Cisco JOINT and IPS hardware bypass
Hi all
I have a question about the Cisco JOINT, ASA - AIP - SSM (IPS) and material of the IPS 4200 bypass unit series. Please let me know if the material fails in both cases how to cross traffic. Is there any circumvention of integrated equipment built in the same
Concerning
Ankur
Sorry for the late reply. I've been on vacation for a week.
ByPass hardware is not available for the JOINT-2 no matter if you use inline vlan pairs or couples inline interface.
For devices need special interface cards or a hardware bypass switch separate, and none of them are available on the JOINT-2.
You must configure your network so that there is a second way around the JOINT 2 JOINT-2 failure.
This can be done with a standard network cable.
Suppose you have your JOINT-2 configured for inline vlan VLAN 10 matching and 20.
Configure a standard switchport as an access port on vlan 10.
Set up an another standard switchport as an access port on vlan 20.
Now using a standard network cable connect these 2 all switch ports.
Stop your JOINT-2 and traffic should now be passed through this network cable and your network connectivity must be maintained.
Bring your JOINT-2 backup, and now spanning tree runs and will choose the JOINT-2 or the network as the main way and the other cable will set in a State of block.
Run ' show vlan spanning-tree 10 ' and ' show vlan spanning tree 20 "to determine if the cable ports or port JOINT-2 is in a BLK State.»
If the cable ports are in a State BLK, then you don't need to modify the spanning tree.
If the JOINT-2 port is in a State BLK, then you need to change the spanning tree cost and/or priority for JOINT-2 port by using the following commands:
-[No] port-channel channel_number-STP intrusion detection doesn't cost port_cost
Defines the cost of port tree covering for the data port on the specified module. Without the option restore shipping tree covering for the data port on the module specified in the default value.
-[not] port-channel channel_number spanning tree priority priority intrusion detection
Sets the priority of the port spanning tree for the data port on the specified module. Without the option restores the priority of port spanning tree for the data port on the module specified in the default value.
To learn more about spanning-tree and how these parameters interact with spanning tree you can look through this section of the user guide for the switch or to search cisco.com for documentation of spanning tree:
NOTE: Your switch must be configured for rapid PVST for failover more rapid. Work with your administrator to switch to determine which spanning tree Protocol is used on your switch. The JOINT-2 does not work with STDS to ensure that STD is not used.
Tags: Cisco Security
Similar Questions
-
Configure to integrate Cisco ASA and JOINT
Hello
We have Cisco ASA and JOINT, need assistance on the integration of the same thing; Please email me so that I'll share the details of the architecture.
Thank you best regards &,.
REDA
Hi reda,.
If I correctly your diagram, you do not want to send any traffic from the external switch to the JOINT with a SPAN port and all traffic from your DMZ interfaces with another.
Is this correct?
If so, can you tell me why you want to inspect the traffic before it goes through the firewall? As I said in my original answer, we generally advise putting IP addresses after the firewall.
Not to mention that in your case, I guess that some traffic will be inspected twice so you will need to assign a different virtual sensors to each JOINT internal interfaces to ensure that the same instance does not see the traffic of several times.
Kind regards
Nicolas
-
Techniques need more details 4250XL IPS and IPS-4255
4250XL IDS launched before the IPS technology, am I right?
Can I deploy a 4250XL ID as an IPS, if yes, then it's true to upgrade this version IDS 4.1 to IPS ver 5.0
I add 4 10/100/1000BaseT ports on ID 4250XL.
Because, I have to deploy IPS to 1 Gbps throughput.
and I could not find an IPS in CISCO will produce 1 Gbit/s with 4-port 10/100/1000BaseT.
How many simultaneous sessions support IPS 4200 series.
How can I use feature Redundant Power Supply on IPS-4255.
Technical documentation 42xx is linked off the coast of http://www.cisco.com/go/ips. I don't know if IPS 5.0 information is still (it's kinda new). There is no option RPS for the 4240/4255, but recommends the use of a UPS would be justified for packaging line if you have unreliable power.
