import all
network 192.168.100.0 255.255.255.0
LAB domain name
DNS 8.8.8.8 Server 4.2.2.2
default router 192.168.100.1
4 rental
!
Laboratory of IP domain name
8.8.8.8 IP name-server
IP-server names 4.2.2.2
inspect the IP log drop-pkt
IP cef
No ipv6 cef
!
type of parameter-card inspect global
Select a dropped packet newspapers
Max-incomplete 18000 low
20000 high Max-incomplete
Authenticated MultiLink bundle-name Panel
!
redundancy
!
property intellectual ssh version 2
!
type of class-card inspect entire game ESP_CMAP
match the name of group-access ESP_ACL
type of class-card inspect the correspondence SDM_GRE_CMAP
match the name of group-access GRE_ACL
type of class-card inspect entire game PAC-cls-icmp-access
match icmp Protocol
tcp protocol match
udp Protocol game
type of class-card inspect correspondence sdm-cls-VPNOutsideToInside-13
game group-access 154
class-card type check ALLOW-VPN-TRAFFIC-OUT match-all
match the ALLOW-VPN-TRAFFIC-OUT access group name
type of class-card inspect entire game PAC-cls-insp-traffic
match Protocol pptp
dns protocol game
ftp protocol game
https protocol game
match icmp Protocol
match the imap Protocol
pop3 Protocol game
netshow Protocol game
Protocol shell game
match Protocol realmedia
match rtsp Protocol
smtp Protocol game
sql-net Protocol game
streamworks Protocol game
tftp Protocol game
vdolive Protocol game
tcp protocol match
udp Protocol game
http protocol game
type of class-card inspect entire game AH_CMAP
match the name of group-access AH_ACL
inspect the class-map match ALLOW VPN TRAFFIC type
match the ALLOW-VPN-TRAFFIC-OUT access group name
type of class-card inspect correspondence ccp-invalid-src
game group-access 126
type of class-card inspect entire game PAC-insp-traffic
corresponds to the class-map PAC-cls-insp-traffic
type of class-card inspect entire game SDM_VPN_TRAFFIC
match Protocol isakmp
match Protocol ipsec-msft
corresponds to the AH_CMAP class-map
corresponds to the ESP_CMAP class-map
type of class-card inspect correspondence ccp-icmp-access
corresponds to the class-ccp-cls-icmp-access card
type of class-card inspect the correspondence SDM_VPN_PT
game group-access 137
corresponds to the SDM_VPN_TRAFFIC class-map
!
type of policy-card inspect self-out-pmap
class type inspect PCB-icmp-access
inspect
class class by default
Pass
policy-card type check out-self-pmap
class type inspect SDM_VPN_PT
Pass
class class by default
Drop newspaper
policy-card type check out-pmap
class type inspect PCB-invalid-src
Drop newspaper
class type inspect ALLOW VPN TRAFFIC OUT
inspect
class type inspect PCB-insp-traffic
inspect
class class by default
Drop newspaper
policy-card type check out in pmap
class type inspect sdm-cls-VPNOutsideToInside-13
inspect
class class by default
Drop newspaper
!
security of the area outside the area
safety zone-to-zone
safety zone-pair zp-self-out source destination outside zone auto
type of service-strategy inspect self-out-pmap
safety zone-pair zp-out-to source out-area destination in the area
type of service-strategy check out in pmap
safety zone-pair zp-in-out source in the area of destination outside the area
type of service-strategy inspect outside-pmap
source of zp-out-auto security area outside zone destination auto pair
type of service-strategy check out-self-pmap
!
crypto ISAKMP policy 1
BA 3des
preshared authentication
Group 2
ISAKMP crypto key iL9rY483fF address 172.24.92.103
!
Crypto ipsec transform-set esp-SHA-ESP-3DES-3des esp-sha-hmac
tunnel mode
!
