Split tunneling ACL in easy VPN
Hello
When you look at the following example:
I noticed that the split tunneling ACL defined under the "crypto isakmp client configuration group cisco of" are:
access-list 199 permit ip 192.168.1.0 0.0.0.255 any
access-list 199 permit ip 192.168.3.0 0.0.0.255 any
And the local pool assigned to the customer to fred:
192.168.2.1 192.168.2.10
Is the above mentioned access list not the access list incorrect because there is no mention of 192.168.2.1 to 192.168.2.10?
The statement in the license should say the VPNclient that only traffic 192.168.1.0 AND 192.168.3.0 * should * be encrypted and jumped into the tunnel. Not all traffic since?
If the correct access list would read as follows:
access-list 199 permit ip any 192.168.1.0 0.0.0.255
access-list 199 permit ip any 192.168.3.0 0.0.0.255
Or am I wrong?
Hello
This list (mentioned in the doc) would work fine, but it's better if you use 192.168.2.0 24 in the destination network to be entered specific or specific for all these 10 IPs (.1-->. 10.
Thank you
AFAQ
Tags: Cisco Security
Similar Questions
-
Hello everyone
I have setup a VPN connection, which I can connect to. For all customers of connection, I want to give them an IP (from a subnet maybe) and let them use this IP address for all that they do.
Therefore, this:
and not current:

My inside is 192.168.1.0
My VPN IP pool is 192.168.30.5 - 200
My server (DNS, files, Web site) is 192.168.1.222Here's my setup. I scored what I thought might have something to do with it:
ASA Version 9.2 (1)
!
ciscoasa hostname
activate 8Ry2YjIyt7RRXU24 encrypted password
volatile xlate deny tcp any4 any4
volatile xlate deny tcp any4 any6
volatile xlate deny tcp any6 any4
volatile xlate deny tcp any6 any6
volatile xlate deny udp any4 any4 eq field
volatile xlate deny udp any4 any6 eq field
volatile xlate deny udp any6 any4 eq field
volatile xlate deny udp any6 any6 eq field
2KFQnbNIdI.2KYOU encrypted passwd
names of
pool of IP local IP-pool 192.168.30.5 - 192.168.30.200 mask 255.255.255.0
!
interface Ethernet0/0
switchport access vlan 2
!
interface Ethernet0/1
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
!
interface Ethernet0/7
!
interface Vlan1
nameif inside
security-level 100
IP 192.168.1.253 255.255.255.0
!
interface Vlan2
nameif outside
security-level 0
IP address dhcp setroute
!
boot system Disk0: / asa921 - k8.bin
passive FTP mode
permit same-security-traffic intra-interface
network obj_any object
subnet 0.0.0.0 0.0.0.0
network of the object Server-25
Home 192.168.1.222
Description of the test server
network of the object server-80
Home 192.168.1.222
Description of the test server
network of the object server-443
Home 192.168.1.222
Description of the test server
network of the object server-2525
Home 192.168.1.222
Description of the test server
network of the object server-993
Home 192.168.1.222
Description of the test server
network of the object server-6001
Home 192.168.1.222
Description of the test server
network of the object server-6002
Home 192.168.1.222
Description of the test server
network of the object server-6003
Home 192.168.1.222
Description of the test server
network of the object server-6004
Home 192.168.1.222
Description of the test server
network of the VPN HOST object
192.168.30.0 subnet 255.255.255.0
the object to the Interior-net network
host 192.168.1.0
the VPN server object network
Home 192.168.1.222
outside_access_in list extended access permit tcp any object Server-25 eq smtp
outside_access_in list extended access permit tcp any object server-2525 2525 eq
outside_access_in list extended access permit tcp any object server-80 eq www
outside_access_in list extended access permit tcp any object server-443 https eq
outside_access_in list extended access permit tcp any object server-993 993 eq
outside_access_in list extended access permit tcp any object server-6001 eq 6001
outside_access_in list extended access permit tcp any object server-6002 6002 eq
outside_access_in list extended access permit tcp any object server-6003 eq 6003
outside_access_in list extended access permit tcp any object server-6004 eq 6004
outside_access_in to access ip 192.168.1.0 scope list allow 255.255.255.0 192.168.30.0 255.255.255.0
permit access-list Split-Tunnel-ACL standard 192.168.30.0 255.255.255.0
no pager
Enable logging
asdm of logging of information
Within 1500 MTU
Outside 1500 MTU
ICMP unreachable rate-limit 1 burst-size 1
ASDM image disk0: / asdm - 721.bin
don't allow no asdm history
ARP timeout 14400
no permit-nonconnected arp
NAT (indoor, outdoor) Interior-net Interior-NET static source static destination HOST-VPN-VPN-HOST
NAT VPN VPN-server destination (indoor, outdoor) static static source HOST-VPN-VPN-HOST
!
network obj_any object
NAT dynamic interface (indoor, outdoor)
network of the object Server-25
NAT (inside, outside) interface static tcp smtp smtp service
network of the object server-80
NAT (inside, outside) interface static tcp www www service
network of the object server-443
NAT (inside, outside) interface static tcp https https service
network of the object server-2525
NAT (inside, outside) interface static 2525 2525 tcp service
network of the object server-993
NAT (inside, outside) interface static tcp 993 993 service
network of the object server-6001
NAT (inside, outside) interface static tcp 6001 6001 service
network of the object server-6002
NAT (inside, outside) interface static tcp 6002 6002 service
network of the object server-6003
NAT (inside, outside) interface static 6003 6003 tcp service
network of the object server-6004
NAT (inside, outside) interface static service tcp 6004 6004
Access-group outside_access_in in interface outside
Timeout xlate 03:00
Pat-xlate timeout 0:00:30
Timeout conn 01:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
Sunrpc timeout 0:10:00 h323 0:05:00 h225 mgcp from 01:00 0:05:00 mgcp-pat 0:05:00
Sip timeout 0:30:00 sip_media 0:02:00 prompt Protocol sip-0: 03:00 sip - disconnect 0:02:00
Timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
Floating conn timeout 0:00:00
dynamic-access-policy-registration DfltAccessPolicy
RADIUS AAA server HSS-auth-server protocol
allow only
AAA-server HSS-auth-server (inside) host 192.168.1.222
Timeout 5
key *.