There is no provision for failover in the transducer (other than the bypass mode), but there are drawings (I hope bound off the page that I mentioned above) to do network active / standby designs.
The 4240 and 4255 do not have redundant storage... they have no HDD due to reliability problems. They run a flash and ram disk configuration.
-
HI, I have documentation cisco joint-2 a 500Mbps flow in inline mode and the throughput of 600Mbps in passive.so guess our ihsane-2's in inline mode, then if we put our joint-2 in Bypass mode, how traffic joint-2 can handle without any inspection? (flow)?
Thank you.
The JOINT-2 would be only supported to the same 500Mbps for inspection and by-pass.
There is not a separate ByPass mode ranking.
Having said that, the JOINT-2 will be much higher than 500Mbps in ByPass mode (assuming that nothing else on the sensor).
But I don't know how much of more since don't usually test us the performance in ByPass mode.
You wouldn't want to plan your network on the performance of ByPass capacity.
The other reason is that when the sensor bypass there will be something else in the sensor.
In the case of an update of the Signature, there will be a treatment of signing consuming much of the CPU and memory for ByPass will not perform to its peak performance.
-
Why after connect to my router it take 1-2 minutes to load the router's Web site? No software and the hardware has changed.
Hello
I suggest you check out the link to Linksys support:
-
Backdoor in Cisco routers and firewalls.
The more I read on the NSA scandal (and Yes, I apparently a scandal) less I trust corporations hardware and software. There is no reason for anyone to doubt that all Cisco equipment comes with a backdoor. Because these probable backdoors exist it's a matter of time before hackers discover and exploit them. It's happened to Microsoft a number of times and there is no reason that it could not happen to Cisco. It is no longer our trust Cisco equipment and have already started researching alternatives network.
It is more a crazy conspiracy theory, that is the reality.
In all liklihood, we use a series of firewall to further isolate our network against intrusions. To reduce costs, we can keep our existing in this topology Cisco equipment, but we will replace hardware Cisco when it breaks down or needs to be upgraded. I do the same thing with my home network.
In the last months, we already moved all of our e-mail to secure servers overseas and changed all our McAfee, AVG and Avast antivirus software. We are also researching Linux distributions to replace Microsoft.
If Cisco wants to protect their brand, they need to take a stand or see their market share continue to erode. There must be a CEO to a U.S. company that will take this position and be a hero rather that continue to be a lap dog.
Hello
use open-source based linux firewalls and routers.
and check the source cod
-
configuration Cisco No. 2851 IPS intrusion prevention system
Hi, I wonder - could someone guide me to the implementation of IPS intrusion prevention system. I'm new to the world of cisco and still did not have my head around it. for the intrusion prevention system IPS I put 0/1 (lan) entrants and g 0/0 as a wan?
Hello
You must be careful when activating the IP address of your router. Category will activate you more cpu/memory will be used, and your router may crash.
I'll write all the config as directly here, because it is a good step by step by Cisco:
http://www.Cisco.com/c/en/us/products/collateral/security/iOS-intrusion-...
I'll also join a best practice document from Cisco.
IPS/signature of software should be found on the Cisco's Web site: https://software.cisco.com/download/release.html?mdfid=282941564&reltype...
To answer your question, you can do inbound and outbound on your WAN interface (attacks should come first to the outside).
If you have enough power, why not do as well on the LAN but I will recommend doing it on the WAN, organize and when you're comfortable, you can create one for the LAN interface.
Here is a config I made for a cisco 892 router which works fine:
IP IP config flash card: ips try again 1
IP IP address notify CETS
IPS the ips name iosips IP list
!
category-signature IP ips
all categories
true retreat
category ios_ips base
fake retirement
category all-ddos ddos
fake retirement
enabled true
products-alert event-action connection tcp reset-deny-package-inline connection inline deny deny-attacker-inserted
category, any adware/spyware-adware/spyware
fake retirement
enabled true
products-alert event-action connection tcp reset-deny-package-inline connection inline deny deny-attacker-inserted
category virus/worms/trojans botnet
fake retirement
enabled true
products-alert event-action connection tcp reset-deny-package-inline connection inline deny deny-attacker-inserted
category virus/worms/trojans all-viruses/worms/trojans
fake retirement
enabled true
products-alert event-action connection tcp reset-deny-package-inline connection inline deny deny-attacker-inserted
category models internet_edge
Advanced ios_ips category
fake retirement
!ips-setting IP to auto update
occur - 0 0 06 weekly
Cisco
username password xxxxxx xxxxx!