IPSEC_MAP 1 ipsec-isakmp crypto map
Tunnel Sandbox2 description
defined by peer 172.24.92.103
Set security-association second life 28800
game of transformation-ESP-3DES-SHA
PFS group2 Set
match address 150
!
the Embedded-Service-Engine0/0 interface
no ip address
Shutdown
!
interface GigabitEthernet0/0
WAN description
IP 172.24.92.18 255.255.255.0
NAT outside IP
No virtual-reassembly in ip
outside the area of security of Member's area
automatic duplex
automatic speed
No mop enabled
card crypto IPSEC_MAP
Crypto ipsec df - bit clear
!
interface GigabitEthernet0/1
LAN description
IP 192.168.100.1 address 255.255.255.0
IP nat inside
IP virtual-reassembly in
Security members in the box area
automatic duplex
automatic speed
!
IP forward-Protocol ND
!
IP http server
access-class 2 IP http
local IP http authentication
IP http secure server
!
IP nat inside source map route RMAP_4_PAT interface GigabitEthernet0/0 overload
IP route 0.0.0.0 0.0.0.0 172.24.92.254
!
AH_ACL extended IP access list
allow a whole ahp
ALLOW-VPN-TRAFFIC-OUT extended IP access list
IP 192.168.100.0 allow 0.0.0.255 192.168.1.0 0.0.0.255
ESP_ACL extended IP access list
allow an esp
TELNET_ACL extended IP access list
permit tcp any any eq telnet
!
allowed RMAP_4_PAT 1 route map
corresponds to the IP 108
!
1snmp2use RO SNMP-server community
access-list 108 deny ip 192.168.100.0 0.0.0.255 192.168.1.0 0.0.0.255
access-list 108 allow ip 192.168.100.0 0.0.0.255 any
access-list 126 allow the ip 255.255.255.255 host everything
access-list 126 allow ip 127.0.0.0 0.255.255.255 everything
access-list 137 allow ip 172.24.92.0 0.0.0.255 any
access-list 150 permit ip 192.168.100.0 0.0.0.255 192.168.1.0 0.0.0.255
access-list 154 allow ip 192.168.1.0 0.0.0.255 192.168.100.0 0.0.0.255
!
control plan
!
Line con 0
exec-timeout 0 0
Synchronous recording
line to 0
line 2
no activation-character
No exec
preferred no transport
transport output pad rlogin lapb - your MOP v120 udptn ssh telnet
StopBits 1
line vty 0 4
access-class TELNET_ACL in
exec-timeout 0 0
Synchronous recording
transport of entry all
line vty 5 15
access-class TELNET_ACL in
exec-timeout 0 0
Synchronous recording
transport of entry all
!
Scheduler allocate 20000 1000
0.ca.pool.ntp.org server NTP prefer
1.ca.pool.ntp.org NTP server
!
end
NAT looks fine.
Please create an ACL with bidirecctional ACEs and add it as a group of access to the interface of penetration:
IP access-list extended 180
IP 192.168.100.0 allow 0.0.0.255 192.168.1.0 0.0.0.255 connect
ip permit 192.168.1.0 0.0.0.255 192.168.100.0 0.0.0.255 connect
allow an ip
interface GigabitEthernet0/1
IP access-group 180 to
IP access-group out 180
Generer generate traffic, then run the command display 180 access lists .
Also, if possible activate debug ip icmp at the same time.
Share the results.
Thank you
-
MY problem is that when the vpn is configured, and I try to run a tracert to one of my remote PC across the VPN, the VPN router sends information from the internet and do not attempt to open the tunnel. what I am doing wrong?
I use a cisco router 1700 and connect to a vpn concentrator 3030 Cisco
Current configuration: 1522 bytes
!
version 12.3
horodateurs service debug datetime msec
Log service timestamps datetime msec
encryption password service
!
router host name
!
boot-start-marker
boot-end-marker
!
enable secret 5
!
MMI-60 polling interval
No mmi self-configuring
No pvc mmi
MMI snmp-timeout 180
No aaa new-model
IP subnet zero
!
!
!
IP cef
Max-events of po verification IP 100
!
!
crypto ISAKMP policy 9
BA 3des
md5 hash
preshared authentication
Group 2
ISAKMP crypto key (shared key) (peer IP address)
!
86400 seconds, duration of life crypto ipsec security association
!
Crypto ipsec transform-set esp-3des esp-md5-hmac TS1
!
crypmap 1 ipsec-isakmp crypto map
defined peer (IP ADDRESS of the peer)
game of transformation-TS1
match address 101
!