identity of the user by default-domain LOCAL
Enable http server
http 192.168.1.0 255.255.255.0 inside
No snmp server location
No snmp Server contact
Crypto ipsec transform-set ikev1 ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
Crypto ipsec transform-set ikev1 ESP-DES-SHA esp - esp-sha-hmac
Crypto ipsec transform-set ikev1 SHA-ESP-3DES esp-3des esp-sha-hmac
Crypto ipsec transform-set ikev1 esp ESP-DES-MD5-esp-md5-hmac
Crypto ipsec transform-set ikev1 ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
Crypto ipsec transform-set ikev1 ESP-3DES-MD5-esp-3des esp-md5-hmac
Crypto ipsec transform-set ikev1 ESP-AES-256-SHA esp-aes-256 esp-sha-hmac
Crypto ipsec transform-set ikev1 ESP-AES-128-SHA aes - esp esp-sha-hmac
Crypto ipsec transform-set ikev1 ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
Crypto ipsec transform-set ikev1 ESP-AES-128-MD5-esp - aes esp-md5-hmac
Crypto ipsec pmtu aging infinite - the security association
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 define ikev1 transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA MD5-ESP-3DES ESP-DES-SHA ESP-DES-MD5
outside_map card crypto 65535-isakmp dynamic ipsec SYSTEM_DEFAULT_CRYPTO_MAP
outside_map interface card crypto outside
trustpool crypto ca policy
Crypto isakmp nat-traversal 30
Crypto ikev1 allow outside
IKEv1 crypto policy 10
authentication crack
aes-256 encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 20
authentication rsa - sig
aes-256 encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 30
preshared authentication
aes-256 encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 40
authentication crack
aes-192 encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 50
authentication rsa - sig
aes-192 encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 60
preshared authentication
aes-192 encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 70
authentication crack
aes encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 80
authentication rsa - sig
aes encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 90
preshared authentication
aes encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 100
authentication crack
3des encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 110
authentication rsa - sig
3des encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 120
preshared authentication
3des encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 130
authentication crack
the Encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 140
authentication rsa - sig
the Encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 150
preshared authentication
the Encryption
sha hash
Group 2
life 86400
Telnet timeout 5
SSH stricthostkeycheck
SSH timeout 5
SSH group dh-Group1-sha1 key exchange
Console timeout 0interface ID client DHCP-client to the outside
dhcpd outside auto_config
!
a basic threat threat detection
Statistics-list of access threat detection
no statistical threat detection tcp-interception
internal HSSvpn group strategy
attributes of Group Policy HSSvpn
value of server WINS 192.168.1.222
value of server DNS 192.168.1.222
Ikev1 VPN-tunnel-Protocol
Split-tunnel-policy tunnelall
Split-tunnel-network-list value Split-Tunnel-ACL
HSS.dk value by default-field
activate dns split-tunnel-all
type tunnel-group HSSvpn remote access
attributes global-tunnel-group HSSvpn
address IP-pool pool
HSS-auth-server authentication-server-group
Group Policy - by default-HSSvpn
password-management
IPSec-attributes tunnel-group HSSvpn
IKEv1 pre-shared-key *.
tunnel-group HSSvpn ppp-attributes
No chap authentication
no authentication ms-chap-v1
ms-chap-v2 authentication
!
class-map inspection_default
match default-inspection-traffic
!
!
type of policy-card inspect dns preset_dns_map
parameters
maximum message length automatic of customer
message-length maximum 512
Policy-map global_policy
class inspection_default
inspect the preset_dns_map dns
inspect the ftp
inspect h323 h225
inspect the h323 ras
inspect the rsh
inspect the rtsp
inspect esmtp
inspect sqlnet
inspect the skinny
inspect sunrpc
inspect xdmcp
inspect the sip
inspect the netbios
inspect the tftp
Review the ip options
!
global service-policy global_policy
context of prompt hostname
no remote anonymous reporting call
Cryptochecksum:c85ff8bf61669bef56b4dad704a4930a
: endHello
Change Split Tunnel VPN in full Tunnel VPN, you have really do much in your configuration.
Seems that have already changed you the 'tunnelspecified' 'tunnelall' in configurations of the 'group policy' . You can delete the setup but that defines the ACL of Split Tunnel
attributes of Group Policy HSSvpn
No split-tunnel-network-list value Split-Tunnel-ACLSeems that you use an internal AAA server to manage authentication rather than on the SAA. I guess if you want to assign a specific IP address for VPN user/username, then it must be done on the side Server?
If you had the "username" on the SAA configurations you can set it up under its framework which "username" IP address gets when he or she connects with the VPN Client.
As naturally as you start using the complete Tunnel and all traffic from the VPN Client starts to get in the tunnel to the ASA you will need a NAT for VPN Client users Internet traffic. You can configure this NAT like this for example:
network of the VPN-POOL object
192.168.30.0 subnet 255.255.255.0interface of VPN-POOL dynamic NAT (outside, outside) after auto source
Note that this is a manual of NAT / double NAT statement real "nat" IS NOT inserted under the 'object' , but the 'object' is rather created it can be used in the "nat" command. I see that your other dynamic PAT configurations are configured with NAT Auto / object NAT network. You can do this like that too if you wish. Personally I do like that.
But as I said before, it seems that you have already configured the VPN to be full of Tunnel. It is perhaps not as it is? While it is connected with VPN, you should be able to check the secure routes (or something like that) section to see if it says "0.0.0.0" If Yes, then it should be tunneling all traffic.