!
IPS extended IP access list
allow a full tcp
allow a udp
allow icmp a whole
allow an ipI don't know if you have a firewall on your local network, but when I do IPS on a cisco router if there is no firewall, I recommend you to activate ZBF on router itself. This allows to add a little more security.
Just in case, under a ZBF configuration for home router (like the 892 series):
extended access IP MANAGEMENT list
permit tcp any any eq 22
allow icmp a whole
!
Underisable extended IP access list
deny ip host fragments 224.0.0.5
deny ip host fragments 224.0.0.6
refuse the host ip 224.0.0.5 no fragment
refuse the host ip 224.0.0.6 no fragment
permit icmp any any fragment
allow udp any any fragment
permit tcp any any fragment
permit tcp any RST eq 639
permit tcp any RST bgp eq
IP enable any no fragment
!
zbf-wan-to-lan extended IP access list
permit tcp any host 192.168.0.1 eq 3389 ===> internal of the server accessible from the internet (port forwarding)
!
type of class-card inspect entire game Internet
group-access name zbf-wan-to-lan game
class-map correspondence class-mgmt
match the name of group-access MANAGEMENT
unwanted match class-map
match the name of group-access Underisable
type of class-card inspect entire game All_Protocols
tcp protocol match
udp Protocol game
match icmp Protocol
!
type of policy-card inspect Trusted_to_Internet
class type inspect All_Protocols
inspect
class class by default
drop
type of policy-card inspect Trusted
class class by default
Pass
copp-policy policy-map
unwanted class
drop
class class-mgmt
to comply with-police action 2048000 pass drop action exceeds
class class by default
type of policy-card inspect Internet_to_Trusted
class type inspect Internet
inspect
class class by default
drop
!
!
Trusted zone security
Security for the Internet zone
Trusted zone-pair security-> trusted destination trust Trusted source
traffic LAN to LAN Description
type of service-strategy inspect Trusted
Trusted zone-pair security-> Trusted Internet source Internet destination
Description LAN for Internet traffic
type of service-strategy inspect Trusted_to_Internet
security Internet zone - pair-> Trusted Internet source Trusted destination
Description WAN for Internet traffic
type of service-strategy inspect Internet_to_Trusted
!
the g0/0 interface (WAN)
the Member's area Internet Security
!
G0/1 of the interface (LAN)
approved members area security
!Thank you
-
Hi all
Been given an I may not work and would appreciate some comments please. I've been trawling the Cisco docs and got the SPI 7.1 CLI guide but not the info that I need, so I'm a bot snookered.
Customer has a pair of ASA5512X with EPI aboard, located on disk0: / on both devices, which are a pair of failover.
There is a management router we use to access the SAA and switches - below. The SAA with the PPE is the EdgeASA1.
As you will see, there is a Management Vlan that is connected to all devices.
We connect through the VPN client to the management router, then SSH from their to each device as required.
The starter for 10 is...
As the SAA is a failover pair, this also means that the IPS also function as a pair, so working with a shared management IP address? I tried to assign different IP addresses for each FPS and this means that the router management had two ARP entries with the same MAC address.
Whatever the case for the first question, I suspect that the IPS in ASDM tab is only for use with IPS modules that have their own physical interface. Can anyone confirm (or not) that this is the case, please?
If this is the case, it seems that the only way to run the IPS is a cli.
If someone has something, I would be very happy.
Thank you very much
Ali
IP addresses can be managed through the M0/0 interface. The URL below describes the connection options for IPS belonging to the family of 55xx-X ASA:
http://www.Cisco.com/en/us/products/sw/secursw/ps2113/products_tech_note09186a0080bd5d03.shtml
-
Cisco VCS and integration Lync2013
Hello!