!
!
interface Ethernet0
IP (IP ADDRESS)
NAT outside IP
Half duplex
crypmap card crypto
!
interface FastEthernet0
IP (IP ADDRESS)
IP nat inside
automatic speed
!
the IP nat inside source 1 interface Ethernet0 overload list
IP classless
IP route 0.0.0.0 0.0.0.0 (default router)
no ip address of the http server
no ip http secure server
!
!
access-list 1 permit one
access-list 101 permit ip host (LOCALHOST using NAT) host (the remote host 1)
access-list 101 permit ip host (LOCALHOST using NAT) host (remote host 2)
access-list 101 permit ip host (LOCALHOST using NAT) host (the remote host 3)
access-list 101 permit ip host (LOCALHOST using NAT) host (the remote host 4)
!
!
Line con 0
line to 0
line vty 0 4
7 PASSWORD password
opening of session
!
end
Hi Jim
You must change the access list statement also the declaration of overloaded nat...
You must deny traffic between 2 vpn networks is natted...
You can check the below link configuration to the top of the same...
http://www.Cisco.com/en/us/Tech/tk583/TK372/technologies_configuration_example09186a008009448f.shtml
regds
-
Newbie Help Needed: Cisco 1941 router site to site VPN traffic routing issue
Hello
Please I need help with a VPN site-to site, I installed a router Cisco 1941 and a VPN concentrator based on Linux (Sophos UTM).
The VPN is established between them, but I can't say the cisco router to send and receive traffic through the tunnel.
Please, what missing am me?
A few exits:
ISAKMP crypto to show her:
isakmp crypto #show her
IPv4 Crypto ISAKMP Security Association
DST CBC conn-State id
62.173.32.122 62.173.32.50 QM_IDLE 1045 ACTIVE
IPv6 Crypto ISAKMP Security Association
Crypto ipsec to show her:
Interface: GigabitEthernet0/0
Tag crypto map: QRIOSMAP, local addr 62.173.32.122
protégé of the vrf: (none)
local ident (addr, mask, prot, port): (192.168.20.0/255.255.255.0/0/0)
Remote ident (addr, mask, prot, port): (192.168.2.0/255.255.255.0/0/0)
current_peer 62.173.32.50 port 500
LICENCE, flags is {origin_is_acl},
#pkts program: encrypt 0, #pkts: 0, #pkts digest: 0
#pkts decaps: 52, #pkts decrypt: 52, #pkts check: 52
compressed #pkts: 0, unzipped #pkts: 0
#pkts uncompressed: 0, #pkts compr. has failed: 0
#pkts not unpacked: 0, #pkts decompress failed: 0
Errors #send 0, #recv 0 errors
local crypto endpt. : 62.173.32.122, remote Start crypto. : 62.173.32.50
Path mtu 1500, mtu 1500 ip, ip mtu IDB GigabitEthernet0/0
current outbound SPI: 0x4D7E4817 (1300121623)
PFS (Y/N): Y, Diffie-Hellman group: group2
SAS of the esp on arrival:
SPI: 0xEACF9A (15388570)
transform: esp-3des esp-md5-hmac.
running parameters = {Tunnel}
Conn ID: 2277, flow_id: VPN:277 on board, sibling_flags 80000046, crypto card: QRIOSMAP
calendar of his: service life remaining (k/s) key: (4491222/1015)
Size IV: 8 bytes
support for replay detection: Y
Status: ACTIVE
Please see my config:
crypto ISAKMP policy 1
BA 3des
md5 hash
preshared authentication
Group 2
encryption... isakmp key address 62.X.X... 50
ISAKMP crypto keepalive 10 periodicals
!
!
Crypto ipsec transform-set esp-3des esp-md5-hmac TS-QRIOS
!
QRIOSMAP 10 ipsec-isakmp crypto map
peer 62.X.X set... 50
transformation-TS-QRIOS game
PFS group2 Set
match address 100
!
!
!
!