Hope this helps :)
-Jouni
-
Restrictions of ASA Anyconnect for Split Tunneling network list
Hello
I have a question. We use Cisco ASA 5520 9.1.1 firmware version with configure SSL VPN Anyconnect(Anyconnect client version 2.5.605).)
We use the big Split Tunneling access-list with 200 ACEs.
If I add more than 200 entries in the list of access and then I connect to the VPN, and after that, we will see that only 200 entries have been added to the routing table.
So my question is... There is a limit for Split Tunneling ACL when you use the Anyconnect client?
Thank you
Hello
This is very well document in one of internal bug at Cisco . Unfortunately, as it is internal I will not be able to share the same with you. The only workaround available as of now is to combine your networks and make the list as small as possible covering all the required network you need which is less than or equal to 200
Thank you
Jeet Kumar
-
Hello.
All started to play with split-mining.
So far so good.
I can access the server when the Tunnel of splitting is disabled, and my itinerary looks very good. But cannot access the internet.
I can not access the server when the Tunnel of splitting is enabled, my itinerary seems wrong. But can access the internet.
I think it's my access list the problem (also tried to overthrow).
split_test list extended access allowed host 4.4.4.4 ip 10.10.253.0 255.255.255.0
attributes of the strategy of group test_policy
Split-tunnel-policy tunnelspecified
value of Split-tunnel-network-list split_test
I read that I can't filter on the ports during the shared use of tunnelling, is this correct?
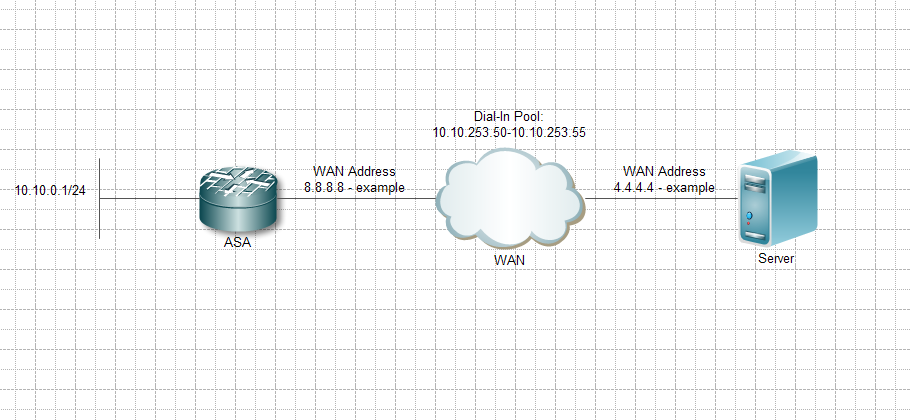
I have attached a quick drawing of the installation.
Best regards, Søren.
Hello
Then you can use the following version of above indicate changes in configurations
attributes of the strategy of group test_policy
No split-tunnel-network-list split_test value
No list of extended split_test access not allowed host 4.4.4.4 ip 10.10.253.0 255.255.255.0
host of access TUNNEL of SPLIT standard allowed 4.4.4.4 list
attributes of the strategy of group test_policy
no value of split-tunnel-network-list SPLIT-TUNNEL
The above configuration would be basically set up the VPN Client connection so that connections for ONLY the IP 4.4.4.4 the VPN connection will be provided by the user.
As I understand it, the traffic of users to the destination server would only be encrypted between the Client and the ASA. From there it would be just like any traffic between hosts on the external network. Except of course your ASA has a separate VPN L2L connection on the site where the Server 4.4.4.4.
Even if the above Split Tunnel ACL configuration is correct, you will still need to manage the NAT for VPN Client users. To determine the NAT configuration correct, I need to know the version of the software of your ASA and the current dynamic PAT rule for internal users, for example if the VPN users are supposed to use the same public IP address for their IP NAT address.
Also, you will at least have to add this configuration on the SAA
permit same-security-traffic intra-interface
This will allow connections to VPN users enter through the 'outside' of the interface and head to this same ' outside ' interface. It is not possible without the above configured command even if all other configurations were correct.
-Jouni
Post edited by: Jouni Forss (typos in the post)
-
access list of split tunneling
Hello
I have some problems on ASA 5520 split tunneling configuration.
Here's the scenario:
Number of remote users connects ipsec with ASA 5520 (in central) using ubuntu vpnc-client.
Split tunneling is used, in order to allow remote users to surf the Internet using their ISP.
The goal is to remove the possibility for ssh/telnet servers within the local enterprise network for remote users.
Here is a part of the config:
internal REMOTE_gp group strategy
attributes of Group Policy REMOTE_gp
VPN-idle-timeout no
Protocol-tunnel-VPN IPSec
Group-lock no
Split-tunnel-policy tunnelspecified
value of Split-tunnel-network-list REMOTE_splittunnel-group type REMOTE access remotely
tunnel-group REMOTE General attributes
authentication-server-group RADIUSGR
Group Policy - by default-REMOTE_gp
REMOTE tunnel-group ipsec-attributes
pre-shared-key *.
ISAKMP keepalive retry threshold 15 10
RADIUS protocol AAA-server RADIUSGR
AAA-server RADIUSGR (INSIDE_LAN) 192.168.0.244
REMOTE_split list extended access deny tcp 192.168.0.0 255.255.255.0 ssh telnet rank everything
permit access ip 192.168.0.0 scope list REMOTE_split 255.255.255.0 192.168.100.0 255.255.255.0
ip subnet ##192.168.100.0/24 - where from Radius Server to allocate ip addresses to remote users.