Could you tell me please, when CISCO officially support Lync2013 - free new software for VCS - C and documentation on integration?
The main interest is the possibility of transferring video between CISCO/MCU and Lync endpoints on the H.264 Protocol, who hails from Lync2013.
Right now, I've got VCS - C and RTM Lync2013 X7.2. During the video call without AMGW appeal established as audio only.
When using with Lync2010, it worked on Protocol H.263 and CIF resolution.
Evgeniy salvation,
We are currently investigating the possibilities to achieve interoperability between Lync 2013, VCS and video devices on the side of the VCS standards-based, it is a work in progress and at this stage, it is to early to provide any factual information on when interop will be available.
In contrast to Lync 2010, Lync 2013 does not support H.263 for video and it so that will remove the OCS/Lync integration. I do however think that you should be able to make a two-way video between Lync 2013 and VCS-joined endpoints if you use an AMGW tried that yet?
Thank you
Andreas
-
Placement of IDS and IPS, inside or outside?
Hello
I have an IDS and IPS, now decide where they should be placed. ID inside and outside of the firewall IPS, or vice versa. Ive read various advantages and disadvantages, but I would like to get some advice from people who have experience in investment.
Thank you
The SAA is a firewall that has the IDS/IPS functionality, in addition to other things - where a "security device".
As a firewall, the device of the SAA is placed on the edge of the network, i.e., probably as the first device inside the WAN (bridge, modem) connection, although sometimes it makes sense to have a router on the outside, especially if there are multiple connections to ISPS for redundancy, load balancing, or quality of Service implementations.
What ASA model are we talking about?
IDS/IPS functionality produced inside the unit - there is a "module" that is internal to the unit that manages the functions. In the case of the IPS, it will prevent the malicious traffic to enter your organization (often called inside network) network. In the case of the IDS, it will report all traffic and issue a warning by all means have been configured. These correspond vaguely to inline mode and "Promiscuous" mode respectively.
I'm no expert, but I hope I could help answer your original question...
jeremyNLSO
Berlin, Germany -
Cisco show and share to publish on the internet
Dear Experts
We have new deployment for Cisco SNS, and we publish SNS on the internet. I need help to do it and any recommendations, please.
Thank you
Richard
Hi Richard
Solve you your problem? I have to make sure of the following.
1. you can access external SNS internally.
2-natting is ok between IP Public & private.
3. for the DNS record, make sure that the name must be the same on the inside & outside. For example internlly vod.bnp.med.ca and create a record public vod.bnp.med.ca should be the same FQDN, otherwise your SNS will never work. For authentication, you must publish the DMM.
Note: your question this internal FQDN differs from the external FQDN of the SNS.
Thank you
Please note all relevant information
-
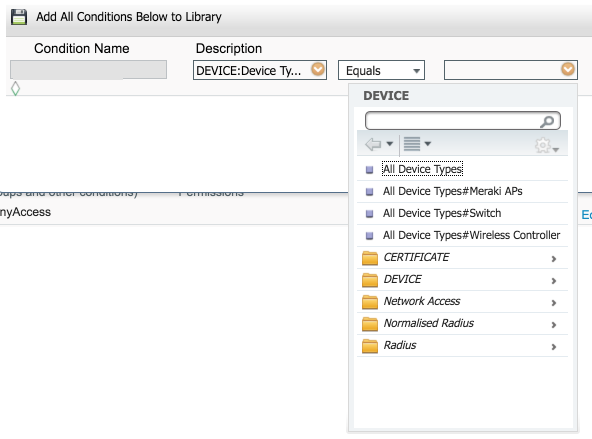
I am very new to Cisco ISE and Meraki. I try to get the Radius configuration for wireless authentication. When I do a test of the Meraki to ISE, it passes.
When I try to connect from my laptop, I look at the logs of the Radius and it passes; However, it does not connect me to good policy. I keep hitting the default policy. I have my Meraki police above the default policy in the strategy defined in article. I have attached what looks like my strategy game.