!
interface GigabitEthernet0/0
Description WAN CONNECTION
62.X.X IP... 124 255.255.255.248 secondary
62.X.X IP... 123 255.255.255.248 secondary
62.X.X IP... 122 255.255.255.248
NAT outside IP
IP virtual-reassembly in
automatic duplex
automatic speed
card crypto QRIOSMAP
!
interface GigabitEthernet0/0.2
!
interface GigabitEthernet0/1
LAN CONNECTION description $ES_LAN$
address 192.168.20.1 255.255.255.0
IP nat inside
IP virtual-reassembly in
automatic duplex
automatic speed
!
IP nat pool mypool 62.X.X... ... Of 122 62.X.X 122 30 prefix length
IP nat inside source list 1 pool mypool overload
overload of IP nat inside source list 100 interface GigabitEthernet0/0
!
access-list 1 permit 192.168.20.0 0.0.0.255
access-list 2 allow 10.2.0.0 0.0.0.255
Note access-list 100 category QRIOSVPNTRAFFIC = 4
Note access-list 100 IPSec rule
access-list 100 permit ip 192.168.20.0 0.0.0.255 192.168.2.0 0.0.0.255
access-list 101 permit esp 62.X.X host... 50 62.X.X host... 122
access list 101 permit udp host 62.X.X... 50 62.X.X... host isakmp EQ. 122
access-list 101 permit ahp host 62.X.X... 50 62.X.X host... 122
access-list 101 deny ip any any newspaper
access-list 110 deny ip 192.168.20.0 0.0.0.255 192.168.2.0 0.0.0.255
access-list 110 permit ip 192.168.20.0 0.0.0.255 any
!
!
!
!
sheep allowed 10 route map
corresponds to the IP 110
The parts of the configuration you posted seem better than earlier versions of the config. The initial problem was that traffic was not in the VPN tunnel. That works now?
Here are the things I see in your config
I don't understand the relationship of these 2 static routes by default. It identifies completely the next hop and a mask the bytes of Middleweight of the next hop. Sort of, it seems that they might be the same. But if they were the same, I don't understand why they both make their appearance in the config. Can provide you details?
IP route 0.0.0.0 0.0.0.0 62.X.X... 121
IP route 0.0.0.0 0.0.0.0 62.172.32.121
This static route implies that there is another network (10.2.0/24) connected through the LAN. But there is no other reference to it and especially not for this translation. So I wonder how it works?
IP route 10.2.0.0 255.255.255.0 192.168.20.2
In this pair of static routes, the second route is a specific subnet more and would be included in the first and routes for the next of the same break. So I wonder why they are there are. There is not necessarily a problem, but is perhaps something that could be cleaned up.
IP route 172.17.0.0 255.255.0.0 Tunnel20
IP route 172.17.2.0 255.255.255.0 Tunnel20
And these 2 static routes are similar. The second is a more precise indication and would be included in the first. And it is referred to the same next hop. So why have the other?
IP route 172.18.0.0 255.255.0.0 Tunnel20
IP route 172.18.0.0 Tunnel20 255.255.255.252
HTH
Rick
-
I'm tring to define you Site IPSEC to a VPN of Site connection a md seem to run into problems. Can someone look over my setup and lead me in the right direction:

#sh ROUTER1 card crypto
'TOWIFE' 1-isakmp ipsec crypto map
Peer = 10.2.2.1
Expand the access list IP HusbandToWife
HusbandToWife 192.168.1.0 ip access list allow 0.0.0.255 192.168.3.0 0.0.0.255
Current counterpart: 10.2.2.1
Life safety association: 4608000 Kbytes / 3600 seconds
PFS (Y/N): N
Transform sets = {}
3DESHMAC,
}
Interfaces using crypto card TOWIFE:
FastEthernet0/0ROUTER1 #sh running-config
Building configuration...Current configuration: 1027 bytes
!
version 12.4
horodateurs service debug datetime msec
Log service timestamps datetime msec
no password encryption service
!
ROUTER1 hostname
!
boot-start-marker
boot-end-marker
!
!
No aaa new-model
memory iomem size 5
IP cef
!
!
!
!
!
Authenticated MultiLink bundle-name Panel
!
!
!
!
!
Archives
The config log
hidekeys
!
!
crypto ISAKMP policy 1
preshared authentication
address of spike key crypto isakmp 10.2.2.1
!
!
Crypto ipsec transform-set esp-3des esp-sha-hmac 3DESHMAC
!