INSIDE_LAN_in list extended access deny tcp 192.168.0.0 255.255.255.0 eq ssh 192.168.100.0 255.255.255.0
INSIDE_LAN_in list extended access deny tcp 192.168.0.0 255.255.255.0 eq telnet 192.168.100.0 255.255.255.0
permit access ip 192.168.0.0 scope list INSIDE_LAN_in 255.255.255.0 any
It has nat enabled on the interface, but there is a special instruction in nat0 ACL for 192.168.100.0 subnet
permit access ip 192.168.0.0 scope list INSIDE_LAN_nat0_outbound 255.255.255.0 192.168.100.0 255.255.255.0
The problem is that the remote users can easily ssh and telnet servers in network INSIDE_LAN. Everything I put in INSIDE_LAN_in ACL, remote users still have full access to this network. Restrictions in the REMOTE_split ACL do not work either.
You must configure vpn-filter rather to block telnet and ssh access as follows:
Remote filter access list deny tcp 192.168.100.0 255.255.255.0 192.168.0.0 255.255.255.0 eq 22
Remote filter access list deny tcp 192.168.100.0 255.255.255.0 192.168.0.0 255.255.255.0 eq 23
distance-filter 192.168.100.0 ip access list allow 255.255.255.0 192.168.0.0 255.255.255.0
attributes of Group Policy REMOTE_gp
VPN-value filter-remote control
Split tunnel acl has the following statement and it should be extended to standard ACLs instead of:
REMOTE_split list of permitted access 192.168.0.0 255.255.255.0
Hope that helps.
-
Easy VPN between two ASA 9.5 - Split tunnel does not
Hi guys,.
We have set up a site to site vpn using easy configuration vpn between ver 9.5 race (1) two ASA. The tunnels are up and ping is reached between sites. I also configured split tunnel for internet traffic under the overall strategy of the ASA easy vpn server. But for some unknown reason all the customer same internet traffic is sent to the primary site. I have configured NAT to relieve on the side of server and client-side. Please advise if no limitation so that the installation program.
Thank you and best regards,
Arjun T P
I have the same question and open a support case.
It's a bug in the software 9.5.1. See the bug: CSCuw22886
-
Cisco easy VPN access Internet without Split Tunnel
Hey guys
IM wondering if anyone has a config that can help me get access to internet via an easy vpn tunnel on a cisco 877 router.
Basically, we are traveling to be users able to use the internet through vpn, rather than using split tunneling. The reason for this is that we have several sites that are attached by lists of external IP access for some services.
We hope that mobile users to interact with these sites through the central router and use external IP of access routers secure sites.
I hope that makes sense. I know that we can use a proxy but we also use other services of bases no proxy on these sites, it would be rather routed direct access.
Thank you
Luke
Hi Luke,.
Please use the installation of the client VPN (complete tunnel) link below.
Note the useful message.
Thank you
Kasi
-
What is is it possible to use the acl extended for split tunneling on ASA?
I'm setting up VPN IPSEC RA on SAA and I would like to know if it is possible to use the ACL extended as part of the split tunneling?
Thank you!
Yes, you can use the extended ACL. See this example:http://www.cisco.com/c/en/us/support/docs/security/asa-5500-x-series-nex...
Kind regards
Averroès.
-
Disable Split Tunneling - SAs are not when I change crypto ACL
Hello!
When I change my ACL Crypto I receive an error message in phase I: "PROPOSAL_NOT_CHOSEN NOTIFIER' of IKE. I do this to disable the ST and get all the hollow tunnel traffic. Please see the config below:
crypto ISAKMP policy 10
md5 hash
preshared authentication
life 3600
ISAKMP crypto key cisco address x.x.x.x
!
!
Crypto ipsec transform-set esp - the esp-hmac-md5 ENCRYPTION
!
crypto map ipsec-isakmp CLIENT 1
defined peer x.x.x.x
game of transformation-CRYPTO
match address 115
!
access-list 115 permit ip 10.10.10.0 0.0.0.255 10.10.11.0 0.0.0.255
access-list 115 deny ip any one
I changed the ACL 115 to so I can disable split tunneling, and it looks like this:
access-list 115 permit ip 10.10.10.0 0.0.0.255 any
access-list 115 deny ip any one
What is a failure? I have donthink the crypto ACL must be the same?
OK, you use a card dynamic encryption on your head just as I suggested, so that's fine. What you have done, which is causing your problem (and usually causes more problems than it's worth), is to assign an access list to the dynamic encryption card. It is not necessary, because with a dynamic encryption the router head card accept any model of traffic the remote router sends.
In your case since you changed the remote router to be 'all', it is no longer maps to the 115 ACL on the head and now is failing.
Way easier around it is simply to remove the 'match 115' address card dynamic encryption on the head. This will not affect any of your other tunnels and allow the remote router to establish a tunnel.
The exact commands you would use are as follows:
> crypto dynamic-map PERSONAL 10
> no address for correspondence 115
-
Hello
First of all - thanks to all who post here. I often browse the forums and search for help here and its very useful, so a big pat on the back for all who contribute. My first post, so here goes...
I've got my ASA 5505 v8.2 configured to allow the AnyConnect. This works. Client can connect and access remote systems via VPN. What causes me a massive headache, is the customer loses internet connectivity. I played a bit with my config a bit so what I am about to post that I know for sure is incorrect, but any help is greatly appreciated.
Notes
1. the router was set up for a VPN site to site standard that is no longer functional, but as you can see all the settings are always in the router.