Devices does not really matter. Here is what I see when I create a device group (where you add the access point to this group), and then create the condition:
And here is where I create the condition of strategy game and you should be able to select the Meraki access points:
This will give you the condition similar to what I posted above. This is perhaps why you aren't hit that is not matching the condition for this game.
-
Cisco ACS GANYMEDE + AAA can be activated for telnet to Cisco 600 and 700 routers?
Unfortunately you can not configure radius AAA or Ganymede in routers series 600 or 700.
-
The traffic load between the power of Cisco ASA and FireSight Management Center fire
Hi all
I have a stupid question to ask.
Can I know what is the traffic load and the e/s flow between firepower Cisco ASA and FireSight Management Center?
Currently working on a project, client require such information to adapt to their network. Tried to find in the document from Cisco, but no luck.
Maybe you all have no idea to provide.
It varies depending on the number of events reported from the module to the CSP. No event = only health controls and policy changes are exchanged. 10,000 events per second = much more traffic.
Generally it is not a heavy load, however.
-
What is the difference between Cisco NAC and ACS?
I am currently part of a new construction project and my Cisco account manager and sales engineer recommend Cisco NAC for our new MDF. I'm confused because I don't clearly know the difference between a Cisco ACS and the NAC. What is the difference?
Thank you
Chris
Chris,
The two are completely different, maybe the sales rep could present you with more information and application. Each offers a variety of services tailored to the specific needs. I think that we need to read more in depth on the proceeds of the NAC. NAC seems an excellent solution for authentication authorization but other regulatory compliance.
When you see ask your representative to sales for more information/demo.
ACS is more widely use as a central point to access control to network devices routers, an example is for acs accounting management and the authority to order on all devices on the network using acs as RADIUS server. Considering that the NAC is over a central point of safety inspection on earlier systems of access to your network by via LAN or outside, an example of these respected regulatory defined could be inspections could be virus definition checks before getting lan access thus preventing access to the LAN if the system does not have regulatory compliance defined in NAC access is denied. Another example could be the unknown local host connections etc... So, it seems that NAC is a much broader product that provides endpoint security internal, not only the authentication authorization as acs... ACS has been there for a long time, NAC is rather new product.
NAC
http://www.Cisco.com/en/us/NetSol/ns466/networking_solutions_package.html
ACS
http://www.Cisco.com/en/us/products/sw/secursw/ps5338/index.html
Rgds
Jorge
Maybe you are looking for
-
Tab titles Safari do not expand fully when I hover over title to label
Before my 10.11.4 ElCapitan updated, if I had a few tabs open in a Safari window and toss over a tab title it would display the full title of the tab for example instead of "start new Di... "the title could expand to" start new Discussion " Community
-
External USB HDD PX1269E - 1 50 cannot be recognized on computer
Hello I recently bought an external hard drive, Toshiba 500 GB external USB Hard Drive PX1269E - 1 50 I want to use it on my Pentium 4 3.6 ghz memory 1 GB 400 GB internal hard drive and motherboard ASUS P4P800.I installed Windows XP Profesional SP2 o
-
Satellite A100-151: BIOS Downgrade
Hello I upgraded my BIOS Notebook´s to Version 1.80.Now, I have some problems of grafical (screen looks a bit like JPG-arthefacts). Not nice.Is it possible to downgrade the (before the upgrade is recorded) BIOS-file BIOS. BAK?If the answer is "Yes",
-
Had a big storm - got the new modem. but they said that my drivers where missing or damaged. Downloaded Marvell Yukon of gateway - to the GT5432 model. Always says cable unplugged network. However, Bishop says peripheral device works correctly. Don
-
Changed to the Vista Basic theme
PC SWITCHED TO VISTA BASIC, I'M USING VISTA PREMIUM DUE TO THE AERO. I HAVE AN UPDATE THAT IS ONE OPTION FOR NVIDIA GEFORCE. THIS COULD BE THE PROBLEM