TOWIFE 1 ipsec-isakmp crypto map
defined peer 10.2.2.1
Set transform-set 3DESHMAC
match address HusbandToWife
!
!
!
!
!
!
interface FastEthernet0/0
10.1.1.1 IP address 255.255.255.0
automatic duplex
automatic speed
card crypto TOWIFE
!
interface FastEthernet0/1
IP 192.168.1.1 255.255.255.0
automatic duplex
automatic speed
!
IP forward-Protocol ND
!
!
IP http server
no ip http secure server
!
HusbandToWife extended IP access list
ip permit 192.168.1.0 0.0.0.255 192.168.3.0 0.0.0.255
!
!
!
!
!
control plan
!
!
Line con 0
line to 0
line vty 0 4
!
!
endRouter3 #sh card crypto
'TOHUSBAND' 1-isakmp ipsec crypto map
Peer = 10.1.1.1
Expand the access list IP WifeToHusband
WifeToHusband 192.168.3.0 ip access list allow 0.0.0.255 192.168.1.0 0.0.0.255
Current counterpart: 10.1.1.1
Life safety association: 4608000 Kbytes / 3600 seconds
PFS (Y/N): N
Transform sets = {}
3DESHMAC,
}
Interfaces using crypto card TOHUSBAND:
FastEthernet0/0Router3 #sh running-config
Building configuration...Current configuration: 1033 bytes
!
version 12.4
horodateurs service debug datetime msec
Log service timestamps datetime msec
no password encryption service
!
name of host Router3
!
boot-start-marker
boot-end-marker
!
!
No aaa new-model
memory iomem size 5
IP cef
!
!
!
!
!
Authenticated MultiLink bundle-name Panel
!
!
!
!
!
Archives
The config log
hidekeys
!
!
crypto ISAKMP policy 1
preshared authentication
spike key crypto isakmp 10.1.1.1 address
!
!
Crypto ipsec transform-set esp-3des esp-sha-hmac 3DESHMAC
!
TOHUSBAND 1 ipsec-isakmp crypto map
defined peer 10.1.1.1
Set transform-set 3DESHMAC
match address WifeToHusband
!
!
!
!
!
!
interface FastEthernet0/0
address 192.168.3.1 IP 255.255.255.0
automatic duplex
automatic speed
card crypto TOHUSBAND
!
interface FastEthernet0/1
10.2.2.1 IP address 255.255.255.0
automatic duplex
automatic speed
!
IP forward-Protocol ND
!
!
IP http server
no ip http secure server
!
WifeToHusband extended IP access list
ip licensing 192.168.3.0 0.0.0.255 192.168.1.0 0.0.0.255
!
!
!
!
!
control plan
!
!
Line con 0
line to 0
line vty 0 4
!
!
endPlease provide us with 'see the crypto isakmp peer', ' show crypto ipsec his ' and 'show ip access-list' output of these two routers site2site. Y at - it all matches in ACL? Can you ping peers of each other?
---
HTH. Please rate this post if this has been helpful. If it solves your problem, please mark this message as "right answer".
-
LAN ASA 5505 VPN client access issue
Hello
I'm no expert in ASA and routing so I ask support the following case.
There is a (running on Windows 7) Cisco VPN client and an ASA5505.
The objectives are client can use the gateway remote on SAA for Skype and able to access devices in SAA within the interface.
The Skype works well, but I can't access devices in the interface inside through a VPN connection.
Can you please check my following config and give me any advice to fix NAT or VPN settings?
ASA Version 7.2 (4)
!
ciscoasa hostname
domain default.domain.invalid
activate wDnglsHo3Tm87.tM encrypted password
2KFQnbNIdI.2KYOU encrypted passwd
names of
!
interface Vlan1
nameif inside
security-level 100
IP 192.168.1.1 255.255.255.0
!
interface Vlan2
nameif outside
security-level 0
IP address dhcp setroute
!
interface Vlan3
prior to interface Vlan1
nameif dmz
security-level 50
no ip address
!
interface Ethernet0/0
switchport access vlan 2
!
interface Ethernet0/1
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
!
interface Ethernet0/7
!