2. the router also a DMZ configuration has to allow access to the internet with the help of the DMZ to some customers
CONFIGURATION:
ASA Version 8.2 (5)
!
hostname MYHOST
activate mUUvr2NINofYuSh2 encrypted password
UNDrnIuGV0tAPtz2 encrypted passwd
names of
name x.x.x.x LIKES-SD
!
interface Ethernet0/0
switchport access vlan 2
!
interface Ethernet0/1
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
!
interface Ethernet0/7
switchport access vlan 7
!
interface Vlan1
nameif inside
security-level 100
192.168.101.1 IP address 255.255.255.0
!
interface Vlan2
nameif outside
security-level 0
IP x.x.x.x 255.255.0.0
!
interface Vlan7
prior to interface Vlan1
nameif DMZ
security-level 20
IP 137.57.183.1 255.255.255.0
!
passive FTP mode
clock timezone STD - 7
the obj_any_dmz object-group network
10 extended access-list allow ip 192.168.25.0 255.255.255.0 192.168.6.0 255.255.255.0
permit access ip host x.x.x.x 192.168.25.0 extended list no_nat 255.255.25 5.0
tunneling split list of permitted access standard 192.168.101.0 255.255.255.0
192.168.101.0 IP Access-list extended sheep 255.255.255.0 allow all
pager lines 24
Enable logging
debug logging in buffered memory
asdm of logging of information
Within 1500 MTU
Outside 1500 MTU
MTU 1500 DMZ
mask 192.168.101.125 - 192.168.101.130 255.255.255.0 IP local pool Internal_Range
ICMP unreachable rate-limit 1 burst-size 1
don't allow no asdm history
ARP timeout 14400
Global interface 10 (external)
NAT (inside) 0-list of access no_nat
NAT (inside) 1 access-list sheep
NAT (DMZ) 10 137.57.183.0 255.255.255.0
Route outside 0.0.0.0 0.0.0.0 x.x.x.x 1
Route inside 192.168.8.0 255.255.255.0 192.168.101.2 1
Timeout xlate 03:00
Timeout conn 01:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
Sunrpc timeout 0:10:00 h323 0:05:00 h225 mgcp from 01:00 0:05:00 mgcp-pat 0:05:00
Sip timeout 0:30:00 sip_media 0:02:00 prompt Protocol sip-0: 03:00 sip - disconnect 0:02:00
Timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
Floating conn timeout 0:00:00
dynamic-access-policy-registration DfltAccessPolicy
the ssh LOCAL console AAA authentication
http server enable 64000
http 0.0.0.0 0.0.0.0 inside
No snmp server location
No snmp Server contact
Server enable SNMP traps snmp authentication linkup, linkdown cold start
Crypto ipsec transform-set esp-aes-256 batus, esp-sha-hmac
life crypto ipsec security association seconds 28800
Crypto ipsec kilobytes of life - safety 4608000 association
correspondence address card crypto 100 10 batus
crypto batus 100 peer LIKES-SD card game
batus batus 100 transform-set card crypto
batus outside crypto map interface
Crypto ca trustpoint ASDM_TrustPoint1
registration auto
name of the object CN = MYHOST
ClientX_cert key pair
Configure CRL
string encryption ca ASDM_TrustPoint1 certificates
certificate 0f817951
308201e7 a0030201 30820150 0202040f 0d06092a 81795130 864886f7 0d 010105
05003038 31173015 06035504 03130e41 494d452d 56504e2d 42415455 53311d 30
1b06092a 864886f7 0d 010902 160e4149 4d452d56 504e2d42 41545553 301e170d
31333036 32373137 32393335 5a170d32 33303632 35313732 3933355a 30383117
30150603 55040313 0e41494d 452-5650 4e2d4241 54555331 1d301b06 092 d has 8648
86f70d01 0902160e 41494d 45 2d56504e 424154 55533081 9f300d06 092 2d has 8648
86f70d01 01010500 03818d 30818902 00 818100c 9 ff840bf4 cfb8d394 2 c 940430
1887f25a 49038aa0 1299cf10 bda2a436 227dcdbf f1c5566b c35c2f19 8b3514d3
4e24f5b1 c8840e8c 60e2b39d bdc0082f 08cce525 97ffefba d42bb087 81b9adb9
db0a8b2f b643e651 d17cd6f8 f67297f2 d785ef46 c3acbb39 615e1ef1 23db072c
783fe112 acd6dc80 dc38e94b 6e56fe94 d59d5d02 03010001 300 d 0609 2a 864886
8181007e f70d0101 05050003 29e90ea0 e337976e 9006bc02 402fd58a a1d30fe8
b2c1ab49 a1828ee0 488d1d2f 1dc5d150 3ed85f09 54f099b2 064cd 622 dc3d3821
fca46c69 62231fd2 6e396cd1 7ef586f9 f41205af c2199174 3c5ee887 42b684c9
7f4d2045 4742adb5 d70c3805 4ad13191 8d802bbc b2bcd8c7 8eec111b 761d89f3
63ebd49d 30dd06f4 e0fa25
quit smoking
crypto ISAKMP allow outside
crypto ISAKMP policy 40
preshared authentication
aes-256 encryption
sha hash
Group 5
life 86400
Telnet timeout 5
SSH 0.0.0.0 0.0.0.0 inside
SSH 0.0.0.0 0.0.0.0 DMZ
SSH timeout 10
Console timeout 0
a basic threat threat detection
Statistics-list of access threat detection
no statistical threat detection tcp-interception
SSL encryption rc4 - md5, rc4-aes128-sha1 aes256-3des-sha1 sha1 sha1
SSL-trust outside ASDM_TrustPoint1 point
WebVPN
allow outside
SVC disk0:/anyconnect-win-2.4.1012-k9.pkg 1 image
enable SVC
internal ClientX_access group strategy
attributes of Group Policy ClientX_access
VPN-tunnel-Protocol svc
Split-tunnel-network-list value split tunneling
access.local value by default-field
the address value Internal_Range pools
IPv6 address pools no
WebVPN
SVC mtu 1406
generate a new key SVC time no
SVC generate a new method ssl key
username privilege 15 encrypted password ykAxQ227nzontdIh ClientX
ClientX username attributes
VPN-group-policy ClientX_access
type of service admin
tunnel-group x.x.x.x type ipsec-l2l
tunnel-group ipsec-attributes x.x.x.x
pre-shared key *.
tunnel-group ClientX type remote access
attributes global-tunnel-group ClientX
address pool Internal_Range
Group Policy - by default-ClientX_access
type tunnel-group SSLClientProfile remote access
attributes global-tunnel-group SSLClientProfile
Group Policy - by default-ClientX_access
type tunnel-group ClientX_access remote access
!
class-map inspection_default
match default-inspection-traffic
!
!
type of policy-card inspect dns preset_dns_map
parameters
maximum message length automatic of customer
message-length maximum 512
Policy-map global_policy
class inspection_default
inspect the preset_dns_map dns
inspect the ftp
inspect h323 h225
inspect the h323 ras
inspect the rsh
inspect the rtsp
inspect esmtp
inspect sqlnet
inspect the skinny
inspect sunrpc
inspect xdmcp
inspect the sip
inspect the netbios
inspect the tftp
Review the ip options
!
global service-policy global_policy
context of prompt hostname
no remote anonymous reporting call
Cryptochecksum:e7d92a387d1c5f07e14b3c894d159ec1
: end
-----------------------
Thanks for any help!
In your group strategy, you specified the ACLs that should be used for split Tunneling, but you forgot to change the policy, so the ASA always uses tunnel-all. Here's what you'll need:
attributes of Group Policy ClientX_access
Split-tunnel-network-list value split tunneling
Split-tunnel-policy tunnelspecified
--
Don't stop once you have upgraded your network! Improve the world by lending money to low-income workers:
http://www.Kiva.org/invitedBy/karsteni -
Split tunneling VPN site-to-site
Dear all,
I have two ASA 5510 with VPN site-to-site, I can send all Internet traffic to the central site (HQ),
How to set the split tunneling to access Campus LAN (192.168.2.0/24) of LAN2.
Thank you in advance.
Best regards
Zoltan
You can have 'decline' instruction on your ACL crypto and he will deviate the traffic is encrypted to the site-to-site VPN tunnel.
For ASA 1:
access-list extended 100 permit ip 10.10.16.192 255.255.255.192 10.10.16.128 255.255.255.192
access-list extended 100 permit ip 10.0.0.0 255.0.0.0 10.10.16.128 255.255.255.192
access-list extended 100 deny ip 192.168.2.0 255.255.255.0 10.10.16.128 255.255.255.192
access-list extended 100 permit ip any 10.10.16.128 255.255.255.192
For ASA 2:
access-list extended 100 permit ip 10.10.16.128 255.255.255.192 10.10.16.192 255.255.255.192
access-list extended 100 permit ip 10.10.16.128 255.255.255.192 10.0.0.0 255.0.0.0
access-list extended 100 deny ip 10.10.16.128 255.255.255.192 192.168.2.0 255.255.255.0
access-list extended 100 permit ip 10.10.16.128 255.255.255.192 all
Hope that helps.
-
Remote VPN: split tunnel filtering
Hello!
The question is about the split tunnel filtering capabilities without using the vpn-filter.
Suppose, we have ASA configured for remote VPN tunneling with split without VPN filter.
- 10.0.0.0/8 is the private netwrok.
- 10.1.0.0/24 is the private network, defined in the split tunnel
- 172.16.1.0/24 is the VPN SECURE network
When the remote client connects, it receives the routes to the private network (10.1.0.0/24).
What happens if the remote client adds the route to a private network (which is not defined by a tunnel of split) by itself (e.g. 10.2.0.0/24)?
Our test LAB, we can see that the customer does not have access to 10.2.0.0/24.
Where the place in this case filtering?
- By default, all vehicles coming from VPN, bypasses all ACLs configured on interfaces ASA.
- Filter VPN is not configured.
- Nat0 don't traffic 10.0.0.0/8 to 172.16.1.0/24 NAT
- of the sh ip cry his on the VPN server, we can see, this ident is 0.0.0.0/0
- local ident (addr, mask, prot, port): (0.0.0.0/0.0.0.0/0/0)
- Remote ident (addr, mask, prot, port): (172.16.1.1/255.255.255.255/0/0)
The ACL of split tunnel is capable for remote client traffic filtering?
I understand that your question is in what regards the IPSec VPN Client, no AnyConnect VPN Client, however, I think that the behavior of the split tunnel is the same.
Here's the answer to your question:
A. AnyConnect applies the policy of tunnel in 2 ways:
Monitoring of track 1) and repair (for example if you change the routing table), AnyConnect will restore it to what has been configured.
(2) filtering (on platforms that support filter engines). Filtering ensures that even if you can perform a kind of injection of the route, the filters would block packets.
-
Hello
There is an "acl" parameter that is not clear to me, it is configured at customer site:
Crypto ipsec VPN ezvpn client
connect auto
Cisco key band EASYVPN
client mode
peer 10.0.0.1
username cisco password cisco
xauth userid local mode
ACL 101
Everything that I added to the ACL 101 tunnel is always present. I found a description:
Step 6
ACL {name - acl |} ACL-number}
Example:Device (ezvpn-crypto-config) # acl acl-list1
Specifies several subnets in a VPN tunnel.
"Specifies several subnets in a VPN tunnel". -what it means, source?
I tried to use this setting, and I added the access list:
access-list 123 allow ip 10.10.10.0 0.0.0.255 host 20.0.0.20
access-list 123 allow ip 50.50.50.0 0.0.0.255 host 20.0.0.20
where 10.10.10.0 and 50.50.50.0 are source and 20.0.0.20 is the destination.
When I ping with source 10.10.10.3 (physical int) for 20.0.0.20 - numbers of BA & desc packages grows.
but when I ping with source 50.50.50.50 (int loop) for 20.0.0.20 - I see that it wasn't to push into the tunnel.
Could someone explain how the work parameter and for what is it?
Thank you
Hubert
Hubert,
Ref:
in client mode several subnets are not supported, nor what they sense.
You specify what internal subnets of announcement to the server that are configured behind this device.
In client mode, the server sees only the assigned IP address.
M.
-
Impossible to access them Internert through the split tunneling VPN client.