passive FTP mode
DNS server-group DefaultDNS
domain default.domain.invalid
permit same-security-traffic inter-interface
permit same-security-traffic intra-interface
inside_access_in list extended access permitted tcp 192.168.1.0 255.255.255.0 any
inside_access_in list extended access permitted udp 192.168.1.0 255.255.255.0 any
outside_access_in list of allowed ip extended access entire 192.168.1.0 255.255.255.0
pager lines 24
Enable logging
asdm of logging of information
Within 1500 MTU
Outside 1500 MTU
MTU 1500 dmz
local pool VPNPOOL 10.0.0.200 - 10.0.0.220 255.255.255.0 IP mask
ICMP unreachable rate-limit 1 burst-size 1
ASDM image disk0: / asdm - 524.bin
don't allow no asdm history
ARP timeout 14400
NAT-control
Global 1 interface (outside)
NAT (inside) 1 10.0.0.0 255.255.255.0
NAT (inside) 1 192.168.1.0 255.255.255.0
NAT (outside) 1 10.0.0.0 255.255.255.0
inside_access_in access to the interface inside group
Access-group outside_access_in in interface outside
Timeout xlate 03:00
Timeout conn 01:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
Sunrpc timeout 0:10:00 h323 0:05:00 h225 mgcp from 01:00 0:05:00 mgcp-pat 0:05:00
Sip timeout 0:30:00 sip_media 0:02:00 prompt Protocol sip-0: 03:00 sip - disconnect 0:02:00
Timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
the ssh LOCAL console AAA authentication
Enable http server
http 192.168.1.0 255.255.255.0 inside
No snmp server location
No snmp Server contact
Server enable SNMP traps snmp authentication linkup, linkdown cold start
Crypto ipsec transform-set esp-SHA-ESP-3DES-3des esp-sha-hmac
Crypto-map dynamic outside_dyn_map pfs set 20 Group1
Crypto-map dynamic outside_dyn_map 20 the value transform-set ESP-3DES-SHA
map outside_map 65535-isakmp ipsec crypto dynamic outside_dyn_map
outside_map interface card crypto outside
crypto ISAKMP allow outside
crypto ISAKMP policy 10
preshared authentication
3des encryption
sha hash
Group 2
life 86400
Telnet timeout 5
SSH 192.168.1.0 255.255.255.0 inside
SSH timeout 5
SSH version 2
Console timeout 0
dhcpd outside auto_config
!
dhcpd address 192.168.1.2 - 192.168.1.33 inside
dhcpd dns xx.xx.xx.xx interface inside
dhcpd allow inside
!
attributes of Group Policy DfltGrpPolicy
No banner
WINS server no
value of server DNS 84.2.44.1
DHCP-network-scope no
VPN-access-hour no
VPN - connections 3
VPN-idle-timeout 30
VPN-session-timeout no
VPN-filter no
Protocol-tunnel-VPN IPSec l2tp ipsec webvpn
disable the password-storage
disable the IP-comp
Re-xauth disable
Group-lock no
disable the PFS
IPSec-udp disable
IPSec-udp-port 10000
Split-tunnel-policy tunnelall
Split-tunnel-network-list no
by default no
Split-dns no
Disable dhcp Intercept 255.255.255.255
disable secure authentication unit
disable authentication of the user
user-authentication-idle-timeout 30
disable the IP-phone-bypass
disable the leap-bypass
allow to NEM
Dungeon-client-config backup servers
MSIE proxy server no
MSIE-proxy method non - change
Internet Explorer proxy except list - no
Disable Internet Explorer-proxy local-bypass
disable the NAC
NAC-sq-period 300
NAC-reval-period 36000
NAC-by default-acl no
address pools no
enable Smartcard-Removal-disconnect
the firewall client no
rule of access-client-none
WebVPN
url-entry functions
HTML-content-filter none
Home page no
4 Keep-alive-ignore
gzip http-comp
no filter
list of URLS no
value of customization DfltCustomization
port - forward, no
port-forward-name value access to applications
SSO-Server no
value of deny message connection succeeded, but because some criteria have not been met, or because of a specific group policy, you are not allowed to use the VPN features. Contact your administrator for more information
SVC no
SVC Dungeon-Installer installed
SVC keepalive no
generate a new key SVC time no
method to generate a new key of SVC no
client of dpd-interval SVC no
dpd-interval SVC bridge no
deflate compression of SVC
internal group XXXXXX strategy
attributes of XXXXXX group policy
Protocol-tunnel-VPN IPSec
Split-tunnel-policy tunnelall
Split-tunnel-network-list no
XXXXXX G910DDfbV7mNprdR encrypted privilege 15 password username
username password encrypted XXXXXX privilege 0 5p9CbIe7WdF8GZF8
attributes of username XXXXXX
Strategy Group-VPN-XXXXXX
username privilege 15 encrypted password cRQbJhC92XjdFQvb XXXXX
tunnel-group XXXXXX type ipsec-ra
attributes global-tunnel-group XXXXXX
address VPNPOOL pool
Group Policy - by default-XXXXXX
tunnel-group ipsec-attributes XXXXXX
pre-shared-key *.