I divided tunnel configured on a PIX 515. The remote VPN client connects to the PIX very well and can ping hosts on the internal network, but cannot access the Internet. Am I missing something? My config as shown below.
In addition, I don't see the routes on the VPN client via statistics (screenshot below)
All opinions are appreciated.
Rob
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------
8.0 (3) version PIX
!
hostname PIX-to-250
enable the encrypted password xxxxx
names of
!
interface Ethernet0
nameif outside
security-level 0
IP address x.x.x.250 255.255.255.240
!
interface Ethernet1
nameif inside
security-level 100
IP 192.168.9.1 255.255.255.0
!
XXXXX encrypted passwd
passive FTP mode
DNS domain-lookup outside
DNS server-group Ext_DNS
Server name 194.72.6.57
Server name 194.73.82.242
the LOCAL_LAN object-group network
object-network 192.168.9.0 255.255.255.0
object-network 192.168.88.0 255.255.255.0
Internet_Services tcp service object-group
port-object eq www
area of port-object eq
EQ object of the https port
port-object eq ftp
EQ object of port 8080
port-object eq telnet
the WAN_Network object-group network
object-network 192.168.200.0 255.255.255.0
ACLOUT list extended access allowed object-group LOCAL_LAN udp any eq log field
ACLOUT list extended access allow icmp object-group LOCAL_LAN no matter what paper
ACLOUT list extended access permitted tcp object-group LOCAL_LAN connect to any object-group Internet_Services
access-list extended ACLIN all permit icmp any what newspaper echo-reply
access-list extended ACLIN all permit icmp any how inaccessible journal
access-list extended ACLIN allowed icmp no matter what newspaper has exceeded the time
Comment by split_tunnel_list-LAN Local access list
split_tunnel_list list standard access allowed 192.168.9.0 255.255.255.0
access-list extended SHEEP allowed object-group ip LOCAL_LAN 192.168.100.0 255.255.255.0
pager lines 24
Enable logging
Outside 1500 MTU
Within 1500 MTU
IP local pool testvpn 192.168.100.1 - 192.168.100.99
no failover
ICMP unreachable rate-limit 1 burst-size 1
don't allow no asdm history
ARP timeout 14400
Global 1 interface (outside)
NAT (inside) 0 access-list SHEEP
NAT (inside) 1 0.0.0.0 0.0.0.0
Access-group ACLIN in interface outside
ACLOUT access to the interface inside group
Route outside 0.0.0.0 0.0.0.0 195.171.252.45 1
Route inside 192.168.88.0 255.255.255.0 192.168.88.254 1
Route inside 192.168.199.0 255.255.255.0 192.168.199.254 1
Timeout xlate 03:00
Timeout conn 01:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
Sunrpc timeout 0:10:00 h323 0:05:00 h225 mgcp from 01:00 0:05:00 mgcp-pat 0:05:00
Sip timeout 0:30:00 sip_media 0:02:00 prompt Protocol sip-0: 03:00 sip - disconnect 0:02:00
Timeout, uauth 0:05:00 absolute
dynamic-access-policy-registration DfltAccessPolicy
Enable http server
No snmp server location
No snmp Server contact
Server enable SNMP traps snmp authentication linkup, linkdown cold start
Crypto ipsec transform-set esp-3des esp-sha-hmac Set_1
Crypto-map dynamic outside_dyn_map 10 game of transformation-Set_1
life together - the association of security crypto dynamic-map outside_dyn_map 10 seconds 280000
Crypto-map dynamic outside_dyn_map 10 the value reverse-road
outside_map 10 card crypto ipsec-isakmp dynamic outside_dyn_map
outside_map interface card crypto outside
crypto ISAKMP allow outside
crypto ISAKMP policy 1
preshared authentication
3des encryption
sha hash
Group 2
life 43200
crypto ISAKMP policy 65535
preshared authentication
3des encryption
sha hash
Group 2
life 86400
Telnet timeout 5
SSH timeout 5
Console timeout 0
a basic threat threat detection
Statistics-list of access threat detection
internal testvpn group policy
attributes of the strategy of group testvpn
Protocol-tunnel-VPN IPSec
Split-tunnel-policy tunnelspecified
name of user testuser encrypted password xxxxxx
type tunnel-group testvpn remote access
tunnel-group testvpn General-attributes
address testvpn pool
Group Policy - by default-testvpn
testvpn group of tunnel ipsec-attributes
pre-shared-key *.
!
class-map inspection_default
match default-inspection-traffic
!
!
type of policy-card inspect dns preset_dns_map
parameters
message-length maximum 512
Policy-map global_policy
class inspection_default
inspect the preset_dns_map dns
inspect the ftp
inspect h323 h225
inspect the h323 ras
inspect the netbios
inspect the rsh
inspect the rtsp
inspect the skinny
inspect esmtp
inspect sqlnet
inspect sunrpc
inspect the tftp
inspect the sip
inspect xdmcp
inspect the icmp
!
global service-policy global_policy
context of prompt hostname
Cryptochecksum:5dcb5dcdff277e1765a9a0c366b88b9e
: end
# 250 A - PIX
You have not assigned the ACL split tunnel to your strategy.
PLS, configure the following:
attributes of the strategy of group testvpn
value of Split-tunnel-network-list split_tunnel_list
-
Router Cisco client VPN SPlit tunnel does not work
Hello!
I have configured the Cisco VPN CLient on a 2821 router, and it works fine.
I could access the inside resourses normally >
the problem is that when I connect with VPN I lost internet connectivity?What wrong with my setup?
Below the current configuration of the router.
Kind regards!CISCO2821 #sh run
Building configuration...
Current configuration: 5834 bytes
!
version 12.4
horodateurs service debug datetime msec
Log service timestamps datetime msec
no password encryption service
!
hostname CISCO2821
!
boot-start-marker
start the flash c2800nm-adventerprisek9 - mz.124 - 20.T.bin system
boot-end-marker
!
forest-meter operation of syslog messages
logging buffered 51200 warnings
!
AAA new-model
!
!
connection local VPN-LOCAL-AUTHENTIC AAA authentication
local AAA authorization network VPN-LOCAL-AUTHOR
!
!
AAA - the id of the joint session
!
dot11 syslog
IP source-route
!
!
IP cef
!
!
"yourdomain.com" of the IP domain name
8.8.8.8 IP name-server
No ipv6 cef
!
Authenticated MultiLink bundle-name Panel
!
!
voice-card 0
No dspfarm
!
!
username secret privilege 0 vpn 5 $1$ tCf1$ XAxQWtDRYdfy9g3JpVSvZ.
Archives
The config log
hidekeys
!
!
crypto ISAKMP policy 44
BA aes
preshared authentication
Group 2
life 44444
!
ISAKMP crypto group configuration of VPN client
key VPNVPNVPN
VPN-pool
ACL VPN-ACL-SPLIT
Max-users 5000
!
!
ISAKMP crypto ISAKMP-VPN-profile
identity VPN group match
list of authentication of client VPN-LOCAL-AUTHENTIC
VPN-LOCAL-AUTHOR of ISAKMP authorization list.
client configuration address respond
Configuration of VPN client group
virtual-model 44
!
!
Crypto ipsec transform-set VPN - SET esp - aes esp-sha-hmac
!
Crypto ipsec VPN-profile
transformation-VPN-SET game
Set isakmp VPN ISAKMP-PROFILE
!
!
interface GigabitEthernet0/0
IP 192.168.2.214 255.255.255.0
NAT outside IP
IP virtual-reassembly
IP tcp adjust-mss 1412
automatic duplex
automatic speed
!
interface GigabitEthernet0/1
IP 192.168.1.1 255.255.255.0
IP nat inside
IP virtual-reassembly
IP tcp adjust-mss 1412
automatic duplex
automatic speed
!
interface FastEthernet0/0/0
no ip address
Shutdown
automatic duplex
automatic speed
!
type of interface virtual-Template44 tunnel
IP unnumbered GigabitEthernet0/0
ipv4 ipsec tunnel mode
Tunnel ipsec VPN-PROFILE protection profile
!
interface Dialer0
no ip address
IP mtu 1452
IP virtual-reassembly
Shutdown
!
local pool IP VPN-POOL 192.168.1.150 192.168.1.250
IP forward-Protocol ND
IP http server
IP 8081 http port
23 class IP http access
local IP http authentication
no ip http secure server
IP http timeout policy slowed down 60 life 86400 request 10000
!
!
IP nat inside source list ACL - NAT interface GigabitEthernet0/0 overload
!
IP access-list standard ACL-TELNET
allow a
!
extended ACL - NAT IP access list
ip permit 192.168.1.0 0.0.0.255 any
IP extended ACL-VPN-SPLIT access list
ip permit 192.168.1.0 0.0.0.255 192.168.1.0 0.0.0.255
scope of access to IP-VPN-ACL-SPLIT list
!
control plan
!
exec banner ^ C
% Warning of password expiration.
-----------------------------------------------------------------------
Professional configuration Cisco (Cisco CP) is installed on this device
and it provides the default username "cisco" single use. If you have
already used the username "cisco" to connect to the router and your IOS image
supports the option "unique" user, that user name is already expired.
You will not be able to connect to the router with the username when you leave
This session.
It is strongly recommended that you create a new user name with a privilege level
15 using the following command.
username
secret privilege 15 0 Replace
and with the username and password you want use.
-----------------------------------------------------------------------
Line con 0
exec-timeout 0 0
Synchronous recording
line to 0
line vty 0 4
ACL-TELNET access class in
exec-timeout 30 0
privilege level 15
Synchronous recording
transport input telnet ssh
line vty 5 15
ACL-TELNET access class in
exec-timeout 30 0
privilege level 15
Synchronous recording
transport input telnet ssh
line vty 16 988
ACL-TELNET access class in
exec-timeout 30 0
Synchronous recording
transport input telnet ssh
!
Scheduler allocate 20000 1000
end
CISCO2821 #.
I think that you made a mistake with your ACL name. the ACL applied is "VPN-ACL-SPLIT" which is an empty ACL. You must switch to that of "ACL-VPN-SPLIT" that has the entry "ip 192.168.1.0 allow 0.0.0.255 192.168.1.0 0.0.0.255" inside.
Maybe you are looking for
-
How to change the display on Tecra 8100 drivers?
I downloaded the driver for Tecra 8100 my girlfriend updates, but I can't figure out how to install them. The laptop is running Win2k sp4. I tried the 'normal' method of "update driver" and then selecting the new pilots, but Win2k still find the orig
-
Hi, I have a problem with SM and Bluetooth controller.
Dear support, I have problem with Bluetooth controller and SM Bus controller. I can't find the drivers for the device: SM Bus controller: PCI\VEN_1022 & DEV_780B & SUBSYS_216A103C & REV_16PCI\VEN_1022 & DEV_780B & SUBSYS_216A103CPCI\VEN_1022 & DEV_78
-
Missing selector of CharmBar and app
Hey guys... Sorry, my first time posting here... I'm not surw if this question has been asked before, but I couldn't find one... so here it is... I just bought this tablet a few days ago... wonderful works... But all of a sudden, I can't get the Bar
-
System32\secuload is not a valid Windows image error message.
Whenever I start my PC, I get the following error message. "The request on the DLL C:\\WINDOWS\system32\secuload.dll is not a valid Windows image. Please check this against your installation diskette. "I usually get 20 or if these and I have to clic
-
Slide show with music on a DVD begins by cutting music and photos of freezing when you watch on TV.
Original title: photos and Audio in and out on DVD I made a slideshow with music using many transitions, when I saw on the computer it works fine, when I burn it to a DVD and watch it on TV it starts cutting out music and freezing pictures, how to fi