!
class-map inspection_default
match default-inspection-traffic
!
!
type of policy-card inspect dns preset_dns_map
parameters
message-length maximum 512
Policy-map global_policy
class inspection_default
inspect the preset_dns_map dns
inspect the ftp
inspect h323 h225
inspect the h323 ras
inspect the rsh
inspect the rtsp
inspect esmtp
inspect sqlnet
inspect the skinny
inspect sunrpc
inspect xdmcp
inspect the sip
inspect the netbios
inspect the tftp
inspect the icmp
!
global service-policy global_policy
context of prompt hostname
Cryptochecksum:a8fbb51b0a830a4ae823826b28767f23
: end
ciscoasa #.
Thanks in advance!
fbela
config #no nat (inside) 1 10.0.0.0 255.255.255.0< this="" is="" not="">
Add - config #same-Security-permit intra-interface
#access - extended list allowed sheep ip 192.168.1.0 255.255.255.0 10.0.0.0 255.255.255.0
#nat (inside) 0 access-list sheep
Please add and test it.
Thank you
Ajay
-
How to configure the VPN connection so that doctors may be able to work remotely from home or anywhere on the server of PACS in hospital.
Hello
Your question is beyond the scope of these forums.
Please post this question in the Technet forums.
Windows client | Deploy, manage, desktop, 7, Vista, XP | TechNet:
http://TechNet.Microsoft.com/en-us/Windows/cc468658.aspxConcerning
-
My previous internet provider set a VPN on my IE8. They have now failed and I have to delete.
I am currently connected to my new provider and when I go to delete it it tells me that this is impossible because it is in use. It is not in use? Any suggestions? I have even closed all my IE Windows and went at it through Control Panel/Network and internet connections / positioned upward or change your internet connection... received the same error
Hello
You can start your computer in safe mode and try to remove the VPN connections.
Step 1: Safe Mode
Start your computer in safe mode
http://Windows.Microsoft.com/en-us/Windows7/start-your-computer-in-safe-mode
Step 2: Remove VPN connections
un) Click start.
b) in the search box type network and sharing Center.
c) click change the parameters of the map.
d) in the left pane, you can see the maps and the VPN connection, just right-click on the VPN connection and select delete.
Maybe you are looking for
-
Unlike satellite Pro 6100 (PS610E) - two versions of the Bios?
Hello There are two files of bios for this old laptop... 1.90 - TRAD1.90 - WIN What is the difference? Best regards & thanks in advance Tom
-
Photosmart C310 with wireless connection with MAC does not print
Status, connections, power in ink, etc. everything is OK. State indicates point printed but paper or envelopes come out blank.
-
Network user authentication information
Whenever I try to access the network. my family, I wonder my user id and password. However in 'Managing the credentials', the Vault has no id user or password in it. There are other devices on the network, and this laptop is the only device that we
-
Check the file C: System! I swear I fix one thing and get another!
When I start my computer, I get the "checking file system on C: the type of system is NTFS volume name is OS one of your disks needs to be checked for consistency? and he tells me he is highly recommended, but I can push a button and get out of the a
-
discount for students on an os win 7
Is there a discounted student os disk full windows 7 64 bit available? not the upgrade I would like the full operating system with disc! If so how can I get it? I don't see how to get a copy with the student discount premium upgrade... I need to do